A Systematic Literature Review on Cloud Computing Security: Threats and Mitigation Strategies
Ieee account.
- Change Username/Password
- Update Address

Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- BMC Med Inform Decis Mak

A scoping review of cloud computing in healthcare
Lena griebel.
Department of Medical Informatics, Friedrich-Alexander-University Erlangen-Nürnberg, Wetterkreuz 13, Erlangen, D-91058 Germany
Hans-Ulrich Prokosch
Felix köpcke, dennis toddenroth, jan christoph, martin sedlmayr.
Cloud computing is a recent and fast growing area of development in healthcare. Ubiquitous, on-demand access to virtually endless resources in combination with a pay-per-use model allow for new ways of developing, delivering and using services. Cloud computing is often used in an “OMICS-context”, e.g. for computing in genomics, proteomics and molecular medicine, while other field of application still seem to be underrepresented. Thus, the objective of this scoping review was to identify the current state and hot topics in research on cloud computing in healthcare beyond this traditional domain.
MEDLINE was searched in July 2013 and in December 2014 for publications containing the terms “cloud computing” and “cloud-based”. Each journal and conference article was categorized and summarized independently by two researchers who consolidated their findings.
102 publications have been analyzed and 6 main topics have been found: telemedicine/teleconsultation, medical imaging, public health and patient self-management, hospital management and information systems, therapy, and secondary use of data. Commonly used features are broad network access for sharing and accessing data and rapid elasticity to dynamically adapt to computing demands. Eight articles favor the pay-for-use characteristics of cloud-based services avoiding upfront investments. Nevertheless, while 22 articles present very general potentials of cloud computing in the medical domain and 66 articles describe conceptual or prototypic projects, only 14 articles report from successful implementations. Further, in many articles cloud computing is seen as an analogy to internet-/web-based data sharing and the characteristics of the particular cloud computing approach are unfortunately not really illustrated.
Conclusions
Even though cloud computing in healthcare is of growing interest only few successful implementations yet exist and many papers just use the term “cloud” synonymously for “using virtual machines” or “web-based” with no described benefit of the cloud paradigm. The biggest threat to the adoption in the healthcare domain is caused by involving external cloud partners: many issues of data safety and security are still to be solved. Until then, cloud computing is favored more for singular, individual features such as elasticity, pay-per-use and broad network access, rather than as cloud paradigm on its own.
Electronic supplementary material
The online version of this article (doi:10.1186/s12911-015-0145-7) contains supplementary material, which is available to authorized users.
Medicine is an increasingly data-intensive and collaborative endeavor [ 1 ]. Advances in the OMICS-fields (genomics, proteomics and the like) generate considerable amounts of data to be processed and stored. Secondary use of clinical data with text-or data mining algorithms also entails a growing demand for dynamic, scalable resources. Often these resources are only utilized temporarily so that permanent infrastructure investments are hard to justify and flexible on-demand services are sought alternatively.
Cloud computing seems a viable solution to fulfill these demands. Commercial providers like Amazon and Microsoft promise to make hundreds of virtual machines available at ones’ fingertips, almost immediately and just for the time they are really needed. The advantage of such offers is, that such resources only have to be paid for the configuration, size and time they are actually used.
Thus, the term “cloud computing” is described by the National Institutes of Standards and Technology (NIST) [ 2 ] as a model for enabling ubiquitous, convenient, on-demand access to a shared pool of configurable computing resources. As essential characteristics of cloud computing Mell and Grance have listed (1) on demand self-service, (2) broad network access, (3) resource pooling with other tenants, (4) rapid elasticity, and (5) measured services. Clouds promise advantages in dynamic resources like computing power or storage capacities, ubiquitous access to resources at anytime from any place, and high flexibility and scalability of resources. These benefits have been the reason for increasing adoption of cloud computing in many business areas. In recent years this concept has seemingly also been introduced in the healthcare domain. At least, a continuously increasing number of articles and publications appears in the popular literature and is provided by healthcare IT companies, but also in the scientific literature cloud computing for healthcare applications is gaining attention.
When reviewing the large amount of most recent literature dealing with cloud approaches in healthcare it becomes obvious, that many reports are dealing with cloud-computing technologies as a replacement for grid computing in the OMICS-field, while other fields of application (e.g. health information systems, health information exchange or image processing and management) still seem to be underrepresented. In the popular literature the application of cloud computing for healthcare information system provision for example is often used as a buzz word, but real evidence on research in healthcare cloud computing (beside the big topic of OMICS) or even its successful and resource saving application is missing. Researchers have proposed cloud computing as a new business paradigm for biomedical information sharing [ 3 ]. Kuo asked “if cloud computing can benefit health services” [ 4 ] and described opportunities and challenges of healthcare cloud computing [ 5 ]. Ahuja and colleagues have recently tried to survey the current state of cloud computing in the healthcare domain [ 6 ]. However, their overview has by far neither been representative nor comprehensive (many of their limited number of 27 references were company website information or publications with a commercial background).
Thus, since currently no real overview on the application of cloud computing in healthcare exists, it is the objective of our scoping literature review, to uncover the current myth on healthcare cloud computing. It is our aim to provide a comprehensive overview on the existing literature and elicit the key messages of the current publications. Further, we want to identify “hot spots” within the healthcare domain (but outside of the OMICS area) where cloud computing concepts and applications have mostly been discussed. For the articles published as “cloud computing application for health care” we wanted to check if the typical cloud computing service models (software, platform or infrastructure as a service) as well as their respective deployment models (private, community, public or hybrid cloud) are differentiated. Finally, we wanted to verify, how far the buzz word “cloud computing” has really already achieved more than only the “conceptual design” and “challenges” state and entered into the status of routine daily application, hopefully even with measures on its proven value for the healthcare domain.
Thus, our review questions were:
- Does the existing literature provide enough evidence for the successful application of cloud computing in healthcare?
- What are the major application areas?
- Are particular types of cloud concepts (public clouds, private clouds or hybrid clouds) more dominant than others?
- Are particular cloud computing services (e.g. infrastructure as a service, software as a service, and platform as a service) more dominant than others?
- Is there evidence, that the benefits, advantages and cost savings, which are typically assigned to cloud computing, could already be realized in healthcare environments?
- What are the barriers, which still need to be overcome in order to make cloud computing a successful technology also in the healthcare domain?
Carrying out the review comprised the four stages of (1) collecting publications through a MEDLINE database search, (2) a first relevance screening to filter the results, (3) a review of the relevant papers and (4) a summarization of the content.
Within this review we consider the concept of healthcare to include all activities related to diagnosis, therapy and prevention of human diseases, or injuries, as well as clinical research and healthcare management. Publications on cloud computing for research in basic medical science (e.g. molecular medicine and genomics) however have not been considered.
Search strategy
We searched the MEDLINE database in July 2013 and conducted an updated MEDLINE literature research in December 2014 for the terms “cloud computing” and “cloud-based”. Further, articles were subsequently included based on references in the publications of this first search.
All references were imported into the literature management program EndNote. All results were screened for relevance against our inclusion criteria.
Selection of studies
The review team consisted of six researchers with expertise in medicine, computer science, medical informatics and statistics, working in groups of two. Each group was assigned one third of the papers in each round. Thus, each paper was reviewed independently by two reviewers. Conflicts between reviewers were resolved by short discussion rounds reaching a consensus.
At first, a relevance screening round based on the bibliographic data of a publication (type of publication, title, abstract, keywords) was conducted to remove obviously irrelevant papers. Details on this relevance screening are given in Additional file 1 .
Excluded were papers on clouds in a non-computing sense (e.g. scatter plot analyses, clouds in a meteorological context) as well as cloud-computing in non-healthcare related topics (e.g. clouds used for biological analyses or for veterinary medicine). For the remaining papers, full-texts were obtained. If full-text was not available the article was excluded.
In the next step, based on the available full texts, papers published in languages other than English, editorials, letters to the editor, commentaries and press articles were excluded as non-scientific and out of the scope of this review. Articles dealing with cloud computing in genomics without a concrete relevance for patient care were excluded as they were not in the scope of our review. Additional file 2 provides the eligibility screening form used in this full-text screening step.
For the remaining papers, the content has been extracted as described in the following section.
Full text screening and data extraction
The review protocol contained detailed instructions, inclusion/exclusion criteria, and a data extraction form (see Additional file 3 ). The data extraction form was handed to all reviewers in MS Office Excel 2010 format. This form included 14 closed and 8 open questions.
The closed questions captured e.g. the state of the described cloud computing system (i.e. theoretical, conceptual, prototype, successful), users addressed by the described system (e.g. physicians, patients, researchers), and the provider of the cloud (e.g. proprietary, i.e. self-constructed cloud computing solutions or commercially hosted solutions). Based upon NIST’s definition of cloud computing, its five essential characteristics (self-service, broad network access, resource pooling, rapid elasticity and measured service) [ 2 ] were checked for being mentioned by the authors. Besides advantages, also challenges were extracted, for example security concerns or dependencies on cloud providers.
Using open questions, the reviewers identified the main objective and the most important result of the article or of the described project, and in each case also summarized the specific usage of cloud computing. If mentioned, security concerns and countermeasures as well as cost considerations were noted. Finally, the definition of cloud computing, if it was used in a paper was collected.
Conducting this analysis of the articles enabled us to get an overview on the current state of research on cloud computing in healthcare and to collect the key messages of eligible publications.
Record selection and article type
Up to July 2013, 258 articles were found through literature research using the MEDLINE database. After the exclusion of one duplicate article and 63 articles, where title and abstract obviously illustrated that the contents of the article was from a completely different field, 194 remained for a cursory full text screening. Ten full texts were not available. 126 additional articles were removed during this step. 13 additional publications were identified from references of the screened literature, retrieved and included in the final analysis step. The first literature research thus resulted in 71 articles for the qualitative analysis. This literature research was updated in December 2014. During that research 200 further articles have been found in MEDLINE; 58 articles were removed due to their title and abstract. Of 21 articles the full text was not available; 90 further articles did not fit to the eligibility criteria. 31 new articles remained that were included in the qualitative analysis. Thus, in total 102 articles contributed to the subsequent qualitative synthesis. Of these 78 were journal papers, 24 were papers from conferences. The record selection process is shown in Figure 1 . Additional file 4 gives an overview of all 102 articles that were used for the qualitative synthesis and includes detailed results of the characterization of all eligible reviewed articles.

Scoping literature review flowchart.
Of the 102 articles only one has been published in the year 2008 and none in 2009. Seven articles have been published in 2010. From 2010 to 2011 the number of published articles concerning cloud computing in healthcare doubles up to 14 articles, and doubles again from 2011 to 2012 from 14 up to 29 articles. In 2013 27 articles have been published. Until December 2014 24 articles were identified–thus the trend seems not to be stable (Figure 2 ).

Yearly distribution of published articles.
Categorization of cloud computing research in healthcare: main domains
The final list of papers was screened again to identify any new topic complementing the MEDLINE result list. Each two reviewers independently tagged the articles in the qualitative synthesis with main domains included in the papers. The final set of topics was discussed by all reviewers and similar topics were grouped to one main topic. Finally the following six domains for the application of cloud computing to healthcare, sorted in descending order by the number of included articles, were identified (Figure 3 ):
- Telemedicine/Teleconsultation
- Medical Imaging
Public health and patients’ self-management
- Hospital management/clinical information systems
Secondary use of data

Cloud computing in healthcare–main domains.
Besides these categories we identified several articles that did not fit into one of the hot spots–these articles are explained in the “other domains” section.
In the following we describe the papers according to the identified categories, for more detailed information concerning MEDLINE articles’ content, please refer to the Additional file 4 .
Telemedicine/teleconsultation
Supporting communication and sharing data among stakeholders in healthcare is the most prominent domain including 34 articles. However, most publications describe just a typical telemedicine application when they report on the possibility to ubiquitously collect, access and share or analyze patient data from different hospitals or healthcare providers in dedicated health services networks.
Oshidori-Net2 for example is reported to be an “EPR and PACS sharing system” for six Japanese hospitals on an infrastructure which the authors call “server-based computing” and denote this to be cloud computing technology. The article further mentions that the server for this environment was built on virtual servers and virtual routers, but no further details on the cloud deployment or service model are given [ 7 ]. Similarly, Shih et al. [ 8 , 9 ] present a study in which 65 organ transplant healthcare professionals from China and Taiwan as well as 15 eHealth technology experts were questioned to identify pros and cons of so called “e-health documents” to be shared between institutions on a Web-platform. However, the article gives no information on why their proposal should be some type of cloud computing and not just a typical telemedicine platform for secure sharing of patient records for the respective organ transplant patients [ 8 , 9 ]. Rajkumar and Iyengar describe the concept of a Peer-to-Peer network to transfer medical resources like patient records and medical histories between diverse actors such as hospitals and ambulances in a medical emergency scenario [ 10 ]. In this scenario each hospital owns a community cloud to upload and share patient data with the nurse in the ambulance. A cloud application and an architecture test bed has been created, nevertheless the authors only present their concept and promise a reliable system to reduce the death rate in emergency care resulting from time delays during the patient transportation due to the missing opportunity to share important patient information with the hospital.
Also, Koufi et al. have named their concept “cloud emergency medical services” and provided a figure in which they depict their system components as infrastructure as a service, platform as a service and software as a service [ 11 ]. They further mention, that the system’s prototype implementation has been performed on a laboratory cloud computing infrastructure and that data are stored on multiple data centers in the cloud. Unfortunately, no further details on the specific type of cloud (private, community or public), the pay-for-use model or aspects of resource pooling with other tenants and rapid elasticity are given.
In another example Fujita et al. [ 12 ] called their implementation “Cloud Cardiology®”, mentioning, that “a cloud server enables to share ECG simultaneously inside and outside the hospital”. Nowhere in the further article itself, however, are any details presented why this server should really be a “cloud server” and not just a secured web-server for a telemedicine application, which provides a health information exchange platform in the internet.
Rao et al. propose a solution were also underserved, regions lacking infrastructure may benefit from cloud computing, without however illustrating in detail in which terms their approach should be a cloud application and not just a typical telemedicine service for rural areas [ 13 ]. Al-Zaiti et al. analyze the current problems and options for ECG transmission prior to hospitalization [ 14 ]. They see an option to standardize protocols used by different vendors and lower the investment cost for adopting the technology thanks to cloud services. One possible solution is presented by Fong and Chung [ 15 ] who describe a mobile cloud-based healthcare service by noncontact ECG monitoring. However, the software is described as client–server architecture implemented using standard web technologies and no cloud technologies are mentioned by the authors. Also Wang et al. [ 16 ] propose in their conceptual work a hybrid cloud computing environment to store data from personal health sensors worn at the body such as ECG sensors and to perform processing tasks. The purpose of the cloud is to accelerate computation intensive processing tasks by shifting them to the cloud server and therefore extend the battery life of mobile devices.
In contrast to the above examples, Hsieh and Hsu have presented a very comprehensive and detailed description of a 12-lead ECG telemedicine service based on cloud computing [ 17 ]. They have clearly described how the processing, visualization, management and e-learning services are deployed within the commercial Microsoft Azure cloud platform. They further present the reasons for adopting the Azure platform and the financial background of the implementation, based on the Azure pricing model with monthly costs directly related to CPU hours and GB storage used. As a second positive example we have identified the article of Hiden et al. who have described their development e-Science Central (a platform as a service which itself was built on an infrastructure as a service environment) [ 18 ]. Their article comprehensively illustrates not only the set of cloud services provided, which cover data storage services, but also service execution, workflow enactment and security. Finally as one of three case studies they present a medical pilot investigation (the MOVEeCloud project) where medical specialists assess the physical activity of patients based on data uploaded to the e-Science Central cloud by wearable accelerometers.
