

8 Introduction to Viruses
Viruses are typically described as obligate intracellular parasites , acellular infectious agents that require the presence of a host cell in order to multiply. Viruses that have been found to infect all types of cells – humans, animals, plants, bacteria, yeast, archaea, protozoa…some scientists even claim they have found a virus that infects other viruses! But that is not going to happen without some cellular help.
Virus Characteristics
Viruses can be extremely simple in design, consisting of nucleic acid surrounded by a protein coat known as a capsid . The capsid is composed of smaller protein components referred to as capsomers . The capsid+genome combination is called a nucleocapsid .
Viruses can also possess additional components, with the most common being an additional membranous layer that surrounds the nucleocapsid, called an envelope . The envelope is actually acquired from the nuclear or plasma membrane of the infected host cell, and then modified with viral proteins called peplomers . Some viruses contain viral enzymes that are necessary for infection of a host cell and coded for within the viral genome. A complete virus, with all the components needed for host cell infection, is referred to as a virion .
Virus Genome
While cells contain double-stranded DNA for their genome, viruses are not limited to this form. While there are dsDNA viruses, there are also viruses with single-stranded DNA ( ssDNA ), double-stranded RNA ( dsRNA ), and single-stranded RNA ( ssRNA ). In this last category, the ssRNA can either positive-sense ( +ssRNA , meaning it can transcribe a message, like mRNA) or it can be negative-sense ( -ssRNA , indicating that it is complementary to mRNA). Some viruses even start with one form of nucleic acid in the nucleocapsid and then convert it to a different form during replication.
Virus Structure
Viral nucleocapsids come in two basic shapes, although the overall appearance of a virus can be altered by the presence of an envelope, if present. Helical viruses have an elongated tube-like structure, with the capsomers arranged helically around the coiled genome. Icosahedral viruses have a spherical shape, with icosahedral symmetry consisting of 20 triangular faces. The simplest icosahedral capsid has 3 capsomers per triangular face, resulting in 60 capsomers for the entire virus. Some viruses do not neatly fit into either of the two previous categories because they are so unusual in design or components, so there is a third category known as complex viruses . Examples include the poxvirus with a brick-shaped exterior and a complicated internal structure, as well as bacteriophage with tail fibers attached to an icosahedral head.
Virus Replication Cycle
While the replication cycle of viruses can vary from virus to virus, there is a general pattern that can be described, consisting of five steps:
- Attachment – the virion attaches to the correct host cell.
- Penetration or Viral Entry – the virus or viral nucleic acid gains entrance into the cell.
- Synthesis – the viral proteins and nucleic acid copies are manufactured by the cells’ machinery.
- Assembly – viruses are produced from the viral components.
- Release – newly formed virions are released from the cell.
Outside of their host cell, viruses are inert or metabolically inactive. Therefore, the encounter of a virion to an appropriate host cell is a random event. The attachment itself is highly specific, between molecules on the outside of the virus and receptors on the host cell surface. This accounts for the specificity of viruses to only infect particular cell types or particular hosts.
Penetration or Viral Entry
Many unenveloped (or naked ) viruses inject their nucleic acid into the host cell, leaving an empty capsid on the outside. This process is termed penetration and is common with bacteriophage, the viruses that infect bacteria. With the eukaryotic viruses, it is more likely for the entire capsid to gain entrance into the cell, with the capsid being removed in the cytoplasm. An unenveloped eukaryotic virus often gains entry via endocytosis , where the host cell is compelled to engulf the capsid resulting in an endocytic vesicle, allowing the virus access to the cell contents. An enveloped eukaryotic virus gains entrance for its nucleocapsid through membrane fusion , where the viral envelope fuses with the host cell membrane, pushing the nucleocapsid past the cell membrane. If the entire nucleocapsid is brought into the cell then there is an uncoating process to strip away the capsid and release the viral genome.
The synthesis stage is largely dictated by the type of viral genome, since genomes that differ from the cell’s dsDNA genome can involve intricate viral strategies for genome replication and protein synthesis. Viral specific enzymes, such as RNA-dependent RNA polymerases, might be necessary for the replication process to proceed. Protein production is tightly controlled, to insure that components are made at the right time in viral development.
The complexity of viral assembly depends upon the virus being made. The simplest virus has a capsid composed of 3 different types of proteins, which self-assembles with little difficulty. The most complex virus is composed of over 60 different proteins, which must all come together in a specific order. These viruses often employ multiple assembly lines to create the different viral structures and then utilize scaffolding proteins to put all the viral components together in an organized fashion.
The majority of viruses lyse their host cell at the end of replication, allowing all the newly formed virions to be released to the environment. Another possibility, common for enveloped viruses, is budding , where one virus is released from the cell at a time. The cell membrane is modified by the insertion of viral proteins, with the nucleocapsid pushing out through this modified portion of the membrane, allowing it to acquire an envelope.
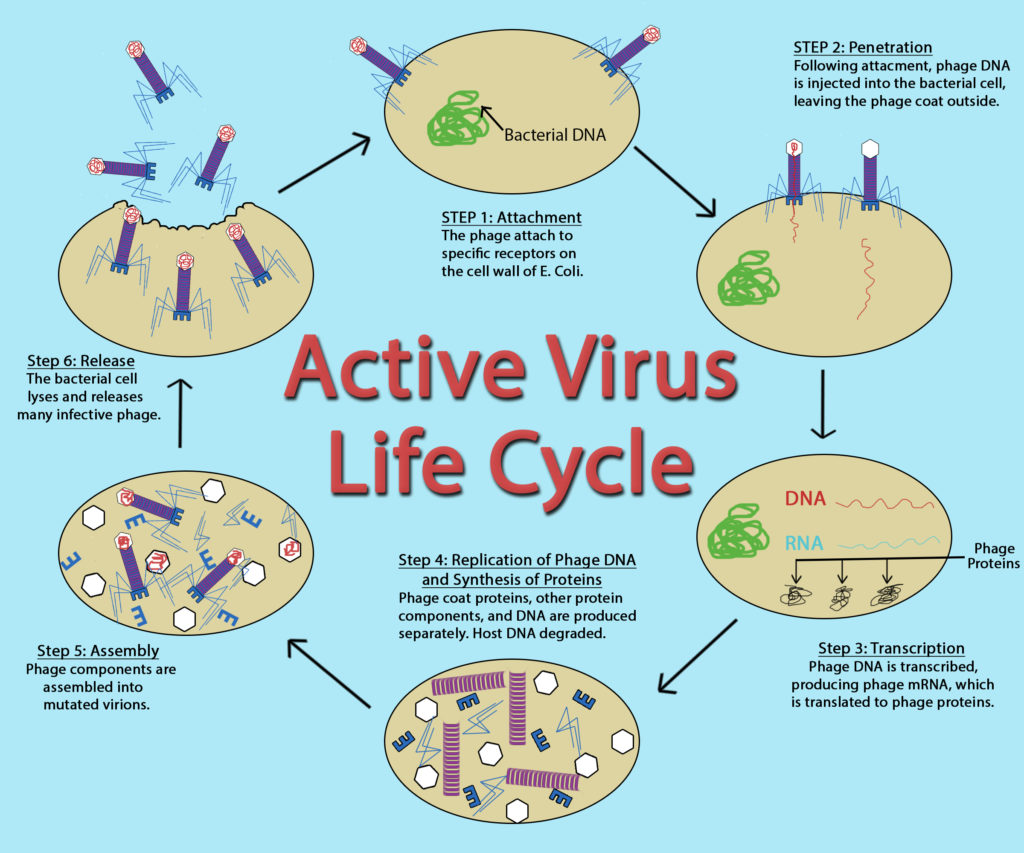
Bacteriophage
Viruses that infect bacteria are known as bacteriophage or phage . A virulent phage is one that always lyses the host cell at the end of replication, after following the five steps of replication described above. This is called the lytic cycle of replication.
There are also temperate phage , viruses that have two options regarding their replication. Option 1 is to mimic a virulent phage, following the five steps of replication and lysing the host cell at the end, referred to as the lytic cycle. But temperate phage differ from virulent phage in that they have another choice: Option 2, where they remain within the host cell without destroying it. This process is known as lysogeny or the lysogenic cycle of replication.
A phage employing lysogeny still undergoes the first two steps of a typical replication cycle, attachment and penetration. Once the viral DNA has been inserted into the cell it integrates with the host DNA, forming a prophage . The infected bacterium is referred to as a lysogen or lysogenic bacterium . In this state, the virus enjoys a stable relationship with its host, where it does not interfere with host cell metabolism or reproduction. The host cell enjoys immunity from reinfection from the same virus.
Exposure of the host cell to stressful conditions (i.e. UV irradiation) causes induction , where the viral DNA excises from the host cell DNA. This event triggers the remaining steps of the lytic cycle, synthesis, maturation, and release, leading to lysis of the host cell and release of newly formed virions.
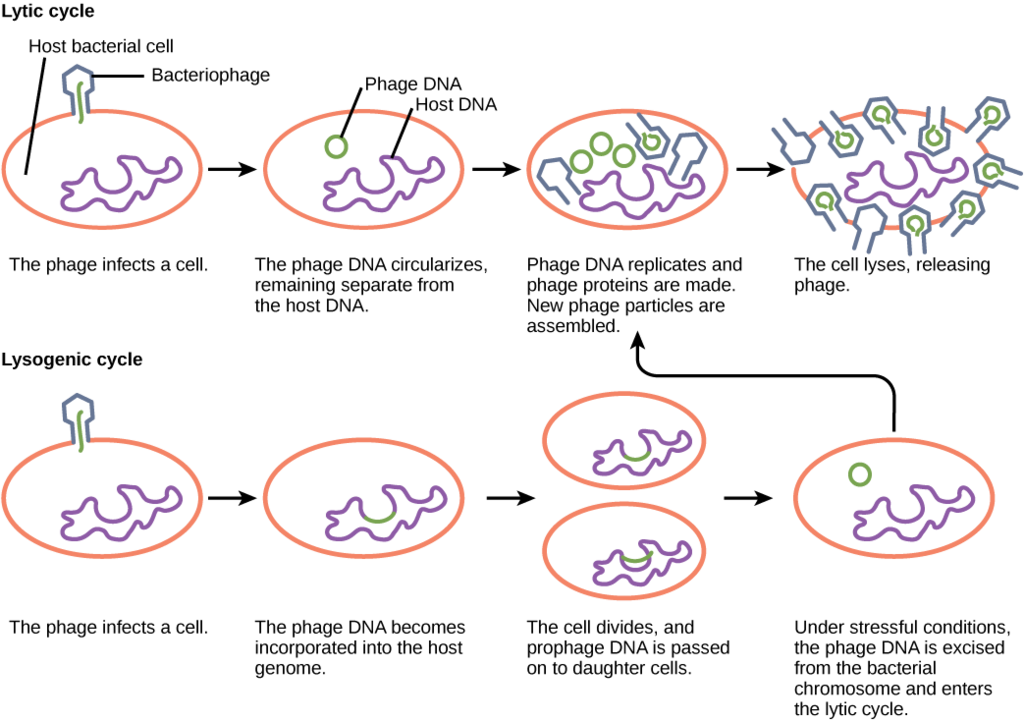
So, what dictates the replication type that will be used by a temperate phage? If there are plenty of host cells around, it is likely that a temperate phage will engage in the lytic cycle of replication, leading to a large increase in viral production. If host cells are scarce, a temperate phage is more likely to enter lysogeny, allowing for viral survival until host cell numbers increase. The same is true if the number of phage in an environment greatly outnumber the host cells, since lysogeny would allow for host cells numbers to rebound, ensuring long term viral survival.
Lysogens can experience a benefit from lysogeny as well, since it can result in lysogenic conversion , a situation where the development of a prophage leads to a change in the host’s phenotype. One of the best examples of this is for the bacterium Corynebacterium diphtheriae , the causative agent of diphtheria. The diphtheria toxin that causes the disease is encoded within the phage genome, so only C. diphtheriae lysogens cause diphtheria.
Eukaryotic Viruses
Eukaryotic viruses can cause one of four different outcomes for their host cell. The most common outcome is host cell lysis, resulting from a virulent infection (essentially the lytic cycle of replication seen in phage). Some viruses can cause a latent infection , inserting their viral DNA into the host cell genome, allowing them to co-exist peacefully with their host cells for long periods of time (much like a temperate phage during lysogeny). Some enveloped eukaryotic viruses can also be released one at a time from an infected host cell, in a type of budding process, causing a persistent infection . Lastly, certain eukaryotic viruses can cause the host cell to transform into a malignant or cancerous cell, a mechanism known as transformation .
Viruses and Cancer
There are many different causes of cancer, or unregulated cell growth and reproduction. Some known causes include exposure to certain chemicals or UV light. There are also certain viruses that have a known associated with the development of cancer. Such viruses are referred to as oncoviruses . Oncoviruses can cause cancer by producing proteins that bind to host proteins known as tumor suppressor proteins , which function to regulate cell growth and to initiate programmed cell death, if needed. If the tumor suppressor proteins are inactivated by viral proteins then cells grow out of control, leading to the development of tumors and metastasis, where the cells spread throughout the body.
virus, obligate intracellular parasite, capsid, bacteriophage, capsomere, nucleocapsid, envelope, peplomer, virion, dsDNA, ssDNA, dsRNA, +ssRNA, -ssRNA, helical viruses, icosahedral viruses, complex viruses, attachment, penetration, viral entry, synthesis, assembly, release, naked virus, endocytosis, membrane fusion, budding, bacteriophage, phage, virulent phage, lytic cycle, temperate phage, lysogeny, lysogenic cycle, prophage, lysogen, lysogenic bacterium, induction, lysogenic conversion, virulent infection, latent infection, persistent infection, transformation, oncovirus, tumor suppressor proteins.
Study Questions
- What are the general properties of a virus?
- What is the size range of viruses? How do they compare, size-wise, to bacteria?
- What is the general structure of viruses? What are the different components?
- What viral shapes exist?
- How do envelopes and enzymes relate to viruses?
- What types of viral genomes exist?
- What are the 5 basic steps of viral replication? What happens at each step? How do bacterial/archaeal viruses differ from eukaryotic viruses, in regards to replication details?
- What are the 2 types of viral infection found in Bacteria/Archaea ? What are the specific terms associated with viral infection of bacterial/archaeal cells?
- What are the 4 types of viral infection found in eukaryotes?
- How do some viruses cause cancer?
Exploratory Questions (OPTIONAL)
- What is the largest bacterium or archaean ever discovered? What is the smallest eukaryote ever discovered?
General Microbiology Copyright © 2019 by Linda Bruslind is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License , except where otherwise noted.
- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World

