We use cookies to give you the best experience possible. By continuing we’ll assume you’re on board with our cookie policy

- A Research Guide
- Research Paper Topics

40 Terrorism Research Paper Topics
Read also: How to start off a research paper ?
- How does the development of technologies affect the tactics of terrorists?
- The tragedy of 9/11
- The Incels movement: a growing danger?
- Terrorism and religion
- Using minors and vulnerable social groups in terrorist acts
- The role of terrorism in the creation and development of Israel
- The most powerful international terrorism groups: Boko Haram, Al Qaeda and others
- Partisan movements and terrorism
- The history of terrorism
- What methods are justified when fighting terrorism?
- Hiroshima bombing: can it be considered terrorism?
- Terrorism in media and films
- The process of radicalization. The creation of terrorist groups
- Motivations of terrorist groups
- Terrorism and Mafia: similarities, differences and cooperation
- Terrorism as a tool for politics. Can it be used to benefit some particular political forces?
- Guantanamo Bay Detention Camp: was it justified?
- Suicide bombing and psychological conditioning of suicide bombers
- Bioterrorism
- Terrorism and human trafficking
- Terrorism threat and the international travel safety
- Is non-violent response to terrorism possible?
- The ways to work with society to prevent terroristic acts
- The first psychological aid to the victims or witnesses of terrorist act
- Why terrorists use hostages? What shall the potential hostages do to survive?
- The main differences between political and non-political terrorism
- The recruiting strategies of terrorists
- Counterterrorism all over the world
- The most prominent terrorist leaders
- The most famous counterterrorist operations
- What can society do to prevent terrorism?
- The future of terrorism. May it evolve?
- The process of taking responsibility for terrorist act: why and how the terrorists do this?
- The model of Israel society. Is it good for fighting terrorism?
- Terrorism as international crime
- Nuclear terrorism
- Terrorism and blackmailing
- Is it possible to exit a terrorist cell?
- Ideological terrorism
- The different definitions of terrorism and the cause of their creation
By clicking "Log In", you agree to our terms of service and privacy policy . We'll occasionally send you account related and promo emails.
Sign Up for your FREE account

Forget about ChatGPT and get quality content right away.

A Department of Homeland Security Emeritus Center of Excellence led by the University of Maryland
A consortium of researchers dedicated to improving the understanding of the human causes and consequences of terrorism

Al-Qaida and Affiliated Movements

Bioterrorism

Chemical Threats

Community Resilience

Conflict Management and Negotiation

Crisis Communication and Management

Cybersecurity and Cyberterrorism

Ecoterrorism

Emergency Preparedness and Management

Ethnic Conflict and Violence
Foreign Fighters
Geographic Information System (GIS)

Global Security

Group Behavior

Homeland Security Education and Training

Innovation and Technology

International Relations

Islamic State of Iraq and the Levant (ISIL)

Leadership in Violent Extremist Organizations

Left-wing Terrorism

Media and Terrorism

Natural Hazards

Not Terrorism Related

Nuclear Terrorism

Policing Terrorism

Political Conflict and Violence
Psychology of Terrorism

Public Communications and Warnings

Punishment of Terrorism

Radiological Threats

Red Teaming

Right-wing Terrorism

Risk Management

Scenario Planning and Forecasting

Security Policy

September 11th

Single-issue Terrorism

Social Media

Suicide Attacks
Terrorism and Economics

Terrorism Databases and Resources
Terrorism Trends

Terrorist Networks

Threat Assessment

Victims of Disasters

Violence Adoption and Desistance
Weapons and Tactics
Start in the news, media contact.
Deanne Winslett Communications and Transition Manager 301-405-6632 [email protected]
Contact us Online Find an Expert
Advertisement
Computational techniques to counter terrorism: a systematic survey
- Published: 03 June 2023
- Volume 83 , pages 1189–1214, ( 2024 )
Cite this article
- Jaspal Kaur Saini 1 &
- Divya Bansal 2
288 Accesses
2 Citations
Explore all metrics
Terrorist Network Analysis (TNA) is the field of analyzing and defining the scope of terrorism and researching the countermeasures in order to handle exponentially increasing threats due to ever growing terrorist based activities. This field constitutes several sub-domains such as crawling the data about terrorist attacks/groups, classification, behavioral, and predictive analysis. In this paper we present a systematic review of TNA which includes study of different terrorist groups and attack characteristics, use of online social networks, machine learning techniques and data mining tools in order to counter terrorism. Our survey is divided into three sections of TNA: Data Collection, Analysis Approaches and Future Directions. Each section highlights the major research achievements in order to present active use of research methodology to counter terrorism. Furthermore, the metrics used for TNA analysis have been thoroughly studied and identified. The paper has been written with an intent of providing all the necessary background to the researchers who plan to carry out similar studies in this emerging field of TNA. Our contributions to TNA field are with respect to effective utilization of computational techniques of data mining, machine learning, online social networks, and highlighting the research gaps and challenges in various sub domains.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions

Similar content being viewed by others

Fake news, disinformation and misinformation in social media: a review
Esma Aïmeur, Sabrine Amri & Gilles Brassard

Cyber risk and cybersecurity: a systematic review of data availability
Frank Cremer, Barry Sheehan, … Stefan Materne

Online social networks security and privacy: comprehensive review and analysis
Ankit Kumar Jain, Somya Ranjan Sahoo & Jyoti Kaubiyal
Abbasi A, Chen H (2005) Analysis to extremist- messages. Intell Syst IEEE 20(5):67–75
Article Google Scholar
Agrawal R, Srikant R (1994) Fast algorithms for mining association rules. Proc 20th int conf very large data bases, VLDB. vol 1215
Allanach J, Tu H, Singh S, Willett P, Pattipati K (2004) Detecting, tracking, and counteracting terrorist networks via hidden markov models. In: IEEE Aerospace Conference, pp 3246–3257
Allister D, Ipung HP, Nugroho SA (2010) Text classification techniques used to faciliate cyber terrorism investigation. In: 2nd International conference on advances in computing, control, and telecommunication technologies
Apollo Social Sensing Toolkit (2020) [Online]. Available: http://apollo2.cs.illinois.edu/index.html
Archetti F, Djordjevic D, Giordani I, Sormani R, Tisato F (2014) A reasoning approach for modelling and predicting terroristic attacks in urban environments. In: Security Technology (ICCST), 2014, pp 1–6
Asongu SA, Orim S-MI, Nting RT (2019) Terrorism and social media: global evidence. J Global Inf Technol Manag 22.3:208–228
Google Scholar
AutoMap: Project — CASOS (2016) [Online]. Available: http://www.casos.cs.cmu.edu/projects/automap/ . [Accessed: 08 May 2016]
Baraldi A, Blonda P (1999) A survey of fuzzy clustering algorithms for pattern recognition. IEEE Trans Syst Man Cybern Part B 29(6):778–785
Berzinji A, Abdullah FS, Kakei AH (2003) Analysis of terrorist groups on facebook. In: 2013 European intelligence and security informatics conference analysis, p 7695
Best DM, Northwest P (2015) Clique: Situational awareness. IT Prof 117(August):66–68
Bhattacharyya S, Jha S, Tharakunnel K, Westland JC (2011) Data mining for credit card fraud: A comparative study. Decis Support Syst 50(3):602–613
BioWar: Project — CASOS (2016) [Online]. Available: http://www.casos.cs.cmu.edu/projects/biowar/ . [Accessed: 08 May 2016]
Brajawidagda U, Reddick CG, Chatfield AT (2016) Social media and urban resilience: A case study of the 2016 Jakarta terror attack. In: Proceedings of the 17th International digital government research conference on digital government research
Brynielsson J, Sharma R (2015) Detectability of low-rate HTTP server DoS attacks using spectral analysis. In: 2015 IEEE/ACM International conference on advances in social networks analysis and mining, pp 954–961
Burke R, Mobasher B, williams C, Bhaumik R (2006) Classification features for attack detection in collaborative recommender systems. In: KDD ’06 Proceedings of the 12th ACM SIGKDD international conference on Knowledge discovery and data mining, pp 542–547
Cao L, Member S, Zhao Y (2008) Mining Impact-Targeted activity patterns in imbalanced data. IEEE Trans Knowl Data Eng 20(8):1053–1066
Chen J, Li B (2009) Random forest for relational classification with application to terrorist profiling. In: Granular computing, 2009, GRC ’09. IEEE International Conference, pp 630–633
Chen J, Xu J, Chen P, Ding G, Lax RF, Marx BD (2008) Fuzzy clustering and iterative relational classification for terrorist profiling. In: Granular Computing, 2008. GrC 2008. IEEE International Conference on, pp 142–147
Coffman TR, Suite JR, Marcus SE (2004) Dynamic classification of groups through social network analysis and HMMsl. 2. In: IEEE Aerospace conference proceedings dynamic classification of groups through social network analysis and HMMsl.2 Thayne R. Coffman 2 1” Century technologies, Inc. 11675 Jollyville Rd Suite 300 Austin, TX 78759 tcoffman@2 1 technologies.com 5 12-342-00 I , pp 1–9
Dark Web Forums (2016) [Online]. Available: http://www.azsecure-data.org/dark-web-forums.html . [Accessed: 08 May 2016]
Dark Web Project (2016) [Online]. Available: http://www.azsecure-data.org/about.html . [Accessed: 08 Feb 2016]
David Liben-Nowell JK (2013) The link prediction problem for social networks. Int Rev Res Open Distance Learn 14(4):90–103
Desmarais BA, Cranmer SJ, Hill C, Carolina N (2011) Forecasting the locational dynamics of transnational terrorism:, a network analytic approach. In: European intelligence and security informatics conference, pp 171–177
Deylami HA (2015) Link prediction in social networks using hierarchical community detection. In: IKT2015 7th International conference on information and knowledge technology, pp 1–5
Dhote Y, Mishra N (2013) Survey and analysis of temporal link prediction in online social networks. In: International Conference ondvances in Computing, Communications and Informatics (ICACCI), pp 1178–1183
Dickerson JP (2011) Dealing with Lashkar-e-Taiba: A multi-player game-theoretic perspective. In: 2011 European intelligence and security informatics conference, pp 354–359
Dimensions AT (2015) Security QoS profiling against cyber terrorism in airport network systems. In: 2015 International Conference on Cyberspace Governance (CYBER-ABUJA), pp 241–251
Duman E, Ozcelik MH (2011) Expert Systems with Applications Detecting credit card fraud by genetic algorithm and scatter search. Expert Syst Appl 38(10):13057–13063
Duo-yong S (2011). In: Intelligence and Security Informatics (ISI), 2011 IEEE International Conference on, no 70973138, pp 373–378
DyNetML— CASOS (2016) [Online]. Available: http://www.casos.cs.cmu.edu/projects/dynetml/ . [Accessed: 08 May 2016]
Engene JO (2006) The data set Terrorism in Western Europe: Events Data, or TWEED for short, was constructed and collected for the purpose of analysing patterns of terrorism in Western Europe as related to historical and structural preconditions (see Jan Oskar Engene: Eur. [Online]. Available: http://folk.uib.no/sspje/tweed.htm
Fire M, Tenenboim L, Lesser O, Puzis R, Rokach L, Elovici Y (2011) Link prediction in social networks using computationally efficient topological features. Proceedings - 2011 IEEE Int Conf Privacy, Secur Risk Trust IEEE Int Conf Soc Comput PASSAT/SocialCom 2011:73–80
Fu J, Sun D, Chai J (2012) Multi-factor analysis of terrorist activities based on social network. In: 2012 5th International conference on business intelligence and financial engineering multi-factor, pp 476–480
Goldstein BH (2006) Modeling, IEEE Spectr, no September, pp 26–34
Goyal T, Saini JK, Bansal D (2019) Analyzing behavior of ISIS and Al-Qaeda using association rule mining. In: Proceedings of 2nd International conference on communication, computing and networking, Springer, Singapore
Guohui LI, Song LU, Xudong C, Hui Y, Heping Z (2014) Study on correlation factors that influence terrorist attack fatalities using Global Terrorism Database. In: 2014 International symposium on safety science and technology study, pp 698–707
Haglich P, Rouff C (2010) Detecting emergence in social networks. In: IEEE international conference on social computing/IEEE international conference on privacy, security, risk and trust, pp 693–696
Hogan B (2011) Visualizing and interpreting facebook networks
Hsiao H, Lin CS, Chang S (2009) Constructing an ARP attack detection system with SNMP traffic data mining. In: Proceedings of the 11th international conference on electronic commerce. ACM, pp 341–345
Huang Z, Chen H, Yu T, Sheng H, Luo Z (2009) Semantic text mining with linked data. In: 2009 5th International joint conference on INC, IMS and IDC, pp 338–343
Huillier GL, Huillier GL, Alvarez H, Aguiler F, Aguilera F (2010) Topic-based social network analysis for virtual communities of interests in the dark web topic-based social network analysis for virtual communities interests in the dark web. In: ACM SIGKDD Workshop on intelligence and security informatics, p9, pp 66–73
International Terrorism: Attributes of Terrorist Events (ITERATE) (2016) [Online]. Available: http://www.icpsr.umich.edu/icpsrweb/DSDR/studies/07947#datasetsSection . [Accessed: 08 Feb 2016]
JDK (2016) [Online]. Available: http://www.oracle.com/technetwork/java/javase/downloads/index.html . [Accessed: 07 May 2016]
Jan G (2011) Visual investigation of similarities in global terrorism database by means of synthetic social networks. In: Computational Aspects of Social Networks (CASon), 2011 International Conference on, IEEE, 2011, pp 255–260
Jayaweera I, Sajeewa C, Liyanage S, Wijewardane T, Perera I, Wijayasiri A (2015) Crime analytics: Analysis of crimes through newspaper articles. In: 2015 Moratuwa Eng Res Conf, pp 277–282
Jin L, Diego S, Chen Y (2013) Understanding user behavior in online social networks: A survey, no September, pp 144–150
Johnson CW (2005) Applying the lessons of the attack on the world trade center, 11th september 2001, to the design and use of interactive evacuation simulations. In: Proceedings of the SIGCHI conference on Human factors in computing systems. ACM, 2005, pp 651–660
Katipally R, Cui X (2010) Multistage attack detection system for network administrators using data mining, pp 0–3
Kaur A, Saini JK, Bansal D (2019) Detecting radical text over online media using deep learning. arXiv: 1907.12368
Kengpol A, Neungrit P (2014) A decision support methodology with risk assessment on prediction of terrorism insurgency distribution range radius and elapsing time: An empirical case study in Thailand. Comput Ind Eng 75:55–67
Klausen J (2016) The role of social networks in the evolution of Al Qaeda-inspired violent extremism in the United States, 1990-2015 Brandeis University
Krause L, Lehman L, Wheeler A, Drive S (2003) A family of agent based models
Lautenschlager J, Ruvinsky A, Warfield I, Kettler B (2015) Group profiling automation for crime and terrorism (GPACT). Procedia Manuf 3(Ahfe):3933–3940
Liu Z, Xin L, Peng P (2011) Comparison of two mathematical models for predicting the fallout hazard from terrorist nuclear detonations. In: International conference on electronic & mechanical engineering and information technology, pp 4007–4009
Moon I, Carley KM (2007) Modeling and networks in social and Geospatial dimensions
Mannes A, Michael M, Pate A, Sliva A, Subrahmanian VS, Wilkenfeld J (2008) Stochastic opponent modeling agents: A case study with hezbollah, Soc Comput Behav Model Predict no. September 2002, pp 37–45
Mannes A, Shakarian J, Sliva A, Subrahmanian VS (2011) A computationally-enabled analysis of lashkar-e-taiba attacks in jammu & kashmir. In: 2011 European intelligence and security informatics conference, pp 224–229
Mason R, Mcinnis B, Dalal S (2012) Machine learning for the automatic identification of terrorist incidents in worldwide news media, pp 84–89
Mathieu B, Truong P, You W, Labs O (2012) Information-centric networking: A natural design for social network applications, no July, pp 44–51
McKerlich R, Ives C, McGreal R (2013) Uncovering the darkweb: A case study of jihad on theWeb. Int Rev Res Open Distance Learn 14(4):90–103
Miller RR (2002) Viewpoint Information Management in, vol 45, no 9, pp 31–33
Mitchell TM (1997) Machine learning, no 1
NODEXL (2007) [Online]. Available: http://www.smrfoundation.org/tools/
National Consortium for the Study of Terrorism and Responses to Terrorism (START) (2015) GTD Global terrorism database, START. p 63
Ngai EWT, Hu Y, Wong YH, Chen Y, Sun X (2011) The application of data mining techniques in financial fraud detection: A classification framework and an academic review of literature. Decis Support Syst 50(3):559–569
Nguyen LT, Wu P, Chan W, Field M (2012) Predicting collective sentiment dynamics from time-series social media. In: WISDOM ’12 Proceedings of the 1st international workshop on issues of sentiment discovery and opinion mining
ORA-LITE: Software — CASOS (2016) [Online]. Available: http://www.casos.cs.cmu.edu/projects/ora/software.php . [Accessed: 08 May 2016]
Ozgul F, Atzenbeck C, Erdem Z (2011) How much similar are terrorists networks of Istanbul?. In: 2011 International conference on advances in social networks analysis and mining how, pp 468–472
Ozgul F, Erdem Z, Bowerman C (2009) Prediction of past unsolved terrorist attacks, pp 37–42
PHP: Hypertext Preprocessor (2016) [Online]. Available: https://secure.php.net/ . [Accessed: 07 May 2016]
Pagán JV (2010) Improving the classification of terrorist attacks a study on data pre-processing for mining the global terrorism database. In: 2010 2nd International Conference on Software Technology and Engineering(ICSTE) Improving, pp 104–110
Pavel A (2005) Responding to terrorist attacks and natural disasters: a case study using simulation. In: Winter simulation conference, pp 886–894
Projects - Construct — CASOS (2016) [Online]. Available: http://www.casos.cs.cmu.edu/projects/construct/ . [Accessed: 08 May 2016]
Projects - OrgAhead — CASOS (2016) [Online]. Available: http://www.casos.cs.cmu.edu/projects/OrgAhead/ . [Accessed: 08 May 2016]
Python Programming Language (2016) [Online]. Available: https://www.python.org/ . [Accessed: 07 May 2016]
R (2016) The R project for statistical computing. [Online]. Available: https://www.r-project.org/ . [Accessed: 07 May 2016]
R. C., DARPA (2019) RDWTI — RAND [Online]. Available: http://www.rand.org/nsrd/projects/terrorism-incidents.html
Rejaie R, Torkjazi M, Valafar M, Willinger W (2010) Sizing up online social networks. Network, IEEE 24(5):32–37
START (2005) MAROB. [Online]. Available: http://www.cidcm.umd.edu/mar/mar_data.asp
START (2020) Global Terrorism Database. [Online]. Available: http://www.start.umd.edu/gtd/
Sang J, Deng Z, Lu D, Xu C (2015) Cross-OSN user modeling by homogeneous behavior quantification and local social regularization. IEEE Trans Multimed 17(12):2259–2270
Sardarnia K, Safizadeh R (2019) The internet and its potentials for networking and identity seeking: A study on ISIS. Terror Political Violence 31.6:1266–1283
Scanlon JR, Gerber MS (2014) Automatic detection of cyber-recruitment by violent extremists. Secur Inform 3(1):1–10
Schreck T, Keim D (2013) Visual analysis of social media data, pp 68–75
Serra E, Subrahmanian VS (2014) A survey of quantitative models of terror group behavior and an analysis of strategic disclosure of behavioral models. IEEE Trans Comput Soc Syst 1(1): 66–88
Shen H, Member S, Li Z, Liu J, Grant JE (2015) Knowledge sharing in the online social network of Yahoo! Answers and Its Implications. IEEE Trans Comput 64(6):1715–1728
MathSciNet Google Scholar
Siegrist D (2000) Advanced information technology to counter biological terrorism. ACM SIGBIO Newsletter 20.2:2–7
Skillicorn DB (2015) Empirical assessment of al qaeda, isis, and taliban propaganda. In: Intelligence and Security Informatics (ISI), 2015 IEEE International Conference on, pp 61–66
Skillicorn DB, Spezzano F, Subrahmanian VS (2014) Understanding south asian violent extremist group-group interactions, no Asonam, pp 687–694
South Asia Terrorism Portal (SATP) (2016) [Online]. Available: http://www.satp.org/ . [Accessed: 08 Feb 2016]
Spezzano F, Mannes A (2013) STONE: Shaping terrorist organizational network efficiency. In: 2013 IEEE/ACM International conference on advances in social networks analysis and mining STONE, pp 348–355
Su P, Mao W, Zeng D, Zhao H (2012) Mining actionable behavioral rules. Decis Support Syst 54(1):142–152
Subrahmanian EVS (2012) Handbook of computational approaches to counter terrorism, Springer Science & Business Media
Suicide Attack Database (SAD) (2016) [Online]. Available: https://cpostdata.uchicago.edu/search_new.php . [Accessed: 08 Feb 2016]
Taquechel E, Guard USC (2010) Layered defense: Modeling terrorist transfer threat networks and optimizing network risk reduction, no December, pp 30–35
The crawler4j Open Source Project on Open Hub (2016) [Online]. Available: https://www.openhub.net/p/crawler4j . [Accessed: 07 May 2016]
Thuraisingham B (2004) Data mining for counter-terrorism. Data Mining:, Next Generation Challenges and Future Directions, pp 157–183
UCINET Software (2016) [Online]. Available: https://sites.google.com/site/ucinetsoftware/home . [Accessed: 08 May 2016]
Valenzuela ML, Feng C, Momen F, Rozenblit JW (2010) A non-numerical predictive model for asymmetric analysis
Visualization AW, Lee J (2008) Exploring global terrorism data: A web-based visualization of temporal data, vol 15, no 2, pp 7–14
Wang P (2014) A tale of three social networks, pp 10–15
Wang J (2014) A novel method of centrality in terrorist network, pp 144–149
Wang T, Liao G (2014) A review of link prediction in social networks. In: International conference on management of e-commerce and e-government, pp 149–152
Weil T (2015) Happened to sony happen to us?, no April
Weinstein C, Campbell W, Delaney B, Leary GO, Street W (2009) Modeling and detection techniques for counter-terror social network analysis and intent recognition
Wiil UK, Gniadek J, Memon N (2010) Measuring link importance in terrorist networks. In: 2010 International conference on advances in social networks analysis and mining. IEEE, pp 225–232
Worldwide Incident Tracking System (WITS) (2004) [Online]. Available: https://esoc.princeton.edu/files/global-terrorism-database-worldwide-incident-tracking-system
Xiong H, Wu J, Chen J (2009) K-means clustering versus validation measures: a data-distribution perspective. IEEE Trans Syst, Man, Cybern Part B 39(2):318–331
Xu R, Wunsch D (2005) Survey of clustering algorithms. IEEE Trans Neural Netw 16(3):645–678. [Online]. Available: https://doi.org/10.1109/TNN.2005.845141
Ze L, Duo-yong S, Shu-quan G, Bo L (2014) Detecting Key Individuals in Terrorist Network Based on FANP Model. In: 2014 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining (ASONAM 2014), pp 724–727
Zhou Y, Qin J, Reid E, Lai G, Chen H (2005) Studying the presence of terrorism on the web: A knowledge portal approach. In: Proceedings of the 5th ACM/IEEE-CS joint conference on Digital libraries. ACM, 2005, p 402
(2017). https://www.start.umd.edu/gtd/images/START_GlobalTerrorismDatabase_TerroristAttacksConcentrationIntensityMap_45Years.png [Date Accessed 23 Nov 2017]
Download references
This work was partially supported by Cyber Security Research Centre, Punjab Engineering College (Deemed to be University), Chandigarh, India.The author Jaspal K Saini is grateful to Visvesvaraya PhD scheme for Electronics and IT for funding this research.
Author information
Authors and affiliations.
School of Computing, IIIT Una, Una, Himachal Pradesh, India
Jaspal Kaur Saini
Punjab Engineering College (Deemed To Be University), CSRC, Chandigarh, India
Divya Bansal
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Jaspal Kaur Saini .
Ethics declarations
Conflict of interests.
The authors declare that they have no conflict of interest.

Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Saini, J.K., Bansal, D. Computational techniques to counter terrorism: a systematic survey. Multimed Tools Appl 83 , 1189–1214 (2024). https://doi.org/10.1007/s11042-023-15545-0
Download citation
Received : 29 October 2021
Revised : 18 November 2022
Accepted : 19 April 2023
Published : 03 June 2023
Issue Date : January 2024
DOI : https://doi.org/10.1007/s11042-023-15545-0
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Computational techniques
- Data science
- Data mining
- Machine learning
- Online social networks
- Terrorist network
- Find a journal
- Publish with us
- Track your research
528 Terrorism Essay Topic Ideas & Examples
⁉️ how to write a terrorism essay: do’s and don’ts, 🏆 best terrorism topic ideas & essay examples, 🥇 most interesting terrorism topics to write about, ⚡ shocking terrorism essay topics, 📌 simple & easy terrorism essay titles, 👍 good essay topics on terrorism, 💡 interesting topics to write about terrorism, ❓ terrorism essay questions.
Current-day problems, from global warming to human rights, continue to be a topical subject, urging students to address acute issues.
However, this relatability means that you, as an essay writer, may find yourself faced with conflicting facts and circumstances, which your inherent bias may affect.
Thus, a terrorism essay becomes not merely an academic endeavor, but an attempt to immerse yourself in contemporary issues with a multitude of opinions.
- Research and outline your subject beforehand. This process will not only save your time but also help you structure your thoughts and arguments coherently.
- Use tools, such as topic sentences and brainstorming techniques, in the prewriting phase of your paper. Doing so will help you understand how you would like to develop your central theme.
- Start compiling a bibliography early on. When many different viewpoints exist, creating a structured argument in favor of a particular approach may require a wide array of supporting book and journal titles.
- Give a historical overview of your issue. For example, if you are writing about global terrorism, then it is apparent that a worldwide network of violent radicals did not come into existence overnight. Acknowledge and explain the origins of your assigned issue.
- Read other’s sample essays. This action will help you gain a better understanding of what works and what does not in terrorism essay topics.
- Use terrorism essay quotations. Since this is a contemporary issue, then there are bound to be many people involved in activities to counter terrorism, survivors of attacks, and general onlookers. Utilize their perspectives and memories to give your essay a unique touch.
- Remain respectful throughout your paper. Recognize the gravity of your essay and understand the privilege you have when writing about ideas that you may not have experienced.
- Write your essay with no references. Despite watching TV coverages, listening to critics, and reading tabloids, none of us are experts on war or terrorism. Always cite the sources of your information to uphold the integrity of your work.
- Plagiarize from the work of others. While you may read essays written by your peers or those that are available online, directly copying from them is an academic offense.
- Go off point. If you are writing about the history of Al Qaeda, do not disintegrate your work into a how to stop terrorism essay. However, you may give some points in your conclusion on how the overall situation may be amended.
- Write controversial terrorism essay titles. While your title should be catchy and grab your readers’ attention, you should not resort to cheap tactics to make your headings memorable by shock value. Remember that your audience may perceive this tactic as making light of your subject, thus destroying your hard-earned credibility.
- Try to advocate for a pro-terrorist approach. While it is a sound idea to subvert some essay topics, this is not the case in such papers and your work should always be against terrorism.
- Integrate examples from unreliable sources. While readers are often less informed than the essay’s writer is, the opposite may also occur. Therefore, always check the facts, which you include in your work, to avoid embarrassment.
- Draw out your essay to stress the seriousness of the subject. Use your instructor’s specified word count as a measure for how much you should write. Your readers will not appreciate a long-winded paper, as they are hoping instead to get a quick and concise introduction to an important problem.
Want to get more inspiration on terrorism essay topics? Head over to IvyPanda!
- “To Any Would-Be Terrorists” by Naomi Shihab Nye While trying to address the extremist audience, the writer resorted to the strong methods of personification to be able to talk straight to each reading the letter. Despite the character of the text, the writer […]
- Cause and Effect of Terrorism There are several effects of terrorism that are destructive in the nature. The effects are destruction of properties, loss of lives and decline in the economy of a country.
- Terror in “The Dumb Waiter” Play by Harold Pinter Pinter exemplifies the existential view of the absurd and the non-existence in The Dumb Waiter in the same manner as that employed in Waiting for Godot by Beckett.
- Analyzing the Concept of Terrorism It is worth noting that a clear definition of terrorism is mostly subjective and is rarely objective due to the fact that it is an act of political violence.
- What Makes Terrorism Different From Other Forms of Violence The purpose of this paper is to define terrorism and identify the crucial features that distinguish terrorism from different types of abuse.
- Bioterrorism: Impact of Science and Technology The bacteria of a disease can be obtained easily and grown in a fermentor- it is also easy to build and operate one.
- The Psychological Explanation of Terrorism Therefore, most psychologists argue that in the quest to underpin the possible causes of terrorist activities, there is the need to discriminate between the motivations for joining, being retained, and disserting terrorist factions.
- Terrorism: Can Terrorism Ever Be Justified? However, it needs to be pointed out that the general action of terrorism is morally wrong, especially when considered to be a war.
- Islamic Terrorism in Ridley Scott’s “Body of Lies” As it was implied earlier, in order for us to be able to gain a better understanding of the phenomenon of Islamic terrorism, we need to make an inquiry into the very tenets of Islam, […]
- Terrorism, Hate Crimes and Racial Profiling The Patriotic Act defines domestic terrorism as an act dangerous to human life, which violates criminal laws of the USA and is aimed to intimidate the civilian population and influence the government policies through coercion […]
- Analysis of a Domestic Terrorist Group and Homeland Security Policies The Boogaloo Movement is a severe menace, and the government must take all necessary measures to put a stop to it, it is concluded.
- Suspected Terrorist Interrogation and Use of Torture Regardless, torture is still popular across the globe, and it has elicited a new debate questioning whether it is immoral and unacceptable to use torture in the case of efforts to fight terror in the […]
- Terrorism, Corruption, and Climate Change as Threats Therefore, threats affecting countries around the globe include terrorism, corruption, and climate change that can be mitigated through integrated counter-terror mechanisms, severe punishment for dishonest practices, and creating awareness of safe practices.
- Problems the US Faced in the Prosecution of the International Terrorists Differentiating a potential extremist from the rest of the population has been challenging because most international criminals interact with civilians and become part of them.
- Terrorist Impact on Maritime Transportation Security Notably, the United States established the Transportation Security Administration under the Department of Transportation, which was soon transferred to the newly formed Homeland Security Department.
- International Terrorism: Waves and Countermeasures The concept of modern terrorism emerged in Russia, and after a decade, it spread to Western Europe, the Balkans, and Asia.
- The Nexus of Homeland Security and Terrorism The Department of Homeland Security is one of the several bureaucracies formed to tackle the issues of rising insecurity due to external powers and potential facilitators within the US.
- The Future and Change of Terrorism As a result, even if terrorists get their hands on these weapons, they might hesitate to use them on individuals because of the associated implications.
- The Terrorist Attack Recovery Process Terrorism response strategies and the recovery process vary according to the scope of damages and the implications of the methods used in the terror attacks.
- Preparing for a Potential Terrorist Attack The ultimate aim of preparedness is to limit exposure to adversities during and after a terrorist attack. Thus, a recommended approach to limiting the potential security hazard of terrorist attacks is assessing its attributes and […]
- Role of Terrorism in Russo-Ukrainian War Due to this factor, one of the most influential and widespread typologies of terrorism is the New Terrorism that emerged after the tragedy of 2001 in the USA.
- Anti-Terrorism Clarification Act of 2018 Therefore, the current policies are a response to existing problems, and as the problem inside the country has become smaller, the reaction has also decreased.
- Role of Media in Terrorism and Its Force Multipliers The following passages describe the role of the media in terrorism, how terrorists use laws to their advantage, the concept of asymmetrical warfare, and force multiplier as they apply to terrorism.
- Anti-Terrorism Security Complex for Civil Aviation It is expected that the increase in the number of flights in the absence of a strengthened anti-terrorist culture should also lead to an increase in the number of unintended consequences of such flights – […]
- Terrorism: Goals and Strategies Their main purpose can range from changing the direction of the politics in the state to overthrowing the exciting government and establishing control over the population.
- Religious Terrorism: Ideologies and Methods of Al Qaeda and ISIS Strict adherence to the recorded practices and sayings of the Prophet in the letter of the Koran is emphasized. It endorses the rationalization of terrorism and violence in the efforts to fight against infidels.
- Principles of Leadership and Future of Terrorism At the present time, leadership is presented in various forms; however, the primary objectives of the model generally include the improvement of organizational performance and the enhancement of the relationships between the members.
- The 2012 Tel Aviv Bus Bombing and Crisis Management Musa was the manufacturer and detonator of the bomb, which he used Mafarji to deliver inside the Tel Aviv-based commuter bus.
- Terrorism: The Role of Social Media This paper will discuss the role of the internet in terrorist activities, with a focus on social media. In the electronic age, terrorists use social media for recruitment, training, public terror, and action.
- The Role of the Military in Domestic Terrorism Acts The video focuses on the issue of domestic terrorism in the U.S.in light of the January 6th attack on the Capitol.
- Addressing Challenges of Religious Terrorism The various methods used in religious terrorism are spiritual scriptures to justify the violent acts and the use of apocalyptic images of destruction to justify the actions.
- Terrorism and Changes in Police Management Firstly, the police and organizations related to the population’s safety prioritized the prevention of terrorism to minimize the damage. Organizing in the police station involves the creation of organizational structure, points of authority, and responsibilities.
- Terrorists’ Minds and Radicalization Processes Moreover, the models agree that radicalization is a stepwise process in which one stage or step leads to another and eventually reaches the act of terrorism.
- The Terrorism and Oil Industry Relationship Since terrorism is a source of political instability in the world, there is expected to be a positive correlation between oil prices and terrorist attacks. The purpose of this research was to examine the relationship […]
- Understanding the Definition of WMDs and the Constraints on Terrorist Acquisition The most known WMD a nuclear weapon is limited in numbers and difficult to create. The most probable WMD for terrorists to acquire are chemical weapons.
- Online Interventions Addressing Terrorism and Radicalization The study will also identify that the Sakinah campaign can be considered a suitable example of how it is possible to address Internet terrorism and radicalization.
- A Terrorism Attack in the Middle East Countries in the Middle East are prone to terrorist attacks rendering it one of the unsafest regions in the world. The importance of this study is to understand the purpose of terrorist attacks in the […]
- Behavioral Factors of Individual Terrorists The behavior of individual terrorists is dictated by the group dynamics, their mental health, and well-being, as well as the underlying incentives for joining a terrorist organization.
- The Ways Terrorists Raise and Move Money Moreover, the government has put into action the freezing orders and blocking of united states individuals who are presumed to have a hand in terrorist activities.
- Terrorism and Transnational Organized Crime as Threats to Homeland Security The US is among the nations that have suffered some of the worst terrorist attacks worldwide and it is also a hub of international criminal activities due to its wealth of resources and powerful economic […]
- Planning for Terrorist Events: Case Study To review the response of France’s forces and evaluate its efficiency To provide several recommendations for the prevention of attacks during the FIFA World Cup 2022 in Qatar Terrorist attacks that took place across Paris […]
- Global Impact of 9-11 Events on Terrorism Prevention Many people resorted to religion and faith, and the majority reported that they were praying more frequently. Moreover, it stimulated the intervention in Iraq and Afghanistan to fight terrorist groups.
- September 11, 2001 Attacks: What We Have Learned About Terrorism Since 9,11 The world has remembered one of the most tragic attacks in the USA in 2001, and the consequences of this event stay one of the most discussed.
- Global Counter-Terrorism Strategy One of the most serious problems of modern political society is the threat of terrorism, which, due to globalization, requires the unification of the international community.
- The Case of Saudi Arabia’s Soft Counter-Terrorism Strategy Therefore, this assessment is essential for government agencies, consulting organizations, and society in general, since innocent people suffer from the consequences of terrorism.
- Terrorism Prevention: Operation Geronimo Intelligence briefings had been vital in this operation, and there was sufficient evidence to show that the wanted terrorist was in the compound. In conclusion, the operation was a necessary undertaking in ensuring international peace […]
- Trump Tells Story About Killing Terrorists With Bullets Dipped in Pigs’ Blood The text reflects on Donald Trump’s recollection of the myth that terrorists were killed before the bullets used were dipped in pig blood.
- US Strategy From the Cold War to the Post-Global War on Terrorism Before the collapse of the United Soviet Socialist Republic in 1991, the United State’s strategy during the Cold War era had been one of deterrence to the potential threats of the USSR and its allies […]
- Analysis of the Terrorist Organizations: “Red Brigades” and “Boko Haram” The most famous action in the organization’s history is the abduction and murder of the former Prime Minister of Italy Aldo Moro in the spring of 1978.
- Tools Required to Intercept and Obstruct Terrorism in the US The very first section of this act is devoted to strengthening the internal security of the population of the States in the framework of countering terrorism.
- Countering Terrorism Through Innovative Approaches The vital issue of this meeting became the issue of the technological development of international terrorism, its rapid growth in the online world, and acquaintance with the most recent technologies.
- Iran’s Involvement in Sponsoring Global Terrorism Due to the particular features of the theocratic regimes, in the case of Iran, the inclination towards terrorism can be explained by two pillars of the Islamic doctrine underlining the constitution.
- Criminalistics: Forensic Science, Crime, and Terrorism These writings can be on the second, third, and so on pages, depending on the pressure on the writing subject, that is, a pen or pencil.
- Terrorism: the Victim of Terrorism and of Mechanisms to Combat It The Concept of Terrorism: Unlawful act Broad interpretations Threatening lives Generic term of terror Caused by forces opposed to the state Sociopolitical
- Countering Terrorism and Preventive Measures Considering the events of the past century, including the first and 9/11 bombing of the World Trade Center in 1993 and 2001, United States Embassy in Beirut and Kuwait bombing, and many other attacks, the […]
- Why Terrorism Is Not a Serious Threat to International and National Security We accept the existence of this threat, but we are still sure terrorism narrative as an existential threat is doing more damage to a larger amount of people than local terroristic attacks.
- An Analysis of Terrorist Activities The main terrorist attack of al Qaeda was the 9/11 Bombing of the World Trade Centers, claiming the lives of thousands of people and leading to the beginning of the War on Terror.
- Biowarfare and Bioterrorism: History and Origin According to Edmond and William, the dawn of bioterrorism dates back to the nineteenth century, when Louis Pasteur and Robert Koech studied and understood the basics of microbiology. Moreover, another application of biological weapons is […]
- Response to a Hypothetical Terrorist Event Prior to explicit action, the first thing to do in such a situation is to assess the environment depending on the location of terrorists and the type of attack and to outline the civilians that […]
- Biological Warfare and Agro-Terrorism However, the most important thing from which those infected with botulism die is paralysis of the respiratory muscles and the respiratory failure that follows. The bacteria Bacillus Anthracis, which causes anthrax, is one of the […]
- Terrorism Impacts on Policing in Belgium Nevertheless, when studying the world experience of countries facing the threat of high extremist activity and falling victim to attacks by militant fanatics at the beginning of the 21st century, the Belgian government has strengthened […]
- Researching of Morals of Terrorists Terrorism attacks are a form of violence, and the moral implication is death in the form of revenge. Realism is a form of acceptance that everyone on the battlefield is a civilian with their families.
- The Structures, Motivations, and Qualities of Terrorist Groups This implies that the structures of terrorist groups are determined by the capacity and character of the government and society where they operate.
- The Functionalism Theory Assumptions of Terrorism The functionalism theory echoes the candid assumptions of terrorism and further resonates with the evolving terrorism threat. As Barkan outlines, the functionalism perspective postulates that terrorism creates social bonding and solidarity within societies at war.
- Terrorism: Cargo and Passenger Screening To avoid such events, security systems need to be improved by the management both in the field of technological equipment and in the training of professionals.
- The United Kingdom’s Strategy for Countering Terrorism The objectives of this strategy are the prevention of radical manifestations in the fields of labor, law, politics, science and education, culture and sports, communication, and healthcare. In addition, it is characterized by legal information […]
- Motivations of Lone-Wolf Terrorists The phenomenon of lone-wolf terrorism is an interesting one because it challenges one to attempt to understand the motivation of a person to commit a violent criminal act knowing of the severe consequences.
- Public Policy Issue: Domestic Terrorism At the same time, proponents of the policy argue that the rise of domestic terrorism is due to the failure of holding accountable and confronting the perpetrators by the responsible authorities and not a case […]
- Radicalization and Terrorism in the United States The individuals or self-proclaimed bombers are one of the major threats that the USA will have to be on the lookout for most of the time.
- America: Racism, Terrorism, and Ethno-Culturalism The myth of the frontier is one of the strongest and long-lived myths of America that animates the imagination of the Americans even to this day.
- Domestic, Transnational, and Maritime Terrorism All types of terrorism are based on the forcible imposition of a worldview, ideology, morality, politics using violence, threats of murder or other forms as the primary means of achieving goals.
- “Terrorism” Is a Biased Term According to Bin Ladin, the bombing of the World Trade Center was an intimidation technique targeting the Americans due to the violence against the Islamic community.
- Terrorism and Data Mining Algorithms However, this is a necessary evil as the nation’s security has to be prioritized since these attacks lead to harm to a larger population compared to the infringements.
- Cyber-Terrorism and International Interventions Most of the cyber-attacks that have occurred involve the direction of the malware and attacks to specific critical systems and Information Technology infrastructures.
- Terrorism and Media Coverage In that regard, the issue of media coverage is specifically important to consider in situations involving hostages, as the media either covering a news report or responding to the terrorists’ demands is in a position […]
- Airfreight Security Breaches and Terrorism The majority of terrorist attacks happened after the 1990s, thereby indicating the deterioration of the security system and breaches in it.
- Terror and Religion One of the common religious terror activities has been on martyrdom, the practice of causing death to oneself on the basis of being a witness to ideological and theological perspectives and beliefs.
- Encryption, Stenography & Cyber Criminal Terrorist The internet and the ICT system as a whole are vulnerable to cyber attacks. This is the method of using to trademark to protect our images and copyright on our intellectual properties.
- Radicalization and Terrorism Phenomena A precursor to radicalization and terrorism is the lack of proper socio-political integration of certain communities in countries. Radicalization lies at the heart of terrorism and plays a central role in the propagation of ideas.
- Boko Haram Terrorist Organization: History and Facts Since the inception of the organization in 2002, the primary goal of Boko Haram has been to impose Islamic rule in Nigeria by promoting a version of the religion that forbids participation in any social […]
- Local Efforts to Counter the Terror Threat in New York City The program encompasses a series of both current and future policy efforts that are associated with the private sector security as well as counterterrorism in the state.
- Cyber-Terrorism and Healthcare Information Systems – Past, Present, and Future The cyber appliances in the health sector then again sustain correspondence amongst shareholders and service providers and as well support resources management.
- Bioterrorism Response by Healthcare Organizations Bioterrorism is a frequently used term that proves human responsibility on the development of its outcomes and effects on people and other living beings on Earth.
- Response to Terrorist Attacks: The Role of Military and Public Sector Entities Nevertheless, to understand the basis of such partnership, one has to understand the actions that the public sector takes and has taken to respond to terrorism in the United States and globally.
- Terrorism: What Is It and How to Counter It? Counterterrorism is one of the goals of international cooperation and is an activity aimed at preventing and combating terrorism. One of the most important areas of action is also to prevent the radicalization of both […]
- Emergency Operations in Case of Radiological Terrorism An excellent example of an explosion that profoundly affected the Americans is the 9/11 attack that led to the destruction of the Twin Towers and the Pentagon.
- Command Structure of Sharing the Information About Possible Acts of Terror Following the infamous events of 9/11, the government of the United States introduced new strategies and roles that have continued to reshape the roles and involvement of law enforcers in cases of terrorism.
- Bio-Terrorism: When Microbes Become a Threat to Human Existence In general, due to the cooperation of scientists, policymakers, and public agencies across the globe, the international community has recognized the potential of biological weapons and is prepared for the majority of threats.
- How Terrorism Impacts the Human Experience From the point of view of modern definitions or attempts to define these phenomena, the difference is most often established in the globality of the character, duration of the act, and the number of actors […]
- Annotated Bibliography About Terrorism This is a book review article written by Khanna on the book “Terrorism as a war” written by Walter Laqueur and published by Continuum Books.
- Cyberterrorism, Competing Factions, and Possible Course of Action Various aspects can be analyzed concerning cyberterrorism, competing factors, and possible course of actions in corporations to show that cyberterrorism is a legitimate option for the expression of grievances by terrorists.
- Importance of Emergency Response to Terrorist Attack According to the scenario presented, it makes sense to involve the DoD since the terrorists, supposedly AWOLs, pose an extreme threat to the lives of civilians and the military.
- National Response to Terrorism & Natural Disaster The National Response Framework governs the national security and crisis response to dynamic emergencies and natural disasters that occur in the community.
- Terrorism: Definitions, Features Shared by Terrorists However, since there is no agreed-upon definition of a terrorist attack, it is possible to state that some incidents were omitted from the statistics. Terrorism is difficult to combat and requires the input of international […]
- Alienation and Solidarity: The Logic of Suicide Terrorism Pape’s “The Strategic Logic of Suicide Terrorism” discusses the growing prevalence of suicide attacks in the arsenal of terrorist movements from 1980 onward.
- Terrorists and Their Rights Under US Laws The key problems of the research are the ways in which Islamists are protected by the US legislation and society, where the threat comes from, and what the consequences might be.
- Anti-Terrorism Protocol and Counter-Terrorism Units The 1995 Tokyo sarin attack is a case in point because it proved the real possibility of such a scenario and was used as the reference for the L.A. First of all, as shown in […]
- Oklahoma City Bombing as Domestic Terrorist Act The federal building housed the offices of various government agencies, including the Bureau of Alcohol, Tobacco, and Firearms, which was directly involved in the Waco debacle. The attack allowed McVeigh to send a message to […]
- Foreign Fighters and Contemporary Terrorism Finally, recruiters have received access to the vulnerable groups directly, which is demonstrated in the book In the Skin of a Jihadist written by an investigative journalist Anne Erelle.
- Terrorist Attacks: Paul Hanson vs. Patrick Crusius He made some preparations in the form of stockpiling weapons and researching the locations in which they reside. Crusius was more discrete in his information gathering, though it was still the failure of the FBI […]
- Terrorism Liaison Officer’s Responsibilities The analyst was involved in the assessment of the case and contributed to false-positive reporting regarding the journalist and other civilians being terrorists.
- Domestic Security Agencies and Cyberterrorism Thus, it can be concluded that terrorism and cyberterrorism have become one of the many global challenges, and for this reason, they should be the object of close attention to the world community.
- Terrorism in the United States of America The group might disintegrate in the future because of its dwindling number of followers, leadership wrangles, and a lack of finances to fund its activities.
- Identifying Terrorism-Related Situations In the selected setting of Philadelphia, the general environment appears to be in control, yet further measures may need to be undertaken to prevent the instances of protests from reaching a state of havoc.
- Task Force and the Fusion Center: Terrorism Prevention Thus, it can be argued that the main task of JTTF in targeted violence prevention is crime investigation and intelligence generation.
- Fusion Centers: The Role in Terrorism Prevention Boston Globe reports that the information-sharing system currently in use is not efficient in preventing terrorism, highlighting the fact that the FBI and the CIA probes of Tamerlan Tsarnaev were unbeknown to Massachusetts counterterrorist units.
- DHS and Intelligence: Terrorism The organization of the fight against terrorism requires a comprehensive approach to the analysis of the sources and subjects of terrorist activity, a clear definition of the functions and areas of responsibility of each item […]
- The Molly Maguires as a Domestic Terrorism Group It is these origins of the Molly Maguires terrorist group that gave them their thirst for blood and led to the killing of a myriad of Irishmen until the group was exterminated in the proximities […]
- Australian Anti-Terrorism Laws In the quest to protect citizens, some governments have gone to the extend of inflicting torture on terror suspects in need to obtain some information from the suspect, which raises concern about the suspect’s civil […]
- Bioterrorism Preparedness and Public Health Response Therefore, the current state of the preparedness cannot be estimated as high or sufficient, and the approach needs to be elaborated.
- Aggressive Behavior Among the Al-Shabaab Terrorists The former are the underlying sources that propel susceptible individuals to radicalization, while the latter are the incentives that the terrorist groups offer to attract and retain recruits.
- War on Terrorism: Budget and Policy Discussion The discussion of the specific Acts and Policies directed at USA security is going to be considered with the purpose to follow the changes which occurred in the USA after 9/11 attacks.