The improvement of the monitoring of discharged patients’ health-related quality of life and vital signs is the objective of caREMOTE, a prototype development of a cancer reporting and monitoring telemedicine system which is accessible by mobile devices [ 19 ]. For this prototype the cloud infrastructure was built on the Google App Engine (GAE) and data was stored in Google’s Big table technology. According to the authors, building such applications with GAEs sandbox technology leads to an isolation of the caREmote database within the cloud and secures the sensitive patient data from being violated. For a final routine application, this security aspect alone however, would by far not be sufficient. Therefore the authors intend to implement the Advanced Encryption Standard (AES) in a future version.
Similarily, Hussain et al. [ 20 ] implemented a system to use sensory data e.g. from smartphone sensors to detect activity patterns and ultimately lifestyle patterns. While the analysis was done on a local cluster of 4 host machines, the system is based on Hadoop as a typical big data technology which is easily scalable in clouds. Almashaqbeh el al. describe a cloud-based real-time remote health monitoring system (CHMS) which aims to integrate multi-hop sensor networks and cloud computing. However, the focus of the presentation is on routing the messages effectively (quality of service) through networked routers and computers and it therefore does not refer to any cloud or NIST characteristics [ 21 ].
The paper by Zao et al. puts a focus on telemonitoring in the neuroscience field [ 22 ]. The researchers present a prototypic online EEG-BCI (Brain Computer Interface) system based on wireless EEG headsets and mobile phones to predict users’ (patients, healthy persons) cognitive states in dynamic real-life situations. Cloud servers deliver the power to conduct semantic searches to find data segments matching with certain personal, environmental, and event specification used as a basis for the cognitive state prediction model.
Medical imaging
One of the second largest domains of use with 15 articles is medical imaging focusing on the storage, sharing and computation of images.
Kakadis [ 23 ] provides a more theoretical description of various aspects of cloud computing with a special focus on medical imaging. Computing intensive image processing, sharing/workflows and archiving are the three major application areas, security the major challenge. As a visionary paper it remains on a conceptual level and does not explicitly refer to implementations. Similarly, Gerard also motivates the utilization of cloud technologies in radiology in his extended outlook, if adequate service level agreements are in place to guarantee uptime and performance and security is granted [ 24 ].
A cloud-based Picture Archiving and Communication System (PACS) might enable the storage of medical images as “PACS-as-a-Service” [ 25 ] or even provide a highly flexible “radiology round-the-clock” [ 26 ]. Rostrom et al. [ 1 ] have built a proof-of-concept prototype to demonstrate that the secure exchange of images between a client and a DICOM server hosted in the Microsoft Azure cloud is possible. The development of a DICOM (Digital Imaging and Communications in Medicine) compliant bridge for easily sharing DICOM services across healthcare institutions supports the provision of medical imaging services across the different institutions [ 25 , 27 ]. Also an efficient transport of large image files between PACS and image analysis servers is under development [ 28 ]. Doukas [ 29 ] implemented an Android client to receive patient information and images from a central server that runs in an Amazon virtual machine and measured download times of images via 3G and WLAN. Besides the server being in the Internet, neither details on the particular cloud-features nor on data protection/safety are issues mentioned.
Especially computationally intensive tasks are predestined to be put in a cloud computing environment. Cloud computing with its ability to lease computing capacities can be a suitable solution due to its pay-for-use approach, its ubiquitous access to data and its elasticity [ 30 ]. Maratt [ 31 ] compared the accuracy and efficiency of templating as part of the preoperative planning for total hip arthroplasty between traditional printing and a digital SaaS. While the outcome confirms that digital templating is quite as good as traditional methods, the article does not focus on the cloud per se, but more on the medical outcome as prerequisite for the acceptance of digital service. Yoshida et al. [ 32 ] describe the implementation of a framework for distributed image processing and positively evaluated the performance gained by using more processing units. However, the evaluation used multi-core CPUs in a single machine and the transfer to cloud-environments is mentioned only as an additional conceptual possibility. Similarly, Qu et al. [ 33 ] evaluated five image texture analysis methods using a “CometCloud” called hybrid cloud-grid distribution framework. Despite the cloud features, the evaluation reported was performed on a local, grid-like cluster. In contrast, Meng et al. [ 34 ] implemented a cone-beam CT reconstruction algorithm using MapReduce and evaluated it on 10 to 200 Amazon cloud nodes experiencing a 1/n decrease of computing time.
Supporting research, Avila-Garcia [ 35 ] describes the objectives of a Microsoft-funded project to implement a virtual research environment to lower the barriers to cancer imaging. While the paper cites some grid frameworks and enlists some general features required by researchers, no explicit links to cloud technologies are given when describing the functions to be implemented.
Public Health is concerned with prevention, health promotion or improvement for individual citizens and patients but also for large population groups (epidemiology). Identically to the domain of medical imaging 15 articles belong to this domain.
Several papers include the idea that cloud computing might be used to support citizens and patients in managing their health status. Botts et al. [ 36 ] describe a pilot study named HealthATM which is a cloud-based personal health infrastructure to provide individuals from underserved population groups (i.e. people without health insurance) with instant access to their health information. The authors see cloud computing as a way to provide broad access to health data to population groups but do not explain how this highly scalable cloud architecture was implemented in detail, because the main focus of the paper was on the acceptance and usability of a personal electronic health records system in underserved populations.
The work of Piette et al. focusses on underserved patient groups as well. In two papers they describe how they created systems to inform underserved patient groups suffering from diabetes [ 37 ] resp. hypertension [ 38 ] with automated telephone calls to enable an improved self-management of the diseases. Although the authors mention that they use cloud computing to provide the application they do not differentiate between clouds and the Internet in general.
In their conference poster, Takeuchi et al. present a prototypic cloud-based system to store personal health and lifestyle data using mobile devices. In a cloud infrastructure they claim to have implemented data-mining technologies to extract individually important information such as lifestyle patterns. Although other persons like dietitians should have the possibility to add comments into the system it is not explained how data access in the cloud will be managed [ 39 ].
Similarly, the work of He et al. as well focusses on enabling citizens to manage their own health. They see cloud computing as a “component as a service” to develop a private healthcare cloud which should provide early warning of diseases [ 40 ]. Siddiqui et al. describe the concept of a Telecare Medical Information System (TMIS) which includes different medical services for patients and medical professionals such as a remote monitoring of physiological signals. The user should connect to the TMIS by using his/her smartphone and thus the smartphone needs to be equipped with authentication possibilities to ensure data privacy and data security. The authors propose a three-factor authentication (3FA) based on a dynamic cloud computing environment to enable the remote user authentication [ 41 ]. Van Gorp and Comuzzi discuss the prototype of MyPHRMachines where a cloud is used to deploy health-related data and the application software to view and analyze it in a personal health record system. After uploading their medical data to MyPHRMachines, patients can access them again from remote virtual machines that contain the right software to visualize and analyze them without any need for conversion. The patients should be able to can share their remote virtual machine session with selected caregivers [ 42 ].
Other projects are focused on specific user groups, such as the paper from Xu et al. [ 43 ] who worked on creating an automated cloud-based stress disorder monitor screening enabling patients suffering from Post-Traumatic Stress Disorder (PTSD) to monitor their progress during the treatment. According to the authors the so-called TPM (Tele-PTSD Monitor) system should be accessible via Public Switched Telephone Networks or via the Internet; latter might be realized using Amazon Elastic Compute Cloud. More information on the detailed cloud approach is not given to the reader.
Likewise, Su and Chiang describe IAServ (Intelligent Aging-in-place Home care Web Services) which is an electronic platform to provide healthcare services for elderly people at home. The objective of the platform is to prevent institutionalization of the users. Although the authors present an interesting architecture approach including an agent environment and a knowledge proceeding layer and explicitly mention the use of cloud computing services several times it remains unclear where a cloud computing system is used in the architecture of IAServ [ 44 ].
The work of Tseng and Wu as well focusses on enabling a healthy lifestyle of elderly people. They describe the prototype of iFit, which is a platform for the promotion of physical fitness to elder people through game-like activities. A so-called expert cloud is used to provide expert fitness diagnoses through a web service by receiving physiological data from the user and returning the corresponding fitness level and giving fitness suggestions to the user [ 45 ].
On a population level, Jalali et al. identified cloud computing as a solution to work with data of large populations by conceptualizing the use of virtual private clouds for public health reporting [ 46 ]. Price et al. worked on reducing execution time for epidemic analyses by using cloud structures [ 47 ]. Eriksson et al. describe a cloud-based architecture for simulating pandemic influenza outbreaks [ 48 ]. Ahnn et al. furthermore provide a theoretical paper on a way to create a cloud-based mobile health platform with a focus on energy efficiency [ 49 ].
Hospital management and clinical information systems
Another interesting field of cloud computing in healthcare described by 13 articles is the deployment of clinical information systems into clouds. Commercial HIS vendors (compare e.g. the CSC Health Cloud [ 3 ]) have started to propagate new managed HIS services for their customers and also offer infrastructure as a service on a monthly payment basis. According to Low and Chen the selection of such an outsourcing provider needs to be evaluated very well. They proposed a provider selection evaluation model based on the Fuzzy Delphi Method (FDM) and the Fuzzy Analytic Hierarchy Process (FAHP) and identified decision criteria such as system usefulness, ease of use and reliability, high service quality or professionalism of the outsourcing provider [ 50 ]. Yoo et al. have chosen a more conservative approach by establishing a private cloud within Seoul National University Bundang Hospital (Korea) based on virtualization technology, a virtual desktop infrastructure and 400 virtual machines, which supported easy and overall access to each of the hospital’s information systems from all devices throughout the hospital. For this implementation they performed a five year cost-benefit analysis and showed that their approach reached its break-even point in the fourth year of the investment [ 51 ].
Two publications [ 52 , 53 ] describe the environment of two Romanian hospital departments with two different clinical subsystems which are capable to exchange data between each other based on HL7 CDA. Even though the authors introduced their article with a general description of the different cloud deployment and service models, the remainder of the articles provides no evidence of cloud-use or requirement.
As the Malaysian government initiated a paradigm shift to use electronic hospital information and management systems (HIMS) cloud computing could be the method of choice to reduce the escalating costs of data storing and sharing according to Ratnam and Ramayah. Although the authors do not describe this cloud system in detail, they mention that a cloud platform using Microsoft Windows Azure was used as prototype architecture [ 54 ].
In China, Yao et al. [ 55 ] created a community cloud-based medical service delivery framework (CMSDF) to enable the exchange of resources between a large general hospital with its associated smaller healthcare institutions–so called Grassroot healthcare institutions being the smallest administrative level of medical institutions in China including for example community health service centers or rural clinics. In the prototype CMSDF a cloud-based Virtual Desktop Infrastructure is owned and managed by a large hospital which is able to share its medical software as SaaS with the Grassroot healthcare institutions. According to the author for the 34 cooperative sanatoriums that participated, 89.9% of investment and maintenance cost were saved because the smaller facilities had not to buy and host expensive software on their own.
Rodrigues et al. specifically address the risks of hosting electronic health records on cloud servers [ 56 ]. The authors conducted a review of papers about security and privacy issues which different cloud computing providers currently use for the development of their platforms. They emphasize that shifting health resources to cloud systems needs the consideration of several requirements regarding privacy and confidentiality of patient data and mention that an external company was needed to audit the cloud platform provider’s security mechanisms.
Seven papers describe applications for planning, managing or assessing therapeutic interventions.
Chang et al. [ 57 ] describe a website for access to information on drug compounds used in Traditional Chinese Medicine. In future, the iSMART portal shall provide genetic research features for drug research; however, until now only a webserver to the database exists publicly and no information on the cloud-specific development is given.
Dixon et al. describe a prototype of a clinical decision support system (CDS) that packages a patient’s data and sends it to a remote SaaS for analysis, i.e. rule application [ 58 ]; a comparison of the local assessments versus the remotely generated results are analyzed in [ 59 ]. While the service model for cloud computing seems fulfilled, no features of SaaS such as scalability or pay-per-use are mentioned. Another evaluation of a cloud-based decision support system for early recognition of sepsis is described by Amlad et al. [ 60 ]. An add-on to the Cerner EHR was used to continuously monitor patient to recognize possible outbreak of sepsis. While the system performed well, the added benefit of being cloud-based is not described.
A large part of the papers from this domain evaluate the performance gain when moving Monte Carlo simulations for radiation therapy planning into the cloud. Poole et al. [ 61 ] used the Amazon Cloud to simulate a clinical linear accelerator and experienced a 1/n reduction of computing time usage when up to 20 worker instances were instantiated. Similarly, Miras et al. [ 62 ] used Microsoft Azure with up to 64 virtual machines of different sizes to measure a speedup of up to 37x. A more complex calculation is performed by Na et al. [ 63 ] who uses Amazon cloud with up to 100 worker instances for a speedup of 10-14x. The difference in the speedup is caused by the ability to parallelize the algorithms and the overhead for worker management and data communication. Cost of routine use has been estimated by all three to be below or at par of an equivalent local hardware cluster. However, all three studies are limited as the use cases focused on the performance of the mathematical libraries outside real world applications.
Also the paper of Parsons et al. [ 64 ] includes a description of an Amazon cloud-based model for Monte Carlo simulation of radiation dose. They used a web application called VirtuaLinac to model radiation treatment components.
This domain includes articles describing cloud computing utilization for enabling secondary use of clinical data; e.g. for data analysis, text mining, or clinical research. Six papers belong to this domain.
Regola and Chawla discuss possibilities to store and share research health data and data from electronic health records in a cloud structure to reach an HIPAA (Health Insurance Portability and Accountability Act) complying environment [ 65 ]. For them, cloud computing offers the advantage of providing researchers with large computing resources. Data security can be achieved by providing proprietary cloud solutions where researchers can create their own customized networks and virtual servers.
Similarly, Chard et al. describe an approach to enable cloud-based services which should offer high scalability and HIPAA-compliant data security. They propose a cloud-based Software-as-a-Service NLP prototype to enable the extraction, procession, management, and comparison of medical data from several hospitals. Nevertheless, it does not become clear how data security should be achieved as-at the moment-the data in this cloud is not anonymous yet, but shall be accessible only to the particular data provider [ 66 ]. Also a cloud-based NLP service is described by Christoph et al. [ 67 ], here the free text is deidentified before put into the cloud. While the project described uses a community cloud, the OpenNebula-based implementation is said to run also in private or public scenarios. The main benefits of using cloud computing is in lowering the cost for processing data (no upfront investment, pay per use) and the managed services which enables the use of complex, computing intensive services by data providers with small IT departments.
Shen et al. describe generic standards-based services that can be transferred as virtual machines to other hospitals so that clinical pathways can be learned from order sets documented in EHRs. They mention that data mining models and results might be shared between different hospitals over a cloud-based server. Nevertheless the authors equal cloud computing with the Internet in general [ 68 ].
In the last article of this domain Rea et al. claim that they created a prototypic system that enables a cloud-based architecture to mine and normalize data for interchanging between hospitals [ 69 ]. The authors nevertheless do not explain how they face possible security and safety concerns when putting sensitive health data into a cloud, e.g. does this prototype include a private or a public cloud?
Other domains
The main topic of some papers could not be assigned to one of the other categories.
Doukas et al. describe an infrastructure for automated skin lesion classification to detect skin cancer in an early stage. This assessment system is based on mobile technologies used by patients–a cloud provides the essential data processing components for pattern recognition [ 70 ].
Shen et al. implemented a cloud bio-signal (e.g. electroencephalography, electrocardiograph) analysis system but it hard to identify where exactly the cloud component can be found in their system architecture [ 71 ]. Papakonstantinou et al. describe the prototype of a semantic wiki to support training in healthcare process management which allows cost savings, accelerated time to delivery, and offloaded maintenance [ 72 ].
