

The challenge
Preferably, role assignments are automated through privileged release pipelines. The two PowerShell commands that can be used to automate this – New-AzureADServiceAppRoleAssignment and New-AzureADUserAppRoleAssignment – are not easy to use, as it is not always clear what the exact Ids are that you have to provide.
The solution
That’s why I prefer to automate this based on display names and let a script take care of fetching the required Ids. Lately, I have developed such a script to assign Azure AD application roles to users and applications. Hereby, I share it with the community. The script can be found in this gist .
Config file
The script is driven by a simple config file , that contains a JSON array of role assignments:
- description : free text field that describes the role assignment
- client_type : “user” or “application”
- client_principal_name: the users’ UPN ([email protected]) or the display name of the service principal (enterprise application)
- server_app_registration_name : the display name of the app registration to which you want to grant the client access
- role_name the display name of the application role you want to assign to the configured client
You can use the script like this:
- Download the script and the config file.
- Update the config files to your needs
- Trigger the script via PowerShell
If you are interested, this is how the script looks like:
I hope that this script helps you to accelerate your security automation.
Cheers Toon
UPCOMING TRAININGS
CHECK OUT OUR TRAININGS
Azure Integration Services
Azure migration.
- Azure Governance
Azure Security
Azure foundations, recent posts.
- Azure Service Bus vs Event Grid Pull Delivery
- Trying the new Microsoft Applied Skills
- Finally a correct way to configure RBAC for DevOps agents!
- What do the new API Management v2 tiers mean for you?
- Validate payloads in Azure API Management
- Announcement
- API Management
- Architecture
- Azure App Service
- Azure Data Factory
- Azure DevOps
- Azure Event Grid
- Azure Functions
- Azure Kubernetes Service
- Azure Policy
- Azure Resource Graph
- Azure Resource Manager
- Azure Service Bus
- Azure Stream Analytics
- BizTalk Server
- Container Apps
- Geen categorie
- Home Automation
- Microsoft Learn
- Service Bus
MEET THE YOUR AZURE COACH TEAM
Your Azure Coach is specialized in organizing Azure trainings that are infused with real-life experience. All our coaches are active consultants, who are very passionate and who love to share their Azure expertise with you.
Toon Vanhoutte
Azure integration services & serverless.

Wim Matthyssen
Azure infra, security & governance, azure development and ai/ml, azure identity and security, stéphane eyskens, cloud-native azure architecture, geert baeke, azure kubernetes service & containerization, maik van der gaag, azure infrastructure as code & devops, bart verboven, sammy deprez, azure ai, ml & cognitive services, sander van de velde.

Manage Azure Role Assignments Like a Pro with PowerShell
Today’s blog post is a little bit different. I have a couple of examples of how you can use PowerShell snippets and simple commandlets to get or set role assignmnets in your Azure Subscriptions.
PowerShell examples for managing Azure Role assignments
List all role assignments in a subscription, get all role assignments for a specific resource group, get all role assignments for a specific user, add a role assignment to a user, remove a role assignment for a user, remove all role assignments for a specific user, list all built-in roles, list all custom roles, create a custom role, update a custom role, delete a custom role, list all users or groups assigned to a specific role, list all permissions granted by a specific role, list all resource groups that a user has access to, create a role assignment for a service principal, powershell script to manage azure role assignments.
And now there is a script that combines some of these examples into one usable function:
I hope this was useful. Let me know if you liked the format of this blog and if you want me to include more of these examples.
Vukasin Terzic
Recent Update
- Writing your first Azure Terraform Configuration
- Transition from ARM Templates to Terraform with AI
- Getting started with Terraform for Azure
- Terraform Configuration Essentials: File Types, State Management, and Provider Selection
- Dynamically Managing Azure NSG Rules with PowerShell
Trending Tags
Retrieve azure resource group cost with powershell api.
The Future Of Azure Governance: Trends and Predictions
Further Reading
In my previous blog posts, I wrote about how simple PowerShell scripts can help speed up daily tasks for Azure administrators, and how you can convert them to your own API. One of these tasks is...
Azure Cost Optimization: 30 Ways to Save Money and Increase Efficiency
As organizations continue to migrate their applications and workloads to the cloud, managing and controlling cloud costs has become an increasingly critical issue. While Azure provides a robust s...
Custom PowerShell API for Azure Naming Policy
To continue our PowerShell API series, we have another example of a highly useful API that you can integrate into your environment. Choosing names for Azure resources can be a challenging task. ...

