Operating System Design/Case studies
The goal of this book is to discuss the different issues involved in operating system design, the different strategies that have been tried and to provide concrete examples where possible. Given the number of open-source operating systems available, specific implementations will be used as examples where possible.
- 1 Example Operating Systems
- 2 Example filesystems
- 3 Case Study Areas
- 4 Further reading

Example Operating Systems [ edit | edit source ]
Naturally, open source operating systems lend themselves to teaching more than proprietary operating systems. The source code of all the following operating systems is available free of charge online:
- Net/Free/OpenBSD
While the following operating systems are closed source, enough is known about their implementation that they can all be used as specific examples of approaches to various OS design issues and tasks.
- Microsoft Windows 9x
Example filesystems [ edit | edit source ]
Case study areas [ edit | edit source ].
The following areas of operating system design can all be illustrated with specific examples from real operating systems. In some cases different approaches to the same task can be seen within one OS. For example, many operating systems support multiple file system types.
- Loading the operating system
- Initialising the operating system for use
- Managing tasks (processes)
- Managing memory
- File systems and storage management
- User interfaces
For example, in the "Managing tasks" section we might use the example of task management in a single tasking operating system like DOS, as well as some of the different scheduling algorithms that have been used in various multitasking operating systems.
The case study can include comparative analysis about any concept of different operating systems or comparison between the different versions of same operating systems. It can include the total functionality of the operating system given.
Further reading [ edit | edit source ]
- Embedded Systems/Common RTOS gives yet more examples of real-time operating systems, many of them open-source.
- A Neutral Look at Operating Systems gives yet more examples of operating systems, many of them proprietary.
Previous : Introduction — Next : History
- Book:Operating System Design
Navigation menu
Subscribe to the PwC Newsletter
Join the community, edit social preview.

Add a new code entry for this paper
Remove a code repository from this paper, mark the official implementation from paper authors, add a new evaluation result row, remove a task, add a method, remove a method, edit datasets, android os case study.
19 Apr 2021 · Mayank Goel , Gourav Singal · Edit social preview
Android is a mobile operating system based on a modified version of the Linux kernel and other open source software, designed primarily for touchscreen mobile devices such as smartphones and tablets. It is an operating system for low powered devices that run on battery and are full of hardware like Global Positioning System (GPS) receivers, cameras, light and orientation sensors, Wi-Fi and LTE (4G telephony) connectivity and a touch screen. Like all operating systems, Android enables applications to make use of the hardware features through abstraction and provide a defined environment for applications. The study includes following topic: Background And History Android Architecture Kernel And StartUp Process Process Management Deadlock CPU Scheduling Memory Management Storage Management I/O Battery Optimization
Code Edit Add Remove Mark official
Datasets edit.
INTRODUCTION
Operating systems, lecture 16: case study: unix, chris staff dept. of computer science and artificial intelligence university of malta, next lecture: introduction to distributed operating systems, lecture outline, aims and objectives, the processing environment, the file system, process management, memory management, next lecture..., introduction to distributed operating systems.

Case Studies of Popular Operating Systems
Introduction.
Operating systems (OS) are the backbone of any computer or computing device as they manage computer hardware and software resources to provide a user-friendly environment. There are numerous operating systems available today, but some have gained immense popularity due to their performance, features, and user base. In this article, we will delve into case studies of two widely used operating systems: UNIX and Windows.
UNIX, developed in the late 1960s, is a powerful and versatile operating system known for its stability, security, and scalability. It has greatly influenced the development of operating systems, shaping modern computing as we know it. Here are a few key case studies highlighting the significance of UNIX.
Case Study 1: The Unix Time-Sharing System
The Unix Time-Sharing System, developed by Ken Thompson and Dennis Ritchie at Bell Laboratories, is considered one of the first successful implementations of a multi-user operating system. Its introduction revolutionized the way computers were used, enabling simultaneous access to a shared mainframe by multiple users. This development significantly contributed to the growth of computer systems in academic and research settings.
Case Study 2: The Linux Kernel
The Linux kernel, initially developed by Linus Torvalds in 1991, is based on the UNIX operating system. It is an open-source project that has provided a fertile ground for collaboration and innovation. Linux offers a high degree of stability, security, and adaptability, making it the foundation for a wide range of systems, from embedded devices to supercomputers. Its success showcases the effectiveness of open-source development and the power of community-driven software.
Windows, developed by Microsoft, dominates the consumer operating system market with its user-friendly interface and broad software compatibility. It has evolved over time to cater to the needs of various devices and industries. Let's explore a couple of case studies that exhibit the impact of Windows on the computing landscape.
Case Study 1: Windows 95
Windows 95, released in 1995, marked a significant turning point in the evolution of Microsoft's operating systems. It introduced a more intuitive user interface with the introduction of the Start button and taskbar. Windows 95 also improved system stability, enhanced multimedia capabilities, and provided better support for the emerging internet. This version of Windows played a critical role in popularizing personal computers among general users.
Case Study 2: Windows 10
Windows 10, released in 2015, represents the latest iteration of the Windows operating system. Microsoft aimed to create a unified platform that works seamlessly across different devices, including desktops, laptops, tablets, and smartphones. Windows 10 introduced numerous features like Cortana (a digital assistant), the Microsoft Store, and the Edge web browser. Its consistent updates and focus on security have made it one of the most secure Windows versions to date.
UNIX and Windows are two well-known operating systems that have shaped the modern computing landscape. UNIX has influenced the development of multi-user systems and community-driven open-source projects like Linux. Windows, on the other hand, has focused on providing user-friendly interfaces and broad software compatibility.
These case studies showcase the impact and evolution of these popular operating systems and how they have addressed the needs of various industries and user bases over time. Both UNIX and Windows continue to play vital roles in the ever-changing world of technology, meeting the demands of modern computing environments.
noob to master © copyleft
We use cookies to enhance our website for you. Proceed if you agree to this policy or learn more about it.
- Essay Database >
- Essays Samples >
- Essay Types >
- Case Study Example
Operating System Case Studies Samples For Students
42 samples of this type
WowEssays.com paper writer service proudly presents to you a free database of Operating System Case Studies meant to help struggling students deal with their writing challenges. In a practical sense, each Operating System Case Study sample presented here may be a pilot that walks you through the essential phases of the writing process and showcases how to develop an academic work that hits the mark. Besides, if you need more visionary assistance, these examples could give you a nudge toward an original Operating System Case Study topic or encourage a novice approach to a banal issue.
In case this is not enough to slake the thirst for efficient writing help, you can request personalized assistance in the form of a model Case Study on Operating System crafted by an expert from scratch and tailored to your particular requirements. Be it a simple 2-page paper or a profound, extended piece, our writers specialized in Operating System and related topics will submit it within the pre-set period. Buy cheap essays or research papers now!
Good Software For A New Company Case Study Example
Computer purchase feedback case studies examples, news analysis case study examples.
Don't waste your time searching for a sample.
Get your case study done by professional writers!
Just from $10/page
Case Study On Operating Systems
Example of web server hardware and software case study, web server hardware and software, ubuntu 15.04 linux implementation proposal case study.
Ubuntu 15.04 Linux Implementation Proposal.
Introduction:
Supporting os and nos case study, good case study about internet service management, internet service management, apple case study example, it auditing for dalton, walton & carlton inc. - it infrastructure case study, auditing windows operating systems, what are the economic considerations of information security and its management case study examples.
In every economic undertaking, one has to consider the security perils associated with his undertaking before realizing the expected utility. Since information is a vital component that determines success of any economic activity, systems keeping, managing and disseminating such information have to be safeguarded in order to protect the information. During this process, several factors are considered:
Free Case Study On Google Today And In The Future
Q1 four main products of google, example of case study on how to use the database, introduction, web servers usually require server-side scripting engines these scripts are some case study, q11. list and discuss 5 areas where threats to data security may occur., expertly crafted case study on security threats on mobile devices, good how to evaluate mergers and acquisitions: microsoft acquisition of nokia devices case study example, 1-strategic rationale: what are the primary reasons for the acquisition, comparison of samsung and blackberrys mobile phone department case studies example, introduction: issue identification, good causes and effects of laptop failures using failure mode and effect analysis case study example.
Computers have been embraced by most people due to their benefits like speed of work, a complex storage area hence space saving, and the accuracy of the data and information. Nevertheless, laptops are prone to some failures which can have adverse effects on the organizations and individuals who solely rely on it (Liu, Ashok 165). The failure mode of laptops and the effects they have are all diverse in nature since they are different and affect different soft wares and hard wares in the laptop.
Failure mode
Case study on apple, google and microsoft – business models and areas of strength, compare the business models and areas of strength of apple, google and microsoft, samsung: case study example, how samsung has moved from being a copy cat to a leading brand, example of definitions memo case study, free case study about apple case study, swot analysis – apple inc. case studies example.
Apple Inc. is an American company, headquartered in Cupertino, California, and was founded in the year 1976 by Steve Jobs, Steve Wozniak and Ronald Wayne. The company produces hardware and software products including smartphones, personal computers, tablet computers, media players, iCloud and iOS operating systems. The current paper is aimed to enlighten the SWOT analysis of the company in order to incorporate the self-assessment to fit within the organization.
Liferay: Case Study Case Studies Example
Liferay development model vs closed source development model, free strategic analysis of nokia phones case study sample, leadership, strategy and innovation google 3 case study samples, the clarion school for boys, inc. milwaukee division: making information systems case study examples, company profile, blackberry company analysis case study example, risk management study case study sample, case study on is cyber warfare a serious problem why or why not, chapter 8, pg. 306: stuxnet and the changing face of cyberwarfare, case study on strategic management: apple inc.
<Student’s name> <University>
Strategic Management is a function of control, extended to long-term goals and actions of the company. Strategy Formulation (modus operandi) and its precise tools are the core of governance and an important sign of good management of the company. Strategic management is a development and implementation of actions leading to long-term excess of the level of effectiveness of the company above the competition.
Strategy - the image of organizational actions and management approaches used to achieve organizational goals and objectives.
Case study on why the tablet has destroyed the pc, apple target case study sample, case study on googles strategy, strategic operations management case study example, free case study on external analysis, microsoft corporation external analysis case study examples, more information about affiliation, research grants, conflict of interest and how to contact., free case study on google strategic management, microsoft sustainability efforts case study sample, free case study on computer security, free case study on computers configurations, case study on eric schmidt's gang of four: google, apple, amazon, and facebook.
Eric Schmidt, the current Executive Chairman of internet giant Google said that today’s technological landscape is being ruled by the four horsemen, that being Google, Facebook, Apple and Amazon. These four companies are growing at unprecedented levels, sometimes competing and sometimes cooperating with each other, in different and distinct platforms. Google corners the search engine field, Facebook the social identity field, Apple the technical consumer hardware field and Amazon the e-commerce field.
Password recovery email has been sent to [email protected]
Use your new password to log in
You are not register!
By clicking Register, you agree to our Terms of Service and that you have read our Privacy Policy .
Now you can download documents directly to your device!
Check your email! An email with your password has already been sent to you! Now you can download documents directly to your device.
or Use the QR code to Save this Paper to Your Phone
The sample is NOT original!
Short on a deadline?
Don't waste time. Get help with 11% off using code - GETWOWED
No, thanks! I'm fine with missing my deadline