Second Live as a virtual environment is mentioned in two publications. Garcia-Penalvo et al. describe an interesting training environment for ongoing and already skilled pharmacists in virtual worlds [ 73 ]. Their objective is that students and teachers get each an own avatar in the Second Life environment to practice and train laboratory work to assure a high education and work quality. In the authors’ conceptual paper cloud computing is thought to support the mechanisms of data recovery and analysis to proper evaluate the processes in Second Life. Also Stoicu-Tivadar et al. propose a medical education approach based on the Second Life environment. They describe an information system that provides training for medical students to treat patients using avatars. According to the authors cloud computing should be used to store data bases such as a medical guidelines database remotely but no further details on the use of clouds are given [ 74 ].
Medical students may profit from radiology cases provided for use on mobiles according to Balkman and Loehfelm [ 75 ]. They build a learning web-portal based on Googles App Engine which was perceived well, although the latency of bringing images to mobile devices is seen as a downside. In the end, a student must be evaluated by his performance. Ferenchick and Solomon have developed a mobile assessment tool (basically web based questionnaires) for observers to document proved student skills [ 76 ].
Another work that is not captured by the defined domains is dealing with mobile health applications that require data-intensive multimedia and security algorithms–the authors refer to the cloud-based provision as “Security as a Service” [ 77 ].
An interesting approach is the work of Nagata et al., who successfully implemented a cloud-based EHR for reducing adverse health consequences of the earthquake and nuclear disaster in Fukushima in 2011. To allow the emergency teams in Fukushima an efficient management and handling of patient data, access to EHRs for assessing patient data was provided in the form of software as service [ 78 ].
Furthermore, we found one article containing a short SWOT (strengths-weaknesses-opportunities-challenges) analysis of cloud computing in healthcare [ 4 ], and another dealing with implementation of strategic planning of organizations moving to a cloud [ 5 ]. Finally, two “overview articles” have been identified: one provided an overview on data privacy solutions in cloud computing [ 79 ] and secondly, the work of Ahuja et al. names several benefits and challenges of cloud computing [ 6 ]. Both such overview approaches however, are not performed systematically, but only include some major thoughts on cloud computing in healthcare, its advantages and disadvantages.
Implementation status
Our literature research revealed 22 theoretical papers that did not describe a specific cloud project but provided more common information on cloud computing in healthcare [ 4 - 6 , 8 , 14 , 23 , 24 , 26 , 49 - 52 , 56 , 79 - 87 ]. 12 articles include descriptions of basic conceptual work for cloud projects, but included no creation of a real system [ 16 , 30 , 35 , 46 , 53 , 54 , 63 , 77 , 88 - 92 ]. If applications are described they are usually in a prototype status [ 1 , 7 , 10 - 13 , 15 , 17 - 22 , 28 , 29 , 31 , 33 , 34 , 39 - 45 , 47 , 48 , 55 , 58 , 59 , 61 - 70 , 72 - 75 , 93 - 101 ]. Successful implementations of cloud systems in healthcare were only described in 13 of the 104 articles [ 9 , 25 , 27 , 32 , 36 - 38 , 51 , 57 , 60 , 71 , 78 , 102 ].
The distribution of the diverse implementation status is shown in Figure 4 .

Distribution of implementation status.
Definitions of cloud computing and NIST characteristics
Most articles rather describe features of the cloud than define it. These features include pay-as-you-go access to computing resources avoiding upfront investments and underutilizing private resources [ 1 , 21 , 25 , 30 , 31 , 53 , 62 , 65 ]. Scalability and flexibility are also presented as important characteristics for using cloud-based services, as system capabilities can easily adjust (scale) to momentary needs [ 1 , 25 , 50 , 62 , 82 , 84 ]. Availability and ubiquitous access are often mentioned [ 11 , 20 , 23 , 51 , 53 , 98 ] as well as the option to virtualize resources with distributed computing technologies, sometimes referred to as remote hosting [ 11 , 25 , 37 , 81 ].
These features can be linked to the five NIST characteristics of cloud-computing, i.e. rapid elasticity, followed by broad network access, resource pooling, on-demand self-service and measured service at least. But only eight publications directly cite NIST’s definition [ 4 , 5 , 18 , 23 , 24 , 40 , 52 , 55 , 63 , 67 , 75 , 81 , 83 , 85 , 100 ]. Thus, in most of the articles presenting cloud applications, details about the real deployment and service models remain unclear.
Some authors emphasize the more technical aspects of clouds: cloud computing is said to be more than just web-based applications, but also includes the necessary hardware, i.e. a physical network of many computers [ 5 , 26 , 77 , 84 ]. In five papers the cloud is even equated with the Internet in general [ 8 , 9 , 68 , 71 , 102 ].
Users and providers
Most cloud-based services are provided using own, proprietary infrastructure. If commercial services are used, Amazon services are applied most often: Elastic Computing Cloud (EC2) is referred to eleven times [ 13 , 34 , 48 , 61 , 63 , 66 , 72 , 90 , 93 , 97 ] and Amazon’s S3 service (Simple Storage Service) three times [ 25 , 29 , 40 ]. One application [ 65 ] used the Virtual Private Cloud (Amazon VPC) to provide more secure services. Cloud infrastructures by other vendors such as Microsoft or Google play a minor role [ 1 , 12 , 17 , 19 , 36 , 62 , 75 , 98 ].
End users of the applications described are from five main groups: physicians, other medical staff, patients, clinical researchers, and IT experts. Several articles describe physicians and other medical staff storing, sharing and analyzing patient data or medical images [ 1 , 7 - 9 , 11 - 13 , 17 , 19 , 25 , 27 - 29 , 31 , 36 , 46 , 51 , 58 , 69 , 71 , 78 , 88 , 90 , 92 , 94 , 96 , 102 ]. Also therapy planning or simulation of radiation dose might be enabled for physicians using cloud systems [ 64 ].
Patients are mainly focused in projects on personal healthcare management [ 16 , 19 , 22 , 29 , 36 - 43 , 49 , 96 ]. Medical researchers should be enabled to access large pools of data for medical research purposes [ 18 , 30 , 35 , 57 , 65 , 66 , 68 , 69 ], whereas programmers and hospital IT staff should be enabled to work on the creation of cloud-based solutions [ 8 , 34 , 53 , 62 , 93 , 95 ].
Challenges of cloud computing in healthcare
Three types of concerns using cloud computing in healthcare could be identified: safety/security of data as a threat to privacy, reliability and transparency of data handling by third parties, and lack of experience or evidence of a new technology.
First, in our literature we found that many authors mentioned data privacy and data confidentiality concerns. There is the fear that unauthorized persons might access sensible medical data in a cloud [ 1 , 5 , 13 , 18 , 24 , 25 , 28 , 29 , 31 , 46 , 51 , 52 , 63 , 65 - 67 , 72 , 81 , 83 , 85 , 88 , 94 , 96 ] which might hurt confidentiality of sensitive data about patients, therapies or physicians [ 41 , 103 ].
It is especially important that data security, privacy and confidentiality are focused [ 65 ] if handling of sensitive health data is outsourced to a commercial cloud, which means “that a third party now has control over the cloud-hosted area” [ 56 ]. Rodrigues et al. state that “cloud-based EHR must maintain the same level of data security as data stored in the servers of the health care provider” [ 56 ], but do not illustrate how this should be achieved.
In the US the Department of Health & Human Services has passed the Health Insurance Portability and Accountability Act (HIPAA) in 1996 which includes national standards for transactions in electronic healthcare concerning data privacy and security [ 104 ]. These standards provide a framework which should be considered when designing cloud services [ 1 , 63 , 65 , 66 , 83 ].
Many examples for improving data privacy and reducing confidentiality risks by authentication and authorization mechanisms are described [ 1 , 6 , 13 , 17 , 18 , 25 , 51 , 66 , 83 , 88 , 94 ]. For example, secure transmission protocols such as PCoIP could be employed, special security certificates could be utilized [ 66 ], access control lists (ACLs) can identify users’ role and the actions permitted [ 13 , 18 ], and licenses or electronic keys are handed over to authorized cloud users such as patients or physicians [ 88 ]. Further, a digital signature can ensure that data was entered or sent by the acclaimed person [ 56 ].
Data encryption is as well important to ensure data privacy [ 1 , 6 , 13 , 17 , 26 , 48 , 83 , 102 ]. Standardized encryption algorithms might be used [ 63 , 102 ] as well as secured data transmission using HTTPS [ 53 , 96 ]. Data encryption nevertheless can be problematic in emergency situations when physicians need instant access to patient data in a cloud and an access key is missing [ 58 ].
In principle, as few data as possible shall be put into the cloud [ 58 ]. Often it has to be anonymized before leaving an organization [ 30 , 65 ]. Sometimes it is possible to store identifiable data in separate entities to separate concerns [ 25 ]. Nevertheless, organizations often need to inform their patients before migrating their data to a third-party cloud computing provider [ 56 ]. The theoretical paper of Wang et al. focusses on the problem that cloud server providers might not be trustworthy (e.g. he might delete of modify some parts of the stored medical records). According to the authors an independent committee should be built to recover the original medical records from the cloud in the case of untrusted cloud providers [ 87 ].
Second, fears on technical issues exist when trying to implement a secure computing environment. Data might be lost due to technical problems with the cloud system [ 17 , 25 , 40 , 83 ] or vice versa, sensitive data cannot be fully deleted anymore once put into a remote cloud, leaving data in form of a fuzzy cloud structure [ 5 , 83 ]. In general, there is a fear of dependence on a cloud provider: a loss of control over their data [ 23 , 25 , 82 ]. Using audit trails might be a possibility to better control the use of a cloud system or facilitating data recovery [ 26 ]. This is why it is important to select only partners for outsourcing and cloud computing which can prove their security measures [ 56 , 89 , 100 ] and make handling of data completely transparent for the data owners [ 56 ]. Additionally, service-level agreements should be established between the customer organization and the cloud provider concerning data encryption and safety policies [ 23 , 100 ]. On the other hand clouds can even be utilized to store data using resource intensive security algorithms as kind of “Security-as-a-Service” [ 77 ].
Third, there are also concerns about the maturity of the cloud service–there might still be lack of evidence of successful cloud implementation in healthcare [ 4 , 83 ]. With regards to the economic advantages, Schweitzer proposes to conduct an economic analysis to ensure that savings through cloud computing are not overestimated because of hidden costs (e.g. cost for in-house IT support) [ 83 ].
Since for this relatively new domain with just emerging evidence standardized keywords and subject headings have yet not been well established, we decided on conducting a scoping review, as this approach is well suited for clarifying a complex concept and refine subsequent research inquiries [ 105 ]. While this approach yielded an overview on the status of cloud-computing in healthcare and identified the hot-topics, a systematic follow-up review could dig deeper into specific areas. Our review could help to focus on specific topics and to cope with the pace of publications.
The analysis of papers with regards to cloud features was hampered by the lack of information provided by the respective authors. Too often cloud was used synonymously with “Internet-based” or “running in a virtual machine” or “potentially scalable to a cloud” lacking any evidence of the real benefits. From the list of papers reviewed only eight papers refer explicitly to the NIST’s cloud computing definition itself. A large part of the papers do not even try to give a definition of cloud computing in general or describe in more detail what particularly makes their system to a cloud computing application. This is why we also conclude that future publications should more explicitly state their position with regards to the NIST characteristics.
Our findings may be limited by using MEDLINE as the main database as many publications especially in non-scientific media present cloud-based applications from a more practical or operational point of view. Searching the general Internet for cloud computing in healthcare reveals a very large number of hits of various kinds and qualities. Numerous cloud projects and offerings have not been scientifically published or evaluated. For example, CareCloud is a cloud-based software application including a complete infrastructure to document and facilitate caring processes in a hospital [ 106 ]; Box is a content sharing company which lately extends its cloud-based services to storage data to the healthcare sector enabling exchange of medical data between several physicians [ 107 ]. Well-known cloud services in health care are Microsoft’s Health Vault, a cloud-based platform to store and maintain health and fitness data [ 108 ] or the discontinued of Google Health service [ 109 ].
Of course, cloud computing is a hot topic and new papers are constantly published. Since 2010 the number of articles on cloud computing in healthcare has doubled almost every year. So the current review can only be a snapshot of a current state. However, comparing the publications date ranges of the topics shows no shift in the areas of research. A limitation is also that applications using cloud features may not be published with a title, abstract or keywords containing the word “cloud” and are thus not fitting our inclusion criteria.
The aim of this review was to get an overview on the status of cloud-computing in healthcare and to identify areas of interest beyond typical “OMICS” topics. We found that especially resource intensive (e.g. medical imaging) and communication intensive areas such as various kinds of “tele-”applications are predestined for cloud computing use.
Considering our research objectives, we were able to a) provide a comprehensive overview on the existing literature and elicit the key messages of the current publications and b) identify the “hot spots” within the healthcare domain where cloud computing concepts and applications have mostly been discussed.
The question, if the buzz word “cloud computing” has really already achieved more than just the “conceptual design” and “challenges” state and entered into the status of routine daily application still needs to be negated. Only 14 of the 102 publications have described successful applications. The vast majority of papers still was in an early prototype stage or only described potential options, challenges and risks of cloud services for the healthcare domain, but no actual application.
Thus, even though from 2010 to 2012 the number of articles on cloud computing in healthcare has doubled every year we had to realize, that many publications do not reference the characteristics of cloud computing as defined by NIST [ 2 ]. A large part of the papers do not even try to give a definition of cloud computing in general or describe in more detail what particularly makes their system to a cloud computing application.
It appeared to us, that many researchers do already declare their application as a cloud computing application, if only the two features of broad network access for data sharing among different stakeholders and data access from everywhere are given. Such type of applications, however, have already been implemented for a long time and–as long as the scenario has focused on supporting patient diagnostics and therapy–such approaches are typically named telemedicine applications, health information exchange or personal electronic health records.
In our opinion, an application which really enhances its provision by means of cloud computing should explicitly describe the cloud-specific characteristics of their application following the NIST definitions, such as rapid elasticity or measured service where a pay-per-use model supersedes upfront investments. Resource pooling helps organizations to consolidate and simplify infrastructure services and continue existing trends in virtualization. While in the consumer market on demand self-services are often used, in healthcare environments they only seem to play a minor role. Authors should also illustrate how this new technology/business model makes their application more cost effective than without cloud technology.
Further, if cloud computing is a major feature of a healthcare application, we recommend that in future publications, authors do describe the particular deployment model chosen (which often also relates to a description of data privacy measures applied, being very important for sensitive personal health data) and also which particular type of cloud service is applied. In too many of the recent publications those descriptions were missing and the impression remained, that authors often called a typical internet-/web-based telemedicine application now a cloud application, just because cloud computing is a current buzzword.
Acknowledgements
The work has been co-financed by the German Federal Ministry of Economics and Technology (BMWi) in the Trusted Cloud Initiative (Grant No FKZ 01MD11009). We acknowledge support by Deutsche Forschungsgemeinschaft and Friedrich-Alexander-Universität Erlangen-Nürnberg within the funding programme Open Access Publishing.
Abbreviations
Additional files.
Relevance screening form on basis of title and abstract. Shows how the large pool of MEDLINE articles found by keyword research was screened according to title and abstract.
Eligibility screening form on basis of full-text screening. Shows how the remained articles after the relevance screening where further screened on basis of eligibility criteria.
Characterization form on basis of full-text analysis. Shows how the content of the articles found eligible where characterized into several fields of interest.
Results from MEDLINE article analysis (n=102). Includes detailed results of the characterization of all eligible reviewed articles.
Competing interests
The authors declare that they have no competing interests.
Authors’ contributions
LG carried out the literature research and lead the study selection and screening process. FK, DT, IE, JC, IL, LG, and MS analyzed and categorized the identified articles. HUP, MS, and LG worked on drafting the manuscript. All authors read and approved the final manuscript.