a blog by Sander Berkouwer
- The things that are better left unspoken
HOWTO: Get an overview of the Privileged roles assigned within an Azure AD tenant

Unless you’re using the Azure AD Privileged Identity Management (PIM) portal features from your tenant’s Azure AD Premium P2 licenses, you might have a hard time to get an overview of the Privileged roles assigned within an Azure AD tenant.
There is, however, a free, easy and Microsoft-supported way, using the AzureADIncidentResponse Windows PowerShell module.
Getting ready
First, we need to install the Windows PowerShell modules we need. Perform the following lines of Windows PowerShell in an elevated Windows PowerShell session:
Install-Module AzureAD -Force
Install-Module MSOnline -Force
Install-PackageProvider NuGet -Force
Install-Module PowerShellGet -Force
&( Get-Process -Id $pid ). Path -Command { Install-Module MSAL.PS }
Install-Module AzureADIncidentResponse
Note: We need to install both the AzureAD and MSOnline modules, as the output of these modules differs. This is the state of Azure AD PowerShell today . The above lines update the PowerShell modules, if you don’t run the latest versions.
Note: If you receive error ‘Unable to download’ when you try to install the AzureAD or MSOnline PowerShell Module, use these steps to resolve the situation .
Getting Azure AD Privileged roles
Microsoft shared its Azure AD Incident Response Windows PowerShell module on the PowerShell Gallery. Using the cmdlets in this Windows PowerShell module, we can easily get an overview of the Privileged roles assigned within an Azure AD tenant.
Run the following lines of Windows PowerShell to do so:
Import-Module AzureADIncidentResponse
Connect-AzureADIR <YourTenantId>
Sign in with an account with sufficient permissions to read privileged roles within your Azure AD tenant. By default, any user account and guest account can be used, unless account enumeration is disabled in Azure Active Directory . By default, any guest user account can be used, unless their permissions have been restricted.
Get-AzureADIRPrivilegedRoleAssignment <YourTenantId> | Out-GridView
These lines of Windows PowerShell result in a GridView window displaying the DirectoryRole containing the privileged role assignment and its DirectoryRoleObjectId . Per role, the RoleMemberName , RoleMemberObjectType (typically User or ServicePrinicpal ), RoleMemberUPN and RoleMemberObjectId are displayed. The RoleMemberEnabled column provides information on the status of the role assignment. RoleMemberMail and RoleMemberAlternateEmail can be used to contact a privileged user if need be. Finally, RoleMemberOnPremDn provides the distinguished name (DN) attribute for the privileged user, if the user is synchronized from on-premises.
This information is presented per privileged role. If a user or service principal has multiple roles, multiple lines indicate these role memberships.
The information can be used to:
- Seek out dangerous service principals with privileged roles.
While initially conceived as an incident response tool, the Azure AD Incident Response Windows PowerShell module proves useful for many other investigations.
Posted on April 21, 2021 by Sander Berkouwer in Entra ID
One Response to HOWTO: Get an overview of the Privileged roles assigned within an Azure AD tenant

Super helpful today. Thank you
leave your comment cancel
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Advertisement

Search this site
Dirteam.com / activedir.org blogs.
- Strategy and Stuff
- Dave Stork's IMHO
- The way I did it
- Sergio's Shack
- Things I do
- Tomek's DS World
Microsoft MVP (2009-2024)
Veeam vanguard (2016-2024), vmware vexpert (2019-2022).