Computer viruses explained: Definition, types, and examples
This malicious software tries to do its damage in the background while your computer still limps along..

Computer virus definition
A computer virus is a form of malicious software that piggybacks onto legitimate application code in order to spread and reproduce itself.
Like other types of malware , a virus is deployed by attackers to damage or take control of a computer. Its name comes from the method by which it infects its targets. A biological virus like HIV or the flu cannot reproduce on its own; it needs to hijack a cell to do that work for it, wreaking havoc on the infected organism in the process. Similarly, a computer virus isn’t itself a standalone program. It’s a code snippet that inserts itself into some other application. When that application runs, it executes the virus code, with results that range from the irritating to the disastrous.
Virus vs. malware vs. trojan vs. worm
Before we continue a brief note on terminology. Malware is a general term for malicious computer code. A virus, as noted, is specifically a kind of malware that infects other applications and can only run when they run. A worm is a malware program that can run, reproduce, and spread on its own , and a Trojan is malware that tricks people into launching it by disguising itself as a useful program or document. You’ll sometimes see virus used indiscriminately to refer to all types of malware, but we’ll be using the more restricted sense in this article.
What do computer viruses do?
Imagine an application on your computer has been infected by a virus. (We’ll discuss the various ways that might happen in a moment, but for now, let’s just take infection as a given.) How does the virus do its dirty work? Bleeping Computer provides a good high-level overview of how the process works. The general course goes something like this: the infected application executes (usually at the request of the user), and the virus code is loaded into the CPU memory before any of the legitimate code executes.
At this point, the virus propagates itself by infecting other applications on the host computer, inserting its malicious code wherever it can. (A resident virus does this to programs as they open, whereas a non-resident virus can infect executable files even if they aren’t running.) Boot sector viruses use a particularly pernicious technique at this stage: they place their code in the boot sector of the computer’s system disk, ensuring that it will be executed even before the operating system fully loads, making it impossible to run the computer in a “clean” way. (We’ll get into more detail on the different types of computer virus a bit later on.)
Once the virus has its hooks into your computer, it can start executing its payload , which is the term for the part of the virus code that does the dirty work its creators built it for. These can include all sorts of nasty things: Viruses can scan your computer hard drive for banking credentials, log your keystrokes to steal passwords, turn your computer into a zombie that launches a DDoS attack against the hacker’s enemies, or even encrypt your data and demand a bitcoin ransom to restore access . (Other types of malware can have similar payloads.)
How do computer viruses spread?
In the early, pre-internet days, viruses often spread from computer to computer via infected floppy disks. The SCA virus, for instance, spread amongst Amiga users on disks with pirated software . It was mostly harmless, but at one point as many as 40% of Amiga users were infected.
Today, viruses spread via the internet. In most cases, applications that have been infected by virus code are transferred from computer to computer just like any other application. Because many viruses include a logic bomb — code that ensures that the virus’s payload only executes at a specific time or under certain conditions—users or admins may be unaware that their applications are infected and will transfer or install them with impunity. Infected applications might be emailed (inadvertently or deliberately—some viruses actually hijack a computer’s mail software to email out copies of themselves); they could also be downloaded from an infected code repository or compromised app store.
One thing you’ll notice all of these infection vectors have in common is that they require the victim to execute the infected application or code. Remember, a virus can only execute and reproduce if its host application is running! Still, with email such a common malware dispersal method, a question that causes many people anxiety is: Can I get a virus from opening an email? The answer is that you almost certainly can’t simply by opening a message; you have to download and execute an attachment that’s been infected with virus code. That’s why most security pros are so insistent that you be very careful about opening email attachments, and why most email clients and webmail services include virus scanning features by default.
A particularly sneaky way that a virus can infect a computer is if the infected code runs as JavaScript inside a web browser and manages to exploit security holes to infect programs installed locally. Some email clients will execute HTML and JavaScript code embedded in email messages, so strictly speaking, opening such messages could infect your computer with a virus . But most email clients and webmail services have built-in security features that would prevent this from happening, so this isn’t an infection vector that should be one of your primary fears.
Can all devices get viruses?
Virus creators focus their attention on Windows machines because they have a large attack surface and wide installed base. But that doesn’t mean other users should let their guard down. Viruses can afflict Macs, iOS and Android devices, Linux machines, and even IoT gadgets. If it can run code, that code can be infected with a virus.
Types of computer virus
Symantec has a good breakdown on the various types of viruses you might encounter , categorized in different ways. The most important types to know about are:
- Resident viruses infect programs that are currently executing.
- Non-resident viruses , by contrast, can infect any executable code, even if it isn’t currently running
- Boot sector viruses infect the sector of a computer’s startup disk that is read first , so it executes before anything else and is hard to get rid of
- A macro virus infects macro applications embedded in Microsoft Office or PDF files. Many people who are careful about never opening strange applications forget that these sorts of documents can themselves contain executable code. Don’t let your guard down!
- A polymorphic virus slightly changes its own source code each time it copies itself to avoid detection from antivirus software.
- Web scripting viruses execute in JavaScript in the browser and try to infect the computer that way.
Keep in mind that these category schemes are based on different aspects of a virus’s behavior, and so a virus can fall into more than one category. A resident virus could also be polymorphic, for instance.
How to prevent and protect against computer viruses
Antivirus software is the most widely known product in the category of malware protection products. CSO has compiled a list of the top antivirus software for Windows , Android , Linux and macOS , though keep in mind that antivirus isn’t a be-all end-all solution . When it comes to more advanced corporate networks, endpoint security offerings provide defense in depth against malware . They provide not only the signature-based malware detection that you expect from antivirus, but antispyware, personal firewall, application control and other styles of host intrusion prevention. Gartner offers a list of its top picks in this space , which include products from Cylance, CrowdStrike, and Carbon Black.
One thing to keep in mind about viruses is that they generally exploit vulnerabilities in your operating system or application code in order to infect your systems and operate freely; if there are no holes to exploit, you can avoid infection even if you execute virus code. To that end, you’ll want to keep all your systems patched and updated, keeping an inventory of hardware so you know what you need to protect, and performing continuous vulnerability assessments on your infrastructure.
Computer virus symptoms
How can you tell if a virus has slipped past your defenses? With some exceptions, like ransomware, viruses are not keen to alert you that they’ve compromised your computer. Just as a biological virus wants to keep its host alive so it can continue to use it as a vehicle to reproduce and spread, so too does a computer virus attempt to do its damage in the background while your computer still limps along. But there are ways to tell that you’ve been infected. Norton has a good list ; symptoms include:
- Unusually slow performance
- Frequent crashes
- Unknown or unfamiliar programs that start up when you turn on your computer
- Mass emails being sent from your email account
- Changes to your homepage or passwords
If you suspect your computer has been infected, a computer virus scan is in order. There are plenty of free services to start you on your exploration: The Safety Detective has a rundown of the best.
Remove computer virus
Once a virus is installed on your computer, the process of removing it is similar to that of removing any other kind of malware—but that isn’t easy. CSO has information on how to remove or otherwise recover from rootkits , ransomware , and cryptojacking . We also have a guide to auditing your Windows registry to figure out how to move forward.
If you’re looking for tools for cleansing your system, Tech Radar has a good roundup of free offerings , which contains some familiar names from the antivirus world along with newcomers like Malwarebytes. And it’s a smart move to always make backups of your files , so that if need be you can recover from a known safe state rather than attempting to extricate virus code from your boot record or pay a ransom to cybercriminals.
Computer virus history
The first true computer virus was Elk Cloner , developed in 1982 by fifteen-year-old Richard Skrenta as a prank. Elk Cloner was an Apple II boot sector virus that could jump from floppy to floppy on computers that had two floppy drives (as many did). Every 50th time an infected game was started, it would display a poem announcing the infection.
Other major viruses in history include:
- Jerusalem : A DOS virus that lurked on computers, launched on any Friday the 13th, and deleted applications.
- Melissa : A mass-mailing macro virus that brought the underground virus scene to the mainstream in 1999. It earned its creator 20 months in prison.
But most of the big-name malware you’ve heard of in the 21st century has, strictly speaking, been worms or Trojans, not viruses. That doesn’t mean viruses aren’t out there, however—so be careful what code you execute.
Related content
Cisa opens its malware analysis and threat hunting tool for public use, top cybersecurity m&a deals for 2024, isc2 study pegs average us cybersecurity salary at $147k, up from $119k in 2021, top cybersecurity product news of the week, from our editors straight to your inbox.