Contributor Information
Lena Griebel, Email: [email protected] .
Hans-Ulrich Prokosch, Email: [email protected] .
Felix Köpcke, Email: [email protected] .
Dennis Toddenroth, Email: [email protected] .
Jan Christoph, Email: [email protected] .
Ines Leb, Email: [email protected] .
Igor Engel, Email: [email protected] .
Martin Sedlmayr, Email: [email protected] .

Emerging Trends in Expert Applications and Security pp 617–623 Cite as
Cloud Computing Research Issues, Challenges, and Future Directions
- Dhirender Singh 19 ,
- R. K. Banyal 19 &
- Arvind Kumar Sharma 20
- Conference paper
- First Online: 20 November 2018
1285 Accesses
Part of the book series: Advances in Intelligent Systems and Computing ((AISC,volume 841))
Cloud computing could be a hot research area among the researchers in today’s world. Cloud computing is thought on be a promising resolution for mobile computing as a result of many reasons for quality, portability, and communication. The need for mobility in cloud computing has given the worth to mobile cloud computing. The cloud computing during this paper has been explored the variety of mechanism for providing data security in order that cloud computing would be widely accepted by the variety of many users. Also, this paper presents an overview of cloud computing research issues, challenges, and future directions.
- Cloud Computing
- Provide Data Security
- Cloud Forensics
- Cloud Consumers
- Past Research Papers
These keywords were added by machine and not by the authors. This process is experimental and the keywords may be updated as the learning algorithm improves.
This is a preview of subscription content, log in via an institution .
Buying options
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Alex ME, Kishore R (2017) Forensics framework for cloud computing. Comput Electr Eng 60:193–205. https://doi.org/10.1016/j.compeleceng.2017.02.006
Article Google Scholar
Aljawarneh SA, Alawneh A, Jaradat R (2017) Cloud security engineering: early stages of SDLC. Futur Gener Comput Syst 74:385–392. https://doi.org/10.1016/j.future.2016.10.005
Alshammari A, Alhaidari S, Alharbi A, Zohdy M (2017) Security threats and challenges in cloud computing. In: 2017 IEEE 4th international conference on cyber security and cloud computing, pp 46–51. https://doi.org/10.1109/cscloud.2017.59
Gonzales D, Kaplan JM, Saltzman E et al (2017) Cloud-trust-a security assessment model for infrastructure as a service (IaaS) clouds. IEEE Trans Cloud Comput 5:523–536. https://doi.org/10.1109/TCC.2015.2415794
Jiugen Y (2017) Research on interactive application of online education based on cloud computing and large data, pp 593–596
Google Scholar
Kajaree D, Behera R (2017) A survey on web crawler approaches. Int J Innov Res Comput Commun Eng 5:1302–1309. https://doi.org/10.15680/IJIRCCE.2017
Malgey S, Chauhan P (2016) A review on security issues and their impact on cloud computing environment. Int J Adv Res Comput Commun Eng 5:249–253. https://doi.org/10.17148/IJARCCE.2016.5653
Pei D, Guo X, Zhang J (2017) A video encryption service based on cloud computing
Sadok L, Okba K, Oueslati W (2017) Management by composition of applications, pp 144–150
Skourletopoulos G, Mavromoustakis CX, Mastorakis G et al (2017) Advances in mobile cloud computing and big data in the 5G era, p 22. https://doi.org/10.1007/978-3-319-45145-9
Surbiryala J, Li C, Rong C (2017) Framework for improving security in cloud computing. IEEE 260–264
Download references
Author information
Authors and affiliations.
Rajasthan Technical University, Kota, India
Dhirender Singh & R. K. Banyal
University of Kota, Kota, India
Arvind Kumar Sharma
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Arvind Kumar Sharma .
Editor information
Editors and affiliations.
Jaipur Engineering College and Research Centre, Jaipur, Rajasthan, India
Vijay Singh Rathore
Intelligent Systems Lab, University of Amsterdam, Amsterdam, The Netherlands
Marcel Worring
Sri Aurobindo Institute of Technology, Indore, Madhya Pradesh, India
Durgesh Kumar Mishra
Sabar Institute of Technology for Girls, Ahmedabad, Gujarat, India
Department of Computer Science and Engineering, Jaipur Engineering College and Research Centre, Jaipur, Rajasthan, India
Shikha Maheshwari
Rights and permissions
Reprints and permissions
Copyright information
© 2019 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper.
Singh, D., Banyal, R.K., Sharma, A.K. (2019). Cloud Computing Research Issues, Challenges, and Future Directions. In: Rathore, V., Worring, M., Mishra, D., Joshi, A., Maheshwari, S. (eds) Emerging Trends in Expert Applications and Security. Advances in Intelligent Systems and Computing, vol 841. Springer, Singapore. https://doi.org/10.1007/978-981-13-2285-3_72
Download citation
DOI : https://doi.org/10.1007/978-981-13-2285-3_72
Published : 20 November 2018
Publisher Name : Springer, Singapore
Print ISBN : 978-981-13-2284-6
Online ISBN : 978-981-13-2285-3
eBook Packages : Intelligent Technologies and Robotics Intelligent Technologies and Robotics (R0)
Share this paper
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
Advances, Systems and Applications
- Open access
- Published: 23 December 2019
Load balancing in cloud computing – A hierarchical taxonomical classification
- Shahbaz Afzal ORCID: orcid.org/0000-0002-1217-9357 1 &
- G. Kavitha 1
Journal of Cloud Computing volume 8 , Article number: 22 ( 2019 ) Cite this article
58k Accesses
91 Citations
1 Altmetric
Metrics details
Load unbalancing problem is a multi-variant, multi-constraint problem that degrades performance and efficiency of computing resources. Load balancing techniques cater the solution for load unbalancing situation for two undesirable facets- overloading and under-loading. In contempt of the importance of load balancing techniques to the best of our knowledge, there is no comprehensive, extensive, systematic and hierarchical classification about the existing load balancing techniques. Further, the factors that cause load unbalancing problem are neither studied nor considered in the literature. This paper presents a detailed encyclopedic review about the load balancing techniques. The advantages and limitations of existing methods are highlighted with crucial challenges being addressed so as to develop efficient load balancing algorithms in future. The paper also suggests new insights towards load balancing in cloud computing.
Introduction
Cloud Computing is an internet based network technology that shared a rapid growth in the advances of communication technology by providing service to customers of various requirements with the aid of online computing resources. It has provisions of both hardware and software applications along with software development platforms and testing tools as resources [ 1 , 2 ]. Such a resource delivery is accomplished with the help of services. While as the former comes under category of Infrastructure as a service (IaaS) cloud, the latter two comes under headings of Software as a service (SaaS) cloud and platform as a service (PaaS) cloud respectively [ 3 ]. The cloud computing is an on-demand network enabled computing model that share resources as services billed on pay-as-you-go (PAYG) plan [ 4 ]. Some of the giant players in given technology are Amazon, Microsoft, Google, SAP, Oracle, VMware, Sales force, IBM and others [ 1 , 2 ]. Majority of these cloud providers are high- tech IT organizations. The cloud computing model is viewed under two different headings. The first one is the service delivery model, which defines the type of the service offered by a typical cloud provider. Based on this aspect, there are popularly following three important service models SaaS, PaaS and IaaS [ 5 , 6 ]. The other aspect of cloud computing model is viewed on its scale of use, affiliation, ownership, size and access. The official ‘National Institute of Standards and Technology’ (NIST) definition for cloud computing outlines four cloud deployment models namely private, public, community and hybrid clouds [ 7 ].
A cloud computing model is efficient if its resources are utilized in best possible way and such an efficient utilization can be achieved by employing and maintaining proper management of cloud resources. Resource management is achieved by adopting robust resource scheduling, allocation and powerful resource scalability techniques. These resources are provided to customers in the form of Virtual Machines (VM) through a process known as virtualization that makes use of an entity (software, hardware or both) known as hypervisor [ 8 ]. The greatest advantage of cloud computing is that a single user physical machine is transformed into a multiuser virtual machines [ 9 , 10 ]. The Cloud Service Provider (CSP) plays a crucial role in service delivery to users and is a complex task with given available virtual resources. While serving user requests, some VMs will get a heavy traffic of user tasks and some will get a lesser traffic. As a result, the Cloud Service Provider (CSP) is left with unbalanced machines which have a huge gradient of user tasks and resource utilization [ 11 ].
The problem of load unbalancing is an undesirable event in the CSP side that degrades the performance and efficacy of the computing resources along with guaranteed Quality of Service (QoS) on agreed Service Level Agreement (SLA) between consumer and provider. Under these circumstances there arises need for load balancing (LB) and is a peculiar topic of research interest among researchers. The load balancing in cloud computing can be done at physical machine level or VM level [ 2 ].
A task utilize resources of a VM and when a bunch of tasks arrive at a VM, the resources gets exhausted which means no resource is now available to handle the additional task requests. When such situation arises the VM is said to have entered into an overloaded state. At this point of time, tasks will either suffer from starvation or end up in deadlock with no hope of accomplishing them. Consequently there is necessity to migrate tasks to another resource on other VM. The workload migration process includes three basic steps: load balancing which checks the current load on machine resource, resource discovery which finds another suitable resource and workload migration which moves extra tasks to available resources. These operations are performed by three different units commonly known as load balancer, resource discovery and task migration units respectively.
Load balancing is the process of redistribution of workload in a distributed system like cloud computing ensuring no computing machine is overloaded, under-loaded or idle [ 12 , 13 ]. Load balancing tries to speed up different constrained parameters like response time, execution time, system stability etc. thereby improving performance of cloud [ 14 , 15 ]. It is an optimization technique in which task scheduling is an NP hard problem. There are a large number of load balancing approaches proposed by researchers where most of focus has been concerned on task scheduling, task allocation, resource scheduling, resource allocation, and resource management. To the best of our knowledge, we could not find an in-depth and comprehensive literature concerned with factors that cause load unbalancing situation. The survey papers based on load balancing could not provide a proper systematic classification of methods and techniques. The main aim of the paper is to review the existing work along with the advantages and pitfalls in them. A comparison is also made among different existing load balancing techniques and the challenges faced in cloud load balancing. The survey also outlines factors responsible for load unbalancing problem and also suggests methods that can be used in future work. The contributions of this paper are summarized as follows:
Explore the factors that cause load unbalancing problem in cloud computing.
Provide a systematic overview of the existing approaches in the load balancing process and the way in which these approaches have been used in the cloud technology.
Provide the in-depth classification of different load balancing techniques, methods, strategies and algorithms.
Analyze the challenges faced by researchers in developing an efficient load balancing algorithm.
The remaining paper is structured as follows. Section “ Load balancing model background ” features a brief description about load balancing model in cloud computing. Section “ Research methodology ” highlights some related works. The research methodology is discussed in section “ Research methodology ”. Section “ Proposed classification of load balancing algorithms ” proposes taxonomy based classification. The results are evaluated in section “ Results and discussion ” while section “ Discussion on open issues on load balancing in cloud computing ” discusses upon open issues in cloud load balancing. Finally section “ Conclusion and future work ” concludes our work and points out some future directions.
Load balancing model background
In this section a two level load balancing architecture model is presented in imbalanced clouds for achieving best load shedding as shown in Fig. 1 which is a modified architecture given by Gupta et al. [ 16 ]. The virtual machine manager and virtual machine monitor are abstracted in this model. The first level load balancing is performed at the Physical Machine (PM) level and the second level is performed at the VM level. Based on this, there are two task migration sets;
Intra VM task migration
Inter VM task migration
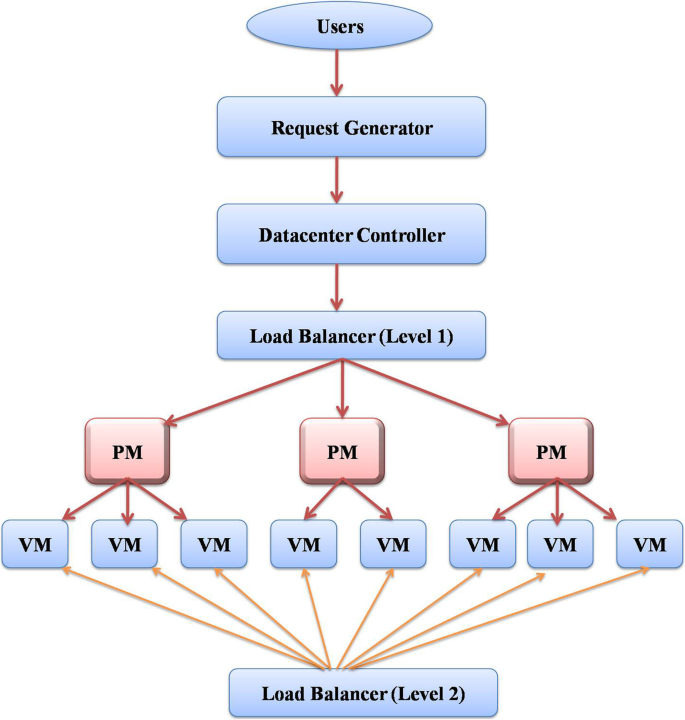
Two level Load Balancing Architecture
The request generator generates user requests which are user tasks that need computing resources for their execution. Data center controller is in-charge of task management. The load balancer checks which VM to assign for a given user task. The first level load balancer balances the given workload on individual Physical Machines by distributing the workload among its respective associated Virtual Machines. The second level load balancer balances the workload across different Virtual Machines of different Physical Machines.

Activities involved in load balancing
Scheduling and allocating tasks to VMs based on their requirements constitute the cloud computing workload. The load balancing process involves the following activities [ 2 ]:
Identification of user task requirements
This phase identifies the resource requirement of the user tasks to be scheduled for execution on a VM.
Identification of resource details of a VM
This checks the status of resource details of a VM. It gives the current resource utilization of VM and the unallocated resources. Based on this phase, the status of VM can be determined as balanced, overloaded or under-loaded with respect to a threshold.
Task scheduling
Once resource details of a VM are identified the tasks are scheduled to appropriate resources on appropriate VMs by a scheduling algorithm.
Resource allocation
The resources are allocated to scheduled tasks for execution. A resource allocation policy is being employed to accomplish this. A large number of scheduling and allocation policies are proposed in literature. While, scheduling is required for speeding up the execution, allocation policy is used for proper resource management and improving resource performance. The strength of the load balancing algorithm is determined by the efficacy of the scheduling algorithm and the allocation policy [ 17 , 18 , 19 ].
Migration is an important phase in load balancing process in cloud and latter is incomplete without the former. Migration is of two kinds in cloud based on entity taken into consideration- VM migration and task migration. VM migration is the movement of a VM from one physical host to another to get rid of the overloading problem and is categorized into types as live VM migration and non live migration. Likewise task migration is the movement of tasks across VMs and is of two types: intra VM task migration and inter VM task migration. A large number of migration approaches has been proposed in literature. An efficient migration technique leads to an efficient load balancing. From the extensive survey it has been concluded that task migration process is more time and cost effective than VM migration and the trend has shifted from VM to task migration [ 20 , 21 , 22 , 23 , 24 ].
Related work
In general a lot of work have been done in the field of cloud computing particularly in scheduling (tasks, VMs and Compute), resource provisioning, resource management, energy management and load balancing etc. However, load balancing has been an eagle’s eye among researchers because of its essence in cloud computing between the stakeholders’ i.e. Cloud Service Provider and Cloud Service Consumer. Based on analysis of existing review literature one of the reasons presented is absence of proper classification among different approaches. A thorough review about the existing work in literature has been presented in this section.
