

Cyber violence: What do we know and where do we go from here?
May 31, 2017
This paper reviews the existing literature on the relationship between social media and violence, including prevalence rates, typologies, and the overlap between cyber and in-person violence. This review explores the individual-level correlates and risk factors associated with cyber violence, the group processes involved in cyber violence, and the macro-level context of online aggression. The paper concludes with a framework for reconciling conflicting levels of explanation and presents an agenda for future research that adopts a selection, facilitation, or enhancement framework for thinking about the causal or contingent role of social media in violent offending. Remaining empirical questions and new directions for future research are discussed.
Get access to the full article from Aggression and Violent Behavior, Volume 34, here .
Authors: Jillian Peterson and James Densley
DOI: https://doi.org/10.1016/j.avb.2017.01.012
- Peer-Reviewed
- Watch or Listen
- By Jill and James
- Data Visualizations
- February 2022
- January 2022
- December 2021
- November 2021
- October 2021
- September 2021
- August 2021
- February 2021
- January 2021
- December 2020
- November 2020
- October 2020
- September 2020
- August 2020
- February 2020
- January 2020
- December 2019
- November 2019
- October 2019
- September 2019
- August 2019
- February 2019
- November 2018
- February 2018
- December 2017
- October 2017
- August 2017
Privacy Overview
- UN Women HQ
A Guide for Women and Girls to Prevent and Respond to Cyberviolence

A Guide for Women and Girls to Prevent and Respond to Cyberviolence has been developed to help build awareness on the different forms of cyberviolence and provide some essential practices and strategies to minimize being subjected to cyberviolence - and to be able to respond in case it happens.
Restrictions, lockdowns and other response measures to the COVID-19 pandemic have boosted people’s already-growing online presence, interactions and reliance on digital services. This connective technology holds enormous potential for empowering women and girls; it expands access to public services, creates opportunities for education and skills development, enables social engagement at a distance, provides a wealth of entertainment and open doors to employment and entrepreneurship. Unfortunately, it can also lead to cyberviolence - harms such as bullying, harassment, loss of privacy and direct violence - especially against women and girls who are just crossing the digital divide. These risks need to be eliminated so that women and girls have equal access to and use of digital tools and can equally benefit from growth in the digital economy.
The guide has been produced by UN Women and UNICEF under the joint UN project ‘Accelerating Women’s Empowerment for Economic Resilience and Renewal: The post-COVID-19 reboot in Armenia’, implemented by UNDP, UNIDO, UNICEF and UN Women.
View online/download
Armenian , English
Bibliographic information
Latest news.
- About UN Women
- Executive Director
- Regional Director
- Guiding documents
- Report wrongdoing
- Procurement
- UN Women in Action
- EU 4 Gender Equality
- Digital Library
- 16 Days of Activism against Gender-Based Violence
- Refugee Response Plan
- UN System Coordination in Europe and Central Asia
- Women's Entrepreneurship EXPO
- Programme implementation
- Transformative Financing for Gender Equality in the Western Balkans
- Leadership and Political Participation
- Economic Empowerment
- Ending Violence against Women
- National Planning and Budgeting
- Representative
- Women's Economic Empowerment
- Gender-Responsive Governance and Leadership
- Communications and Advocacy
- Partnership and Coordination
- Economic Empowerment of Women
- Elimination of Violence against Women
- National planning and budgeting
- Sustainable Development Agenda
- Ending violence against women
- Peace and security and engendering humanitarian action
- Economic empowerment
- Peace and security
- Leadership and political participation
- UN system coordination
- Gender Equality Facility
- Ending violence against women and girls
- Refugee Response
- Gender-responsive planning and budgeting
- Private sector partnerships and male engagement
- Strengthening Civil Society Capacities and Multi-Stakeholder Partnerships
- Regional Civil Society Advisory Group
- Regional Forum on Sustainable Development for the UNECE region
- UN Commission on the Status of Women (CSW68)
- International Women's Day 2023
- UN Commission on the Status of Women (CSW67)
- Supporting women and girls in Türkiye in the aftermath of the earthquakes
- Ukraine crisis is gendered, so is our response
- Regional Forum on Sustainable Development for the UNECE Region
- International Women’s Day 2022
- International Day of Women and Girls in Science
- Women, peace and security
- Gender equality matters in COVID-19 response
- Generation Equality
- International Girls in ICT Day
- Women refugees and migrants
- Women in humanitarian action
- International Day of Rural Women
- Women and the SDGs
- Media contacts
- Publications
- SDG monitoring report
- Progress of the world’s women
ORIGINAL RESEARCH article
Effects of information overload, communication overload, and inequality on digital distrust: a cyber-violence behavior mechanism.

- 1 School of Management, Jiangsu University, Zhenjiang, China
- 2 Department of Business Administration, Sukkur Institute of Business Administration University, Sukkur, Pakistan
- 3 School of Finance and Economics, Jiangsu University, Zhenjiang, China
In recent years, there has been an escalation in cases of cyber violence, which has had a chilling effect on users' behavior toward social media sites. This article explores the causes behind cyber violence and provides empirical data for developing means for effective prevention. Using elements of the stimulus–organism–response theory, we constructed a model of cyber-violence behavior. A closed-ended questionnaire was administered to collect data through an online survey, which results in 531 valid responses. A proposed model was tested using partial least squares structural equation modeling using SmartPLS 3.0, v (3.2.8). Research findings show that information inequality is a strong external stimulus with a significant positive impact on digital distrust and negative emotion. However, the effects of information overload on digital distrust and the adverse effects of communication overload on negative emotions should not be ignored. Both digital distrust and negative emotions have significant positive impacts on cyber violence and cumulatively represent 11.5% changes in cyber violence. Furthermore, information overload, communication overload, information inequality, and digital distrust show a 27.1% change in negative emotions. This study also presents evidence for competitive mediation of digital distrust by information overload, information inequality, and cyber violence. The results of this study have implications for individual practitioners and scholars, for organizations, and at the governmental level regarding cyber-violence behavior. To test our hypotheses, we have constructed an empirical, multidimensional model, including the role of specific mediators in creating relationships.
Introduction
Cyber violence refers to any behavior on the Internet advocating violence or using language calculated to inflame the passions to achieve mass emotional catharsis ( Hou and Li, 2017 ), which can be considered an extension of social violence to the Internet ( Li et al., 2017 ). In the past 2 years, with the rapid growth of Internet users, cyber violence incidents on social media have appeared frequently, including such behavior as bullying, flaming, and verbal abuse, and even death threats. For example, Doctor An, the protagonist of the “collision” incident at the Deyang swimming pool in 2018, committed suicide as a result of the added stress of cyber violence. During the COVID-19 (coronavirus disease 2019) epidemic in 2020, private information such as ID numbers and photographs of confirmed COVID-19 patients and people who live in Hubei province was widely spread on social networks. This resulted in suffering and serious secondary harm to the parties involved from excessive hardcore prevention and control. Studies have shown that cyber violence can have serious adverse consequences on an individual's psychology and physiology ( Sincek et al., 2017 ; Backe et al., 2018 ) and is a major factor in fomenting social instability. Therefore, clarifying the mechanism of cyber violence and understanding its essence constitute a worthwhile goal for governmental policy makers to develop scientific guidelines for relevant online behavior, as well as protecting the physical and mental health of Internet users and maintaining social stability and unity.
In the academic world, domestic and foreign scholars from many fields, such as political philosophy ( Finlay, 2018 ), law ( Cheung, 2009 ), media ( Zhang, 2012 ), sociology ( Owen et al., 2017 ), and psychology ( Hou and Li, 2017 ), have made many useful contributions to the study of cyber violence. The research concerns of Chinese scholars with regard to cyber violence mainly focus on analyzing the type of behavior and key influences, the characteristics of the current situation, and new development trends in governance. The research methods mainly involve qualitative analysis and typical case studies. These investigations have produced a wealth of data, providing a solid theoretical basis and practical information for future scholars. However, the work to date has mainly centered on the occurrence and development of cyber violence from the macro and medium perspective. Only rarely have investigators combed through the antecedents and internal mechanisms of the formation of cyber violence from the viewpoint of individual users. Therefore, utilizing the theoretical framework of stimulus–organism–response (SOR) modeling, this article combines external environmental stimuli with individual cognition to explore the relationships between the various factors that generate cyber violence to reveal its mechanism.
Theoretical Background and Hypotheses Development
Theoretical background.
In the 1970s, some scholars began to realize that all aspects of the environment are external stimuli that affect an individual's cognition and emotion, which in turn influences them toward responsible behavior, leading to the proposal of the well-known SOR theory ( Mehrabian and Russell, 1974 ). Domestic scholars have applied SOR theory to the study of consumers' shopping behavior ( Zhang and Lin, 2017 ), online shopping trends ( Syastra and Wangdra, 2018 ), employee complaints ( Xie et al., 2019 ), and many other social phenomena. Thus, SOR theory and its associated framework have become accepted as the primary research tools for effectively analyzing individual behavior. Based on previous studies and SOR theory, this article holds that the formation of cyber violence progresses through three stages, namely, influences of environmental stimuli (S), psychological activity of the organism (O), and its collective responses (R). Our model has the following attributes:
1. In terms of external stimulation, individual users are affected by the information and communication overload (CO) unique to the digital era, and the information inequality (II) caused by the information cocoon room effect.
2. The combined effects of the above stimuli cause individuals to have complex psychological reactions, such as feeling of doubt and disagreement among users, expressed as digital distrust (DD) and negative emotions such as anxiety and disgust.
3. Individual reactions may take the form of specific negative behavior, such as cyber violence.
Based on the above analysis, behavior leading to cyber violence is essentially a kind of feedback from digital users for coping with negative influences from the external environment combined with internal psychological stress. The external environmental factors include information overload (IO), CO, and II. Online distrust and negative emotions are typical psychological responses to these external factors. Cyber violence is the behavioral feedback resulting from these individual psychological activities.
Hypotheses Development
Information overload.
IO refers to the situation where information exceeds the ability of a user to process and utilize it, resulting in negative feelings of failure. IO is a function of information quality and quantity—specifically, excessive quantity and poor quality ( Rong, 2010 ; Cheng et al., 2014 ). Excess information is usually a result of redundancy, and users can reduce this factor with various digital technologies that continuously compare the effectiveness of information among users and increase the possibility of disagreements among users. The decrease in information quality makes users doubt the truth of the information presented and have to take time to determine its veracity. When users have to spend too much time in an attempt to obtain effective information, negative emotions will occur ( Asif Naveed and Anwar, 2020 ). The research of Congard and Carole (2020) on IO in the international network environment also showed that too much information will generate negative emotions among users. Therefore, this article proposes the following hypotheses:
H1a: IO has a significant positive effect on DD.
H1b: IO has a significant positive effect on negative emotions.
Communication Overload
CO refers to a situation in which a network's communication needs exceed an individual's communication ability ( Cho et al., 2011 ; Tripathy et al., 2016 ), which can interrupt a user's study or work schedule ( Cao and Sun, 2017 ). CO can disturb the normal routine of users ( Mcfarlane and Latorella, 2002 ), and the frequent interruptions make it difficult for them to concentrate ( O'Connail and Frohlich, 1995 ; Mcfarlane, 1998 ). This can lead to a decline in the accuracy of judgment and thus negatively affect users' feelings about trusting the information and even other individuals ( Mcfarlane and Latorella, 2002 ). At the same time, when faced with social communications that have to be dealt with, users who lack effective communication skills may be at a loss and can suffer from fatigue and anxiety ( Mcfarlane, 1998 ). Consequently, we proposed the following hypotheses:
H2a: CO has a significant positive effect on DD.
H2b: CO has a significant positive effect on negative emotions.
Information Inequality
II results from inherent social inequities that affect how people at different socioeconomic levels gain access to information and what types of information are distributed to them. Differences in information access are mainly related to the level of technological development in a region, but also to individual educational background. Good education and high-quality social resources generally ensure equal access to and use of information technology and information resources ( Figueiredo, 2018 ). The essence of information distribution inequality is the selectiveness inherent in the power to control information, which is considered a necessary element of resource distribution ( Hargittai and Hsieh, 2013 ). As inequities in information access have been largely addressed by most countries, the II discussed in this article will mostly refer to its unequal distribution. Controlling who gets what information is much easier on Internet-based platforms than with print media. Mastering the technology for channeling fragmented information according to some algorithm has allowed media giants to take advantage of the system to restrict distribution and deprive users of their right to information. II selectively influences users' perceptions, reduces comprehension and objective understanding of the world, and lowers trust among users. When information flow is selectively altered to make it more homogeneous, the user's rational and cognitive abilities become inoperable. Rational thinking cannot take place when facts are withheld or misrepresented. In such a situation, differences of opinion are increased, and communication barriers occur among different groups, resulting in further narrowing of information bandwidth and the creation of an information “cocoon” around the users, producing cognitive dissonance in the group and increased communication difficulties ( Hargittai and Hsieh, 2013 ). When the differences in values between groups are constantly expanding, negative emotions are likely to occur. To address this, we proposed the following hypotheses:
H3a: II has a significant positive impact on DD.
H3b: II has a significant positive effect on negative emotions.
Digital Distrust
The Pew Research Center released a study entitled “The Future of Well-Being in a Tech-Saturated World” in April 2018 ( Janna and Lee, 2018 ). In the report, DD was defined for the first time as exclusion among digital technology users. When people believe that others are better than themselves, DD will reduce individual initiative and intensify the further weaponization of shock, fear, anger, humiliation, and other emotions on the Internet, thus causing disagreement and questioning ( Judith, 2016 ). People's positive emotion is the mental state represented as “trust,” whereas the negative emotion is the mental state represented by “distrust” ( Sha et al., 2015 ). DD can divide users, create negative emotions, and potentially tear society apart, making negative behavior such as cyber violence more likely to occur. Consequently, the following hypotheses were proposed:
H4: DD has a significant positive effect on negative emotions.
H5: DD has a significant positive effect on cyber violence.
Negative Emotions
Negative stimuli can produce negative emotions ( Liu and Liu, 2013 ). In the Internet environment, users' negative emotions include regret, anxiety, fear, disgust, irritability, etc. ( Ruensuk et al., 2019 ). In his research on China's cyber violence from the perspective of initiators and participants, Hou and Li (2017) showed that the motivations for cyber violence could be divided into moral judgments and cathartic malicious attacks, arising from cathartic emotions. The Internet provides a convenient place for people to vent their emotions, but if this is done carelessly, it can result in the rapid spread of negative feelings and the instigation of cyber violence. Therefore, the following hypothesis is proposed:
H6: Negative emotions have a significant positive effect on cyber violence.
The Mediating Role of Digital Distrust
For products that they have purchased, consumers often post comments or reviews in which they rate the item positively or negatively according to their experience with it. The negative deviation theory states that negative information can have a powerful deterrent effect on users, in contrast to positive or neutral information. Other researchers ( Zhu et al., 2020 ) found that positive information was considered more trustworthy than negative information. Furner and Zinko (2017) studied the influence of IO on the development of trust and purchase intention based on online product reviews in a mobile vs. web context. The results confirmed that IO had a strong influence on trust. Furner Christopher et al. (2016) revealed an association between IO, trust, and purchase intention. A recent study ( Zhu et al., 2020 ) supported the idea of a mediating role of trust and satisfaction between information quality, social presence, and purchase intention. Therefore, this article proposed the following hypothesis:
H7: DD mediates the relationship between information and CO and II.
Our SOR-based cyber violence mechanism model constructed according to the above assumptions is shown in Figure 1 .
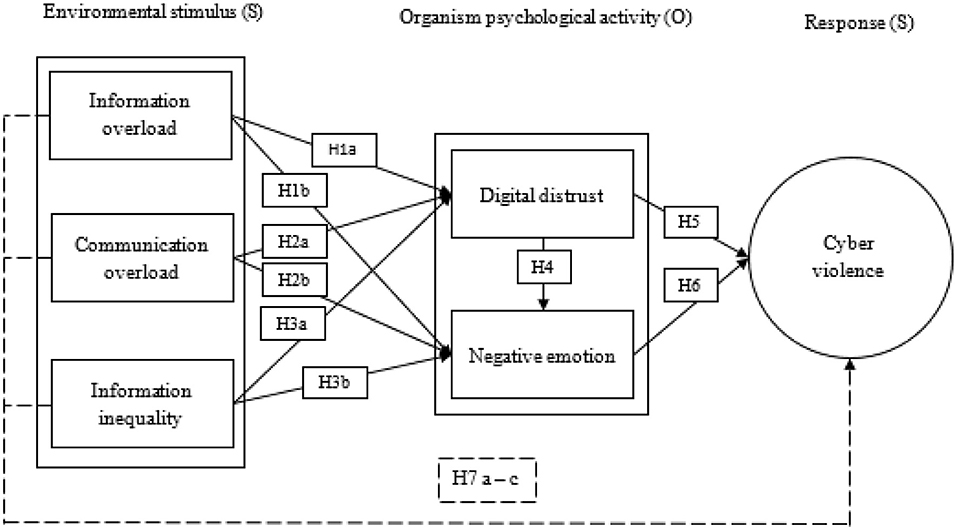
Figure 1 . Theoretical model.
Research Methodology
Sample and procedure.
A sample of 531 was obtained from general public using a convenient random sampling approach because of time and budget constraints. A closed-ended questionnaire was administered by email and through online platforms such as WeChat and WhatsApp. Online surveys are often used when the population is large ( Tian et al., 2020 ). Authenticated online surveys are considered a valid tool for new research and provide a fast, simple, and less costly approach to collecting data ( Qalati et al., 2021 ). The formal survey was designed and conducted from February 2020 to April 2020, and the major reason for collecting data in 4 months' lag time was to mitigate common method bias (CMB) ( Li et al., 2020 ). In the present study, 783 questionnaires were collected from a general audience, of which 252 were invalidated because of a selection of the same option and the use of the same IP for the response. This left 531 valid questionnaires for an effective response rate of 67.82%.
Respondents' Information
Table 1 reflects that a total of 322 male and 209 female participants accounted for 60% and 40%, respectively. Respondents younger than 25 (245), 26–30 (146), 31–40 (67), 41–50 (41), and older than 50 years accounted for 46.1, 27.5, 12.7, 7.7, and 6%, respectively. Regarding the frequency of microblog usage, approximately more than one-third of participants accounted for once a day (35.6%) and several times a day (36.9%), whereas more than one-quarter of them (27.5%) for several times a week. Regarding the duration of microblog usage under a year (42), 1–2 (151), 2–3 (157), 3–4 (67), and more than 4 (114) years accounted for 7.9, 28.4, 29.6, 12.6, and 21.5%, respectively.
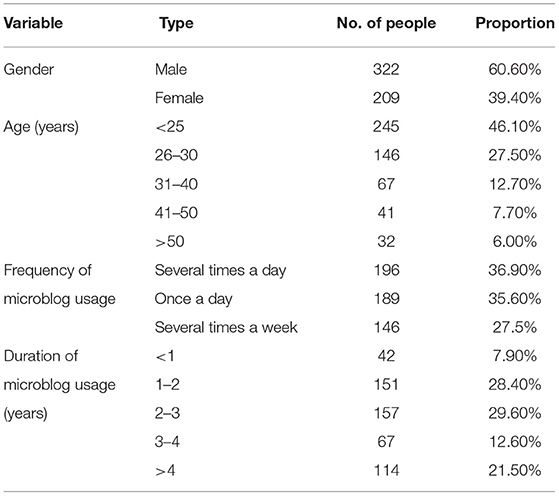
Table 1 . Descriptive statistics.
The study used seven-point Likert scales (1 = very unimportant to 7 = very important) to record responses. A pilot survey containing 21 questions was first conducted to validate the questionnaire method. After analyzing and discussing the pilot study results with experts, the questions, wording, and semantics of the questionnaire were modified, resulting in a final list of 18 items that were issued as the formal questionnaire ( Table 3 ). IO was measured using three items from Karr-Wisniewski and Lu (2010) , Lee et al. (2016) . CO was assessed using three items ( Cho et al., 2011 ; Lee et al., 2016 ; Shi et al., 2020 ). II was measured using three items adapted from Lee et al. (2016) and Yu et al. (2017) . DD was measured using three items from Zhu et al. (2020) . Negative emotions were assessed using three items adapted from Kang et al. (2013) and Chiu et al. (2020) , and cyber violence was assessed using three items from Lee et al. (2016) and Sari and Camadan (2016) .
Data Analysis
To consider the influence of multiple variables on the model and verify the validity of the theoretical hypotheses, structural equation modeling (SEM) was used to analyze the data. SPSS 24.0 and SmartPLS 3.2.8 were the statistical software used in the study. In particular, SPSS was used for descriptive information of the participants and some test related to CMB and sample adequacy, whereas SmartPLS 3.0 was used for partial least squares (PLS) SEM because it is widely used across fields ( Hair Joseph et al., 2019 ; Ahmed et al., 2020 ). Furthermore, it is considered a comprehensive software program with an intuitive graphical user interface to run PLS-SEM analysis, which certainly has had a massive impact. Besides, it enables the specification of complex interrelationships between observed and latent constructs ( Hair Joseph et al., 2019 ).
Common Method Bias and Bartlett Spherical Test
The Kaiser–Meyer–Olkin (KMO) value and Bartlett spherical test value of sample data were calculated. The KMO value was 0.745, the chi-squared value was 4,199.094, the degrees of freedom were 276, and the p < 0.001 ( Table 2 ). The larger the KMO value, the stronger the correlation between variables. The variables were suitable for factor analysis, and the structural validity between variables was good ( Chen et al., 2016 ). This study used three approaches to detect the CMB. First, Harman's single factor test stated that the first factor represents only 16.18% of the variance, which is far below the acceptable threshold (50.0%) ( Podsakoff et al., 2003 ). Second, variance inflation factor (VIF), which is called the full-collinearity approach using SmartPLS ( Ali Qalati et al., 2021 ), requires to be ≤ 3 ( Hair Joseph et al., 2019 ) ( Table 3 ). Third, Bagozzi et al. (1991) proposed that if the correlation among the constructs was >0.9, there is evidence of CMB. However, none of the constructs was found to be greater than the minimum cutoff value ( Table 4 ).
Table 2 . KMO and Bartlett test.

Table 3 . Measurement model.
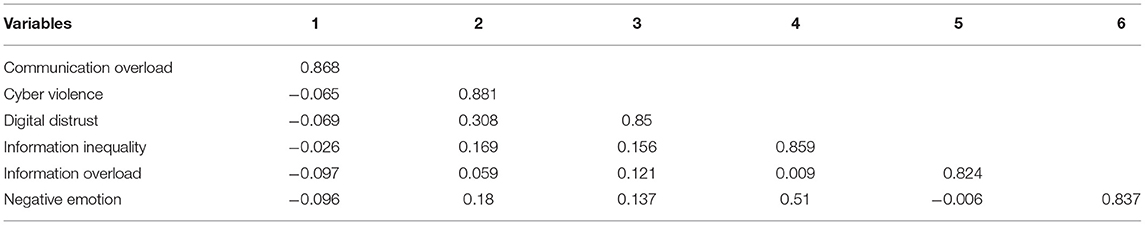
Table 4 . Discriminant validity.
Measurement Model
According to Roldán and Sánchez-Franco (2012) , a proposition to measure the model is required to assess the individual items for reliability, internal consistency, content validity, convergent validity, and discriminant validity. Individual item reliability was measured by outer loadings of items related to a particular dimension ( Hair et al., 2012 ). Hair et al. (2016) recommended that factor loading should be between 0.40 and 0.70, whereas Hair et al. (2017) proposed a value of ≥0.7 ( Table 3 ). According to Nunnally (1978) , Cronbach α values should exceed 0.7: the threshold values of constructs in this study ranged between 0.782 and 0.857. The internal consistency reliability ( Bagozzi and Yi, 1988 ) required that the composite reliability (CR) be ≥0.7, and the CR coefficient values in this study were between 0.863 and 0.912. Regarding convergent validity, Fornell and Larcker (1981) recommended that the average variance extracted (AVE) should be ≥0.5. The AVE values in this study were between 0.679 and 0.776, confirming a satisfactory level of convergent validity. With regard to discriminant validity, Fornell and Larcker (1981) stated that the square root of the AVE for each construct should exceed the correlation of the construct with other model constructs. Table 4 gives the discriminant validity of the results.
Structural Model
In this article, SmartPLS 3.2.8 was used to estimate the path coefficient and verify the hypothesis. This article used PLS bootstrapping with 5,000 bootstraps for the 531 cases to demonstrate results associated with the path coefficients and their significance level ( Table 5 ). Among them, H1a, H2b, H3a, H3b, H5, H6, H7a, and H7c passed the significance test. However, the path coefficient of H2b was −0.081, which proves the hypothesis stating that CO had a significant negative impact on negative emotions, but it is very close to the rejection cutoff. The model path analysis found that the hypotheses, H1b, H2a, H4, and H7b, were not valid. The graphical presentation of the model with path and significance level is shown in Figure 2 . The results can be interpreted to conclude that IO and II have a significant positive impact on DD and that II has a significant positive effect on negative emotions. CO has a significant negative impact on negative emotions. DD and negative emotions have a significant positive effect on cyber violence. According to Zhao et al. (2010) , there are five types of mediation: complementary, competitive, indirect only, direct only, and no effect (non-mediated). The authors stated that if the mediated effect ( a × b ) and direct effect c both exist and point in the same direction, it is called complementary mediation. The evidence from this study proves that DD is a complementary mediator. There is no global measure of goodness of fit in SmartPLS-SEM ( Hair et al., 2011 ).