- Most Popular
- Explore all categories
the linux operating system (a case study)
- The Linux Operating System (A Case Study)
Upload: gajesh-bhat
Post on 11-Apr-2017
Embed Size (px): 344 x 292 429 x 357 514 x 422 599 x 487

THE LINUX OPERATING SYSTEMA Case Study

THE POWER OF OPEN SOURCE IS THE POWER
OF PEOPLEPhilippe Kahn

WHAT IS LINUX ?
➤ According to wikipedia Linux is a Unix-like and mostly POSIX-compliant computer operating system ‘assembled’ under the model of free and open-source software development and distribution.
➤ In Simple words Linux is a Kernel that is assembled with free software components(Not a Necessary Condition)to form Linux Based Operating Systems. Eg: Gnu/Linux ,Android.
➤ The ‘Kernel’ is a computer program that constitutes the central core of a computer's operating system.
➤ Every operating system has a Kernel.

Source : The Linux Gamer
What is Linux ? (Video)

HISTORY OF LINUX
➤ Linux was Developed by a person named ‘Linus Torvalds’ In 1991, while attending the University of Helsinki,Finland.
➤ He became curious about operating systems and was frustrated by the licensing of MINIX OS, which at the time limited it to educational use only. So he began to work on his own operating system kernel, which eventually became the Linux kernel.
Linus Torvalds. Principal author of the Linux kernel

THE PHILOSOPHYBe the change that you wish
to see in the world.

THE LINUX PHILOSOPHY
➤ Linux is based on the Principle’s of Free Software and Open Source.
➤ Free Software is a Software that respects users freedom.
➤ Free Software need not be free or gratis in terms of price. It only means Freedom to Run,Modify,Redistribute the source code as one wishes.
➤ Free Software concept was Introduced by the ‘Free Software Foundation’ and the ‘GNU Project’ founded in 1985 by Richard Stallman.
➤ Most Prominent Free and Open Source software’s today are Under ‘GNU GPL’ licence created by the Free Software Foundation and GNU Project.

➤ Open-source software (OSS) is computer software with its source code made available with a license in which the copyright holder provides the rights to study, change, and distribute the software to anyone and for any purpose.Open-source software may be developed in a collaborative public manner.
➤ Open Source software is a more or less a technical term used in the Industry due to the model followed called “Open Source Development Model”
➤ Open Source and Proprietary Software can co-exist in a System together. This is the main difference between Free Software and Open Source.
➤ Famous Examples of Open Sources Software are Mozilla Firefox,Thunderbird,Eclipse etc..

THE DESIGNNecessity is the mother of

➤ A Linux-based system is a modular Unix-like operating system, deriving much of its basic design from principles established in Unix during the 1970s and 1980s.
➤ Linux is ‘Monolithic’ in Nature.
➤ A monolithic kernel is an operating system architecture where the entire operating system is working in kernel space and is alone in supervisor mode.
➤ Here the Kernel controls and coordinates the entire system and its resources.
➤ A set of primitives or system calls implement all operating system services such as process management, concurrency, and memory management. Device drivers can be added to the kernel as modules.
➤ Linux is Primarily written in Assembly language and C.
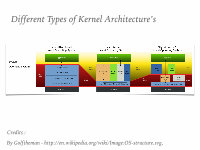
By Golftheman - http://en.wikipedia.org/wiki/Image:OS-structure.svg,
Different Types of Kernel Architecture’s

➤ Linux Uses ‘GNU Userland’ which Provides the most Common implementations of C Library.
➤ It also makes use of CLI Shell and many of the common Unix tools which carry out many basic operating system tasks.
➤ The graphical user interface (or GUI) used by most Linux systems is built on top of an implementation of the’ X Window System’.
➤ Most Recent and advanced development in terms of GUI is the development of ‘Wayland’ a new display server which community believes will replace the X Window System in the near future.

➤ The Linux Uses many other tools and components from various free and open source projects.
➤ Components like Boot-loader,init programs,Software Libraries and other toolkits are used from a variety of projects.
➤ GRUB is a famous Boot-loader in the Linux Space.
➤ Primarily Linux was designed to run on Desktop Computers but it now covers almost 80% of the Server market.
➤ Linux has a very adaptable and open designs and practices which allows the linux into different spheres such as Mobile, Cloud,Embedded Devices etc..

THE USER INTERFACE
What you see is what you get

➤ Linux is traditionally known for its Command-line interface (CLI) although a lot Graphical user interface’s (GUI) exist for the platform.
➤ The User Interface in Linux is Commonly Known as Shell.
➤ For desktop systems, the default mode is usually a graphical user interface, although the CLI is available through terminal emulator windows or on a separate virtual console.
➤ Linux Widely uses BASH(Bourne Again Shell) which is developed by GNU.
➤ There are many GUI’s available Such as Gnome,KDE,XFCE,WVM etc..
Gnome Shell

THE DEVELOPMENTEternal vigilance is the price of eternal development

THE DEVELOPMENT
➤ Linux is developed on the Open Source Development model.
➤ Any Person with the knowledge and skill can contribute to growth of the project.
➤ Linux Development uses ‘Git’ Revision Control System to maintain millions of lines of code ,used by thousands of free and open source projects and ‘Git’ was developed by Linus Torvalds himself.
➤ Linux is the largest Coillabrative Development project in history of computing and still growing to this date.
➤ Every new feature or a fix goes through heavy scrutiny before it gets into the linux platform. Hence Linux guarantees high standards of Security and Stability.

➤ The heart and Soul of Linux Developments are the Community.
➤ Every Variant of Linux that are called ‘Distributions’ aka ‘Distros’ have their own Communities built to help with development and get continuous feedback.
➤ In many cities and regions, local associations known as Linux User Groups (LUGs) seek to promote their preferred distribution and by extension free software.
➤ They hold meetings and provide free demonstrations, training, technical support, and operating system installation to new users.

THE DEVELOPMENT : HOW LINUX IS BUILT ?
Credits : The Linux Foundation

THE DEVICES AND DIVERSITYAn Essential part of creativity is not being afraid

THE DEVICES AND DIVERSITY
➤ The Linux kernel is a widely ported operating system kernel, available for devices ranging from mobile phones to supercomputers.
➤ Linux kernels are ‘forked’ and modified to meet the needs of the device.
➤ ‘Fork’ is nothing but a copy that is later modified or updated.
➤ Beside the Linux distributions designed for general-purpose use on desktops and servers, distributions may be specialised for different purposes including: computer architecture support, embedded systems, stability, security, localisation to a specific region or language, targeting of specific user groups, support for real-time applications, or commitment to a given desktop environment.
➤ Examples are Kali Linux (Security),Ubuntu(Desktop),CentOS(Server)

THE DEVICES AND DIVERSITYLinux is also used in Embed devices and SBC’s(Single Board Computers) that have
Revolutionised the education and Maker Spaces.
A Sample of Raspberry Pi A Camera made with Raspberry Pi
Build A Low-Cost Home Surveillance Camera With A Raspberry Pi
http://blog.initialstate.com/3-raspberry-pi-camera-projects/

In-car entertainment system of the Tesla Model S is based on Ubuntu

➤ Linux is used in all the major Industries such as Space,Production,Entertainment,Defence,Energy etc.
➤ The Famous NYSE(New York Stock Exchange) and BSE(Bombay Stock Exchange) use Linux as their platform for trading every day.
➤ The Ubuntu derivatives Edubuntu and The Linux Schools Project, as well as the Debian derivative Skolelinux, provide education-oriented software packages. They also include tools for administering and building school computer labs and computer-based classrooms, such as the Linux Terminal Server Project (LTSP).
➤ Due to Stability,Reliability and Security Linux has found its way into many sectors and sky seems to be only the limit.

LOOKING FORWARD
The Best way to predict the future is to create it.