Josh Fruhlinger is a writer and editor who lives in Los Angeles.
More from this author
Defense in depth explained: layering tools and processes for better security, what is an sbom software bill of materials explained, 11 infamous malware attacks: the first and the worst, 9 types of computer virus and how they do their dirty work, most popular authors.

Show me more
Customers of sisense data analytics service urged to change credentials.

OWASP Top 10 OSS Risks: A guide to better open source security

What “next-gen” identity security actually means - and why it’s increasingly essential

CSO Executive Sessions: Geopolitical tensions in the South China Sea - why the private sector should care

CSO Executive Sessions: 2024 International Women's Day special

CSO Executive Sessions: Former convicted hacker Hieu Minh Ngo on blindspots in data protection

A review: Mechanism of action of antiviral drugs
Shamaila kausar.
1 Institute of Molecular Biology and Biotechnology, The University of Lahore, Lahore, Pakistan
Fahad Said Khan
2 Department of Eastern Medicine, Government College University Faisalabad, Faisalabad, Pakistan
Muhammad Ishaq Mujeeb Ur Rehman
Muhammad akram, muhammad riaz.
3 Department of Allied Health Sciences, Sargodha Medical College, University of Sargodha, Sargodha, Pakistan
Ghulam Rasool
Abdul hamid khan.
4 Department of Eastern Medicine, University of Poonch, Rawalakot, Azad Jammu and Kashmir, Pakistan
Iqra Saleem
5 Department of Pharmacy, Faculty of Medical and Health Sciences, University of Poonch, Rawalakot, Azad Jammu and Kashmir, Pakistan
Saba Shamim
Antiviral drugs are a class of medicines particularly used for the treatment of viral infections. Drugs that combat viral infections are called antiviral drugs. Viruses are among the major pathogenic agents that cause number of serious diseases in humans, animals and plants. Viruses cause many diseases in humans, from self resolving diseases to acute fatal diseases. Developing strategies for the antiviral drugs are focused on two different approaches: Targeting the viruses themselves or the host cell factors. Antiviral drugs that directly target the viruses include the inhibitors of virus attachment, inhibitors of virus entry, uncoating inhibitors, polymerase inhibitors, protease inhibitors, inhibitors of nucleoside and nucleotide reverse transcriptase and the inhibitors of integrase. The inhibitors of protease (ritonavir, atazanavir and darunavir), viral DNA polymerase (acyclovir, tenofovir, valganciclovir and valacyclovir) and of integrase (raltegravir) are listed among the Top 200 Drugs by sales during 2010s. Still no effective antiviral drugs are available for many viral infections. Though, there are a couple of drugs for herpesviruses, many for influenza and some new antiviral drugs for treating hepatitis C infection and HIV. Action mechanism of antiviral drugs consists of its transformation to triphosphate following the viral DNA synthesis inhibition. An analysis of the action mechanism of known antiviral drugs concluded that they can increase the cell’s resistance to a virus (interferons), suppress the virus adsorption in the cell or its diffusion into the cell and its deproteinisation process in the cell (amantadine) along with antimetabolites that causes the inhibition of nucleic acids synthesis. This review will address currently used antiviral drugs, mechanism of action and antiviral agents reported against COVID-19.
Introduction
Infectious diseases are well known since ancient time to human civilisation. Infectious disease are caused due to different microorganisms (bacteria, viruses and fungi). 1 Viral structure is simple and consists of a protein coat, nucleic acid, viral enzymes and, sometimes, a lipid envelope, unlike the complex structure of fungi, helminths and protozoa. Additionally, viruses use the host’s cellular machinery for replication, hence are obligate intracellular pathogens. Such characteristics create the difficulties in developing drugs with selective toxicity against viruses. 2 Viruses are ultra microscopic agents having either DNA or RNA as the genetic material and are known to cause variety of diseases in humans, animals and plants. The fight between humans and viruses is continuous process, as both will adopt different strategies to fight against each other. Antiviral drugs development is a tedious process involving many stages such as target identification and screening, lead generation and optimisation, clinical studies and the drug registration, etc. 3 Dynamic antiviral drug development is a pressing need, as viral infections have caused millions of human fatalities worldwide over the course of human civilisation. The approval of first antiviral drug ‘idoxuridine’ in June 1963 has opened a new era in antiviral drug development. Since then, number of drugs with antiviral potential have been developed for clinical use for the treatment of millions of human beings worldwide. 4 Antiviral drugs are a class of medicines particularly used for the treatment of viral infections. Specific antiviral drugs are used for treating specific viruses just like the antibiotics for bacteria. Antiviral drugs, unlike the most antibiotics, do not destroy their target pathogens; rather inhibit their development. As the viruses use the host’s cells to replicate, hence makes it difficult to design a safe and effective antiviral drug. Therefore, it is difficult to find the drug targets that would interfere with the virus without damaging the host’s cells. Furthermore, the major complications in developing anti-viral drugs and vaccines are because of viral variation. 5 One of the important ways of finding antiviral drugs is the computer based drug discovery and for this approach nelfinavir is an example discovered in the 1990s for the treatment of human immunodeficiency virus (HIV) infection. 6
In spite of modern tools and stringent measures for the quality control only a few antiviral drugs are getting approved for the use of human either due to the side effects or resistance to antiviral drugs. With increase in the awareness about the viruses, their mechanism of infection and the rapid evolvement of novel strategies and techniques for antiviral will speed up the novel antiviral drugs development. 7 The current scenario all over the world indicates that continuous emergence of microbial threats at an accelerating pace, mainly due to unprecedented climate change and globalisation. 8
Viruses such as poxviruses, herpes, adenoviruses and papilloma viruses usually contain double-stranded DNA, leaving single-digit DNA. DNA virus enters the cell centre and leads to new viruses.
RNA viruses include influenza, measles, mumps, colds, meningitis, polio, retroviruses (AIDS, T-cell leukaemia), arena viruses, all considered, single descriptor RNA (ssRNA). RNA virus does not enter the cell centre (in addition to the cold virus contamination this season). Viral RNA is then used to make a DNA copy of the viral RNA, which is organised by the host genome followed by a retroviruses.
Steps of viral infections
Viral infection involves the entry of viral DNA into a host cell, replication of that DNA and releasing the new viruses. The six steps of viral replication include viral attachment, invasion, uncoating, replication, assembly and release. The steps of virus life cycle highlighting the entry and exit of the virus are described below 9 ( Figure 1 and Table 1 ).