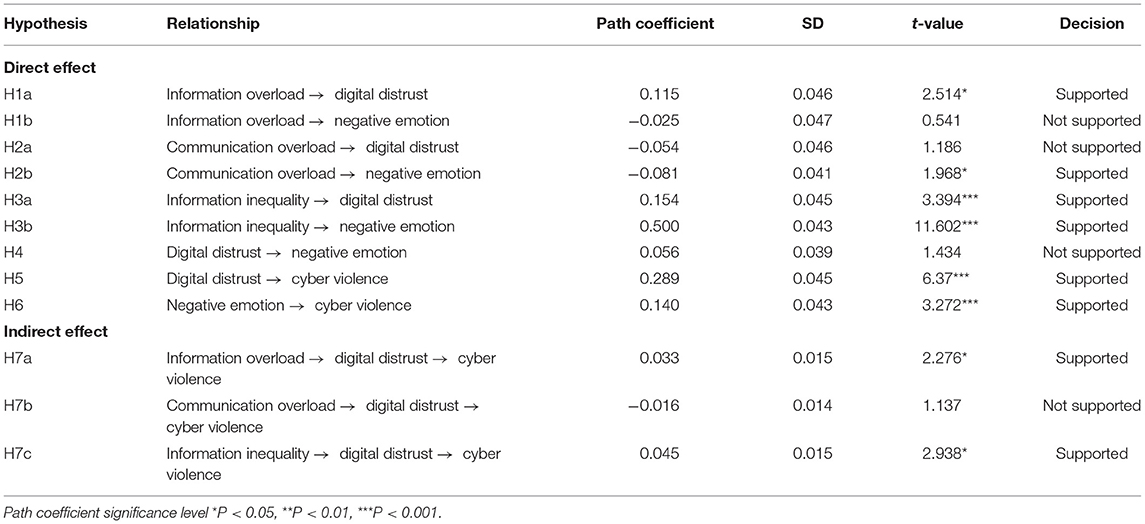
Table 5 . Path coefficients and hypothesis testing.
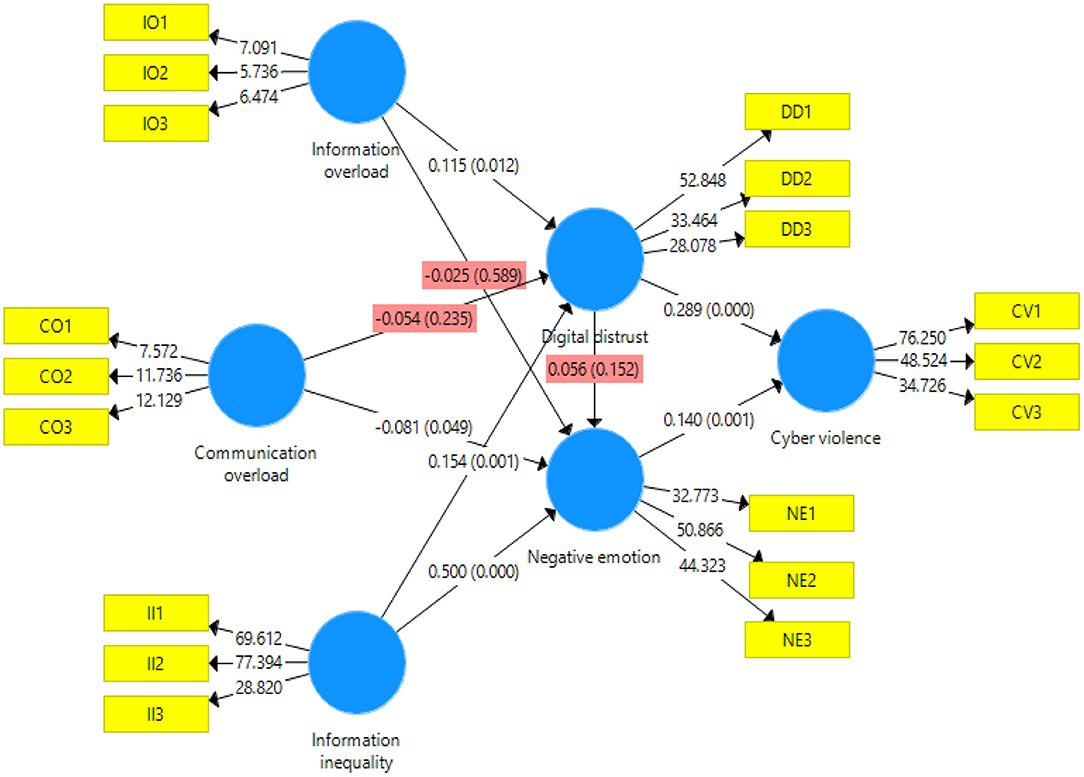
Figure 2 . Structural equation modeling.
According to Cohen (1988) , R 2 values of 0.60, 0.33, and 0.19 are, respectively, substantial, moderate, and weak. However, Falk and Miller (1992) argued that an R 2 value as low as 0.10 is also acceptable. The R 2 value for this study was 0.115 for cyber violence. This suggests that DD and negative emotion explain 11.5% of the variation ( Table 6 ), as the R 2 -value is sufficiently above the minimum cutoff according to Falk and Miller (1992) . This study also employed the cross-validated redundancy measure ( Q 2 ) to evaluate the model. Henseler et al. (2009) suggested that a Q 2 > 0 shows that the model has predictive relevance. Values of 0.02, 0.15, and 0.35, respectively, indicate that an exogenous construct has a small, medium, or considerable predictive relevance for a specific endogenous construct. The current study's model has weak predictive relevance for cyber violence and DD and medium for negative emotions ( Table 6 ).
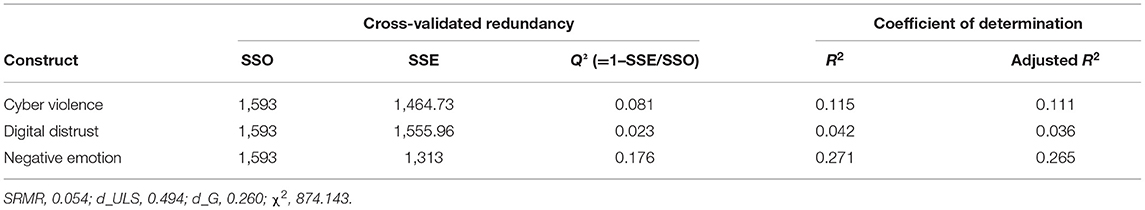
Table 6 . Strength of the model.
Standardized root mean square residual (SRMR) was used to assess the goodness of fit. SRMR is an absolute measure of fit: a value of zero indicates a perfect fit, and a value of <0.08 is considered a good fit ( Hu and Bentler, 1999 ). In this study, the SRMR value obtained was 0.054, which is well-below the minimum cutoff ( Table 6 ).
Utilizing the results from 531 valid questionnaires, five of the nine hypotheses regarding the mechanism of cyber violence in this article were verified, and all of them were significantly correlated. IO and II have a significant positive impact on DD, as supported by hypotheses H1a and H3a. Thus, digital users need to sift through the overload of information in order to dispel doubts and prevent disagreements with others. Because the user has gradually lost control of information access, effective information acquisition is more difficult. This results in a growing divergence between users that eventually creates DD. There are two main reasons for this. On the one hand, it is one of the characteristics of the digital age that information redundancy and information quality decline when IO exists. On the other hand, digital users have come to see that technological empowerment in the digital era has resulted in information control. This may manifest as problems such as living in an information cocoon and being subject to algorithm discrimination, which prevents users from obtaining the full complement of information and using it for production and creation. This conclusion is consistent with previous studies. II (path coefficient = 0.149) has a slightly stronger effect on DD than IO (path coefficient = 0.114). This demonstrates that the control of information by businesses empowered by digital technology has emerged as a growing threat to online shoppers and social media users. Therefore, improving information quality, reducing redundancy, and strengthening users' rights to access all information will help to reduce DD.
II has a significant positive impact on negative emotions, as supported by our findings in support of H3b. The more that digital users feel the unequal power of information control, the stronger their negative emotions will be. This conclusion is consistent with previous studies. The development of a digital society has led users to pay more attention to the value of information. Possessing excellent opportunities for searching, processing, and analyzing information is the sine qua non for success in social competition. However, when information access and distribution are deliberately manipulated over a period of time, conflicts among social groups will grow, and their mutual interests will diverge to the point where the different social groups may be torn apart, and severe negative social emotions will be the result. To prevent this from happening, stricter limits on information control by businesses need to be enacted and enforced. Internet users should be given equal access to and use of information to reduce differences of opinion and communication barriers between different groups to eliminate negative emotions.
DD and negative emotions have a significant positive impact on cyber violence, supported by findings from the H5 and H6 paths. The more serious the doubts and differences among digital users, the stronger will be the associated negative emotions, and the more serious the online violence. Compared with negative emotions (path coefficient = 0.176), DD has a higher degree of influence (path coefficient = 0.322), which indicates that the causes of cyber violence are not only the negative emotions associated with the emotional catharsis of users, but the doubts and disagreements between users that have become embedded in their minds. The goal, then, is the construction of a free and fair communication channel between users, eliminating doubts and disagreements, providing a clean and honest Internet environment, to stop negative emotions and cyber violence.
CO negatively affects negative emotions but is inconsistent with the H2b hypothesis, so the path is not supported. This suggests that digital users believe that negative emotions and behavior do not increase even in the presence of unmanageable communication and IO. This conclusion is inconsistent with previous studies, which may be due to the fact that CO has been widely perceived as an emerging social problem. However, compared with the more prominent problematic Internet use or social network addiction, it appears to have a lower impact and is easily ignored ( Gui and Büchi, 2019 ). In addition, academic research results on the correlation between CO and negative emotions are inconsistent. For example, Chen and Lee concluded that CO caused by too frequent use of Facebook produced anxiety ( Chen and Lee, 2013 ), whereas Jelenchick et al. found that the constant use of this social network on the university campus had nothing to do with anxiety ( Jelenchick et al., 2013 ). Therefore, the conclusions drawn from this article should be tempered by the consideration that Chinese digital users may not have a systematic understanding of CO, and the results may be related to the type of Internet platform and study group, as well as their environment and cultural background.
In this article, H1b, H2a, H4, and H7b were not verified; however, that does not mean that IO has no effect on negative emotions or that CO does not foster DD. DD had no effect on negative emotions and no mediating effect between CO and cyber violence. There are many possible reasons for the lack of verification of the hypotheses, but these will have to be pursued in subsequent studies. The conclusions from this investigation are that to circumvent the generation of cyber violence based on the perspective of individual users, more attention should be paid to the influence of IO, II, DD, and negative emotions, as well as their significant correlation.
Theoretical Implications
This study has several theoretical implications and makes a significant contribution to the existing literature on cyber violence. First, prior studies have paid more attention to information quality and less to the cumulative effects of IO, CO, and II. Second, this study leverages the application of the SOR model to the online environment, where the responses can be treated as new stimuli. Third, this study is grounded on the SOR theory to explain the intrinsic association between information, communication, II, and DD, negative emotions, and cyber-violence behavior. It should be noted that CO is not a significant antecedent of either DD or negative emotion, whereas IO and inequality comprise significant drivers of both. Our findings highlight the important mediating role of DD and negative emotions, revealing the clear association between an individual's perceptions of the digital world and its power to generate negative emotions. Therefore, this study can be considered as a new approach to understanding the path from stimuli such as IO, CO, and II to Internet behavior mediated by DD and negative emotions in the context of e-commerce.
Practical Implications at the National, Enterprise, and Individual Level
At the national level, the government and relevant departments should impose new laws and regulations to clearly define the boundaries of information rights and interests between enterprises and users and to ensure that all users share equally in the access to information. The government need to be more proactive in regulating the network environment, establishing a spam tracing mechanism, punishments for deliberate misinformation, and controls on the generation and dissemination of low-quality, redundant information. Digital users should be encouraged to communicate with the authorities about incipient problems before they become a source of differences and doubts. Purging social groups of negative emotions necessitates the creation of a positive Internet ecosystem.
At the enterprise level, emerging Internet businesses need to establish the survival logic of “maximization of users' rights and interests rather than profit maximization.” Managers need to reconfigure the enterprise's value system and ease up on the control of information access and distribution to restore users' information rights and interests. The corporate Internet information review system needs to replace the production and diffusion of useless information with diversified high-quality information, to help users understand the world and reach a social consensus. More attention should be paid to users' emotional needs, and the engendering of negative emotions by the media should be stopped.
At the individual level, users should maintain a positive and optimistic attitude, but still be alert to the formation of information cocoons and algorithmic discrimination. They should take steps to enhance their information literacy, effectively identify and filter out low-quality information, and cultivate their information search and analysis ability. Their goals should be to strengthen their level of self-cognition, objectively view the self's need for information, conscientiously obtain objective information from multiple channels and points of view, and strive to reduce doubts and disagreements.
The theoretical model developed in this article is applicable to the analysis of the mechanism of cyber violence and provides the basis for a reasonable explanation of the formation of DD and negative emotions, which can be further explored in future studies.
Limitations and Future Research Suggestions
This study has certain limitations that highlight avenues for future research. We used a convenient random sampling approach because of budget and time constraints. Collecting data from China only limits our findings' generalizability, and future studies should employ a cross-cultural approach to investigate the causes of cyber-violence behavior. As data were collected through an online survey, which also impedes the generalizability of findings in other countries, thus we call for future studies to include field surveys. The questionnaire survey scope could be expanded to increase the accuracy of the research results, as the sample size and reach may also be considered a limitation. Future studies could also investigate the effects of the government's policy on the mechanism.
The selection of research variables could be further subdivided into the internal environment and external environment variables to probe more deeply into the etiology of network violence. The follow-up will continue to analyze the above issues in detail to provide more theoretical and practical guidance for research on cyber violence.
Comparative studies could also be performed to validate our results and expand application of the proposed model using organizations and small- and medium-sized enterprises. This study did not examine the relationship between participants' attitudes, DD, negative emotions, and intentions, and future programs should investigate the influence of participant's attitudes and intentions. Finally, the mediating role of DD and negative emotions should be explored further.
Data Availability Statement
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding author/s.
Ethics Statement
The studies involving human participants were reviewed and approved by Jiangsu University. The patients/participants provided their written informed consent to participate in this study.
Author Contributions
All authors listed have made a substantial, direct and intellectual contribution to the work, and approved it for publication.
This study is supported by National Statistics Research Project of China (2016LY96).
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Ahmed, N., Li, C., Qalati, S. A., Rehman, H. U., Khan, A., and Rana, F. (2020). Impact of business incubators on sustainable entrepreneurship growth with mediation effect. Entrep. Res. J . 1–23. doi: 10.1515/erj-2019-0116
CrossRef Full Text | Google Scholar
Ali Qalati, S., Li, W., Ahmed, N., Ali Mirani, M., and Khan, A. (2021). Examining the factors affecting SME performance: the mediating role of social media adoption. Sustainability 13:75. doi: 10.3390/su13010075
Asif Naveed, D.-M., and Anwar, M. (2020). Towards information anxiety and beyond. Webology 17, 65–80. doi: 10.14704/WEB/V17I1/a208
Backe, E. L., Lilleston, P., and Mccleary-Sills, J. (2018). Networked individuals, gendered violence: a literature review of cyberviolence. Viol. Gender 2018, 135–146. doi: 10.1089/vio.2017.0056
Bagozzi, R. P., and Yi, Y. (1988). On the evaluation of structural equation models. J. Acad. Market. Sci. 16, 74–94. doi: 10.1007/BF02723327
Bagozzi, R. P., Yi, Y., and Phillips, L. W. (1991). Assessing construct validity in organizational research. Adm. Sci. Q . 36, 421–458. doi: 10.2307/2393203
Cao, X., and Sun, J. (2017). Exploring the effect of overload on the discontinuous intention of social media users: an S-O-R perspective. Comput. Hum. Behav . 81, 10–18. doi: 10.1016/j.chb.2017.11.035
Chen, W., and Lee, K. H. (2013). Sharing, liking, commenting, and distressed? The pathway between facebook interaction and psychological distress. Cyberpsychol. Behav. Soc. Netw. 16, 728–734. doi: 10.1089/cyber.2012.0272
PubMed Abstract | CrossRef Full Text | Google Scholar
Chen, X.-S., Chen, G.-F., and Zhang, R. (2016). Research on the relationship between the index structure of journal evaluation based on factor analysis and SEM model. Informat. Sci. 34, 61–64. doi: 10.13833/j.cnki.is.2016.10.011
CrossRef Full Text
Cheng, W.-Y., Cao, J.-D., and Lu, S.-Y. (2014). Revision of information anxiety scale. Information 33, 6–9. doi: 10.13833/j.cnki.is.2014.01.014
Cheung, A. S. Y. (2009). A study of cyber-violence and internet service providers' liability: lessons from China. Pacific Rim Law & Policy J. 18, 323–346.
Google Scholar
Chiu, H. T., Yee, L. T. S., Kwan, J. L. Y., Cheung, R. Y. M., and Hou, W. K. (2020). Interactive association between negative emotion regulation and savoring is linked to anxiety symptoms among college students. J. Am. Coll. Health 68, 494–501. doi: 10.1080/07448481.2019.1580712
Cho, J., Ramgolam, D. I., Schaefer, K. M., and Sandlin, A. N. (2011). The rate and delay in overload: an investigation of communication overload and channel synchronicity on identification and job satisfaction. J. Appl. Commun. Res. 39, 38–54. doi: 10.1080/00909882.2010.536847
Cohen, J. (1988). Statistical Power Analysis for the Behavioral Sciences. Hillsdale, NJ: Lawrence Erlbaum Associates, Publishers.
PubMed Abstract | Google Scholar
Congard, A., and Carole, R. (2020). Measuring Situational Anxiety Related to Information Retrieval on the Web Among English-Speaking Internet Users . Oxford: Oxford University Press.
Falk, R. F., and Miller, N. B. (1992). A Primer for Soft Modeling. Akron, OH: University of Akron Press.
Figueiredo, A. (2018). “Information frictions in education and inequality,” in 2018 Meeting Papers (Mexico City).
Finlay, C. J. (2018). Just war, cyber war, and the concept of violence. Philos. Technol. 31, 1–21. doi: 10.1007/s13347-017-0299-6
Fornell, C., and Larcker, D. F. (1981). Evaluating structural equation models with unobservable variables and measurement error. J. Market. Res. 18, 39–50. doi: 10.1177/002224378101800104
Furner Christopher, P., Zinko, R., and Zhu, Z. (2016). Electronic word-of-mouth and information overload in an experiential service industry. J. Serv. Theo. Pract. 26, 788–810. doi: 10.1108/JSTP-01-2015-0022
Furner, C. P., and Zinko, R. A. (2017). The influence of information overload on the development of trust and purchase intention based on online product reviews in a mobile vs. web environment: an empirical investigation. Electro. Markets 27, 211–224. doi: 10.1007/s12525-016-0233-2
Gui, M., and Büchi, M. (2019). From use to overuse: digital inequality in the age of communication abundance. Soc. Sci. Comput. Rev. 39:089443931985116. doi: 10.1177/0894439319851163
Hair Joseph, F., Risher Jeffrey, J., Sarstedt, M., and Ringle Christian, M. (2019). When to use and how to report the results of PLS-SEM. Euro. Bus. Rev. 31, 2–24. doi: 10.1108/EBR-11-2018-0203
Hair, J. F., Ringle, C. M., and Sarstedt, M. (2011). PLS-SEM: Indeed a silver bullet. J. Market. Theo. Pract. 19, 139–152. doi: 10.2753/MTP1069-6679190202
Hair, J. F., Sarstedt, M., Pieper, T. M., and Ringle, C. M. (2012). The use of partial least squares structural equation modeling in strategic management research: a review of past practices and recommendations for future applications. Long Range Plan. 45, 320–340. doi: 10.1016/j.lrp.2012.09.008
Hair, J. F. Jr., Hult, G. T. M., Ringle, C., and Sarstedt, M. (2016). A Primer on Partial Least Squares Structural Equation Modeling (PLS-SEM). Los Angeles, CA: Sage Publications. doi: 10.15358/9783800653614
Hair, J. F. Jr., Sarstedt, M., Ringle, C. M., and Gudergan, S. P. (2017). Advanced Issues in Partial Least Squares Structural Equation Modeling. Los Angeles, CA: Sage Publications.
Hargittai, E., and Hsieh, Y. P. (2013). “Digital inequality,” The Oxford Handbook of Internet Studies , ed W. H. Dutton (Oxford: Oxford University Press), 129–150. doi: 10.1093/oxfordhb/9780199589074.013.0007
Henseler, J., Ringle, C. M., and Sinkovics, R. R. (2009). “The use of partial least squares path modeling in international marketing,” in New Challenges to International Marketing . Emerald Group Publishing Limited (Bingley). doi: 10.1108/S1474-7979(2009)0000020014
Hou, Y., and Li, X. (2017). Cyber violence in China: its influencing factors and underlying motivation. J. Pek. Univers. 54, 101–107.
Hu, L. T., and Bentler, P. M. (1999). Cutoff criteria for fit indexes in covariance structure analysis: conventional criteria versus new alternatives. Struct. Equat. Model. Multidiscipl. J. 6, 1–55. doi: 10.1080/10705519909540118
Janna, A., and Lee, R. (2018). The Future of Well-Being in a Tech-Saturated World . Available online at: https://www.pewresearch.org/internet/2018/04/17/the-future-of-well-being-in-a-tech-saturated-world/
Jelenchick, L. A., Eickhoff, J. C., and Moreno, M. A. (2013). “Facebook Depression?” Social networking site use and depression in older adolescents. J. Adolesc. Health 52, 128–130. doi: 10.1016/j.jadohealth.2012.05.008
Judith, D. (2016). The Social Machine: Designs for Living Online. Cambridge: Leonardo.
Kang, Y. S., Min, J., Kim, J., and Lee, H. (2013). Roles of alternative and self-oriented perspectives in the context of the continued use of social network sites. Int. J. Informat. Manage. 33, 496–511. doi: 10.1016/j.ijinfomgt.2012.12.004
Karr-Wisniewski, P., and Lu, Y. (2010). When more is too much: operationalizing technology overload and exploring its impact on knowledge worker productivity. Comput. Hum. Behav. 26, 1061–1072. doi: 10.1016/j.chb.2010.03.008
Lee, A. R., Son, S.-M., and Kim, K. K. (2016). Information and communication technology overload and social networking service fatigue: a stress perspective. Comput. Hum. Behav. 55, 51–61. doi: 10.1016/j.chb.2015.08.011
Li, H., Zeng, L., and Teng, S. (2017). Research on the development of network violence:intension and type,status characteristics and governance measures——an analysis based on the cases of network violence during 2012-2016. J. Intelli. 36, 139–145.
Li, W., Qalati, S. A., Khan, M. a,.S, Kwabena, G. Y., Erusalkina, D., et al. (2020). Value co-creation and growth of social enterprises in developing countries: moderating role of environmental dynamics. Entrepren. Res. J . 1–28. doi: 10.1515/erj-2019-0359
Liu, Z.-M., and Liu, L. (2013). Public negative emotion model in emergencies based on aging theory. J. Indust. Eng. Eng. Manage. 27, 15–21. doi: 10.13587/j.cnki.jieem.2013.01.008
Mcfarlane, D. (1998). Interruption of People in Human-Computer Interaction. Washington, DC: The George Washington University
Mcfarlane, D., and Latorella, K. (2002). The scope and importance of human interruption in human-computer interaction design. Humancomput. Interact. 17, 1–61. doi: 10.1207/S15327051HCI1701_1
Mehrabian, A., and Russell, J. A. (1974). An Approach to Environmental Psychology . Cambridge: MIT.
Nunnally, J. (1978). Psychometric Methods . New York, NY: McGraw-Hill.