➤ Linux has always been the fastest to catch up with the technology and trends and has shown the promise of growth over the years.
➤ Linux and Linux based companies are growing over a rapid pace.
➤ As Computers get smaller and problems around us get complex there is need to use the technology and harness the powers of linux and technology to solve problems of future.
➤ Internet of things,Quantum Computing and Virtual and Augmented Reality are the challenges that linux has to face in the upcoming days.
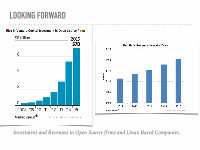
Investment and Revenues in Open Source firms and Linux Based Companies.

Augmented Reality and Linux
AR Desktop Built using open source ARToolkit
https://www.assetstore.unity3d.com/jp/#!/content/19492
Watch Video at :
https://www.youtube.com/watch?v=amxO38aoKZc

Linux foundations Project ‘Zephyr’ a tiny OS for Internet of things
Internet of things and Linux
Zephyr Architecture Zephyr Microkernel
http://thehackernews.com/2016/02/zephyr-internet-of-things-os.html

“Future depends on what we do in the present…
-Mahatma Gandhi

Linux For Beginners: The Ultimate Guide To The Linux Operating System & Linux
Operating Systems and Using Linux
Linux Operating System Configuration Guide
Linux Operating System
Operating System(Windows and Linux)
Implementing Linux Operating System Security
Operating Systems LINUX Lab Manual
2. Operating System Case Study: Linux - Eie | Homeeie.polyu.edu.hk/~em/it0506pdf/2 Linux.pdf · 2. Operating System Case Study: Linux 2. Operating System Case Study: ... zTo facilitate
IBM Tivoli Agentless Monitoring for Linux Operating ...€¦ · iv IBM Tivoli Agentless Monitoring for Linux Operating ... 2 IBM Tivoli Agentless Monitoring for Linux Operating Systems
The free operating system that has taken over the world · PDF file CASE STUDY ABOUT THE LINUX PROJECT The Linux kernel which forms the core of the Linux operating system is
UNIX/LINUX OPERATING SYSTEM
Becoming Linux Expert Series-Install Linux Operating System
OPERATING SYSTEMS LINUX - os.ucg.ac.me · OPERATING SYSTEMS LINUX Božo Krstajić, PhD, ... installed on Slackware Linux. ... Compressing files is easy:
1 ENG224 INFORMATION TECHNOLOGY – Part I 2. Operating System Case Study: Linux
Operating System - Linux
Operating System Design - Linux
The Linux Operating System
Introduction to the Linux Operating System What is Linux
Linux OS (Or) Open Source Operating System · PDF file1 Linux OS (Or) Open Source Operating System Getting Start with Linux OS What is Linux? Linux OS [m True 32-bit Operating System
Linux Operating System Vulnerabilities
Linux Performance Tools - Linux/VM: Two great operating systems
History of Linux Operating System
Linux/Unix-based Operating Systems
LINUX OPERATING SYSTEM - Study Mafiastudymafia.org/.../2015/08/CSE-Linux-Operatig-system-report.pdf · LINUX OPERATING SYSTEM LINUX is modern , ... A thread may be implemented in
Linux Operating System Ppt
THE LINUX OPERATING SYSTEM: AN INTRODUCTION Shahid · PDF fileTHE LINUX OPERATING SYSTEM: ... The LINUX Operating System: An Introduction ... modify and recompile the kernel of the
THE LINUX OPERATING SYSTEM -
linux training | linux training videos | linux training pdf | red hat linux (operating system)
Operating Systems Linux Installation
Operating System LINUX MANDRIVA
CASE STUDY 1: UNIX AND LINUX - Instituto de Computaçãocelio/mc514/docs/figs-10.pdf · CASE STUDY 1: UNIX AND LINUX ... UNIX operating system (process management, ... The sequence
Embedded Operating Systems and Linux
Introduction To Linux Operating System
UNIT 1 INSTALL YOUR OPERATING (WINDOWS/LINUX) Install … · Install Your Operating System UNIT 1 INSTALL YOUR OPERATING (WINDOWS/LINUX) SYSTEM (WINDOWS/LINUX) Structure Page Nos
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
- Operating System Tutorial
- What is an Operating System?
- Functions of Operating System
- Types of Operating Systems
- Need and Functions of Operating Systems
- Commonly Used Operating System
Structure of Operating System
- Operating System Services
- Introduction of System Call
- System Programs in Operating System
- Operating Systems Structures
History of Operating System
- Booting and Dual Booting of Operating System
Types of OS
- Batch Processing Operating System
- Multiprogramming in Operating System
- Time Sharing Operating System
- What is a Network Operating System?
- Real Time Operating System (RTOS)
Process Management
- Introduction of Process Management
- Process Table and Process Control Block (PCB)
- Operations on Processes
- Process Schedulers in Operating System
- Inter Process Communication (IPC)
- Context Switching in Operating System
- Preemptive and Non-Preemptive Scheduling
CPU Scheduling in OS
- CPU Scheduling in Operating Systems
- CPU Scheduling Criteria
- Multiple-Processor Scheduling in Operating System
- Thread Scheduling
Threads in OS
- Thread in Operating System
- Threads and its types in Operating System
- Multithreading in Operating System
Process Synchronization
- Introduction of Process Synchronization
- Race Condition Vulnerability
- Critical Section in Synchronization
- Mutual Exclusion in Synchronization
Critical Section Problem Solution
- Peterson's Algorithm in Process Synchronization
- Semaphores in Process Synchronization
- Semaphores and its types
- Producer Consumer Problem using Semaphores | Set 1
- Readers-Writers Problem | Set 1 (Introduction and Readers Preference Solution)
- Dining Philosopher Problem Using Semaphores
- Hardware Synchronization Algorithms : Unlock and Lock, Test and Set, Swap
Deadlocks & Deadlock Handling Methods
- Introduction of Deadlock in Operating System
- Conditions for Deadlock in Operating System
- Banker's Algorithm in Operating System
- Wait For Graph Deadlock Detection in Distributed System
- Handling Deadlocks
- Deadlock Prevention And Avoidance
- Deadlock Detection And Recovery
- Deadlock Ignorance in Operating System
- Recovery from Deadlock in Operating System
Memory Management
- Memory Management in Operating System
- Implementation of Contiguous Memory Management Techniques
- Non-Contiguous Allocation in Operating System
- Compaction in Operating System
- Best-Fit Allocation in Operating System
- Worst-Fit Allocation in Operating Systems
- First-Fit Allocation in Operating Systems
- Fixed (or static) Partitioning in Operating System
- Variable (or Dynamic) Partitioning in Operating System
- Paging in Operating System
- Segmentation in Operating System
- Virtual Memory in Operating System
Page Replacement Algorithms
- Page Replacement Algorithms in Operating Systems
- Program for Page Replacement Algorithms | Set 2 (FIFO)
- Belady's Anomaly in Page Replacement Algorithms
- Optimal Page Replacement Algorithm
- Program for Least Recently Used (LRU) Page Replacement algorithm
- Techniques to handle Thrashing
- Storage Management
- File Systems in Operating System
- File Allocation Methods
- Free space management in Operating System
- Disk Scheduling Algorithms
- RAID (Redundant Arrays of Independent Disks)
OS Interview Questions
- Last Minute Notes – Operating Systems
- Operating System Interview Questions
OS Quiz and GATE PYQ's
- OS Process Management
- OS Memory Management
- OS Input Output Systems
- OS CPU Scheduling
- 50 Operating System MCQs with Answers
An operating system is a type of software that acts as an interface between the user and the hardware. It is responsible for handling various critical functions of the computer or any other machine. Various tasks that are handled by OS are file management, task management, garbage management, memory management, process management, disk management, I/O management, peripherals management, etc.
Generation of Operating System
Below are four generations of operating systems.
- The First Generation
- The Second Generation
- The Third Generation
- The Fourth Generation
1. The First Generation (1940 to early 1950s)
In 1940, an operating system was not included in the creation of the first electrical computer. Early computer users had complete control over the device and wrote programs in pure machine language for every task. During the computer generation, a programmer can merely execute and solve basic mathematical calculations. an operating system is not needed for these computations.
2. The Second Generation (1955 – 1965)
GMOSIS, the first operating system (OS) was developed in the early 1950s. For the IBM Computer, General Motors has created the operating system. Because it gathers all related jobs into groups or batches and then submits them to the operating system using a punch card to finish all of them, the second-generation operating system was built on a single-stream batch processing system.
3. The Third Generation (1965 – 1980)
Because it gathers all similar jobs into groups or batches and then submits them to the second generation operating system using a punch card to finish all jobs in a machine, the second-generation operating system was based on a single stream batch processing system . Control is transferred to the operating system upon each job’s completion, whether it be routinely or unexpectedly. The operating system cleans up after each work is finished before reading and starting the subsequent job on a punch card. Large, professionally operated machines known as mainframes were introduced after that. Operating system designers were able to create a new operating system in the late 1960s that was capable of multiprogramming —the simultaneous execution of several tasks in a single computer program.
In order to create operating systems that enable a CPU to be active at all times by carrying out multiple jobs on a computer at once, multiprogramming has to be introduced. With the release of the DEC PDP-1 in 1961, the third generation of minicomputers saw a new phase of growth and development.

