Configuring 802.1X VLAN Assignment and MAB
1. Overview
2. Example for VLAN Assignment
3. Example for MAB
802.1X authentication is a network access control method which safeguards network security . If the client passes the RADIUS server authentication then the client can access the LAN. Otherwise, the client cannot access the LAN.
VLAN Assignment and MAB are two important features of 802.1X authentication, and act as safety controls.
VLAN Assignment
VLAN Assignment allows the RADIUS server to send the VLAN configuration to the port dynamically. VLAN Assignment is used together with 802.1X authentication. After the port is authenticated, the RADIUS server assigns the VLAN based on the username of the client connecting to the port. The username-to-VLAN mappings must already be stored in the RADIUS server database.
The figure below shows the typical topology of VLAN Assignment. VLAN Assignment is port-based. With VLAN Assignment enabled, the RADIUS server will send the VLAN configuration when the port is authenticated. VLAN IDs are assigned based on switch ports.
If the assigned VLAN is nonexistent on the switch, the switch will create the related VLAN automatically, add the authenticated port to the VLAN and change the PVID based on the assigned VLAN.
If the assigned VLAN exists on the switch, the switch will directly add the authenticated port to the related VLAN and change the PVID instead of creating a new VLAN .
If no VLAN is supplied by the RADIUS server or if 802.1X authentication is disabled, the port will be still in its original VLAN.

MAB (MAC Authentication Bypass) uses the MAC address of a device to determine whether the client can get access to the network. After checking the MAC addresses of the clients that you want to access the network, add these MAC addresses into the database of the RADIUS server. With MAB enabled on th port, the switch will learn the MAC address of the device automatically and send the authentication server a RADIUS access request frame with the client’s MAC address as the username and password. If the authorization succeeds, the RADIUS server grants the client access to the network. Thus devices can be authenticated without any client software installed. And MAB can be used to authenticate devices without 802.1X capability like IP phones.
MAB interacts with the other features:
802.1X authentication— MAB takes effect only if 802.1X authentication is enabled on the port.
VLAN Assignment— MAB can be used on a port with VLAN Assignment enabled. That is, if a client has an authorized MAC address identity, the switch assigns the client to a specific VLAN if VLAN Assignment is configured on the corresponding port.
2 Example for VLAN Assignment
2.1 Network Requirements
To enhance network security, a company requires that the employees can access the network normally only when their computers pass the authentication successfully. At the same time, to reduce the workload of the configuration, it is required that the ten authenticated computers can be automatically assigned to the VLANs of their departments. The network topology is shown as below.

2.2 Configuration Scheme
802.1X Authentication is commonly used in solving authentication and security problems for LAN ports. VLAN Assignment can assign multiple clients to different VLANs depending on their authentication information. Thus configure 802.1X Authentication and VLAN Assignment to meet the requirement.
The configuration is briefly summarized in the following outlines:
1) Build a RADIUS Server.
2) Configure 802.1X and VLAN Assignment on the switch.
3) Start the authentication on 802.1X client software.
2.3 RADIUS Server Introduction
A RADIUS server receives user authentication requests, authenticates the user, and then returns authentication results to the authenticator (the switch).
This guide takes FreeRADIUS.net as an example to build a RADIUS server. FreeRADIUS.net installation file can be downloaded from http://freeradius.net/index.html . Run the file and follow the wizard to install the FreeRADIUS.net on a local computer.
After installing FreeRADIUS.net on the computer, some configurations files should be modified to satisfy the 802.1X authentication requirements:
Modify the clients.conf to add RADIUS client (the switch) information.
Modify the users.conf to add user authentication information.
2.4 Configuration
Configuration Guidelines:
VLAN Assignment takes effect only when the control type is Port Based . Set the control type as Port Based on the ports connected to clients .
802.1X authentication and Port Security cannot be enabled at the same time. Before enabling 802.1X authentication, make sure that Port Security is disabled.
Keep 802.1X authentication disabled on ports connected to the authentication server, the internet and the management computer, which ensures the traffic will not be blocked for the switch.
Demonstrated with T2600G-28TS acting as the authenticator, FreeRADIUS.net acting as the RADIUS server and TP-Link 802.1X Client Software, the following sections provide configuration procedures. The configuration procedures on the switch will be given in two ways: using the GUI and using the CLI.
2.4.1 Build a RADIUS Server
For the network administrator, the first thing is to build a RADIUS server, and put the user information for employees into the RADIUS server. The network administrator can set different username and password for each employee or set a public username and password shared by all the employees in the same department. The setting of the username and password depends on the actual demands.