Xcitium Security MVP (2023)

Recent Posts
- Some Domain Controllers may restart unexpectedly after applying the March 12, 2024 Updates
- Pictures of the Dutch Workplace Ninja's meetup at Pink Elephant
- I'm presenting at the Veeam User Group Netherlands meetup
- On-premises Identity-related updates and fixes for February 2024
- What's New in Entra ID for February 2024
Recent Comments
- Andy on Ten things you need to be aware of before using the Protected Users Group
- Cédric on Ten things you need to be aware of before using the Protected Users Group
- Sander Berkouwer on Ten things you should know about Azure AD Connect and Azure AD Sync
- Thanny Lopez on Ten things you should know about Azure AD Connect and Azure AD Sync
- Bill on TODO: Move from the ‘Allow users to remember multi-factor authentication on devices they trust’ option to Conditional Access
The information on this website is provided for informational purposes only and the authors make no warranties, either express or implied. Information in these documents, including URL and other Internet Web site references, is subject to change without notice. The entire risk of the use or the results from the use of this document remains with the user. Active Directory, Microsoft, MS-DOS, Windows, Windows NT, and Windows Server are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. All other trademarks are property of their respective owners.
- Career Model
- Proactive Mentorship
- Productivity
- Review Model
- Work:Life Balance
- 3D Printing
- Announcements
- Conferences
How to find all the Azure Built-In Roles for Azure RBAC with Azure CLI, PowerShell, Docs, or AzAdvertizer
Here are a bunch of ways you can find which roles are built into Azure. This will come in super handy when you need to assign a role to a service principal or user with Azure CLI commands like this:
- Query the big honking json
- Query all, but only return Name and Id in a nice table
- Filter by name contains:
This one filters for roles with “Map” in the name:
Azure PowerShell
https://docs.microsoft.com/en-us/powershell/module/az.resources/get-azroledefinition?view=azps-3.8.0
This page has all the built in roles: https://docs.microsoft.com/azure/role-based-access-control/built-in-roles

AzAdvertizer
Just found this site today by Julian Hayward. It’s a great way to find roles
https://www.azadvertizer.net/azrolesadvertizer_all.html

Azure RBAC: role assignments and ARM templates

This post is about Azure's role assignments and ARM templates. Role assignments can be thought of as "permissions for Azure".
If you're deploying to Azure, there's a good chance you're using ARM templates to do so. Once you've got past "Hello World", you'll probably find yourself in a situation when you're deploying multiple types of resource to make your solution. For instance, you may be deploying an App Service alongside Key Vault and Storage .
One of the hardest things when it comes to deploying software and having it work, is permissions. Without adequate permissions configured, the most beautiful code can do nothing . Incidentally, this is a good thing. We're deploying to the web; many people are there, not all good. As a different kind of web-head once said:

Azure has great power and suggests you use it wisely .
Access management for cloud resources is critical for any organization that uses the cloud. Azure role-based access control (Azure RBAC) helps you manage who has access to Azure resources, what they can do with those resources, and what areas they have access to. Designating groups or individual roles responsible for specific functions in Azure helps avoid confusion that can lead to human and automation errors that create security risks. Restricting access based on the need to know and least privilege security principles is imperative for organizations that want to enforce security policies for data access.
This is good advice. With that in mind, how can we ensure that the different resources we're deploying to Azure can talk to one another?
Role (up for your) assignments
The answer is roles. There's a number of roles that exist in Azure that can be assigned to users, groups, service principals and managed identities. In our own case we're using managed identity for our resources. What we can do is use "role assignments" to give our managed identity access to given resources. Arturo Lucatero gives a great short explanation of this:
Whilst this explanation is delightfully simple, the actual implementation when it comes to ARM templates is a little more involved. Because now it's time to talk "magic" GUIDs. Consider the following truncated ARM template, which gives our managed identity (and hence our App Service which uses this identity) access to Key Vault and Storage:
Let's take a look at these three variables:
The three variables above contain the subscription resource ids for the roles Storage Blob Data Contributor , Key Vault Secrets Officer and Key Vault Crypto Officer . The first question on your mind is likely: "what is ba92f5b4-2d11-453d-a403-e96b0029c9fe and where does it come from?" Great question! Well, each of these GUIDs represents a built-in role in Azure RBAC. The ba92f5b4-2d11-453d-a403-e96b0029c9fe represents the Storage Blob Data Contributor role.
How can I look these up? Well, there's two ways; there's an article which documents them here or you could crack open the Cloud Shell and look up a role by GUID like so:
Or by name like so:
As you can see, the Actions section of the output above (and in even more detail on the linked article ) provides information about what the different roles can do. So if you're looking to enable one Azure resource to talk to another, you should be able to refer to these to identify a role that you might want to use.
Creating a role assignment
So now we understand how you identify the roles in question, let's take the final leap and look at assigning those roles to our managed identity. For each role assignment, you'll need a roleAssignments resource defined that looks like this:
Let's go through the above, significant property by significant property (it's also worth checking the official reference here ):
- type - the type of role assignment we want to create, for a key vault it's "Microsoft.KeyVault/vaults/providers/roleAssignments" , for storage it's "Microsoft.Storage/storageAccounts/providers/roleAssignments" . The pattern is that it's the resource type, followed by "/providers/roleAssignments" .
- dependsOn - before we can create a role assignment, we need the service principal we desire to permission (in our case a managed identity) to exist
- properties.roleDefinitionId - the role that we're assigning, provided as an id. So for this example it's the keyVaultCryptoOfficer variable, which was earlier defined as [subscriptionResourceId('Microsoft.Authorization/roleDefinitions', 'ba92f5b4-2d11-453d-a403-e96b0029c9fe')] . (Note the use of the GUID)
- properties.principalId - the id of the principal we're adding permissions for. In our case this is a managed identity (a type of service principal).
- properties.scope - we're modifying another resource; our key vault isn't defined in this ARM template and we want to specify the resource we're granting permissions to.
- properties.principalType - the type of principal that we're creating an assignment for; in our this is "ServicePrincipal" - our managed identity.
There is an alternate approach that you can use where the type is "Microsoft.Authorization/roleAssignments" . Whilst this also works, it displayed errors in the Azure tooling for VS Code . As such, we've opted not to use that approach in our ARM templates.
Many thanks to the awesome John McCormick who wrangled permissions with me until we bent Azure RBAC to our will.
- Role (up for your) assignments
- Creating a role assignment