O'Connail, B., and Frohlich, D. (1995). “Timespace in the workplace: dealing with interruptions,” in Proceedings of the Conference Companion on Human Factors in Computing Systems (Denver, CO), 262–263. doi: 10.1145/223355.223665
Owen, T., Noble, W., and Speed, F. (2017). “Biology and cybercrime: towards a genetic-social, predictive model of cyber violence,” in New Perspectives on Cybercrime (Cham: Palgrave Macmillan), 27–44. doi: 10.1007/978-3-319-53856-3_3
Podsakoff, P. M., Mackenzie, S. B., Lee, J.-Y., and Podsakoff, N. P. (2003). Common method biases in behavioral research: a critical review of the literature and recommended remedies. J. Appl. Psychol. 88:879. doi: 10.1037/0021-9010.88.5.879
Qalati, S. A., Vela, E. G., Li, W., Dakhan, S. A., Hong Thuy, T. T., and Merani, S. H. (2021). Effects of perceived service quality, website quality, and reputation on purchase intention: the mediating and moderating roles of trust and perceived risk in online shopping. Cog. Bus. Manage. 8:1869363. doi: 10.1080/23311975.2020.1869363
Roldán, J. L., and Sánchez-Franco, M. J. (2012). “Variance-based structural equation modeling: Guidelines for using partial least squares in information systems research,” in Research Methodologies, Innovations and Philosophies in Software Systems Engineering and Information Systems . Hershey, PA: IGI Global, 193–221. doi: 10.4018/978-1-4666-0179-6.ch010
Rong, Y. (2010). On knowledge and information service oriented to information anxiety. Informat. Stud. Theo. Applicat. (Beijing). 32, 64–67. doi: 10.16353/j.cnki.1000-7490.2010.05.010
Ruensuk, M., Oh, H., Cheon, E., Oakley, I., and Hong, H. (2019). “ Detecting Negative Emotions During Social Media Use on Smartphones,” in Asian HCI Symposium'19 (Glasgow). doi: 10.1145/3309700.3338442
Sari, S. V., and Camadan, F. (2016). The new face of violence tendency:cyber bullying perpetrators and their victims. Comput. Hum. Behav. 59, 317–326. doi: 10.1016/j.chb.2016.02.027
Sha, Y., Yan, J., Wang, Z., and Management S. O. University L. Management S. O. (2015). Public trust on the red cross society of China after Ya'an earthquake—analysis based on sentiment analysis of microblog data. J. Public Manage. 12, 93–104. doi: 10.16149/j.cnki.23-1523.2015.03.009
Shi, C., Yu, L., Wang, N., Cheng, B., and Cao, X. (2020). Effects of social media overload on academic performance: a stressor–strain–outcome perspective. Asian J. Commun. 30, 179–197. doi: 10.1080/01292986.2020.1748073
Sincek, D., Duvnjak, I., and Mili, M. (2017). Psychological outcomes of cyber-violence on victims, perpetrators and perpetrators/victims. Hrvat. Revija Za Rehabili. Istrai. 53:98. doi: 10.31299/hrri.53.2.8
Syastra, M., and Wangdra, Y. (2018). Analisis online impulse buying dengan menggunakan framework SOR. J. Sist. Inform. Bisnis 8:19. doi: 10.21456/vol8iss2pp133-140
Tian, H., Iqbal, S., Akhtar, S., Qalati, S. A., Anwar, F., Khan, M., et al. (2020). The impact of transformational leadership on employee retention: mediation and moderation through organizational citizenship behavior and communication. Front. Psychol. 11:314. doi: 10.3389/fpsyg.2020.00314
Tripathy, S., Aich, S., Chakraborty, A., and Lee Gyu, M. (2016). Information technology is an enabling factor affecting supply chain performance in Indian SMEs: a structural equation modelling approach. J. Model. Manage. 11, 269–287. doi: 10.1108/JM2-01-2014-0004
Xie, Y., Li, L., Qin, Y., Dun, H., and University H. (2019). A literature review of employee grievance and prospects based on SOR theory framework. Chin. J. Manage. 16, 783–790.
Yu, T.-K., Lin, M.-L., and Liao, Y.-K. (2017). Understanding factors influencing information communication technology adoption behavior: the moderators of information literacy and digital skills. Comput. Hum. Behav. 71, 196–208. doi: 10.1016/j.chb.2017.02.005
Zhang, B., and Lin, J.-B. (2017). The influence factor of consumers′adverse selection in the context of food harm:based on the perspective of SOR theory. Stats Inform. Forum 32, 116–123.
Zhang, Y. (2012). The violent tendency of internet public opinion and countermeasures. J. Intelli. 31, 86–90.
Zhao, X., Lynch, J. G. Jr, and Chen, Q. (2010). Reconsidering baron and kenny: myths and truths about mediation analysis. J. Consum. Res. 37, 197–206. doi: 10.1086/651257
Zhu, L., Li, H., Wang, F.-K., He, W., and Tian, Z. (2020). How online reviews affect purchase intention: a new model based on the stimulus-organism-response (S-O-R) framework. Aslib J. Inform. Manage. 72, 463–488. doi: 10.1108/AJIM-11-2019-0308
Keywords: cyber violence, information overload, communication overload, information inequality, digital distrust, negative emotions, SOR theory
Citation: Fan M, Huang Y, Qalati SA, Shah SMM, Ostic D and Pu Z (2021) Effects of Information Overload, Communication Overload, and Inequality on Digital Distrust: A Cyber-Violence Behavior Mechanism. Front. Psychol. 12:643981. doi: 10.3389/fpsyg.2021.643981
Received: 19 December 2020; Accepted: 10 March 2021; Published: 20 April 2021.
Reviewed by:
Copyright © 2021 Fan, Huang, Qalati, Shah, Ostic and Pu. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY) . The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Sikandar Ali Qalati, 5103180243@stmail.ujs.edu.cn ; sidqalati@gmail.com
† These authors have contributed equally to this work
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
Cyber Violence: Structures and Effectiveness
Recently, social media has become a platform for cyber violence. This issue primarily concerns public health and is associated with adverse mental or physical outcomes. As a result, cyberbullying is one of the top contemporary problems that needs to be approached from different angles to be resolved entirely. The purpose of this paper is to review several articles concerning cyber violence and draw a conclusion about their structures and effectiveness.
The first article is named Cyber violencitsat do we know and where do we go from here? and written by J. Peterson and J. Densley. The report is published in a journal called Aggression and Violent Behaviour in May 2017. The primary method the authors use is the selection and analysis of the already extant materials and sources related to the topic. It denotes that the authors resorted to the second type of research, which represents utilizing the existing articles and library sources to provide evidence-based theory. The material is well structured and has all the organizational components (introduction, main body, and conclusion). The authors introduce the acuteness of cyber violence to the reader, represent individual, group, and environmental explanations of the phenomenon, and investigate different approaches towards the issue (Peterson & Densley, 2017). Therefore, to my mind, this article is wisely structured, and all the elements are interrelated. I find it appealing due to the authors’ ability to apply theoretical material to ground their standpoint.
The second article is named Adolescent cyberbullying: A review of characteristics, prevention, and intervention strategies. It was posted in the journal Aggression and Violent Behavior in 2015 by R. Ang. The methods used in the text include firm reliance on secondary scientific research. The article has a logical organization of paragraphs, and it is easy to navigate throughout the whole paper. The author investigates adolescent cyber violence and thinks of it in terms of adults’ tendency to be involved in high-risk behaviors (Ang, 2015). While explaining the point of view, the author uses different variables associated with cyberbullying and parent-adult behavior to establish the relation between them. In the climax part of the article, the author suggests the strategies for better protection of adolescents online. I found this article quite convincing due to the strong scientific base, the author’s ability to analyze the dependence between the variables, and present the guidelines for the issue which were presented in an understandable manner.
The third article is entitled Cyberbullying prevention and intervention efforts: current knowledge and future direction and was issued in the Canadian Journal of Psychiatry in 2016 by D. Espelageand J. Hong. The methodology comprises the implementation of scientific articles that include results of surveys and experiments and theoretical underpinnings. The structure of the material seems well organized as it contains the main elements. Though the introduction and the conclusion are missing, the reader can clearly understand that other paragraphs substitute these parts. The authors described the present situation concerning the spread of cyber harassment, explained the extant preventive methods, exemplified the efficacy of school-based cyberbulextentinterventions, and expressed their attitude towards future prevention programs. According to Espelageand and Hong (2016), future researches must attract health care workers to prevent long-term health consequences. Thus, I consider this article relevant as it gives much information to reflect upon and has strong scientific underpinnings.
The fourth article stands under the title Out of the beta phase: Obstacles, challenges, and promising paths in the study of cyber criminology. The paper was issued in 2015 in the International Journal of Cyber Criminology by B. Diamond and M. Bachmann. The article’s organization follows the standards of a scientific article outline; therefore, one may orientate well throughout the paper. The methodology implemented relates to the second type of research, which is based on using extant scientific evidence. The article provides an overview of the present state of cyber criminology and views it from the aspects of teaching, research, and theory. The author suggested that there are still not enough pieces of evidence concerning the behavioral side behind cyber violence. In my opinion, this article is decent as it vividly discloses the study of cyber criminology and significantly explained why cyberbullying will be the main focus of it.
The fifth article is called the Effects of the cyberbullying prevention program media heroes (Medienhelden) on traditional bullying. The paper was published in the journal named Aggressive Behavior in 2016 by several authors: E. Chaux, A. Velásque, A. Schultze-Krumbholz, and H. Scheithauer. The authors used the methods of pretest–post-test quantitative experimental evaluation of the program, and to underpin the results, they use the theoretical base. The paper’s structure is well organized and comprises additional elements for the experiment part. The study focuses on analyzing the spillover effects of the cyber violence preventive programs named Media Heroes on conventional bullying. This prevention program aims to promote empathy, awareness of risks and their repercussions, and strategies that would help to defend the victims. In my opinion, this article may be an excellent example of a research work that other researchers may use to support their evidence.
Ang, R. P. (2015). Adolescent cyberbullying: A review of characteristics, prevention, and intervention strategies. Aggression and Violent Behavior, 25, 35–42. doi:10.1016/j.avb.2015.07.011
Espelage, D. L., & Hong, J. S. (2016). Cyberbullying Prevention and Intervention Efforts: Current Knowledge and Future Directions. The Canadian Journal of Psychiatry, 62 , 6, 374–380. doi:10.1177/0706743716684793
Chaux, E., Velásquez, A. M., Schultze-Krumbholz, A., & Scheithauer, H. (2016). Effects of the cyberbullying prevention program media heroes (Medienhelden) on traditional bullying . Aggressive Behavior, 42(2), 157–165. doi:10.1002/ab.21637
Diamond, B., & Bachmann, M. (2015). Out of the beta phase: obstacles, challenges, and promising paths in the study of cyber criminology. International Journal of Cyber Criminology , 9, 1, 24–34.
Peterson, J., & Densley, J. (2017). Cyber violence: What do we know and where do we go from here? Aggression and Violent Behavior, 34, 193-200.
Cite this paper
- Chicago (N-B)
- Chicago (A-D)
StudyCorgi. (2022, February 2). Cyber Violence: Structures and Effectiveness. https://studycorgi.com/cyber-violence-structures-and-effectiveness/
"Cyber Violence: Structures and Effectiveness." StudyCorgi , 2 Feb. 2022, studycorgi.com/cyber-violence-structures-and-effectiveness/.
StudyCorgi . (2022) 'Cyber Violence: Structures and Effectiveness'. 2 February.
1. StudyCorgi . "Cyber Violence: Structures and Effectiveness." February 2, 2022. https://studycorgi.com/cyber-violence-structures-and-effectiveness/.
Bibliography
StudyCorgi . "Cyber Violence: Structures and Effectiveness." February 2, 2022. https://studycorgi.com/cyber-violence-structures-and-effectiveness/.
StudyCorgi . 2022. "Cyber Violence: Structures and Effectiveness." February 2, 2022. https://studycorgi.com/cyber-violence-structures-and-effectiveness/.
This paper, “Cyber Violence: Structures and Effectiveness”, was written and voluntary submitted to our free essay database by a straight-A student. Please ensure you properly reference the paper if you're using it to write your assignment.
Before publication, the StudyCorgi editorial team proofread and checked the paper to make sure it meets the highest standards in terms of grammar, punctuation, style, fact accuracy, copyright issues, and inclusive language. Last updated: October 30, 2022 .
If you are the author of this paper and no longer wish to have it published on StudyCorgi, request the removal . Please use the “ Donate your paper ” form to submit an essay.
Our websites may use cookies to personalize and enhance your experience. By continuing without changing your cookie settings, you agree to this collection. For more information, please see our University Websites Privacy Notice .
UConn Today
- School and College News
- Arts & Culture
- Community Impact
- Entrepreneurship
- Health & Well-Being
- Research & Discovery
- UConn Health
- University Life
- UConn Voices
- University News
April 19, 2021 | Caitlin Elsaesser, Assistant Professor of Social Work
How Social Media Turns Online Arguments Between Teens Into Real-World Violence
Social media isn’t just mirroring conflicts happening in schools and on streets – it’s triggering new ones

Common social media practices like commenting and tagging can exacerbate arguments among teens and in some cases lead to violence (Adobe Stock).
The deadly insurrection at the U.S. Capitol in January exposed the power of social media to influence real-world behavior and incite violence. But many adolescents, who spend more time on social media than all other age groups, have known this for years.
“On social media, when you argue, something so small can turn into something so big so fast,” said Justin, a 17-year-old living in Hartford, during one of my research focus groups. (The participants’ names have been changed in this article to protect their identities.)
For the last three years, I have studied how and why social media triggers and accelerates offline violence . In my research , conducted in partnership with Hartford-based peace initiative COMPASS Youth Collaborative , we interviewed dozens of young people aged 12-19 in 2018. Their responses made clear that social media is not a neutral communication platform.
In other words, social media isn’t just mirroring conflicts happening in schools and on streets – it’s intensifying and triggering new conflicts. And for young people who live in disenfranchised urban neighborhoods, where firearms can be readily available, this dynamic can be deadly.
Internet Banging
It can result in a phenomenon that researchers at Columbia University have coined “internet banging.” Distinct from cyberbullying, internet banging involves taunts, disses, and arguments on social media between people in rival crews, cliques, or gangs. These exchanges can include comments, images, and videos that lead to physical fights, shootings and, in the worst cases, death .
It is estimated that the typical U.S. teen uses screen media more than seven hours daily, with the average teenager daily using three different forms of social media. Films such as “ The Social Dilemma ” underscore that social media companies create addictive platforms by design, using features such as unlimited scrolling and push notifications to keep users endlessly engaged.
According to the young people we interviewed, four social media features in particular escalate conflicts: comments, livestreaming, picture/video sharing, and tagging.
Comments and Livestreams
The feature most frequently implicated in social media conflicts, according to our research with adolescents, was comments. Roughly 80% of the incidents they described involved comments, which allow social media users to respond publicly to content posted by others.
Taylor, 17, described how comments allow people outside her friend group to “hype up” online conflicts: “On Facebook if I have an argument, it would be mostly the outsiders that’ll be hypin’ us up … ‘Cause the argument could have been done, but you got outsiders being like, ‘Oh, she gonna beat you up.’”
Meanwhile, livestreaming can quickly attract a large audience to watch conflict unfold in real time. Nearly a quarter of focus group participants implicated Facebook Live, for example, as a feature that escalates conflict.
Brianna, 17, shared an example in which her cousin told another girl to come to her house to fight on Facebook Live. “But mind you, if you got like 5,000 friends on Facebook, half of them watching … And most of them live probably in the area you live in. You got some people that’ll be like, ‘Oh, don’t fight.’ But in the majority, everybody would be like, ‘Oh, yeah, fight.’”
She went on to describe how three Facebook “friends” who were watching the livestream pulled up in cars in front of the house with cameras, ready to record and then post any fight.
Strategies to Stop Violence
Adolescents tend to define themselves through peer groups and are highly attuned to slights to their reputation. This makes it difficult to resolve social media conflicts peacefully. But the young people we spoke with are highly aware of how social media shapes the nature and intensity of conflicts.
A key finding of our work is that young people often try to avoid violence resulting from social media. Those in our study discussed four approaches to do so: avoidance, deescalation, reaching out for help and bystander intervention.
Avoidance involves exercising self-control to avoid conflict in the first place. As 17-year-old Diamond explained, “If I’m scrolling and I see something and I feel like I got to comment, I’ll go [to] comment and I’ll be like, ‘Hold up, wait, no.’ And I just start deleting it and tell myself … ‘No, mind my business.’”
Reaching out for support involves turning to peers, family or teachers for help. “When I see conflict, I screenshot it and send it to my friends in our group chat and laugh about it,” said Brianna, 16. But there’s a risk in this strategy, Brianna noted: “You could screenshot something on Snapchat, and it’ll tell the person that you screenshot it and they’ll be like, ‘Why are you screenshotting my stuff?’”
The deescalation strategy involves attempts by those involved to slow down a social media conflict as it happens. However, participants could not recount an example of this strategy working, given the intense pressure they experience from social media comments to protect one’s reputation.
They emphasized the bystander intervention strategy was most effective offline, away from the presence of an online audience. A friend might start a conversation offline with an involved friend to help strategize how to avoid future violence. Intervening online is often risky, according to participants, because the intervener can become a new target, ultimately making the conflict even bigger.
Peer Pressure Goes Viral
Young people are all too aware that the number of comments a post garners, or how many people are watching a livestream, can make it extremely difficult to pull out of a conflict once it starts.
Jasmine, a 15-year-old, shared, “On Facebook, there be so many comments, so many shares and I feel like the other person would feel like they would be a punk if they didn’t step, so they step even though they probably, deep down, really don’t want to step.”
There is a growing consensus across both major U.S. political parties that the large technology companies behind social media apps need to be more tightly regulated. Much of the concern has focused on the dangers of unregulated free speech .
But from the vantage point of the adolescents we spoke with in Hartford, conflict that occurs on social media is also a public health threat. They described multiple experiences of going online without the intention to fight, and getting pulled into an online conflict that ended up in gun violence. Many young people are improvising strategies to avoid social media conflict. I believe parents, teachers, policymakers and social media engineers ought to listen closely to what they are saying.
Originally published in The Conversation .
Recent Articles

April 26, 2024
New Alzheimer’s Treatment Available at UConn Health
Read the article

Marissa Salvo Named the 2024 School of Pharmacy Faculty Service Award Recipient

Mathew Chandy ’24, College of Liberal Arts and Sciences
Cyber Violence Essays
Essay on cyber violence, popular essay topics.
- American Dream
- Artificial Intelligence
- Black Lives Matter
- Bullying Essay
- Career Goals Essay
- Causes of the Civil War
- Child Abusing
- Civil Rights Movement
- Community Service
- Cultural Identity
- Cyber Bullying
- Death Penalty
- Depression Essay
- Domestic Violence
- Freedom of Speech
- Global Warming
- Gun Control
- Human Trafficking
- I Believe Essay
- Immigration
- Importance of Education
- Israel and Palestine Conflict
- Leadership Essay
- Legalizing Marijuanas
- Mental Health
- National Honor Society
- Police Brutality
- Pollution Essay
- Racism Essay
- Romeo and Juliet
- Same Sex Marriages
- Social Media
- The Great Gatsby
- The Yellow Wallpaper
- Time Management
- To Kill a Mockingbird
- Violent Video Games
- What Makes You Unique
- Why I Want to Be a Nurse
- Send us an e-mail
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 25 November 2022
Cyber violence caused by the disclosure of route information during the COVID-19 pandemic
- Ying Lian 1 ,
- Yueting Zhou 1 ,
- Xueying Lian 2 &
- Xuefan Dong ORCID: orcid.org/0000-0002-2318-4805 2 , 3
Humanities and Social Sciences Communications volume 9 , Article number: 417 ( 2022 ) Cite this article
2260 Accesses
4 Citations
1 Altmetric
Metrics details
- Cultural and media studies
- Science, technology and society
- Social policy
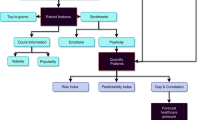
Disclosure of patients’ travel route information by government departments has been an effective and indispensable pandemic prevention and control measure during the COVID-19 pandemic. However, this measure may make patients susceptible to cyber violence (CV). We selected 13 real cases that occurred in China during the COVID-19 pandemic for analysis. We identified several characteristics that commonly appeared due to route information, such as rumors about and moral condemnation of patients, and determined that patients who are the first locally confirmed cases of a particular wave of the pandemic are more likely to be the victims of CV. We then analyzed and compared six real cases using data mining and network analysis approaches. We found that disclosing travel route information increases the risk of exposing patients to CV, especially those who violate infection prevention regulations. In terms of disseminating information, we found that mainstream media and influential we-media play an essential role. Based on the findings, we summarized the formation mechanism of route information disclosure-caused CV and proposed three practical suggestions—namely, promote the publicity of the media field with the help of mainstream media and influential we-media, optimize the route information collection and disclosure system, and ease public anxiety about the COVID-19 pandemic. To our knowledge, this study is one of the first to focus on CV on social media during the COVID-19 pandemic. We believe that our findings can help governments better carry out pandemic prevention and control measures on a global scale.
Similar content being viewed by others

Early warnings of COVID-19 outbreaks across Europe from social media
Government disclosure in influencing people’s behaviors during a public health emergency
In.To. COVID-19 socio-epidemiological co-causality
Introduction, cyber violence (cv).
Although the Internet has provided numerous advantages to the world, such as a convenient communication channel, rapid knowledge sharing, and a transparent public engagement process, some disadvantages have emerged, of which CV is a representative example. Definitions of CV vary but generally refer to internet-related behaviors that espouse violence or use language in a calculated manner to inflame passions and eventually achieve mass emotional catharsis (Peterson and Densley, 2017 ). According to several investigations, the prevalence of CV has reached a considerable level worldwide (Barlett et al., 2012 ; Cava et al., 2020 ; Jones et al., 2013 ; Peskin et al., 2017 ), especially among youths like students (Saleem et al., 2021 ). A national telephone survey of about 4500 youths aged 10–17 in 2000, 2005, and 2010 in the US reported a significant increase in the rate of online harassment between 2000 and 2010 (Jones et al., 2013 ). The survey also found that girls are more likely to experience CV, especially cyber dating violence. According to Hinduja et al., 20% of a random sample of 4441 students aged between 10 and 18 years experienced CV (Hinduja et al., 2013 ). In general, CV is much easier to perpetrate than traditional (or offline) violence because its carrier, the Internet, transcends geographic and temporal boundaries (Cava et al., 2020 ). However, CV can also generate the same adverse effects on victims as traditional violence, including but not limited to fear and other distressing emotions (Casas et al., 2013 ; Peterson and Densley, 2017 ) and even suicidal behavior. For example, a famous Korean actress committed suicide in October 2008 because of CV (Chiyohara, 2010 ).
CV and social media
Many studies have demonstrated a relatively close relationship between CV and social media. For instance, Patton et al. (Patton et al., 2014 ) and Nagle (Nagle, 2018 ) systematically reviewed related studies and found significant positive correlations between CV and social media. Moreover, Ge found that CV frequently occurred on social networking sites like Twitter, Facebook, and Weibo (Ge, 2020 ). He further explained that users’ moral sensitivity could be reduced by social media, with CV constituting one of its main behavioral consequences. Ephraim found that CV against women and girls is becoming increasingly visible and prevalent, mainly contributing to increased social media use (Ephraim, 2013 ). Jane found that gendered CV on social media is becoming worse. Still, social media platform managers and policymakers fail to effectively address and prevent this problem, causing feminist digilantism to be more visible and forceful (Jane, 2017 ). Craig et al. conducted a cross-national study of 180,919 youths aged 11 to 15 from 42 countries to explore the relationship between cyberbullying and social media use (Craig et al., 2020 ). The results showed that the amount of time spent on social media was significantly correlated with the likelihood of being victimized by cyberbullying.
CV in the COVID-19 pandemic
Since December 2019, COVID-19 has spread worldwide and has become an ongoing global health crisis. According to Tsao et al., as of January 2021, there had been more than 95 million cases of COVID-19, with about 2 million deaths (Tsao et al., 2021 ). In addition to its physical damage to human beings, COVID-19 has had adverse psychological impacts, of which CV has been the primary concern in recently published articles (Alsawalqa, 2021 ; Barlett et al., 2021 ; Barlett et al., 2021 ; Han et al., 2021 ; Jain et al., 2020 ; Li et al., 2020 ; Shirish et al., 2021 ; Yang, 2021 ). Most studies have posited a positive relationship between cyberbullying and the COVID-19 pandemic. For instance, Barlett et al. found that the prevalence of CV has significantly increased during the pandemic (Barlett et al., 2021 ). Han et al. proposed that the loneliness and isolation caused by the pandemic have stimulated CV behavior (Han et al., 2021 ). Yang conducted a web-based national survey of 5,608 individuals in China to investigate the correlation between CV, depression, and psychological coping strategies during the peak of the pandemic (Yang, 2021 ). The results showed that cyberbullying played a mediating role between the other two aspects.
There is no doubt that the government, as the leader and manager of society, should work to eliminate CV as much as possible, especially during major emergencies, such as the COVID-19 pandemic. However, one particular manifestation of CV during the pandemic has proven challenging to thwart—namely, route information disclosure-caused CV (RIDCCV). In this study, we defined RIDCCV as the CV caused by route information disclosure by the government. Generally, route information disclosure of infected patients is an effective tool for pandemic prevention and control, one which has been implemented by many countries, such as China and Japan. Route information disclosure is typically more frequent and common because national pandemic prevention and control measures tend to be normalized, and self-prevention consciousness can become fatigued (Morgul et al., 2021 ). However, according to previous studies, the personal information of infected individuals, including but not limited to their gender, age, place of residence, and recent travel route, is usually disclosed by the government through social media and official government websites or reposts that are available to the public to halt the spread of infection (Hu et al., 2020 ). These publication channels enable netizens to obtain the personal information of infected individuals much more quickly. They also create a platform that increases the risk of information leakage and CV to a large extent. Moreover, in most cases, grassroots staff in government departments are responsible for the route information disclosure of infected people if non-standard operations exist, such as unintentional dissemination of personal information, illegal sale of personal information, and insufficient removal of sensitive information before disclosure, information leakage, and CV would be easily triggered. Thus, although route information disclosure is of great significance in pandemic prevention and control, the probability of causing citizen information leakage and CV has increased.