To avoid the format error of the adding code, use Notepad++ to edit configuration files.
One client section means a RADIUS client. You can choose one of the client sections and edit the following attributes. Or you can add a new client section to meet your requirements.
The clients.conf can be modified in three aspects:
The IP address of network segment of the authenticator (T2600G-28TS). After the installation is completed, the default configuration file contains the commonly used network segment. Thus you can keep it as default in most cases.
The secret which is the shared key between the RADIUS server and the switch. The RADIUS server and the switch use the key string to encrypt passwords and exchange responses.
The shortname which is used as an alias for the fully qualified domain name, or the IP address. A value can be filled in optionally for the shortname.
According to the network topology, add the following code and save the file.

The user information can be modified in four aspects:
User-name and User-Password , which is the authentication information of the clients . You can replace rfc3580 with the username which you want and replace demo with the new password. Or you can ignore the default user information and add new user information which has identical format in the next line.
Tunnel-Type , which indicates the tunneling protocol to be used. To configure VLAN Assignment, specify this value as VLAN.
Tunnel-Medium-Type , which indicates the transport medium to use when creating a tunnel for tunneling protocols. To configure VLAN Assignment, specify this value as IEEE-802.
Tunnel-Private-Group-Id , which indicates the group ID for a particular tunneled session, that is the assigned VLAN ID.
According to the network topology, add the following codes and save the file.

4) Click Restart FreeRaDIUS.net Service to restart FreeRaDIUS.net.
2.4.2 Configure VLAN Assignment on the Switch
Using the GUI
1) Choose the menu Network Security > AAA > Global Config to load the following page. In the Global Config section, enable AAA function and click Apply .
2) Choose the menu Network Security > AAA > Dot1x List to load the following page. In the Authentication Dot1x Method List section, select an existing RADIUS server group for authentication from the Pri1 drop-down list and click Apply .

3) Choose the menu Network Security > AAA > RADIUS Config to load the following page. Enter the IP address of the RADIUS server and the shared key which is pre-defined in the Radius Clients.conf.

4) Choose the menu Network Security > 802.1X > Global Config to load the following page. In the Global Config section, enable 802.1X and VLAN Assignment globally and click Apply .

5) Choose the menu Network Security > 802.1X > Port Config to load the following page. Select the port 1/0/3-13 which you want to deploy 802.1X VLAN Assignment and set the status for port1/0/3-13 as Enable . Set the control type as Port Based for port1/0/3-13. Set the status for port 1/0/1 and port 1/0/2 as Disable so that the RADIUS server and the internet will not be blocked for the switch.

Using the CLI
1) Enable AAA globally and configure the RADIUS parameters.
T2600G-28TS#configure
T2600G-28TS(config)#aaa enable
T2600G-28TS(config)#aaa authentication dot1x default radius
T2600G-28TS(config)#radius -server host 192.168.0.253 auth-port 1812 key 123456
2) Globally enable 802.1X authentication and set the authentication protocol. Enable VLAN Assignment.
T2600G-28TS(config)#dot1x system-auth-control
T2600G-28TS(config)#dot1x auth-method eap
T2600G-28TS(config)#dot1x vlan-assignment
3) Disable 802.1X authentication on port 1/0/1and port 1/0/2. Enable 802.1X authentication on port 1/0/3, set the mode as Auto, and set the control type as Port-Based.
T2600G-28TS(config)#interface range gigabitEthernet 1/0/1-2
T2600G-28TS(config-if-range)#no dot1x
T2600G-28TS(config-if-range)#exit
T2600G-28TS(config)#interface range gigabitEthernet 1/0/3-13
T2600G-28TS(config-if-range)#dot1x
T2600G-28TS(config-if-range)#dot1x port-method port-based
T2600G-28TS(config-if-range)#dot1x port-control auto
4) Verify the configurations.
Verify the global configurations of 802.1X authentication:
T2600G-28TS#show dot1x global
802.1X State: Enabled
Authentication Method: EAP
Handshake State: Enabled
Guest VLAN State: Disabled
Guest VLAN ID: N/A
802.1X Accounting State: Disabled
802.1X VLAN Assignment State: Enabled
Quiet-period State: Disabled
Quiet-period Timer: 10 sec.
Max Retry-times For RADIUS Packet: 3
Supplicant Timeout: 3 sec.
Verify the configurations of 802.1X authentication on the port:
T2600G-28TS#show dot1x interface
Port State MAB State GuestVLAN PortControl PortMethod Authorized LAG
---- ------ ------------ ------------ -------------- -------------- ------------- -----
Gi1/0/1 disabled disabled disabled auto mac-based authorized N/A
Gi1/0/2 disabled disabled disabled auto mac-based authorized N/A
Gi1/0/3 enabled disabled disabled auto port-based unauthorized N/A
Gi1/0/4 enabled disabled disabled auto port-based unauthorized N/A
Verify the configurations of RADIUS:
T2600G-28TS#show aaa global
AAA global status: Enable
Module Login List Enable List
Console default default
Telnet default default
Ssh default default
Http default default
T2600G-28TS#show aaa authentication dot1x
Methodlist pri1 pri2 pri3 pri4
default radius -- -- --
T2600G-28TS#show aaa group radius
192.168.0.253
2.4.3 Set Up Authentication on 802.1X Client Software
Before the employee can access the internet, the employee should input the authentication information on the 802.1X Client Software. The authentication information is the username and password which is set by the network administrator in the RADIUS server.