- Criminology: Terrorism–Security Policy for Large Events This attack proved to the government the vulnerability of the state concerning external threats, especially because, prior to the attack, the customary means of attack had been the use of military force as evidenced in […]
- Causes of Terrorism Terrorism is defined as violent actions that are aimed at instilling fear to people as a means of coercing them to submit to ideologies of a certain group.
- Violent Resistance and Terrorism The following study is an attempt to establish the root causes of violent resistance, the challenges facing the world due to violent resistance, and possible remedies to the problem citing specific cases that are helpful […]
- Terror Groups – Abu Nidal Organization Abu Nidal is the Arabic meaning of ‘father of the struggle.’ The terror group was named after its leader and founder Sabri al-Banna who was born in Palestine to a land owning family. Among the […]
- Impacts of Terrorism on Police Mission in the U.S. The incidence of September 11 2001 has remarkably transformed the police force in the U.S. There is an increase in the level of monitoring of international travels and boundaries by the police force.
- Homeland Security: Digital Crime and Terrorism Activities However, the US law enforcement system is characterized by the activities of different agencies, including the Federal Bureau of Investigations, Department of Homeland Security, Secret Service, Immigration and Customs Enforcement.
- Understanding the Basics of Terrorism On the other side of the rail is another man lying flat on the ground with a sniper rifle in his hands ready to wreak havoc.
- “Policing Terrorism” by Waddington He is of the argument that case-specific policing is focused on the outcome of court verdicts. He points out an incident in which the palace security was breached, and the commissioner of police reacted to […]
- Definite Paths to Terrorism: Main Dimensions This assimilation is enforced by the use of violence to instil discipline and loyalty in the participants. In conclusion, there are other dimensions of the Islamic terrorism namely Al-Qaeda and Hezbollah.
- War on Terror: Propaganda and Freedom of the Press in the US There was the launching of the “Center for Media and Democracy”, CMD, in the year 1993 in order to create what was the only public interest at that period. There was expansive use of propaganda […]
- Terrorism and U.S. National Security Thomas Jefferson was the author of the Statute of Virginia for religious freedom in the year 1777 as well as the author of the famous United States Declaration of independence in the year 1776.
- Domestic Terrorism Trends: Challenges of the Coming Years Under the provisions of the US PATRIOT act, acts of domestic terrorism entail dangerous acts that pose a threat to human life and amount to a violation of various criminal laws of the US and/or […]
- Organizations Convincing to Become a Suicide Terrorist One of the underlying tenets taught to candidate suicide bombers is: “Islam is the answer and jihad is the way”. Pathological altruism refers to any behavior or personal tendency in which ‘the goal or motivation […]
- Bioterrorism: Term Review According to Meinhardt, “water supplies and water distribution systems represent potential target for terrorist activity in the United States because of the critical need for water in every sector of our industrialized society”.
- US & UK Human Rights While Countering Terrorism The threat of terror and the further legal reactions of the nations to the problem were considered as challenging, and it is necessary to examine differences and similarities associated with the promotion of human rights […]
- Organizational Change: Models Influencing American Terrorism This paper seeks to discuss the three models of terrorism, the effects of international terrorism locally, and the impacts of international terrorism on local cell groups.
- The Goal of a Terrorist Attack This objective is being accomplished by the mean of exposing people to the graphic accounts of terrorist acts-in-making, as was the case with the attacks of 9/11.
- Local Response to Terrorism Local response to terrorism involves using the resources and the law enforcement officers at the state and county level to detect and prevent acts of terror.
- Adjusting to Terrorism: The Issue of Detention Without Trial The country also needs to train more prosecutors and legal experts so that justice is disseminated to suspected terrorists who continue to be held at Guantanamo Bay without trial.
- Biological Terrorism: Dealing With the Threat It is therefore the responsibility of the recipient of this information to take action to secure his/her life against the potential lethality of the agent in question.
- The Maritime Terrorism Risk and Liability The research describes in detail aspects of maritime terrorism but does not clearly state the research question to be explored. However, in the summary part of the research paper there is several questions implied as […]
- Bioterrorism Preparedness in Healthcare Organizations It is also necessary to carry out a test on the public health emergencies for this would help the department to be aware of the strengths and weaknesses which are in the system.
- Adjusting to Terrorism In the US, the Department of Homeland Security is the primary body that deals with all matters of homeland security, including the prevention of terrorism. As such, the department needs to address it as a […]
- Impact of Terrorism on the Economy The premise of the essay is to evaluate the nature and the nature and the severity of the risks posed by terrorism on IFAD a United Nations specialized agency.
- A Criminal Justice Approach to Suppressing Terrorism The threat of terrorism substituted communism as the rationale which was used for justifying the state of emergency in America prior to 1990s.
- Comparison Between Organized Crime And Terrorism Organized crime refers to unlawful activities conducted by members of highly organized gangs and associations. Its defined by members and activities of a group.
- Boilover: Fire Aspects of the World Trade Center Terrorist Attacks Analysis These includes the intensity of the incident heat on the burning object, the composition of the burning fire, the ability of air that supports combustion to reach the burning fire, the mass of the burning […]
- Secure Transportation System Against Global Terror The good news is that cooperation, coordination, and new technology can be used to secure the global transportation system and halt the activities of terror groups.
- Sharing Terror Data: Criminal Analysis The FBI continuing investigation of the attacks to identify the hijackers and their sponsors, codenamed “PENTTBOM,” represents the largest investigation ever in the history of the agency.
- Torture and War Towards Terrorism An example of mental torture can be explained by the following; Y is a friend to X, they have been caught in the same crime act, Y is then taken to a separate room adjacent […]
- Women and Terrorism Relations The role of women in secular terrorist organizations has been more pronounced in history due to the conservative nature of religious terrorist movements, which often exclude women from their ranks.
- Investigation Methods: Terrorism and Cyber Crime The question on whether the investigations in these areas of cyber crime and terrorism to remain incident driven or to adopt strategic approach are still is of great concern to the security agencies and the […]
- Terrorism: Assessing the Past to Forecast the Future The terrorists groups all over the world, having the knowledge of lethargic weapons held by their enemies, are engaged in the discoveries of how the rapidly growing technology may improve the lethargy of their current […]
- Terrorism Response Strategy The preliminary assessment is performed on the basis that before implementing any rescue operations, the hazards that are contained in the area must be positively identified and the resources available or necessary to deal with […]
- Homeland Security and Terrorism The important root causes of terrorism are mainly two: a perceived sense of social & political injustice such that the group seeks to right the wrong and, the view that violence is the only way […]
- Terrorism Preparedness and Response The third and most important step to take is to switch off the available electrical gadgets to prevent the spread of fire. Of importance to prevent such catastrophes is cooperation from citizens, media, and the […]
- Terrorism Mitigation and Risk In order to avert the danger of possible portable nuclear attacks, it is important to assess the possibility and impact of attacks in the first place.
- Terrorism Risk Assessment: Threat of Al Shabaab and Hezbollah to the USA Attacks such as those that happened outside the US and more are likely to occur due to what Hezbollah perceives as the US posing a threat to its ties with Iran.
- Four Priorities of Action for Combating Terrorism on Our Shores There is therefore the need to employ new pragmatic foreign policy steps that promote the national interest within the broader values of international peace and security if any gains are to be realized in the […]
- The Cyber Terrorism Plan and Counter Strategy The news of hacking the website of the Pentagon will immediately get the attention of the media and this message will spread everywhere at the speed of light.
- The Potential for State Sponsored Terrorism Also, he mainly tries to bring all the enemies of the United States together and he believes that the United States is a devilish country.
- Bioterrorism and Biosecurity The epidemiology of the infection is spread in the world evenly though in some of the parts there is only one form of Anthrax, for instance in the United States of America and therefore our […]
- Bioterrorism and Biosecurity – Aum Shinrikyo The Aum Shinrikyo began their attacks in 1994 in Matsumoto where they used the refrigerator truck to release sarin near the homes of three judges who were overseeing a lawsuit that was predicted to go […]
- Terrorism: A Definition and Analysis The Federal Bureau of Investigation defines terrorism as the perpetration of violence and force unlawfully against people or property with a sole aim of intimidating or coercing the government or the targeted population or any […]
- International Political Economy, Democratization, and Terrorism IPE describes the global power dynamics that control international trade and finance, fuel globalization, and wealth distribution across the globe. Sachs argues that globalization and the emergence of political economics have led to the increased […]
- Terrorism Definition at the National Level The development of a unified definition of terrorism at the global level is challenging because the domestic laws of several countries differ significantly.
- War and Terrorism in the Modern World They are used to frighten the public and pursue political goals, for example, to change the government in the country. For instance, acts of terrorism are meant to inflict fear and intimidation to put pressure […]
- Sociology. Terror and Violence Impacts A comparison between theory and the actual case is made in order to promote the claim that terror leads to mental health issues that will pursue the victims for the whole life, but such consequences […]
- US and Terrorism Relations Overview
- Agro-Terrorism: Definition and Impacts
- Terrorism and Trauma in American Literature
- War on Terror: The Battle Continues
- Terrorism Nowadays: Islamic State of Iraq and Syria
- How Terrorism Affects Airline Security
- Terrorist Networks as a Threat to the United States Today
- Consequence Management and Terrorist Attacks Analysis
- Terrorist Groups’ Establishment: The Theory of Four-Wave Terroristic Groups
- Homeland Security: Terrorism Issue
- Domestic & Global Terrorism and Its legal Aspects
- Crime Myths and Domestic Terrorism
- Terrorist Attacks in Paris, 13th November 2015
- Hue Newton: A Terrorist and a Thinker
- Impact on Terrorist Activities of Regional Governments
- Regional Terrorism: The Bali Bombing, Australian and Indonesian Responses
- How to End Terrorism: Diplomacy or Military Action?
- Terrorism: Methods and Weapons
- Terrorism: Analysis of Definitions
- Screening for Terrorist for Aviation Security
- The Role of Hashemite Kingdom of Jordan in the Fight Against Terrorism
- Terrorist Event Countering: First Responders Risk
- Financing Terrorism: Challenges and Solutions
- Hashemite Kingdom of Jordan and Terrorism
- Domestic Terrorism: Burning Social Issue
- Al Shabaab: An Intriguing Example of Islamist Terror
- Causes and Motivations of Terrorism
- Ali Al-Timimi’s Case of Terrorism
- “The Lessons of Terror: A History of Warfare Against Civilians” by C. Carr
- Biological and Chemical Terrorism: Preparedness and Response
- Legislation Related to Bioterrorism
- Israel’s Response to Munich Terror Attack
- Bioterrorism and Its Harmful Consequences
- Domestic Terrorism in USA
- The Evolution of Terrorism on the World Stage
- Terrorism and Liberal Democracy: What We Should Know
- Michael Collins and His Terrorist Method
- Biological Weapon and Bioterrorism
- War and Terrorism in Algeria
- Is Terrorism Still the Most Important Security Issue for Australia?
- Primoratz’ Definition of Terrorism
- War on Terror and Its Effect on Individual Right
- Terrorism and Modern Society
- Terrorism: An Objective Definition
- Crimes Against the State: Terrorist Attacks and Death Penalty
- “Nuclear Terrorism: Risks, Consequences, and Response” by Jim Walsh: Stimulating Ideas, Logical Organization, Engaging Voice
- Origins of Terrorism and Solutions
- Terrorists R’ Us: Different Perspectives, the Real Meaning
- Middle-East and Africa Terrorist Movements
- Terrorism in Western Europe: Finland, Denmark and England
- Most Effective Anti-Terrorist Tactics, Organizations in the World
- The History of Ku Klux Klan: A Terrorist Organization Founded in the Southern States After the American Civil War
- The Use of Counter-Terrorism Attacks During the Algerian War of Independence From F.L.N.
- History and Financing of Terrorism: From Time Immemorial to Nowadays
- Comparison Between Secular and Religious Terror
- The Origins of Modern Terrorism
- Cultural Reaction of English Civilians Against Terrorist Situations in Their Country
- Political Violence and Terrorism. Crowd Behavior
- Domestic Terrorism: The Forgotten Threat
- Is Terrorism an Act of War?: Different Types of Terrorism
- Types of Terrorism: Centers Establishment
- Sociology of Terror: Contemporary Sense
- Anti-Terrorists Tactics and Organizations
- Understanding the War on Terror in the United States
- Foreign Policy Challenges Created by the War on Terror
- The Threat of International Terrorism in Modern World
- Middle-Eastern and African Terrorist Movements
- Terrorist Organizations and Funding
- Terrorist Recruitment Process: Who Joins and Why
- Should the U.S. Use Torture on Terror Suspects?
- Nigeria – Preventing Nuclear Terrorism
- Terrorism Impact on Global Business Environment
- Terrorism. Irish Republican Army
- Community Policing and War on Terror
- Biosecurity and Bioterrorism
- Terrorism Today and Its Definition
- Religious Violence. Terror in the Mind of God by Juergensmeyer
- Terrorism and U.S. Foreign Policy by P. R. Pillar
- Palestinian Islamic Jihad: Radical Terrorism
- Money Laundering and Terrorist Finance
- Pakistan’s Double Game in the War on Terror
- Eradicated Terrorism in the World
- The Interrelation Between Terrorism and Technology
- War on Terror & Violation of Constitutional Rights
- Media and the War on Global Terrorism
- Is the Geneva Convention Applicable to War on Terror?
- Adjusting to Terrorism in Modern World
- Death Sentence to Muslim Terrorists: Should We Murder People Who Had Done the Same Before?
- How the US is Dealing with Terrorism?
- Terrorism and Security Issues Review
- “Terrorism in Latin America” by Mark Sullivan
- How Terrorist Have Financial and Recruitment Growth Since 1980
- Effects of the September 11, 2001 Terror Attacks on Sino-American Relations
- Recent Developments in the History of Terrorism
- War on Terrorism: Role of Law Enforcement
- Current Issues in Iraq and Terrorism
- War on Terror. 42-Day Detention: An Equitable Solution?
- Early Response to Weapons of Mass Destruction Terrorism
- Terrorism and the Affects on American Way of Living
- Counter Terrorism Measures in the UK
- The War on Terrorism in the United States
- United States & EU Efforts to Fight Terrorism
- Global Terrorism and State Security Measures
- American Governmnet Against the Threat of Terrorism
- Terrorism: 9/11 Conspiracy Theories
- Trends in Global Terrorism. Conflict Resolution and Iraq
- “Terrorism and Economic Security” by Robert L. Hutchings
- The War on Terror Cannot be Won
- Bioterrorism and Health Care Delivery
- Terrorism and Weapons of Mass Destruction
- Terrorism: Countering and Responding to the Treat
- Crimean Crisis and Russian State Terrorism
- Cyberterrorism as a Global Concern
- The United States and Terrorism
- Anti-Terrorist New York City Police Department Shield
- Terrorist Ideologies: Selecting a Target
- A Terrorist Attack on Atlanta, Georgia
- How Counselors Assist Survivors of Terrorism
- Fraud, Money Laundering, and Terrorism Financing
- Comprehensive Terrorist-Related Screening Procedures
- Terrorism and National Security
- Terrorism and Security Dilemma After 9/11
- International Law: Extradition of Terrorists
- The Functioning of Terrorist Groups
- Suicide Terrorism and Its Psychological Factors
- Terrorist Organization: Euskadi Ta Askatasuna (ETA)
- The Great Terror in the Factories, 1935–1938
- Workers During “The Great Terror” by R. Conquest
- “Terror and Democracy at the Age of Stalin” by Goldman
- Female Gender Role in “The Terrorist” Film
- Terrorism Studies and Framing Concept
- Terrorism as Spectacle: Extremist Propaganda
- Terror in the Mind of God by Mark Juergensmeyer
- Counter Terrorism and Public Awareness Plan
- Terrorist Organization Hezbollah: Tactics and Strategies
- The Hezbollah Terrorist Organization
- Terrorism, Social Activism and Political Violence
- “Faces of State Terrorism” by Laura Westra
- Organized Terrorism Against Government Leaders
- War on Terror and Its Victory Meaning
- Terrorism Definitions by the Global Community
- Can Terrorism Only Be Defeated by Military Means?
- Terrorism Impact on Tourism Industry After 2015
- Terrorist Attack: Contemporary Social or Cultural Issues
- Poverty as a Factor of Terrorist Recruitment
- War on Drugs and Terror and American Promise
- Hazard Vulnerability Analysis and Terrorism
- Terrorist Participation and Its Motives
- The UAE Against Money Laundering and Terrorism Financing
- Cyberterrorism as the Greatest Risk for the US
- Cultural Miscommunication and Hostility Against Muslims
- Domestic Terrorism and Homegrown Extremism in America
- The Rise of Terrorist Organisations in Post-Invasion Iraq
- Factors That Motivate to Terrorism
- Domestic Terrorism in the United States of America
- State-Sponsored and Non-State Terrorism
- Terrorism, Human Trafficking, and International Response
- Internet Crimes and Digital Terrorism Prevention
- Vietnam War vs. War on Terror in the Middle East
- Immigration Services Against Crime and Terrorism
- Ideology and Terrorism: Rights from Wrongs?
- Islamic and Christian Religion and Terrorism
- American War on Terror and Operational Strategies
- Death Penalty for Murder by Terrorism
- Local Operational Planning for Potential Terrorist Threats
- Preventing Terrorism: Strategies and Challenges
- Terrorism Preventive Measures in the United States
- Aum Shinrikyo Terrorist Group’s Activity
- Bioterrorism Attacks and Nursing Countermeasures
- Intelligence, Civil Law, and Terrorism Investigations
- Terrorism Prevention on the International Level
- Psychological Profiling in Terrorism Prevention
- Terrorism Definitions and Controversies
- Violent Extremism and Suicide Terrorist Attacks
- Al-Qaeda Emergence, Ideology, and New Terrorism
- Terror Attacks and Intelligence Community in the US
- Distressed Terrorism: Politics, Religion and Ideology
- Terrorism or Hate Crime: Similarities and Differences
- War on Terror: Critical Terrorism Studies’ Views
- Egyptian Tourism Industry and Terrorism Effects
- Terrorism and US Activities in the Middle East
- Islamic State Global Terror Threat Countermeasures
- War on Terror in Saudi Arabia and Arab Gulf States
- Saudi Arabian Lone Wolf Terrorism in 2011-2016
- Terrorist Groups: Critical Discourse Analysis
- War on Terror in Central Asia and the Caucasus
- US Intelligence to Prevent Terrorist Attacks
- Terrorism: Power of the Islamic State of Iraq and Syria Power
- Female Terrorism: Causes and Features
- Terrorism: the Evolution of ISIS
- Cyber Security’s and Counter Terrorism’ Intersection
- What Are the Global Impact of Terrorism in Business Domain?
- East African Community Counter-Terrorism Vision
- Terrorism and Torture: History and Arguments
- How Does Modern Terrorism Operate?
- Digital Media Usage to Recruit and Promote Terrorism
- Modern Terrorism and Globalization
- Stereotyping Terrorists and Mental Sanity
- Homeland Security Changes: Adjusting to Terrorism
- Propaganda: Terrorist, Government, State, Non-State
- Paternalist Terror in China in 1950-1953
- China in 1950-53: “Paternalist Terror” by J. Strauss
- Terrorist and Government Propaganda in Media
- Human Trafficking as a Terrorist Activity
- Coping with Terrorism in the USA
- Terrorism in the Middle East
- Contemporary Terrorism: The American Army Special Forces
- Conventions on Terrorism in the 21st Century
- Countering Terrorism: The US Intelligence Community
- Terrorism and Its Organisations: Al Qaeda and ISIL
- First Responders to Terrorist Attack
- Violence and Terror Definition Comparison
- The Westgate Terror Attack in Kenya
- Fighting Terrorism: “Iraqi Freedom” and “Enduring Freedom”
- Terrorist Organizations: Al-Qaeda and ETA
- Current Hurdles in Combating Terrorism
- Ethnic, Racial and Religious Profiling in Terrorism
- Halal Food and Terrorist Organizations in Australia
- Osama Bin Laden’s Role in Terror
- Hospitals Security Upgrade: Terrorist or Criminal Actions
- Homeland Security: Basque ETA Terrorist Organization
- International Counter Terrorism’ Elements
- Terrorism: Aspects, Approaches and Implications
- Use of Torture Against Terror Suspects
- Bioterrorism: Biological Agents as Weapons
- Different Methods Against Terrorism: Israel and Palestine
- Terrorism: The Islamic State of Iraq and the Levant
- Terrorism: Post-9/11 Maritime Security Initiatives in the USA
- Bio-Terrorism Preparedness and Response
- Jonathan Moreno: Bioethics After the Terror
- What is the Best Way for Fighting Terrorism According to Mortenson?
- The Advanced Community Planning in Response to the Potential Threat of Terrorism
- The Impacts of the Intelligence Reform and Terrorism Prevention Act of 2004 on the National Intelligence Community
- War on Terrorism: How to Cope With the Global Threat?
- Terrorism and the Global Economies
- The Primary Causes of Terrorist Political Violence
- Terrorism as a Serious Threat
- Rumsfeld’s Memo & The War on Global Terrorism
- Terrorism Handling in Our Life
- Defense Imperatives: “Thwarting Terrorism & Bringing Terrorists to Justice”
- Understanding the Failure of the Global War on Terrorism and Suggestions for Future Strategies
- Counter-Terrorism and the Patriot Act
- Al-Qaeda as a Terrorist Organization
- Human and Technical Intelligence in Countering Terrorism
- Financial Markets After Terrorist Assault and The Enron Financial Outrage
- Terrorism, Counter-Terrorism, and Intelligence
- Torture as a Counter-Terrorism Tool in 21st Century
- Lessons From the Mumbai Terrorist Attacks
- Proliferation of Nuclear Weapons to Rogue States and International Terrorists
- Does Poverty Lead to Terrorism?
- Terrorism and Jihadist Movement
- US Exceptionalism in Constructing and Conceptualizing a Terrorist
- American Exceptionalism in Constructing and Conceptualizing a Terrorist
- History of Cyber Terrorism
- “Monsters, Inc.” and the War on Terror
- Economic Concerns in the Aftermath of Terrorism
- Terrorism in International Relations
- Terrorism in Israel and Palestine
- Local, State, and Federal Partnerships: Terrorism
- Hezbollah: A Terrorist Organisation?
- United States Domestic Terrorism
- Impacts of the ‘War on Terror’ on Human Rights
- International Terrorism: The Challenge to Global Security
- Salafist Takfiri Terrorism
- Anti Money Laundering and Combating the Financing of Terrorism
- Weapons of Mass Destruction: The Terrorist Threat
- Terrorists’ Usage of Chemical or Biological Agents
- Cyber Security Threat Posed by a Terrorist Group
- The Effect of Terrorism on Human Rights: The Clash Between the Human Rights Advocates and Victims of Terrorism
- Eliminating Terrorism at the Domestic Level
- Terrorism, Poverty and Financial Instability
- United States War on Terror Policy
- The Real Cause of Terrorism in Palestine
- Terrorism: Searching for a Definition
- Industrial Terrorism in Modern World
- Terrorist Cells and Groups Within the Northern Region of Africa
- Terrorism as a Communication Strategy
- How the U.S. Can Combat the Terrorist Threat in Africa?
- Hypothetical Scenario of a Terrorist Attack
- NYPD Counterterrorism Program
- Terrorism Before and After the September 11 Attacks
- U.S. War in Afghanistan: Pros and Cons
- Orientalist Constructions of Muslim Bodies and the Rhetoric of the «War on Terror»
- Jemaah Islamiyah Terrorist Group
- The U.S. Government Strategies Against the Terrorist Threats
- How Readily Terrorists Can Acquire Nuclear Weapons
- Post September 11, 2001 Terrorist Attacks
- Civil Liberties, Habeas Corpus and War on Terror
- Concept of Terrorism Phenomenon in Modern World
- Handling of Bio-Terrorist Threats
- The Spectacle of Terror
- Foreign Policy: United States and Fight with Terrorism
- Law Enforcement and Terrorism
- What New Demands on Policing Have Resulted From the International ‘War on Terror’?
- Leila Khaled: Freedom Fighter or Terrorist?
- Religious and Secular Terrorism: Analyzing Differences and Points of Intersection
- “Arabic Islamic Culture” and Terrorism: Inherent Concepts or Not?
- Terrorist Acts Prevention and Aftermaths Minimization
- Torture During the Algerian War and Its Relevance on the War on Terror
- The Definition of Terrorism
- International Terrorism: The Operations of the Hezbollah
- The Kurdish Conflict in the Middle East
- The US Anti-Terrorism Efforts Are Failing
- The Media and Terrorism
- Terrorist Groups in Turkey
- Terrorism: The United States’ Involvement
- America’s War on Terrorism
- Terrorism, Its Groups and Categories
- Terrorism in Political Protest
- Impact of Terrorism on Italian Economy
- “What Is the Definition of Terrorism? And Why Is the White House Afraid of Using the Term?” by Timothy Kelly
- Habeas Corpus and the War on Terror
- Civil Liberties, Habeas Corpus and the War on Terror
- Benefits of Preparing for Emergencies and Terrorism
- Preparing for Incidents of Terrorism at the Local Level
- Domestic Terrorism in the Post 9/11 Era
- Eco-Defense and Kinds of Ecological Terrorism
- Bush Doctrine, Explanation of the Administration and War on Terror
- Moral Convictions of Terrorists
- Why Terrorism is a Contested Concept
- Presidential Powers and the War on Terror
- Agro-Terrorism: The Lessons to Learn
- Terrorism: The War on Iraq
- Stereotyping Comparison: All Italians Are in a Mob, All Jamaicans Smoke Weed, All Muslims Are Terrorists
- The Al-Qaida Terrorist Group’s Recent Happenings
- The Fight Against Terrorism by Christian and Islam Leaders
- Is Terrorism Ever Justified?
- The War on Terrorism
- The Terrorist Attacks in the United States
- The Problems of Terrorism in Modern World
- Counter-Terrorism Plans Development
- Consequence Management After the 9/11 Terrorist Attacks
- Intelligence Reform and Terrorist Prevention Act
- Terror and Terrorism
- September 11: Terror Attack and Huge Casualties
- The Concept of Terrorism
- Homeland Security: Collecting Information about Terrorism
- Terrorists and the Left and Right: Definitions & Examples
- Should the USA Use Drones to Combat Terrorism?
- How Are Terrorists Financing Their Acts of Terrorism?
- What Can History Teach Us About Terrorism?
- Why Do Americans Feel More Sympathy for Western Terrorism?
- How Can the United States of America Better Defend Itself Against Terrorism?
- Can the U.S. Prevent Future Acts of Domestic Terrorism?
- What Has Been the Effect of Globalization on Terrorism?
- How Can Businesses Cope With Terrorism?
- Can Democracy Stop Terrorism?
- Should the U.S. Government Be Scared of Cyber Terrorism?
- Why Does Western Europe Experience More Terrorism Than America?
- Are Terrorism and Globalization Linked to Politics?
- What Are the Causes of Terrorism, and How Can It Be Stopped?
- Are Muslim Communities Affected by Counter-Terrorism Legislation?
- Does American Foreign Policy Cause Terrorism?
- Does the Media Encourage Terrorism?
- Does the Terrorism Act Infringe Upon Our Human Rights?
- What Challenges Are Posed by International Terrorism to Democracy?
- How Can the Digital World Lead to a New Type of Terrorism?
- Whose Support Matters for the Occurrence of Terrorism?
- How America Prevents Terrorism?
- Does Higher Education Decrease Support for Terrorism?
- Can Foreign Aid Dampen the Threat of Terrorism to International Trade?
- Should Americans Fear Urban Terrorism?
- Can Illegal Immigration Lead to Terrorism?
- Does Distinguishing Domestic Terrorism From International Terrorism Help?
- Will the American Economy Benefit From the War Against Terrorism?
- Are Some Rights Negotiable When It Comes to Fighting Terrorism?
- Why Has Terrorism Become Such an Important Issue Over the Last 40 Years?
- Will Terrorism Lose Its Significance?
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2024, March 3). 528 Terrorism Essay Topic Ideas & Examples. https://ivypanda.com/essays/topic/terrorism-essay-examples/
"528 Terrorism Essay Topic Ideas & Examples." IvyPanda , 3 Mar. 2024, ivypanda.com/essays/topic/terrorism-essay-examples/.
IvyPanda . (2024) '528 Terrorism Essay Topic Ideas & Examples'. 3 March.
IvyPanda . 2024. "528 Terrorism Essay Topic Ideas & Examples." March 3, 2024. https://ivypanda.com/essays/topic/terrorism-essay-examples/.
1. IvyPanda . "528 Terrorism Essay Topic Ideas & Examples." March 3, 2024. https://ivypanda.com/essays/topic/terrorism-essay-examples/.
Bibliography
IvyPanda . "528 Terrorism Essay Topic Ideas & Examples." March 3, 2024. https://ivypanda.com/essays/topic/terrorism-essay-examples/.
- Civil Disobedience Essay Topics
- Al-Qaeda Ideas
- Global Issues Essay Topics
- Jihad Topics
- Crime Ideas
- Criminal Justice Essay Topics
- CyberCrime Topics
- Islam Topics
- Organized Crime Titles
- Islamophobia Paper Topics
- Nuclear Weapon Essay Topics
- Sunni Islam Paper Topics
- Torture Essay Ideas
- North Korea Titles
- Racial Profiling Essay Topics