4. The Fourth Generation (1980 – Present Day)
The fourth generation of personal computers is the result of these PDPs. The Generation IV (1980–Present)The evolution of the personal computer is linked to the fourth generation of operating systems. Nonetheless, the third-generation minicomputers and the personal computer have many similarities. At that time, minicomputers were only slightly more expensive than personal computers, which were highly expensive.
The development of Microsoft and the Windows operating system was a significant influence in the creation of personal computers. In 1975, Microsoft developed the first Windows operating system. Bill Gates and Paul Allen had the idea to advance personal computers after releasing the Microsoft Windows OS. As a result, the MS-DOS was released in 1981, but users found it extremely challenging to decipher its complex commands. Windows is now the most widely used and well-liked operating system available. Following then, Windows released a number of operating systems, including Windows 95, Windows 98, Windows XP , and Windows 7, the most recent operating system. The majority of Windows users are currently running Windows 10. Apple is another well-known operating system in addition to Windows.
Types of Operating System
Operating Systems have evolved in past years. It went through several changes before getting its original form. These changes in the operating system are known as the evolution of operating systems . OS improve itself with the invention of new technology. Basically , OS added the feature of new technology and making itself more powerful. Let us see the evolution of operating system year-wise in detail:
- No OS – (0s to 1940s)
- Batch Processing Systems -(1940s to 1950s)
- Multiprogramming Systems -(1950s to 1960s)
- Time-Sharing Systems -(1960s to 1970s)
- Introduction of GUI -(1970s to 1980s)
- Networked Systems – (1980s to 1990s)
- Mobile Operating Systems – (Late 1990s to Early 2000s)
- AI Integration – (2010s to ongoing)
1. No OS – (0s to 1940s)
As we know that before 1940s, there was no use of OS . Earlier, people are lacking OS in their computer system so they had to manually type instructions for each tasks in machine language(0-1 based language) . And at that time , it was very hard for users to implement even a simple task. And it was very time consuming and also not user-friendly . Because not everyone had that much level of understanding to understand the machine language and it required a deep understanding.
2. Batch Processing Systems -(1940s to 1950s)
With the growth of time, batch processing system came into the market .Now Users had facility to write their programs on punch cards and load it to the computer operator. And then operator make different batches of similar types of jobs and then serve the different batch(group of jobs) one by one to the CPU .CPU first executes jobs of one batch and them jump to the jobs of other batch in a sequence manner.
3. Multiprogramming Systems -(1950s to 1960s)
Multiprogramming was the first operating system where actual revolution began. It provide user facility to load the multiple program into the memory and provide a specific portion of memory to each program. When one program is waiting for any I/O operations (which take much time) at that time the OS give permission to CPU to switch from previous program to other program(which is first in ready queue) for continuos execution of program with interrupt.
4. Time-Sharing Systems -(1960s to 1970s)
Time-sharing systems is extended version of multiprogramming system. Here one extra feature was added to avoid the use of CPU for long time by any single program and give access of CPU to every program after a certain interval of time. Basically OS switches from one program to another program after a certain interval of time so that every program can get access of CPU and complete their work.
5. Introduction of GUI -(1970s to 1980s)
With the growth of time, Graphical User Interfaces (GUIs) came. First time OS became more user-friendly and changed the way of people to interact with computer. GUI provides computer system visual elements which made user’s interaction with computer more comfortable and user-friendly. User can just click on visual elements rather than typing commands. Here are some feature of GUI in Microsoft’s windows icons, menus and windows.
6. Networked Systems – (1980s to 1990s)
At 1980s,the craze of computer networks at it’s peak .A special type of Operating Systems needed to manage the network communication . The OS like Novell NetWare and Windows NT were developed to manage network communication which provide users facility to work in collaborative environment and made file sharing and remote access very easy.
7. Mobile Operating Systems – (Late 1990s to Early 2000s)
Invention of smartphones create a big revolution in software industry, To handle the operation of smartphones , a special type of operating systems were developed. Some of them are : iOS and Android etc. These operating systems were optimized with the time and became more powerful.
8. AI Integration – (2010s to ongoing)
With the growth of time, Artificial intelligence came into picture. Operating system integrates features of AI technology like Siri, Google Assistant, and Alexa and became more powerful and efficient in many way. These AI features with operating system create a entire new feature like voice commands, predictive text, and personalized recommendations.
Note: The above mentioned OS basically tells how the OS evolved with the time by adding new features but it doesn’t mean that only new generation OS are in use and previously OS system are not in use, according to the need, all these OS are still used in software industry.
FAQs on History of Operating System
Q.1: how has the development of computer hardware been impacted by the evolution of operating systems.
The design and advancement of computer hardware have been significantly influenced by the development of operating systems. By time by time hardware producers added new features and capabilities to their products as operating systems improved in order to better support the functionality offered by the operating systems after a long variation of time. Like for instance, basically the development of memory management units (MMUs) in hardware to handle memory addressing and protection followed the introduction of virtual memory in operating systems. Similarly, the demand for operating system multitasking and multiprocessing support prompted the creation of more potent and effective processors and other hardware components.
Q.2: How has the development of distributed systems impacted how operating systems have changed over time?
Operating systems have been significantly impacted by the rise of distributed systems, such as client-server architectures and cloud computing. To support network communication, distributed file systems, and resource sharing across multiple machines, operating systems had to develop. Distributed operating systems also developed to offer scalability, fault tolerance, and coordination in distributed environments. These modifications improved the ability to manage resources across interconnected systems by advancing networking protocols, remote procedure calls, and distributed file systems.
Q.3: What is the mother of operating system?
UNIX is the mother of operating System. Unix is an Operating System that is truly the base of all Operating Systems like Ubuntu, Solaris, POSIX, etc.
Please Login to comment...
Similar reads.