2) Enter the username and password. In this example, enter “tplink” as the username and “admin1” as the password , which is set in the RADIUS server, then click Connect .

Then the 802.1X client software will automatically register to the RADIUS server and get the authority to the internet from the RADIUS server.

When passing the authentication, the following screen will appear.

2.5 Verify the Configuration Result
After all the configurations are completed, you can follow the steps below to verify whether 802.1X VLAN Assignment works. Taking port 3 for a example, you can check the switch by using GUI and CLI.
1) Choose the menu Network Security > 802.1X > Port Config to check whether the port 1/0/3 passes the 802.1X authentication successfully. After passing the 802.1X authentication successfully, the Authorized state will change from Unauthorized to Authorized .

2) Choose the menu VLAN > 802.1Q VLAN > Global Config to check whether the port 1/0/3 is assigned to the corresponding VLAN.

1) Verify the 802.1X authorization states on the port:
---- ----- ---------- --------- ------------- ------------- ------------- -----
Gi1/0/3 enabled disabled disabled auto port-based authorized N/A
2) Verify the VLAN information:
T2600G-28TS#show vlan
VLAN Name Status Ports
----- -------------------- --------- ----------------------------------------
1 System-VLAN active Gi1/0/1, Gi1/0/2, Gi1/0/4, Gi1/0/5,
Gi1/0/6, Gi1/0/7, Gi1/0/8, Gi1/0/9,
Gi1/0/10, Gi1/0/11, Gi1/0/12, Gi1/0/13,
Gi1/0/14, Gi1/0/15, Gi1/0/16, Gi1/0/17,
Gi1/0/18, Gi1/0/19, Gi1/0/20, Gi1/0/21,
Gi1/0/22, Gi1/0/23, Gi1/0/24, Gi1/0/25,
Gi1/0/26, Gi1/0/27, Gi1/0/28
5 N/A active Gi1/0/3
Primary Secondary Type Ports
------- --------- ------------------ ----------------------------------------
The port has been assigned to the related VLAN. That means 802.1X VLAN Assignment works.
3 Example for MAB
3.1 Network Requirements
The network administrator wants to restrict the authority of a device to access the network resources. The device should be authenticated before getting access to the internet. For convenience, it is better that the authentication process can be performed automatically. The network topology is shown as below.

3.2 Configuration Scheme
MAB uses the MAC address of a device to determine whether the device can get access to the network. Thus MAB can be used to authenticate devices without 802.1X Client Software.
The configuration is briefly summarized in two steps:
2) Configure MAB on TP-Link switch.
3.3 Configuration
MAB uses the MAC address of the client as the username and password. Please check the MAC addresses of the clients that you want to access the network in advance.
MAB takes effect only when 802.1X Authentication is enabled. Enable 802.1X Authentication on the ports connected to clients.
MAB takes effect only when Guest VLAN is disabled. Ensure that Guest VLAN is disabled when configuring MAB.
Keep 802.1X authentication disabled on ports connected to the authentication server, the internet and the management computer, which ensures they will not be blocked from accessing the switch.
Demonstrated with T2600G-28TS acting as the authenticator, FreeRADIUS.net acting as the RADIUS server, the following sections provide configuration procedures. The configuration procedures on the switch will be given in two ways: using the GUI and using the CLI.
3.3.1 Build a RADIUS Server
1) Go to http://freeradius.net/index.html to download the FreeRADIUS.net and follow the wizard to install it.