Ghomi et al. [ 25 ] proposed a survey on load balancing algorithm in cloud computing. The authors presented classification on task scheduling and load balancing algorithms in seven different categories that include hadoop- map reduce load balancing, agent based load balancing, natural phenomena based load balancing, application oriented load balancing, general load balancing, network aware load balancing and workflow specific load balancing which in literature fall under two domains based on system state and who initialized the process. From each category, the different algorithms are grouped together and their advantages and limitations are listed. Meanwhile, Milani et al. [ 26 ] reviewed existing load balancing techniques, established on the survey; authors grouped existing algorithms into three broad domains as static, dynamic and hybrid. The authors formalized relevant questions towards load balancing and addressed key concern about importance, expectation level of metrics, role and challenges faced in load balancing. A proper search operation was followed in search query to retrieve most relevant content from different publishing sources assisted by Boolean operations in search strings and selection criteria phase was executed with Quality Assessment Checklist (QAC). However the two surveys examined limited QoS metrics in their work that are Response time, Makespan, Scalability, Resource utilization, Migration Time, Throughput and Energy saving leaving behind a gap to consider other important QoS metrics like migration cost, service level violations, degree of balance, task rejection ratio etc. This gap in metric selection for analysis is overcome in this survey.
Kalra and Singh [ 27 ] conducted a comparative study of various scheduling algorithms for cloud and grid computing considering five fundamental meta-heuristic methods namely Ant Colony Optimization (ACO), Genetic Algorithm (GA), Particle Swarm Optimization (PSO), League Championship Algorithm (LCA) and BAT algorithm. Besides this a thorough comparison is made among the techniques; however their work is limited to scheduling algorithms for meta-heuristic techniques only. Also the survey concentrates on evolutionary algorithms only and lacks broad classification.
Mesbahi and Rahmani [ 28 ] classified load balancing algorithms into three categories: general algorithm based, architectural based and artificial intelligence based, studied the basic requirements and essentials in designing and implementing a desired load balancer for cloud provider. Like other previous studies, this paper considers static and dynamic categorization as broad classification. However, authors suggested key challenges in designing load balancing algorithms. Further, authors made a judgment on the basis of study on algorithms that have properties of being dynamic, distributive and non-cooperative are best.
Kanakala et al. [ 29 ] proposed a classification paper on existing load balancing algorithms which are grouped into static and dynamic algorithms like ones discussed in previous studies. They also identified challenges in finding solution for problem of load balancing. Among the challenges are geographical distribution of nodes, migration time, system performance, energy management and security which are long ago listed in the literature. In-fact the authors compared existing load balancing algorithms on the basis of certain QoS metrics like throughput, speed, response time, migration time etc. The paper concluded that there is tradeoff among metrics. The limitation of paper is that only eight load balancing algorithms are compared from a vast set of algorithms.
Shah et al. [ 30 ] discusses a comprehensive overview with respect to the load balancing algorithms. The different load balancing methods were classified as static and dynamic based on the state of the system, homogeneous and heterogeneous based on VM type uniformity. Performance metrics were also used to classify the load balancing methods. Further, the advantages and disadvantages of each algorithm were discussed. The paper does not address the literature in a systematic manner.
Neghabi et al. [ 31 ] presented a well defined, systematic and potential review about load balancing techniques in software defined networks and broadly classified them into deterministic and non-deterministic approaches along with associated metrics being investigated into depth. The study poses some important questions and tries to answer them along dimensions of their significance, metric analysis, role and challenges being faced in load balancing of software defined networks. The study carried out by the authors presents the detailed advantages and limitations of existing literature in communication networks. Further the paper holds a strong foundation and solid correlation among load balancing metrics, despite the fact that it does not go specific to cloud computing domain. Also, the study is based on single level classification rather than hierarchical classification.
From above listed survey papers, it is concluded that already existing survey papers are lacking from a good classification system. A criterion is fixed for classification purpose, but no generalization and specialization characteristics are drawn, which eventually lead to inadequate and insufficient conclusions. Further, existing review articles does not examine some important parameters like algorithmic complexity of load balancing algorithms and also the percentage of occurrence of load balancing metrics in literature. The existing survey papers lacks full description of QoS metric set, most likely new metrics (as migration cost, service level violations, degree of balance, task rejection ratio) should have been introduced in survey. A taxonomy based classification is proposed in this paper to prove its effectiveness over the existing literature. Also, the classification of QoS metrics is proposed in this survey as performance metrics and economic metrics [ 32 ]. So, to guide future researchers in developing an efficient, robust, fault tolerant and advanced load balancing algorithm and to give them new insights into future work, a taxonomy based classification system is introduced in this paper. The proposed methodology of classification is based on various characteristics of load balancing algorithms- ‘nature of algorithm’, ‘state of the algorithm’, ‘trait used for load balancing’, ‘mode of execution’, ‘type’, ‘functionality’, and ‘technique used by algorithm’.
Research methodology
To go deep into roots of load balancing process as to what causes load unbalancing problem a proper research methodology was followed. The literature survey was conducted in accordance with general research strategy that outlines the way in which load unbalancing problem is undertaken and identifies the methods, theories, algorithms, approaches and paradigms used in it. The load unbalancing problem was studied in accordance with constructive generic framework (CGF) methodology [ 33 ] where it is broken down into sub- processes i.e. the factors, variables and parameters that are associated with load balancing. Further the literature study was enhanced by following the research guideline for Systematic Literature Review (SLR) as contemplated by Kitchenham with a special focus on research related to load balancing mechanism in cloud [ 26 , 34 ]. An SLR is a repeated research method that can be replicated by other researchers to explore more knowledge.
In order to feature the importance of load balancing in cloud computing, a set of questions were framed to address the key issues and challenges in load unbalancing.
Question identification
A set of questions were identified from literature survey that need to be answered before going into the load balancing process. Some of the questions have been answered in literature while others are not. The questions are given as follows:
RQ1: What causes the load unbalancing problem? This question tries to answer why load unbalancing problem happens. This involves identification of factors responsible for cause of load unbalancing. The question cannot be answered until each individual factor is considered and studied with full detail. The load balancing process is incomplete unless knowledge about variables leading to unbalancing is not clear. This is of prime importance and till date no study considered this question. So, this paper presents answer of this question.
RQ2: Why load balancing is the need of hour in cloud computing? This question tries to answer the issues and challenges faced by cloud service providers.
RQ3: Does load balancing consider the evaluation of single objective (single attribute) or multi-objective (multi-attribute) function(s)? This question classifies the existing load balancing algorithms into single objective and multi-objective approaches.
RQ4: What is the time complexity of load balancing algorithm? This question answers the amount of time taken by load balancing algorithm to complete the load balancing process. Algorithm complexity is not taken as a standard for classifying the LB algorithms in the existing literature. The algorithm should run with real time algorithm complexity to be of practical use.
This section explores the causes for load unbalancing problem in IaaS clouds and tries to answers RQ1. The following factors are the causes for load unbalancing problem in IaaS clouds.
The dynamic nature of user tasks.
The unpredictable and probabilistic traffic flow to a cloud provider.
Lack of robust, accurate and efficient mapper and generator function to map the tasks to the appropriate resources.
The scheduling process itself is an NP hard problem.
The heterogeneous nature of user tasks demanding varying resource requirements.
The uneven and non- uniform distribution of tasks across computing resources along with their dependencies also contributes to load unbalancing situation.
Load balancing is a promising solution to load unbalancing problem that arise due to circumstances discussed in this section. This section answers RQ2 with the importance of load balancing in cloud computing. The load balancing algorithm has to enhance response time, cost of execution, execution time, throughput, fault tolerance, migration time, degree of balance, makespan, resource utilization and scalability. At the same time to reduce the resource wastage, migration cost, power consumption, energy consumption, carbon emission and SLA violations. The degradation of values of these factors leads to poor Quality of Service (QOS) to CSC and drop in economy in the form of profit to CSP. So keeping in view QOS and economy, it has become a big challenge for CSPs to provide QOS according to guaranteed SLA. However, to improve performance and economic metrics in one go is still a milestone for researchers to conclude the load balancing as NP hard problem like scheduling. This is because as we try to improve one specific metric the associated metrics begin to diminish and bottleneck persists, thus declaring load unbalancing as a multi- constrained multi-objective problem.
The section discusses classification of load balancing approaches as single objective and multi-objective on the basis of number of objective functions solved by a particular algorithm and tries to answer RQ3. RQ3 is also an elucidation of the RQ2 to consider load unbalancing as a multi-objective problem. Till date there exists no perfect load balancing algorithm in literature that takes into accounts all of the metrics in a single algorithm. Different researchers propose single objective algorithm to speed up a single metric while others tried to improve more than one metric at a time. The limitation of single objective approaches is that introduction of these in load balancing process altogether would result in huge complexity of architectural design and may become impractical for use. So prime attention is shifted from single objective to multi-objective approaches. Table 3 reviews different existing approaches based on single objective or multi-objective function(s) solved by a particular approach.
The RQ4 tries to answer time complexity of the algorithm being used in load balancing process and should be considered as a benchmark to determine performance of a load balancing algorithm. However, as a matter of concern we could not find enough literature determining the algorithmic complexity of an approach being used in the process. Out of top 35 studies conducted in this research only 7 studies considers the algorithmic complexity in their work which accounts to only 20% and the figure may drop as we increase the search space.
Milani et al. [ 26 ] identified the three main primary questions in the existing literature and justified them in their work. The questions were formalized as follows;
What is the consequence on load balancing with the growth of cloud users? The authors pointed out that from 2010 to 2015 there is a momentous rise in research papers on the scope of load balancing that follows a positive exponential curve and in our work find it more increasing in 2016, 2017 and 2018. This shows the importance of load balancing in the cloud computing with increasing number of users.
What is the capability of present load balancing approaches to meet the primary load balancing metrics? The question was answered and validated through the argument that dynamic load balancing algorithms are more practical, robust, efficient and fault tolerant than static ones.
What are the problems, issues, challenges and solutions identified in load balancing for future trends? The limitations and advantages of the existing approaches were listed and based on that challenges faced by researchers were discussed.
Data collection search process
The data collection search process includes papers gathered from reputed sources, journals and publications from five most authentic and potential databases that are scientifically and technically peer- reviewed: IEEE Xplore Digital Library, Science Direct, ACM Digital Library, Springer and Elsevier. The search was organized in June 2018 with data collected from 2010 to June 2018. The data source consist of review and survey papers, journal papers and conference papers excluding book chapters. A well organized search process was adopted to retrieve relevant data started with fundamental terms to advanced ones. The search strings were framed for source databases with inclusion and exclusion criteria similar to the one used by [ 26 ]. Search keywords were formed along with their synonyms to increase the search space. Initially, the basic terms and keywords were used in search query processing like “Load Balancing in Cloud Computing”, “Workload Distribution in Cloud Computing”, “Resource Distribution in Cloud”, “Task scheduling”, “Migration process in Cloud Computing”, “Resource utilization in Cloud”, “Resource allocation policies in Cloud”, “Load scheduling in Cloud” and much more. Later on the advanced terms were used following by integration of basic keywords in query operation assisted by Boolean operations as “Boolean OR” and “Boolean AND” [ 26 , 35 ] to narrow down the search space for relevant data. As an illustration the following keywords were integrated “Resource allocation AND Task scheduling”, “Task Migration” “Task scheduling” and “Resource utilization”. Later on the advanced search operation was equipped to collect most reliable papers for data collection, like the use of Inspec controlled and non- controlled keywords were applied followed by advanced filters. As an example the following advanced search operation was applied in the IEEE Xplore. “Advanced keyword/phrase” option which include two sub options “metadata only” and “full text and metadata” each using three Boolean operations “AND”, “OR” “NOT”. Similarly, command search and citation search options were also used.
Proposed classification of load balancing algorithms
In this section load balancing algorithms are classified based on various criteria. A top down approach is proposed and followed in classification process. The limitation of existing review papers is that there is no proper and significant hierarchical taxonomical classification of load balancing algorithms which makes it quite difficult to identify where a particular algorithm holds its place in taxonomy. The various criteria used for classification purpose include ‘nature of algorithm’, ‘state of algorithm’, ‘trait used for load balancing’, ‘type of load balancing’, and ‘technique used in load balancing ’. For the first time in literature an in-depth analysis of the LB algorithms have been achieved in this work which the previous studies were lacking. Based on nature of algorithm, the load balancing algorithms are either proactive or reactive. This is first broad categorization we placed in taxonomy and which till date have not been shown in any of the literature studies. Based on state of system, the LB algorithms are static, dynamic or hybrid. On the basis of trait used in load balancing, LB algorithms are classified as scheduling and allocation algorithms. On the basis of type of LB algorithms they are grouped as VM LB algorithms, CPU LB algorithms, Task LB algorithms, Server LB algorithms, Network LB algorithms and Normal Cloud Load balancing algorithms. On the basis of functionality, the load balancing methods are grouped as hardware load balancing; elastic load balancing and latter is further grouped into network load balancing, application load balancing and classic load balancing. Based on the technique, Load balancing algorithms are classified as; Machine learning, Evolutionary, Nature Inspired, mathematical derived algorithms, and swarm based techniques.
Nature of the algorithm
The first categorization of load balancing algorithms in this work has been done on the basis of nature of algorithm. On the basis of this classification, LB algorithms are classified as proactive based approaches and reactive based approaches. However in other fields of technology particularly in the communication and networking for mobile adhoc networks (MANETS), the nature of the communication routing protocols has been extensively studied under these two variants [ 36 ].
A proactive based LB algorithmic technique is an approach to algorithmic design which takes into consideration action by causing change and not only reacting to that change when it happens. It is intended to yield a good outcome to avoid a problem in advance rather than waiting until there is a problem. Proactive behavior aims at identification and exploitation of opportunities and in taking preemptory action against potential problems and threats. The limitation of existing approaches is that a limited number of proactive approaches have been used and that too in a traditional manner with no novel concepts. Table 1 depicts proactive approaches in existing LB approaches. Polepally et al. [ 37 ] proposed dragonfly optimization and constraint measure-based LB approach in cloud computing by distributing uniform load across VMs with minimal power consumption. Xiao, et al. [ 38 ] proposed game theory based fairness-aware LB algorithm to minimize expected response time while maintain fairness. The Nash equilibrium point of the game corresponds to load balancing at optimal level.
The reactive based approaches act in response to a situation rather than controlling it. In reactive based approach of load balancing the problem of load unbalancing is solved as it arises and after which the consequences are visible. Most of load balancing algorithms fall under this category. The main flaw that has been analyzed from literature of existing works on load balancing is that load unbalancing problem is left to happen and then researchers propose some approaches to tackle that problem by optimizing some load balancing parameter(s) [ 32 ] as given in Fig. 2 . Table 2 discusses the reactive approaches in the existing LB approaches e.g. Adhikari et al. [ 39 ] proposed a heuristic-based scheduling and load balancing algorithm for IaaS cloud to minimize task completion time, makespan, waiting time, and increase resource utilization. Proactive approaches are more effective than reactive approaches as the former tries to avoid the problem in advance while in latter the solution is provided after the problem occurs.