- Technical Scripter 2022
- Computer Subject
- Operating Systems
- Technical Scripter
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
- Open access
- Published: 30 April 2024
Strengthening event-based surveillance (EBS): a case study from Afghanistan
- Mohamed Mostafa Tahoun 1 , 2 ,
- Mohammad Nadir Sahak 3 ,
- Muzhgan Habibi 3 ,
- Mohamad Jamaluddin Ahadi 4 ,
- Bahara Rasoly 4 ,
- Sabrina Shivji 5 ,
- Ahmed Taha Aboushady 3 , 6 ,
- Pierre Nabeth 3 ,
- Mahmoud Sadek 3 &
- Alaa Abouzeid 1 , 7
Conflict and Health volume 18 , Article number: 39 ( 2024 ) Cite this article
179 Accesses
1 Altmetric
Metrics details
The sustained instability in Afghanistan, along with ongoing disease outbreaks and the impact of the COVID-19 pandemic, has significantly affected the country.
During the COVID-19 pandemic, the country’s detection and response capacities faced challenges. Case identification was done in all health facilities from primary to tertiary levels but neglected cases at the community level, resulting in undetected and uncontrolled transmission from communities. This emphasizes a missed opportunity for early detection that Event-Based Surveillance (EBS) could have facilitated.
Therefore, Afghanistan planned to strengthen the EBS component of the national public health surveillance system to enhance the capacity for the rapid detection and response to infectious disease outbreaks, including COVID-19 and other emerging diseases. This effort was undertaken to promptly mitigate the impact of such outbreaks.
We conducted a landscape assessment of Afghanistan’s public health surveillance system to identify the best way to enhance EBS, and then we crafted an implementation work plan. The work plan included the following steps: establishing an EBS multisectoral coordination and working group, identifying EBS information sources, prioritizing public health events of importance, defining signals, establishing reporting mechanisms, and developing standard operating procedures and training guides.
EBS is currently being piloted in seven provinces in Afghanistan. The lessons learned from the pilot phase will support its overall expansion throughout the country.
Background information
Following years of war and recent political changes, Afghanistan is facing a severe humanitarian crisis, with 24.4 million people needing humanitarian assistance and 18.1 million requiring health assistance to survive as of 2022. These challenges have heightened the risk of infectious disease outbreaks due to interrupted access to health services, increased food insecurity, internal displacement, and higher-than-usual rates of cross-border return (1). The country has recently experienced multiple outbreaks, including measles, diarrheal disease (including cholera), dengue fever, Crimean Congo hemorrhagic fever, pertussis, and malaria [ 1 ].
From the first reported case of COVID-19 in February 2020 to 3 December 2022, a total of 206,675 confirmed cases of COVID-19 and 7,840 deaths were reported [ 2 ]. However, the national serosurvey of COVID-19 morbidity in Afghanistan, which was conducted during June and July 2021, revealed that around 10 million people (31.5% of the population) were seropositive for antibodies against SARS-CoV-2, reflecting either current or previous COVID-19 infection [ 3 ].
Amidst Afghanistan’s complex challenges, the “One Health” concept stands out as essential, emphasizing the interdependence of human, animal, and environmental health. This approach promotes collaborative surveillance, integrating public health, veterinary, and environmental sciences to improve infectious disease detection, response, and management. Given Afghanistan’s vulnerability to health crises, adopting One Health and enhancing collaborative efforts are crucial for addressing immediate issues and building long-term resilience against future emergencies, ensuring a unified and effective approach to safeguarding health across all fronts.
The World Health Organization (WHO) recommends adopting an early warning and response (EWAR) function to enhance the capabilities of the surveillance system in detecting infectious diseases and outbreaks [ 4 ]. Event-based surveillance (EBS) is a crucial component of EWAR [ 5 ]. EBS helps rapidly detect unusual occurrences and outbreaks with pandemic potential, especially in areas with limited access to formal healthcare with a focus on all hazards approach, ensuring alignment with One Health concept. This rapid detection of potential events can trigger a quicker response than what might be expected from routine surveillance. For example, during a pandemic, EBS can detect new clusters and trigger response actions. EBS should work alongside case-based and laboratory surveillance systems such that individual cases identified in a cluster are referred to a health facility and have a sample collected, where appropriate. This link to case-based surveillance is essential to accurately count cases, track necessary epidemiologic and virologic information, and guide affected persons.
In Afghanistan, the National Disease Surveillance and Response (NDSR) system, operating under the General Directorate of Monitoring, Evaluation, and Health Information System, conducts infectious disease surveillance. This system includes indicator-based surveillance (IBS) and EBS components. The IBS component of NDSR gathers data on 17 notifiable diseases, prioritizing them based on preventability and public health importance from selected sentinel sites. However, EBS has been limited in scope and functionality, relying on few health facilities and communities through unstructured reporting.
During the onset of the COVID-19 pandemic, outbreak detection was primarily restricted to some health facilities later to all of them. The significance of EBS in Afghanistan became apparent following the escalation of the first COVID-19 wave in May 2020. During this period, numerous clusters of COVID-19 cases and deaths emerged within the community, yet they remained unreported and unmanaged. Consequently, the Ministry of Public Health (MoPH) surveillance department took action to enhance the EBS system.
The prioritization of EBS strengthening in Afghanistan, particularly in response to the COVID-19 pandemic, stems from its ability to capture a broader spectrum of signals related to disease activity, including outbreaks that might be missed or underreported in a weakened healthcare infrastructure. This approach compensates for the gaps left by traditional IBS, especially in scenarios where logistical, financial, or infrastructural constraints might hamper laboratory or case-based surveillance. By prioritizing EBS, Afghanistan aims to leverage its agility and broader scope to better navigate the complexities of disease surveillance in a context marked by significant disruptions to healthcare services and reporting mechanisms, thus offering a pragmatic path forward in bolstering the country’s disease outbreak response capabilities.
This paper highlights the EBS implementation process and shares lessons from an emergency country context. It presents the main steps and outputs of the first phase of EBS implementation in Afghanistan and discusses the subsequent steps in the implementation process.
The implementation of the EBS system in Afghanistan started through collaboration between the MoPH, the WHO Country Office Afghanistan (WCO), the WHO Regional Office for the Eastern Mediterranean (EMRO), the United States Centers for Disease Control and Prevention (CDC), and the Global Health Development/Eastern Mediterranean Public Health Network (GHD|EMPHNET). The MoPH led the EBS enhancement process and implementation in the country with the technical support of WHO, the CDC, and GHD|EMPHNET.
The initial phase involved conducting a landscape assessment to better understand the existing surveillance system in Afghanistan, facilitating the design of an EBS that would integrate seamlessly. The landscape assessment was conducted through guided interviews with key surveillance officials at the MoPH and WCO using a questionnaire developed by the CDC. The questionnaire focused on gathering information related to detection, reporting, verification, and risk assessment of potential public health threats.
The results of the assessment were utilised in the second phase, involving the crafting of the EBS work plan. This work plan was drafted at country level with technical support from EMRO and CDC. The work plan outelined the implementation steps and activities aimed to enhance EBS in Afghanistan. These activities included identifying and training EBS mentors at the MoPH, mapping EBS stakeholders, identifying EBS information sources, prioritizing EBS events and defining signals, developing EBS guidelines and Standard Operating Procedures (SoPs), contextualizing EBS training materials, deploying the Epidemic Intelligence from Open Sources (EIOS) tool to implement the media scanning component of EBS, identifying EBS pilot sites (provinces), evaluating the pilot sites and expanding EBS throughout the country.
The MoPH surveillance department designated three mentors to enhance the EBS system. These mentors identified all relevant stakeholders for EBS in Afghanistan, referring to the existing IHR stakeholders list, and made necessary additions or exclusions to ensure representation for all an hazards approach through a multi-sectoral collaboration.
They assigned the mapped stakeholders to a coordination committee (CC). In the first meeting, the EBS mentors introduced EBS, explained its importance, and presented the EBS workplan to the CC. In a second meeting, the CC, guided by the EBS mentors, identified priority information sources for EBS. Subsequently, the CC established a smaller Technical Working Group (TWG) to prioritize events, develop signals, and create Standard Operating Procedures (SoPs) and training materials.
The TWG convened regular biweekly meetings with an initial focus on identifying priority events under EBS. Events are considered to be manifestations of disease or occurrences which have potential to create disease of known or unknown origin. “Event” in the event-based surveillance context is a signal that is verified to be truly occurring [ 4 ].
To facilitate the practice of prioritizing events, EBS mentors developed a complete list of events ahead of the meetings based on a risk assessment process using locally developed tool by WHO country office and MOH. No sensitivity analyses was done for any unusual event. The EBS mentors discussed the list with the TWG, and based on several criteria, including the potential impact of the event on public health, epidemic-prone diseases, historically prevalent diseases with the potential to re-emerge, and diseases targeted for eradication or elimination, priority events were selected.
After prioritizing events, the TWG created corresponding signals. Signlas are bits of information or occurences that may represent an acute risk to human health [ 4 ]. The TWG finalized the drafted signals with technical input from the WHO EMRO and US CDC. Following the creation of signals, the flow of information for EBS, focal points at each level, and roles and responsibilities were discussed by the TWG. The embedding of the EBS flow of information into the existing surveillance structure took place. Subsequently, all pieces developed for EBS were merged into a technical guideline with technical support from WHO, CDC, and GHD|EMPHNET. The selection of pilot sites for EBS implementation was carried out by the EBS CC.
Key processes
Landscape assessment.
The landscape assessment of the surveillance system in Afghanistan highlighted the existence of an established National Disease Surveillance and Response (NDSR) system. NDSR includes different administrative levels (Fig. 1 ).
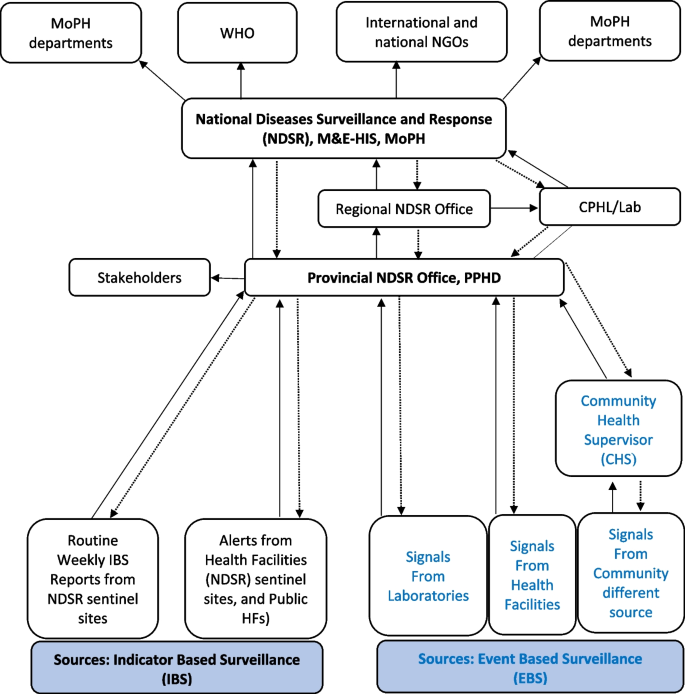
NDSR Structure and communication pathways in Afghanistan. NDSR Structure relies on IBS and EBS. IBS collects data from sentinel sites on priority disease. EBS (in blue) recentlcy been incorporated into NDSR structure. At the regional level and national level, NDSR offices disseminate information collected from EBS and IBS to relevant stakeholders, NGO’s, WHO and key department of Ministry of health
The NDSR functions at the national level and is responsible for the overall coordination of infectious diseases in the country. There are eight regional NDSR offices, each including several provinces, and their main responsibility is to coordinate the surveillance activities in their regions and report to the national surveillance office. Each province has its own surveillance office that is responsible for the implementation of surveillance activities in its province. In 2021, there were 519 sentinel sites (health facilities) (of 3750 health facilities countrywide) reporting to the NDSR system, including regional hospitals, provincial hospitals, district hospitals, and comprehensive and basic health facilities.