To avoid the format errors when adding code, use Notepad++ to edit configuration files.
One client section means a RADIUS client. You can choose one of the section clients and edit the following attributes. Or you can add a new client section to meet your requirements. The Clients.conf should be modified in three aspects:
The shortname which is used as an alias for the fully qualified domain name, or the IP address of the RADIUS client. A value can be filled in optionally for the short name.

MAB uses the MAC address as the username and password. You can replace rfc3580 and demo with the allowed MAC address. Or you can ignore the default user information and add the MAC address in the next line.
Add the following codes and save the file:

5) Click Restart FreeRaDIUS.net Service to restart FreeRaDIUS.net.
3.3.2 Configure MAB on the Switch
1) Choose the menu Network Security > AAA > Global Config , enable AAA function on the switch and click Apply .
2) Choose the menu Network Security > AAA > Dot1x List, select an existing RADIUS server group for authentication from the Pri1 drop-down list and click Apply .
3) Choose the menu Network Security > AAA > RADIUS Config , and enter 192.168.0.253 which is the IP address of the RADIUS server. Enter the shared key between the RADIUS server and the switch. The RADIUS server and the switch use the key string to encrypt passwords and exchange responses.

4) Choose the menu Network Security > 802.1X > Global Config , enable 802.1X globally and click Apply .

5) Choose the menu Network Security > 802.1X > Port Config to load the following page. Select port 1/0/3 and set the status as Enable and set Control Type as Port Based . Enable MAB for port 1/0/3. Set the status for port 1/0/1 and port 1/0/2 as Disable so that the RADIUS server and the internet will not be blocked for the switch.

1) Enable AAA globally.
2) Globally enable 802.1X authentication and set the authentication protocol.
3) Disable 802.1X authentication on port 1/0/1and port 1/10/2. Enable 802.1X authentication and MAB on port 1/0/3, set the mode as Auto, and set the control type as Port Based.
T2600G-28TS(config)#interface gigabitEthernet 1/0/3
T2600G-28TS(config-if)#dot1x
T2600G-28TS(config-if)#dot1x port-method port-based
T2600G-28TS(config-if)#dot1x port-control auto
T2600G-28TS(config-if)#dot1x mab
T2600G-28TS(config-if)#exit
802.1X VLAN Assignment State: Disabled
---- ----- --------- ----------- -------------- ----------- ------------- -----
Gi1/0/3 enabled enabled disabled auto port-based unauthorized N/A
3.4 Verify the Configuration Result
After all configurations are completed, you can follow the steps below to test whether MAB works.
1) Choose the menu Network Security > 802.1X > Port Config to check whether the port 1/0/3 has passed the authentication successfully.

The port authentication state changes from Unauthorized to Authorized , that is, the port has passed the authentication.
2) Open a web browser and browse a website to check whether the PC can get access to the internet.
---- ------- ------------ ------------ ------------ --------------- ------------ -----
Gi1/0/3 enabled enabled disabled auto port-based authorized N/A
2) Open a web browser and browse a website and to check whether the PC can get access to the internet.

- CCNA 200-301
- CCNA 200-301 Labs
- CCNP 350-401 ENCOR
- CCNP 350-401 ENCOR Labs
- CCNP 300-410 ENARSI
- CCIE Enterprise Infrastructure
- Cisco Packet Tracer Lab Course
- NRS II IRP Course
- NRS II MPLS Course
- NRS II Service Architecture
- Nokia Configuration Course
- Nokia SRC Program
- JNCIA Junos
- HCIA (HCNA)
- HCIA Configuration Course
- What is Huawei R&S Certification?
- Huawei ICT Certifications
- Python Course
- IPv6 Course
- IP Multicast Course
- NRS I Configuration Course
- Cisco Packet Tracer How To Guide
- Online Courses
- Udemy Courses
- CCNA Flashcard Questions
- Protocol Cheat Sheets
- Subnetting Cheat Sheet
- Linux Cheat Sheet
- Python Cheat Sheet
- CLI Commands Cheat Sheets
- Miscellaneous Cheat Sheets
- Cisco Packet Tracer Labs
- Cisco GNS3 Labs
- Huawei eNSP Labs
- Nokia GNS3 Labs
- Short Config Videos
- Network Tools
- IPCisco on Social Media
- Network Engineer Interview Questions
- Personality Interview Training
- Sign In/Up | Members
- Lost password
- Sign In/Sign Up
- ENROLL HERE