- Adding or removing role assignments using Azure Portal
Go back to AZ-304 Tutorials
In this article you will learn about assigning roles using Azure portal and the process of adding and removing role assignments.
However, Azure’s role-based access control (RBAC) refers to the authorization system for managing access to Azure resources. And, to grant access, you assign roles to users, groups, service principals, or managed identities at a particular scope.
Prerequisites
For adding or removing role assignments, you must have:
- Firstly, Microsoft.Authorization/roleAssignments/write
- Secondly, Microsoft.Authorization/roleAssignments/delete permissions, such as User Access Administrator or Owner
Access control (IAM)
Access control (IAM) is the page that is for assigning roles to grant access to Azure resources. It’s also known as identity and access management and appears in several locations in the Azure portal. There are questions for assigning roles to help in understanding about the Access control (IAM) page.
- Who needs access? This refers to a user, group, service principal, or managed identity.
- What role do they need? Permissions are grouped together into roles, so you can select from a list of several built-in roles orcan use custom roles.
- Where do they need access? This refers to the set of resources that the access applies to. However, “where” can be a management group, subscription, resource group, or a single resource such as a storage account.
Adding a role assignment
- Firstly, in the Azure portal, click All services and then select the scope that you want to grant access to.
- Secondly, click the specific resource for that scope.
- Then, Click Access control (IAM).
- Fourthly, click the Role assignments tab for viewing the role assignments at this scope.
- After that, click Add > Add role assignment. However, if you don’t have permissions to assign roles, the Add role assignment option will be disabled.
- Then, in the Role drop-down list, select a role such as Virtual Machine Contributor.
- There in the Select list, select a user, group, service principal, or managed identity. And, if you don’t see the security principal in the list, you can type in the Select box to search the directory for display names, email addresses, and object identifiers.
- Lastly, click Save to assign the role.
Assigning a user as an administrator of a subscription
For giving users the role of an administrator of an Azure subscription, first assign them the Owner role at the subscription scope. As the Owner role gives the user full access to all resources in the subscription, including the permission to grant access to others. However, these steps are the same as any other role assignment.
- Firstly, in the Azure portal, click All services and then Subscriptions.
- Then, click the subscription where you want to grant access.
- Thirdly, click Access control (IAM).
- After that, click the Role assignments tab to view the role assignments for this subscription.
- Then, click Add > Add role assignment. However, if you don’t have permissions to assign roles, the Add role assignment option will be disabled.
- And, in the Role drop-down list, select the Owner role.
- Then, in the Select list, select a user.