Indeed, some existing studies have proposed that the information disclosure of infected people could lead them to suffer from abuse and discrimination during pandemics, such as COVID-19 (Deng and Feng, 2021 ; Di Trani et al., 2020 ; Jain et al., 2020 ; Liu et al., 2021 ). Liu et al. explained that this phenomenon is primarily caused by the perceived threat posed by infected individuals, which is a rapid and natural psychological response to emerging infectious diseases (Liu et al., 2021 ). In this view, the government can inadvertently stimulate CV. In addition, social media plays a promotional role in this process. In particular, social media allows people to post cyberbullying content with a low risk of exposing their identity (Vos et al., 2018 ). To date, few studies have focused on route information disclosure during the COVID-19 pandemic. Among them, Jung et al. (Jung et al., 2020 ) and Kim (Kim, 2021 ) focused on the privacy risks caused by the information disclosure practices of government departments in South Korea, in which route data were considered. However, they did not discuss any issues pertaining to CV.
The post-pandemic era is approaching, and the route information disclosure practices of governments are becoming increasingly normalized and frequent, which means that more RIDCCV may be aroused. There is no doubt that it is necessary to disclose the personal route information of confirmed patients and their close contacts to improve the effectiveness of epidemic prevention and control measures and interrupt the transmission of infectious diseases, such as COVID-19. Thus, all individuals have an obligation to cooperate with the epidemic prevention department by submitting the necessary aspects of their private lives. However, this does not mean unrestricted disclosure and dissemination of personal information. The excessive disclosure of personal information in the public sphere violates the right to privacy and affects everyday life (Mutimukwe et al., 2020 ), but it also negatively impacts the credibility of government agencies and hinders the normal progress of epidemic prevention and control (Jung et al., 2020 ).
Thus, it is of great significance to analyze real cases of RIDCCV and identify some valuable solutions to diminish or outright eliminate its occurrence, which has important implications for both current and future efforts to conduct better social governance during public emergencies, such as pandemics. We claim that, although reducing personal mobility is essential for preventing the spread of infectious diseases, each individual has the right to engage in outdoor activities without breaking the law. In addition, we assert that the anxiety caused by the COVID-19 pandemic is not a justification for CV.
This study aimed to address knowledge deficiencies concerning RIDCCV on social media during the COVID-19 pandemic. To achieve this goal, we first selected 13 representative cases of RIDCCV to identify typical characteristics. Six of these cases were then further analyzed. In particular, we collected and analyzed social media–based data about these six cases using data mining and network analysis approaches. The primary difference between the six cases is that three involved infected people who violated the Chinese epidemic prevention law. The other three were people who did not follow Chinese epidemic prevention recommendations. Specifically, this study sought to answer the following three research questions:
RQ1: What were the social media contents of the six cases of RIDCCV?
RQ2: Were there any differences between these six cases regarding the social media contents of RIDCCV?
RQ3: Who plays a vital role in disseminating information on social media?
The remainder of this paper is organized as follows. In section “Cases”, the 13 cases are described. Section “Methods” demonstrates the structure of the applied methods, including the data collection and mining approaches. Section “Results” presents the research results. Finally, section “Discussion and conclusions” presents our primary findings and discussions about the formation mechanism of RIDCCV in COVID-19 and proposes several practical recommendations.
On December 8, 2020, the government of the Pidu District in Chengdu, Sichuan Province, officially announced that a woman, the granddaughter of two, was diagnosed with COVID-19. Her route information was also published, indicating that she had ventured out to many crowded public places before her diagnosis, including, but not limited to, a park and several bars. In addition, it should be noted that she was not required to isolate, meaning that she did not violate any epidemic prevention regulations. However, many netizens believed that her actions had placed them in danger. Thus, her personal information, such as her name, ID number, and family address, was exposed on the Internet. In the early morning of December 8, more people participated in the discussion of this event, the content of which was pervaded by a litany of negative opinions, such as speculation about the girl’s private life and insulting personal attacks.
A woman who returned from South Korea to Shenyang, Liaoning Province, on November 29, 2020, was asked to isolate herself at home. She was diagnosed with novel coronavirus pneumonia on December 23, 2020. On December 24, 2020, her route information following her return was announced by the Shenyang Health Commission, indicating that she did not fully comply with the quarantine regulations for inbound personnel in China. Specifically, during the isolation period, she went out to some crowded places despite having developed a fever. Because of her actions, 21 people were infected with COVID-19, and Shenyang began to carry out large-scale screening to detect potential infected cases. Thus, her personal information, such as her name, ID number, mobile phone number, and address, was exposed on the Internet. She and her family were cursed and abused by netizens on social media.
On August 4, 2021, government authorities disclosed the route information of a confirmed case of COVID-19, who had returned from Hainan Province to Beijing. According to previous media reports, the subject was a male teacher at the Central Academy of Fine Arts. They took China Southern Airlines flight CZ8804 from Sanya Airport to Beijing Daxing Airport on July 30. After he was diagnosed, the netizens speculated that he had gone to Sanya with his wife’s girlfriend and that she was also isolated. The rumor spread through the WeChat groups, resulting in CV against the man, which affected him, and the families involved.
On the evening of August 1, 2021, the Wuhan Economic Development Zone inspected the residents of a critical area through a tourist group in Huai’an, Jiangsu Province, and found that a migrant worker at a construction site had intersected with the activity itinerary of a tourist group in Huai’an while waiting for the train at the Jingzhou high-speed rail station on July 27. He underwent viral nucleic acid testing (NAT) on the morning of August 2, and the result was positive. His route information showed that he had traveled to many places in Wuhan on the 27th and 28th, and that two women were close contacts. Subsequently, netizens perpetuated rumors that the two women were the man’s “ex-girlfriend” and “current girlfriend,” and their personal information, such as ID numbers and telephone numbers, was exposed on the Internet. On August 5, the incident was further fermented, and negative opinions increased among netizens’ comments, such as speculation about private lives and other malicious remarks about the people involved.
On August 1, 2021, Shangqiu reported a new, locally confirmed COVID-19 case. The patient was hospitalized at Zhengzhou Sixth Hospital because her family was at high risk for COVID-19. The patient was the first in Shangqiu; after her diagnosis, she fully complied with the epidemic prevention and quarantine regulations. However, subsequently, her personal information was exposed on the Internet. She was rumored to be seriously ill or dead, and netizens further rumored that she had had an affair, which caused her online abuse that adversely affected her daily life.
A person who returned to Putian from Singapore was suspected to be the source of a wave of pandemic cases in Fujian. He returned on August 4, 2021, and fully complied with the epidemic prevention and control regulations during the quarantine period. Nine NAT results were negative, and one serum test was negative. He was diagnosed on September 10, but could not explain how he had become infected. After his route information was published on September 12, he received a large number of harassing phone calls, and some netizens spread rumors about his private life. This harassment seriously affected his daily life and made him worry about whether his family would also be affected.
On September 21, 2021, the Second People’s Hospital of Bayan County in Heilongjiang province reported a new case of a positive COVID-19 infection. The next day, the patient’s route information showed that she had taken the high-speed rail from Ji’an City to Nanchang and then flew from Nanchang to Harbin. After arriving in Harbin, she went to multiple restaurants and entertainment venues and played board games for three consecutive days. After her epidemiological investigation report was issued, her personal information, including her name, her partner’s name, and a detailed address, was exposed on the Internet. After that, the patient was accused by many netizens and even insulted online. In addition, she received moral criticism via CV because many netizens thought she should not have visited public places during the COVID-19 pandemic.
The government department disclosed the route information of two people with confirmed cases of COVID-19 who had returned from the Philippines to Harbin. They were two of the three first locally confirmed cases of a wave of the pandemic in Harbin. They had previously worked abroad and returned to China on August 3; after their return, they did not violate any epidemic prevention regulations, and their NAT results were negative. After the release of the quarantine on September 1, they went to multiple restaurants and entertainment venues. One of the persons was in close contact with the person described in Case 7 and had played live-action role laying (LARP) games with her. On September 21, Harbin Infectious Disease Hospital reported that the two were diagnosed as positive for COVID-19. After the government department disclosed their route information, the close contact of Case 7 suffered CV. His name and other personal information were leaked. Some netizens expressed dissatisfaction with his return to China, stating that they should keep away from crowded public places after their return during the COVID-19 pandemic.
On October 15, an elderly couple from Shanghai reportedly had abnormal NAT results in Jiayuguan City while traveling. However, they left for Xi’an alone after being informed not to leave. As of 17:30 on October 15, Jiayuguan City carried out an epidemiological investigation, NAT, personnel control, and environmental sanitizing at the places and with the contacts involved in the couple’s trip to detect potential infected cases. Then, on October 17, they were both confirmed to be infected, and the government disclosed their route information. CV occurred because some netizens thought they should not have left for Xi’an alone. They were condemned and targeted with personal abuse online. However, on October 18, the reporter covering the case interviewed the couple and the Gansu Provincial Health Commission staff exclusively and found that the statement “left by themselves” was untrue. The couple did not travel without authorization after testing positive and did not violate epidemic prevention and control regulations during the period. After this revelation, some netizens expressed sympathy for the two elderly people. However, other netizens noticed that when the two were in Xi’an, after learning that their NAT results were abnormal and before the NAT retest results came out, they still went to other places in Xi’an. Therefore, some netizens condemned this behavior, and at the same time, there were unfavorable comments on regional epidemic prevention and control.
A male in Wulian County, Rizhao, Shandong Province, tested positive for COVID-19 via NAT on the evening of October 25 and had a history of living in Yinchuan City, Ningxia, from October 15 to 18. On October 26, Wulian County officials held a press conference on COVID-19. After the subject had arrived in Rizhao on the 18th, he tested negative on the 19th, and then he was active mainly near his work unit and residential area. On October 25, he went to the rehabilitation hospital and was later diagnosed. After the Chinese Center for Disease Control and Prevention announced the case, some netizens said that he had concealed the trip. However, the official did not confirm the matter. His ID and telephone numbers were leaked, and he was attacked by public opinion.
On October 10, a tour guide took a team to the Ceke port (where there had been a previous epidemic) for a short visit. The head of the travel agency where the guide worked said that after ending the trip to Ejina Banner, Inner Mongolia, the tour guide was infected with COVID-19 while taking another team in Gannan Prefecture, Gansu Province. The tour group colleagues and tourists in close contact with him tested negative. After the tour guide was diagnosed, his information was leaked, and he was targeted with personal abuse online.
On October 13, a male subject returned to Shijiazhuang from Ejina Banner, Inner Mongolia, where the epidemic already existed. He had lived and worked in Ejin Naqi from September 26 to October 12, but he did not report his travel as soon as he returned. On October 22, after the man learned that people with a history of travel in medium- and high-risk areas needed to report, he took the initiative to report his trip without concealing his residence history. On November 1, he was notified of a positive COVID-19 diagnosis. After his route information was disclosed, he was condemned and received personal abuse online because his failure to report in time triggered small disease outbreaks in Shenze, Xinji, and other places.
On November 1, the Fourth People’s Hospital of Chengdu reported that a male subject had a positive NAT for the new coronavirus. The Municipal Center for Disease Control and Prevention confirmed this case. The man traveled to Xi’an, Yinchuan, Lanzhou, and Chongqing on a business trip from October 8 to 27 and drove back to Chengdu on the 28th. During the business trip, he had symptoms such as dizziness and chills, but after visiting the doctor on the 27th, he obtained a negative NAT report. He did not report to the community after his return on the 28th. The next day, he developed fever symptoms, but he denied any travel history in medium- and high-risk areas in the country at the time of treatment. After his route information was disclosed, he became the target of CV because of violations of epidemic prevention and control regulations. He was accused, insulted, and personally attacked by netizens.
Data collection
First, we identified 13 representative cases of RIDCCV that occurred between November 2020 and November 2021 in China by devoting continuous attention to online posts related to RIDCCV on social media. Then, we employed three doctoral students with research experience in CV to ascertain the whole story of each case by manually searching relevant information on the Internet and manually confirming whether the following six features existed:
The person violated epidemic prevention and control regulations.
The person was the first locally confirmed case of a wave of the pandemic.
Personal information was leaked (name, telephone, etc.).
The person was nicknamed by people on social media.
There were rumors.
There was moral criticism.
Six cases were then considered for further analysis: Case 1, Case 2, Case 4, Case 7, Case 9, and Case 13. We chose these six cases for analysis because they generated more online posts than the other cases. In addition, they can be classified into two markedly different groups: people who had violated epidemic prevention and control regulations (Case 2, Case 9, and Case 13) and people who did not (Case 1, Case 4, and Case 7). This difference could, to a large extent, improve the richness of the data we collected from social media. In other words, conducting a comprehensive comparative analysis based on public opinions on social media concerning these cases was possible. Moreover, to eliminate the ambiguity caused by their names, we renamed Case 1, Case 2, Case 4, Case 7, Case 9, and Case 13 as Research Case 1 (RCase 1), Research Case 2 (RCase 2), Research Case 3 (RCase 3), Research Case 4 (RCase 4), Research Case 5 (RCase 5), and Research Case 6 (RCase 6), respectively.
The social media platform Weibo (Chinese Twitter) was utilized to obtain data regarding the RIDCCV on the six cases during the COVID-19 pandemic. According to Li et al. ( 2020 ), Weibo has been one of the leading platforms employed by the Chinese government to disclose COVID-19-related information. Many Chinese government agencies have created their own official accounts on Weibo. Weibo has been deployed as a data source by many studies focusing on issues in China (Tao and Su, 2021 ; Wu et al., 2021 ). Octopus, a mature web crawler tool, was used to collect data from Weibo, as it has shown great effectiveness in previous studies (Li et al., 2021 ; Liu and Hu, 2019 ). In addition, it should be noted that the data collection process was implemented daily to acquire the maximum amount of data. The data were collected as follows:
For RCase 1, we collected the original posts containing the keywords “girl,” “COVID-19,” and “Pixian County” on Weibo and their associated comments from December 7 to December 16, 2020, yielding a total of 63,719 online posts.
For RCase 2, we collected original posts containing the keywords “old lady Yin,” “COVID-19,” and “Shenyang” on Weibo and their associated comments from December 23, 2020 to January 18, 2021, which yielded a total of 47,913 online posts.
For RCase 3, original posts containing the keywords “Wuhan” and “COVID-19” on Weibo and their associated comments from August 5 to 11, 2021 were collected, which yielded a total of 13,840 online posts.
For RCase 4, the applied keywords were “Harbin,” “COVID-19,” and “LARP Games,” and the collection period was between September 21 and September 29, 2021, which yielded 17,037 online posts.
For RCase 5, we collected original posts containing the keywords “Xi’an” and “COVID-19” on Weibo and their associated comments from October 17 to 24, 2021, which yielded 21,896 online posts.
For RCase 6, original posts containing the keywords “Chengdu” and “COVID-19” on Weibo and their associated comments from November 5 to 12, 2021 were collected, yielding a total of 13,114 online posts.
The collected data included user names, posting times, and the content of the posts. We then used the data-cleaning function of the Statistical Package for the Social Sciences (SPSS) version 25.0 (IBM Corp., Armonk, NY) to delete incomplete data. Invalid data, such as advertisements, were manually removed. Finally, the amount of remaining data related to the six cases comprised 62,888, 45,538, 12,558, 15817, 21,073, and 12,291 items, respectively.
Data mining methods
To answer the first research question— What were the social media content of the six cases of RIDCCV?— text mining analysis was performed on collected online posts related to six RCases via natural-language processing techniques. The following information demonstrates the methods used in this research.
Sentiment analysis
Sentiment analysis was applied to assess how the public felt about the topic. In this study, we employed bi-directional long short-term memory (Bi-LSTM), a commonly applied deep learning algorithm in sentiment analysis. Bi-LSTM is composed of a forward LSTM and a backward LSTM and has demonstrated optimal performance in processing Chinese microblogging data for sentiment analysis (Dou et al., 2021 ; Ling et al., 2020 ). In addition, the R package of Jieba with the basic lexicon of Sougou Pinyin was used to finish the word segmentation task. Word2Vec, a word vector training tool launched by Google, was used for word embedding. For the Bi-LSTM, the hidden size of each LSTM unit was set at 300, and the learning rate was set at 0.01 for optimization. We used a dataset containing 120,000 online posts collected from Weibo to train the model, half labeled as positive and half labeled as negative. These data are available at https://qcsdn.com/q/a/49489.html . We then used the obtained classifier to identify the sentiment tendencies in our collected online posts.
To test the overall performance of the results, three students were employed to manually check the accuracy of the sentiment classification of 5,000 online posts. Only those considered correct by all three students were classified in the correct group. The final average accuracy rate of the 5,000 tested data for each RCase was 89.77%, indicating an acceptable margin of error. Thus, the sentiment tendency results were highly reliable.
Topic clustering
Many topic clustering algorithms have been proposed by existing studies, of which Latent Dirichlet Allocation (LDA) is one of the most commonly applied models. LDA has been employed in various areas, such as politics, technology, economy, management, and transportation. Inspired by these studies, this study used LDA to implement text analysis for topic clustering regarding the collected data. The basis of LDA refers to the statistical correlation of words presented in researched documents without considering word order. For parameter settings, the k-dimensional topic smoothing parameter and the k-dimensional word smoothing parameter are set as 0.1 and 0.01, respectively (Xu et al., 2018 ). Additionally, the trial-and-error method was used to determine the optimum value of the number of topics. According to Kaplan and Vakili ( 2015 ), although this method spends much time repeating the clustering procedures with varying numbers of topics, its accuracy can be guaranteed to a large extent. Before carrying out topic clustering, we used Jieba to segment the collected posts by words. The term frequency-inverse document frequency (TF-IDG) method was applied to measure the weight of each characteristic word in each post. TF-IDF is a numerical statistic method for assessing the importance of each word in particular documents, which has been commonly applied by previous studies in information retrieval and (Kim et al., 2019 ; Mee et al., 2021 ). The calculation method of TF-IDF is displayed as formula (1).
In formula (1), W ij , TF ij , and ID ij represent the weight, word frequency, and reverse file frequency of word i in document j , respectively. N is the total number of documents, and DF j is the total number of documents containing the word i .
Social network analysis
To investigate the role played by different users in disseminating information related to RIDCCV on social media, the social network analysis method was applied. In particular, based on the collected data, we constructed the network spread of the six cases based on the original posts and comments. Each node represents a user, and each edge measures a commenting relation. The constructed networks were both weighted-directed networks, in which the weight was measured as the number of commenting relations. Then, we carried out a weighted PageRank analysis using the method proposed by Zhang to further explore the importance of each user in the spreading networks (Zhang, 2017 ).
In addition, to provide a more comprehensive and detailed picture of the user, we conducted a classification analysis. According to existing studies focusing on information spread, mainstream media and we-media were commonly considered and compared (Luqiu et al., 2019 ; Wang, 2021 ; Wu, 2018 ; Xu et al., 2018 ). Mainstream media is the media that has an enormous influence, reaches a large mainstream audience, guides public opinion, and generates a strong social influence. In comparison, we-media is a new type of media formed based on the development of microblog technology. In general, there are two different arguments regarding the differences between mainstream media and we-media. One is that mainstream media equals traditional media, such as online news, television, and major websites, while we-media equals microblogs, such as Twitter and Weibo (Peng et al., 2015 ; Wang, 2021 ). The other argument is that mainstream media equals official media, while we-media can be viewed as non-official media created by individuals or non-official organizations (Al-Zaman and Noman, 2021 ; Wu, 2018 ). In this study, the latter classification criteria were employed. Furthermore, following Dong and Lian ( 2022 ), we used the industrial category, an attribute of user profiles on Weibo, to determine whether a given user was official or not. In particular, Dong and Lian ( 2022 ) identified 70 official categories, such as government–emergency management, newspaper–official newspaper, government–technology, and government–judicial administration.
We also considered the influence of we-media based on their number of followers. Users were classified into four groups according to the profiles displayed on the homepage of each user on Weibo: mainstream/official media, influential media, we-media, and normal users. We-media users who had more than 300,000 followers were classified into the influential we-media group. Until now, there have been no accurate criteria for judging whether a user was an influential user. Although the number of followers proved to be an essential indicator in many previous studies (Ge, 2020 ; Luqiu et al., 2019 ; Shi et al., 2021 ), the aim of this study was not to accurately identify influential users but rather to provide a relatively detailed understanding of the role of we-media in spreading information on social media. Thus, our classification criteria were largely rational.
Characteristics of 13 RIDCCV cases
The coding results regarding the characteristics of the 13 selected RIDCCV cases are shown in Table 1 , with the summarized results shown in Tables 2 and 3 . The CV victims in 11 of the cases represent the first locally confirmed case of a wave of the pandemic, and personal information was leaked (11 of 13 cases). In addition, some cases demonstrated the existence of moral criticism and rumors caused by disclosing the subject’s travel route information.
Text mining results for six RCases
Figure 1 displays the content analysis results of RCase 1. We extracted the top 100 keywords based on the ranking results of the TF-IDF values. The figure shows that some general words, such as “Come on” and “Chengdu,” also had high TF-IDF values. In addition, it is interesting to note that “Bar” had a considerably high TF-IDF value, which reflects how people seemed to pay more attention to the fact that the girl in RCase 1 visited several bars. Indeed, debates about whether “Should the girl go to bars?” represented a new derived topic in RCase 1. These debates occurred partly because, in traditional Chinese conceptions, young girls visiting bars is discouraged, although the younger generation in China generally disagrees with this view. For instance, someone asked, “Why do so many people think going to bars means bad children?” Regarding the sentiment analysis results, the proportion of negative and positive comments was 72.55% and 27.45%, respectively. Five topics with a negative tendency and four with a positive tendency were extracted from the commenting data. Specifically, for the topics with a negative sentiment tendency, “Condemn the girl because she went to many crowded public places,” “Condemn cyber violence to the girl,” “Condemn people who created rumors and disclosed privacy information of the girl,” “Fears of disease outbreaks,” and “Worried that they could not go home for Spring Festival because of the disease” were obtained. In terms of topics with a positive sentiment tendency, “Express appreciation and salute to medical workers,” “Hope everyone can comply with prevention measures of the government,” “Hope the epidemic around the world will end soon,” and “Call upon government to reasonably publish route information of infected people” were identified.
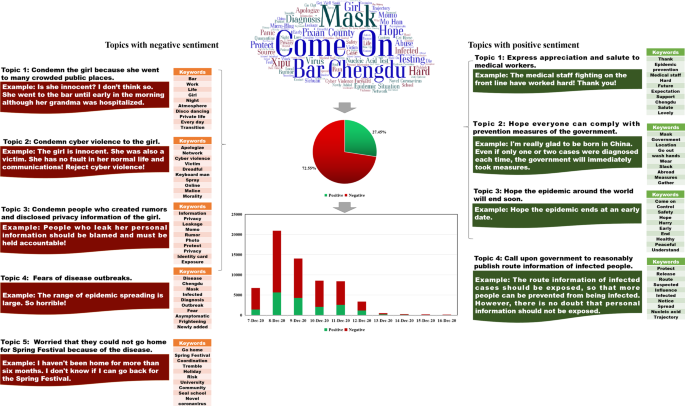
This figure shows the sentiment analysis and topic clustering results of RCase 1.
Figure 2 displays the content analysis results of RCase 2. Here, we also extracted the top 100 keywords according to the ranking results of the TF-IDF values. Similar to the results of Case 1, in addition to some general words, such as “Come on” and “Shenyang,” keywords with high TF-IDF values also included “Quarantine,” “Stoll,” “Home,” and “Hard.” This finding indicates that most people were concerned about the traveling behavior of the woman during quarantine. Concerning the sentiment analysis results, it can be noted that the proportion of negative and positive comments was 77.66% and 22.34%, respectively. Three topics with a negative tendency and three with a positive tendency were extracted from the commenting data. Specifically, for the topics with a negative sentiment tendency, “Condemn the woman,” “Fears of disease outbreaks,” and “Worried that they could not go home for New Year’s Day because of the disease” were obtained. In terms of topics with a positive sentiment tendency, “Salute medical workers,” “Praise the government,” and “Wish disease can end soon because of the prevention and control measures” were identified.