Common inhibitory actions of antiviral drugs.
Mechanism of action of antiviral drugs used for the treatment of COVID-19.
- The virus attaches to a host cell injecting its genetic material into the host cell during attachment and penetration stage.
- In the next step, the viral DNA or RNA is itself incorporated into the genetic material of the host cell inducing it to replicate the viral genome. This step involves the uncoating, replication and assembly during the virus life cycle.
- During release, the host cell releases the newly created viruses, either through the breakage of the cell, waiting cell death or by budding off through the cell membrane. 9 , 10
Antiviral medication and its mechanism of action
Acyclovir is the basis of 2′-deoxiguanosin which applies antiviral effects after manipulation on acyclovir triphosphate. The hidden development of this methodology, an increase in acyclovir monophosphate, is catalysed by thymidine kinase caused by cells contaminated by herpes simplex infection 11 , 12 or varicella zoster infection or phosphotransferase made by cytomegalovirus. Cellular protein then adds phosphate to produce acyclovir diphosphate and acyclovir triphosphate. Acyclovir triphosphate slows the mixing of viral DNA by countering 2′-deoxy guanosin triphosphate as a substrate for viral DNA polymerase. 11 , 12 After acyclovir (not 2′-deoxiguanosin) was implanted in a duplicate of viral DNA, fusion stopped. The acyclovir monophosphate circuit into viral DNA is irreversible, given the way exonuclease bound to polymerases 3′, 5′ cannot separate them. 13 In this technique, viral DNA polymerase is inactivated in the same way. Acyclovir triphosphate is 30 times greater than herpes simplex type 1 DNA polymerase inhibitors than human alpha-DNA polymerase cells. 14 The small formation of acyclovir triphosphate in uninfected cells and its expression for DNA viral load results in harmless cellular toxic effects. In addition, more than 80% of acyclovir that appears during diffusion is unaffected in the urine. 15 The 50% central acyclovir inhibitory group in contradiction of herpes simplex disease type 1 is 0.1 μM, and 0.4 μM against herpes simplex disease type 2 16 and 47.1 µM against cytomegalovirus. 17 Even with reduced oral bioavailability, obsession with plasma acyclovir exceeds 50% inhibitory concentration for type 1 and 2 herpes simplex contamination that grows in adults after a combination of 200 mg d ‘Acyclovir, on the other hand, 800 mg is very important to provide plasma obsession over the centre 50% inhibitory concentration for varicella zoster virus. Acyclovir with a fairly short half-life of plasma, 7.7 mg should be given every 4–6 h for patients damaged by varicella-zoster infection. Acyclovir has been shown to be suitable for the treatment of pollution resulting from contamination with herpes simplex types 1 and 2 18 and varicella-zoster virus and to disguise specific types of cytomegalovirus. 16
Valacyclovir
Valacyclovir, L-valyl ester from acyclovir, is also available in oral form. After swallowing, drug is immediately changed to acyclovir by the substance valacyclovir hydrolase in the digestive tract and liver. The original bioavailability is three to several times that of acyclovir. 19 Valacyclovir has proven exceptional in treatment of pollution obtained by the herpes simplex virus and varicella-zoster virus and in prophylaxis against cytomegalovirus. Ganciclovir, which starts overseeing the Journal late, contrasts with acyclovir by extending a hydroxymethyl group in position 3′ from a non-cyclic side chain. The assimilation and arrangement of its action are similar to acyclovir, on the other hand, it actually has carbon 3′ with a hydroxyl package that can allow the widening of the foundation design similar to levelled DNA chain terminators. Ganciclovir is replaced by ganciclovir monophosphate by viral encoded phosphotransferase sent to cells contaminated with cytomegalovirus. This is a substrate that is superior to acyclovir for this phosphotransferase, and half the presence of intracellular ganciclovir triphosphate in any case is 12 h, compared to 1–2 h for acyclovir. This difference is the reason why ganciclovir is better than acyclovir for the treatment of cytomegalovirus. Peak plasma fixation after intravenous administration in common portions is much higher than 3 μM, which should inhibit most cytomegalovirus strains. 20 Intravenous ganciclovir is very powerful for hiding and treating cytomegalovirus. Oral ganciclovir has also been found to be beneficial in hiding cytomegalovirus 28, but its value is limited by its low bioavailability (8%–9%). 21
Penciclovir
Penciclovir is basically like ganciclovir, in contrast only by replacing the methylene connection for oxygen either in the non-cyclic ribose portion of the particle. Its digestive component and activity are similar to acyclovir, so again, it is only a DNA chain terminator that is bound. The inhibitory effect of in vitro penciclovir on herpes simplex 1 and 2 types and varicella-zoster infection is alike to acyclovir. 22 Now, it has claimed only as topical plan for the treatment of cold sores. Intravenous preparations are considered as treatment for mucocutaneous herpes in immunocompromised patients.
Famciclovir
Famciclovir is a simple diacetyl-6-deoxy from penciclovir. All this is assimilated after oral organisation and is quickly used for penciclovir by deacetylation in digestive tract, blood and liver, next it is oxidised by liver in position 6 of purine cycle. Half of the presence of a dynamic intracellular drug, penciclovir triphosphate, is very long, offering the possible for a dose once a day. Famciclovir works against genital herpes and the shingles virus. 23
Foscarnet (trisodium phosphonoformate) is a simple and natural inorganic pyrophosphate. This building structure with DNA, DNA polymerase at the site which limits the pyrophosphate, maintains the division of the pyrophosphate from the nucleoside triphosphate and along this line blocks a further increase in base format. Foscarnet should be administered intravenously, as fair oral details have not yet been made. It is not treated at a clear level and is destroyed by glomerular filtration and removal of the cylinder. Clinical examination shows that foscarnet is identical to ganciclovir for the treatment of cytomegalovirus and better than vidarabine for the treatment of contamination caused by an acyclovir-resistant herpes simplex infection. 24
Ribavirin is a simple guanosine that has an inadequate purine cycle as opposed to a serving of non-cyclic ribose. After intracellular phosphorylation, ribavirin triphosphate interferes with the initial timeliness of virus translation, for example, by supplementing and expanding the birther’s RNA and suppressing ribonucleoprotein synthesis. It has a wide range of in vitro movements against RNA infections. The significant convergence of the metabolites – 1,2,4-triazole-3-carboxamide – is higher when urinating after oral administration than after intravenous administration, which indicates that drug is lowered in digestive tract and the liver. Ribavirin aerosol is assimilated on an elementary basis, as indicated by proximity of fixation which can be measured in plasma. Clinical suitability has been demonstrated for treatment of contamination caused by dengue (with details oral and intravenous ribavirin) and hepatitis C (by mouth) ribavirin mixed with interferon. 25
Lamivudine is a pyrimidine nucleoside that was initially manufactured as an antiretroviral drug. It is simple cytidine that is converted intracellularly to lamivudine triphosphate which contains hepatitis B DNA polymerase as well as HIV reverse transcriptase. Lamivudine is a prescription nucleoside reverse transcriptase inhibitor (NRTI) that is used in combination with other drugs as antiviral treatment for human immunodeficiency virus type-1 (HIV-1) and as a monotherapy for hepatitis B virus (HBV). 26 The high oral bioavailability and generally long half-life (5–7 h) of lamivudine allow once every day dose up in patients with hepatitis B.
Amantadine and rimantadine
Amantadine hydrochloride is an amine having a special ring of 10 carbon atoms; Rimantadine hydrochloride is a pair prepared by combining an ethyl carbon linkage with ammunition and a C10 cycle. Both drugs appear to suppress influenza infection replication by blocking the particle channel of the M2 protein virus, which reduces the effect of this viral protein on virus release and pH guidelines in contaminated cells. Amantadine has a high oral bioavailability and a number of symptoms, especially in patients with 60 years of age or older, who have approximately several times higher plasma concentrations than young adults receiving one and a half doses – plasma life is approximately 12 h longer. Amantadine is eliminated by glomerular filtration and non-drug cylindrical release, so the altered pharmacokinetics in the elderly is likely to be due to decreased renal capacity. Rimantadine is also well consumed; 75% of the dose is processed in the liver, mainly by hydroxylation. Elderly people need a dose reduction, probably due to age-related decreases in liver capacity. These two drugs are active in the inhibition and treatment of influenza infection. 27
Interferon alpha
Normal interferon is a glycoprotein that has the proposed antiviral effect due to the registration of cellular chemicals that inhibit the incorporation of viral proteins. The commercial arrangement of interferon alpha is slightly smaller than that of ordinary proteins (subatomic mass, approximately 19,000) and is produced in microbes by recombinant DNA strategy. 11 Interferon is not available orally and should be administered by intramuscular or subcutaneous infusion. Insufficient information is available on the inhibition of viral replication in vitro, presumably because interferons inhibit their antiviral activity by suppressing and interpreting viral RNA and retaining cells. Interferon alpha has been shown to be effective in the treatment of diseases caused by human herpesvirus 8, papillomavirus (Kaposi’s sarcoma) virus, hepatitis B and C virus.
Antiviral drugs and COVID-19
The worldwide outbreak of COVID-19 virus infection is associated with the unavailability of specific drug(s) to combat with this viral infection. To date, nearly 10 million people are infected and about 500,000 people die worldwide due to COVID-19 viral infection. To find the solutions for this viral infection, great efforts have been made and are continued to develop vaccines, small molecule drugs or monoclonal antibodies that can prevent the infection spread to avoid the expected human, social and economic devastation related to this infection. Several FDA approved drugs have been reported in the literature and in hospitals during clinical trials to treat or reduce the COVID-19 severity.
Remdesivir (GS-5734)
Remdesivir is a novel antiviral drug originally used for treating Marburg virus and Ebola virus infections and this drug was developed by Gilead Sciences. The chemical formula of remdesivir is C27H35N6O8P with a molecular mass of 602.6 g/mol. This is a prodrug of a nucleotide analogue metabolised intracellularly to adenosine triphosphate analogue inhibiting the viral RNA polymerases ( Figure 2 ). It acts as an inhibitor of RNA dependant RNA polymerase and its characteristics and pharmacokinetics have been studied in MERS-CoV and SARS-CoV infections. This drug causes decline in the replication of viral genome and its production due to the alterations in the viral exonuclease function and disturbed proof reading. It can be recommended to prevent the disease progression severity in COVID-19 patients since it prevents the replication of the virus. To confirm its therapeutic potential against COVID-19, double blind randomised clinical trials with such patients are underway in phase 3. 28 In vitro studies have shown that in addition to its efficacy against COVID-19 in epithelial cells of the human airways, remdesivir has virologic as well as clinical efficacy in a non human primate model. 29