- VLAN Port Types and Port Assignment
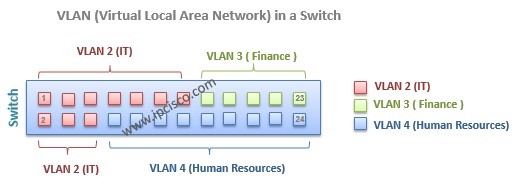
In this lesson, we will focus on some of the key lessons of VLANs. We will learn how to assign ports to VLAN, VLAN Port types and VLAn Tagging.
Table of Contents

Static and Dynamic VLAN Assignments
VLANs can be assigned statically and dynamically . Static configuration is more common, but dynamic is also used.
Static VLAN assignment is like its name. You will statically assign the ports to the VLAN.
Dynamic VLAN assignment can be done by VLAN Membership Policy Server(VMPS) . VMPS needs VLAN-MAC address relationship database. Here, we will use the static one, like many network engineer.
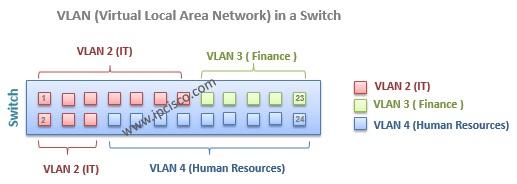
VLAN Port Types
There are two type port used in VLANs. These are: – Access Ports, – Trunk Ports
Access ports are the ports that are member of a single VLAN . Host devices are connected to it. This is also default Cisco switch port type.
Trunk ports are the ports that are member of more than one VLAN or all VLANs . This ports are used between switches. To span VLANs between more than one switch, some ports are needed to carry VLAN information accross the switches. These ports are trunk ports. You can also carry each VLAN without using any trunk port. But this way is not efficient and not common.
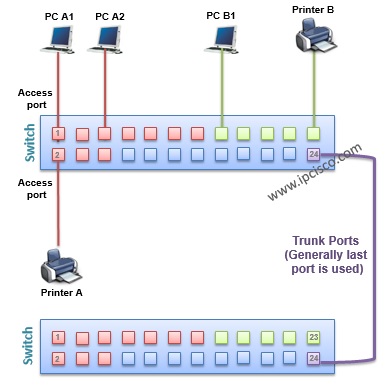
- VLAN Frame Tagging
While carrying the frames between VLANs across multiple swithes, frame tagging is required. Because the other end switch need to understand that where the frame will go ( to which VLAN) on the other end. And tagging is used only for the frames going out a trunk port. This is not used for access ports, and anyway this is not necessary.
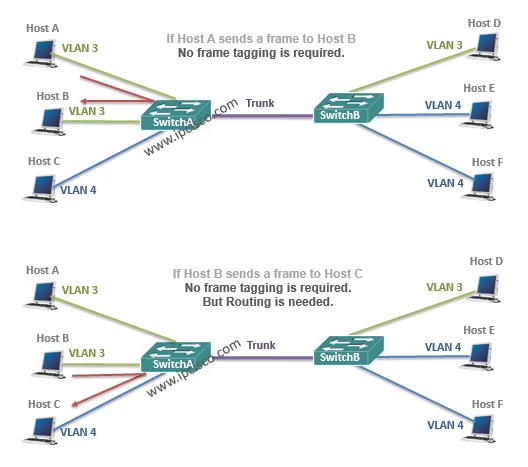
No VLAN Frame Tagging Require
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Network Basics
- Network Topology Types
- Network Cabling
- TCP/IP Model
- OSI Referance Model
Network Devices
- Hubs, Switches and Routers
- Network Device Types
- Local Area Networks
- Home Network IP Address Allocation and Internet Connection
ICMP and ARP
- Gratuitous ARP
IPv4 Addressing
- IPv4 Header versus IPv6 Header
- IPv4 Addressing Basics
- Subnetting in IPv4
IPv6 Addressing
- IPv6 Addressing Basics
- Address Types of IPv6
- New Features of IPv6
- Subnetting in IPv6
TCP and UDP
- UDP (User Datagram Protocol)
- TCP Header : TCP Flags
- TCP Header : TCP Window Size, Checksum and Urgent Pointer
- TCP Header : TCP Options
- TCP versus UDP
- TCP Header : Sequence and Acknowledgement Number
- TCP (Transmission Control Protocol)
- GVRP (GARP VLAN Registration Protocol)
- Virtual LANs (VLANs)
- GVRP Configuration on Huawei
- VLAN Configuration on Huawei Switches
Spanning Tree
- MSTP Configuration on Huawei eNSP
- Spanning Tree Protocol
- STP Mechanism
- Rapid STP (RSTP)
- RSTP Configuration on Huawei
- STP Configuration on Huawei
Link Aggregation
- LACP Overview
- Link Aggregation on Huawei Routers
- RIPv2 Configuration on Huawei eNSP
- Routing Information Protocol
- RIP Next Generation
- RIPng Configuration on Huawei
- OSPv2 Configuration on Huawei eNSP
- OSPF Basics
- OSPF Adjacency Mechanism
- Packet Types in OSPF
- LSA Types in OSPF
- Area Types in OSPF
- Network Types in OSPF
- OSPF Miscellenaous
- OSPFv3 (Open Shortest Path First Version 3)
- OSPFv3 Configuration on Huawei
WAN Protocols
- WAN Technologies
- PPPoE (Point-to-Point Protocol over Ethernet)
- HDLC and PPP
- PPP Configuration on Huawei
- HDLC Configuration on Huawei