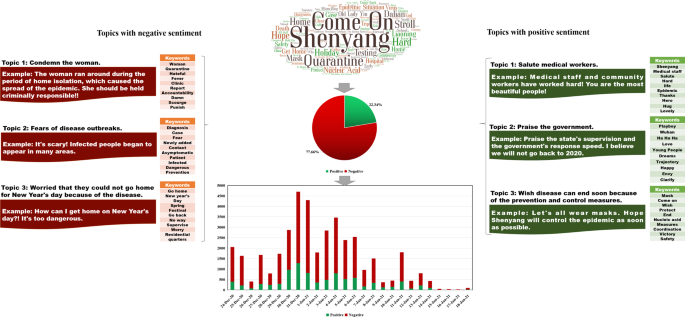
This figure shows the sentiment analysis and topic clustering results of RCase 2.
Figure 3 displays the content analysis results of RCase 3. Based on the TF-IDF values, we identified the top 100 keywords. In addition to some general words, such as “Wuhan” and “Come on,” the keywords “Playboy” (which relates to the specific story of this case), “Privacy,” and “Epidemiological Survey” (which are related to the leaks of personal information in the epidemiological survey announcement) had high TF-IDF values as well. Regarding the sentiment analysis results, the proportion of negative and positive comments was 62.54% and 37.46%, respectively. Moreover, a rapidly decreasing trend can be found in the number of online posts related to this case. For the topic clustering results, four topics with a negative tendency were identified: “Condemn the cyberviolence behavior,” “Condemn the personal information leakage,” “Condemn people who created rumors,” and “Fears of disease spreading.” In addition, three topics with a positive tendency were obtained, including “Salute medical workers,” “Praise the government for effective control,” and “Wish disease can end soon.”
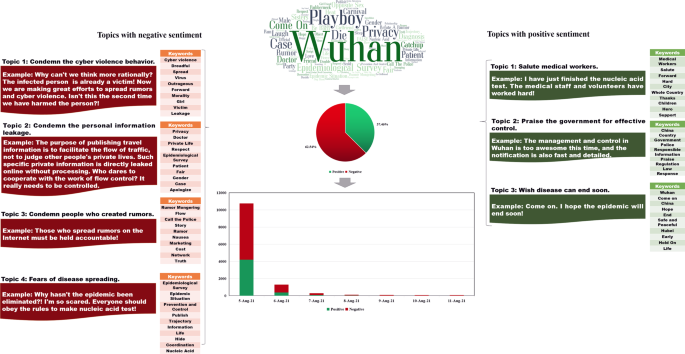
This figure shows the sentiment analysis and topic clustering results of RCase 3.
Figure 4 displays the content analysis results of RCase 4. We extracted the top 100 keywords according to the ranking results of the TF-IDF values, which shows that the keywords “Play,” “Quarantine,” “LARP Games,” and “Nucleic Acid” had high TF-IDF values. This finding indicates that most people were concerned that the infected person played LARP games for three consecutive days in Harbin, which caused many infections. Concerning the sentiment analysis results, it can be noted that the proportion of negative and positive comments was 85.66% and 14.34%, respectively. Three topics with a negative tendency and three with a positive tendency were extracted from the commenting data. In particular, for the topics with a negative sentiment tendency, “Worried that they could not go home,” “Condemn the cyberviolence behavior and personal information leakage,” and “Fear about the disease” were obtained. These topics are similar to those obtained in RCase 1 because both cases had similar timings, occurring close to holidays. In terms of topics with a positive sentiment tendency, we identified “Wish the disease will end as soon as possible,” “Salute medical workers,” and “Make fun of events and Harbin-related topics, such as LARP games and Spicy Hotchpotch.”
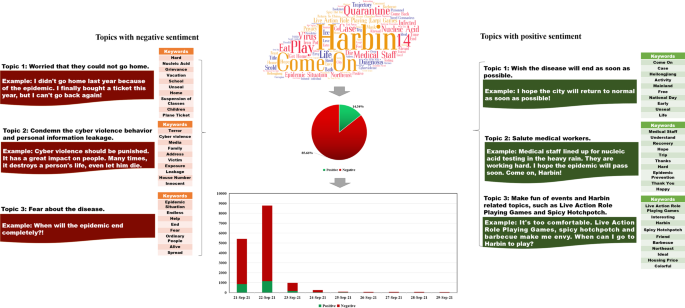
This figure shows the sentiment analysis and topic clustering results of RCase 4.
Figure 5 displays the content analysis results of RCase 5. The results regarding the top 100 keywords based on the TF-IDF values showed that except for some general keywords such as “Come On” and “Xi’An,” the keywords “Jiayuguan” (a famous scenic spot in Xi’an, China), “Nucleic Acid,” “Gansu,” “Abnormal,” and “Scold” had high TF-IDF values. Regarding the sentiment analysis results, 84.53% of the collected comments showed a negative sentiment tendency, and 15.47% showed a positive tendency. In addition, four negative topics were identified: “Condemn the couple because they violated epidemic prevention and control measures,” “Condemn the cyber violence behavior,” “Worried about the disease,” and “Accuse the government of loopholes in epidemic control and personal information leakage.” The topics with a positive sentiment tendency were “Hope the epidemic will end soon,” “Suggest the local government and scenic spots could improve the effectiveness of epidemic control and management,” and “Accept and understand the apology of the old couple.”
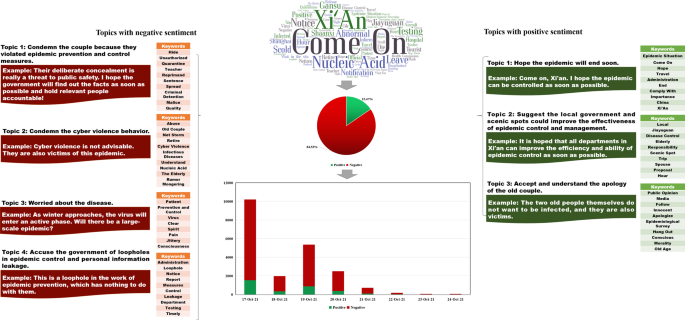
This figure shows the sentiment analysis and topic clustering results of RCase 5.
Figure 6 displays the content analysis results of RCase 6. According to the results, the keywords related to the place of occurrence and epidemic prevention and control have high TF-IDF values, including “Chengdu,” “Come On,” “Salute,” “Diagnosis,” “Hold On,” and “Mask.” For the sentiment analysis results, the proportion of negative and positive comments was 73.33% and 26.67%, respectively. In addition, three topics with a negative tendency and three with a positive tendency were extracted from the commenting data. Specifically, for the topics with a negative sentiment tendency, “Condemn the person and think he should be convicted,” “Worried that they could not go home during the Spring Festival,” and “Expressed panic about the epidemic and hoped to work at home” were obtained. Topics with a positive sentiment tendency were “Hope the epidemic will end soon and the world will get well,” “Praise the government for effective control measures,” and “Salute medical workers and volunteers in communities.”
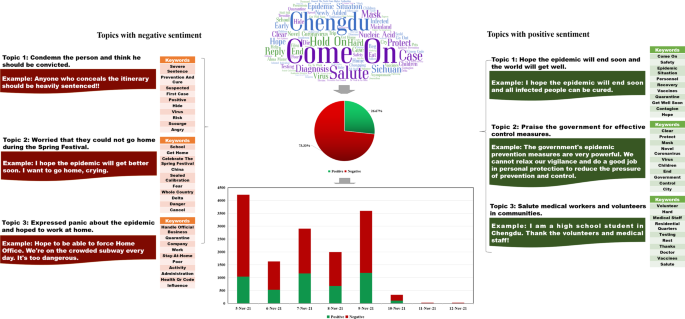
This figure shows the sentiment analysis and topic clustering results of RCase 6.
Comparison of the six cases
To answer the second research question— Were there any differences regarding the social media content of RIDCCV between these six cases? —we conducted a comparative analysis regarding the similarities and differences. To provide a more comprehensive understanding of public opinion, we divided the six cases into two groups based on whether the person violated epidemic prevention and control measures. Group 1 contained cases in which the subjects violated the regulations (RCase 2, RCase 5, and RCase 6), and Group 2 contained cases in which the subjects did not violate the regulations (RCase 1, RCase 3, and RCase 4).
On the one hand, the data reflected similarities, as follows:
Some people expressed appreciation for and saluted the medical workers and the government. This finding is consistent with some previous studies focusing on social media data related to the COVID-19 pandemic in (Duan et al., 2021 ; Hou et al., 2021 ; Luo et al., 2021 ), indicating the public’s common approval of Chinese epidemic prevention policies.
Opinions about fears concerning disease outbreaks appeared in the data of most researched cases. Many such opinions were generally found in social media data related to the COVID-19 pandemic, regardless of the research topic (Luo et al., 2021 ).
The results of text mining for RCase 1, RCase 4, and RCase 6 showed that some people worried that they could not return home for the holidays. This opinion was expressed mainly because these three cases occurred around the Spring Festival and National Day rather than during the event itself.
Regarding the sentiment analysis results, most opinions on social media expressed a negative sentiment. The proportion of posts with negative sentiment was 72.55%, 77.66%, 62.54%, 85.66%, 84.53%, and 73.33% in the six cases, respectively.
On the other hand, regarding the differences between the two groups, the focus of the negative opinions was very different. As shown in Fig. 2 , in RCase 2, most negative opinions involved condemnations of the woman because she broke quarantine. Moreover, in RCase 6, many negative opinions expressed the person’s condemnation and claimed he should be heavily sentenced. However, in RCase 1, as displayed in Fig. 1 , some negative opinions were directed at those engaging in CV against the woman and those spreading rumors and disclosing her private information. Notably, negative opinions about personal attacks on her private life were only expressed at the beginning of the Spring Festival, after which public opinions on social media gradually shifted from CV against the women to denouncing and condemning those who had divulged the private information and spread rumors with the development of the event.
In RCase 4, many negative opinions expressed the condemnation of CV behavior. For instance, a user posted, “Cyber violence should be punished. It has a great impact on people…” Nevertheless, it is evident that although the old couple in RCase 5 violated the epidemic prevention and control regulations, there were still some negative opinions expressing the condemnation of CV behavior, similar to the cases in Group 2. This is because the negligence of epidemic prevention workers in Jiayuguan was also a primary reason for the epidemic spreading in Xi’an. In addition, because the couple was older, many people could not bear seeing them suffer from CV.
Moreover, because RCase 1 and RCase 2 occurred at roughly the same time, there were some online posts containing discussions comparing the two cases, which may yield new findings. Thus, we extracted online posts containing at least one of the following keywords: “Chengdu,” “Pixian,” or “girl” from the data of RCase 2. Then, those posts focusing explicitly on a comparison between the two cases were manually selected—a total of 72 posts that included three main topics, as shown in Table 1 . The three main topics were “Hope the epidemic will end soon and call on the government to find out the source of the epidemic as soon as possible,” “Call on the government to strengthen management in route information disclosure,” and “Sympathize with the girl in Case 1 and think the woman in RCase 1 deserves cyber violence and is not worth being pitied.” The changes in the proportion of posts related to the three topics over time are shown in Fig. 7 . The figure shows that most people had opinions about Topic 2 and Topic 3 when comparing RCase 1 and RCase 2.
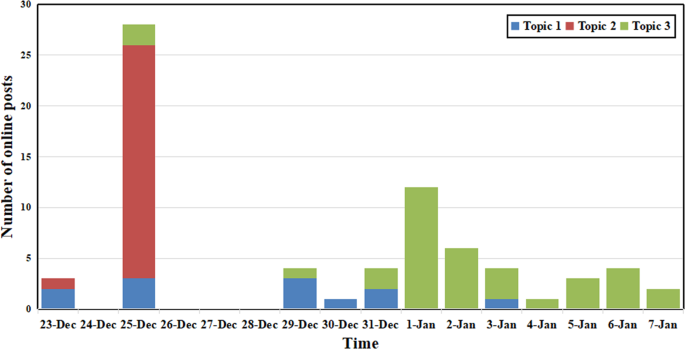
This figure shows the changes in the proportion of posts related to the three topics over time.
Specifically, in the early stage of RCase 1, Topic 1 was of greatest concern and peaked on December 25. This is mainly because the woman’s relatives posted on social media that their personal information had been leaked and that they had been harassed and attacked since December 23. They also added that they had actively reported personal information to the government as per government epidemic prevention regulations in Shenyang. However, the information leak subjected them to CV, which they had to endure in addition to COVID-19 infection. In the later stage of RCase 2, Topic 3 accounted for the largest proportion of posts, remaining a dominant issue until January 7, 2021. These findings support the argument that people commonly resisted CV against infected patients if they had not intentionally spread the virus to others and had not violated the regulations.
To answer the third research question— Who plays an important role in disseminating information on social media?— we conducted a spreading network analysis. Using social network analysis, we constructed the network spread of the six cases based on the original posts and comments. Figure 8 displays these networks. We then employed the weighted PageRank algorithm proposed by Zhang (Zhang, 2017 ) to explore the importance of each user. This study set the parameter for controlling the algorithm’s performance at 0.85. Finally, based on the classification method demonstrated in section “Social network analysis”, the users contained in our constructed networks were divided into four groups: mainstream/official media, influential we-media, we-media, and everyday users. The top 10 nodes with the largest PageRank values of the six cases were selected and classified, as shown in Table 4 . Most of the selected users were mainstream media or influential we-media users, accounting for 50% and 30% in RCase 1, 70% and 30% in RCase 2, 10% and 70% in RCase 3, 50% and 50% in RCase 4, and 80% and 20% in RCase 5 and RCase 6, respectively.
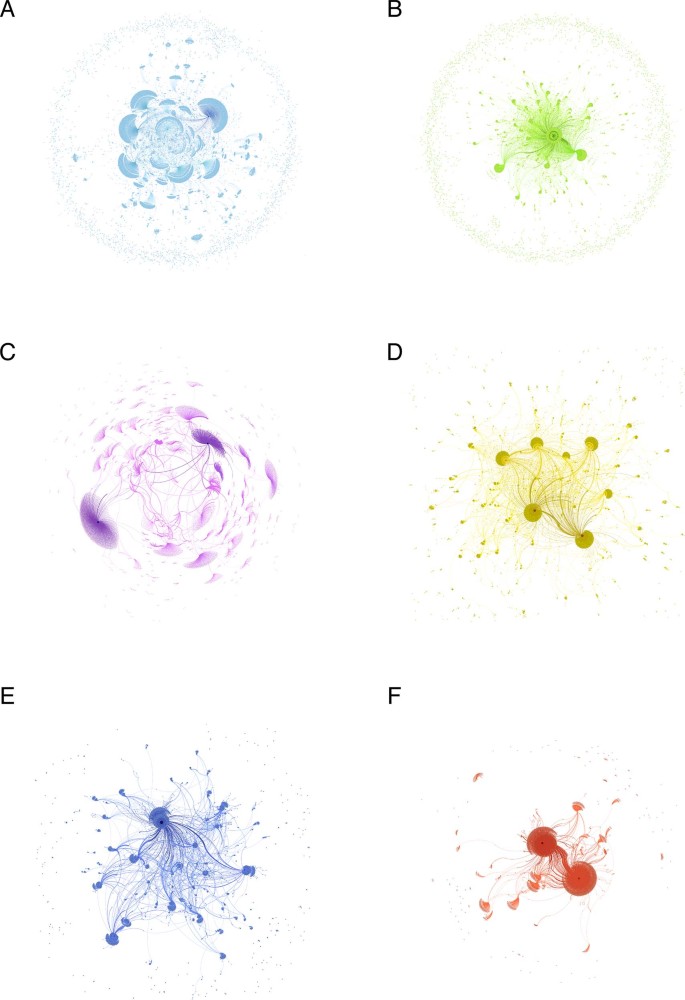
A Spreading network of RCase 1. B Spreading network of RCase 2. C Spreading network of RCase 3. D Spreading network of RCase 4. E Spreading network of RCase 5. F Spreading network of RCase 6.
Discussion and conclusions
Main findings.
This study conducted a content analysis focusing on CV behavior caused by travel route information disclosure during the COVID-19 pandemic. First, 13 representative cases of RIDCCV that occurred between November 2020 and November 2021 in China were selected to identify common features. Then, six cases were analyzed and compared using public opinion data from social media and text mining approaches. This approach aimed to understand public attitudes toward RIDCCV on social media, the differences between the six cases, and how to effectively avoid RIDCCV during future pandemics and other emergencies. Based on the results, the answers to the research questions posed are as follows:
For the first question, we found that the Chinese public generally agrees with the current strict epidemic prevention policies implemented by the Chinese government but has also experienced anxiety due to the restrictions imposed on travel, especially during holidays, such as the Spring Festival and National Day. For the six analyzed cases, many opinions condemning the infected patients for their actions, which spread the COVID-19 virus, can be found on social media, some of which expressed CV. In addition, some people also held opinions against CV against the patients, especially the girls in RCase 1 and RCase 3, as they believed that the persons were victims and did not spread COVID-19 on purpose. Moreover, many people called on the government to strictly protect patients’ privacy and establish an effective and reasonable route information disclosure mechanism.
For the second question, we found that although most people expressed negative sentiments, the focus of their negative opinions in the six cases was substantially different. In particular, people resisted CV against patients if they had not intentionally spread the virus to others without breaking the law. This finding offers a more detailed understanding of the formation mechanism of CV behavior during emergencies—intentional harm is the root cause of CV.
For the third question, we created six spreading networks based on the original posts and comments of six cases. A weighted PageRank analysis was conducted to explore the importance of users in the networks. We found that mainstream media and influential we-media played an essential role.
We concluded that publishing the route information of infected patients can assist the public in being better aware of their proximity to patients so that they can effectively protect themselves and thereby reduce their anxiety. To date, to a large extent, the COVID-19 pandemic has been effectively controlled in some countries, such as China. However, there are still many areas where COVID-19 remains a serious and complex threat. Thus, the publication of route information of infected patients cannot be stopped for an extended period.
Nevertheless, there is no doubt that every individual has the right to privacy. Network technology provides people with a convenient and virtual communication platform to express their viewpoints. While enjoying this right, we must realize that we should be responsible for our words and deeds. It is a fact that some patients have expanded the range of infection due to a lack of awareness of prevention and control regulations. Their actions have burdened the public and society at large. However, we cannot use this as an excuse to engage in unwarranted and malicious speculation about patients; doing so may eventually evolve into slander, abuse, insults, and even violence against patients. As to whether patients should be held responsible for the spread of the pandemic or criminally investigated for their actions, these are the responsibilities of government authorities, not individual citizens.
Formation mechanism of RIDCCV in the COVID-19 pandemic
This sub-section explains the formation mechanism of RIDCCV during the pandemic. From the perspective of motivation, all of our considered RIDCCV cases could be classified as the same kind of CV event. They were all related to ethically sensitive social “hot topics” during a particular period and originated with an initial call for justice. People expected each other to uphold epidemic prevention and control regulations and sought to punish those who violated these measures by posting opinions on social media (Liao et al., 2020 ). People approach the arena of virtual opinions as a highly liberalized, open, and anonymous cyberplace, but also as a platform for social supervision and catharsis concerning negative emotions. During the COVID-19 pandemic, when the published route information showed that someone had violated epidemic prevention regulations, people were quick to reach a consensus and establish a new set of moral norms based on a traditional public order to swiftly render a moral judgment of violators on the Internet, which ultimately evolved into RIDCCV.
For example, “three kinds of obedience and four virtues” is the primary embodiment of traditional Chinese moral values of women. Specifically, three kinds of obedience include daughters to their fathers before marriage, wives to their husbands after marriage, and widows to their sons after their husband’s death. The four virtues include morality, proper speech, modest manner, and diligent work (Basu et al., 2017 ). Although this standard has been widely criticized for a long time, its influence on today’s moral foundations in China is still significant (Zuo et al., 2012 ). Currently, women are expected to always be modest in manner and kept passive and sexually innocent in their relationships with men (Zuo et al., 2012 ). These moral standards for women were widely discussed in RCase 1, calling into question the girl’s private life and purity. On a larger scale, leaked private information and exposed route information have served as the basis for moral trials of netizens, ultimately escalating into verbal abuse and other violent acts in the tense and panicked atmosphere of the COVID-19 pandemic. In addition, the characteristics of the cases displayed in Table 1 indicate that those who were identified as the first locally confirmed cases of a particular wave of the pandemic were more likely to be victims of CV.
Rumors are also the primary cause of RIDCCV on social media during emergencies (Barlett et al., 2021 ). In some cases, rumors about patients and their families were quickly generated after the government exposed the route information of infected people. These rumors became a justification for people to use offensive language and launch personal attacks, which finally escalated into CV. A previous study found that distorted and exaggerated rumors generally spread rapidly in public emergencies (Lu et al., 2020 ). Social contradictions and negative emotions in the rumors stimulate and incite the corresponding moral principles of people. According to previous studies, uncertainty, and disturbed environment, as well as the degree of relevance to the public, are positively correlated with rumor propagation (Kim, 2018 ). The occurrence of public emergencies increases the uncertainty of the information environment. In contrast, fears about disease and death increase the uneasiness of the audience, especially in areas with high-security risks, and the technology of social media increases the relevance of rumors to the audience. Therefore, rumors spread more widely in the context of public health emergencies and are more readily accepted by the audience, culminating in the occurrence of CV.
Moreover, group polarization plays an influential role in RIDCCV (Bertolotti et al., 2013 ). According to existing research, online public opinions concerning sudden, unexpected public events have the characteristics of information flooding and uncertainty, which immerse people in a panicked atmosphere (Keller et al., 2021 ) and consequently increase the probability and degree of group polarization. In the six cases, after the route information of patients had been exposed, the behavioral motivation of CV evolved from “justice” to purely malicious attacks to achieve emotional catharsis. A large number of public opinions about dissatisfaction with adverse effects in daily life and work were posted on social media, which resonated with many netizens in unaffected areas. Finally, under the influence of an irrational and extreme emotional atmosphere, public opinions tend to be consistent, thereby enabling the group polarization inherent in CV to form.
Governance measures for RIDCCV
Based on our study findings, we recommend several measures to prevent RIDCCV during emergencies, such as the COVID-19 pandemic.
Optimize the route information collection and disclosure system
In most cases, grassroots staff in government agencies are in charge of publishing the necessary personal information about confirmed patients and their close contacts. These staff are the most likely to cause information leakage. Therefore, the government should balance the requirements for epidemic prevention and protecting people’s privacy by formulating and optimizing personal route information collection and disclosure mechanisms. In addition, more extensive training is also needed to enhance privacy protection awareness and legal literacy among grassroots staff. Since the beginning of 2021, Beijing and Shanghai have adopted the epidemiological survey reporting method of “only mentioning the route but not people,” Footnote 1 which no longer discloses the age, gender, and other personal information of confirmed cases. This method not only achieves the purpose of disseminating epidemic information, but also ensures the protection of patients’ personal information and reduces the risk of privacy disclosure. This strategy is, therefore, worth advocating in cities around the world. In addition, the government should pay more attention to patients who are the first locally confirmed cases of a specific wave of an epidemic or pandemic, as they are more likely to be victimized by CV on the Internet.
Ease public anxiety about the COVID-19 pandemic
Changeable social interests, an open network environment, and the complex psychology of netizens partly accelerate the formation of CV (Jain et al., 2020 ). On one hand, it is necessary to purify the network communication ecology from top to bottom and standardize the governance of cyberspace. On the other hand, during public health emergencies, such as the COVID-19 pandemic, the psychological interaction between an uncertain environment and anxiety has become the breeding ground for CV. In addition, social emotions generally become more volatile and uncertain when public health emergencies occur (Li et al., 2022 ). Thus, the government also needs to confront the negative emotions of the public, such as fear and dissatisfaction, by understanding and addressing their most pressing problems and grasping the psychological characteristics of people in cyberspace from the bottom to the top. In particular, service teams composed of mental health professionals and social workers should be established to provide psychological services for cured and isolated patients and ordinary people who think they have psychological problems because of the pandemic. The focus of these services should include psychological counseling for people with anxiety, depression, insomnia, and post-traumatic stress disorder (Redmond et al., 2020 ). Moreover, the government must promptly identify people prone to self-injury, suicide, attacks, or other psychotic symptoms.
Promote publicity with the help of mainstream media and influential we-media
When emergencies occur, the mainstream media and influential we-media focus on reporting hot events, which may arouse widespread attention from the government and the public. In most cases, the more emphasis is given by the mainstream media, and the more influential we become, the higher the public’s attention to an issue. According to the agenda-setting theory, the agenda-setting function of mainstream media and influential we-media offers a deeper understanding of discussed topics; the media agenda affects the public agenda (Liu et al., 2011 ). In other words, the mainstream media and influential we-media play an essential role as opinion leaders in guiding public opinion on the Internet (Lai et al., 2021 ). Therefore, the government should encourage the mainstream media and influential we-media to persistently report facts, from the announcement of official epidemic prevention and control regulations to people’s personal protection actions and shift the public’s attention from private issues to public issues to maintain and promote the publicity of the media. In addition, mainstream media and influential we-media should be responsible for preventing the generation and spread of rumors.
In terms of CV, mainstream media and influential we-media should take full advantage of their capacities, such as large audiences and the authority to act as gatekeepers of information transmission during emergencies. When CV appears on the Internet, mainstream media and influential we-media should increase the number and strengthen the intensity and depth of reports about the incidents that triggered CV to enable people to better judge the authenticity of the information and guide them toward a deeper understanding of the actual situation and the true meaning of the incidents.