After the surge of the COVID-19 pandemic in May 2020, the country mandated both laboratory-confirmed and suspected clinical COVID-19 cases reporting from all health facilities daily using online reporting forms through a data capture tool developed using DHIS2.
The assessment found a well-established sentinel IBS within the NDSR. However, the EBS component was limited, relying on a small number of health facilities and communities as information sources without clear reporting mechanisms. Common signals such as hemorrhagic fever (1 and above), clusters of diarrhea (5+), and clusters of rash with fever (5+) in children were reported from these sources to provincial and national NDSR. The national NDSR then conducts outbreak investigations and laboratory confirmations.
Afghanistan’s challenging terrain, characterized by mountains, poses a unique challenge, with over 9 million individuals residing in under-served or hard-to-reach areas (defined as more than a one-hour walking distance to the nearest health facility). The IBS system gathers data solely from sentinel sites, not encompassing all health facilities, potentially leading to delays in case presentation at the nearest health facility due to both geographical barriers and the population’s health-seeking behavior.
Information in an EBS system can include informal sources such as media reports, reputable and well-connected community members, or other non-traditional sources for health information in addition to official or formal sources [ 4 ]. There was no specific and clear Community Event-Based Surveillance (CEBS), Health Facility Event-Based Surveillance (HEBS), Internet Event-Based Surveillance, laboratory, or veterinary EBS in place. Coordination with the animal health sector was limited to quarterly zoonotic committee meetings at the national and provincial levels and information sharing occured one way where only the MoPH surveillance department shared weekly surveillance information to animal health and other relevant sectors. There was no established reporting mechanism for disease and events from the private sector in the country. In addition, the lack of standardized guidelines and SoPs for EBS in Afghanistan posed a challenge for implementation and sustainability.
Assigning national EBS mentors
CDC and WHO EMRO trained the three assigned mentors for EBS from the surveillance department of the MoPH on the principles and methods of EBS. The EBS mentors played an important role in advocating for and leading the integration of EBS in-country, coordinating with all stakeholders, and developing EBS guidelines and SoPs. In the second phase of EBS implementation, the mentors trained provincial and regional surveillance officers on EBS. EBS mentors intends to ensure the sustainability of event-based surveillance as part of the national disease surveillance strategy.
Mapping the EBS stakeholders
Major stakeholders identified include the MoPH, Central Public Health Laboratory (CPHL), Ministry of Agriculture, Irrigation and Livestock (MAIL), Ministry of Borders and Tribal Affairs, Ministry of Hajj and Religious Affairs, Afghanistan Nuclear Energy Agency (ANEA), National Disaster Management Authority, National Environment Protection Agency, Civil Aviation Authority Afghanistan, International Organization for Migration (IOM), and the WHO Country Office in Afghanistan. Maintaining constant communications among these stakeholders involved establishing an EBS coordination committee (CC), led by the MoPH.
The CC, under the leadership of the MoPH, played a central role in mobilizing all necessary resources for EBS, identifying EBS information sources, and validating signals, guidelines, SoPs, training materials, data collection tools, and the work plan for EBS implementation. Additionally, the CC led the monitoring and evaluation of EBS implementation in the country.
To streamline focus on EBS activities, the TWG was established, comprising key focal points from the MoPH, MAIL, CPHL, and WCO. The TWG, through its collaboration, prioritized events, defined signals, developed EBS SoPs, contextualized training materials, and identified sites for EBS implementation.
The information sources for EBS
EBS requires multi-sectoral collaboration and coordination between different stakeholders and relies on information sources beyond the traditional health system. While these may be directly linked to human health, data can also be provided by the non-human health sector, local communities, media, and international sources. Some information sources have key informants, who generally are community members with strong ties within their communities, such as religious leaders, schoolteachers, or even shop owners. The EBS CC identified and prioritized the EBS information sources in Afghanistan as described in Table 1 below.
Identify priority events and define signals
The prioritized events for EBS in Afghanistan include clusters of COVID-19 cases, avian influenza, acute hemorrhagic fever, vaccine-preventable diseases such as measles and poliomyelitis, cholera, norovirus (food poisoning), zoonotic priority diseases causing outbreaks, and emerging new diseases. The EBS TWG defined signals for each of these prioritized events and identified information sources, with key members from the Ministry of Education, municipality, Haj and Awkaf, Community Based Health Care department of the MoPH, MAIL, and other relevant stakeholders. These signals are standardized across the country.
Table 2 displays the list of signals defined for communities, health facilities, laboratories, and veterinary services.
EBS flow of information
The flow of information for the EBS (Fig. 2 ) was defined based on the steps of EBS and the current structure of the surveillance system. The flow of information relies mainly on key surveillance officers functioning at the local, provincial, regional and national levels as well as focal points from other relevant sources (laboratories, health facilities, veterinary services and PoEs).
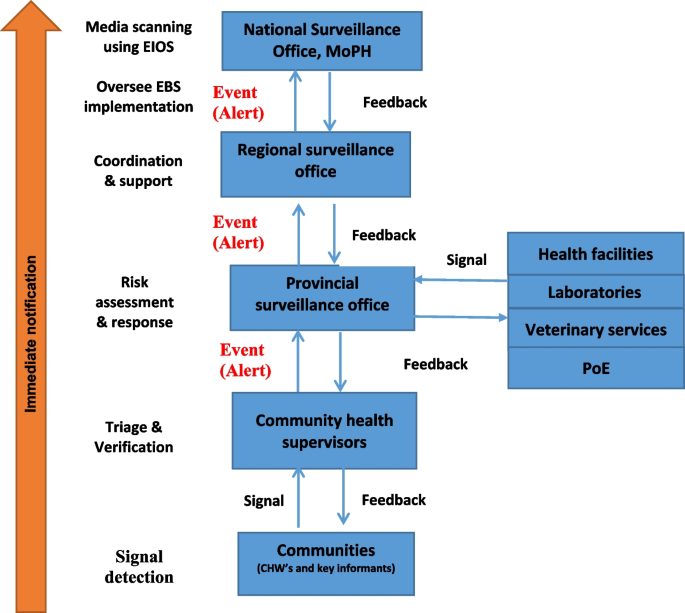
EBS flow of information in Afghanistan
In Afghanistan, the community signals should be notified immediately by CHWs and other key informants to the community health supervisors (CHSs). Meanwhile, signals from health facilities, veterinary services, laboratories, and PoEs should be reported immediately to the surveillance focal points at the provincial level. Each community signal will be triaged and verified within 24 h of detection by CHSs and by surveillance officers at the provincial level for health facility, laboratory, PoE and veterinary-related signals.
Triage involves evaluating two questions: (1) Is the reported information pertinent to early warning (i.e., could this signal indicate a genuine public health event)? and (2) Has the signal been previously reported (i.e., is it a duplicate)? Verification is conducted by addressing three questions: (1) Is the report accurate (i.e., is it truel)? (2) Has the information been provided by a trustworthy source or sources? and (3) Does the report fulfill the criteria for one or more of the already developed list of signals?. Once a signal is verified as true, reported by credible source and meet criterial for the list of signals, it is called event (alert).
The community-verified events must be immediately reported to the provincial surveillance officers to undergo a risk assessment and response process jointly with its RRTs. Meanwhile, provincial surveillance officers must triage and verify signals from the health facility, veterinary services, laboratories, and PoEs and if verified, should initiate the risk assessment and provide a response immediately in coordination with the provincial RRTs. High-risk events as indicated by the risk assessment process must be assessed or responded to within 48 h of notification.
To conduct risk assessment, the team need to formulate risk assessment questions. These questions will differ from one event to another. Examples of these questions are:
Does the suspected disease have a high potential for spread?
Is there higher than expected mortality and morbidity from the diseases?
Is there a cluster of cases or deaths?
Does the disease have possible consequences on trade or travel?
Does the event affect livestock/wildlife?
Are there any environmental consequences?
Once sufficient information has been collected, the risk assessment team must determine the the leve of risk and type of action. The WHO risk matrix should should be used for this purpose (Table 3 ).
Based on the level of risk the team should determine the outcome of risk assessment and actions needed. Table 4 describes the potential outcomes of the risk assessment based on information collected during the risk assessment process and assigned level of risk.
Feedback mechanism should be maintained through all levels, ensuring that all levels are aware of the actions has been take on the reported signal and events. This will not only essure that the system runs smoothly but also to enable trust and motivation at each levels.
The provincial surveillance officers should report EBS activities to the national team. The regional surveillance office is responsible for coordinating the EBS implementation in their provinces, providing training, conducting supervisory visits, and providing other operational support.
The central team of NDSR will lead the EBS implementation by coordinating the training of regional and provincial EBS personnel, supporting cascade training, providing training materials and SoPs, monitoring and evaluating EBS implementation, and conducting regular meetings to review data collected and provide feedback. The national surveillance office and the regional surveillance office are also responsible for giving support to the provincial-level surveillance officers in providing an appropriate response to the verified events in coordination with all other sectors.
Furthermore, the National Surveillance Officer is responsible for conducting regular monitoring of the media using the Epidemic Intelligence from Open Sources (EIOS) system, focusing on the prioritized list of events and diseases. During the verification process of signals detected through EIOS, the regional and provincial surveillance officers will serve as contacts. Once a signal is verified, the national surveillance officer will perform a rapid risk assessment and initiate a response.
Developing operational EBS guidelines
After defining EBS information sources, prioritizing events, defining signals, and outlining the EBS information flow, EBS TWG developed a comprehensive operational guideline. This guideline integrates these steps and provides direction to EBS focal points at each level for effective implementation.
EBS TWG tailored Afghanistan’s EBS guidelines uniquely to its specific context, seamlessly integrating EBS into the existing NDSR structure and optimizing available human resources. They prioritized events based on the Afghan context, and carefully developed signals. These guidelines received technical support from the US CDC and WHO. Various guidelines, including WHO’s guidelines on EWAR with a specific focus on EBS and the US CDC’s EBS framework, served as references [ 4 , 6 ].
The guideline itself is structured into three main sections, further subdivided into subsections, as elaborated in Table 5 .
Contextualizing the EBS training materials
In order to facilitate the training of EBS focal points at different levels (Fig. 2 ), training manuals were developed using the CDC-developed EBS training manual as a reference [ 6 ]. A total of five facilitator and corresponding participant training manuals exist to train focal points for EBS in communities, health facilities, laboratories, veterinary services, and at the provincial surveillance office.
EIOS deployment
Media is an important source of information for EBS [ 7 ]. Afghanistan integrated media scanning as one of the surveillance functions under EBS. The EIOS tool has been deployed to facilitate the media scanning function in the country.
WHO proposes the EIOS tool to its member states to strengthen and solidify the surveillance system’s early detection, verification, assessment, and communication functions by utilizing publicly available, open-access information.
After ministerial approval for the initiation of the EIOS, a rigorous configuration process was conducted to capture the local context and language. First, the priority diseases were identified, and for Afghanistan, the list was previously identified through the NDSR. Afterwards, the keywords were translated to the local languages, Pashto and Dari. The local news sources, social media (SM) accounts, and relevant websites were identified to be added to the sources list on the portal. Finally, a physical workshop was conducted to build the MoPH capacities to use EIOS. The steps of EIOS deployment are mentioned in Fig. 3 .