Possible mechanism of Remdisivir against SARS-CoV-2 at molecular level. (a) Diagram shows the entry of SARS-CoV-2 virus and the synthesis of its RNA that can be blocked by Remdisivir. (b) Molecular mechanism of viral RNA synthesis inhibition by Remdisivir. 30
Remdesivir has broadspectrum antiviral activity against several virus family members including the coronaviruses for example, Middle East respiratory syndrome coronavirus (MERSCoC) and SARSCoV, and filoviruses for example, Ebola and has shown therapeutic and prophylactic efficacy in these coronaviruses when used as non clinical models. Remdesivir when tested through in vitro studies using the Vero E6 cells showed an EC50 value of 1.76 µM that revealed its activity against SARS-CoV-2 suggesting its working concentration probably be achieved in nonhuman primate models. 31 Intravenous remdesivir treatment showed significant improvement for the first COVID-19 patient in US 32 and then a trial has been started to rapidly evaluate the safety and efficacy of remdesivir in nCoV-19 infected hospitalised patients. In a cohort of hospitalised patients with severe COVID-19 treated with remdesivir, improvements in the clinical finding were observed in 68% patients. 33 Without any placebo or active comparator in the study, it is difficult to draw any solid conclusion about the efficacy of remdesivir therapy. Currently in the United States, four clinical trials are enrolling the patients and two additional trials in China only have been registered on ClinicalTrials.gov , {"type":"clinical-trial","attrs":{"text":"NCT04252664","term_id":"NCT04252664"}} NCT04252664 (mild-moderate disease) and {"type":"clinical-trial","attrs":{"text":"NCT04257656","term_id":"NCT04257656"}} NCT04257656 (severe disease). 34
Nitazoxanide
Nitazoxanide and its active constituent, tizoxanide showed the potential against MERS CoV and SARS CoV-2 in an in vitro study using Vero E6 cells with EC50 of 0.92 and 2.12 µM, respectively. 31 It also showed broad spectrum activity against certain viruses including norovirus, rotavirus, parainfluenza, respiratory syncytial virus and influenza virus in addition to coronaviruses. This antiviral activity is due to the fact that action mechanism is based on interfering with the host regulated pathways of virus replication rather than the specific pathways of the virus. 35 The innate antiviral mechanisms are upregulated by nitazoxanide through the amplification of cytoplasmic RNA sensing and type 1 IFN pathways. Nitazoxanide upregulate the precise host mechanisms interfering with the viral infection and the viruses target to bypass the host cellular defences. 36 Studies have shown that nitazoxanide when used against influenza viruses block the maturation of viral hemagglutinin at post translational stage. 35 This drug is being evaluated in randomised controlled clinical trials for the management of some acute respiratory infections such as influenza, even though the results are yet unavailable or not encouraging. Although encouraging results are found through the in vitro activity of nitazoxanide against SARS-CoV-2 and more studies are required to clearly determine its role in managing the COVID-19. 37
Antagonistic impacts of antiviral drugs
Because infections involve intracellular pathogens that have cellular capacity, cynics once accepted that no specific inhibitor of viral reproduction could be found. This confidence was strengthened by the disappointments of the first antivirals like idoxuridine and cytarabine essential, and moderately late with fialuridine. Fortunately, drugs have been developed that affect viral replication to a greater extent than cells. All antiviral drugs, whether alone or not, can have effects and some are unexplained, such as thrombotic microangiopathy linked to valaciclovir in patients with immunodeficiency syndrome. 38
Virus inactivating agents
Some compound operators have been performed which use a fairly attractive antiviral movement by straight disabling infection. Calcium elenolate, a monoterpene gained from corrosive liquid concentrates hydrolysed from various pieces of the olive tree, uses a virucidal effect in vitro against a variety of RNA and DNA infections, clearly by communicating with the protein layer of the infecting molecule. 39 In a creature study, intranasal administration reduced yields of parainfluenza infection without significant adverse effects. Human preparations with this compound have only demonstrated viability if treatment is started immediately after infection. Certain dihydroisoquinolines have shown an inactivating effect on influenza A and B infections and parainfluenza infections; these infections had a strong antiviral effect in cell culture and were later found to have a moderate effect in animal tests. The mixtures have in any case been neglected in order to obtain the antiviral effect required in humans. 40
Restraint of viral attachment, entrance and uncoating
Because the infection first contaminated a eukaryotic cell, certain general stages of the disease process occur that can be spots of outbreak by potential antiviral drugs. At these stages, the contaminating virion binds to receptors on the cell film, enters the cell layer and once in the cell’s cytoplasm, the virion’s protein layer is emptied and the viral nucleus corrodes the substance.
Contact or viral adsorption was the least viable site to attack antiviral agents, without discovering substances that were still dynamic enough to warrant a clinical trial. The sulfated polysaccharide is thought to communicate with infectious particles, thereby reducing the rate of cell binding in vitro. 41 Affected infections include encephalomyocarditis, reverberation, flu, dengue fever and rabies. A moderate effect in vivo has also been observed against dengue infection in mice. Heparin, an unfavourably charged mucopolysaccharide, clearly forms a non-infectious complex with a herpes infection that prevents it from being secreted into the host cell. An action against herpes infection was observed both in vitro and in the analysis of creatures, in the latter case a heparin infusion was injected into the skin of the rabbit before or as a whole. Because of the ionic concept of communication, in all respects, heparin would have an impressive degree of non-specificity.
Inhibitors of enzymes associated with virions
Dna polymerases.
Countless substances accept antiviral movement due to the inhibition of DNA polymerases associated with virions. Antivirals of this type can be widely collected in pyrophosphate analogues and analogues of conventional nucleoside polyphosphates. This latter collection is regularly distinguished in the sweet portion of the particle or in the particles of purine or pyrimidine, although hardly in both. There are two interesting mixtures in main classification: trisodium phosphonooformate (PF An) and trisodium phosphonoacetate (PA). PFA removes half of DNA polymerase type I from herpes simplex infection at 3.5 p.M. The effect of eukaryotic DNA polymerase on α can reduce protein expansion. For cell expansion (HeLa cells), a more notable requirement of 100 µM PFA in the medium was to achieve half inhibition. PFA is generally dynamic in vitro against DNA-containing herpes simplex 1 and 2 infections and infection in simulated animals. Like PF A, P may give the impression that a potent inhibitor of herpes simplex infection depends on DNA polymerase, but has no effect on the polymerase of the host cell (WI-38). Exceptionally, point-to-point reactions to the polymerisation and trade of nucleoside triphosphate pyrophosphates using DNA polymerase activated by infection with turkey herpes. 42 PA appeared to communicate with DNA polymerase at the level of the site limiting polyphosphates. 43 Overby et al. 43 have shown that resistance to PA infection is rightly linked to a similar relative obstruction of the comparison without cellular DNA polymerase.
RNA polymerases
Various substances are recognised to prevent DNA and RNA-mediated RNA polymerase in vitro, and this activity is repeatedly believed to be responsible for antiviral activity. For example, in a careful report, Ericsson et al. reported that a very important class of malaria, ribavirin triphosphate (RTP), is a potent antioxidant that promotes RNA polymerase. The polarisation of viral polymers is strong for ATP and GTP, but not for UTP or CTP. RNA interference polymers have been identified as more complex than guanine-containing dinucleotides, and Plotch and Krug have shown that ApG or GpC is inserted at the 5′ end of the AcG gene. Ericsson et al. discovered that RTP abolished ApG and GpC-mediated enhancement of the virtual polymerase. It is not well understood that this approach may reflect the unique effects of influenza ribavirin infection. Ericsson et al. stated that a more important goal is that RTP blockade of viral RNA polymerase inhibitors extends from the formation of cellular polymers to non-functional eukaryotic RNAs. Jamieson et al. showed that RTP does not inhibit eukaryotic RNA polymerases I and II and does not affect eukaryotic polymerases (A) Deoxypyrimidine nucleoside kinase and thymidine kinase. Deoxypyrimidine kinase initiates the virus. There are two ways to do this, of course: the first is immediate competition with conventional substrates, and the second is catalytic restriction by allosteric modulators. 44 Kit et al., pointed out that pseudorabies and viral growth are phosphorylated, while stimulating a kinase ready to phosphorylate another thymidine, deoxycytidine, which phosphorylates thymidine. It has been described in detail and compared with human and mouse mitochondrial chemistry in some embodiments, especially phosphorylated extractions, although dCTP does not control thymidine virus infection. 45 All thymidine kinases are critically involved in dTTP. Cheng et al. 46 showed that thymidine analogues have antiviral activity, whereas herpes simplex virus can activate thymidine kinase and Declercq and Torrence 47 (10S) showed some of the thyroid analogues, which is especially true for herpesviruses. Cheng et al found in a cautious report that many 5-subdeoxyuridine-rich companies are herpes simplex 1 and 2-thymidine kinase have been shown to be a strong driving force. 5-IdC and 5-BrdC are more and more active, attractive inhibitors of thymidine kinase. Herpes simplex class 1 fights only thymidine kinase. The above combinations are herpes simplex type 1 or herpes simplex type 2. It is an active ingredient in the regeneration of but not a specific type of herpes simplex virus that has rapidly acquired the ability to stimulate thymidine kinase. 48
Viral neuraminidase
There are different views on the work of virion-associated neuraminidases, but whether they are infiltrated or agglomerated, the severity of influenza side effects increases among volunteers and increases the immune response to neuraminidase against plasma. Concentration is declining. 2-Deoxy-2,3-dehydro-N-trifluorocetylneuramine caustic is an inhibitor of influenza infection. This involves the enzymatic removal of neuramine caustic from the infected envelope, as well as the widespread collection of infectious particles and, ultimately, the inhibition of viral replication. mRNA guanylyl transferase and mRNA methyl transferase mRNAs consist of 7 methylguanose structures associated with 2′× triphosphate hybrids from 5′ locations of various viruses and eukaryotes. The structure contains ‘O’ methylribonucleoside and a suitable chemical containing the ‘upper’ structure, which was found in the Vaccine and Reovirus Centres. Subsequent tests in this area showed that infections containing various RNAs and DNAs had a ‘superior’ structure, while poliomyelitis was not an infection and ribavirin was not dynamic against polio infection. Therefore, the effect on the polishing procedure was studied. 49 Show that RTP is a potent and severe inhibitor of vaccine-infected mRNA guanyltransferase (Kj = 32 p.M and GTP Km = 22 p.M). Furthermore, in the absence of GTP, 1 mm RTP inhibits vaccine mRNA methylation, but synepungin increases success even if it is an antifungal operator. The peptides in influenza viruses do not bind rapidly to the ribavirin field, but that peptide synthesis in host kidney cells is not regulated. This recognition may be due to the formation of a viral RNA mixture or a ‘top’. The replication of influenza infection in reticulocytes is approximately 15 terminal nucleotides generated from globin mRNA, as well as 5′ ‘top‘ effects requires additional synchronisation of host cell mRNA.
Inhibitors of the translational processes of viral mRNA
Mrna translation.
This suggests that the interpretation of various mRNAs in the wheat germ range is restricted to 7-methylguanosine-5′-monophosphate (m7-GMP). However, guanosine nucleotides are released rapidly upon entering the 7-methyl collection or other methyl collections. Not enough, surprisingly, m7-GMP suppresses RNA interpretation of satellite tobacco spoilage infections in the wheat germ range. This could be part of another recognition section of the ‘upper’ restriction site. Additional studies using reovirus mRNA in wheat germ have shown by Adams et al. 50 Regarding the mRNA interpretation of vesicular stomatitis infection in reticulocytes. 51 In a subsequent report, Bergman and Rodish determined the amount of mRNA infection in vesicular stomatitis infection by binding K + low wheat embryo ribosomes. 52 They added that the interpretation of mRNA in the reticulocyte range was less important 5′ ‘up’ under any response condition.
Early viral polypeptide chains
Parafluorophenylalanine (pFPhe) was first used in 1951 in a simple, non-corrosive manner and along these lines has been shown to have broad spectrum antiviral activity against RNA and DNA infections. The way it works is to replace the protein phenylalanine, which does not stimulate antiviral peptides well. Continuously, an entirely new method destroys cells that are contaminated with Calascovirus, so methylene GTP inhibits encephalomyocarditis protein synthesis and enters these cells (not yet normal). Contreras et al. further showed that other explanatory inhibitors were some toxic cells rather than simple cells. 53
Inhibitors of the synthesis of viral DNA
Many exacerbations that inhibit the binding of viral DNA occur either by direct blocking of the polymerase (and were hidden by previous regions), while, on the other hand, due to the impedance in the previous binding or binding. Square DNA replication or in collaboration with the layout, which ultimately makes defective material work.
Fused to DNA
The fusion of 5-ldU with viral DNA instead of thymine and its subsequent delicacy and distortion of this DNA were investigated, and an extensive variety of halogenated deoxypyrimidine nucleosides was rather widely illuminated. The fusion of these substances can lead to non-functional DNA along these lines that destroy the nose of genetic data. In addition, there are other DNA-related deoxythymine analogues that have been specifically tested by De Clerk and Torrens. It is interesting to note that 5-AlddU is associated with herpes simplex DNA, and the authors draw attention to the pronounced corrosion instability of P-N bonds along these lines. However, the organic effects of this binding can be quite intimidating, since DNA usually does not cause corrosion. Ara-AMP binds to herpes simplex infected DNA, as well as the DNA of L5178 Y cells and mouse fibroblasts.
Inhibitors of non-viral enzymatic processes involved in DNA synthesis
Among the procedures that can change the proportion or volume of DNA mixtures, antiviral specialists mainly influence the estimates of thymidylate synthetase and deoxynucleoside triphosphate pools either directly or bypassing. Countless deoxyuridine subsidiaries show incredible barriers to synthetic TMP. In the model, 5-iodoacetamido-methyldeoxyuridine and 5-ethyldeoxyuridine, as well as 5-fluorodeoxyuridine and 5-trifluoromethyldeoxyuridine 5′-monophosphate. Linking to the Intercalation pattern ensures successful DNA replication due to the presence of various substances that interact with DNA. Although a significant number of these substances have been demonstrated to be dynamic antiviral experts, these effects also affect cell DNA replication. Muller recently investigated these substances for their antiviral effects. In addition, Kersten and Kersten recently completed an amazing study of these experts. In addition, daunomycin interacts only with adriamycin, which is essentially the same as in real life with DNA infections, especially with the herpes simplex virus and vaccinia, as well as with carcinogenic RNA infections that mimic the middle of the DNA pathway. Both of these agents are considered implant specialists and are generally toxic, since both of them inhibit nuclear-corrosion combinations, including DNA mockups.
Inhibitors of the biosynthesis and assembly of viral glycoprotein
Both DNA and RNA infections include membranes with glycopeptides integrated into the infection, recommended by another possible direction of antiviral drugs. Influenza infections include hemagglutinin spikes. This is an important part of the envelope glycoprotein of the infection and is suitable for connecting infectious molecules with their cellular receptors. Another important part of the influenza infection film is chemical neuraminidase (N-acetylneuraminic acid glycohydrolase), which is outside the infection and appears to be associated with the lipid membrane of the infection like hemagglutinin. The effects of the mixture on neuraminidase have been investigated in previous areas.
The fight between human and viruses in on and both are rapidly improving the strategies of attacking and defence. In recent years, there has been tremendous progress in understanding the genetic basis and molecular mechanism of diseases. Various new drugs have been formulated and the development of a lot more is in underway. Though, the new infectious diseases caused by viruses such as COVID-19 remain a challenge. Furthermore, the drugs failure in human trials is a general process that requires to be worked out and addressed. The promising results are expected through the emergence of many new technologies. A greater help in the development of new drugs with antiviral activities is provided by the growing knowledge about viruses and the rapidly developing techniques and tools. The better understanding about viruses will make it possible to establish useful measures for fighting against the viral diseases and the researchers around the globe are putting their possible efforts to control the spread of viral diseases and we hope that we live in the world free from viral diseases.
Acknowledgments
We acknowledge Dr Abid Rashid for guiding us in writing this article.
Declaration of conflicting interests: The author(s) declared no potential conflicts of interest with respect to the research, authorship, and/or publication of this article.
Funding: The author(s) received no financial support for the research, authorship, and/or publication of this article.