Implications of this study
The implications of this study are as follows:
This study identified a crucial overlapping area in the social media, communication, and crisis management literature, specifically the intersection between CV and epidemic prevention. In addition, the study was one of the first to assess CV behavior on social media as caused by route information disclosure during the COVID-19 pandemic. Our findings indicate that, for RIDCCV, people are naturally resistant to CV against patients who may have unknowingly spread the virus to others without breaching the law. In addition, some characteristics that commonly appeared in RIDCCV were identified, such as the existence of rumors and moral condemnation caused by the official route information disclosure, and that those patients who are the first locally confirmed cases of a particular wave of the pandemic are more likely to be victimized by CV.
This study conducted content and network analyses focusing on social media data related to six RIDCCV cases in China. The formation mechanism of RIDCCV was proposed. As information disclosure is one of the commonly applied countermeasures in emergencies, these findings could be applied to network governance strategies for government departments during other major emergencies, such as natural disasters, accident disasters, and national security events. Therefore, our study enhances network governance and crisis management knowledge.
This study highlighted the importance and necessity of privacy protection in route information disclosure during the COVID-19 pandemic. We believe that information disclosure can effectively alleviate public panic and bolster trust in the government. However, effective control of virus transmission cannot be realized at the expense of patient privacy.
Based on our findings, we offer three practical recommendations:
Promote the publicity of the media field with the help of mainstream media and influential we-media.
Optimize the route information collection and disclosure system.
Ease public anxiety about the COVID-19 pandemic.
These recommendations are of great practical significance for the government to better balance the route information disclosure of patients to prevent CV during global emergencies. Government institutions can use social media to respond to public requests in a comprehensive and timely manner. This could also promote excellent two-way communication during critical crisis moments. Such actions would help preserve and develop the relationship between the government and the general public.
Study limitations and future research directions
This study had several limitations that future studies could address.
The effects of different patient characteristics, such as gender, age, and occupation, on CV were not considered. In future studies, we will propose a more detailed analysis of CV for a variety of patient types identified during the COVID-19 pandemic.
The six considered cases occurred during one specific period of the pandemic in China. However, we believe that the public’s focus shifts in stages during crises, generating different factors that could, in turn, lead to CV. Thus, future research will consider more RIDCCV cases in different periods of the COVID-19 pandemic.
Other factors, such as the types of government departments and stages of crises that influence the governance of CV, also warrant further research. For example, CV governance is a complex task during the crisis, requiring the participation and collaboration of many government departments, including but not limited to communications, education, and police. Thus, it is worth studying how to effectively combine these departments and build a collaborative CV governance system. In addition, the early stage of a crisis should receive significant attention in future research, as governance measures are generally incomplete and imperfect. Those imperfections may lead to a higher risk of privacy leaks and subsequent CV.
All of these issues should be considered in future studies.
Data availability
The datasets generated during and/or analyzed during the current study are available from the corresponding author on reasonable request. The codes used in this article are included in the Supplementary Information.
https://baijiahao.baidu.com/s?id=1689753315143554756&wfr=spider&for=pc .
Alsawalqa RO (2021) Cyberbullying, social stigma, and self-esteem: the impact of COVID-19 on students from East and Southeast Asia at the University of Jordan. Heliyon 7(4):e06711
Article CAS PubMed PubMed Central Google Scholar
Al-Zaman MS, Noman MMS (2021) Social media news in crisis? Popularity analysis of the top nine facebook pages of bangladeshi news media. J Inf Sci Theory Pract 9(2):18–32
Google Scholar
Barlett CP, Gentile DA, Kaufman JC (2012) Attacking others online: the formation of cyberbullying in late adolescence. Psychol Pop Media Cult 1(2):123–135
Article Google Scholar
Barlett CP, Rinker A, Roth B (2021) Cyberbullying perpetration in the COVID-19 era: an application of general strain theory. J Soc Psychol 161(4):466–476
Article PubMed Google Scholar
Barlett CP, Simmers MM, Roth B, Gentile D (2021) Comparing cyberbullying prevalence and process before and during the COVID-19 pandemic. J Soc Psychol 161(4):408–418
Basu S, Zuo X, Lou C, Acharya R, Lundgren R (2017) Learning to be gendered: gender socialization in early adolescence among urban poor in Delhi, India, and Shanghai, China. J Adolesc Health 61(4):S24–S29
Bertolotti T, Magnani L, Rizza C, Pereira ÂG (2013) A philosophical and evolutionary approach to cyber-bullying: social networks and the disruption of sub-moralities. Ethics Inf Technol 15(4):285–299
Casas JA, Del Rey R, Ortega-Ruiz R (2013) Bullying and cyberbullying: convergent and divergent predictor variables. Comput Human Behav 29(3):580–587
Cava M, Martínez-Ferrer B, Buelga S, Carrascosa L (2020) Sexist attitudes, romantic myths, and offline dating violence as predictors of cyber dating violence perpetration in adolescents. Comput Human Behav 111:106449
Chiyohara R (2010) Cyber-violence and cyber-contempt. J Inf Manage 30(3):88–98
Craig W, Boniel-Nissim M, King N, Walsh SD, Boer M, Donnelly PD, Harel-Fisch Y, Malinowska-Cieślik M, Gaspar De Matos M, Cosma A, Van den Eijnden R, Vieno A, Elgar FJ, Molcho M, Bjereld Y, Pickett W (2020) Social media use and cyber-bullying: a cross-national analysis of young people in 42 countries. J Adolesc Health 66(6):S100–S108
Deng S, Feng X (2022) How perceived threat of COVID-19 related to aggressive tendencies during the pandemic in Hubei Province and other regions of China: mediators and moderators. Curr Psychol 41:3349–3362
Di Trani M, Mariani R, Renzi A, Trabucchi G, Tambelli R, Danskin K (2020) The impact of coping strategies and perceived family support on depressive and anxious symptomatology during the coronavirus pandemic (COVID-19) lockdown. Front Psychiatry 11:587724
Article PubMed PubMed Central Google Scholar
Dong X, Lian Y (2022) The moderating effects of entertainers on public engagement through government activities in social media during the COVID-19. Telemat Inform 66:101746
Dou Z, Cheng Z, Huang D (2021) Research on migrant works’ concern recognition and emotion analysis based on web text data. Front Psychol 12:741928
Duan Y, Liu L, Wang Z (2021) COVID-19 sentiment and the Chinese stock market: evidence from the official news media and sina weibo. Res Int Bus Finance 58:101432
Ephraim PE (2013) African youths and the dangers of social networking: a culture-centered approach to using social media. Ethics Inf Technol 15(4):275–284
Ge X (2020) Social media reduce users’ moral sensitivity: online shaming as a possible consequence. Aggress Behav 46(5):359–369
Han Z, Wang Z, Li Y (2021) Cyberbullying involvement, resilient coping, and loneliness of adolescents during covid-19 in rural china. Front Psychol 12:664612
Hinduja S, Patchin JW, Runions KC, Shapka JD, Wright MF (2013) Social influences on cyberbullying behaviors among middle and high school students. J Youth Adolesc 42(5):711–722
Hou K, Hou T, Cai L (2021) Public attention about COVID-19 on social media: an investigation based on data mining and text analysis. Pers Individ Dif 175:110701
Hu G, Li P, Yuan C, Tao C, Wen H, Liu Q, Qiu W (2020) Information disclosure during the COVID-19 epidemic in China: city-level observational study. J Med Internet Res 22(8):e19572
Jain O, Gupta M, Satam S, Panda S (2020) Has the COVID-19 pandemic affected the susceptibility to cyberbullying in India? Comput Hum Behav Rep 2:100029
Jane EA (2017) Feminist digilante responses to a slut-shaming on facebook. Soc Media Soc 3(2):205630511770599
Jones LM, Mitchell KJ, Finkelhor D, Willoughby T, Hamby S, Sugarman D (2013) Online harassment in context: trends from three youth internet safety surveys (2000, 2005, 2010). Psychol Violence 3(1):53–69
Jung G, Lee H, Kim A, Lee U (2020) Too much information: assessing privacy risks of contact trace data disclosure on people with COVID-19 in South Korea. Front Public Health 8:305
Kaplan S, Vakili K (2015) The double-edged sword of recombination in breakthrough innovation. Strateg Manag J 36(10):1435–1457
Keller SN, Honea JC, Ollivant R (2021) How social media comments inform the promotion of mask-wearing and other COVID-19 prevention strategies. Int J Environ Res Public Health 18(11):5624
Kim D, Seo D, Cho S, Kang P (2019) Multi-co-training for document classification using various document representations: TF-IDF, LDA, and Doc2Vec. Inf Sci 477:15–29
Kim H (2021) COVID-19 apps as a digital intervention policy: a longitudinal panel data analysis in South Korea. Health Policy 125(11):1430–1440
Kim JW (2018) Rumor has it: The effects of virality metrics on rumor believability and transmission on Twitter. New Media Soc 20(12):4807–4825
Lai K, Li D, Peng H, Zhao J, He L (2021) Assessing suicide reporting in top newspaper social media accounts in China: content analysis study. JMIR Ment Health 8(5):e26654
Li L, Liu X, Zhang X (2021) Public attention and sentiment of recycled water: evidence from social media text mining in China. J Clean Prod 303:126814
Li L, Zhang Q, Wang X, Zhang J, Wang T, Gao T, Duan W, Tsoi KK, Wang F (2020) Characterizing the propagation of situational information in social media during COVID-19 epidemic: a case study on Weibo. IEEE Trans Comput Soc Syst 7(2):556–562
Li M, Chen Z, Rao L (2022) Emotion, analytic thinking and susceptibility to misinformation during the COVID-19 outbreak. Comput Human Behav 133:107295
Li S, Wang Y, Xue J, Zhao N, Zhu T (2020) The impact of COVID-19 epidemic declaration on psychological consequences: a study on active Weibo users. Int J Environ Res Public Health 17(6):2032
Liao Q, Yuan J, Dong M, Yang L, Fielding R, Lam WWT (2020) Public engagement and government responsiveness in the communications about COVID-19 during the early epidemic stage in China: infodemiology study on social media data. J Med Internet Res 22(5):e18796
Ling M, Chen Q, Sun Q, Jia Y (2020) Hybrid neural network for sina weibo sentiment analysis. IEEE Trans Comput Soc Syst 7(4):983–990
Liu S, Lithopoulos A, Zhang C, Garcia-Barrera MA, Rhodes RE (2021) Personality and perceived stress during COVID-19 pandemic: testing the mediating role of perceived threat and efficacy. Pers Individ Dif 168:110351
Liu X, Hu W (2019) Attention and sentiment of Chinese public toward green buildings based on Sina Weibo. Sustain Cities Soc 44:550–558
Liu X, Lindquist E, Vedlitz A (2011) Explaining media and congressional attention to global climate change, 1969—2005: an empirical test of agenda-setting theory. Polit Res Q 64(2):405–419
Lu Y, Ji Z, Zhang X, Zheng Y, Liang H (2020) Re-thinking the role of government information intervention in the COVID-19 pandemic: an agent-based modeling analysis. Int J Environ Res Public Health 18(1):147
Luo C, Chen A, Cui B, Liao W (2021) Exploring public perceptions of the COVID-19 vaccine online from a cultural perspective: Semantic network analysis of two social media platforms in the United States and China. Telemat Inform 65:101712
Luqiu LR, Schmierbach M, Ng Y (2019) Willingness to follow opinion leaders: a case study of Chinese Weibo. Comput Human Behav 101:42–50
Mee A, Homapour E, Chiclana F, Engel O (2021) Sentiment analysis using TF–IDF weighting of UK MPs’ tweets on Brexit. Knowl Based Syst 228:107238
Morgul E, Bener A, Atak M, Akyel S, Aktaş S, Bhugra D, Ventriglio A, Jordan TR (2021) COVID-19 pandemic and psychological fatigue in Turkey. Int J Soc Psychiatry 67(2):128–135
Mutimukwe C, Kolkowska E, Grönlund Å (2020) Information privacy in e-service: Effect of organizational privacy assurances on individual privacy concerns, perceptions, trust and self-disclosure behavior. Gov Inform Q 37(1):101413
Nagle J (2018) Twitter, cyber-violence, and the need for a critical social media literacy in teacher education: A review of the literature. Teach Teach Educ 76:86–94
Patton DU, Hong JS, Ranney M, Patel S, Kelley C, Eschmann R, Washington T (2014) Social media as a vector for youth violence: a review of the literature. Comput Human Behav 35:548–553
Peng Y, Li J, Xia H, Qi S, Li J (2015) The effects of food safety issues released by we media on consumers’ awareness and purchasing behavior: a case study in China. Food Policy 51:44–52
Peskin MF, Markham CM, Shegog R, Temple JR, Baumler ER, Addy RC, Hernandez B, Cuccaro P, Gabay EK, Thiel M, Emery ST (2017) Prevalence and correlates of the perpetration of cyber dating abuse among early adolescents. J Youth Adolesc 46(2):358–375
Peterson J, Densley J (2017) Cyber violence: what do we know and where do we go from here? Aggress Violent Behav 34:193–200
Redmond P, Lock JV, Smart V (2020) Developing a cyberbullying conceptual framework for educators. Technol Soc 60:101223
Saleem S, Khan NF, Zafar S (2021) Prevalence of cyberbullying victimization among Pakistani Youth. Technol Soc 65:101577
Shi L, Cheng Y, Shao J, Wang X, Sheng H (2021) Leader-follower opinion dynamics of signed social networks with asynchronous trust/distrust level evolution. IEEE Trans Netw Sci Eng 9(2):495–509
Article MathSciNet Google Scholar
Shirish A, Srivastava SC, Chandra S (2021) Impact of mobile connectivity and freedom on fake news propensity during the COVID-19 pandemic: a cross-country empirical examination. Eur J Inf Syst 30(3):322–341
Tao Z, Su Y (2021) Authors’ reply to: methodological clarifications and generalizing from weibo data. comment on “nature and diffusion of COVID-19-related oral health information on Chinese social media: analysis of tweets on Weibo”. J Med Internet Res 23(5):e29145
Tsao S, Chen H, Tisseverasinghe T, Yang Y, Li L, Butt ZA (2021) What social media told us in the time of COVID-19: a scoping review. Lancet Digit Health 3(3):e175–e194
Vos SC, Sutton J, Yu Y, Renshaw SL, Olson MK, Gibson CB, Butts CT (2018) Retweeting risk communication: the role of threat and efficacy. Risk Anal 38(12):2580–2598
Wang X (2021) The motivations and uses of mainstream and social media during the COVID-19 pandemic in China: a structural equation modeling approach. Comput Hum Behav Rep 4:100098
Wu P, Zhao N, Li S, Liu Z, Wang Y, Liu T, Liu X, Zhu T (2021) Exploring the psychological effects of COVID-19 home confinement in China: a psycho-linguistic analysis on Weibo data pool. Front Psychol 12:587308
Wu X (2018) Discursive strategies of resistance on Weibo: a case study of the 2015 Tianjin explosions in China. Discourse. Context Media 26:64–73
Xu F, Qi Y, Li X (2018) What affects the user stickiness of the mainstream media websites in China? Electron Commer Res Appl 29:124–132
Xu K, Qi G, Huang J, Wu T, Fu X (2018) Detecting bursts in sentiment-aware topics from social media. Knowl Based Syst 141:44–54
Yang F (2021) Coping strategies, cyberbullying behaviors, and depression among Chinese netizens during the COVID-19 pandemic: a web-based nationwide survey. J Affect Disord 281:138–144
Article CAS PubMed Google Scholar
Zhang F (2017) Evaluating journal impact based on weighted citations. Scientometrics 113(2):1155–1169
Zuo X, Lou C, Gao E, Chend Y, Niu H, Zabin LS (2012) Gender differences in adolescent premarital sexual permissiveness in three Asian cities: effects of gender-role attitudes: the three-city study of Asian adolescents and youth: Hanoi, Shanghai, and Taipei. J Adolesc Health 50(3):S18–S25
Download references
Acknowledgements
This research was supported by the National Natural Science Foundation of China [grant number 72274010, 71904010].
Author information
Authors and affiliations.
School of Journalism, Communication University of China, No.1 Dingfuzhuang East Street, 100024, Beijing, People’s Republic of China
Ying Lian & Yueting Zhou
College of Economics and Management, Beijing University of Technology, 100124, Beijing, People’s Republic of China
Xueying Lian & Xuefan Dong
Research Base of Beijing Modern Manufacturing Development, Beijing University of Technology, 100124, Beijing, People’s Republic of China
Xuefan Dong
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Xuefan Dong .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Ethical approval
This article does not contain any studies with human participants performed by any of the authors.
Informed consent
Additional information.
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
Supplemental material, rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Lian, Y., Zhou, Y., Lian, X. et al. Cyber violence caused by the disclosure of route information during the COVID-19 pandemic. Humanit Soc Sci Commun 9 , 417 (2022). https://doi.org/10.1057/s41599-022-01450-8
Download citation
Received : 09 April 2022
Accepted : 16 November 2022
Published : 25 November 2022
DOI : https://doi.org/10.1057/s41599-022-01450-8
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
This article is cited by
A dataset on corporate sustainability disclosure.
- Jinfang Tian
Scientific Data (2023)
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies

Cyber Violence And Its Effects On Modern Society
Title: Understanding Cyber Violence in contemporary society Research Question The literature review will compare cyber violence to traditional interpersonal violence in order to comprehend the characteristics of cyber violence in contemporary society. Introduction Cyber violence was defined as “an aggressive, intentional act carried out by a group or individual, using electronic forms of contact, repeatedly and over time against a victim who cannot easily defend him or herself.” (Smith, Maddavi, Carvalho, Fisher, Russell, and Tippett, 2008: 376). The prevalence and impacts of cyber violence will be discussed in the literature review (Zweig, Dank, Yanher, and Lachman 2013; Madlock and Westermann 2011). Subsequently, competing theories regarding cyber violence will be introduced. Some scholars presented evidence to support the position that cyber violence was driven by more malicious intentions compared to traditional forms of interpersonal violence (Suler, 2004). Conversely, other empirical studies provided evidence to support the position that cyber violence was a reincarnation of traditional forms of interpersonal violence in a modern context (Bauman and Newman 2013; Toledano, Werch, and Wiens 2015). Specifically, the effects of cyber violence on individual victims were similar compared to the effects of traditional forms of interpersonal violence on individual victims (Bauman and Newman 2013; Toledano et al. 2015) Empirical research on cyber violence
Bullying In The 1990s's Compared To Now
Almost everyone owns a smart phone or a laptop meaning, individuals have easy access to the World Wide Web. Individuals rely on the internet as a social life. Data was taken between the years 2004-2015; 9 trials were performed in fact. The Cyber Bullying Research Center conducted the experiment allowing many individuals to observe the serious
The Internet : The Psychological Effects Of The Internet
One of the consequences of the usage of the internet that can be psychologically harmful to a person is cyber-bullying. Cyber-bullying is happening more frequently in the article of Psychological, Physical, and
Bullying Evolution : Cyber Bullying
The internet has created an entirely new world of social communications particularly for youths. There are no more barriers. Family, friends, young and old may now stay in touch with just about everyone, anywhere in the world through the use of email, text messaging, web chat, and instant messaging. Although, most interactions are friendly and in good nature, there are some that are not. The use of technology as a tool to antagonize, torment and intimidate others is now a widespread problem. Sadly, this form of bullying like all others is most common among children and young adults. Research done by Cox Communications on children between 13 thru 18 year-olds, 25 percent said they were cyber-bullied whether online or by cell phone (Cox Com. 2009). Also in 2007, the National Crime Prevention Council reported cyber-bullying as a problem that affected approximately half of all American teens. Since it is popular among this group of American teens, then it is safe look at some of possible reason cyber bullies of this age group are encouraged to take part in such activity.
Cyber Bullying Is A Significant Problem
1. This article was written based on a study of cyber bullying behaviors in a large group of middle and high school students. Increases in technology, and access to that technology have increased student ability to bully using an online forum. Not a lot of research had been done into this subject at the time of this article. Taking this into consideration there had been a few large scale studies done that corroborated the belief that cyber bullying is a significant problem. Researchers believed that due to the potential for exposure to this type of bullying, more studies needed to be done. With increased research there was the hope of diminishing the number of incidents of cyber bullying and the effects of those incidents. The research that had been completed also pointed to additional issues, including behavior problems, suspensions, substance abuse and depression among students who had experienced cyber bullying. The other side of previous research showed that the students who used cyber bullying as a weapon were more aggressive in their behaviors.
COSC 631: Web Development And Programming II
The world has become a global village and therefore many activities like education, business, relationship formation and many other aspects relating to humans are done over internet and with cyber-crime these aspects of human have been threatened and in some cases victims lose a lot of money mainly in the e-commerce field. The effect of cyber bullying has caused many individuals to commit suicide. Loss of private data has been witnessed at the organizational and individual level causing the victims great losses when they cannot recover the data.
Chelsea K. Anker's Research
Yang states that it has become easier to cause bullying or harassment through the internet recently. His statements are very true, the recent burst in social media leads to sharing about your life and the people around you, and it may also result in people harassing you and/or your loved ones. In Chelsea K. Anker’s research submission, she states cases of abuse drawn from cyber-bullying and the many results upon those
Daijohna Lloyd-Shorter. Dr. Herrmann. 13 March 2017.
Cyberbullying has been a big problem for teens and adults around the world. Cyberbullying is the use of electronic communication to bully a person, typically by sending messages of an intimidating or threatening nature. For most cyberbullying isn’t anything serious it’s just a person just joking around or just speaking their mind but its more than that its feelings being involved families being broken even hearts.
Social Media And Satire
The definition of cyberbullying is ‘the use of electronic communication to bully a person, typically by sending messages of an intimidating or threatening nature.’
Bullying In Australia
Technology is rapidly advancing at a dizzying rate which has seen many amazing feats but has also introduced and increased the act of Cyberbullying. Cyber bullying can be defined as targeting someone using any form of technology (this includes social media) to tease, stalk or humiliate someone online (Dictionary.com, 2016). Cyberbullying is so detrimental because it encourages the targeting of an individual; It is often done in secret with the bully hiding who they are by creating false profiles or names, or sending anonymous messages. It is difficult to remove as it is shared online so it can be recorded and saved in different places. Cyberbullying has such a negative impact that research shows that there is a correlation between the violent
Misogynistic Cyberbullying Among Teens
Cyberbullying, once thought of as a tormentor among teens, is rapidly increasing among adults in a wide range of internet outlets that allow information to be shared on a global scale for the destruction of a victim’s life on a social, an educational, and an employment wide strike. The rise in adult cyber-bullying affects female individuals at a much more alarming rate than their male counterparts. This misogynistic cyber-bullying tendency is brought to light in the book, “The Offensive Internet,” by Martha Craven Nussbaum, and Saul X. Levmore, with the following statistics; “The nonprofit organization Working to Halt Online Abuse explains that, from 2000 to 2007, 72.5 percent of the individuals reporting cyber harassment identified themselves
Cyber Criminology: The Prevalence of Cyberstalking, Online Harrassment and Bullying
- 3 Works Cited
There is further difficulty in defining cyberstalking because it is often a term that is interchangeable with cyberbullying and cyberharassment (Jameson, 2008, p.236). This wide array of internet criminal activity is defined along a continuum of cybercrime extending from purely in the physical world to purely in cyberspace (Gordon and Ford, 2006, p.15). The exclusionary definition of cyberstalking and distinguishing it from other similar cybercrimes helps with narrowing the definition of cyberstalking. Cyberbullying is the use of the internet to exhibit aggressive behavior aimed at intimidating or inducing fear
Suicide Among Teen Victims Of Cyberbullying Essay
Social media is the ultimate platform for bullies. Using social media, perpetrators can bully their victims to the point of anxiety, fear, low self-esteem, suicidal ideations and in some cases to the committal of the suicidal act. Cyberbullying is defined as the deliberate repetition of hostility toward a group or persons with the intent to induce psychological, emotional, or physical harm through the use of digital communication (Niels, Menno, et. Al, 2013). A study conducted in 2014, stated that nearly 75% of school age youth have been the victim of cyberbullying (Giumetti, Kowalski, et al., 2014).
Causes Of Online Abuse By Anne Flaherty
In the paper of victims of online abuse by “Anne Flaherty”, The main idea is to present information regarding Cyber bullying and ”what are now considered” crimes as registered by the US government and society.
The Dangers Of Cyberbullying
Though cyberbullying occurs online, it can also lead to physical confrontations. According to The Dangers of Cyberbullying a radio interview

The Negative Effects of Cyberbullying Essays
- 10 Works Cited
We use technology in almost every aspect of our daily lives; it is how we stay connected in this fast-paced world. Technology provides many benefits, but it has the potential to destroy many people. With technology use on the rise, bullying has taken a new, more destructive form. Cyberbullying, as defined by the Cyberbullying Research Center, is the willful and repeated harm inflicted through the medium of electronic text (qtd. in Chait). Cyberbullying is a serious problem and has serious consequences.