Adding a role assignment for a managed identity
For adding role assignments for a managed identity use the Access control (IAM) page. However, when you use the Access control (IAM) page, you start with the scope and then select the managed identity and role. In this section, you will learn about an alternate way to add role assignments for a managed identity. Using these steps, you start with the managed identity and then select the scope and role.
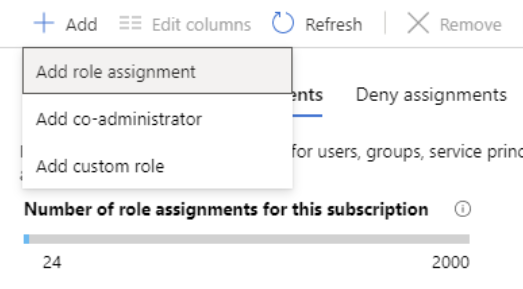
System-assigned managed identity
- Use these steps for assigning a role to a system-assigned managed identity by starting with the managed identity.
- Firstly, in the Azure portal, open a system-assigned managed identity. Then, in the left menu, click Identity.
- After that, under Permissions, click Azure role assignments. However, if roles are already assigned to the selected system-assigned managed identity then you will see the list of role assignments.
- For changing the subscription, click the Subscription list. Then, click Add role assignment.
- Then, use the drop-down lists to select the set of resources that the role assignment applies to such as Subscription, Resource group, or resource. And, if you don’t have role assignment write permissions for the selected scope, an inline message will be displayed.
- After that, in the Role drop-down list, select a role such as Virtual Machine Contributor.
User-assigned managed identity
- Use these steps for assigning a role to a user-assigned managed identity by starting with the managed identity.
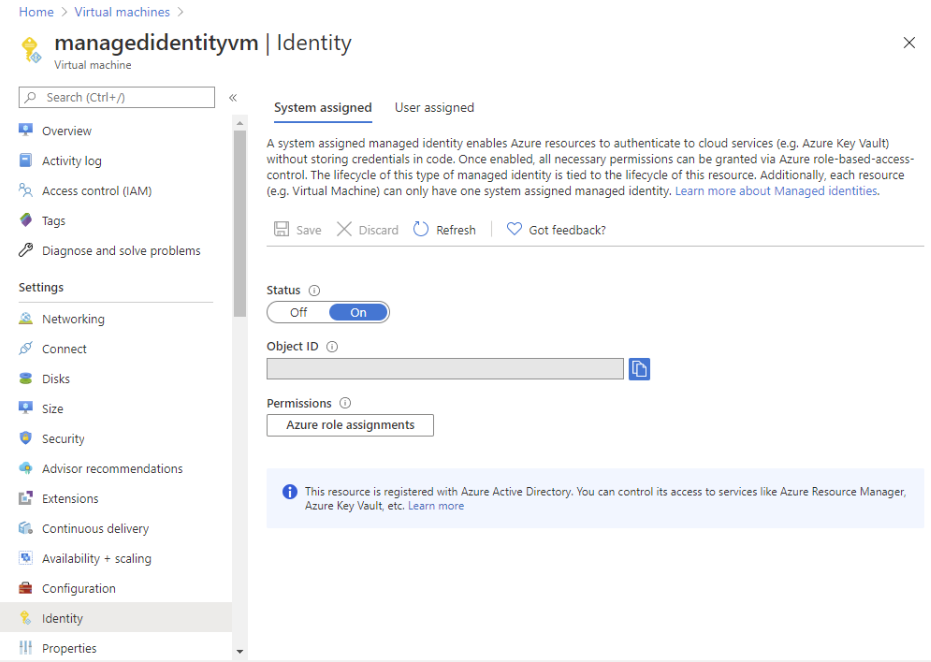
- Firstly, in the Azure portal, open a user-assigned managed identity. Then, in the left menu, click Identity.
- After that, under Permissions, click Azure role assignments. However, if roles are already assigned to the selected user-assigned managed identity then you will see the list of role assignments.
Removing a role assignment
In Azure RBAC, for removing access from an Azure resource, you first remove a role assignment. Use these steps to remove a role assignment.
- Firstly, Open Access control (IAM) at a scope, such as management group, subscription, resource group, or resource, where you want to remove access.
- Then, click the Role assignments tab to view all the role assignments for this subscription.
- After that, in the list of role assignments, add a checkmark next to the security principal with the role assignment you want to remove.
- Then, Click Remove.
- Lastly, in the remove role assignment message that appears, click Yes.
However, if you see a message that inherited role assignments cannot be removed, then you are trying to remove a role assignment at a child scope. So, you should open Access control (IAM) at the scope where the role was assigned and try again.