Terrorism: Perspectives from the Behavioral and Social Sciences (2002)
Chapter: 4. recommendations for research, 4 recommendations for research.
This analysis suggests a number of areas in which systematic theoretical and empirical research—some ongoing, some new—can create, confirm, refine, and reject understandings about terrorism as a social and political phenomenon, thereby improving the knowledge base for efforts to contend with it. As is the case throughout this report, we highlight Islamic-based terrorism, but many of the research recommendations cover a wider range of terrorist activities. We present these suggested areas in the form of a numbered list.
ORIGINS, CHARACTERISTICS, AND DYNAMICS OF TERRORISM
To develop individual-level background profiles of terrorists, using as many samples of terrorists as can be made available. Entries in these profiles could include data on family background (parents’ occupations or economic circumstances, size of family, place in sibling order), education, job history, political history, circumstances of recruitment and indoctrination into terrorism, and career history as a terrorist. Such research must rely on multiple unrepresentative samples, including populations of detainees, terrorist suspects garnered from intelligence sources, and writings of terrorists themselves if available. Comparisons with like populations—persons engaged in illegal international drug trafficking, members of religious cults and extremist movements—might also prove of some use.
To assess the motivational dynamics of terrorists and the characteristics of their value systems. Extremely difficult to
conduct, this kind of research could tap data dealing with past psychological histories of terrorists, attitudes toward authority, religiosity, and history of mental disturbance, as well as psychological measures of narcissism, ambivalence, and different types and levels of psychological commitment to terrorist activities. Information could come from some of the same samples that would yield individual-level background profiles. Also useful would be applications of cognitive analysis in the field of computer science and facets of artificial intelligence to untangle and structure the constituent elements of value structures.
To examine the evidence regarding impacts of values on actions, in order to derive knowledge about factors that serve as critical drivers to transform potential or latent terrorists into overt terrorists.
To determine the types and range of structures, processes, and organizational careers of terrorist organizations.
With respect to structure, comparative studies could yield structural typologies of terrorist organizations—hierarchical or flat structure, religious or secular, types of sanctions holding them together, and types of leaders, including level of internal differentiation of leadership. Estimates of organizational effectiveness and vulnerability according to type could also be generated.
With respect to group processes, empirical study could reveal typical communication processes and breakdowns, bases of internal conflict, competition among leaders, breakdown and restoration of social control, formation of subcliques, coordination of attacks and other operations, conduct of relations with other groups and networks, and modes of contending with pressures from outside, including states in their host societies.
With respect to the careers of organizations, study could yield knowledge about conditions facilitating the formation of groups; patterns of recruitment; the role of religious and nonreligious leaders; the impact of terrorist success, failure, and inaction on organizational morale and momentum; tendencies to transform into lobbies or political parties; schismatic tendencies and their consequences; and conditions contributing to the stagnation and extinction of terrorist organizations.
With respect to the power base, it is important to determine the resources available to terrorist organizations as a way of understanding their capabilities in terms of funding, training, information, and refuge.
To develop estimates of the probability of selection of different patterns of action and different types of targets by terrorist groups. Factors to be taken into account in generating such estimates include symbolic resonance with the ideological emphases of terrorist organizations (in the Middle East, anti-Christian, anti-Israel, extreme Jewish fundamentalist, antiglobal capitalism, antisecular), terrorists’ own thinking about what kinds of events induce terror, their own strategic assessments about what kinds of events are maximally disruptive, the hopedfor political and military effects of attacks, and the degree to which different attacks are spectacular and news-generating. These kinds of estimates will be facilitated by gaining access to and systematizing work on the communication patterns, language, and idioms used by terrorists themselves.
To develop through comparative research knowledge about the relevant audiences for terrorism and modes of communicating with these audiences as a way of determining the impacts of audience on the content of communication.
To elucidate the effects of host states harboring or giving rise to terrorists, in terms of the impact of type of state (according to wealth, poverty, and political culture) and state policies (support, benign neglect, attempts to domesticate or coopt, political repression) on the sources of terrorist groups, their potential for recruitment, and the careers and effectiveness of terrorist organizations
To survey and monitor demographic trends in fertility, mortality, and nuptiality in societies likely to develop terrorist activity; to draw out implications of these patterns for their potential to generate economic and educational development and to produce classes of idle, poverty-stricken, and frustrated youth.
To develop further work on the cultural and social backgrounds to terrorism, especially different types of Islamic revivalism. This could be broken down into subtopics, such as transnational or global Islamic movements; linguistic, cultural, and contextual factors; local or regional movements; conditions that promote different types of revivalism; implications for Muslim communities in the United States; and case studies of religious-based terrorism in particular countries (Islamic as well as non-Islamic).
To conduct historical and comparative research on the effects of Western economic, political, cultural, military, and
foreign policy activities on less developed countries—by categories of countries and types of activities—as well as the short-term impact on the patterns of terrorist activities. Such research is difficult to conduct with reliability and objectivity, first, because of the limited theoretical foundations to guide such work; second, because it is difficult to isolate and trace these consequences through the fabric of the affected societies; and third, because the research topics themselves are ideologically loaded and lie at the basis of debates and political divisions in American society. It is also important to examine the current influences across developing countries—shaped by common historical experiences with the West—that may be used to encourage the diffusion of terrorism.
Cutting across all the above types of research is the methodological need to systematize and allow ease of access to different types of data and databases—such as these exist—that may be related to different facets of terrorism. These tasks are formidable because many of these data appear in different languages, are gathered for a great diversity of purposes, and are not immediately comparable with one another.
RESPONSES TO TERRORISM
To evaluate warning systems. Comparative empirical studies of past disaster and terrorist situations should attempt to evaluate the respective consequences of effective warnings, failures to warn, miswarnings (false alarms), and overwarning.
To monitor immediate responses to disasters. Most disasters are both sudden and ephemeral, and immediate responses give way quickly to a wide variety of recovery and rebuilding activities. Relevant research agencies (universities, think tanks, government) should establish the capacity to move quickly to the scene and study immediate responses while they are occurring. Most research on short-term disaster responses relies on hastily assembled journalistic reports and after-the-fact accounts based of recollections by participants. Both sources are subject to selectivity and distortion. Teams of behavioral and social science researchers, collecting data on the spot and analyzing them in the context of established knowledge about disaster situations, would supplement and probably improve
on existing ways of generating information and understanding. Some universities have a tradition of fire brigade research; efforts should be made to expand and systematize it.
To track group differences in response to crises. Most thinking about preparedness, warning, and response rests on the assumption of an undifferentiated community or public. Research on disasters, however, has revealed that individuals and groups differ both in readiness and response according to previous disaster experience, ethnic and minority status, knowledge of the language, level of education, level of economic resources, and gender (Tierney et al., 2001). Research on these and other differences should be extended and deepened and taken into account when designing systems of preparedness, warning, and response to terrorist attacks and other disaster situations.
To evaluate the behavior of agencies of response to crisis. There should be a deepening of research—basic, comparative, and applied—on the structure of agencies designated as responsible for dealing with attacks and other disasters, on the optimal patterns of information dissemination and communication among them, and on the most effective strategies of coordination and self-correcting of coordination under extreme conditions. Research should also focus on the origins and consequences of organizational failure, miscommunication, lack of coordination, and jurisdictional conflict and squabbling.
To evaluate the practice of ethnic profiling. Advocated as both a necessary and effective method of identifying and apprehending terrorist suspects, ethnic profiling raises both methodological and policy issues. A scientific review should be made of its methodological underpinnings, including implied statistical assumptions and possible fallacies. In addition, the practice of profiling raises many questions about intrusiveness on civil rights and possible boomerang political effects in affected groups. A starting point for research might be an examination of scientific issues and political effects in affected groups. Such a study group could consult not only the literature on terrorism but also that in other areas (e.g., police arrest practices, housing discrimination) in which the issue has emerged.
To assess both short-term and long-term group responses to terrorism and terrorist attacks in terms of attitudes and opinions. Questions would include the attitudinal consequences of living in prolonged situations of heightened anxiety, as well as
the dynamics of the balance between tendency toward national and community solidarity (tending to diminish group difference and conflict) and the tendency for fault lines dividing groups along ethnic, religious, and political dimensions to become more salient. In the current atmosphere, special attention should be given to the situation of Muslim Americans—blacks, Asians, and Arabs—who consider themselves part of the nation’s demographic, cultural, and political fabric but who have experienced considerable stress in the context of national reactions to terrorist activities emanating from the states of origin of some of these citizens. This last line of research could be supplemented by comparative work on ethnic, especially Muslim, minorities in European countries, including France, Germany, and the United Kingdom, where the forces shaping the national and ethnic loyalties differ from those in the United States.
To develop sequential and cumulative analyses of terrorist events. Because terrorist attacks tend to be sudden, surprising, and of short duration, they are usually regarded as discrete events. In reality, however, they build on one another, and any new attack or attacks is read, variably by different groups, in the context of the past history of such events. One of the interpretative frames of reacting to the attack on the World Trade Center, for example, was the memory of the unsuccessful effort to destroy it by bombing in 1993. Reactions to anthrax episodes were strongly conditioned—and exaggerated—because they occurred so soon in the wake of September 11. The whole history of mutual terrorism between Palestine and Israel is a history of stored memories of many past occurrences, evoked when new attacks occur and referred to continuously by both sides. Historical research on the interrelated sequencing of reactions, interpretations, and memories of terrorist events would deepen theoretical and empirical understanding of those phenomena. Conceptual models, such as path dependency (employed in economics, political science, and other fields) and the logic of “value added,” would offer guidelines to framing and conducting this kind of research. Formal modeling of these kinds of sequences should also be explored.
The events and aftermath of September 11, 2001, profoundly changed the course of history of the nation. They also brought the phenomenon known as terrorism to the forefront of the nation's consciousness. As it became thus focused, the limits of scientific understanding of terrorism and the capacity to develop policies to deal with it became even more evident. The objective of this report is to bring behavioral and social science perspectives to bear on the nature, determinants, and domestic responses to contemporary terrorism as a way of making theoretical and practical knowledge more adequate to the task. It also identifies areas of research priorities for the behavioral and social sciences.
READ FREE ONLINE
Welcome to OpenBook!
You're looking at OpenBook, NAP.edu's online reading room since 1999. Based on feedback from you, our users, we've made some improvements that make it easier than ever to read thousands of publications on our website.
Do you want to take a quick tour of the OpenBook's features?
Show this book's table of contents , where you can jump to any chapter by name.
...or use these buttons to go back to the previous chapter or skip to the next one.
Jump up to the previous page or down to the next one. Also, you can type in a page number and press Enter to go directly to that page in the book.
Switch between the Original Pages , where you can read the report as it appeared in print, and Text Pages for the web version, where you can highlight and search the text.
To search the entire text of this book, type in your search term here and press Enter .
Share a link to this book page on your preferred social network or via email.
View our suggested citation for this chapter.
Ready to take your reading offline? Click here to buy this book in print or download it as a free PDF, if available.
Get Email Updates
Do you enjoy reading reports from the Academies online for free ? Sign up for email notifications and we'll let you know about new publications in your areas of interest when they're released.
Russia and the Far-Right: Insights From Ten European Countries