An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
#protect2024 Secure Our World Shields Up Report A Cyber Issue
Understanding Anti-Virus Software
What does anti-virus software do.
Although details may vary between packages, anti-virus software scans files or your computer’s memory for certain patterns that may indicate the presence of malicious software (i.e., malware). Anti-virus software (sometimes more broadly referred to as anti-malware software) looks for patterns based on the signatures or definitions of known malware. Anti-virus vendors find new and updated malware daily, so it is important that you have the latest updates installed on your computer.
Once you have installed an anti-virus package, you should scan your entire computer periodically.
- Automatic scans – Most anti-virus software can be configured to automatically scan specific files or directories in real time and prompt you at set intervals to perform complete scans.
- Saving and scanning email attachments or web downloads rather than opening them directly from the source.
- Scanning media, including CDs and DVDs, for malware before opening files.
How will the software respond when it finds malware?
Sometimes the software will produce a dialog box alerting you that it has found malware and ask whether you want it to “clean” the file (to remove the malware). In other cases, the software may attempt to remove the malware without asking you first. When you select an anti-virus package, familiarize yourself with its features so you know what to expect.
Which software should you use?
There are many vendors who produce anti-virus software, and deciding which one to choose can be confusing. Anti-virus software typically performs the same types of functions, so your decision may be driven by recommendations, particular features, availability, or price. Regardless of which package you choose, installing any anti-virus software will increase your level of protection.
How do you get the current malware information?
This process may differ depending on what product you choose, so find out what your anti-virus software requires. Many anti-virus packages include an option to automatically receive updated malware definitions. Because new information is added frequently, it is a good idea to take advantage of this option. Resist believing alarmist emails claiming that the “worst virus in history” or the “most dangerous malware ever” has been detected and will destroy your computer’s hard drive. These emails are usually hoaxes. You can confirm malware information through your anti-virus vendor or through resources offered by other anti-virus vendors.
While installing anti-virus software is one of the easiest and most effective ways to protect your computer, it has its limitations. Because it relies on signatures, anti-virus software can only detect malware that has known characteristics. It is important to keep these signatures up-to-date. You will still be susceptible to malware that circulates before the anti-virus vendors add their signatures, so continue to take other safety precautions as well.
Related Articles
Lessons from xz utils: achieving a more sustainable open source ecosystem, cyber resilient 911 symposium blog post, cisa joins the minimum viable secure product working group, jcdc working and collaborating to build cyber defense for civil society and high-risk communities.
- Choose your language...
- English (English)
- Spanish (Español)
- French (Français)
- German (Deutsch)
- Italian (Italiano)
- Portuguese (Português)
- Japanese (日本語)
- Chinese (中文)
- Korean (한국어)
- Taiwan (繁體中文)
- Organization Size
- Hybrid Cloud
- Zero Trust & Least Privilege
- Developer Security & Operations
- IoT Security Solutions
- Anti-Ransomware

See how use cases come to life through Check Point's customer stories.
- Financial Services
- Federal Government
- State & Local Government
- Telco Service Provider
- Small & Medium Business
- Infinity Platform
- Secure the Network
- Secure the Cloud
- Secure the Workspace
- Core Services
- Platform Overview Industry leading AI-Powered and Cloud-Delivered cyber security platform
- Infinity Core Services Prevention first security operations, AI Copilot, ThreatCloud AI, and 24/7 managed security services, consulting and training
- Infinity Portal Learn about and sign into Check Point's unified security management platform
- Infinity Platform Agreement Predictable cyber-security environments through a platform agreement
- See All Products >

Introducing Quantum Force
- Next Generation Firewall (NGFW) Security Gateway Industry-leading AI powered security gateways for modern enterprises
- SD-WAN Software Defined Wide Area networks converging security with networking
- Security Policy and Threat Management Manage firewall and security policy on a unified platform for on-premises and cloud networks
- Operational Technology and Internet of Things (IoT) Autonomous IoT/OT threat prevention with zero-trust profiling, virtual patching and segmentation
- Remote Access VPN Secure, seamless remote access to corporate networks
- Cloud Network Security Industry-leading threat prevention through cloud-native firewalls
- Cloud Native Application Protection Platform Cloud native prevention first security
- Code Security Developer centric code security
- Web Application and API Security Automated application and API security
- Email and Collaboration Security Email security including office & collaboration apps
- Endpoint Security Comprehensive endpoint protection to prevent attacks & data compromise
- Mobile Security Complete protection for the mobile workforce across all mobile devices
- SASE Unifying security with optimized internet and network connectivity
- SaaS Security Threat prevention management for SaaS
- Managed Prevention & Response Service SOC operations as a service with Infinty MDR/MPR
- Extended Prevention & Response AI-Powered, Cloud-Delivered Security Operations with Infinity XDR/XPR
- Secure Automation and Collaboration Automate response playbooks with Infinity Playblocks
- Unified Security Events and Logs as a Service Infinity Events cloud-based analysis, monitoring and reporting
- AI Powered Teammate Automated Security Admin & Incident Response with AI Copilot
- ThreatCloud AI The Brain behind Check Point’s threat prevention
- Cyber Risk Assessment Assess your cyber risks and plan actionable strategy
- Attack Surface & Penetration Testing Evaluate security defenses against potential cyber attacks and threats
- Security Controls Gap Analysis (NIST, CIS) Analyze technology gaps and plan solutions for improved security and ROI
- Threat Intelligence & Brand Reputation Analyzed data on cyber threats, aiding proactive security measures
- See All Assess Services >


Learn hackers inside secrets and beat them at their own game
- Security Deployment & Optimization Strategic deployment and refinement of security for optimal protection
- Advanced Technical Account Management Proactive service delivered by highly skilled Cyber Security professionals
- Lifecycle Management Services Effectively maintain the lifecycle of security products and services
- See All Transform Services >
- Certifications & Accreditations Comprehensive cyber security training and certification programs
- CISO Training Globally recognized training for Chief Information Security Officers
- Security Awareness Empower employees with cyber security skills for work and home
- Cyber Park - Cyber Range Simulated gamification environment for security training
- Mind Training Hub Check Point Cyber Security and Awareness Programs training hub
- See All Master Services >
- Incident Response Manage and mitigate security incidents with systematic response services
- Managed Detection and Response 24/7 SOC Operations for Check Point + 3rd party solutions, 24/7 response
- Digital Forensics Comprehensive investigation and analysis of cyber incidents and attacks
- See All Respond Services >
- SOC-as-a-Service Leverage SOC expertise to monitor and manage the security solutions
- NOC-as-a-Service and Network Security Management of IT network and firewall infrastructure
- Cloud & IT Access to managed Cloud and IT technologies, expertise, and resources
- See All Managed Services >
- Support Programs Programs designed to help maximize security technology utilization
- Check Point PRO Proactive monitoring of infrastructure program offerings
- Contact Support
- Platform Overview
- Infinity Core Services
- Infinity Portal
- Infinity Platform Agreement
- Next Generation Firewall (NGFW) Security Gateway
- Security Policy and Threat Management
- Operational Technology and Internet of Things (IoT)
- Remote Access VPN
- Cloud Network Security
- Cloud Native Application Protection Platform
- Code Security
- Web Application and API Security
- Email and Collaboration Security
- Endpoint Security
- Mobile Security
- SaaS Security
- Managed Prevention & Response Service
- Extended Prevention & Response
- Secure Automation and Collaboration
- Unified Security Events and Logs as a Service
- AI Powered Teammate
- ThreatCloud AI
- Cyber Risk Assessment
- Attack Surface & Penetration Testing
- Security Controls Gap Analysis (NIST, CIS)
- Threat Intelligence & Brand Reputation
- Security Deployment & Optimization
- Advanced Technical Account Management
- Lifecycle Management Services
- Certifications & Accreditations
- CISO Training
- Security Awareness
- Cyber Park - Cyber Range
- Mind Training Hub
- Incident Response
- Managed Detection and Response
- Digital Forensics
- SOC-as-a-Service
- NOC-as-a-Service and Network Security
- Cloud & IT
- Support Programs
- Check Point PRO
- Find a Partner
- Channel Partners
- Technology Partners
- MSSP Partners
- Azure Cloud
- Partner Portal

Check Point is 100% Channel. Grow Your Business with Us!
- Investor Relations
- Resource Center
- Customer Stories
- Events & Webinars
- Check Point Research
- Cyber Talk for Executives
- CheckMates Community