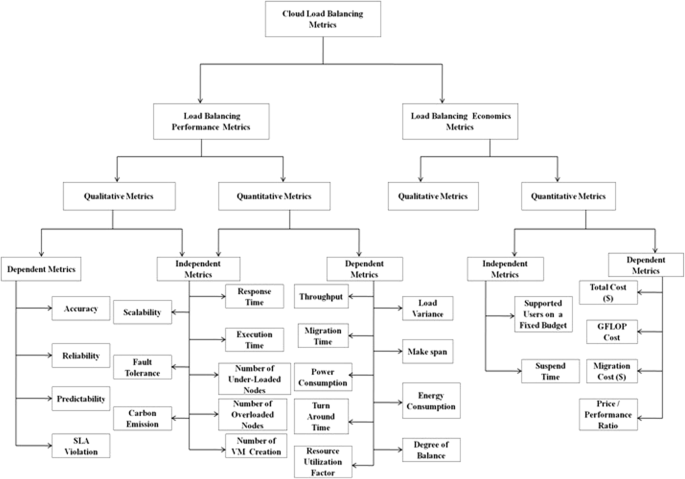
Load Balancing Metrics [ 32 ]
State of the algorithm
On the basis of state information of system that an algorithm relies on, LB algorithms are widely classified as static, dynamic and hybrid. From existing literature survey, it is evident that this is most widely used classification system for LB algorithms. Majority of work on comparative studies on load balancing begin the algorithmic taxonomy by placing this category on top of taxonomy. In static load balancing, traffic load is segregated uniformly across the servers. This is done by algorithm having the prior knowledge about system resources and task requirements. The static LB algorithm schedules tasks to VM for execution at compile time. The advantage of static algorithm is their less complexity but they suffer from a fatal bottleneck of being unable to move tasks during execution in progress to another machine for load balancing. Static algorithms do not consider current state of system and requires advance knowledge about machines and tasks like task resource requirements, communication time, processing power of nodes, memory, storage, bandwidth capacity and so on. The main drawback of static LB algorithm is that migration process is not possible during execution of tasks and hence is not suitable approach for distributed system like cloud where system state changes dynamically.
Further on the basis of mode of execution of tasks, dynamic algorithms are grouped as offline mode also called as batch mode and online mode or live mode as shown in Fig. 3 . In batch mode, the task is allocated only at some predefined instances where as in online mode the user task is mapped to a VM as soon it enters the scheduler. Dynamic load balancing algorithms are comparatively complex algorithms in contrast with their counterparts that handle incoming traffic flow at run time and can change state of a running task at any point of time. Dynamic load balancing takes into consideration the current state of system and has capacity to deal with unpredictable processing load. The advantage of dynamic load balancing is that tasks can move dynamically from an overloaded machine to under-loaded one but are much complex in nature and much complicated to design compared to static LB algorithms.
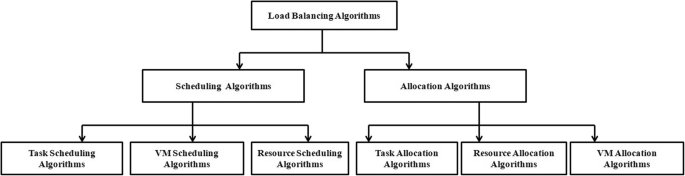
Load balancing algorithms on the basis of nature and state of the system
However dynamic LB algorithms are much efficient in terms of performance, accuracy and functionality. Static load balancing algorithms work smoothly if nodes have small load variations but could not operate in varying load environments. Figure 3 shows the load balancing taxonomy on the basis of nature and state of algorithm.
Trait used for load balancing
The algorithms in this category are classified as scheduling and allocation algorithms. The allocation and scheduling algorithms in cloud are classified based upon current state of VM and accordingly can be static or dynamic. The allocation and scheduling policies play a vital role in resource management and performance monitoring of cloud, which in turn has a good impact on QoS delivery to user. The scheduling policies are decomposed into three subsequent activities task scheduling, resource scheduling and VM scheduling; likewise the allocation policies are decomposed as task allocation, resource allocation and VM allocation respectively.
Task scheduling is the method of assigning user tasks to relevant computing resources for execution while resource scheduling is the process of planning, managing and monitoring computing resources for task execution. VM scheduling is the process of creating, destroying and managing VMs within a physical host apart from managing the VMs during migration process across the hosts. The task allocation is the act of allocating task to a resource on which it is supposed to execute. Resource allocation is the act of allocating a resource to a task for its completion. Task allocation and resource allocation are inversion of each other. VM allocation is the allocation of virtual machine to a user or a set of users. Figure 4 shows the load balancing algorithms on the basis of trait being used.
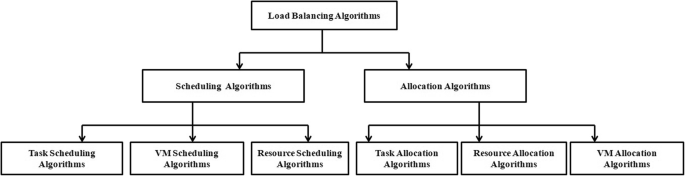
Load balancing on the basis of trait used
Functionality
On the basis of functionality, load balancers are classified as hardware load balancer and elastic load balancer as depicted in Fig. 5 . Hardware load balancers are concerned with the distribution of workload at hardware level i.e. memory, storage and CPU. Elastic Load Balancing automatically distributes incoming application traffic across multiple targets, such as Amazon EC2 instances, containers, and IP addresses. It can handle varying load of user application traffic in a single availability zone or across multiple availability zones. Elastic Load Balancing offers three types of load balancers that all feature high availability, automatic scaling, and robust security necessary to make user applications fault tolerant. Application Load Balancer operates at the request level (layer 7) routing traffic to targets - EC2 instances, containers and IP addresses based on the content of the request. Ideal for advanced load balancing of HTTP and HTTPS traffic, Application Load Balancer provides advanced request routing targeted at delivery of modern application architectures, including micro-services and container-based applications. Application Load Balancer simplifies and improves the security of your application, by ensuring that the latest SSL/TLS ciphers and protocols are used at all times. Network load balancers are implemented at the transport layer of the OSI model. It has ability to handle millions of requests per second. The network load balancing is popularly used by Microsoft azure and AWS in deployment model. The network load balancing feature allows traffic distribution among servers using the TCP/IP internet protocol. Classic Load Balancer provides basic load balancing across multiple Amazon EC2 instances and operates at both the request level and connection level. Classic Load Balancer is intended for applications that were built within the EC2-Classic network.
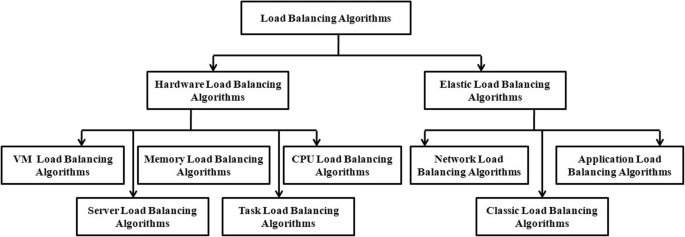
Load balancing on the basis of functionality and type
Type of load balancing
On the basis of type, LB algorithms are classified as VM LB, CPU LB, task LB, server LB, network LB and normal cloud LB as shown in Fig. 5 . VM load balancing is the process of redistribution of VMs from overloaded nodes to under loaded nodes and was first introduced as a new inbox feature in windows server 2016 that allows optimize node utilization in a failure cluster. VM load balancing identifies over committed nodes and redistributes VMs from those nodes to under committed nodes. VMs are live migrated from a node exceeding threshold to a newly added node in failure cluster. VM load balancing is achieved through VM migration process. CPU load balancing is the process of limiting the load on a CPU within its threshold limit. Task Load balancing is the act of distribution of tasks across the VMs from overloaded machines to under loaded machines. Server LB is proper distribution of total incoming load in a datacenter or a server farm across the servers. Network LB is concerned with management of incoming traffic without use of complex protocols.
Technique used in load balancing
On the basis of the technique used, load balancing algorithms are classified as heuristics and meta-heuristics techniques, and optimization techniques.
A heuristic approach is an approach to problem solving accounting a practical method or methodology guaranteed not be optimal, perfect, logical or rationale but sufficient to reach an immediate goal. Finding an optimal solution may be impossible or impractical particularly to load balancing which is a NP hard problem and heuristics play an important role to gear up the process of finding a decent solution. Heuristic methods are designed following strategies derived from previous experience with similar problem sets. Heuristics play a crucial role in load balancing process to sort up various issues faced by CSPs. A lot of research work has been carried out with heuristic and meta-heuristic approaches in cloud load balancing and as such we have classified the heuristic and meta-heuristic methods into nature inspired algorithms and classical algorithms. The nature inspired algorithms are sub divided into evolutionary based algorithms and swarm based algorithms.
Optimization techniques are used to find optimal solutions of a problem. Optimization techniques in cloud load balancing are broadly classified as classical and non classical optimization techniques. These algorithms can be either stochastic or deterministic. A further classification classifies the optimization techniques into constrained based and non constrained based algorithms and these can further be either a single objective or multi-criteria optimization. The multi- criteria optimization is further classified as multi-attribute and multi-objective optimization. The multi- objective algorithms may be either machine learning based, nature inspired based, swarm based or mathematical derived based load balancing algorithms. Figure 6 shows the load balancing algorithms on the basis of technique used.
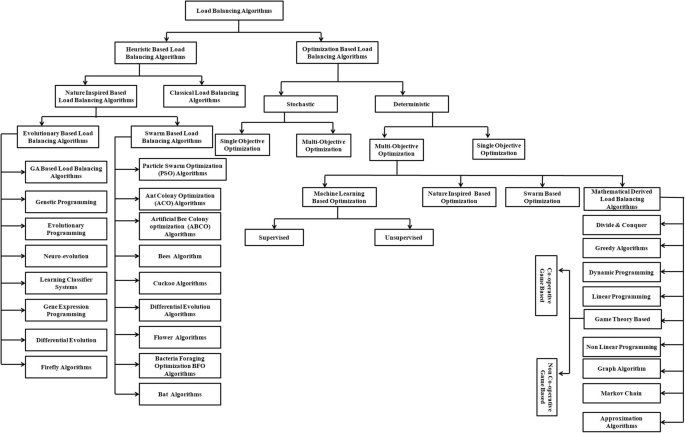
Load balancing algorithms on the basis of technique
Table 1 and Table 2 respectively list the different characteristics of proactive and reactive approaches in related literature along various dimensions. The strength and weakness of each approach is also reflected in Table 1 and Table 2 . Table 3 depicts the different approaches under investigation as single objective and multi-objective. Table 3 also highlights the implementation platform, tool and simulating environment under which a particular approach was studied and investigated. Finally Table 4 presents the essential load balancing metrics analyzed in the existing approaches.
Results and discussion
This section outlines the results achieved from comparative analysis of different load balancing approaches in cloud computing. Figure 7(a) shows the percentage of various scheduling types in proactive based load balancing approaches. It is clear that task scheduling and resource scheduling each with 45.45% contribution are more often considered in proactive based approaches with less attention towards VM scheduling which contribute 9.09%. From Fig. 7(b) it is evident that most of the reactive approaches in existing literature have been studied under task scheduling which amount to 51.85%, followed by VM scheduling which contribute to 25.93% and resource scheduling which contribute to 22.22% respectively. Figure 8 describes the percentage of research articles on cloud load balancing defining the algorithmic complexity. It is calculated that 80% of research articles did not considered algorithmic complexity in their work while only 20% define it in their work. It is analyzed from Fig. 9(a) that proactive approaches are always dynamic in nature while Fig. 9(b) depicts that most of the reactive approaches fall under dynamic state of algorithm which contribute to 68%, followed by static algorithm which contribute 20% and hybrid algorithm which represent 12%. It is evident from Fig. 10(a) that 60% of proactive approaches are multi-objective while 40% are single objective approaches. Likewise 56% of reactive approaches are multi-objective while 44% are single objective approaches as depicted in Fig. 10(b) . Figure 11 displays the testing environment on which a particular approach was run to evaluate the performance metrics. It is clear that CloudSim simulator is extensively used for conducting simulation experiment constituting 33.33% of experimental implementation followed by Cloud Analyst simulator with 19.44% of experimental implementation. C and C++, Matlab implementation of load balancing approaches amount to 11.11% each respectively while others constitute 19.44%. The real time implementation of cloud load balancing approaches is very less and constitutes only 5.56%. Figure 12 depicts the percentage of LB metrics in the existing approaches where response time, execution time, resource utilization, makespan, scalability and execution cost are most widely discussed each with 13.39%, 11.81%, 11.02%, 9.45%, 9.45% and 8.66% respectively.
Percentage based on scheduling trait (task scheduling, VM scheduling, and resource scheduling) in proactive and reactive approaches
Percentage of research articles designating algorithmic complexity
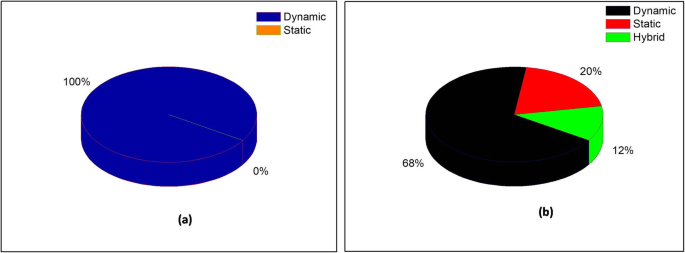
Percentage based on state of algorithm in proactive (dynamic and static)and reactive (dynamic, static, and hybrid) approaches
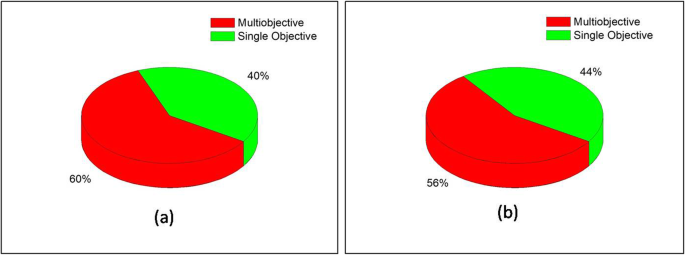
Percentage of multi-objective and single objective algorithms in proactive and reactive approaches
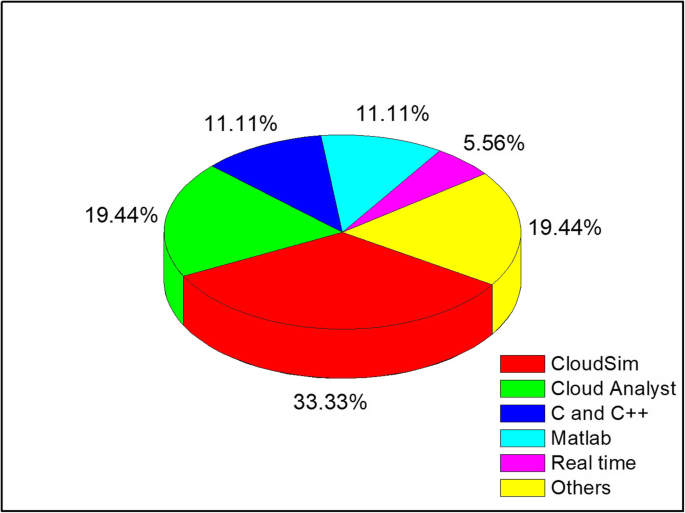
Experimental platforms for cloud load balancing approaches
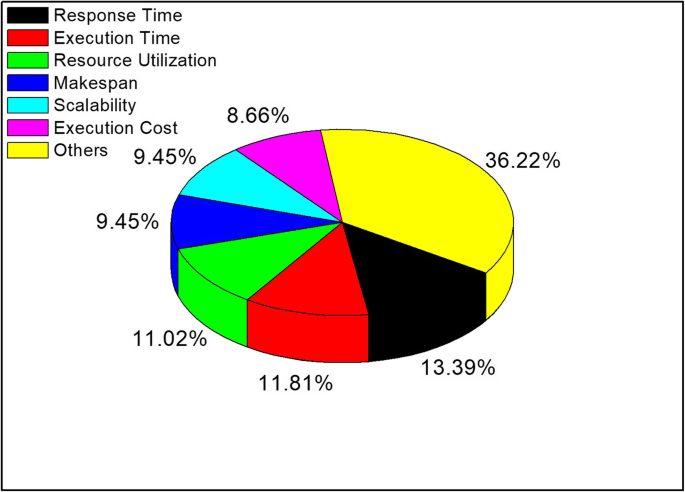
Percentage of LB metrics in Existing approaches
Discussion on open issues on load balancing in cloud computing
The review presented in this article addresses some important issues that had not been taken with good consideration in existing survey literature neither in technical literature and which the cloud load balancing demands rigorously. Thus, we discuss some open research in this section.