GRE and IPSEC VPN
- IPSec VPN Overview
- GRE (Generic Routing Encapsulation)
- IPSec VPN Configuration On Huawei
- Huawei GRE Tunnel Configuration
DHCP and DNS
- DNS Overview
- Dynamic Host Configuration Protocol
- DHCP IP Allocation
- DHCP Configuration On Huawei Routers
Network Address Translation (NAT)
- NAT Configuration on Huawei Routers
- NAT (Network Address Translation)
Access-Lists (ACLs)
- Huawei Access-Lists (ACL)
- AAA (Authentication, Authorization, Accounting)
- AAA Protocols : RADIUS and HWTACACS
- Huawei AAA Configuration
Network Management
- SNMP (Simple Network Management Protocol)
- SNMP Configuration on Huawei
- Basic Huawei Router Configuration
- Huawei Router File System
- Huawei VRP (Versatile Routing Platform)
- Huawei Port Security Configuration on Huawei eNSP
VLAN Routing
- VLAN Routing with Layer 3 Switch on Huawei
- VLAN Routing with Layer 2 Switch and Router on Huawei
- Switch Virtual Interfaces
- Inter VLAN Routing
Static Routing
- Huawei Router Interface Configuration
- Huawei Static Routing and Load Balancing
- Floating Static Route and Default Route Configuration
Other Lessons
- Huawei FTP Configuration
Latest Lessons
- Coaxial Cable Details Part of: CCNA 200-301
- IPv4 vs IPv6 Comparison Part of: CCNA 200-301
- IGMPv3 Overview Part of: IP Multicast Course
- IGMPv3 Overview Part of: CCIE Enterprise Infrastructure
- Subnetting IPv6 Part of: CCIE Enterprise Infrastructure
- IPv6 and Subnetting Part of: CCNP Enterprise 350-401 ENCOR
- IPv6 Link Local Address Type Part of: CCIE Enterprise Infrastructure
- Cisco Switch Configuration on Cisco Packet Tracer Part of: CCNA 200-301
- Switch Configuration on Cisco Packet Tracer Part of: Cisco Packet Tracer Lab Course
- REST API Security Part of: CCNP Enterprise 350-401 ENCOR
- More Lessons
Latest Blog Posts
WHAT YOU WILL FIND?
- 250.000+ Students All Over The World
- 8.000+ Questions & Answers
- 100+ Lab Files & Cheat Sheets
- 30+ IT/Network Courses
- A Real Desire To Help You
- Daily Social Media Shares
- %100 Satisfaction
- CISCO Courses
- NOKIA Courses
- HUAWEI Courses
- JUNIPER Courses
- PYTHON Course
- KEY Courses
- VIDEO Courses
- UDEMY Courses
- Cheat Sheets
- Configuration Files
- Interview Questions
- IPCisco On Social Media
- Pärnu mnt. 139c – 14, 11317, Tallinn, Estonia
- [email protected]
Introduction to protocol-based VLAN
You use the protocol-based VLAN feature to assign packets to VLANs by their application type.
The protocol-based VLAN feature assigns inbound packets to different VLANs based on their protocol type and encapsulation format. The protocols available for VLAN assignment include IP, IPX, and AppleTalk (AT), and the encapsulation formats include Ethernet II and 802.2 SNAP.
A protocol template defines a protocol type and an encapsulation format. A protocol-based VLAN ID and a protocol index, combined, can uniquely identify a protocol template. You can assign multiple protocol templates to a protocol-based VLAN.
Protocol-based VLAN assignment is available only on hybrid ports, and a protocol template applies only to untagged packets.
When an untagged packet arrives, a protocol-based VLAN assignment enabled hybrid port processes the packet by using the following workflow:
If the protocol type and encapsulation format in the packet matches a protocol template, the packet is tagged with the VLAN tag specific to the protocol template.
If no protocol template is matched, the packet is tagged with the PVID of the port.
The port processes a tagged packet as it processes tagged packets of a port-based VLAN.
If the port is in the same VLAN as the packet, it forwards the packet.
If not, the port drops the packet.
© Copyright 2016 Hewlett Packard Enterprise Development LP