Get unlimited topic ideas and a dissertation plan for just £45.00
Order topics and plan

Get 1 free topic in your area of study with aim and justification
Yes I want the free topic

Terrorism Dissertation Topics Ideas
Published by Owen Ingram at January 5th, 2023 , Revised On March 24, 2023
Introduction
Terrorism is a major global threat to public safety and security. It is an unlawful use of violence and intimidation to achieve political, ideological or religious goals. Terrorist attacks are always extremely devastating and have the potential to cause significant destruction, fear, injury and even death.
Terrorists employ many tactics, including bombings, hijackings, hostage takings, assassinations, cyber-attacks and more. The impact of terrorism on society is widespread, as it can cause economic damage by disrupting financial markets, creating social unrest through fear-mongering and creating long-term psychological trauma for affected individuals or communities.
Governments worldwide have implemented various initiatives designed to tackle this type of crime, but terrorist groups continue to operate across international borders with impunity.
Conducting research on terrorism is an essential aspect of a student’s dissertation and understanding of terrorism-related topics. In order to develop a comprehensive understanding of this complex field, students should dedicate time to researching the phenomenon of terrorism and its implications for national security.
In today’s world, terrorism has become one of the most pressing issues faced by countries all over the globe. Thus, it is important for students to be knowledgeable about current events and how they relate to global security.
Developing a solid analytical outlook towards terrorist groups, their goals, and objectives can open up new opportunities in the realm of national security policy-making and counter-terrorism initiatives. Moreover, it can help in developing comprehensive solutions which are aimed at curbing terrorist activity in areas around the world that are prone to violence.
How Should Students Choose Terrorism-Related Dissertation Topics?
When it comes to topics related to terrorism, this task becomes even more difficult as many complex and diverse topics can be investigated. Students should consider certain factors while choosing their dissertation topic to ensure they have chosen an appropriate and practical research area.
First, students should identify what area or field they wish to focus on for their dissertation. For example, suppose a student is interested in researching international terrorism. In that case, they should look for potential research topics related to this field, such as analysing terrorist networks or understanding state responses towards transnational terrorist organisations.
Students can also look on more specific areas, such as examining the role of social media in recruiting individuals into terror networks or looking at counter-terrorism strategies employed by different countries around the world.
Terrorism Dissertation Topics List
- Are counter-terrorism strategies effective? The results of the Campbell systematic review on counter-terrorism evaluation research
- Combating terrorism: strategies of ten countries
- Rethinking Nigeria’s counter-terrorism strategy
- Common threat and common response? The European Union’s counter-terrorism strategy and its problems
- Credibility in the global war on terrorism: Strategic principles and research agenda
- A strategic framework for terrorism prevention and mitigation in tourism destinations
- From convergence to deep integration: Evaluating the impact of EU counter-terrorism strategies on domestic arenas
- Counter-terrorism strategies in Indonesia, Algeria and Saudi Arabia
- Hard versus soft measures to security: Explaining the failure of counter-terrorism strategy in Nigeria
- Putting terrorism in context: Lessons from the Global Terrorism Database
- What is domestic terrorism? A method for classifying events from the global terrorism database
- Characterising chemical terrorism incidents collected by the global terrorism database, 1970-2015
- Machine learning techniques to visualise and predict terrorist attacks worldwide using the global terrorism database
- The impact of terrorism on financial markets: An empirical study
- The impact of terrorism and conflicts on growth in Asia
- The economic impact of terrorism from 2000 to 2018
- The impact of terrorism on European tourism
- The impact of terrorism on Italian employment and business activity
- Impact of terrorism on economic development in Pakistan.
- Psychological impact of terrorism on children and families in the United States
- The impact of terrorism on the brain and behaviour: what we know and what we need to know
- Terrorism, the future, and US foreign policy
- Jewish terrorism in Israel
- Israel–Palestine: One State or Two: Why a Two-State Solution is Desirable, Necessary, and Feasible
- The Terrorism Acts In 2011: Report of the Independent Reviewer on the Operation of the Terrorism Act 2000 and of Part 1 of the Terrorism Act 2006
Also read: Dissertation Topics on Ukraine, Russia and NATO Conflict , Dissertation Topics on USA’s Withdrawal From Afghanistan , International Relations and Geopolitics Dissertation Topics , International Development Dissertation Topics , Criminal Psychology Dissertation Ideas .These subject topics will help you in getting dissertation research ideas, if you are studying in any mentioned subject.
How Can ResearchProspect Help?
ResearchProspect writers can send several custom topic ideas to your email address. Once you have chosen a topic that suits your needs and interests, you can order for our dissertation outline service which will include a brief introduction to the topic, research questions , literature review , methodology , expected results , and conclusion . The dissertation outline will enable you to review the quality of our work before placing the order for our full dissertation writing service!
What are the Benefits of Choosing a Good Terrorism Dissertation Topic?
Choosing the right topic for a dissertation on terrorism can be difficult. However, considering the various factors associated with it can help make the decision more accessible and beneficial to students.
A good terrorism dissertation topic should be relevant, engaging and unique enough to stand out from other written works in the field. It is also essential to address an issue or question that has yet to be looked at in depth.
In addition to helping students build their research skills, choosing an effective dissertation topic on terrorism will allow them to explore an area of interest in depth and develop a better understanding of complex issues related to this subject matter.
Students should also remember that selecting a current issue or one with potential implications for national security is likely to attract greater interest from potential employers or universities when applying for jobs or further study opportunities.
FAQs Related to Terrorism Dissertation Topics
What are some terrorism dissertation topics for students.
In the article above, there are multiple dissertation topics related to terrorism. You can choose any of them. A few areas explored include:
- Counterterrorism,
- Global governance,
- Conflict resolution
Are these dissertation topics unique?
Yes, all these dissertation topics are unique. But other students might have used them. You can take help from our dissertation topic services to get a unique topic for your terrorism dissertation.
What are the benefits of using the dissertation topic service?
The most beneficial part of dissertation topic services is that it offers help from experienced professionals with extensive knowledge in the field of research. This includes an initial consultation to discuss ideas, direct access to resources and databases, advice on turning those ideas into concrete topics, and suggestions on organising a literature review or methodology.
You May Also Like
Are you having trouble finding a good music dissertation topic? If so, don’t fret! We have compiled a list of the best music dissertation topics for your convenience.
A drama dissertation must be fully reflected in its topic. Here’s a list of the 65 most interesting dissertation topics on drama for you.
Here is a list of Technology dissertation topics to help you choose the one studies anyone as per your requirements.
USEFUL LINKS
LEARNING RESOURCES