Steps of EIOS deployment in Afghanistan
Following the training, a close follow-up was conducted. The SoP for EIOS was developed and incorporated into the EBS guidelines.
Pilot implementation
Following the development of country-specific guidelines, implementation commenced with a pilot phase in 7 provinces of the country by the end of 2022. The pilot focused on communities and health facilities. Implementation included training trainers for the 45 NDSR officers and coordinators at the national level, regional and provincial levels, with technical support from the WHO.
Subsequently, these trainers conducted training sessions for 883 medical doctors and CHSs in the piloted provinces. Following this, through third-party contractors, these medical doctors and CHSs further trained approximately 11,000 key informants at the community and health facility levels.
The pilot phase in the seven provinces yielded a total of 2,335 signals, of which 1,197 were verified as events. Risk assessments were conducted on 1,153 of these events.
The EBS in Afghanistan has advanced through several steps aimed at enhancing the country’s surveillance capabilities. This thorough process from assessment to selection of pilot sites, lasting about seven months, included extensive consultations at different levels. Key stakeholders under EBS CC and TWG, the US CDC, and the WHO provided valuable insights and expertise during the assessment and guideline development phases.
The approach to enhancing EBS in Afghanistan included several components that led to increased system efficiency and a more inclusive, structured system, despite the challenges posed by the country’s ongoing emergency situation. Afghanistan’s approach to EBS implementation can serve as a model for other countries facing similar contexts and aiming to establish EBS. One of the key strategies involved creating a roadmap for EBS and implementing it based on the results of a surveillance system landscape assessment. This approach ensured the integration of EBS into the existing structure of the surveillance system, which is the key for this work. The second strategy involved selecting key mentors from the national surveillance team and training them on EBS concepts from the very begining. This approach was crucial to ensure that MoPH took ownership of the system and led EBS efforts in the country.
Additionally establishing an EBS CC and a TWG fostered collaboration among diverse stakeholder groups and sectors. This collaboration aimed to collectively enhance the EBS system and broaden the sources of information for EBS in the country. The success of this approach can be seen in Vietnam [ 8 ], where the establishment of an EBS TWG resulted in improved alignment and reduced redundancies, as recommended in other published guidelines. The collaboration with other sectors for EBS also created political willness to implement the system which is key to highlight.
Finally, the development of SoP’s and signals for each identified information source under EBS establishes formalized reporting linkages among various important entities. One crucial linkage is between the human and animal health sectors, enhancing the detection of zoonotic events and advancing One Health efforts in the country [ 9 , 10 , 11 ]. Another significant linkage is the connection between communities and the health sector. Involving communities improves the detection of outbreaks, COVID-19 clusters and similar risks at the local level, leading to controlled transmission and reduced burden. Numerous countries have demonstrated improved risk detection by implementing community-based EBS [ 8 , 12 , 13 , 14 ]. However, ensuring sustainability is essential when implementing EBS through communities. In Afghanistan, CHWs are integral to the community-based healthcare component of the Basic Package of Health Services (BPHS), which has been implemented for 20 years. NGOs train and supervise CHWs under government or United Nations Children’s Fund (UNICEF) contracts. The MoPH NDSR department coordinates with NGOs through the Community-Based Health Care (CBHC) department to support the surveillance system. CHWs, who are volunteers without incentives, work in pairs at health posts, offering services ranging from health promotion to referrals. They receive training from contracted NGOs for their surveillance roles. They received trainings for EBS through similar NGO’s.
In addition to communities, created linkages with health facilities and laboratories for EBS enables the detection of new emerging diseases and pathogens. EBS through these sources also enable detection of clusters of cases among health workers, which was challenging during the COVID-19 pandemic and resulted in increased transmission among health care workers. A systematic review targeted low and middle income countries similary highlights impotance of health facilities to strengthen the early warning function of national surveillance systems [ 15 ].
Importantly, this is the first time the country used the media as a source for EBS by deploying the EIOS platform. EIOS plays an important role in the detection of risks signaled through media [ 16 ]. EIOS also allows monitoring the health risks in bordering countries through published sources and having the control measures in place in response to the increased cross-border activities.
Afghanistan launched the pilot phase of EBS in seven provinces: Kabul (one zone), Herat, Kandahar, Nangarhar, Badakhshan, Balkh, and Bamiyan. This initial phase is focusing on communities and health facilities. Countries can choose to start implementing EBS from a single source and then expand to other sources by time based on workforce, resources, and infrastructure availability to ensure effectiveness and sustainability [ 6 ]. Afghanistan plans to introduce other sources after evaluating the current pilot phase.
The pilot phase provides insight into operationalizing elements of the guideline and SoP, identifying what does not work well, and offering guidance to adjust the EBS strategy for full-scale implementation in the country. The national surveillance office ensures the efficient implementation of EBS in Afghanistan through regular monitoring and evaluation activities. The monitoring and evaluation framework used in Vietnam for the pilot phase is utilized and developed a supervision visit checklist used at different levels responsible for EBS in Afghanistan [ 17 ]. For the final evaluation of the pilot phase, Afghanistan will adopt and use the Africa CDC Monitoring and Evaluation framework [ 18 ].
EBS implementation in Afghanistan encountered limitations such as delays in launching the pilot phase after selection of pilot sites due to political changes and the assignment of new EBS focal points. The Ministry collaborated closely with WHO to revitalize the EBS through training and consultations with the new mentors. With the changes since 2021, the use of EIOS has been limited, requiring training and onboarding of new focal points to replace those previously responsible. The TWG supporting the EBS had been inactive for an extended period and needs restructuring to support ongoing implementation and evaluation of the system for full countrywide implementation.
Availability of data and materials
No datasets were generated or analysed during the current study.
WHO. Afghanistan Emergency Situation Report [Internet]. 2022. http://www.emro.who.int/images/stories/afghanistan/AFG_WHO_EMERGENCY-SITUATION-REPORT_Jan-31-2022.pdf?ua=1 .
WHO. WHO Health Emergency Dashboard [Internet]. 2022. https://covid19.who.int/region/emro/country/af .
Saeedzai SA, Sahak MN, Arifi F, Abdelkreem Aly E, van Gurp M, White LJ, et al. COVID-19 morbidity in Afghanistan: a nationwide, population-based seroepidemiological study. BMJ Open. 2022;12(7):e060739.
Article PubMed Google Scholar
WHO. Implementation of Early Warning and Response with a focus on Event-Based Surveillance [Internet]. WHO; https://apps.who.int/iris/bitstream/handle/10665/112667/WHO_HSE_GCR_LYO_2014.4_eng.pdf?sequence=1 .
WHO. Public Health Surveillance for COVID-19: interim guidance. 2022; https://www.who.int/publications/i/item/WHO-2019-nCoV-SurveillanceGuidance-2022.2 .
CDC. Training Curriculum for Event-based Surveillance in Health Facilities and Communities [Internet]. 2020. https://stacks.cdc.gov/view/cdc/95230 .
Aiello AE, Renson A, Zivich PN. Social media- and Internet-Based Disease Surveillance for Public Health. Annu Rev Public Health. 2020;41:101–18.
Article PubMed PubMed Central Google Scholar
Clara A, Dao ATP, Do TT, Tran PD, Tran QD, Ngu ND, et al. Factors influencing community event-based Surveillance: lessons learned from pilot implementation in Vietnam. Health Secur. 2018;16(S1):S–66.
Google Scholar
Norzin T, Ghiasbeglou H, Patricio M, Romanova S, Zaghlool A, Tanguay F, et al. Event-based surveillance: providing early warning for communicable disease threats. Can Commun Dis Rep Releve Mal Transm Au Can. 2023;49(1):29–34.
Article Google Scholar
One Health High-Level Expert Panel (OHHLEP), Hayman DTS, Adisasmito WB, Almuhairi S, Behravesh CB, Bilivogui P, et al. Developing one health surveillance systems. One Health Amst Neth. 2023;17:100617.
Balajee SA, Salyer SJ, Greene-Cramer B, Sadek M, Mounts AW. The practice of event-based surveillance: concept and methods. Glob Secur Health Sci Policy. 2021;6(1):1–9.
Merali S, Asiedu-Bekoe F, Clara A, Adjabeng M, Baffoenyarko I, Frimpong JA, et al. Community-based surveillance advances the Global Health Security Agenda in Ghana. Lau EH PLOS ONE. 2020;15(8):e0237320.
Article CAS Google Scholar
Clara A, Ndiaye SM, Joseph B, Nzogu MA, Coulibaly D, Alroy KA, et al. Community-based surveillance in Côte d’Ivoire. Health Secur. 2020;18(S1):S–23.
Clara A, Do TT, Dao ATP, Tran PD, Dang TQ, Tran QD, et al. Event-based surveillance at Community and Healthcare Facilities, Vietnam, 2016–2017. Emerg Infect Dis. 2018;24(9):1649–58.
Kuehne A, Keating P, Polonsky J, Haskew C, Schenkel K, Le Polain de Waroux O, et al. Event-based surveillance at health facility and community level in low-income and middle-income countries: a systematic review. BMJ Glob Health. 2019;4(6):e001878.
Abbas H, Tahoun MM, Aboushady AT, Khalifa A, Corpuz A, Nabeth P. Usage of social media in epidemic intelligence activities in the WHO, Regional Office for the Eastern Mediterranean. BMJ Glob Health. 2022;7(Suppl 4):e008759.
Clara A, Dao ATP, Mounts AW, Bernadotte C, Nguyen HT, Tran QM, et al. Developing monitoring and evaluation tools for event-based surveillance: experience from Vietnam. Glob Health. 2020;16(1):38.
Africa CDC, Africa. CDC event based surveillance framework [Internet]. 2023. https://africacdc.org/download/africa-cdc-event-based-surveillance-framework-2/ .
Download references
Acknowledgements
We are grateful to the following staff of MoPH Afghanistan for their ongoing support of the EBS project: Dr Fazal Elahi Alizai, Director General of Monitoring and Evaluation and Health Information System (M&E HIS)Dr. Sayed Ataullah Saeedzai, former director general of Monitoring & Evaluation and Health Information SystemEBS CC and TWG members Also, we would like to acknowledge the technical support provided by WCO, WHO EMRO, CDC, and GHD|EMPHNET.
Funding for this EBS project was provided by WHO, the United States CDC Global Health Security Agenda, and COVID-19 support under grant number GH0002225, a cooperative agreement for this surveillance activity.
Author information
Authors and affiliations.
World Health Organization Country Office, Kabul, Afghanistan
Mohamed Mostafa Tahoun & Alaa Abouzeid
High Institute of Public Health, Alexandria University, Alexandria, Egypt
Mohamed Mostafa Tahoun
Eastern Mediterranean Region WHO Office, Cairo, Egypt
Mohammad Nadir Sahak, Muzhgan Habibi, Ahmed Taha Aboushady, Pierre Nabeth & Mahmoud Sadek
Ministry of Public Health, Kabul, Afghanistan
Mohamad Jamaluddin Ahadi & Bahara Rasoly
United States Centers for Disease Control and Prevention, Atlanta, USA
Sabrina Shivji
Division of infectious diseases, Brigham and women’s hospital, Harvard medical school, Boston, MA, USA
Ahmed Taha Aboushady
Faculty of Medicine, Cairo University, Cairo, Egypt
Alaa Abouzeid
You can also search for this author in PubMed Google Scholar
Contributions
MH and MNS conducted the surveillance assessment. SS, MMT, MS, MH, MNS and PN analyzed the result of the surveillance assessment and identified EBS gaps. SS, MS, MH and MT trained EBS mentors on EBS. MH, MNS, MS, MMT, SS, MJA, and PN participated in development of EBS workplan, implementation of workplan, development of EBS guidelines and training materials. MS and AA provided the training and deployed EIOS. MJA, MH, MNS, and BR created and coordinated EBS CC and TWG meetings. MMT, MJA, BR, AA, MS, and MH developed an EBS pilot implementation plan. MH, MMT, MS, MNS, SS drafted the manuscript. MMT, MNS, MTS, SS, MJA, AB, PN and AA reviewed and revised the manuscript. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Muzhgan Habibi .
Ethics declarations
Ethics approval and consent to participate.
Not applicable.
Competing interests
The authors declare no competing interests.
Consent for publication
Additional information, publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Supplementary material 1., rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
Tahoun, M.M., Sahak, M.N., Habibi, M. et al. Strengthening event-based surveillance (EBS): a case study from Afghanistan. Confl Health 18 , 39 (2024). https://doi.org/10.1186/s13031-024-00598-1
Download citation
Received : 14 December 2023
Accepted : 19 April 2024
Published : 30 April 2024
DOI : https://doi.org/10.1186/s13031-024-00598-1
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Event-based surveillance
- Early warning and response
- Public health surveillance
- And COVID-19
Conflict and Health
ISSN: 1752-1505
- Submission enquiries: [email protected]