EDR vs Antivirus
Endpoint security is a vital component of an enterprise cybersecurity strategy. Antivirus (AV) and endpoint detection and response (EDR) solutions are both designed to protect against threats to endpoint security but provide very different levels of protection. Learn how these solutions differ and which is the right choice for your organization.
Request A Demo IDC MarketScape Report
What Is EDR?
EDR provide multilayered, integrated endpoint protection. Key features of an EDR security solution include:
- Alert Triage: Security analysts are often overwhelmed by large volumes of alerts from various cybersecurity solutions. EDR triages potential malicious events, enabling security analysts to focus their efforts where they are most effective.
- Threat Hunting Support: Threat hunting enables an organization to identify and respond to threats that were not detected or blocked by enterprise security solutions. EDR solutions should provide integrated support for threat hunting activities.
- Data Aggregation and Enrichment: Contextual information is vital to differentiating between true cyberattacks and false positives. EDR solutions aggregate data from multiple sources and use this data to more accurately identify true threats.
- Integrated Incident Response: EDR should offer support for incident response within the same console. By eliminating context switching, this supports more rapid incident response.
- Multiple Response Options: Different security incidents require different types and levels of response. An EDR security solution should provide multiple options (quarantine, eradication, etc.) for an analyst to address the issue.
These EDR features provide significant security benefits , including:
- Improved Security Visibility: EDR centralize data collection and analytics. This provides an organization with more in-depth visibility into the current security posture of its endpoints.
- Streamlined Incident Response: By using automated data collection, aggregation, and some response activitie, the process of gaining vital security context enables rapid response.
- Automated Remediation: EDR allows an organization to define automated procedures for incident response activities. This reduces the impact and cost of the incident to the organization.
Contextualized Threat Hunting: EDR solutions provide threat hunters with access to the data and context required for threat hunting. This enables more rapid and effective threat hunting and the detection of potential indications of a previously unknown incident.
What Is Antivirus?
Antivirus solutions are designed to identify malicious software or code that has infected a computer. AVs use various methods to identify potential malware infections, including:
- Signature-Based Detection: Signature-based detection identifies known threats based on signatures such as file hashes, command and control domains, IP addresses, and similar features.
- Heuristic Detection: Heuristic or anomaly detection identifies malware based on unusual or malicious functionality. This enables it to identify zero-day threats that signature-based detection would miss.
- Rootkit Detection: Rootkit detection identifies malware designed to acquire deep, administrative access to an infected computer.
- Real-Time Detection: Real-time detection attempts to identify malware at time of use by scanning and monitoring recently-accessed files.
AV solutions enable the detection and remediation of malware infections on a computer. This can include terminating malicious processes, quarantining suspicious files, and eradicating malware infections.
EDR vs Antivirus - What’s The Difference?
AV provides the ability to detect and respond to malware on an infected computer using a variety of different techniques. EDR incorporates AV and other endpoint security functionality providing more fully-featured protection against a wide range of potential threats.
Why AV Is Not Enough
AV is designed to identify malware on a computer, but cyber threat actors are growing increasingly sophisticated. Traditional, signature-based detection is no longer effective at identifying modern malware due to the rapid evolution of malware and the use of unique malware and infrastructure for cyberattack campaigns. Additionally, malware developers are using various techniques such as fileless malware to evade detection by antivirus solutions.
Detection of modern threats to endpoint security requires more information and context than is available to AV systems. EDR integrates a range of security functions, enabling it to detect trends and other indicators of a successful incursion. Additionally, the response capabilities provided by EDR enable security analysts to more quickly act to address potential security incidents, limiting the impact of an attack.
Harmony Endpoint Offering
Endpoint security threats are rapidly evolving. Check Point Harmony Endpoint provides comprehensive protection against a range of endpoint security threats. Harmony Endpoint has been listed as a Major Player in the Worldwide Modern Endpoint Security for Enterprises and for the SMB Vendor assessment by the IDC MarketScape and received the top score from AV TEST in its Corporate Endpoint Protection testing.
Evolving patterns of work make endpoint security an organization’s first line of defense against cyber threat actors. Learn how to protect your organization against endpoint security threats by signing up for a free demo of Check Point Harmony Endpoint.
Recommended Resources
Get started.
Harmony Endpoint
Endpoint security
Harmony Endpoint Solution Brief
Anti-Virus Software Blade
SMB IDC MarketScape
Related Topics
What is Endpoint Protection?
EDR Security
Advanced Threat Protection (ATP)
Endpoint Platform Protection (EPP)

The 5 Best Free Antivirus Software Programs of 2024
There’s basically no excuse for not having top-notch antivirus software on your personal computers these days.
You have multiple well-rated — and no-cost — options to choose from, as PCMag’s latest ratings of free antivirus programs illustrate.
To reach its findings, the publication tested 38 antivirus products and examined the results of other independent labs that have tested the programs.
Don't Miss: If you're under age 60, you can get $3 million in life insurance without needing a medical exam and you can cancel at any time. Instant Decision. No Policy Fees. Apply Today .
The best free antivirus software
PCMag awarded its “Editors’ Choice” honor for 2024 to Avast One Essential . It earned an “outstanding” overall rating of 4.5 out of 5 from PCMag.
In writing about the rankings, Neil J. Rubenking, PCMag’s lead analyst for security, says:
“Avast has been supplying antivirus protection for as long as there’s been an antivirus industry … All four of the independent testing labs we follow include Avast in their reporting, and it aces almost every test. It also takes high scores in our own hands-on testing.”
However, PCMag published its 2024 ranking of free antivirus software before the U.S. Federal Trade Commission fined Avast $16.5 million for selling users’ data. So you might want to consider one of the runners-up instead.
AVG Antivirus Free and Bitdefender Antivirus Free for Windows tied for the second-place spot, with each scoring an “excellent” 4 out of 5. AVG was named “best for useful bonuses,” and Bitdefender is “best for no-frills protection.”
Rounding out the top five are Avira Free Security and Microsoft Defender Antivirus , each earning a “good” rating of 3.5 out of 5.
Related: Are There Jobs That Let You Set Your Own Hours?
Kaspersky Free, which once ranked highly, is conspicuously absent from the list. PCMag notes that Kaspersky’s Russian origins and the war in Ukraine have caused many governments and organizations to censure and cut ties with the business. The Federal Communications Commission has gone so far as to say Kaspersky is a national security threat, and as a result, PCMag no longer recommends their products.
Should you pay for antivirus protection?
PCMag says that paid antivirus programs offer more protection and better protection than free versions. What’s more, tech support may be limited for free program users.
Whether you should pay for antivirus protection comes down to your budget. If a paid program isn’t in your budget, perhaps try a few of the free programs to see which you like best.
One exception is for business computers. PCMag notes that free antivirus programs are often free only for noncommercial use, meaning only for use on personal computers.
Try a newsletter custom-made for you!
We’ve been in the business of offering money news and advice to millions of Americans for 32 years. Every day, in the Money Talks Newsletter we provide tips and advice to save more, invest like a pro and lead a richer, fuller life.
And it doesn’t cost a dime.
Our readers report saving an average of $941 with our simple, direct advice, as well as finding new ways to stay healthy and enjoy life.
Click here to sign up. It only takes two seconds. And if you don’t like it, it only takes two seconds to unsubscribe. Don’t worry about spam: We never share your email address.
Try it. You’ll be glad you did!
This article may contain affiliate links that Microsoft and/or the publisher may receive a commission from if you buy a product or service through those links.


An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.

Animal and Plant Health Inspection Service
Highly Pathogenic Avian Influenza (HPAI) Detections in Livestock

The U.S. Department of Agriculture, Food and Drug Administration, Centers for Disease Control and Prevention, and State veterinary and public health officials are investigating an illness among dairy cows.
As we learn more about this evolving situation, APHIS will continue to provide confirmatory testing for samples from livestock as well as guidance for producers, veterinarians, and state animal health officials. As the situation changes, we will continue to post updated information at the links below.
Detection of Highly Pathogenic Avian Influenza in Dairy Herds: Frequently Asked Questions Detection of Highly Pathogenic Avian Influenza in Dairy Herds: Frequently Asked Questions (Spanish) APHIS Recommendations for HPAI H5N1 Virus in Livestock (214.38 KB)
Confirmed Cases of HPAI in Domestic Livestock
*Data updated weekdays by 4 pm ET.

Latest News
Information for producers and veterinarians.
(PDF, 214.38 KB)
For State Animal Health Officials, Accredited Veterinarians, and Producers
(PDF, 317.46 KB)
APHIS’ current recommendations for testing affected or exposed cattle.
Biosecurity Resources
USDA’s Defend the Flock program offers free tools and resources to help everyone who works with or handles poultry follow proper biosecurity practices.
(PDF, 286.4 KB)
Download the Influenza and Biosecurity: Not Just for the Birds factsheet.
(PDF, 462.94 KB)
Information on loans which can assist livestock producers with implementation of biosecurity measures on their operations.
Centers for Disease Control and Prevention Resources
Food and drug administration resources.
Questions and answers regarding milk safety during highly pathogenic avian influenza (HPAI) outbreaks.
- Ultimate Combo

- Sign Out Sign Out Sign In
238 Best Virus-Themed Templates for PowerPoint & Google Slides
With over 6 million presentation templates available for you to choose from, crystalgraphics is the award-winning provider of the world’s largest collection of templates for powerpoint and google slides. so, take your time and look around. you’ll like what you see whether you want 1 great template or an ongoing subscription, we've got affordable purchasing options and 24/7 download access to fit your needs. thanks to our unbeatable combination of quality, selection and unique customization options, crystalgraphics is the company you can count on for your presentation enhancement needs. just ask any of our thousands of satisfied customers from virtually every leading company around the world. they love our products. we think you will, too" id="category_description">crystalgraphics creates templates designed to make even average presentations look incredible. below you’ll see thumbnail sized previews of the title slides of a few of our 238 best virus templates for powerpoint and google slides. the text you’ll see in in those slides is just example text. the virus-related image or video you’ll see in the background of each title slide is designed to help you set the stage for your virus-related topics and it is included with that template. in addition to the title slides, each of our templates comes with 17 additional slide layouts that you can use to create an unlimited number of presentation slides with your own added text and images. and every template is available in both widescreen and standard formats. with over 6 million presentation templates available for you to choose from, crystalgraphics is the award-winning provider of the world’s largest collection of templates for powerpoint and google slides. so, take your time and look around. you’ll like what you see whether you want 1 great template or an ongoing subscription, we've got affordable purchasing options and 24/7 download access to fit your needs. thanks to our unbeatable combination of quality, selection and unique customization options, crystalgraphics is the company you can count on for your presentation enhancement needs. just ask any of our thousands of satisfied customers from virtually every leading company around the world. they love our products. we think you will, too.
Widescreen (16:9) Presentation Templates. Change size...