Search Results
Creating VLAN Assignment Rules for Dynamic VLAN Assignment in Bridge Mode
To create a VLAN Virtual Local Area Network. In computer networking, a single Layer 2 network may be partitioned to create multiple distinct broadcast domains, which are mutually isolated so that packets can only pass between them through one or more routers; such a domain is referred to as a Virtual Local Area Network, Virtual LAN, or VLAN. assignment rule for dynamic VLAN assignment in bridge mode, complete the following steps:
- To access the WLAN Wireless Local Area Network. WLAN is a 802.11 standards-based LAN that the users access through a wireless connection. SSID Service Set Identifier. SSID is a name given to a WLAN and is used by the client to access a WLAN network. configuration wizard for a new SSID profile or an existing SSID profile, see Configuring a WLAN SSID Profile in Bridge Mode or Configuring a WLAN SSID Profile in Tunnel and Mixed Mode .
- In the WLAN SSID configuration wizard, click the VLANs tab.
In a Bridge mode SSID, all the user traffic is bridged locally. All the wireless traffic is terminated locally at the AP and bridged onto the local Ethernet Ethernet is a network protocol for data transmission over LAN. segment.
- Select Dynamic in Client VLAN Assignment to specify a VLAN ID.
- To create a VLAN assignment rule, click + Add Rule under VLAN Assignment Rules . The New VLAN Assignment Rule window is displayed.
Attribute —Select an attribute from the drop-down list.
Operator —Select either equals or not-equals from the drop-down list, depending on your criteria.
String —Enter a string in the text box.
VLAN —Select a VLAN ID from the drop-down list.
- Click OK to save the changes.
You can create up to eight VLAN assignment rules per SSID.