Complexity of an algorithm is a pivotal element in determining the performance of any load balancing algorithm. Out of 35 potential technical articles considered in this study, it is found that only 7 articles define the corresponding algorithmic complexity which amounts to 20% and also 28 articles does not define the algorithmic complexity which amounts to 80%. Therefore, it is observed that majority of the works does not include algorithmic complexity and hence for future researchers it is suggested that algorithm complexity should be made a benchmark for developing a new load balancing approach with improved practicality.
A reactive approach of load balancing always features migration in particular task migration. Migration of tasks always incurs some cost that is called as migration cost. From the study it is evident that less literature in cloud load balancing focuses on migration cost apart from Service Level Violations, Task Rejection ratio and power consumption. This can be considered as important direction for future researchers in development of reactive approaches with minimum migration cost.
Further, from the study carried out in this work, it is investigated that majority of the works primarily focus on certain metrics and avoids other main metrics. Out of 16 different metrics collected in this study it is revealed that most of existing works on cloud load balancing features 6 metrics as key parameters for evaluation that are response time (13.39%), execution time (11.81%), resource utilization (11.02%), makespan (9.45%), Scalability (9.45%) and execution cost (8.66%) respectively as depicted in Fig. 12 . while the remaining 10 metrics account to only 36.22% and they are Throughput (7.87%), Overhead (7.09%), Fault Tolerance (4.72%), Degree of balance (4.72%), Migration Time (3.93%), Power consumption (3.14%), Waiting time (2.36%), Task Rejection Ratio (1.50%), and Service Level Violation (0.78%). considering these metrics in future works is also one of the insights for future researchers.
Conclusion and future work
The work presents a comparative study on load balancing approaches in reviewed articles. The problem of load unbalancing in cloud computing was discussed along with driving factors that lead to this problem. An abstracted load balancing model was briefly discussed together with activities involved in load balancing process. A proper research methodology was followed in which the problem was studied in guidelines with Constructive Generic Framework (CGF) further reinforced by Systematic Literature Review (SLR) methodology. We framed a set of problem related questions and discussed them in the work. The data collected for this study had been gathered from five reputed potential databases that include IEEE Xplore digital library, Science Direct, ACM digital Library, Springer and Elsevier. The data search process was assisted by different tools and advanced filter options. The data was collected for the period from 2010 to June 2018. A multilevel taxonomy based classification was proposed in this work where the classification process is done on five criteria. The most important criteria used in this work is “Nature of Algorithm”. Based on this criteria we classified 35 articles into two broad categories- 10 of them are proactive and 25 of them are reactive in nature. The statistics showed that proactive approaches are 100% dynamic while reactive approaches need not be dynamic. We also generalized that all proactive approaches are dynamic but all dynamic approaches may not be proactive Also the study revealed that task scheduling had been given much importance both in proactive and reactive approaches contributing 45% and 51.85% respectively.
The challenges of the load balancing algorithms are explored in this work in order to suggest more efficient load balancing methods in future. Majority of the reviewed articles had not considered significant and fundamental QoS metrics for investigation. Some of the essential QoS metrics are not discussed in reviewed articles in full depth e.g. migration time, migration cost, power consumption, service level violation, task rejection ratio and degree of balance. Further our study revealed that algorithm complexity is not given much attention in determining the performance of load balancing algorithm and as such 80% of the works does not consider it for evaluation of performance. Also majority of existing load balancing approaches have been implemented on simulator platforms which overall constitute 94.44%. Real time implementation of load balancing is very less (5.56) and should be encouraged in future works.
From the review conducted during this research process, it is concluded that there are a lot of issues still open in load balancing process which can be bridged in future by applying an efficient and sophisticated load balancing algorithm most importantly along dimensions of additional QoS metrics and algorithm complexity evaluation. The survey also presents some algorithms in taxonomy which can guide the future researchers to deal with load unbalancing problem effectively like nature inspired algorithms, machine learning and mathematical derived algorithms (Markov chain, game theory based).
Availability of data and materials
The data has been gathered from research papers and articles that are mentioned in Table 1 , Table 2 , Table 3 and Table 4 .
Abbreviations
Infrastructure as a service
Software as a service
Platform as a service
Pay-as-you-go
National Institute of Standards and Technology
Virtual Machine
Cloud Service Provider
Cloud Service Consumer
Quality of Service
Service Level Agreement
Ant Lion optimizer
Constructive generic framework
Systematic literature review
Load Balancing
Physical Machine
Mobile adhoc networks
Virtual Private Cloud
Pradhan P, Behera PK, Ray BNB (2016) Modified round Robin algorithm for resource allocation in cloud computing. Proced Comp Sci 85:878–890
Article Google Scholar
Mishra SK, Sahoo B, Parida PP (2018) Load balancing in cloud computing: a big picture. J King Saud Univ Comp Infor Sci:1–32
Reddy VK, Rao BT, Reddy LSS (2011) Research issues in cloud computing. Glob J Comp Sci Technol 11(11):70–76
Google Scholar
Bohn RB, Messina J, Liu F, Tong J, Mao J (2011) NIST cloud computing reference architecture. In: Proceedings of IEEE 7th world congress on services (SERVICES’11), Washington, DC, USA, Jul. 2011, pp 594–596
Bokhari MU, Shallal QM, Tamandani YK (2016, March) Cloud computing service models: a comparative study. In: 3rd international conference on computing for sustainable global development (INDIACom), 16–18, March 2016, pp 890–895
Mahmood Z (2011, August) Cloud computing: characteristics and deployment approaches. In: 2011 IEEE 11th international conference on Computer and Information Technology (CIT), pp 121–126
Buyya R, Vecchiola C, Selvi ST (2013) Mastering cloud computing: foundations and applications programming. Morgan Kaufmann, USA, 2013
Chapter Google Scholar
Jain N, Choudhary S (2016, March) Overview of virtualization in cloud computing. In: Symposium on colossal data analysis and networking (CDAN), pp 1–4
Alouane M, El Bakkali H (2016, May) Virtualization in cloud computing: no hype vs HyperWall new approach. In: 2016 International Conference on Electrical and Information Technologies (ICEIT), pp 49–54
Rimal BP, Choi E, Lumb I (2009, August) A taxonomy and survey of cloud computing systems. In: Fifth international joint conference on INC, IMS and IDC, 2009. NCM’09, pp 44–51
Afzal S, Kavitha G (2018, December) Optimization of task migration cost in infrastructure cloud computing using IMDLB algorithm. In: 2018 International Conference on Circuits and Systems in Digital Enterprise Technology (ICCSDET), pp 1–6
Achar R, Thilagam PS, Soans N, Vikyath PV, Rao S, Vijeth AM (2013, December) Load balancing in cloud based on live migration of virtual machines. In: 2013 annual IEEE India Conference (INDICON), pp 1–5
Magalhães D, Calheiros RN, Buyya R, Gomes DG (2015) Workload modeling for resource usage analysis and simulation in cloud computing. Comp Elect Eng 47:69–81
Dam S, Mandal G, Dasgupta K, Dutta P (2015, February) Genetic algorithm and gravitational emulation based hybrid load balancing strategy in cloud computing. In: Proceedings of the 2015 third international conference on computer, communication, control and information technology (C3IT), pp 1–7
Dave A, Patel B, Bhatt G (2016, October) Load balancing in cloud computing using optimization techniques: a study. In: International Conference on Communication and Electronics Systems (ICCES), pp 1–6
Gupta H, Sahu K (2014) Honey bee behavior based load balancing of tasks in cloud computing. Int J Sci Res 3(6)
Mishra SK, Puthal D, Sahoo B, Jena SK, Obaidat MS (2017) An adaptive task allocation technique for green cloud computing. J Supercomp 405:1–16
Ibrahim AH, Faheem HEDM, Mahdy YB, Hedar AR (2016) Resource allocation algorithm for GPUs in a private cloud. Int J Cloud Comp 5(1–2):45–56
Jebalia M, Ben Letafa A, Hamdi M, Tabbane S (2015) An overview on coalitional game-theoretic approaches for resource allocation in cloud computing architectures. Int J Cloud Comp 4(1):63–77
Noshy M, Ibrahim A, Ali HA (2018) Optimization of live virtual machine migration in cloud computing: a survey and future directions. J Netw Comput Appl:1–10
Gkatzikis L, Koutsopoulos I (2013) Migrate or not? Exploiting dynamic task migration in mobile cloud computing systems. IEEE Wirel Commun 20(3):24–32
Jamshidi P, Ahmad A, Pahl C (2013) Cloud migration research: a systematic review. IEEE Trans Cloud Comp 1(2):142–157
Raviteja S, Atmakuri R, Vengaiah C (2017) A review on cloud computing migration and issues
Shamsinezhad E, Shahbahrami A, Hedayati A, Zadeh AK, Banirostam H (2013) Presentation methods for task migration in cloud computing by combination of Yu router and post-copy. Int J Comp Sci Iss 10(4):98
Ghomi EJ, Rahmani AM, Qader NN (2017) Load-balancing algorithms in cloud computing: a survey. J Netw Comput Appl 88:50–71
Milani AS, Navimipour NJ (2016) Load balancing mechanisms and techniques in the cloud environments: systematic literature review and future trends. J Netw Comput Appl 71:86–98
Kalra M, Singh S (2015) A review of metaheuristic scheduling techniques in cloud computing. Egypt Inform J 16(3):275–295
Mesbahi M, Rahmani AM (2016) Load balancing in cloud computing: a state of the art survey. Int J Mod Educ Comp Sci 8(3):64
Kanakala VR, Reddy VK, Karthik K (2015, March) Performance analysis of load balancing techniques in cloud computing environment. In: 2015 IEEE International Conference on Electrical, Computer and Communication Technologies (ICECCT), pp 1–6
Shah JM, Kotecha K, Pandya S, Choksi DB, Joshi N (2017, May) Load balancing in cloud computing: methodological survey on different types of algorithm. In: 2017 International Conference on Trends in Electronics and Informatics (ICEI), pp 100–107
Neghabi AA, Navimipour NJ, Hosseinzadeh M, Rezaee A (2018) Load balancing mechanisms in the software defined networks: a systematic and comprehensive review of the literature. IEEE Access 6:14159–14178
Afzal S, Kavitha G A taxonomic classification of load balancing metrics: a systematic review
Vacca JR (2009) Computer and information security handbook. Morgan Kauffman, Burlington, MA, p 208
Kitchenham B (2004) Procedures for performing systematic reviews. Keele, UK, Keele University, 33(2004), 1–26
Soltani Z, Navimipour NJ (2016) Customer relationship management mechanisms: a systematic review of the state of the art literature and recommendations for future research. Comput Hum Behav 61:667–688
Pandey K, Swaroop A (2011) A comprehensive performance analysis of proactive, reactive and hybrid manets routing protocols. arXiv preprint arXiv:1112.5703
Polepally V, Chatrapati KS (2017) Dragonfly optimization and constraint measure-based load balancing in cloud computing. Cluster Comp:1–13
Xiao Z, Tong Z, Li K, Li K (2017) Learning non-cooperative game for load balancing under self-interested distributed environment. Appl Soft Comput 52:376–386
Adhikari M, Amgoth T (2018) Heuristic-based load-balancing algorithm for IaaS cloud. Futur Gener Comput Syst 81:156–165
Kumar M, Dubey K, Sharma SC (2018) Elastic and flexible deadline constraint load balancing algorithm for cloud computing. Proced Comp Sci 125:717–724
Borovskiy V, Wust J, Schwarz C, Koch W, Zeier A (2011) A linear programming approach for optimizing workload distribution in a cloud. Cloud Comp:127–132
Krishna PV (2013) Honey bee behavior inspired load balancing of tasks in cloud computing environments. Appl Soft Comput 13(5):2292–2303
Li K, Xu G, Zhao G, Dong Y, Wang D (2011, August). Cloud task scheduling based on load balancing ant colony optimization. In: 2011 sixth annual ChinaGrid conference, pp. 3–9
Singh A, Juneja D, Malhotra M (2015) Autonomous agent based load balancing algorithm in cloud computing. Proced Comp Sci 45:832–841
Lavanya M, Vaithiyanathan V (2015) Load prediction algorithm for dynamic resource allocation. Indian J Sci Technol 8(35)
Chen SL, Chen YY, Kuo SH (2017) CLB: a novel load balancing architecture and algorithm for cloud services. Comp Elect Eng 58:154–160
Ashouraei M, Khezr SN, Benlamri R, Navimipour NJ (2018, August) A new SLA-aware load balancing method in the cloud using an improved parallel task scheduling algorithm. In: 2018 IEEE 6th international conference on future internet of things and cloud (FiCloud), pp 71–76
Kumar M, Sharma SC (2017) Dynamic load balancing algorithm for balancing the workload among virtual machine in cloud computing. Proced Comp Sci 115(C):322–329
Rajput SS, Kushwah VS (2016, December) A genetic based improved load balanced min-min task scheduling algorithm for load balancing in cloud computing. In: 2016 8th international conference on Computational Intelligence and Communication Networks (CICN), pp 677–681
Tang L, Li Z, Ren P, Pan J, Lu Z, Su J, Meng Z (2017) Online and offline based load balance algorithm in cloud computing. Knowl-Based Syst 138:91–104
Ramezani F, Lu J, Hussain FK (2014) Task-based system load balancing in cloud computing using particle swarm optimization. Int J Parallel Prog 42(5):739–754
Vanitha M, Marikkannu P (2017) Effective resource utilization in cloud environment through a dynamic well-organized load balancing algorithm for virtual machines. Comp Elec Eng 57:199–208
Dasgupta K, Mandal B, Dutta P, Mandal JK, Dam S (2013) A genetic algorithm (ga) based load balancing strategy for cloud computing. Proced Technol 10:340–347
Cho KM, Tsai PW, Tsai CW, Yang CS (2015) A hybrid meta-heuristic algorithm for VM scheduling with load balancing in cloud computing. Neural Comput & Applic 26(6):1297–1309
Dam S, Mandal G, Dasgupta K, Dutta P (2015, February) Genetic algorithm and gravitational emulation based hybrid load balancing strategy in cloud computing. In: 2015 third international conference on computer, communication, control and information technology (C3IT), pp 1–7
Vasudevan SK, Anandaram S, Menon AJ, Aravinth A (2016) A novel improved honey bee based load balancing technique in cloud computing environment. Asian J Infor Technol 15(9):1425–1430
Kapur R (2015, August) A workload balanced approach for resource scheduling in cloud computing. In: 2015 eighth international conference on contemporary computing (IC3), pp 36–41
Panwar R, Mallick B (2015, October) Load balancing in cloud computing using dynamic load management algorithm. In: 2015 International Conference on Green Computing and Internet of Things (ICGCIoT), pp 773–778
Sharma S, Luhach AK, Abdhullah SS (2016) An optimal load balancing technique for cloud computing environment using bat algorithm. Indian J Sci Technol 9(28)
Ajit M, Vidya G (2013, July) VM level load balancing in cloud environment. In: 2013 fourth International Conference on Computing,Communications and Networking Technologies (ICCCNT), pp 1–5
Mondal B, Choudhury A (2015) Simulated annealing (SA) based load balancing strategy for cloud computing. Int J Comp Sci Info Technol 6(4):3307–3312
Pasha N, Agarwal A, Rastogi R (2014) Round robin approach for VM load balancing algorithm in cloud computing environment. Int J Adv Res Comp Sci Soft Eng 4(5):34–39
Gulati A, Chopra RK (2013) Dynamic round robin for load balancing in a cloud computing. IJCSMC 2(6):274–278
Galloway JM, Smith KL, Vrbsky SS (2011, October) Power aware load balancing for cloud computing. In: proceedings of the world congress on engineering and computer science, Vol. 1, pp 19–21
Garg S, Gupta DV, Dwivedi RK (2016, November) Enhanced active monitoring load balancing algorithm for virtual machines in cloud computing. In: International conference on System Modeling & Advancement in Research Trends (SMART), pp 339–344
Tripathi AM, Singh S (2018) PMAMA: priority-based modified active monitoring load balancing algorithm in cloud computing. J Adv Res Dynam Cont Syst:809–823
Singh AN, Prakash S (2018) WAMLB: weighted active monitoring load balancing in cloud computing. In: Big data analytics. Springer, Singapore, pp 677–685
Patel G, Mehta R, Bhoi U (2015) Enhanced load balanced min-min algorithm for static meta task scheduling in cloud computing. Proced Comp Sci 57:545–553
Chen H, Wang F, Helian N, Akanmu G (2013, February) User-priority guided min-min scheduling algorithm for load balancing in cloud computing. In: 2013 national conference on parallel computing technologies (PARCOMPTECH), pp 1–8
Mathur S, Larji AA, Goyal A (2017, June) Static load balancing using ASA max-min algorithm. Int J Res Appl Sci Eng Technol
Devi DC, Uthariaraj VR (2016) Load balancing in cloud computing environment using improved weighted round robin algorithm for non-preemptive dependent tasks. Sci World J
Download references
Acknowledgements
The authors are grateful to the editor and anonymous referees for their valuable comments and suggestions. Only the authors are responsible for the views expressed and mistakes made.