Reference: Microsoft Documentation
Prepare for Assured Success
Search code, repositories, users, issues, pull requests...
Provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement . We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
azurerm_role_assignment.role_definition_id changes upon every apply #25328
unique-dominik commented Mar 20, 2024 • edited
magodo commented Mar 21, 2024
Besides, regarding the source of the azurerm_role_assignment.role_definition_id , i.e. the azurerm_role_definition.role_definition_resource_id , its format depends on how we GET it. As a role definition can have multiple assignable scopes, it means you can GET it via different prefix scopes. Depending on how you GET it (e.g. with only the scope prefix, or with one of the assignable_scopes ), it makes the result response's id has the same scope prefix.
Back to the first issue, as the provider version didn't change, and also the API behavior shall remain still. I suspect you've some out-of-band change on the azurerm_role_definition resource (e.g. change of the scope).
- 👀 1 reaction
Sorry, something went wrong.
unique-dominik commented Mar 22, 2024
- 👍 1 reaction
No branches or pull requests
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Steps to assign an Azure role
- 3 contributors
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To grant access, you assign roles to users, groups, service principals, or managed identities at a particular scope. This article describes the high-level steps to assign Azure roles using the Azure portal , Azure PowerShell , Azure CLI , or the REST API .
Step 1: Determine who needs access
You first need to determine who needs access. You can assign a role to a user, group, service principal, or managed identity. This is also called a security principal .

- User - An individual who has a profile in Microsoft Entra ID. You can also assign roles to users in other tenants. For information about users in other organizations, see Microsoft Entra B2B .
- Group - A set of users created in Microsoft Entra ID. When you assign a role to a group, all users within that group have that role.
- Service principal - A security identity used by applications or services to access specific Azure resources. You can think of it as a user identity (username and password or certificate) for an application.
- Managed identity - An identity in Microsoft Entra ID that is automatically managed by Azure. You typically use managed identities when developing cloud applications to manage the credentials for authenticating to Azure services.
Step 2: Select the appropriate role
Permissions are grouped together into a role definition . It's typically just called a role . You can select from a list of several built-in roles. If the built-in roles don't meet the specific needs of your organization, you can create your own custom roles.

Roles are organized into job function roles and privileged administrator roles.
Job function roles
Job function roles allow management of specific Azure resources. For example, the Virtual Machine Contributor role allows a user to create and manage virtual machines. To select the appropriate job function role, use these steps:
Begin with the comprehensive article, Azure built-in roles . The table at the top of the article is an index into the details later in the article.
In that article, navigate to the service category (such as compute, storage, and databases) for the resource to which you want to grant permissions. The easiest way to find what your looking for is typically to search the page for a relevant keyword, like "blob", "virtual machine", and so on.
Review the roles listed for the service category and identify the specific actions you need. Again, always start with the most restrictive role.
For example, if a security principal needs to read blobs in an Azure storage account, but doesn't need write access, then choose Storage Blob Data Reader rather than Storage Blob Data Contributor (and definitely not the administrator-level Storage Blob Data Owner role). You can always update the role assignments later as needed.
If you don't find a suitable role, you can create a custom role .
Privileged administrator roles
Privileged administrator roles are roles that grant privileged administrator access, such as the ability to manage Azure resources or assign roles to other users. The following roles are considered privileged and apply to all resource types.
For best practices when using privileged administrator role assignments, see Best practices for Azure RBAC . For more information, see Privileged administrator role definition .
Step 3: Identify the needed scope
Scope is the set of resources that the access applies to. In Azure, you can specify a scope at four levels: management group , subscription, resource group , and resource. Scopes are structured in a parent-child relationship. Each level of hierarchy makes the scope more specific. You can assign roles at any of these levels of scope. The level you select determines how widely the role is applied. Lower levels inherit role permissions from higher levels.