Medical symbol and virus over pink background

Close up of viruses on brown and gray background

Medical theme depicting isolated viruses with words virus on a purple background

White human with syringe injecting vacine, orange viruses, blue cell germ background

Red blood cells infected with blue viruses

Detailed 3D viruses spread on a blue background with wavy insertion

A skeleton and a virus in the picture

Close-up 3D HIV virus

Viruses in blood

A single green colored avian virus cell with nodes

Medical theme depicting humanoid having flu virus with green color

Tested sample of cells infected by HIV virus on black surface

Slide set consisting of rear view of hacker using laptop and credit card against virus background

Pink color shaped viruses with tint of green

Presentation having flu virus protection mask protective against influenza sickness viruses and disease sick sian woman wearing surgical face mask in public spaces healthcare banner panorama concept backdrop

Internet Virus

Transparent World map in white margins on dark red virus sign on red background

Presentation theme having woman wearing a real anti-pollution anti-smog and viruses face mask dense smog in air

Man with swine flu virus H1N1

Blue and green hive virus cells with black background, medicine

3D blue viruses on dark colored background with viruses shading in the background

Address bar with virus alert, virus depiction and virus word with cursor hovering over virus warning, https, red networking internet background

Human with New h1n1 influenza virus over white background

PPT theme with coronavirus corona virus prevention travel surgical masks and hand sanitizer gel for hand hygiene spread protection

Presentation featuring cybercrime hacking and technology concept - male hacker in dark room writing code or using computer virus program for cyber attack

PPT theme enhanced with medicine people and healthcare concept - female doctor or nurse wearing face protective medical mask for protection from virus disease with computer and clipboard calling on phone at hospital

Slide deck having medicine healthcare and pandemic concept - sad young female doctor or nurse wearing face protective mask for protection from virus disease sitting on floor at hospital

Antivirus artery bacteria biology blood cell in blue

Theme consisting of virus

Presentation theme featuring wanted hackers coding virus ransomware using laptops and computers cyber attack system breaking and malware concept

PPT theme consisting of corona virus prevetion face mask protection n95 masks and medical surgical masks at home

Slide deck with burglar wearing black hooded jacket against virus background

PPT layouts having virus

Slide deck having internet security concept open red padlock virus or unsecured with threat of hacking

PPT theme featuring coronavirus hand sanitizer gel to wash hands for flu virus prevention alcohol based antimicrobial disinfectant product for airport hospital healthcare and home panoramic banner background

3D anti-virus word with mouse connected to v letter and binary codes on network blue background

Presentation theme enhanced with doctor giving a senior woman a vaccination virus protection covid-2019 background

PPT layouts with doctor making a vaccination to a child

Red screen with a bio hazard sign on it

Presentation theme featuring picture showing woman sneezing on tissue on couch in the living-room
More virus templates for powerpoint and google slides:.
Company Info
Got any suggestions?
We want to hear from you! Send us a message and help improve Slidesgo
Top searches
Trending searches

68 templates

33 templates

36 templates

34 templates

9 templates
35 templates
Computer Virus Minitheme
Computer virus minitheme presentation, free google slides theme, powerpoint template, and canva presentation template.
Oh no! A virus has entered this template! Check your data protection settings and change all your passwords… and check out this modern computer virus minitheme, illustrated with viruses and bugs! Perfect for any cyber security-related presentation, all its slides are fully customizable to make your content shine and their color combination is professional yet edgy. Download the template for Google Slides or PowerPoint, edit them and get ready to present your IT content like never before!
Features of this template
- 100% editable and easy to modify
- 20 different slides to impress your audience
- Contains easy-to-edit graphics such as graphs, maps, tables, timelines and mockups
- Includes 500+ icons and Flaticon’s extension for customizing your slides
- Designed to be used in Google Slides and Microsoft PowerPoint
- 16:9 widescreen format suitable for all types of screens
- Includes information about fonts, colors, and credits of the resources used
How can I use the template?
Am I free to use the templates?
How to attribute?
Attribution required If you are a free user, you must attribute Slidesgo by keeping the slide where the credits appear. How to attribute?
Related posts on our blog.

How to Add, Duplicate, Move, Delete or Hide Slides in Google Slides
How to Change Layouts in PowerPoint
How to Change the Slide Size in Google Slides
Related presentations.

Premium template
Unlock this template and gain unlimited access
Register for free and start editing online

IMAGES
VIDEO
COMMENTS
ANTIVIRUS AND VIRUS Powerpoint presentation. This document provides an overview of computer viruses and anti-virus software. It defines what viruses are and how they spread, describes common types of viruses. It then explains what anti-virus software is, how it works to detect and remove viruses, and lists some popular anti-virus programs.
This is when your antivirus presentation comes into action! Help others choose to protect their computers by informing them on the risks of cyberattacks and viruses they can suffer without the right protection. Capture everyone's attention with these cute flat illustrations of users, computers and potential viruses. Download this template now ...
Virus Presentation templates Medical science is moving ahead at an immense speed! Share the most recent scientific researches, medical advances, and treatments of viruses that have marked the history of humanity, such as the Spanish flu or COVID-19. Gather all the necessary information in one of the presentations designed for Google Slides and ...
Concept 17.3: Viruses, viroids, and prions are formidable pathogens in animals and plants. Diseases caused by viral infections affect humans, agricultural crops, and livestock worldwide. Smaller, less complex entities called viroids and prions also cause disease in plants and animals, respectively.
8. Introduction to Viruses. Viruses are typically described as obligate intracellular parasites, acellular infectious agents that require the presence of a host cell in order to multiply. Viruses that have been found to infect all types of cells - humans, animals, plants, bacteria, yeast, archaea, protozoa…some scientists even claim they ...
A computer virus is a form of malicious software that piggybacks onto legitimate application code in order to spread and reproduce itself. Like other types of malware, a virus is deployed by ...
Definition, types, and benefits. Antivirus software monitors your devices for known threats and eliminates or stops them from infecting your devices as quickly as possible. With reliable security software like Norton AntiVirus Plus, your personal data will be better protected from hackers, malware, viruses, and other online threats.
Herpes Simplex Virus 1 (HSV-1) Herpes Simplex Virus 2 (HSV-2) Eradicated in 1979 due to worldwide vaccination campaigns. Ebola. Transmission: contact with contaminated blood or bodily fluids. Symptoms: fatigue, fever, severe headache, vomiting, diarrhea, rash, bleeding. May appear 2-21 days after exposure. . Ebola.
In such viruses, glycoproteins encoded by the virus are embedded in the lipid envelope. The function of the capsid or envelope is to protect the viral genome while it is extracellular and to promote the entry of the genome into a new, susceptible cell. The structure of viruses is covered in detail in Chapter 2.
Free Google Slides theme and PowerPoint template. Viruses are a threat to our health and, because of that, we need as much information about them as possible. Use this template to share a clinical case on a viral disease and make it appealing to doctors, students and people in general. It contains cool illustrations from Stories by Freepik and ...
Although many organizations have deployed antivirus software, new viruses, worms, and other forms of malware (malicious software) continue to rapidly infect large numbers of computer systems. There is no single reason for this apparent contradiction, but fundamental trends are apparent from feedback Microsoft has
A computer virus is a type of malware that attaches to another program (like a document), which can replicate and spread after a person first runs it on their system. For instance, you could receive an email with a malicious attachment, open the file unknowingly, and then the computer virus runs on your computer.
Virus and Antivirus - Free download as Powerpoint Presentation (.ppt), PDF File (.pdf), Text File (.txt) or view presentation slides online. Computer viruses can spread through file sharing and email attachments, infecting systems and causing damage like deleting files or crashing the computer. There are different types of viruses like boot viruses, macro viruses, and worms.
Antiviral drugs are a class of medicines particularly used for the treatment of viral infections. Drugs that combat viral infections are called antiviral drugs. Viruses are among the major pathogenic agents that cause number of serious diseases in humans, animals and plants. Viruses cause many diseases in humans, from self resolving diseases to ...
ClamTk, an open-source antivirus based on the ClamAV antivirus engine, was originally developed by Tomasz Kojm in 2001.. Antivirus software (abbreviated to AV software), also known as anti-malware, is a computer program used to prevent, detect, and remove malware.. Antivirus software was originally developed to detect and remove computer viruses, hence the name.
Anti-virus software (sometimes more broadly referred to as anti-malware software) looks for patterns based on the signatures or definitions of known malware. Anti-virus vendors find new and updated malware daily, so it is important that you have the latest updates installed on your computer. Once you have installed an anti-virus package, you ...
A computer virus is a malicious software program which has the ability to make copies of itself. The computer virus infects the files and programs present on the computer system without the knowledge or permission of the user. It spreads from one computer to another, leaving infections as it travels. Almost all viruses are attached to an ...
Free Google Slides theme and PowerPoint template. In this new template you will find a whole lot of infographics ready to be used in presentations that talk about viruses. These themed diagrams appear as timelines, maps, columns, hexagons and many more. Some health-related icons are provided too to help you place everything into context at a ...
What Is Antivirus? Antivirus solutions are designed to identify malicious software or code that has infected a computer. AVs use various methods to identify potential malware infections, including: Signature-Based Detection: Signature-based detection identifies known threats based on signatures such as file hashes, command and control domains, IP addresses, and similar features.
35 Best Antivirus-Themed Templates. CrystalGraphics creates templates designed to make even average presentations look incredible. Below you'll see thumbnail sized previews of the title slides of a few of our 35 best antivirus templates for PowerPoint and Google Slides. The text you'll see in in those slides is just example text.
here. Start the log: Start a virus scan: Windows icon > All apps > Windows security > Virus and threat protection > Scan options > Full scan > Scan now. 3. Analyze log: The log evaluation via ...
PCMag awarded its "Editors' Choice" honor for 2024 to Avast One Essential. It earned an "outstanding" overall rating of 4.5 out of 5 from PCMag. In writing about the rankings, Neil J ...
Free Google Slides theme and PowerPoint template. Cybersecurity is a must in most companies nowadays. Keep your employees up to date with the world of malware by editing and inserting these infographics into your presentations. You can provide data and statistics about different antivirus software and how to prevent hacking, phishing and other ...
APHIS Recommendations for HPAI H5N1 Virus in Livestock (PDF, 214.38 KB) For State Animal Health Officials, Accredited Veterinarians, and Producers. Testing Recommendations for Influenza A in Cattle (PDF, 317.46 KB) APHIS' current recommendations for testing affected or exposed cattle. ...
Below you'll see thumbnail sized previews of the title slides of a few of our 238 best virus templates for PowerPoint and Google Slides. The text you'll see in in those slides is just example text. The virus-related image or video you'll see in the background of each title slide is designed to help you set the stage for your virus-related ...
Free Google Slides theme and PowerPoint template. Oh no! A virus has entered this template! Check your data protection settings and change all your passwords… and check out this modern computer virus minitheme, illustrated with viruses and bugs! Perfect for any cyber security-related presentation, all its slides are fully customizable to make ...