COMPANY DETAILS

- How It Works
293 Essay Titles & Research Topics on Terrorism
🏆 best topics for essays about terrorism, 📖 terrorism essay topics for college, 📚 terrorism topics for research paper & essay examples, ✍️ good research topics on terrorism, 💡 simple ideas for terrorism research paper topics, 📌 easy terrorism essay topics, 👍 good terrorism essay topics to write about, ❓ research questions about terrorism, ✒️ great terrorism dissertation topics.
- Iranian Revolution and Terrorism: the Rex Cinema Massacre
- Media’s Role on Terrorism
- Pirate Terrorists as an International Threat
- “Unemployment and Terrorism” TED Talk by Mohamed Ali
- John Brown: Terrorist or Freedom Fighter
- Importance of Outsourcing the War on Terror
- Forensics Analysis of Terrorism Crime Scene
- The 26/11 Terrorist Attack on Mumbai The instance of a terrorist act is always a tragic occurrence since, especially when it results in a tremendous number of casualties and the deaths of innocent civilians.
- What Is Terrorism: Main Aspects of Term The success of the counter-terrorism campaigns depends on an adequate understanding of the essence of terrorism in the 21st century.
- Terrorism: Irish Republican Army History and Ideologies The aim of the current essay is to assess the IRA as a notorious terrorist organization in Ireland. The essay majorly focuses on the history and the ideologies of the IRA from 1969.
- Terrorism of Liberation Tigers of Tamil Eelam This paper makes a prognosis of the Liberation Tigers of Tamil Eelam’s future operations and the possibility of stopping its functions in Sri Lanka.
- About the Motives of the Terrorists This article attempts to determine what is more important in influencing the intentions of terrorists: human psychology or the social impact of a group.
- Liberation Tigers of Tamil Eelam and Hezbollah Terrorist Groups In this essay, we are going to discuss and analyze two terrorist groups and highlight some of the attacks that they claimed to bear responsibilities for.
- Connection Between Criminal and Terrorism Organization The paper gives a broad understanding of the nature of terrorism-organized crime collaboration and their operations supporting criminal activities.
- The Case of the 2015 Terrorist Attack in Paris: Bombing Investigation In the case of the Paris attacks in 2015, the targeted autopsy allowed forensic teams to identify victims and terrorists and define the nature of the explosive device.
- British Anti-Terrorist Structures In this paper, all possible mechanisms of anti-terrorist structures are presented in the example of countering Al-Qaeda at the beginning of the 21st century.
- Terrorism Prevention With Community Policing One of the measures that has proven to be effective in addressing terrorism is community policing which requires the engagement of officers and members of the public.
- The Ansar Al-Din Terrorist Organization’s Activities By conducting a simulation, it was found that acts of terrorism are capable of causing enormous damage to the country’s infrastructure and its people.
- The Geneva Convention and Terrorism Prevention The Geneva Conventions and their Additional Protocols form the center of international humanitarian law that regulates the conduct of armed conflicts.
- The Ansar Al-Din Terrorist Group Analysis This paper evaluates the measures implemented by the intelligence agencies to analyze information about Ansar al-Din that is currently available to grasp their terrorist tactics.
- Extremism and Terrorism in Nigeria Considering Nigeria’s high rates of terrorism and extremism, it is vital to illuminate the government’s strategies to eliminate the terrorist cells and extremist groups.
- Terrorism and Associated Media’s Response The media’s response to terrorism is often different from other crimes and specialized in targeting an audience that is susceptible to the current ‘war on terror’ model.
- Impact of Terrorism on the Economy Terrorism’s wider consequences are also dependent on the economy’s ability to reallocate and distribute capital from the affected sectors smoothly.
- Internationally Focused Terrorist Organization: Al Qaeda This paper addresses the inspiration of Al Qaeda, how this inspiration acts as a catalytic means of recruitment, and the means of communication used by Al Qaeda.
- Terrorism: Sources of Inspiration Perceived injustice, attention for a sense of belonging, and the need to find one’s identity are typical inspirations by potential terrorists.
- The Terrorism Definition in International Law Terrorism is an anxiety-inspiring method of repeated violent action, employed by (semi-) clandestine individual, group, or state actors.
- War vs. Terrorism: What Are the Main Differences? War is an armed confrontation between the parties to protect their interests. Terrorism, in turn, is a manifestation of violence aimed at inspiring fear.
- Counterterrorism Approaches: Terrorism Prevention There are five categories of counterterrorism approaches, proactive, defensive, coercive, long-term, and persuasive.
- Communication Technology’s Impact on Global Terrorism The main question of this work is the role of communication technology in modern international terrorism, and to what extent may vigilance and science mitigate adverse outcomes.
- Counter-Terrorism and Unemployment Approaches A more novel approach to unemployment that considers the needs of a disenchanted youth is vital to reducing the draw towards terrorist activities.
- The True Story of Che Guevara: Conflict & Terrorism The name of Ernesto “Che” Guevara is among the most well-known names in the world. The Argentinian freedom fighter played a crucial role in the Cuban revolution.
- Terrorism as a Pressing Social Issue Terrorism is a crime, the aim of which is a violation of public safety, which is expressed in encroachment on the life and health of citizens and infrastructure facilities.
- Modern Terrorism Regarding the Role of Media Modern terrorism uses the media to report its threats and activities. However, governments should not use their power to restrict the media from covering terror-related events.
- The Ku Klux Klan and Modern Terrorism This work will be about the terrorist part of the Ku Klux Klan and its similarities and diversities to other types of domestic terrorism that exist in our contemporary time.
- Terrorist Cells Issues in America The paper focuses on identifying the means used by terrorists to enhance their success and measures that military officers and law enforcement can embrace to help curb terrorism.
- Operation Anaconda: Terrorism Prevention Operation Anaconda has become one of the most significant an example of an operation in which commanders applied six basic principles of mission command.
- Technologies to Reduce Crime and Acts of Terrorism Terrorism can be met with a nonviolent, credible, and justifiable reaction if counterterrorism actions are anchored in an accountable and productive criminal justice system.
- Homeland Security Efforts to Counter Terrorism The counter-terrorism efforts of the Department of Homeland Security have multiple positive outcomes and generally ensure safety for citizens.
- Aaronson’s and McCue’s Speeches on Terrorism Aaronson and McCue have had their chance to deliver their speeches at TED regarding the problem of terrorism. The speakers shed light on the issue from quite a unique perspective.
- The Study of the Future of Terrorism: Review of Literature Politicians, international researchers, world-known philosophers, and engineers devote their lives to creating the best and safest conditions for people.
- US Terrorism and Criminal Justice Decision Making Model Terrorism is a significant security and safety threat. The United States has experienced both domestic and international terrorist attacks.
- Terrorism in Mumbai 2008: Before and After the Attack Before the attack, the terrorists carefully planned this operation, as it was supposed to be large-scale, ambitious, and have a powerful destructive character.
- Future of Terrorism and Emergency Management Today terrorism has become a serious threat to the security of the entire world and regional communities. It is expressed in the commission of explosions.
- Terrorism: The Faith-Based Discourses Although there are many discourses regarding the role of God and religion in terrorism, there are some similarities in what Falwell, the Jewish extremists, and Sayyid Qutb believe.
- The Phenomenon of Terrorism and Its Relation to Globalization This paper states that the phenomenon of terrorism is tightly connected to the concept of inequality of globalization.
- Terrorist Attack in San Bernardino The San Bernardino shootings in 2015 killed 14 innocent people and injured 24 more. It was also the bloodiest mass shooting in the US since 2012.
- Homeland Security Efforts: Counter-Terrorism and Threats The homeland security mission is to protect the country from various types of threats, including terrorism and national disasters.
- Terrorism and Violent Extremist Organizations in Somali and Their Elimination This project aimed to understand how the current Federal Government of Somalia plans for current and future threats against terrorism and violent extremist organizations.
- The Future of Domestic Terrorism in the United States The research issue of this paper is the future development of domestic terrorism in the United States and the possibility of mitigating it.
- Domestic Terrorism and Hate Groups The paper states that domestic terrorism and hate groups are interdependent terms that imply violence towards a state. Both target innocent people.
- Migration, Diasporas, and Terrorism This topic examines the relationship between different concepts (migration, diaspora communities, and terrorism) in the context of globalization.
- Crisis Management During Terrorism Threat In the essay, the crisis management strategies of preparation for change are viewed on the example of the terrorism threat.
- America and Terrorism in the 21st Century There are many threats that people face every day without even realizing it. For example, terrorism is a major global problem addressed by authorities and different organizations.
- Threat of Terrorism in the Middle East If tomorrow the US withdraws its troops from the Middle East, it is highly likely that terrorist activity in the region will subside but will not disappear.
- Terrorism: Radicalization and the Internet The current paper examines the main causes and types of radicalism, as well as what role the Internet plays in the hands of terrorists.
- Terrorism and Homeland Security Terrorism is an act of political violence aimed to incite terror and panic into the target population and further a specific political goal.
- Analysis of Terrorism in Spain The paper looks at the history of terrorism in Spain and how the European Union has countered terrorism and helped Spain fight against it.
- Is Terrorism Ever a Justifiable Form of “Political Violence” Young people are an essential source of support to various terrorist groups as they are used as fighters and even cooks.
- Financing Terrorist Organizations The financing of terrorist organizations is a significant problem for the national security agencies that monitor and suppress extremists’ activities and the entire world community.
- Operational Principles in the US War Against Terror The US war against terror has intensified aftermath of the 9/11 attacks, and to that day, remains one of the most contested and protracted US military operations abroad.
- What Is Water-Related Terrorism and How to Cope With It? Water-related terrorism includes damaging government facilities, and since water resources are vital for human existence, it is profitable for terrorists to attack them.
- Preventing Potential Attacks and Counter Terrorism The objective of this paper is to develop recommendations for a mayor to solve the issues of homeland security efforts to combat terrorism.
- Strategies to Prevent Radicalization and Lone-Wolf Terrorism This paper discusses approaches toward building trust and relationships with the Community to prevent radicalization and formulating counter-terrorism strategies.
- Cyberterrorism Threat to the United States National Security The United States remains vulnerable and largely unprepared for cyber terrorism threats that threaten its national security due to the increased growth of adversary capabilities.
- How Do Terrorists Conduct Cyber Warfare? Terrorism activities are a global concern since they can occur in any part of the world depending on the perpetrators’ target.
- The Threat of Nuclear Terrorism The issue of nuclear terrorism has been discussed by many researchers and policy-makers. Some believe that the threat is unrealistic.
- Terrorism Prevention: Operation Geronimo Operation Geronimo was carried out by the US military in the Pakistani city of Abbottabad. As a result, the head of al-Qaeda was killed.
- An Overview of Investigative Techniques as They Apply to Terrorism The paper focuses on the psychological and behavioral features of terrorists and offers several recommendations on the use of investigative techniques in their case.
- Terrorist Drag in “Stop Being Poor” Video “Stop Being Poor” invokes stereotypes of racialized and gendered deviance in terms that show that only White, rich women deserve to stay alive.
- Impact of Terrorism on Global Stability Terrorism implies planned actions aimed at causing fear and instability among nations. Terrorists use crude weapons to threaten and kill people for political and social gain.
- Terrorism Current Events Terrorist attacks have for a long time culminated in the loss of lives, property destruction, destabilized governments, and resulted in economic paralysis.
- Money Laundering, Corruption and Terrorism Issues Money laundering, corruption and terrorism are rife in East and Southern Africa is largely attributed to the abject poverty that at times seems to be endemic.
- War on Terrorism on USA After 9/11/2001 The discussion of the acts and policies directed at the USA security are going to be considered with the purpose to follow the changes that occurred after the 9/11 attacks.
- Extremism and Terrorism in the Society Extremism includes the activities that are not violent but grossly violate citizens’ rights and freedoms, having an ideological motive behind them.
- Terrorism: Palestine Liberation Organization (PLO) Terrorists are the individuals who practice terrorism; they can also be referred to as the agents of terrorism since they attack nations they are opposed to.
- The Fourth Wave of Terrorism and Religion The diverse religious ethnicities have primeval ancestry evidence in a terror campaign. The fourth or the current wave of terrorism derived its incentives from religious activities
- War on Terrorism. Danger for Civil Citizens War on terrorism is one of the most notable phenomena observed in the world today. The roots of this war lie, allegedly, in the severe threat to the security.
- Terrorism Theories and Media Discourse This paper discusses theoretical comprehension of the terrorism phenomenon, mass media discourse concerning terrorism, and implications for the future.
- Terrorism in Northern Ireland and in Middle East There is no universal instrument to end the terrorism, but profound analysis of this phenomenon is one of the primary measures for the solution of this issue.
- Robust Security System vs Terrorists in Airport America has stepped up its security system by appointing TSA – a government organization to protect the nation’s transport system.
- Drug Trafficking and Terrorism in the Middle East Terrorism and drug trafficking are the major wars that the world has been trying to fight for several centuries.
- Handling of the Terrorist Suspects According to the English Legislations The main aim of this study is to explore how terrorism suspects are handled in relation to English laws. The study examines some of the powers accorded to the police.
- Terror and Religious Belief System Contemporary fourth wave terrorists justify their use of violence through the theological and moral teachings taken from their chosen religious belief system.
- On the Reasons for the Terrorist Attack on September 11 The purpose of this article is to investigate allegedly American offenses that may have led to the 9/11 terrorist attack.
- International Terrorism in the United States Analysis There is a review of the Congressional Research Service report on International Terrorism, the focus being on threat, policy, and response issues.
- Possible Terrorist Attack Local law enforcement agencies with the help of the federal government created a network of databases called fusion centers, after 9/11.
- Terrorism and the Media This paper reveals how several media reporting incidents have embraced an ideology that Islam is inherently violent.
- Targeted Killing: Counter-Terrorism The current paper discusses that targeted killing represents a part of consequentialist philosophy in counter-terrorism.
- Counter Terrorism Methods and Their Effectiveness In many cases, terrorists are destroyed with the help of military people, although to a greater extent, this is the work of special services and the police.
- The Mind of a Terrorist Terrorism seems to bring a certain consolation within the terrorists yet does not offer them the solution to their problem.
- Terrorism: Understanding the Key Issues Terrorism remains a major challenge in many societies today. Terrorism is a necessary practice among many extremist groups in the Middle East.
- Terrorist Response Organizations Members of specialized terrorist response organizations undergo special training which allows them to respond to emergency situations more quickly.
- The US Response to the Terrorism Threats This report outlines the central directions of terrorist activities targeted at the US seaports and the ways American security counteracts them.
- Religion and Middle Eastern Terrorism The Middle Eastern region is occupied by Muslims, Christians and Jews. Their constant conflicts have been attributed to the rise in modern terrorism across the region.
- The Long Term Effects of Terrorism Terrorism attacks have become very common in today’s world especially with the increasing conflicts of power and the increase in financial difficulties around the globe.
- The Emerging Terrorist Threat in Africa Most terrorism acts are usually portrayed as political, emotional, or religious undertones. Terrorist threats in Africa started way back in the 1980s and 1990s.
- Historical Responding to Terrorism Terrorism is not the only resort to injustices. Processes like peace talks, negotiations and compromise of some standards solves any stalemate amicably.
- Bioterrorism: History, Types, and Detection This paper explains what is bioterrorism, gives a background of bioterrorism, and discusses the types of bioterrorism, and the difficulties to detect bioterrorism.
- Terrorism a Critical Issue of the Modern World Terrorism is, undoubtedly, a criminal act aimed at civilians. Terrorists tend to invent new, unusual ways to commit crimes, making them more dangerous and powerful.
- The Past and Present Effects of Terrorism on Society Terrorism is one of the main challenges that the world has encountered for several decades. It can be defined as the use of violence against civilians.
- Global Terrorism and Ways of Its Impact In the 21st century, global terrorism has become a complex problem that all nations need to address from an informed perspective.
- America’s War on Terrorism Terrorism is the organized use of terror or violent acts intended to create and make fear. These are unlawful acts of violence and war.
- UK Anti-Terrorism Strategy and the Human Rights Implications on its Implementation The prevention of terrorism has been given a higher priority, and the new legislation has drawn on new instruments equivalent to the European levels.
- Hacktivism & Cyberterrorism vs Government Response Hacktivism is the use of technology or computer system for social or political motivations. Cyberterrorism can be defined as intentional violent acts conducted in cyberspace.
- Terrorists’ Motives: The Psychology of the Individual The psychology of the individual may be useful to the activities of terrorists but this is realized well if the individual undergoes indoctrination amidst the group.