Related Topics
- Scientific method
Advertisement
Research trends in cybercrime victimization during 2010–2020: a bibliometric analysis
- Review Paper
- Published: 06 January 2022
- Volume 2 , article number 4 , ( 2022 )
Cite this article

- Huong Thi Ngoc Ho 1 &
- Hai Thanh Luong ORCID: orcid.org/0000-0003-2421-9149 2
10k Accesses
11 Citations
1 Altmetric
Explore all metrics
Research on cybercrime victimization is relatively diversified; however, no bibliometric study has been found to introduce the panorama of this subject. The current study aims to address this research gap by performing a bibliometric analysis of 387 Social Science Citation Index articles relevant to cybercrime victimization from Web of Science database during the period of 2010–2020. The purpose of the article is to examine the research trend and distribution of publications by five main fields, including time, productive authors, prominent sources, active institutions, and leading countries/regions. Furthermore, this study aims to determine the global collaborations and current gaps in research of cybercrime victimization. Findings indicated the decidedly upward trend of publications in the given period. The USA and its authors and institutions were likely to connect widely and took a crucial position in research of cybercrime victimization. Cyberbullying was identified as the most concerned issue over the years and cyber interpersonal crimes had the large number of research comparing to cyber-dependent crimes. Future research is suggested to concern more about sample of the elder and collect data in different countries which are not only European countries or the USA. Cross-nation research in less popular continents in research map was recommended to be conducted more. This paper contributed an overview of scholarly status of cybercrime victimization through statistical evidence and visual findings; assisted researchers to optimize their own research direction; and supported authors and institutions to build strategies for research collaboration.
Similar content being viewed by others

Research synthesis of cybercrime laws and COVID-19 in Indonesia: lessons for developed and developing countries
Scholarly influence in criminology and criminal justice of china.

The Nuts and Bolts of the India-Abusive Fake Government of Telangana: Cyberpolicing Against Online Sedition
Avoid common mistakes on your manuscript.
Introduction
To date, the debate of cybercrime definition has been controversial which is considered as one of the five areas of cyber criminology (Ngo and Jaishankar 2017 ; Drew 2020 ). Footnote 1 Several terms are used to illustrate ‘cybercrime’, such as ‘high-tech crime’ (Insa 2007 ), ‘computer crime’ (Choi 2008 ; Skinner and Fream 1997 ), ‘digital crime’ (Gogolin 2010 ), or ‘virtual crime’ (Brenner 2001 ). ‘Cybercrime’, however, has been the most popular in the public parlance (Wall 2004 ). A propensity considers crime directly against computer as cybercrime, while other tendency asserts that any crime committed via internet or related to a computer is cybercrime (Marsh and Melville 2008 ; Wall 2004 ). Hence, there is a distinction between ‘true cybercrime’ or ‘high-tech’ cybercrime and ‘low-tech’ cybercrime (Wagen and Pieters 2020 ). Council of Europe defines ‘any criminal offense committed against or with the help of a computer network’ as cybercrime (Abdullah and Jahan 2020 , p. 90). Despite different approaches, cybercrime generally includes not only new types of crimes which have just occurred after the invention of computer and internet (Holt and Bossler 2014 ; Drew 2020 ) but also traditional types of crimes which took the advantages of information communication technology (ICT) as vehicle for illegal behaviors (Luong 2021 ; Nguyen and Luong 2020 ; Luong et al. 2019 ). Two main cybercrime categories identified, respectively, are cyber-dependent crime (hacking, malware, denial of service attacks) and cyber-enable crime (phishing, identity theft, cyber romance scam, online shopping fraud). Nevertheless, there are several different classifications of cybercrime such as cybercrime against certain individuals, groups of individuals, computer networks, computer users, critical infrastructures, virtual entities (Wagen and Pieters 2020 ); cyber-trespass, cyber-deceptions, cyber-pornography, and cyber-violence (Wall 2001 ).
Due to the common prevalence of cybercrime, the increasing threats of cybercrime victimization are obviously serious. Cybercrime victimization has become a crucial research subfield in recent years (Wagen and Pieters 2020 ). It is difficult to differ “forms of online victimization” and “acts that actually constitute a crime”, then it is usual for researchers to focus less on perspective of criminal law and consider any negative experiences online as cybercrime (Näsi et al. 2015 , p. 2). It was likely to lead to practical gaps between theory and practice in terms of investigating the nexus of offender and victims on cyberspace. In the light of literature review, numerous specific aspects of cybercrime victimization were investigated by questionnaire surveys or interview survey such as the prevalence of cybercrime victimization (Näsi et al. 2015 ; Whitty and Buchanan 2012 ); causes and predictors of cybercrime victimization (Abdullah and Jahan 2020 ; Algarni et al. 2017 ; Ilievski 2016 ; Jahankhani 2013 ; Kirwan et al. 2018 ; Näsi et al. 2015 ; Reyns et al. 2019 ; Saad et al. 2018 ); and the relationship between social networking sites (SNS) and cybercrime victimization (Das and Sahoo 2011 ; Algarni et al. 2017 ; Benson et al. 2015 ; Seng et al. 2018 ). To some extent, therefore, the current study examines cybercrime victimization in the large scale, referring to any negative experiences on cyberspace or computer systems. Nevertheless, no bibliometric analysis was found to show the research trend and general landscape of this domain.
Bibliometric is a kind of statistical analysis which uses information in a database to provide the depth insight into the development of a specified area (Leung et al. 2017 ). The present study aims to address this research gap by providing a bibliometric review of the relevant SSCI articles in WoS database during the period of 2010–2020. The pattern of publications, the productivity of main elements (authors, journals, institutions, and countries/regions), statistic of citations, classification of key terms, research gaps, and other collaborations will be presented and discussed in section four and five after reviewing literatures and presenting our methods conducted. This article contributes an overview of research achievements pertaining to cybercrime victimization in the given period through statistical evidence and visual findings; assists researchers to perceive clearly about the key positions in research maps of this field, and obtain more suggestions to develop their own research direction.
Literature review
- Cybercrime victimization
Cybercrime victimization may exist in two levels including institutional and individual level (Näsi et al. 2015 ). For the former, victim is governments, institutions, or corporations, whereas for the latter, victim is a specific individual (Näsi et al. 2015 ). A wide range of previous studies concerned about individual level of victim and applied Lifestyle Exposure Theory (LET), Routine Activity Theory (RAT) and General Theory of Crime to explain cybercrime victimization (Choi 2008 ; Holt and Bossler 2009 ; Ngo and Paternoster 2011 ). Basing on these theories, situational and individual factors were supposed to play an important role in understanding cybercrime victimization (Choi 2008 ; Van Wilsem 2013 ). However, there was another argument that situational and individual factors did not predict cybercrime victimization (Ngo and Paternoster 2011 ; Wagen and Pieters 2020 ). Overall, most of those studies just focused only one distinctive kind of cybercrime such as computer viruses, malware infection, phishing, cyberbullying, online harassment, online defamation, identity theft, cyberstalking, online sexual solicitation, cyber romance scams or online consumer fraud. Referring to results of the prior research, some supported for the applicability of mentioned theories but other did not share the same viewpoint (Leukfeldt and Yar 2016 ). It was hard to evaluate the effect of LET or RAT for explanation of cybercrime victimization because the nature of examined cybercrime were different (Leukfeldt and Holt 2020 ; Leukfeldt and Yar 2016 ).
Previous research determined that cybercrime victimization was more common in younger group compared to older group because the young is the most active online user (Näsi et al. 2015 ; Oksanen and Keipi 2013 ) and males tended to become victims of cybercrime more than females in general (Näsi et al. 2015 ). However, findings might be different in research which concerned specific types of cybercrime. Women were more likely to be victims of the online romance scam (Whitty and Buchanan 2012 ) and sexual harassment (Näsi et al. 2015 ), while men recorded higher rate of victimization of cyber-violence and defamation. Other demographic factors were also examined such as living areas (Näsi et al. 2015 ), education (Oksanen and Keipi 2013 ; Saad et al. 2018 ) and economic status (Oksanen and Keipi 2013 ; Saad et al. 2018 ). Furthermore, several prior studies focus on the association of psychological factors and cybercrime victimization, including awareness and perception (Ariola et al. 2018 ; Saridakis et al. 2016 ), personality (Kirwan et al. 2018 ; Orchard et al. 2014 ; Parrish et al. 2009 ), self-control (Ilievski 2016 ; Ngo and Paternoster 2011 ; Reyns et al. 2019 ), fear of cybercrime (Lee et al. 2019 ), online behaviors (Al-Nemrat and Benzaïd 2015 ; Saridakis et al. 2016 ). Psychological factors were assumed to have effects on cybercrime victimization at distinctive levels.
Another perspective which was much concerned by researchers was the relationship between cybercrime victimization and SNS. SNS has been a fertile land for cybercriminals due to the plenty of personal information shared, lack of guard, the availability of communication channels (Seng et al. 2018 ), and the networked nature of social media (Vishwanath 2015 ). When users disclosed their personal information, they turned themselves into prey for predators in cyberspace. Seng et al. ( 2018 ) did research to understand impact factors on user’s decision to react and click on suspicious posts or links on Facebook. The findings indicated that participants’ interactions with shared contents on SNS were affected by their relationship with author of those contents; they often ignored the location of shared posts; several warning signals of suspicious posts were not concerned. Additionally, Vishwanath ( 2015 ) indicated factors that led users to fall victims on the SNS; Algarni et al. ( 2017 ) investigated users’ susceptibility to social engineering victimization on Facebook; and Kirwan et al. ( 2018 ) determined risk factors resulting in falling victims of SNS scam.
Bibliometric of cybercrime victimization
“Bibliometric” is a term which was coined by Pritchard in 1969 and a useful method which structures, quantifies bibliometric information to indicate the factors constituting the scientific research within a specific field (Serafin et al. 2019 ). Bibliometric method relies on some basic types of analysis, namely co-authorship, co-occurrence, citation, co-citation, and bibliographic coupling. This method was employed to various research domains such as criminology (Alalehto and Persson 2013 ), criminal law (Jamshed et al. 2020 ), marketing communication (Kim et al. 2019 ), social media (Chen et al. 2019 ; Gan and Wang 2014 ; Leung et al. 2017 ; Li et al. 2017 ; You et al. 2014 ; Zyoud et al. 2018 ), communication (Feeley 2008 ), advertising (Pasadeos 1985 ), education (Martí-Parreño et al. 2016 ).
Also, there are more and more scholars preferring to use bibliometric analysis on cyberspace-related subject such as: cyber behaviors (Serafin et al. 2019 ), cybersecurity (Cojocaru and Cojocaru 2019 ), cyber parental control (Altarturi et al. 2020 ). Serafin et al. ( 2019 ) accessed the Scopus database to perform a bibliometric analysis of cyber behavior. All documents were published by four journals: Cyberpsychology, Behavior and Social Networking (ISSN: 21522723), Cyberpsychology and Behavior (ISSN: 10949313) , Computers in Human Behavior (ISSN: 07475632) and Human–Computer Interaction (ISSN: 07370024), in duration of 2000–2018. Findings indicated the use of Facebook and other social media was the most common in research during this period, while psychological matters were less concerned (Serafin et al. 2019 ). Cojocaru and Cojocaru ( 2019 ) examined the research status of cybersecurity in the Republic of Moldavo, then made a comparison with the Eastern Europe countries’ status. This study employed bibliometric analysis of publications from three data sources: National Bibliometric Instrument (database from Republic of Moldavo), Scopus Elsevier and WoS. The Republic of Moldavo had the moderate number of scientific publications on cybersecurity; Russian Federation, Poland, Romania, Czech Republic, and Ukraine were the leading countries in Eastern Europe area (Cojocaru and Cojocaru 2019 ). Altarturi et al. ( 2020 ) was interested in bibliometric analysis of cyber parental control, basing on publications between 2000 and 2019 in Scopus and WoS. This research identified some most used keywords including ‘cyberbullying’, ‘bullying’, ‘adolescents’ and ‘adolescence’, showing their crucial position in the domain of cyber parental control (Altarturi et al. 2020 ). ‘Cyber victimization’ and ‘victimization’ were also mentioned as the common keywords by Altarturi et al. ( 2020 ). Prior research much focus on how to protect children from cyberbullying. Besides, four online threats for children were determined: content, contact, conduct and commercial threats (Altarturi et al. 2020 ).
Generally, it has been recorded several published bibliometric analyses of cyber-related issues but remained a lack of bibliometric research targeting cybercrime victimization. Thus, the present study attempts to fill this gap, reviewing the achievements of existed publications as well as updating the research trend in this field.
In detail, our current study aims to address four research questions (RQs):
What is overall distribution of publication based on year, institutions and countries, sources, and authors in cybercrime victimization?
Which are the topmost cited publications in terms of cybercrime victimization?
Who are the top co-authorships among authors, institutions, and countries in research cybercrime victimization?
What are top keywords, co-occurrences and research gaps in the field of cybercrime victimization?
Data collection procedure
Currently, among specific approaches in cybercrime’s fileds, WoS is “one of the largest and comprehensive bibliographic data covering multidisciplinary areas” (Zyoud et al. 2018 , p. 2). This paper retrieved data from the SSCI by searching publications of cybercrime victimization on WoS database to examine the growth of publication; top keywords; popular topics; research gaps; and top influential authors, institutions, countries, and journals in the academic community.
This paper employed Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) for data collection procedure. For timeline, we preferred to search between 2010 and 2020 on the WoS system with two main reasons. First, when the official update of the 2009 PRISMA Statement had ready upgraded with the specific guidelines and stable techniques, we consider beginning since 2010 that is timely to test. Secondly, although there are several publications from the early of 2021 to collect by the WoS, its updated articles will be continued until the end of the year. Therefore, we only searched until the end of 2020 to ensure the full updates.
To identify publications on cybercrime victimization, the study accessed WoS and used two keywords for searching: ‘cybercrime victimization’ or ‘cyber victimization’ after testing and looking for some terminology-related topics. Accordingly, the paper applied a combination of many other searching terms besides two selected words such as “online victimization”, “victim of cybercrime”, “phishing victimization”, “online romance victimization”, “cyberstalking victim”, “interpersonal cybercrime victimization”, or “sexting victimization”, the results, however, were not really appropriate. A lot of papers did not contain search keywords in their titles, abstracts, keywords and were not relavant to study topic. After searching with many different terms and comparing the results, the current study selected the two search terms for the most appropriate articles. The query result consisted of 962 documents. Basing on the result from preliminary searching, retrieved publications were refined automatically on WoS by criteria of timespan, document types, language, research areas, and WoS Index as presented in Table 1 . Accordingly, the criteria for automatic filter process were basic information of an articles and classified clearly in WoS system so the results reached high accuracy. The refined results are 473 articles.
After automatic filters, file of data was converted to Microsoft Excel 2016 for screening. The present study examined titles and abstracts of 473 articles to assess the eligibility of each publication according to the relevance with given topic. There are 387 articles are eligible,while 86 irrelevant publications were excluded.
Data analysis
Prior to data analysis, the raw data were cleaned in Microsoft Excel 2016. Different forms of the same author’s name were corrected for consistency, for example “Zhou, Zong-Kui” and “Zhou Zongkui”, “Van Cleemput, Katrien” and “Van Cleemput, K.”, “Williams, Matthew L.” and “Williams, Matthew”. Similarly, different keywords (single/plural or synonyms) used for the same concept were identified and standardized such as “victimization” and “victimisation”; “adolescent” and “adolescents”; “cyber bullying”, “cyber-bullying” and “cyberbullying”; “routine activity theory” and “routine activities theory”.
The data were processed by Microsoft Excel 2016 and VOS Viewer version 1.6.16; then it was analyzed according to three main aspects. First, descriptive statistic provided evidence for yearly distribution and growth trend of publications, frequency counts of citations, the influential authors, the predominant journals, the top institutions and countries/territories, most-cited publications. Second, co-authorship and co-occurrence analysis were constructed and visualized by VOS Viewer version 1.6.16 to explore the network collaborations. Finally, the current study also investigated research topics through content analysis of keywords. The authors’ keywords were classified into 15 themes, including: #1 cybercrime; #2 sample and demographic factors; #3 location; #4 theory; #5 methodology; #6 technology, platforms and related others; #7 psychology and mental health; #8 physical health; #9 family; #10 school; #11 society; #12 crimes and deviant behaviors; #13 victim; #14 prevention and intervention; and #15 others. Besides, the study also added other keywords from titles and abstracts basing on these themes, then indicated aspects examined in previous research.
In this section, all findings corresponding with four research questions identified at the ouset of this study would be illustrated (Fig. 1 ).
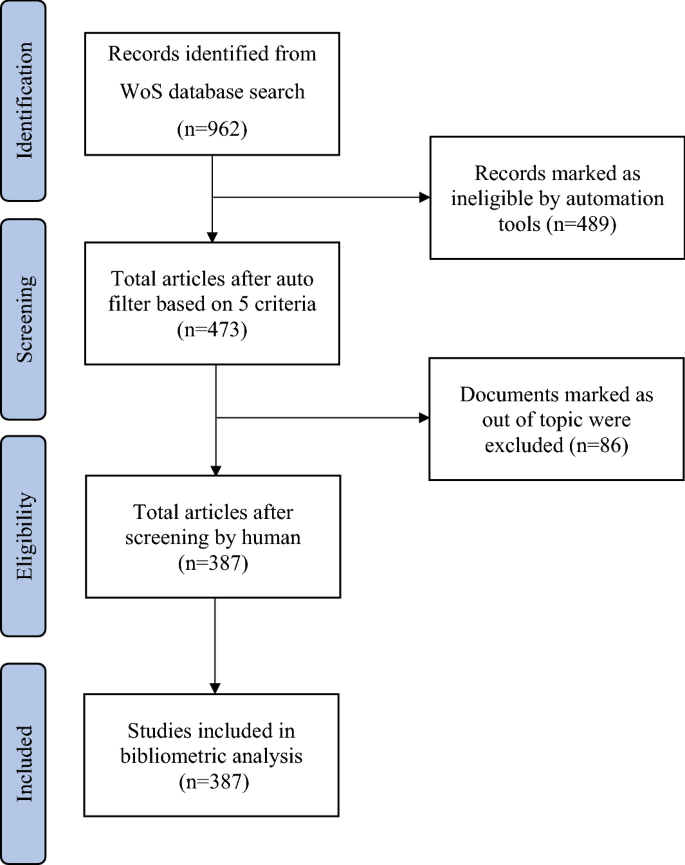
PRISMA diagram depicts data collection from WoS database
Distribution of publication
Distribution by year, institutions and countries.
Basing on retrieved data, it was witnessed an increasing trend of articles relevant to cybercrime victimization in SSCI list during the time of 2010–2020 but it had slight fluctuations in each year as shown in Fig. 2 . The total number of articles over this time was 387 items, which were broken into two sub-periods: 2010–2014 and 2015–2020. It is evident that the latter period demonstrated the superiority of the rate of articles (79.33%) compared to the previous period (20.67%). The yearly quantity of publications in this research subject was fewer than forty before 2015. Research of cybercrime victimization reached a noticeable development in 2016 with over fifty publications, remained the large number of publications in the following years and peaked at 60 items in 2018.
Annual distribution of publications
Distribution by institutions and countries
Table 2 shows the top contributing institutions according to the quantity of publications related to cybercrime victimization. Of the top institutions, four universities were from the USA, two ones were from Spain, two institutions were from Australia and the rest ones were from Czech Republic, Belgium, Greece, and Austria. Specifically, Masaryk University (17 documents) became the most productive publishing institution, closely followed by Michigan State University (16 documents). The third and fourth places were University of Antwerp (13 documents) and Weber State University (10 documents). Accordingly, the institutions from The USA and Europe occupied the vast majority.
In Table 2 , University of Seville (total citations: 495, average citations: 70.71) ranked first and University of Cordoba (total citations: 484, average citations: 60.50) stayed at the second place in both total citations and average citations.
Referring to distribution of publications by countries, there were 45 countries in database contributing to the literature of cybercrime victimization. The USA recorded the highest quantity of papers, creating an overwhelming difference from other countries (159 documents) as illustrated in Fig. 3 . Of the top productive countries, eight European countries which achieved total of 173 publications were England (39 documents), Spain (34 documents), Germany (22 documents), Netherlands (18 documents), Italy (17 documents) and Czech Republic (17 documents), Belgium (14 documents), Greece (12 documents). Australia ranked the fourth point (32 documents), followed by Canada (30 documents). One Asian country which came out seventh place, at the same position with Netherlands was China (18 documents).
Top productive countries based on the number of publications
Distribution by sources
Table 3 enumerates the top leading journals in the number of publications relevant to cybercrime victimization. The total publications of the first ranking journal— Computers in Human Behavior were 56, over twice as higher as the second raking journal— Cyberpsychology, Behavior and Social Networking (24 articles). Most of these journals have had long publishing history, starting their publications before 2000. Only three journals launched after 2000, consisting of Journal of School Violence (2002), Cyberpsychology: Journal of Psychosocial Research on Cyberspace (2007) and Frontiers in Psychology (2010). Besides, it is remarked that one third of the top journals focuses on youth related issues: Journal of Youth and Adolescence , Journal of Adolescence, School Psychology International and Journal of School Violence .
In Table 3 , relating to total citations, Computers in Human Behavior remained the first position with 2055 citations. Journal of Youth and Adolescence had total 1285 citations, ranked second and followed by Aggressive Behavior with 661 citations. In terms of average citations per documents, an article of Journal of Youth and Adolescence was cited 67.63 times in average, much higher than average citations of one in Computers in Human Behavior (36.70 times). The other journals which achieved the high number of average citations per document were School Psychology International (59.00 times), Journal of Adolescence (44.83 times) and Aggressive Behavior (44.07 times).
Distribution by authors
Table 4 displays ten productive authors based on article count; total citations of each author and their average citations per document are also included. Michelle F. Wright from Pennsylvania State University ranked first with twenty publications, twice as higher as the second positions, Thomas J. Holt (10 articles) from Michigan State University and Bradford W. Reyns (10 articles) from Weber State University. Rosario Ortega-Ruiz from University of Cordoba stayed at the third place in terms of total publications but the first place in aspect of total citations (483 citations) and the average citations (60.38 times).
Of the most productive authors based on total publications, there were three authors from universities in the USA; one from the university in Canada (Brett Holfeld); the others were from institutions in Euro, including Spain (Rosario Ortega-Ruiz), Greece (Constantinos M. Kokkinos) and Belgium (Heidi Vandebosch), Netherlands (Rutger Leukfeldt) and Austria (Takuya Yanagida and Christiane Spiel).
Most-cited publications
The most-cited literature items are displayed in Table 5 . The article which recorded the highest number of citations was ‘Psychological, Physical, and Academic Correlates of Cyberbullying and Traditional Bullying’ (442 citations) by Robin M. Kowalski et al. published in Journal of Adolescent Health , 2013. Seven of ten most-cited articles were about cyberbullying; focused on youth population; made comparisons between cyberbullying and traditional bullying; analyzed the impact of several factors such as psychological, physical, academic factors or use of Internet; discussed on preventing strategies. The other publications studied victimization of cyberstalking and cyber dating abuse. All most-cited articles were from 2015 and earlier.
Of the top productive authors, only Bradford W. Reyns had an article appeared in the group of most-cited publications. His article ‘Being Pursued Online: Applying Cyberlifestyle-Routine Activities Theory to Cyberstalking Victimization’ (2011) was cited 172 times.
- Co-authorship analysis
“Scientific collaboration is a complex social phenomenon in research” (Glänzel and Schubert 2006 , p. 257) and becomes the increasing trend in individual, institutional and national levels. In bibliometric analysis, it is common to assess the productivity and international collaboration of research; identify key leading researchers, institutions, or countries (E Fonseca et al. 2016 ) as well as potential collaborators in a specific scientific area (Romero and Portillo-Salido 2019 ) by co-authorship analysis which constructs networks of authors and countries (Eck and Waltman 2020 ).
This section analyses international collaboration relevant to research of cybercrime victimization among authors, institutions, and countries during 2010–2020 through visualization of VOS Viewer software.
Collaboration between authors
Referring to the threshold of choose in this analysis, minimum number of documents of author is three and there were 80 authors for final results. Figure 4 illustrates the relationships between 80 scientists who study in subject of cybercrime victimization during 2010–2020. It shows several big groups of researchers (Wright’s group, Vandebosch’s group, or Holt’s group), while numerous authors had limited or no connections to others (Sheri Bauman, Michelle K. Demaray or Jennifer D. Shapka).