Author information
Authors and affiliations.
Department of Information Technology, B S Abdur Rahman Crescent Institute of Science and Technology, Chennai, 600048, India
Shahbaz Afzal & G. Kavitha
You can also search for this author in PubMed Google Scholar
Contributions
Design the study: SA. Collected the data from different sources: SA and GK. Analysis and interpretation of data: SA. Drafting of Manuscript: GK. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Shahbaz Afzal .
Ethics declarations
Competing interests.
The authors declare that there is no competing interest.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License ( http://creativecommons.org/licenses/by/4.0/ ), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
Reprints and permissions
About this article
Cite this article.
Afzal, S., Kavitha, G. Load balancing in cloud computing – A hierarchical taxonomical classification. J Cloud Comp 8 , 22 (2019). https://doi.org/10.1186/s13677-019-0146-7
Download citation
Received : 21 January 2019
Accepted : 25 November 2019
Published : 23 December 2019
DOI : https://doi.org/10.1186/s13677-019-0146-7
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cloud computing
- Classification
- Cloud service consumer
- Cloud service provider
- Quality of service
- Load unbalancing
- Load balancing
cloud computing Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
Simulation and performance assessment of a modified throttled load balancing algorithm in cloud computing environment
<span lang="EN-US">Load balancing is crucial to ensure scalability, reliability, minimize response time, and processing time and maximize resource utilization in cloud computing. However, the load fluctuation accompanied with the distribution of a huge number of requests among a set of virtual machines (VMs) is challenging and needs effective and practical load balancers. In this work, a two listed throttled load balancer (TLT-LB) algorithm is proposed and further simulated using the CloudAnalyst simulator. The TLT-LB algorithm is based on the modification of the conventional TLB algorithm to improve the distribution of the tasks between different VMs. The performance of the TLT-LB algorithm compared to the TLB, round robin (RR), and active monitoring load balancer (AMLB) algorithms has been evaluated using two different configurations. Interestingly, the TLT-LB significantly balances the load between the VMs by reducing the loading gap between the heaviest loaded and the lightest loaded VMs to be 6.45% compared to 68.55% for the TLB and AMLB algorithms. Furthermore, the TLT-LB algorithm considerably reduces the average response time and processing time compared to the TLB, RR, and AMLB algorithms.</span>
An improved forensic-by-design framework for cloud computing with systems engineering standard compliance
Reliability of trust management systems in cloud computing.
Cloud computing is an innovation that conveys administrations like programming, stage, and framework over the web. This computing structure is wide spread and dynamic, which chips away at the compensation per-utilize model and supports virtualization. Distributed computing is expanding quickly among purchasers and has many organizations that offer types of assistance through the web. It gives an adaptable and on-request administration yet at the same time has different security dangers. Its dynamic nature makes it tweaked according to client and supplier’s necessities, subsequently making it an outstanding benefit of distributed computing. However, then again, this additionally makes trust issues and or issues like security, protection, personality, and legitimacy. In this way, the huge test in the cloud climate is selecting a perfect organization. For this, the trust component assumes a critical part, in view of the assessment of QoS and Feedback rating. Nonetheless, different difficulties are as yet present in the trust the board framework for observing and assessing the QoS. This paper talks about the current obstructions present in the trust framework. The objective of this paper is to audit the available trust models. The issues like insufficient trust between the supplier and client have made issues in information sharing likewise tended to here. Besides, it lays the limits and their enhancements to help specialists who mean to investigate this point.
Cloud Computing Adoption in the Construction Industry of Singapore: Drivers, Challenges, and Strategies
An extensive review of web-based multi granularity service composition.
The paper reviews the efforts to compose SOAP, non-SOAP and non-web services. Traditionally efforts were made for composite SOAP services, however, these efforts did not include the RESTful and non-web services. A SOAP service uses structured exchange methodology for dealing with web services while a non-SOAP follows different approach. The research paper reviews the invoking and composing a combination of SOAP, non-SOAP, and non-web services into a composite process to execute complex tasks on various devices. It also shows the systematic integration of the SOAP, non-SOAP and non-web services describing the composition of heterogeneous services than the ones conventionally used from the perspective of resource consumption. The paper further compares and reviews different layout model for the discovery of services, selection of services and composition of services in Cloud computing. Recent research trends in service composition are identified and then research about microservices are evaluated and shown in the form of table and graphs.
Integrated Blockchain and Cloud Computing Systems: A Systematic Survey, Solutions, and Challenges
Cloud computing is a network model of on-demand access for sharing configurable computing resource pools. Compared with conventional service architectures, cloud computing introduces new security challenges in secure service management and control, privacy protection, data integrity protection in distributed databases, data backup, and synchronization. Blockchain can be leveraged to address these challenges, partly due to the underlying characteristics such as transparency, traceability, decentralization, security, immutability, and automation. We present a comprehensive survey of how blockchain is applied to provide security services in the cloud computing model and we analyze the research trends of blockchain-related techniques in current cloud computing models. During the reviewing, we also briefly investigate how cloud computing can affect blockchain, especially about the performance improvements that cloud computing can provide for the blockchain. Our contributions include the following: (i) summarizing the possible architectures and models of the integration of blockchain and cloud computing and the roles of cloud computing in blockchain; (ii) classifying and discussing recent, relevant works based on different blockchain-based security services in the cloud computing model; (iii) simply investigating what improvements cloud computing can provide for the blockchain; (iv) introducing the current development status of the industry/major cloud providers in the direction of combining cloud and blockchain; (v) analyzing the main barriers and challenges of integrated blockchain and cloud computing systems; and (vi) providing recommendations for future research and improvement on the integration of blockchain and cloud systems.
Cloud Computing and Undergraduate Researches in Universities in Enugu State: Implication for Skills Demand
Cloud building block chip for creating fpga and asic clouds.
Hardware-accelerated cloud computing systems based on FPGA chips (FPGA cloud) or ASIC chips (ASIC cloud) have emerged as a new technology trend for power-efficient acceleration of various software applications. However, the operating systems and hypervisors currently used in cloud computing will lead to power, performance, and scalability problems in an exascale cloud computing environment. Consequently, the present study proposes a parallel hardware hypervisor system that is implemented entirely in special-purpose hardware, and that virtualizes application-specific multi-chip supercomputers, to enable virtual supercomputers to share available FPGA and ASIC resources in a cloud system. In addition to the virtualization of multi-chip supercomputers, the system’s other unique features include simultaneous migration of multiple communicating hardware tasks, and on-demand increase or decrease of hardware resources allocated to a virtual supercomputer. Partitioning the flat hardware design of the proposed hypervisor system into multiple partitions and applying the chip unioning technique to its partitions, the present study introduces a cloud building block chip that can be used to create FPGA or ASIC clouds as well. Single-chip and multi-chip verification studies have been done to verify the functional correctness of the hypervisor system, which consumes only a fraction of (10%) hardware resources.
Study On Social Network Recommendation Service Method Based On Mobile Cloud Computing
Cloud-based network virtualization in iot with openstack.
In Cloud computing deployments, specifically in the Infrastructure-as-a-Service (IaaS) model, networking is one of the core enabling facilities provided for the users. The IaaS approach ensures significant flexibility and manageability, since the networking resources and topologies are entirely under users’ control. In this context, considerable efforts have been devoted to promoting the Cloud paradigm as a suitable solution for managing IoT environments. Deep and genuine integration between the two ecosystems, Cloud and IoT, may only be attainable at the IaaS level. In light of extending the IoT domain capabilities’ with Cloud-based mechanisms akin to the IaaS Cloud model, network virtualization is a fundamental enabler of infrastructure-oriented IoT deployments. Indeed, an IoT deployment without networking resilience and adaptability makes it unsuitable to meet user-level demands and services’ requirements. Such a limitation makes the IoT-based services adopted in very specific and statically defined scenarios, thus leading to limited plurality and diversity of use cases. This article presents a Cloud-based approach for network virtualization in an IoT context using the de-facto standard IaaS middleware, OpenStack, and its networking subsystem, Neutron. OpenStack is being extended to enable the instantiation of virtual/overlay networks between Cloud-based instances (e.g., virtual machines, containers, and bare metal servers) and/or geographically distributed IoT nodes deployed at the network edge.
Export Citation Format
Share document.

IMAGES
VIDEO
COMMENTS
Thus, this paper provides a summative meta-analysis of cloud computing research from 2009 to 2015. With the aim of taking stock and providing insights into theoretical frameworks and models, research methodologies, geographical focus, and trends of cloud computing research over these years. The rest of the paper is organized as follows.
review is thought to inspire enterprises and managers that would like to use cloud computing in. terms of the scope, solution methods, factors, dimensions, and the results achieved in a holistic ...
Additionally, assist cloud computing researchers in making intelligent decisions and identifying research gaps that require further investigation. The remaining structure of the paper is as follows: Section 2 begins with a brief introduction to review methodology, followed by the research questions, article selection procedure, and ...
We also explore the cybersecurity elements associated with cloud computing, focusing on intrusion detection and prevention and understanding how that can be applied in the cloud. Finally, we investigate the future research directions for cloud computing and expand this paper into further articles with experiments and results.
Cloud computing is growing daily, providing a vibrant technical environment where innovative solutions and services can be created. The Cloud promises the capability for cheap and flexible services for end-users and allows small organizations and individuals to host and offer world-scale services, themselves.
The paper also gives a concise description of Cloud Computing concepts and technologies. It starts with a brief history about cloud ... (Moura and Serrão 2015). Table II. Cloud Computing Historical Evolution from 1960s until 2011 ... and even healthcare (Griebel, et al. 2015) . There are also important research areas for Future Networks with a ...
Cloud computing is an evolution of information technology and a dominant business model for delivering IT resources. With cloud computing, individuals and organizations can gain on-demand network access to a shared pool of managed and scalable IT resources, such as servers, storage, and applications. Recently, academics as well as practitioners ...
The Journal of Cloud Computing, Advances, Systems and Applications (JoCCASA) has been launched to offer a high quality journal geared entirely towards the research that will offer up future generations of Clouds. The journal publishes research that addresses the entire Cloud stack, and as relates Clouds to wider paradigms and topics.
Profile Information. Communications Preferences. Profession and Education. Technical Interests. Need Help? US & Canada:+1 800 678 4333. Worldwide: +1 732 981 0060. Contact & Support. About IEEE Xplore.
Cloud computing has become a widely exploited research area in academia and industry. Cloud computing benefits both cloud services providers (CSPs) and consumers. The security challenges associated with cloud computing have been widely studied in the literature. This systematic literature review (SLR) is aimed to review the existing research studies on cloud computing security, threats, and ...
The authors in presented a white paper based on published research papers during 2015-2017. They outlined the serverless definition alongside its advantages and disadvantages. ... we applied backward snowballing to increase the set of relevant papers to serverless cloud computing. In this phase, we could add 21 more papers to our list of ...
Metrics. Since 2012, the Journal of Cloud Computing has been promoting research and technology development related to Cloud Computing, as an elastic framework for provisioning complex infrastructure services on-demand, including service models such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service ...
computing. Thus, this paper provides a summative meta-analysis of cloud computing research from 2009 to 2015. With the aim of taking stock and providing insights into theoretical frameworks and models, research methodologies, geographical focus, and trends of cloud computing research over these years. The rest of the paper is organized as ...
7.1. Challenges. Via analysis and contrast, we observe that cloud computing security protection work has achieved satisfactory research results. However, many problems remain, which prompt the consideration of a variety of security factors and continuous improvements in defense technology and security strategies. 1.
Well-known cloud services in health care are Microsoft's Health Vault, a cloud-based platform to store and maintain health and fitness data [ 108] or the discontinued of Google Health service [ 109 ]. Of course, cloud computing is a hot topic and new papers are constantly published.
A COMPREHENSIVE STUDY ON CLOUD. COMPUTING PARADIGM. Ab Rashid Dar 1, Dr. D. Ravindran 2. 1,2 Department of Computer Science, St. Joseph's College. (Autonomous), Tiruchirappalli Tamil Nadu, (Indi ...
Gartner (20 19) forecasted that there will b e a 17 percent growth of cloud computing in 2020, which totals to 266.4. billion USD in m arket value from 227.8 billion USD in 2019. Sub sequently ...
The rest of the paper is organized into different sections as follows: Sect. 2 presents a brief background of cloud computing and its services. Section 3 discusses a brief summary of literature review. Section 4 presents research issues, challenges, and future directions. The conclusion is shown in Sect. 5 while references are mentioned at the last.
The authors pointed out that from 2010 to 2015 there is a momentous rise in research papers on the scope of load balancing that follows a positive exponential curve and in our work find it more increasing in 2016, 2017 and 2018. ... (2015, August) A workload balanced approach for resource scheduling in cloud computing. In: 2015 eighth ...
This research paper outlines what cloud computing is, the various cloud models and the main security risks and issues that are currently present within the cloud computing industry and offers best practices to service providers as well as enterprises hoping to leverage cloud service to improve their bottom line in this severe economic climate.
The paper further compares and reviews different layout model for the discovery of services, selection of services and composition of services in Cloud computing. Recent research trends in service composition are identified and then research about microservices are evaluated and shown in the form of table and graphs. Download Full-text.
Small, Medium and Micro- sized Enterprises (SMMEs) in particular should explore and build their organisations around cloud computing services to realise greater efficiency and effectiveness within their business functions and processes [2] (Kumalo & van der Poll , 2015). Cloud adoption is the affordable choice, as it offers greater flexibility ...
The research emphasizes the importance of developing a comprehensive risk management plan to mitigate the risks associated with cloud computing for businesses and organizations. Furthermore, it discusses the challenges that cloud computing poses, including issues with interoperability, portability, and performance.
Student. , M.Sc. I.T., I.C.S. College, Khed, Ratnagri. Abstract: Cloud Computing has come of age later Amazons introduce the first of its kind of cloud services in2006. It is. particularly ...
Cloud-native virtualization technology combines virtualization technology with cloud-native computing to provide a more efficient, flexible, and scalable cloud computing environment. In the process of analysis and research in the field of bioinformatics, it is usually necessary to deal with large-scale data sets and complex computing tasks, and the demand for computing power throughout the ...