IMAGES
VIDEO
COMMENTS
PVID. By default, VLAN 1 is the port VLAN ID (PVID) for all ports. You can configure the PVID for a port as required. When you configure the PVID on a port, follow these restrictions and guidelines: An access port can join only one VLAN. The VLAN to which the access port belongs is the PVID of the port. A trunk or hybrid port can join multiple ...
Because a trunk or hybrid port can join multiple VLANs, you can configure a default VLAN for the port. You can use a nonexistent VLAN as the default VLAN for a hybrid or trunk port but not for an access port. After you remove the VLAN that an access port resides in with the undo vlan command, the default VLAN of the port changes to VLAN 1. The ...
The assignment of VLANs are (from lowest to highest precedence): 1. The default VLAN is the VLAN configured for the WLAN (see Virtual AP Profiles ). 2. Before client authentication, the VLAN can be derived from rules based on client attributes (SSID, BSSID, client MAC, location, and encryption type).
Although static VLANs are the most common form of port VLAN assignments, it is possible to have the switch dynamically choose a VLAN based on the MAC address of the device connected to a port. To achieve this, you must have a VTP database file, a VTP server, a VTP client switch, and a dynamic port.
Step 6. Use the switchport access vlan command to assign the port or range of ports into access ports. A port in access mode can have only one VLAN configured on the interface which can carry traffic for only one VLAN. SG350X (config-if-range)#switchport access vlan [vlan-id | none] The options are:
Cisco Business routers come with VLAN 1 assigned to all ports by default. A management VLAN is the VLAN that is used to remotely manage, control, and monitor the devices in you network using Telnet, SSH, SNMP, syslog, or Cisco's FindIT. By default, this is also VLAN 1. A good security practice is to separate management and user data traffic.
Port-based VLAN port assignment screen in the menu interface. NOTE: The "VLAN Port Assignment" screen displays up to 32 static, port-based VLANs in ascending order, by VID. If the switch configuration includes more than 32 such VLANs, use the following CLI command to list data on VLANs having VIDs numbered sequentially higher than the first 32. ...
A VLAN Membership Policy Server (VMPS) provides a centralized server for selecting the VLAN for a port dynamically based on the MAC address of the device connected to the port. When the host moves from a port on one switch in the network to a port on another switch in the network, that switch dynamically assigns the new port to the proper VLAN ...
Static VLANs are also referred to as port-based VLANs. Static VLAN assignments are created by assigning ports to a VLAN. As a device enters the network, the device automatically assumes the VLAN of the port. If the user changes ports and needs access to the same VLAN, the network administrator must manually make a port-to-VLAN assignment for ...
Each tag-based VLAN you built up must be assigned VLAN name and VLAN ID. Valid VLAN ID is 1-4094. User can create total up to 256 Tag VLAN groups. Port-based: Port-based VLAN is defined by port. Any packet coming in or outgoing from any one port of a port-based VLAN will be accepted. No filtering criterion applies in port-based VLAN.
In the Global Config section, enable 802.1X and VLAN Assignment globally and click Apply. 5) Choose the menu Network Security > 802.1X > Port Config to load the following page. Select the port 1/0/3-13 which you want to deploy 802.1X VLAN Assignment and set the status for port1/0/3-13 as Enable.
When a port is assigned to the corresponding VLAN in a MAC address-to-VLAN entry, but has not been assigned to the VLAN by using the port hybrid vlan command, the port sends packets from the VLAN with VLAN tags removed. If you configure both static and dynamic MAC-based VLAN assignment on the same port, dynamic MAC-based VLAN assignment applies.
VLAN Port Types. There are two type port used in VLANs. These are: - Access Ports, - Trunk Ports. Access ports are the ports that are member of a single VLAN. Host devices are connected to it. This is also default Cisco switch port type. Trunk ports are the ports that are member of more than one VLAN or all VLANs.
Port-Based Authentication Initiation and Message Exchange During 802.1x authentication, the switch or the client can initiate authentication. If you enable authentication on a port by using the ... A host is authorized on the port with no VLAN assignment, and subsequent hosts either have no VLAN assignment, or their VLAN information matches the ...
-based VLANs—In the case of untrusted interfaces, you can associate a client to a VLAN based on the source MAC of the packet. Based on the MAC, you can assign a role to the user after authentication. Adding VLAN Details. By default, all ports in the Switches are assigned to VLAN 1. However, if the ports are assigned to different VLANs, the ...
MAC-Based VLANs (MBVs) allow multiple clients on a single switch port to receive different untagged VLAN assignments. VLAN assignment of untagged traffic is based on the source MAC address rather than the port. Clients receive their untagged VLAN assignment from the RADIUS server. This feature adheres to the requirement that if all known RADIUS ...
Step 4. When the port is in Trunk mode, it will be a member of this VLAN. Select the Native VLAN ID in the Native VLAN ID drop-down list. Note: In this example, we will be using VLAN 1 as the native VLAN ID. Step 5. Select User Defined radio button in the Tagged VLANs field. Then enter the VLAN ID's that you want this port to be a member of.
To add a new VLAN assignment rule, complete the following steps: Click + Add Rule in the VLAN Assignment Rules window. The New VLAN Assignment Rule page is displayed. Enter the Attribute, Operator, String, and VLAN details, and then click OK. To delete a VLAN assignment rule, select a rule in the VLAN Assignment Rules window, and then click the ...
The IEEE 802.1X VLAN Assignment feature is automatically enabled when IEEE 802.1X authentication is configured for an access port, which allows the RADIUS server to send a VLAN assignment to the device port. This assignment configures the device port so that network access can be limited for certain users.
The protocol-based VLAN feature assigns inbound packets to different VLANs based on their protocol type and encapsulation format. The protocols available for VLAN assignment include IP, IPX, and AppleTalk (AT), and the encapsulation formats include Ethernet II and 802.2 SNAP. A protocol template defines a protocol type and an encapsulation format.
Creating VLAN Assignment Rules for Dynamic VLAN Assignment in Bridge Mode. To create a VLAN Virtual Local Area Network. In computer networking, a single Layer 2 network may be partitioned to create multiple distinct broadcast domains, which are mutually isolated so that packets can only pass between them through one or more routers; such a domain is referred to as a Virtual Local Area Network ...