When you assign a role at a parent scope, those permissions are inherited to the child scopes. For example:
- If you assign the Reader role to a user at the management group scope, that user can read everything in all subscriptions in the management group.
- If you assign the Billing Reader role to a group at the subscription scope, the members of that group can read billing data for every resource group and resource in the subscription.
- If you assign the Contributor role to an application at the resource group scope, it can manage resources of all types in that resource group, but not other resource groups in the subscription.
It's a best practice to grant security principals the least privilege they need to perform their job. Avoid assigning broader roles at broader scopes even if it initially seems more convenient. By limiting roles and scopes, you limit what resources are at risk if the security principal is ever compromised. For more information, see Understand scope .
Step 4: Check your prerequisites
To assign roles, you must be signed in with a user that is assigned a role that has role assignments write permission, such as Role Based Access Control Administrator at the scope you are trying to assign the role. Similarly, to remove a role assignment, you must have the role assignments delete permission.
- Microsoft.Authorization/roleAssignments/write
- Microsoft.Authorization/roleAssignments/delete
If your user account doesn't have permission to assign a role within your subscription, you see an error message that your account "does not have authorization to perform action 'Microsoft.Authorization/roleAssignments/write'." In this case, contact the administrators of your subscription as they can assign the permissions on your behalf.
If you are using a service principal to assign roles, you might get the error "Insufficient privileges to complete the operation." This error is likely because Azure is attempting to look up the assignee identity in Microsoft Entra ID and the service principal cannot read Microsoft Entra ID by default. In this case, you need to grant the service principal permissions to read data in the directory. Alternatively, if you are using Azure CLI, you can create the role assignment by using the assignee object ID to skip the Microsoft Entra lookup. For more information, see Troubleshoot Azure RBAC .
Step 5: Assign role
Once you know the security principal, role, and scope, you can assign the role. You can assign roles using the Azure portal, Azure PowerShell, Azure CLI, Azure SDKs, or REST APIs.
You can have up to 4000 role assignments in each subscription. This limit includes role assignments at the subscription, resource group, and resource scopes. You can have up to 500 role assignments in each management group. For more information, see Troubleshoot Azure RBAC limits .
Check out the following articles for detailed steps for how to assign roles.
- Assign Azure roles using the Azure portal
- Assign Azure roles using Azure PowerShell
- Assign Azure roles using Azure CLI
- Assign Azure roles using the REST API
- Tutorial: Grant a user access to Azure resources using the Azure portal
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources

IMAGES
VIDEO
COMMENTS
Prerequisites. PowerShell in Azure Cloud Shell or Azure PowerShell; List role assignments for the current subscription. The easiest way to get a list of all the role assignments in the current subscription (including inherited role assignments from root and management groups) is to use Get-AzRoleAssignment without any parameters.. Get-AzRoleAssignment
In the Azure portal, select All services from the Azure portal menu. Select Microsoft Entra ID and then select Users or Groups. Click the user or group you want list the role assignments for. Click Azure role assignments. You see a list of roles assigned to the selected user or group at various scopes such as management group, subscription ...
List role assignments for a user. To list the role assignments for a specific user, use az role assignment list: Azure CLI. az role assignment list --assignee {assignee} By default, only role assignments for the current subscription will be displayed. To view role assignments for the current subscription and below, add the --all parameter.
1.Use Azure portal: Navigate to the vnet in the portal -> Access control (IAM) -> Role assignments -> search for the name of your service principal like below. 2.Use Azure CLI: az role assignment list --assignee SP_CLIENT_ID --scope VNET_ID. Share.
Azure RBAC at the management group level. Sonia's account is showing the scope as the SCuffSubsMG, not the subscription ID. That's because her Owner access to the current subscription is determined by a role assignment that has been added at the management group level, and as this subscription belongs to that management group, the role assignment is inherited too.
The script is driven by a simple config file, that contains a JSON array of role assignments: description: free text field that describes the role assignment. client_type: "user" or "application". client_principal_name: the users' UPN ([email protected]) or the display name of the service principal (enterprise application)
Learn how to manage Azure Role assignments using PowerShell snippets and simple commandlets. Discover examples for listing all role assignments, adding and removing assignments for users or service principals, creating custom roles, and more. Plus, check out a script that combines some of these examples into a single function. Written by Vukasin Terzic.
Unless you're using the Azure AD Privileged Identity Management (PIM) portal features from your tenant's Azure AD Premium P2 licenses, you might have a hard time to get an overview of the Privileged roles assigned within an Azure AD tenant. There is, however, a free, easy and Microsoft-supported way, using the AzureADIncidentResponse Windows PowerShell module. […]
This will come in super handy when you need to assign a role to a service principal or user with Azure CLI commands like this: az role assignment create --assignee 3db3ad97-06be-4c28-aa96-f1bac93aeed3 --role "Azure Maps Data Reader" Azure CLI. Query the big honking json; az role definition list Query all, but only return Name and Id in a nice table
Description. Use the Get-AzRoleAssignment command to list all role assignments that are effective on a scope. Without any parameters, this command returns all the role assignments made under the subscription. This list can be filtered using filtering parameters for principal, role and scope. The subject of the assignment must be specified.
When you create a role assignment by using the Azure portal, Azure PowerShell, or the Azure CLI, the creation process gives the role assignment a unique name for you automatically. \n If you create a role assignment by using Bicep or another infrastructure as code (IaC) technology, you need to carefully plan how you name your role assignments.
John Reilly. This post is about Azure's role assignments and ARM templates. Role assignments can be thought of as "permissions for Azure". If you're deploying to Azure, there's a good chance you're using ARM templates to do so. Once you've got past "Hello World", you'll probably find yourself in a situation when you're deploying multiple types ...
Use the Microsoft Entra ID object ID to identify the principal that you want to assign the role to. When you create a role assignment by using Azure PowerShell, the Azure CLI, Bicep, or another infrastructure as code (IaC) technology, you specify the principal type. Principal types include User, Group, and ServicePrincipal.
Adding a role assignment. Firstly, in the Azure portal, click All services and then select the scope that you want to grant access to. Secondly, click the specific resource for that scope. Then, Click Access control (IAM). Fourthly, click the Role assignments tab for viewing the role assignments at this scope.
Step 2: On the Members tab, select the user you want to delegate the role assignments task to. Figure 3: Select members. Step 3: On the Condition tab, click Add condition to add the condition to the role assignment. Figure 4: Add condition to role assignment. Step 4: On the Add role assignment condition page, specify how you want to constrain ...
from azure.identity import DefaultAzureCredential from azure.mgmt.authorization import AuthorizationManagementClient """ # PREREQUISITES pip install azure-identity pip install azure-mgmt-authorization # USAGE python role_assignments_get_by_id.py Before run the sample, please set the values of the client ID, tenant ID and client secret of the ...
@unique-dominik There are two issues around this:. Why the first diff occurs; Why the plan diff after apply occurs; Begin with the 2nd one: The role assignment service will conditionally modify the role_definition_id depending on the azurerm_role_assignment.scope.. E.g. given:
Step 2: Select the appropriate role. Step 3: Identify the needed scope. Step 4: Check your prerequisites. Show 2 more. Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To grant access, you assign roles to users, groups, service principals, or managed identities at a particular ...
Provisioning scope. There are two ways you can sync accounts from Microsoft Entra ID to Apple Business Manager. Sync only assigned users and groups: This option syncs only the accounts that appear in the Apple Business Manager Entra ID app to Apple Business Manager. When using this method to sync, Microsoft Entra ID accounts must have the role of user to sync to Apple Business Manager.
This command queries the user's currently active Entra ID roles, therefore including all statically assigned roles (in addition to roles currently enabled via PIM). The command already respects roles that come via role assignable groups. We add two additional properties to make the output more digestable.
1 Answer. Sorted by: 1. You van have a look at the Azure build in RBAC roles. It would come down to: resource "azurerm_role_assignment" "this" {. scope = data.azurerm_key_vault.this.id. role_definition_name = "Key Vault Secrets User". principal_id = azurerm_linux_web_app.this.identity..principal_id.