COMMENTS
UNIX Case Study (I) 2. Outline •UNIX / Linux •Processes •Tasks 11. UNIX Case Study (I) 3. Outline •UNIX / Linux •History •Components •Kernel modules •Processes •Tasks ... abstractions of the operating system, including such things as virtual memory and processes. 2. System libraries. The system libraries define a standard set ...
This study provides a comparative analysis of three well-known operating systems: Windows, Linux, and Macintosh. The most important factors to consider when studying them are memory and file ...
Operating System Design/Case studies. The goal of this book is to discuss the different issues involved in operating system design, the different strategies that have been tried and to provide concrete examples where possible. Given the number of open-source operating systems available, specific implementations will be used as examples where ...
This paper presents a comparative study of six (i.e. Windows, Linux, Mac, UNIX, Android and iOS) operating systems. based on the OS features and their strengths and weaknesses. The paper is ...
Android OS CASE STUDY. Android is a mobile operating system based on a modified version of the Linux kernel and other open source software, designed primarily for touchscreen mobile devices such as smartphones and tablets. It is an operating system for low powered devices that run on battery and are full of hardware like Global Positioning ...
Abstract. A case study approach for teaching a course on operating systems is described and evaluated. The choice of a particular system, UNIX, for case study is explained and evaluated. The wider ramifications of this system for the Computer Science curriculum at the University of New South Wales are also mentioned.
The operating system is the first program to do several tasks while focusing on the current task at hand. The first task is prompting the OS to boot the computer. Within minutes, the computer will manage tests to make sure everything is working properly, check for new hardware updates and then start the operating system.
Case Study: Operating Systems Microsoft Windows vs. Apple's MacOS. Introduction. This is a historical case of the battle between the MacOS and the Windows operating systems in the personal computers industry. This discussion will examine which network issues were involved and how the different strategies taken by the two companies, Apple and ...
System supports all shells running concurrently. Appropriate shell is loaded at login, but user can usually (except in sh, rsh) dynamically change the shell. A UNIX command takes the form of. executable_file [-options] arguments. The shell runs a command interpretation loop. accept command. read command. process command.
Case Study 2: The Linux Kernel. The Linux kernel, initially developed by Linus Torvalds in 1991, is based on the UNIX operating system. It is an open-source project that has provided a fertile ground for collaboration and innovation. Linux offers a high degree of stability, security, and adaptability, making it the foundation for a wide range ...
Introduction. Android is a mobil e operating system base d on a modified version of the Linux k ernel and. other open source software, designed primarily for touchscre en mobile devices such as ...
An Operating System (OS) is software that manages and handles the hardware and software resources of a computer system. It provides interaction between users of computers and computer hardware. An operating system is responsible for managing and controlling all the activities and sharing of computer resources. An operating system is a low-level ...
CASE STUDY ON LINUX OPERATING SYSTEM By VYOM BHARDWAJ BHARATI VIDYAPEETH (DEEMED TO BE UNIVERSITY) COLLEGE OF ENGINEERING, PUNE DEPARTMENT OF COMPUTER ENGINEERING ACADEMIC YEAR OF 2019-ACKNOWLEDGEMENT. ... The Linux kernel - the core of the Linux operating system - is the result of one of the largest and most successful cooperative software ...
UNIX is a family of multitasking, multiuser computer operating systems developed in the mid 1960s at Bell Labs. It was originally developed for mini computers and has since been ported to various hardware platforms. UNIX has a reputation for stability, security, and scalability, making it a popular choice for enterprise-level computing.
Operating System a Case Study. An Operating System or OS is the most important software and program that can run Computer, Mobile phone, Hand Held Device, etc. It helps to connect and interface computer hardware to program and application software and other common essential services. The OS is initially loaded on at boot time.
What is Linux Operating System. The Linux Operating System is a type of operating system that is similar to Unix, and it is built upon the Linux Kernel. The Linux Kernel is like the brain of the operating system because it manages how the computer interacts with its hardware and resources. It makes sure everything works smoothly and efficiently.
Case Study on Windows Prof. Sujata Rizal 7 1. Simple Structure In MS-DOS, applications may bypass the operating system. Operating systems such as MS-DOS and the original UNIX did not have well-defined structures. There was no CPU Execution Mode (user and kernel), and so errors in applications could
PROCESS MANAGEMENT: # It. takes place in the kernel space and provides the required tools to handle the processes which run in the. terminal and the graphical interface. . .
42 samples of this type. WowEssays.com paper writer service proudly presents to you a free database of Operating System Case Studies meant to help struggling students deal with their writing challenges. In a practical sense, each Operating System Case Study sample presented here may be a pilot that walks you through the essential phases of the ...
THE DESIGN. A Linux-based system is a modular Unix-like operating system, deriving much of its basic design from principles established in Unix during the 1970s and 1980s. Linux is 'Monolithic' in Nature. A monolithic kernel is an operating system architecture where the entire operating system is working in kernel space and is alone in ...
The Second Generation. The Third Generation. The Fourth Generation. 1. The First Generation (1940 to early 1950s) In 1940, an operating system was not included in the creation of the first electrical computer. Early computer users had complete control over the device and wrote programs in pure machine language for every task.
Examples of popular operating system are Windows, Linux, Unix,Android, iOS, Mac. Operating system is used to perform two major activities- ... Case Studies Backed by a huge marketing campaign, Windows 95 came with a significantly enhanced user interface which introduced the start button and taskbar. It also added
The sustained instability in Afghanistan, along with ongoing disease outbreaks and the impact of the COVID-19 pandemic, has significantly affected the country.During the COVID-19 pandemic, the country's detection and response capacities faced challenges. Case identification was done in all health facilities from primary to tertiary levels but neglected cases at the community level, resulting ...
To progress towards the "dual carbon" goal and reduce the cost and increase the efficiency of solid oxide fuel cells, this study conducts a full life cycle analysis of solid oxide fuel cells, in which the environmental impact caused by the operating devices' manufacturing, fuel gas catalyst reforming, single-cell manufacturing, cell stack manufacturing, and energy consumption and ...