- Terrorism. Hezbollah: Ideology and Financing The problems of combating terrorist crimes in the framework of the modern world are becoming increasingly important.
- Three Cases of Terrorism: Ideological, Nationalist and Religious The main aim of terrorism is to draw the attention of the local population, state, and the entire world to the cause of terrorists.
- The Terrorism Threat in the Modern World This work describes the essence of terrorism, its essence, origins, forms of manifestation, tells about modern single and international approaches to combating terrorism.
- Lone Wolf Terrorism: Theoretical Analysis and Implications for Public Policy Countering lone-wolf terrorism is much more difficult than fighting organized terrorist activity, as it leaves a much smaller informational footprint.
- White Supremacy and the Terrorism Threats White supremacists are uniting in a comparable way with jihadist terror groups, such as Al Qaeda; they are uniting in a comparable way with jihadist terror groups, such as Al Qaeda.
- The Problem of Terrorism Prevention Each government should develop innovative strategies for the struggle against terrorism while special attention should be paid to the financial front in the global war on terrorism.
- Policy Memorandum: Terrorist Organizations Nowadays, terrorist organizations are more geographically dispersed than it was before, and their tactics became more sophisticated and untypical.
- Emerging Terrorist Threat in Africa If judging terrorism only by the media, its face is always changing. In that regard, it can be stated that its most recent face seems to be in Africa.
- Sociological Failure of the War on Terrorism This article explains why the War on Terror has failed sociologically by focusing on three pillars: an international reputation, cost, and lack of results.
- The Earth Liberation Front as the Domestic Terrorist Organization The purpose of this essay is to analyze the ELF’s history, structure, and actions, to fully understand the rationale behind their decisions.
- Domestic and International Terrorism There is an evident dismissal of domestic terrorism, which is also reflected in the fact that there is a more aggressive monitoring approach for the international one.
- Terrorism: Threat and Ways of Combating Terrorism has an aggressive and violent nature and, most importantly, a public character that threatens nation safety and requires law enforcement agencies’ intervention.
- The Phenomenon of Terrorism in the Modern World This essay aims to discuss the phenomenon of terrorism through the prism of two opposing sources, including a speech by the U.S. President and a letter from Osama bin Laden.
- Unconventional Warfare on the Global War on Terror The implications of the findings for US foreign policy can be seen through targeting regional security, rather than focusing on a single country a source of terrorism.
- United States Foreign Policy and Terrorism The foreign policy in the USA aimed at fighting terrorism demonstrates the integrity of the two concepts, human and national security.
- Terrorism and Genocide: Impact on Populations Victims of terror actions usually recover within a short time, given that terrorist actions are considered moderate stress reactions.
- A Duty of Care in Cyberspace and How It Relates to Cyber Terrorism Confronting the threat posed by cyber attackers and to the internet security of critical infrastructure still remains a challenge.
- Terrorism Attack in United States America has invested a lot of money towards improving its ability to detect any act of terrorism, prevent the acts and if they occur, respond to them.
- Terrorism as a Transnational Organized Crime Terrorism and organized crime have always been considered to stand among the primary security threats in any society.
- Terrorism and Genocide: Traumatic Impacts The defense centers of excellence for psychological health and traumatic brain injury were launched to help those veterans who feel their lives are at risk psychologically.
- A Issue of Terrorism Terrorism is a problem that is spread on the level of human awareness, and thus, it should be addressed from the angle of affecting people’s minds and hearts as well.
- The Role of the Media in the Propaganda of Terrorism An article on how the terrorists managed to attract everyone’s attention, as well as a brief overview of the reasons and consequences of the change of government in Tunisia.
- Psychology of Terrorism: Leaders and Development The war on terror has been a losing battle because the leaders in today’s democracies fail to understand the reasons for the terrorism activities.
- A Biological Terror Attack in Agriculture The United States is highly vulnerable to terror attacks of biological nature in agriculture yet such an occurrence can cripple the economy.
- The Three Categories of Dissident Terrorism This paper seeks to contrast the three categories of dissident terrorism as documented by Assistant Vice President Gus Martin in his bestselling book.
- Bioterrorism and Surrounding Issues This paper reviews some of the al Qaeda attacks, the motivation, the mass casualties, panic, and disorder that accompany these attacks and their impacts.
- Torture Debate in America’s War on Terror Torture has mainly been used as a way to extract information from crime suspects for example who are intent on withholding it.
- International Consensus for Terrorism Mitigation It is imperative for various countries to come together and cooperate on diplomatic, law enforcement, military and intelligence capabilities.
- Bioterrorist Attack Involving Botulism and Response The intentional outbreak of botulism was characterized by complaints from people from one location that bought the meat from a single store.
- Community Policing Practice and Terrorism Activities Community policing is the best development ever in the police force. This is because it is still the best way to effectively combat crime and bring it to control.
- Ways to Defend Against Cyber Terrorism With the development of technology, new ways of terrorism on the web are reaching a new level. People need to know how to confront them and protect their privacy.
- Power of Terror as a Political Weapon The use of power of terror by the French monarchy was the main reason that made the people to think about democracy.
- The Power of Cyberterrorism The paper will look at what cyberterrorism could do to opponents and the actual possibility of such an attack.
- History And Threats Of Global Terrorism The paper shall argue that historical events after the cold war demonstrate how vulnerable the US is to global terrorism.
- Parsing and Analysis of the Phenomenon of Terrorism The common objective for most terrorist groups that engage in violent activities has been achieve their political goals.
- Definition of Terrorism Mitigation Terrorism mitigation is the assignment that should be solved on all governmental levels, and, in comparison with risk mitigation the terrorism mitigation entails several additional steps.
- Impact of Bioterrorism on the U.S Agriculture System The paper describes that the term bioterrorism has several definitions depending upon the origin of the attack but in general terms, it refers to any form of terrorist attack.
- Terrorist Attack Prevention Policy on the Example of the US Patriot Act The US Patriot Act is a multi-tiered government policy to prevent terrorist attacks that arose in response to the upheavals of the 2000s.
- The Roots of Islamic Terrorism The history of the Islamic religion has influenced the cause of terrorism since most terrorist groups are linked to the Islamic religion.
- Terrorism Prevention and Scenario Development The paper shall focus on the Aum Shinrikyo cult of Japan and its utilization of WMD as a case study. The Aum Shinrikyo cult staged six attacks against Japanese citizens.
- War on Terror Impact on Muslims & Their Responses The war on terror has been transformed into a war on Muslims. The Muslims living in the US have lived in constant fear and panic.
- How U.S. Political Parties View Terrorism The purpose of this paper is to examine the differences in position between the Democratic Party and the Republican Party on the issue of Terrorism as a national and global threat.
- US Preemptive Attacks: Counter-Terrorism Campaign After the 9/11 attacks, the United States Government and President Bush Administration started their comprehensive counter-terrorism campaign but the world community perceived the practice.
- Causes of the Break Down of Intelligence Before the Terrorist Attack of 9-11 The breakdown of intelligence culminating in the September 11 attacks was largely a result of lack of preparedness, ignorance, failure to learn from the past events.
- Globalized Terrorism Shall Lose Its Significance In this paper this position will be critically elaborated and claims that support a position that globalized terrorism will loose its significance as a strategic challenge are rejected.
- Brainwashed Terrorists: Are Terrorists Crazy? The main reason why terrorist attacks are so frightful is that they are organized by people who are not afraid to die, people who die for their faith, or what they think to be their faith.
- Public Health Problems: Bioterrorism The issues of bioterrorism are not paid much attention in various media in comparison with other factors of everyday life in the global scales.
- Emergency Response and Management in a Terrorist Attack This report depicts the scenario that will ensue if a terrorist attack were launched against an urban population center in the US today.
- Non-Conventional Terrorism and Protection Among the types of terrorism the most inevitable and unpredictable one is non-conventional which terrifies by its unexplored nature and effects.
- War Against Terrorism and Social Injustices Terrorism by itself is the outcome of serious social injustices faced by several communities. Doing more injustice will only worsen the condition.
- Human Rights Conservation and the War on Terror Public Safety is the concept of governmental organizations concerned with protecting their citizens from all kinds of threats.
- Singapore Armed Forces in Counter-Terrorism Efforts The tragedy of Lo Hwei Yen can only serve as a reminder to all Singaporeans that terrorism transcends all borders and that the need to remain vigilant is more urgent than ever.
- The American Skinhead, and Greenpeace: Humanitarians or Terrorists The Greenpeace and American Skinhead movements have come to attract a lot of controversies in regard to their intentions and legality of action.
- IL1 Emerging Infections, Zoonoses and Bioterrorism. IL 1 is included under zoonoses infectious. Other transmissible routes are through direct contact, via contaminated airborne particles, contaminated water.
- Terrorist Groups’ Social and Psychological Origins Terrorism is a complex social issue which requires multiple levels of analysis from interdisciplinary fields of psychology, political science, and cultural and historical studies.
- How Media Helps Promote Terrorists’ Agenda The media serves as the platform that helps to popularize the ideas of various terrorist organizations by familiarizing people with them.
- Non-Conventional Terrorism from Theoretical Viewpoints Non-conventional terrorism mainly uses and executes non-traditional forms of weapons. They might include chemical, biological, and nuclear types of threats.
- Terrorist Campaigns of Extremist Organizations The paper considers extremist actions of such prohibited groups as Vanguard America (VA), the Balochistan Liberation Army (BLA), and Boko Haram (BH).
- 9/11 Terrorist Attacks and Failure to Prevent Them Failure to share information and lack of interagency cooperation was a significant cause as to why the 9/11 terrorist attacks were not prevented despite numerous red flags.
- Terrorism and Other Crimes Against the State This paper overviews crimes against the state and discusses terrorism as an offense, its types, and the legislator allowing for combating it.
- Russian Cyber Terrorism and the United States: A Research Proposal This paper presents the key information on a proposal for a case study of the cyberattacks used as a part of the interference of Russia in the US elections of 2016.
- Russian Cyberterrorism and the United States Cyberspace With the development of the cyberspace, some new uses of the related technologies have appeared, including beneficial and malevolent ones.
- Russian Cyberterrorism and the United States Election 2016
- The Terrorist Aspects of Narcoterrorism
- Vital Issues of Terrorism and Ways to Counter Terrorism
- Terrorism History in the United States
- War on Terrorism: The Modern Perspective
- Generation Kill: Anti-Terrorism Fight After 9/11
- Generation Kill: War on Terrorism After 9/11
- Human Factors in Aviation: 2016 Brussels Terrorist Attacks
- Military Commissions and Terrorism Prevention
- Terrorist Profiling from Various Perspectives
- Terrorist Weapons Sources and Extremist Attacks
- How Terrorists Prepare for Attacks
- The Arab Spring and Terrorism
- Terrorist Surveillance Techniques for Predicting and Identifying Terrorist Activities
- Terrorism Today: the Past, the Players, the Future
- The Roots of Terrorism: Religion
- Local Police Response to Terrorism
- Emergency Management in Past Acts of Terrorism
- Terrorism as a Threat to American Airport Security
- Understanding Terrorism: Course of Action
- United States and Negotiation With Terrorists
- The Impact of Terrorism on Walmart Global Logistics
- Terrorism and The Peshawar School Bus Bombing
- Human Rights Advocates vs. Terrorism Victims
- America’s Fight Against Terrorism
- Terrorism Attacks, Motivations, Political Factors
- Terrorists: Criminals or Crusaders?
- American Domestic Terrorism and Its Historical Roots
- Terrorism as Global Issue and Preventive Laws
- Terrorism: A Philosophical Investigation
- Khobar Towers Bombing and Terrorism in the US
- Terrorism and Its Damage to Modern Society
- Holy Terrors: Religion and Terrorism in the US
- Terrorist Organizations: Key Concepts
- Homegrown Terrorism in the United States
- Terrorist Activities in Media Broadcasting
- Intelligence Requests for Terrorist Attacks Prevention
- Government Preparedness to Chemical and Bio Terrorism
- Policy on National Security and Terrorism in the USA
- Ethical Terrorist Elimination in the United States
- Countering Terrorist Recruitment in the United States
- Terrorism in the USA
- Arab Spring, Terrorism and Libyan Political Changes
- Emergency Management: Past Acts of Terrorism
- Problem of Terrorism in Modern World
- Terrorism’s Serious Problems: Can It Be Justified?
- Homeland Security and Terrorist Attack Prevention
- Terrorism and Homeland Security
- Extremist Groups and Domestic Terrorism in the US
- Terrorist Hazards and Education Role in Security
- How Do We Prepare for Future Terrorist Attacks?
- Disaster Management: Terrorism and Emergency Situations
- Extreme Islamic Terrorist Groups in Comparison
- World Trade Center Disaster and Anti-Terrorism
- Terrorism Financing and Combating Methods
- Terrorist Activity in the United States
- The USA Patriot Act in Fight with Terrorism
- Religion as a Root of Terrorism
- Legislation After the 9/11 Terrorist Attack in New York
- Global War on Terrorism: Main Challenges
- Terrorist Attacks: Death and Horrifying Effects on Innocent People
- Terrorism Evolution from 1972 to 2016
- Terrorism Definition and Motivation
- State Terrorism vs. Critical Terrorism
- Terrorism Definitions in the US Legislation System
- Guantanamo Bay as a Terrorists’ Location
- The Concept of Terrorism
- Events of 9/11 and an Era of New Terrorism
- The US Intelligence Community Role in Countering Terror Threats
- Terrorist Bomb Attacks in France
- Anti-Terrorist Attitudes and Measures in the US
- Tokyo Terrorist Attack in 1995: Stakeholders and Effects
- Terrorism, Its History and Constituents
- Homeland Security: Fast Response to Disasters and Terrorism
- Crimes in America: The 9/11/01 Terrorist Attacks
- Supreme Court’s and Habeas Corpus War on Terror
- History of Cold War and War on Terror
- Preparing for Terrorism and Disasters in the New Age of Health Care
- 9/11 Terrorist Attacks and Its Effect on Muslims
- Information Warfare and Cyberterrorism
- War on Terrorism: Reasons, Essence, and Social Outcomes
- Counter-Terrorism: Constitutional and Legislative Issues
- Psycho-Political Terrorism and Its Main Principles
- Terrorism: Understanding of USC Definitions
- Right and Left Wing Terrorist Groups
- Terrorism in Perspective: Characteristics, Causes, Control
- The Right of Habeas Corpus in the Context of the War on Terror
- Terrorism: Definition, History, Countermeasures
- Intelligence Implications for Self-Radicalized Terrorism
- Why Does Globalization Contribute to the Rise of International Terrorism?
- Is Democracy Promotion a Cure for Ending Terrorism?
- What Is the Effect of Globalization on Terrorism?
- Can Islamic and Global Terrorism Ever Be Defeated?
- What Are the Four Elements of the Government’s Counter Terrorism Strategy?
- Can the State Commit Acts of Terrorism?
- Does the International Community Think That Iran Is a Direct Contributor to Terrorism?
- What Are the Political Causes of Terrorism?
- How Does the Patriot Act Define Domestic Terrorism?
- Why Does Poverty Cause Terrorism?
- Does Economic Growth Cause Terrorism in Pakistan?
- How Does Social Identity Theory Explain Terrorism?
- What Are the Effects of Terrorism in India?
- Does Transnational Terrorism Reduce Foreign Direct Investment?
- How Does Terrorism Affect the Economy?
- What Strategy Aims to Reduce the Threat to the UK From Terrorism?
- Is Terrorism a Social Phenomenon?
- Why Are Developing Countries More Vulnerable to Terrorism?
- How Does Terrorism Affect International Business?
- Does Terrorism Influence Domestic Politics?
- What Is the Difference Between Cybercrime and Cyber Terrorism?
- Is Cyber Attack a Form of Terrorism?
- What Is the Link Between Transnational Organized Crime and Terrorism?
- How Can Cyber Terrorism Be Prevented?
- Does Immigration Increase the Risk of Terrorism?
- The Role of International Relations in Combating Cyberterrorism: Challenges and Strategies
- Analyzing the Psychological Profiles of Terrorists: Motivations and Mindsets
- The Role of Women in Terrorist Organizations: Perpetrators, Supporters, and Defectors
- The Influence of Religion and Ideology in Shaping Terrorism
- The Impact of Political Regimes on Terrorism: A Comparative Analysis of Authoritarian and Democratic States
- The Use of Technology in Modern Terrorism: Drones, Cyber Attacks, and Artificial Intelligence
- Cybersecurity and Critical Infrastructure Protection: Assessing Vulnerabilities to Cyberterrorism
- Homeland Security and Border Control: Addressing the Challenges of Terrorism through Immigration Policies
- The Impact of Terrorism on Tourism and the Global Economy
- The Evolution of Terrorism: A Historical Analysis of Ideologies and Tactics
- Criminology and Terrorism: Analyzing the Social and Psychological Factors Influencing Terrorist Behavior
- Comparative Study of Counterterrorism Strategies in Different Political Systems
Cite this post
- Chicago (N-B)
- Chicago (A-D)
StudyCorgi. (2021, September 9). 293 Essay Titles & Research Topics on Terrorism. https://studycorgi.com/ideas/terrorism-essay-topics/
"293 Essay Titles & Research Topics on Terrorism." StudyCorgi , 9 Sept. 2021, studycorgi.com/ideas/terrorism-essay-topics/.
StudyCorgi . (2021) '293 Essay Titles & Research Topics on Terrorism'. 9 September.
1. StudyCorgi . "293 Essay Titles & Research Topics on Terrorism." September 9, 2021. https://studycorgi.com/ideas/terrorism-essay-topics/.
Bibliography
StudyCorgi . "293 Essay Titles & Research Topics on Terrorism." September 9, 2021. https://studycorgi.com/ideas/terrorism-essay-topics/.
StudyCorgi . 2021. "293 Essay Titles & Research Topics on Terrorism." September 9, 2021. https://studycorgi.com/ideas/terrorism-essay-topics/.
These essay examples and topics on Terrorism were carefully selected by the StudyCorgi editorial team. They meet our highest standards in terms of grammar, punctuation, style, and fact accuracy. Please ensure you properly reference the materials if you’re using them to write your assignment.
This essay topic collection was updated on January 9, 2024 .

An official website of the United States government, Department of Justice.
Here's how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
Comparing Violent Extremism and Terrorism to Other Forms of Targeted Violence

Targeted violence spans a wide array of offenses, from mass shootings to gang or group-violence-related activities to human trafficking. Although each of these topics has been researched extensively, until recently they have not been studied to identify similarities and differences in the context of domestic violent extremism and terrorism. Gaining a better understanding of any links or overlaps between people who perpetrate these types of violence and those engaged in violent extremism and terrorism is essential to developing or adapting targeted violence prevention efforts.
The National Institute of Justice (NIJ) has funded multiple projects that compare individuals who perpetrate violent extremism and terrorism and those who engage in other forms of targeted violence. [1] This article reviews findings from several NIJ-supported projects that explore similarities and differences between:
- Violent extremists and individuals who are involved in gangs.
- People who engage in terrorism and those involved in human trafficking.
- Lone actor terrorists (that is, single individuals whose terrorist acts are not directed or supported by any group or other individuals) and persons who commit nonideological mass murder.
Some of these projects draw on large national databases of individuals who are known to have committed violent acts, while others explore community and stakeholder perceptions of the acts. In addition, some of these projects focus on how communities that contend with heightened risk factors, such as adversity and disadvantage, experience certain types of violence. [2] The article closes with a discussion of possible implications for policy and future research.
Violent Extremists and Individuals Involved in Gangs
Pyrooz and colleagues developed a comparative model that emphasizes explicit, spurious, and indirect links between violent extremist groups and criminal street gangs. Using national data sources on domestic extremists and individuals involved in gangs — the Profiles of Individual Radicalization in the United States (PIRUS) and the National Longitudinal Survey of Youth 1997 (NLSY97), respectively — the researchers compared the two groups across group involvement and demographic, family, religious, and socioeconomic status characteristics. [3] They found that 6% of domestic extremists in PIRUS have a history of gang ties; this constitutes a minimal proportion of domestic extremists and is likely the rare exception among those involved in gangs. Domestic extremists with gang ties more closely resemble nongang extremists in PIRUS than they do individuals involved in gangs in the NLSY97. Although these groups have some similarities, one major difference is that individuals involved in gangs are younger than domestic extremists. This likely contributes to many of the other differences between the groups across the life course, including in education, unemployment, marriage, and parenthood.
A critical step in determining similarities is to examine the circumstances of those who enter these two groups. Based on 45 in-person interviews of individuals involved in U.S. gangs and 38 life history narratives of individuals who radicalized in the United States, Becker and colleagues provided a unique comparison of entrance into these groups by drawing on four broad group entry mechanisms: [4]
- Pull factors (influences that entice vulnerable individuals toward criminal group involvement).
- Push factors (influences that drive vulnerable individuals toward an interest in criminal group involvement).
- Barriers to effective socialization.
- Recruitment.
Individuals involved in gangs were more motivated than extremists by the promise of material rewards (a pull factor). In contrast, extremists were more motivated by cultural disillusionment and a perceived loss of significance (push factors). (For more detail on push and pull factors, see exhibit 1 .) Individuals in gangs were more likely to have been abused by family members (a barrier to effective socialization), while extremists were far more likely to have been recruited through electronic media (recruitment). Evidence for each mechanism was present in both groups and no single mechanism dominated entry into either group. Thus, prevention and intervention efforts that draw on multiple pathways to entry are most likely to be effective.
Exhibit 1. Examples of Push and Pull Factors
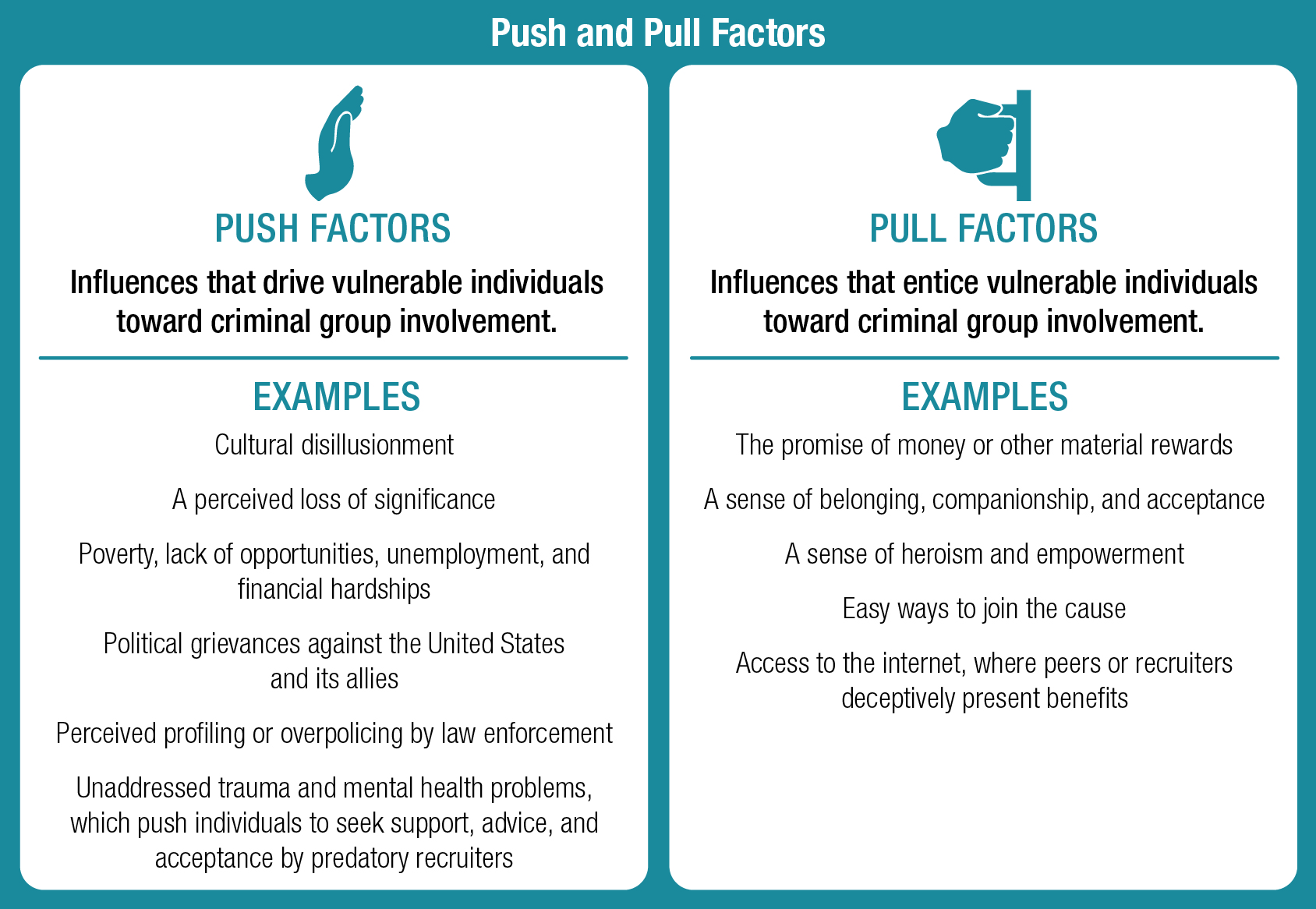
In a separate community-based participatory research study, Ellis and colleagues explored attitudes toward gangs and violent political activism within a community sample of 498 ethnic Somali young adults living in the United States and Canada. [5] Somali communities in North America have been impacted by both gang violence and targeted recruitment by extremist networks; they have also disproportionately experienced structural disadvantages, such as poverty. The analysis showed that attitudes favoring both gangs and violent activism could — but did not necessarily — co-occur; prosocial bonds reduced the likelihood of attitudes in support of both. [6]
One important distinction between gang involvement and violent extremism was the Somali community’s perceptions of these two types of violence. During a series of nine focus groups and in-depth interviews, ethnic Somali young adults described how the community saw radicalization to violent extremism as irrelevant. [7] Despite quantitative data suggesting some overlap in attitudes in support of gangs and violent radicalism, community perceptions of the two issues were highly divergent. Community members viewed political radicalization as an individual choice. On the other hand, these community members considered gang involvement a major community concern and the product of societal factors such as marginalization and a lack of opportunity. [8] This divergence has implications for policy and programming. Although certain risk and protective factors (for example, enhancing prosocial connections) may be common targets for different types of interventions, gang prevention programming may be more accepted by the community than programming focused on radicalization.
Terrorists and Those Involved in Human Trafficking
Research has identified two possible connections between terrorism and human trafficking. First, a terrorist organization may perpetrate human trafficking to advance its interests or meet the needs of its members; this occurs mostly in international contexts and conflict zones. [9] Second, terrorism and human trafficking may co-occur. [10]
Weine and colleagues studied an immigrant community in which terrorism and human trafficking allegedly co-occurred. The researchers conducted in-depth interviews with ethnic Somali young adults and parents, community leaders, service providers, and law enforcement officials in three U.S. cities with large Somali communities. [11] Their findings suggest that terrorism and human trafficking co-occur due to the convergence of risk (push and pull) factors. [12]
Perceived negative personal, social, cultural, economic, and political factors that pushed individuals toward these two forms of violence included:
- Poverty, lack of opportunities, unemployment, and financial hardships that made individuals vulnerable to promises of money and a better life.
- Generational divide due to parents’ lack of familiarity with the English language and American values and culture, and consequent limited ability to provide guidance and support for their children.
- High proportion of female-headed, single-parent households and dual-parent families with working parents who have limited visibility into their children’s whereabouts and thus are unable to combat negative influences or pressures to join violent groups or activities.
- Disconnect between young community members and religious leaders who represent older generations.
- Challenges associated with navigating identities of people who are Somali, Muslim, and African American.
- Unaddressed trauma and mental health problems related to integration into American society, which push youth to seek support, advice, and acceptance by misguided peers or predatory recruiters.
- Exposure to negative influences in the form of “bad company” or terrorism recruiters.
Factors that pulled individuals to both forms of violence, or that recruiters and their proxies used to depict desirable outcomes, included:
- A sense of belonging, companionship, and acceptance.
- Money or other material benefits.
- Access to the internet, where peers or recruiters used deceptive presentations of benefits.
However, some push and pull factors were limited to either terrorism or human trafficking. Distinct push factors for terrorism included:
- Political grievances against the United States and its allies.
- Perceived profiling or overpolicing by law enforcement of Somali and Black individuals and communities.
- Stereotyping and stigmatization by the media.
- Belief that the costs of joining terrorist groups are negligible.
Pull factors unique to terrorism included:
- A sense of heroism and empowerment through following extremist ideology directed at English speakers.
- Easy ways to join the cause.
Distinct push and pull factors for human trafficking, specifically alleged sex trafficking, included:
- Patriarchal beliefs about women’s lower status and submissive behavior.
- Lack of protection for women following gender role violations.
- Victims’ shame or fear of disclosing the victimization.
Taken together, negative societal responses to both human trafficking and terrorism (such as overpolicing, profiling, and media stigmatization) caused community members to perceive race- and ethnicity-based discrimination, feelings of social exclusion due to being labeled terrorists or morally inferior, and victim-blaming for not reporting victimization. Community members also lamented a lack of social services and consequently weak community efficacy, insufficient communal representation and a sense of disempowerment, distrust of government-funded programming, and perceptions that local and federal law enforcement overreact to incidents and work against the community. They were particularly concerned about cultural, social, or political stigma attached to community members who reported victimization or cooperated with law enforcement. Consequently, respondents preferred to resolve problems within the community rather than relying on those outside the community. [13]
Although these findings are drawn from one specific study and community, some of the risk and protective factors identified may have relevance for other populations, particularly those that experience social marginalization and disadvantage. The findings suggest that to prevent violent extremism, terrorism, and human trafficking, efforts must address underlying risks, disadvantages, and social problems. These include building effective prevention programs, strengthening law enforcement and community relations, increasing programmatic emphasis on community needs, and encouraging law enforcement and the media to avoid a continual focus on crime and violent extremism and terrorism in these communities.
Lone Actor Terrorists and Individuals Who Commit Nonideological Mass Murder
Targeted violence takes many forms. It can be carried out by a single person or a group. The violence can be aimed at a specific target, such as a spouse or coworkers, or it can be directed against a category of people, such as children at a school or bystanders in a public space. From the perspective of victims and survivors, the impacts may well be similar, but distinguishing the types of individuals who commit these crimes might illuminate actionable steps toward prevention.
Horgan and colleagues compared lone actor terrorists (single individuals whose terrorist acts are not directed or supported by any group or other individuals) with individuals who commit nonideological mass murder. [14] Although the motivational structure associated with each differs, the violence conducted by them appears very similar: both engage in largely public and highly publicized acts of violence, often with similar weaponry. The reasons behind any type of targeted violence are typically a “complex mix of personal, political and social drivers that crystallize at the same time to drive the individual down the path of violent action.” [15] Both lone actor terrorists and those who commit mass murder share this process. [16]
Furthermore, researchers have found little to distinguish between the sociodemographic profiles of lone actor terrorists and individuals who commit mass murder. In particular, a closer look at pre-attack behaviors revealed that both were likely to “leak” their grievances and intentions to others. [17] Although lone actor terrorists were more likely to communicate intentions or beliefs to friends and family members, others were aware of the grievances held by both groups. [18] Knowing that these individuals leak — or even deliberately broadcast [19] — their intent is important for the development of responses, particularly when there may be natural barriers to reporting this information, such as being the individual’s friend or family member.
Comparing the behavior of lone actor terrorists and individuals who commit mass murder also revealed some critical differences regarding:
- The degree to which they interact with coconspirators.
- Their antecedent event behaviors.
- The degree to which they leak information prior to the attack.
Importantly, researchers realized that they can learn more by focusing on behaviors (what people do) as opposed to focusing on characteristics (what or who people are).
For example, compared to lone actor terrorists, individuals who commit mass murder were significantly more likely to have familiarity with the attack location (79% vs. 30%). This may account for why lone actor terrorists were much more likely to engage in dry runs (34% vs. 4%). Those who committed mass murder were significantly more likely to consume drugs or alcohol just prior to the attack (20% vs. 4%). They followed a different “script” than lone actor terrorists as they moved closer to committing acts of violence; lacking an ideology, their behavior was influenced less by the prevailing social and political climate, and more by feelings of being wronged by a specific person or category of people. Overall, most individuals who committed mass murder did not pay much attention to post-attack planning or other strategic considerations. Indeed, most were either killed at the scene by police or took their own lives. [20]
Further research has compared lone actor terrorists to those who undergo radicalization in a group setting. Hamm and Spaaij found both similarities and differences between lone actor terrorists and group-based terrorists in terms of their sociodemographic profiles, behavioral patterns, and radicalization processes. [21] Compared to members of terrorist groups, lone actors were older, less educated, and more prone to mental health concerns. [22] The latter points to a potentially important mental health component in lone actor terrorism relative to group-based terrorism. Recent evidence has consistently shown that mental health concerns are more prevalent among lone actor terrorists (about 40%) than for group actors and for the general population. [23] However, the relationship between mental health and violent extremism is highly complex. Mental health is neither a reliable risk factor nor a consistent predictor of involvement in terrorism, and research to this point cannot rule out the possibility that negative mental health is a consequence rather than a potentially aggravating factor of involvement in terrorism.
Commonalities also exist between lone actor and group-based terrorists, and the boundary between these categories is often porous and fluid. Whereas group-based terrorists, by definition, exhibit a relatively high degree of interaction with coconspirators, a considerable proportion of lone actor terrorists also display an affinity with extremist groups to frame and give meaning to their beliefs and grievances. The nature and locus of such affinity with extremist groups has changed over time. Currently, it occurs primarily via online networks of like-minded activists or sympathizers found on the internet and social media platforms. [24] This insight reiterates earlier observations regarding leaking behavior: Compared to those who commit mass murder, lone actor terrorists exist in wider social networks, with varying degrees of contact with and influence from friends, family, and coworkers. Crucially, online communities often play an important role in providing a space for individuals to socialize and exchange beliefs and strategies with other extremists or sympathizers.
These studies reveal a striking and counterintuitive finding: Some terrorists, especially lone actors, leak or broadcast their intentions prior to their attacks. Knowing this, the field must develop and promote better strategies to detect and prevent such attacks. Although friends, family members, and coworkers may be well placed to detect violent ideation and intention, the fact that they know the individual creates a natural barrier to reporting. There needs to be greater effort to educate the public about the signs of attack leakage and broadcasting. Furthermore, there must be a concerted effort to provide clear, accessible, and convenient means of reporting such concerns.
Implications
The cumulative findings of these projects have implications for policy, practice, and future research. The current research highlights the various synergies and differences between violent extremism, group-based terrorism, gang activities, human trafficking, mass shootings, and lone actor terrorism. No single study provides a definitive or exhaustive set of explanations or shared risk factors. However, each provides critically important points to consider and address in future research. Moreover, the collective contribution of this body of research lies in providing a broader comparative view beyond single variables or narrow research questions. This review demonstrates that although there is no single, clear-cut overlap between the different criminal activities, they nonetheless exhibit important and sometimes unexpected similarities.
The implications extend beyond increasing knowledge, pointing toward multiple ways for policy and practice to intervene and to conduct evaluative research that addresses their impact. At the individual level, the studies suggest that although the motivational structures that underpin each type of violence vary, situationally specific combinations of push and pull factors shape individuals’ entry into, or radicalization toward, the different forms of violence. At the community level, the findings encourage policymakers and practitioners to consider effective ways to increase community awareness about the overlap in the factors that lead individuals to specific forms of violence, as well as about their potential cooccurrence, such as in the case of human trafficking associated with violent extremism and terrorism. Attention should also be directed to communal grievances that may lead community members to become alienated or engage in violent extremism, and measures should be designed to address them or lessen their impact.
The results further encourage policymakers and practitioners to embrace interventions that invest in strengthening protective measures against violence of any form. For such interventions to be accepted and endorsed by the communities in which they operate, it is important that interventions respond to community concerns, such as addressing social disadvantages that may lead to radicalization and terrorism, rather than focusing prevention efforts on the outcomes of such disadvantages. Finally, at the societal level — government, civil society, or media — promoting inclusion of those who feel they are outsiders, stigmatized, or otherwise undeserving or underserved may help reduce violence of all types.
About This Article
This article was published as part of NIJ Journal issue number 285 . This article discusses the following awards:
- “Gang Affiliation and Radicalization to Violent Extremism Within Somali-American Communities,” award number 2014-ZA-BX-0001
- “Lone Wolf Terrorism in America: Using Knowledge of Radicalization Pathways To Forge Prevention Strategies,” award number 2012-ZA-BX-0001
- “A Comparative Study of Violent Extremism and Gangs,” award number 2014-ZA-BX-0002
- “Across the Universe? A Comparative Analysis of Violent Radicalization Across Three Offender Types With Implications for Criminal Justice Training Education,” award number 2013-ZA-BX-0002
- “Transnational Crimes Among Somali-Americans: Convergences of Radicalization and Trafficking,” award number 2013-ZA-BX-0008
Opinions or points of view expressed in this document represent a consensus of the authors and do not necessarily represent the official position, policies, terminology, or posture of the U.S. Department of Justice on domestic violent extremism. The content is not intended to create, does not create, and may not be relied upon to create any rights, substantive or procedural, enforceable at law by any party in any matter civil or criminal.
[note 1] National Institute of Justice funding award description, “ Gang Affiliation and Radicalization to Violent Extremism Within Somali-American Communities ,” at Children’s Hospital Corporation, award number 2014-ZA-BX-0001; National Institute of Justice funding award description, “ Lone Wolf Terrorism in America: Using Knowledge of Radicalization Pathways To Forge Prevention Strategies ,” at Indiana State University, award number 2012-ZA-BX-0001; National Institute of Justice funding award description, “ A Comparative Study of Violent Extremism and Gangs ,” at the University of Maryland, award number 2014-ZA-BX-0002; National Institute of Justice funding award description, “ Across the Universe? A Comparative Analysis of Violent Radicalization Across Three Offender Types With Implications for Criminal Justice Training Education ,” at the University of Massachusetts Lowell, award number 2013-ZA-BX-0002; and National Institute of Justice funding award description, “ Transnational Crimes Among Somali-Americans: Convergences of Radicalization and Trafficking ,” at the Board of Trustees, University of Illinois Chicago, award number 2013-ZA-BX-0008.
[note 2] This review focuses on the Somali community more than other U.S. communities not because there were necessarily more cases of violent extremism there, but simply because two of the five grants that form the basis of this review were located there.
[note 3] All data in this paragraph come from David C. Pyrooz et al., “ Cut From the Same Cloth? A Comparative Study of Domestic Extremists and Gang Members in the United States ,” Justice Quarterly 35 no. 1 (2018): 1-32.
[note 4] All data in this paragraph come from Michael H. Becker et al., “ A Comparative Study of Initial Involvement in Gangs and Political Extremism ,” Terrorism and Political Violence 34 no. 8 (2022): 1647-1664.
[note 5] B. Heidi Ellis et al., “ Civic Development and Antisocial Attitudes/Behaviors Among Somali Immigrants: Change Over One Year ,” Cultural Diversity and Ethnic Minority Psychology 27 no. 2 (2021): 157-168; and B. Heidi Ellis et al., “ Relation of Psychosocial Factors to Diverse Behaviors and Attitudes Among Somali Refugees ,” American Journal of Orthopsychiatry 86 no. 4 (2016): 393-408.
[note 6] Ellis et al., “ Civic Development and Antisocial Attitudes/Behaviors Among Somali Immigrants ”; and Ellis et al., “ Relation of Psychosocial Factors to Diverse Behaviors and Attitudes Among Somali Refugees .”
[note 7] B. Heidi Ellis et al., “ A Qualitative Examination of How Somali Young Adults Think About and Understand Violence in Their Communities ,” Journal of Interpersonal Violence 37 no. 1-2 (2022): NP803-NP829.
[note 8] Ellis et al., “ A Qualitative Examination of How Somali Young Adults Think About and Understand Violence in Their Communities .”
[note 9] An example of the nexus between terrorism and human trafficking is the use of human trafficking by terrorist organizations to raise money or supply young women to their fighters — a phenomenon primarily found in international radicalization and conflict areas. In these areas, trafficking and sexual violence target girls and women of ideologically opposed groups, which spreads terror in the civilian population. Indeed, some have referred to sex trafficking and violence as a form of terrorism. The incentives for and ability of terrorist groups to engage in human trafficking are determined by their need for resources and the extent of their territorial control. See Daniel Sheinis, “ The Links Between Human Trafficking, Organized Crime, and Terrorism ,” American Intelligence Journal 30 no. 1 (2012): 68-77; Office of the Special Representative and Co-ordinator for Combating Trafficking in Human Beings, “ Trafficking in Human Beings and Terrorism: Where and How They Intersect ,” Vienna, Austria: Organization for Security and Co-operation in Europe, 2021; Cóman Kenny and Nikita Malik, “ Trafficking Terror and Sexual Violence: Accountability for Human Trafficking and Sexual and Gender-Based Violence by Terrorist Groups Under the Rome Statute ,” Vanderbilt Journal of Transnational Law 52 no. 1 (2021): 43-74; U.S. Congress, House, Committee on International Relations, Subcommittee on International Terrorism, Nonproliferation, and Human Rights, “ Global Trends in Trafficking and the ‘Trafficking in Persons Report,’ ” Hearing, June 25, 2003, 108th Cong., 1st sess., Serial No. 108-53; and Nazli Avdan and Mariya Omelicheva, “ Human Trafficking-Terrorism Nexus: When Violent Non-State Actors Engage in the Modern-Day Slavery ,” Journal of Conflict Resolution 65 no. 9 (2021): 1576-1606.
[note 10] Stevan Weine, Edna Erez, and Chloe Polutnik, “ Transnational Crimes Among Somali-Americans: Convergences of Radicalization and Trafficking ,” Final report to the National Institute of Justice, award number 2013-ZA-BX-0008, May 2019, NCJ 252135.
[note 11] The cities (in order of the size of the Somali community living there) are Minneapolis-St. Paul, Minnesota; Columbus, Ohio; and Nashville, Tennessee. It should be noted that although the cases of human trafficking tried in these cities did not result in convictions for various evidentiary concerns, the responses of those who were interviewed addressed human trafficking as if it did happen in the community.
[note 12] Unless otherwise noted, all data in this section come from Weine, Erez, and Polutnik, “ Transnational Crimes Among Somali-Americans ,” 33-42.
[note 13] Weine, Erez, and Polutnik, “ Transnational Crimes Among Somali-Americans ,” 53-57.
[note 14] John G. Horgan et al., “ Across the Universe? A Comparative Analysis of Violent Behavior and Radicalization Across Three Offender Types With Implications for Criminal Justice Training and Education ,” Final report to the National Institute of Justice, award number 2013-ZA-BX-0002, June 2016, NCJ 249937.
[note 15] Horgan et al., “ Across the Universe ,” 111.
[note 16] See also Mark S. Hamm and Ramón Spaaij, “ Lone Wolf Terrorism in America: Using Knowledge of Radicalization Pathways To Forge Prevention Strategies ,” Final report to the National Institute of Justice, award number 2012-ZA-BX-0001, February 2015, NCJ 248691; and Mark S. Hamm and Ramón Spaaij, The Age of Lone Wolf Terrorism (New York: Columbia University Press, 2017).
[note 17] Horgan et al., “ Across the Universe .”
[note 18] Horgan et al., “ Across the Universe .” See also the comprehensive follow-up work by Paul Gill, Lone-Actor Terrorists: A Behavioural Analysis (London: Routledge, 2015).
[note 19] Hamm and Spaaij, The Age of Lone Wolf Terrorism .
[note 20] All data in this paragraph come from Horgan et al., “ Across the Universe ”; and Gill, Lone-Actor Terrorists.
[note 21] Hamm and Spaaij, “ Lone Wolf Terrorism in America .”
[note 22] Hamm and Spaaij, “ Lone Wolf Terrorism in America .”
[note 23] Paul Gill and Emily Corner, “ There and Back Again: The Study of Mental Disorder and Terrorist Involvement ,” American Psychologist 72 no. 3 (2017): 231-241; and Norah Schulten et al., “ Radicalization, Terrorism & Psychopathology: State of Affairs, Gaps and Priorities for Future Research ,” The Hague, The Netherlands: Ministry of Justice and Security, 2019.
About the author
B. Heidi Ellis, Ph.D., is an associate professor of psychology in the Department of Psychiatry at Boston Children’s Hospital and Harvard Medical School, and the director of the Boston Children’s Hospital Trauma and Community Resilience Center. Edna Erez, Ph.D., is a professor in the Department of Criminology, Law, and Justice at the University of Illinois Chicago. John Horgan, Ph.D., is a distinguished university professor in the Department of Psychology at Georgia State University. Gary LaFree, Ph.D., is a distinguished university professor in the Department of Criminology and Criminal Justice at the University of Maryland. Ramón Spaaij, Ph.D., is a professor in the Institute for Health and Sport at Victoria University, Australia, and visiting professor at the Utrecht University School of Governance, The Netherlands.
Cite this Article
Read more about:, related awards.
- Gang Affiliation and Radicalization to Violent Extremism within Somali-American Communities
- Lone Wolf Terrorism in America: Using Knowledge of Radicalization Pathways to Forge Prevention Strategies
- A Comparative Study of Violent Extremism and Gangs
- Across the Universe? A Comparative Analysis of Violent Radicalization Across Three Offender Types with Implications for Criminal Justice Training and Education
- Transnational Crimes among Somali-Americans: Convergences of Radicalization and Trafficking

IMAGES
COMMENTS
40 Terrorism Research Paper Topics. Unfortunately, the theme of terrorism is now still very acute. The terroristic acts aren't history, they can happen in the centers of the peaceful cities of developed countries. No one is safe… but still it isn't the reason not to study terrorism and search ways to prevent it and, possibly, eliminate it ...
The results presented in. Table 1. clearly show that al-Qaeda, jihadism more generally and Iraq were the most frequently researched topics overall in the 2007-2016 period. Several other topics, such as "United States", "Counterterrorism/War on Terror" and "Afghanistan" were also frequent top-5 contenders.
Alex P. Schmid, 50 Un- and Under-researched Topics in the Field of (Counter-) Terrorism Studies, Perspectives on Terrorism, Vol. 5, No. 1 (March 2011), pp. 76-78
The scholarly literature on terrorism research is estimated to have exceeded 18,651 items as of September 2020. Articles of this literature have been disseminated across of range of different sources and disciplines including social and psychological sciences, but their concentration is most noticeable in two particular disciplines: "Political Science" (N = 4177) and "International ...
Research on terrorism has long been criticized for its inability to overcome enduring methodological issues. ... resources available to addressing the topics being investigated. The 9/11 attacks and the global war on terrorism that followed brought new funding and researchers to the field. ... 74.7% of research-based papers were the work of a ...
RAND Europe. RAND Social and Economic Well-Being. From the Munich Olympics to 9/11 to worldwide bombings and mass shootings, terrorism is by no means a localized or recent phenomenon. Efforts to both catalog and counter terrorism, both in the United States and abroad, have been a key focus of RAND research since the early 1970s.
Critical Studies on Terrorism aims to create space for robust, innovative research on terrorism and political violence, and encourages fruitful intellectual engagement between critical and orthodox accounts of terrorism. In particular, the Editors are looking for empirical, theoretical and policy-oriented articles that recognise the inherently ...
Despite the extraordinary social and political consequences often associated with terrorist violence, as well as our responses to it, psychological research on terrorist behavior is conspicuously underdeveloped. This special issue of American Psychologist presents a series of articles that showcase new conceptual, theoretical, and empirical advances in our understanding of terrorism. In doing ...
Weapons and Tactics. Communications and Transition Manager. 301-405-6632. Contact us.
Terrorist Network Analysis (TNA) is the field of analyzing and defining the scope of terrorism and researching the countermeasures in order to handle exponentially increasing threats due to ever growing terrorist based activities. This field constitutes several sub-domains such as crawling the data about terrorist attacks/groups, classification, behavioral, and predictive analysis. In this ...
The findings of this study suggest that globalization has contributed to the rise of terrorism, and that its impacts on global peace and. security are complex and multi-faceted. The impact of ...
The then US President George W. Bush ( 2002)ar-. gued that there is a vicious circle of disenfranchisement, state failure and terror, stating that. because ' [ ...] persistent poverty and ...
Researching of Morals of Terrorists. Terrorism attacks are a form of violence, and the moral implication is death in the form of revenge. Realism is a form of acceptance that everyone on the battlefield is a civilian with their families. The Structures, Motivations, and Qualities of Terrorist Groups.
National Research Council. 2002. Terrorism: Perspectives from the Behavioral and Social Sciences. Washington, DC: The National Academies Press. doi: 10.17226/10570. ... because the research topics themselves are ideologically loaded and lie at the basis of debates and political divisions in American society. It is also important to examine the ...
The post-9/11 average through 2019 is 304 articles per year. Several additional points are apparent. First, the post-9/11 increase started in 2001—in spite of the attacks occurring in September, and time required peer review. 2001 saw 168 articles on terrorism, mostly in the final months of the year.
Research Paper. Snapshot. Topics. Counter-Terrorism & Counter-Extremism. Criminal Justice & Administrative Measures. ... A Look at the State of Research on [Counter-] Terrorism and Violent Extremism 19 Dec 2023. by { The Global Politics of Counter-Terrorism. ...
Two Decades Later, the Enduring Legacy of 9/11. Twenty years ago, Americans came together - bonded by sadness and patriotism - after the 9/11 terrorist attacks. But a review of public opinion in the two decades since finds that unity was fleeting. It also shows how support for the wars in Afghanistan and Iraq was strong initially but fell ...
Terrorism is a subject which provokes extreme perceptions, perceptions which spill easily into considerations of the actors behind the violence. Misconceptions and prejudices born in the wake of ...
Two Decades Later, the Enduring Legacy of 9/11. Twenty years ago, Americans came together - bonded by sadness and patriotism - after the 9/11 terrorist attacks. But a review of public opinion in the two decades since finds that unity was fleeting. It also shows how support for the wars in Afghanistan and Iraq was strong initially but fell ...
Terrorism is a major global threat to public safety and security. It is an unlawful use of violence and intimidation to achieve political, ideological or religious goals. Terrorist attacks are always extremely devastating and have the potential to cause significant destruction, fear, injury and even death.
Response Paper(s) Students will be presented with a number of prompts and will choose one to write on. Undergraduates will do two small reseach papers. Graduate students will write a single long research paper. Papers must fully answer the prompt and provide a thoughtful response. Exams- 50%!! Exams will be based on the following components:
On the contrary, the internet is considered by leading scholars as one of the "hot topics" Footnote 26 in terrorism research and many interesting articles have been published on terrorist use of the internet. ... As further specified in the U.K. Home Office's Online Harms White Paper, ...
This paper states that the phenomenon of terrorism is tightly connected to the concept of inequality of globalization. Terrorist Attack in San Bernardino. The San Bernardino shootings in 2015 killed 14 innocent people and injured 24 more. It was also the bloodiest mass shooting in the US since 2012.
Targeted violence spans a wide array of offenses, from mass shootings to gang or group-violence-related activities to human trafficking. Although each of these topics has been researched extensively, until recently they have not been studied to identify similarities and differences in the context of domestic violent extremism and terrorism. Gaining a better understanding of any links or ...