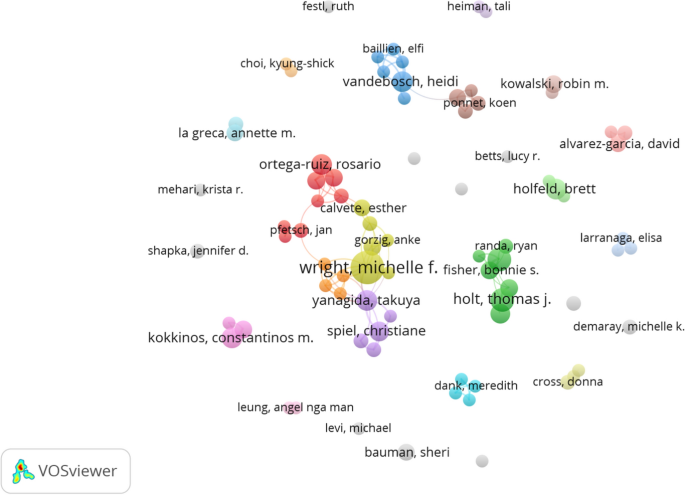
Collaboration among authors via network visualization (threshold three articles for an author, displayed 80 authors)
Figure 5 displayed a significant network containing 23 authors who were active in collaboration in detail. The displayed items in Fig. 5 are divided into five clusters coded with distinctive colors, including red, green, blue, yellow, and purple. Each author item was represented by their label and a circle; the size of label and circle are depended on the weight of the item, measured by the total publications (Eck and Waltman 2020 ). The thickness of lines depends on the strength of collaboration (Eck and Waltman 2020 ).
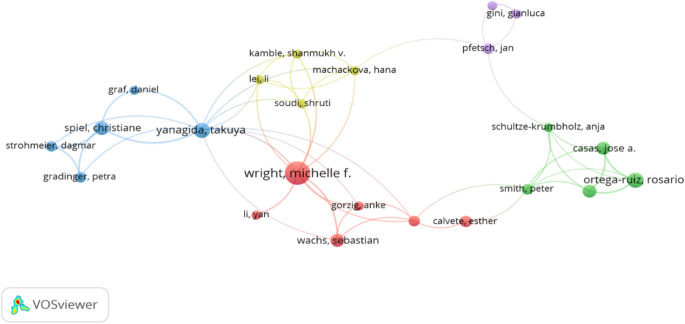
Collaboration among authors via network visualization (threshold three articles for an author, displayed 23 authors)
The most significant cluster was red one which is comprised of six researchers: Michelle F. Wright, Sebastian Wachs, Yan Li, Anke Gorzig, Manuel Gamez-Guadix and Esther Calvete. The remarked author for the red cluster was Michelle F. Wright whose value of total link strength is 24. She had the strongest links with Sebastian Wachs; closely link with Yan Li, Anke Gorzig, Manuel Gamez-Guadix and collaborated with authors of yellow cluster, including Shanmukh V. Kamble, Li Lei, Hana Machackova, Shruti Soudi as well as Takuya Yanagida of blue cluster. Michelle F. Wright who obtained the largest number of published articles based on criteria of this study made various connections with other scholars who were from many different institutions in the world. This is also an effective way to achieve more publications.
Takuya Yanagida was the biggest node for the blue cluster including Petra Gradinger, Daniel Graf, Christiane Spiel, Dagmar Strohmeier. Total link strength for Takuya Yanagida was 28; twelve connections. It is observed that Takuya Yanagida’ s research collaboration is definitely active. Besides, other research groups showed limited collaborations comparing with the red and blue ones.
Collaboration between institutions
The connections among 156 institutions which published at least two documents per one are shown in Fig. 6 . Interestingly, there is obvious connections among several distinctive clusters which were coded in color of light steel blue, orange, purple, steel blue, green, red, yellow, light red, dark turquoise, light blue, brown and light green. These clusters created a big chain of connected institutions and were in the center of the figure, while other smaller clusters or unlinked bubbles (gray color) were distributed in two sides. The biggest chain consisted of most of productive institutions such as Masaryk University, Michigan State University, University of Antwerp, Weber State University, University of Cordoba, Edith Cowan University, University of Cincinnati, University of Victoria, University of Vienna, and University of Seville.
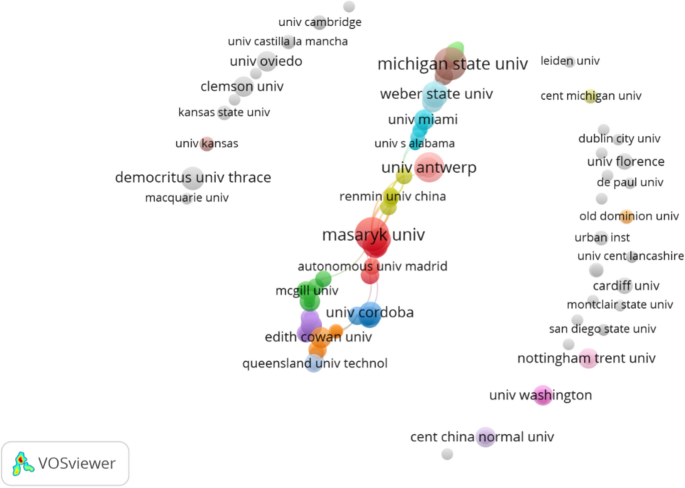
Collaboration among institutions via network visualization (threshold two articles for an institution, 156 institutions were displayed)
Light steel blue and orange clusters presented connections among organizations from Australia. Light green included institutions from Netherland, while turquoise and light blue consisted of institutions from the USA. Yellow cluster was remarked by the various collaborations among institutions from China and Hong Kong Special Administrative Region (Renmin University of China and South China Normal University, University of Hong Kong, the Hong Kong Polytechnic University and the Chinese University of Hong Kong), the USA (University of Virginia), Cyprus (Eastern Mediterranean University), Japan (Shizuoka University), India (Karnataka University) and Austria (University Applied Sciences Upper Austria). Central China Normal University is another Chinese institution which appeared in Fig. 5 , linking with Ministry of Education of the People’s Republic of China, Suny Stony Brook and University of Memphis from the USA.
Masaryk University and Michigan State University demonstrated their productivity in both the quantity of publications and the collaboration network. They were active in research collaboration, reaching twelve and eleven links, respectively, with different institutions, but focused much on networking with institutions in the USA and Europe.
Collaboration between countries
The collaboration among 45 countries which published at least one SSCI documents of cybercrime victimization during the given period was examined in VOS Viewer but just 42 items were displayed via overlay visualization. Figure 7 depicts the international collaborations among significant countries. The USA is the biggest bubble due to its biggest number of documents and shows connections with 26 countries/regions in Euro, Asia, Australia, Middle East. Excepting European countries, England collaborate with the USA, Australia, South Korea, Japan, Thailand, Singapore, Sri Lanka, and Colombia. Spain and Germany almost focus on research network within Euro. China has the strongest tie with the USA, link with Australia, Germany, Czech Republic, Austria, Cyprus and Turkey, Japan, Indian, Vietnam.
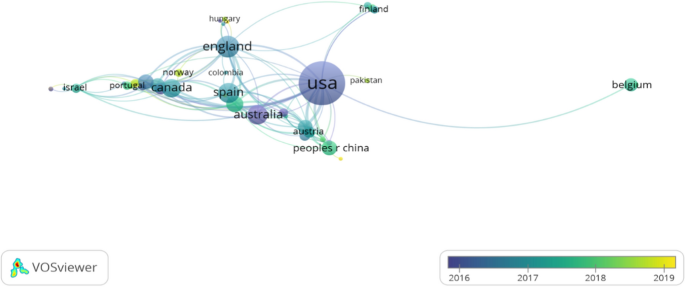
Collaboration among countries via overlay visualization
Color bar in Fig. 7 is determined by the average publication year of each country and the color of circles based on it. It is unsurprised that the USA, Australia, England, or Spain shows much research experience in this field and maintain the large number of publications steadily. Interestingly, although the average publication year of South Korea or Cyprus was earlier than other countries (purple color), their quantities of documents were moderate. The new nodes (yellow circles) in the map included Vietnam, Norway, Pakistan, Ireland, Scotland, Switzerland.
Keywords and co-occurrence
The present paper examined the related themes and contents in research of cybercrime victimization during 2010–2020 through collecting author keywords, adding several keywords from tiles and abstracts. Besides, this study also conducted co-occurrence analysis of author keywords to show the relationships among these keywords.
The keywords were collected and categorized into 15 themes in Table 6 , including cybercrime; sample and demographic factors; location; theory; methodology; technology, platform, and related others; psychology and mental health; physical health; family; school; society; crimes and other deviant behaviors; victim; prevention and intervention; and others.
In the theme of cybercrime, there were numerous types of cybercrimes such as cyberbullying, cyber aggression, cyberstalking, cyber harassment, sextortion and other cyber dating crimes, cyber fraud, identity theft, phishing, hacking, malware, or ransomware. Generally, the frequency of interpersonal cybercrimes or cyber-enable crimes was much higher than cyber-dependent crimes. Cyberbullying was the most common cybercrime in research.
Relating to sample and demographic factors, there were sample of children, adolescent, adults, and the elder who were divided into more detail levels in each research; however, adolescent was the most significant sample. Besides, demographic factor of gender received a remarked concern from scholars.
It is usual that most of the research were carried out in one country, in popular it was the USA, Spain, Germany, England, Australia, Canada or Netherland but sometimes the new ones were published such as Chile, Vietnam, Thailand or Singapore. It was witnessed that some studies showed data collected from a group of countries such as two countries (Canada and the United State), three countries (Israel, Litva, Luxembourg), four countries (the USA, the UK, Germany, and Finland), or six Europe countries (Spain, Germany, Italy, Poland, the United Kingdom and Greece).
A wide range of theories were applied in this research focusing on criminological and psychological theories such as Routine Activities Theory, Lifestyle—Routine Activities Theory, General Strain Theory, the Theory of Reasoned Action or Self-control Theory.
Table 6 indicated a lot of different research methods covering various perspective of cybercrime victimization: systematic review, questionnaire survey, interview, experiment, mix method, longitudinal study, or cross-national research; many kinds of analysis such as meta-analysis, social network analysis, latent class analysis, confirmatory factor analysis; and a wide range of measurement scales which were appropriate for each variable.
Topic of cybercrime victimization had connections with some main aspects of technology (information and communication technologies, internet, social media or technology related activities), psychology (self-esteem, fear, attitude, personality, psychological problems, empathy, perceptions or emotion), physical health, family (parents), school (peers, school climate), society (norms, culture, social bonds), victim, other crimes (violence, substance use), prevention and intervention.
Co-occurrence analysis was performed with keywords suggested by authors and the minimum number of occurrences per word is seven. The result showed 36 frequent keywords which clustered into five clusters as illustrated in Fig. 8 .
Co-occurrence between author keywords via network visualization (the minimum number of occurrences per word is seven, 36 keywords were displayed)
Figure 8 illustrates some main issues which were concerned in subject of cybercrime victimization, as well as the relationship among them. Fifteen most frequent keywords were presented by big bubbles, including: ‘cyberbullying’ (174 times), ‘cyber victimization’ (90 times), ‘adolescent’ (79 times), ‘bullying’ (66 times), ‘victimization’ (56 times), ‘cybercrime’ (40 times), ‘cyber aggression’ (37 times), ‘depression’ (23 times), ‘aggression’ (14 times), ‘routine activities theory’ (13 times), ‘cyberstalking’ (11 times), ‘gender’ (11 times), ‘longitudinal’ (10 times), ‘peer victimization’ (10 times) and ‘self-esteem’ (10 times).
‘Cyberbullying’ linked with many other keywords, demonstrating the various perspectives in research of this topic. The thick lines which linked ‘cyberbullying’ and ‘bullying’, ‘adolescent’, ‘cyber victimization’, ‘victimization’ showed the strong connections between them; there were close relationship between ‘cyber aggression’, ‘bystander”, ‘self-esteem’ or ‘moral disengagement’ and ‘cyberbullying’.
‘Cybercrime’ had strong links with ‘victimization’, ‘routine activities theory’. In Fig. 8 , the types of cybercrime which occurred at least seven times were: cyberbullying, cyber aggression, hacking, cyberstalking, and cyber dating abuse.
The increasing trend over the years reveals the increasing concern of scholarly community on this field, especially in the boom of information technology and other communication devices and the upward trend in research of cyberspace-related issues (Altarturi et al. 2020 ; Leung et al. 2017 ; Serafin et al. 2019 ). It predicts the growth of cybercrime victimization research in future.
Psychology was the more popular research areas in database, defeating criminology penology. As part of the ‘human factors of cybercrime’, human decision-making based on their psychological perspectives plays as a hot topic in cyber criminology (Leukfeldt and Holt 2020 ). Then, it is observed that journals in psychology field was more prevalent in top of productive sources. Besides, journal Computers in Human Behavior ranked first in total publications, but Journal of Youth and Adolescence ranked higher place in the average citations per document. Generally, top ten journals having highest number of publications on cybercrime victimization are highly qualified ones and at least 10 years in publishing industry.
The USA demonstrated its leading position in the studied domain in terms of total publications as well as the various collaborations with other countries. The publications of the USA occupied much higher than the second and third countries: England and Spain. It is not difficult to explain for this fact due to the impressive productivity of institutions and authors from the USA. A third of top twelve productive institutions were from the USA. Three leading positions of top ten productive authors based on document count were from institutions of the USA, number one was Michelle F. Wright; others were Thomas J. Holt and Bradford W. Reyns.
Furthermore, these authors also participated in significant research groups and become the important nodes in those clusters. The most noticeable authors in co-authors network were Michelle F. Wright. The US institutions also had strong links in research network. The USA was likely to be open in collaboration with numerous countries from different continents in the world. It was assessed to be a crucial partner for others in the international co-publication network (Glänzel and Schubert 2006 ).
As opposed to the USA, most of European countries prefer developing research network within Europe and had a limited collaboration with other areas. Australia, the USA, or Japan was in a small group of countries which had connections with European ones. Nevertheless, European countries still showed great contributions for research of cybercrime victimization and remained stable links in international collaboration. The prominent authors from Euro are Rosario Ortega-Ruiz, Constantinos M. Kokkinos or Rutger Leukfeldt.
It is obvious that the limited number of publications from Asia, Middle East, Africa, or other areas resulted in the uncomprehensive picture of studied subject. For example, in the Southeast Asia, Malaysia and Vietnam lacked the leading authors with their empirical studies to review and examine the nature of cybercrimes, though they are facing to practical challenges and potential threats in the cyberspace (Lusthaus 2020a , b ). The present study indicated that Vietnam, Ireland, or Norway was the new nodes and links in research network.
Several nations which had a small number of publications such as Vietnam, Thailand, Sri Lanka, or Chile started their journey of international publications. It is undeniable that globalization and the context of global village (McLuhan 1992 ) requires more understanding about the whole nations and areas. Conversely, each country or area also desires to engage in international publications. Therefore, new nodes and clusters are expected to increase and expand.
The findings indicated that cyberbullying was the most popular topic on research of cybercrime victimization over the given period. Over a half of most-cited publications was focus on cyberbullying. Additionally, ‘cyberbullying’ was the most frequent author keyword which co-occurred widely with distinctive keywords such as ‘victimization’, ‘adolescents’, ‘bullying’, ‘social media’, ‘internet’, ‘peer victimization’ or ‘anxiety’.
By reviewing keywords, several research gaps were indicated. Research samples were lack of population of the children and elders, while adolescent and youth were frequent samples of numerous studies. Although young people are most active in cyberspace, it is still necessary to understand other populations. Meanwhile, the elderly was assumed to use information and communication technologies to improve their quality of life (Tsai et al. 2015 ), their vulnerability to the risk of cybercrime victimization did not reduce. Those older women were most vulnerable to phishing attacks (Lin et al. 2019 ; Oliveira et al. 2017 ). Similarly, the population of children with distinctive attributes has become a suitable target for cybercriminals, particularly given the context of increasing online learning due to Covid-19 pandemic impacts. These practical gaps should be prioritized to focus on research for looking the suitable solutions in the future. Besides, a vast majority of research were conducted in the scope of one country; some studies collected cross-national data, but the number of these studies were moderate and focused much on developed countries. There are rooms for studies to cover several countries in Southeast Asia or South Africa.
Furthermore, although victims may be both individuals and organizations, most of research concentrated much more on individuals rather than organizations or companies. Wagen and Pieters ( 2020 ) indicated that victims include both human and non-human. They conducted research covering cases of ransomware victimization, Bonet victimization and high-tech virtual theft victimization and applying Actor-Network Theory to provide new aspect which did not aim to individual victims. The number of this kind of research, however, was very limited. Additionally, excepting cyberbullying and cyber aggression were occupied the outstanding quantity of research, other types of cybercrime, especially, e-whoring, or social media-related cybercrime should still be studied more in the future.
Another interesting topic is the impact of family on cybercrime victimization. By reviewing keyword, it is clear that the previous studies aimed to sample of adolescent, hence, there are many keywords linking with parents such as ‘parent-adolescent communication’, ‘parent-adolescent information sharing’, ‘parental mediation’, ‘parental monitoring of cyber behavior’, ‘parental style’. As mentioned above, it is necessary to research more on sample of the elder, then, it is also essential to find out how family members affect the elder’s cybercrime victimization.
It is a big challenge to deal with problems of cybercrime victimization because cybercrime forms become different daily (Näsi et al. 2015 ). Numerous researchers engage in understanding this phenomenon from various angles. The current bibliometric study assessed the scholarly status on cybercrime victimization during 2010–2020 by retrieving SSCI articles from WoS database. There is no study that applied bibliometric method to research on the examined subject. Hence, this paper firstly contributed statistical evidence and visualized findings to literature of cybercrime victimization.
Statistical description was applied to measure the productive authors, institutions, countries/regions, sources, and most-cited documents, mainly based on publication and citation count. The international collaborations among authors, institutions, and countries were assessed by co-authors, while the network of author keywords was created by co-occurrence analysis. The overall scholarly status of cybercrime victimization research was drawn clearly and objectively. The research trend, popular issues and current gaps were reviewed, providing numerous suggestions for policymakers, scholars, and practitioners about cyber-related victimization (Pickering and Byrne 2014 ). Accordingly, the paper indicated the most prevalent authors, most-cited papers but also made summary of contributions of previous research as well as identified research gaps. First, this article supports for PhD candidates or early-career researchers concerning about cybercrime victimization. Identifying the leading authors, remarked journals, or influencing articles, gaps related to a specific research topic is important and useful task for new researchers to start their academic journey. Although this information is relatively simple, it takes time and is not easy for newcomers to find out, especially for ones in poor or developing areas which have limited conditions and opportunities to access international academic sources. Thus, the findings in the current paper provided for them basic but necessary answers to conduct the first step in research. Secondly, by indicating research gaps in relevance to sample, narrow topics or scope of country, the paper suggests future study fulfilling them to complete the field of cybercrime victimization, especial calling for publications from countries which has had a modest position in global research map. Science requires the balance and diversity, not just focusing on a few developed countries or areas. Finally, the present study assists researchers and institutions to determined strategy and potential partners for their development of research collaborations. It not only improve productivity of publication but also create an open and dynamic environment for the development of academic field.
Despite mentioned contributions, this study still has unavoidable limitations. The present paper just focused on SSCI articles from WoS database during 2010–2020. It did not cover other sources of databases that are known such as Scopus, ScienceDirect, or Springer; other types of documents; the whole time; or articles in other languages excepting English. Hence it may not cover all data of examined subject in fact. Moreover, this bibliometric study just performed co-authorship and co-occurrence analysis. The rest of analysis such as citation, co-citation and bibliographic coupling have not been conducted. Research in the future is recommended to perform these kinds of assessment to fill this gap. To visualize the collaboration among authors, institutions, countries, or network of keywords, this study used VOS Viewer software and saved the screenshots as illustrations. Therefore, not all items were displayed in the screenshot figures.
Data availability
The datasets generated during and/or analyzed during the current study are available from the corresponding author on reasonable request.
In the ‘commemorating a decade in existence of the International Journal of Cyber Criminoogy’, Ngo and Jaishankar ( 2017 ) called for further research with focusing on five main areas in the Cyber Criminiology, including (1) defining and classifying cybercrime, (2) assessing the prevalence, nature, and trends of cybercrime, (3) advancing the field of cyber criminology, (4) documenting best practices in combating and preventing cybercrime, and (5) cybercrime and privacy issues.
Abdullah ATM, Jahan I (2020) Causes of cybercrime victimization: a systematic literature review. Int J Res Rev 7(5):89–98
Google Scholar
Al-Nemrat A, Benzaïd C (2015) Cybercrime profiling: Decision-tree induction, examining perceptions of internet risk and cybercrime victimisation. In: Proceedings—14th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, TrustCom 2015, vol 1, pp 1380–1385. https://doi.org/10.1109/Trustcom.2015.534
Alalehto TI, Persson O (2013) The Sutherland tradition in criminology: a bibliometric story. Crim Justice Stud 26(1):1–18
Article Google Scholar
Algarni A, Xu Y, Chan T (2017) An empirical study on the susceptibility to social engineering in social networking sites: the case of Facebook. Eur J Inf Syst 26(6):661–687
Altarturi HHM, Saadoon M, Anuar NB (2020) Cyber parental control: a bibliometric study. Child Youth Serv Rev. https://doi.org/10.1016/j.childyouth.2020.105134
Ariola B, Laure ERF, Perol ML, Talines PJ (2018) Cybercrime awareness and perception among Students of Saint Michael College of Caraga. SMCC Higher Educ Res J 1(1):1. https://doi.org/10.18868/cje.01.060119.03
Benson V, Saridakis G, Tennakoon H (2015) Purpose of social networking use and victimisation: are there any differences between university students and those not in HE? Comput Hum Behav 51:867–872
Brenner SW (2001) Is there such a thing as “rough”? Calif Crim Law Rev 4(1):348–349. https://doi.org/10.3109/09637487909143344
Chen X, Wang S, Tang Y, Hao T (2019) A bibliometric analysis of event detection in social media. Online Inf Rev 43(1):29–52. https://doi.org/10.1108/OIR-03-2018-0068
Choi K (2008) Computer Crime Victimization and Integrated Theory: an empirical assessment. Int J Cyber Criminol 2(1):308–333
Cojocaru I, Cojocaru I (2019) A bibliomentric analysis of cybersecurity research papers in Eastern Europe: case study from the Republic of Moldova. In: Central and Eastern European E|Dem and E|Gov Days, pp 151–161
Das B, Sahoo JS (2011) Social networking sites—a critical analysis of its impact on personal and social life. Int J Bus Soc Sci 2(14):222–228
Drew JM (2020) A study of cybercrime victimisation and prevention: exploring the use of online crime prevention behaviours and strategies. J Criminol Res Policy Pract 6(1):17–33. https://doi.org/10.1108/JCRPP-12-2019-0070
E Fonseca B, Sampaio, de Araújo Fonseca MV, Zicker F (2016). Co-authorship network analysis in health research: method and potential use. Health Res Policy Syst 14(1):1–10. https://doi.org/10.1186/s12961-016-0104-5
Feeley TH (2008) A bibliometric analysis of communication journals from 2002 to 2005. Hum Commun Res 34:505–520
Gan C, Wang W (2014) A bibliometric analysis of social media research from the perspective of library and information science. IFIP Adv Inf Commun Technol 445:23–32. https://doi.org/10.1007/978-3-662-45526-5_3
Glänzel W, Schubert A (2006) Analysing scientific networks through co-authorship. Handb Quant Sci Technol Res. https://doi.org/10.1007/1-4020-2755-9_12
Gogolin G (2010) The digital crime tsunami. Digit Investig 7(1–2):3–8. https://doi.org/10.1016/j.diin.2010.07.001
Holt TJ, Bossler AM (2009) Examining the applicability of lifestyle-routine activities theory for cybercrime victimization. Deviant Behav 30(1):1–25. https://doi.org/10.1080/01639620701876577
Holt TJ, Bossler AM (2014) An assessment of the current state of cybercrime scholarship. Deviant Behav 35(1):20–40. https://doi.org/10.1080/01639625.2013.822209
Ilievski A (2016) An explanation of the cybercrime victimisation: self-control and lifestile/routine activity theory. Innov Issues Approaches Soc Sci 9(1):30–47. https://doi.org/10.12959/issn.1855-0541.iiass-2016-no1-art02
Insa F (2007) The Admissibility of Electronic Evidence in Court (A.E.E.C.): Fighting against high-tech crime—results of a European study. J Digital Forensic Pract 1(4):285–289. https://doi.org/10.1080/15567280701418049
Jahankhani H (2013) Developing a model to reduce and/or prevent cybercrime victimization among the user individuals. Strategic Intell Manag. https://doi.org/10.1016/b978-0-12-407191-9.00021-1
Jamshed J, Naeem S, Ahmad K (2020) Analysis of Criminal Law Literature: a bibliometric study from 2010–2019. Library Philos Pract
Kim J, Kang S, Lee KH (2019) Evolution of digital marketing communication: Bibliometric analysis and networs visualization from key articles. J Bus Res
Kirwan GH, Fullwood C, Rooney B (2018) Risk factors for social networking site scam victimization among Malaysian students. Cyberpsychol Behav Soc Netw 21(2):123–128. https://doi.org/10.1089/cyber.2016.0714
Lee S-S, Choi KS, Choi S, Englander E (2019) A test of structural model for fear of crime in social networking sites A test of structural model for fear of crime in social networking sites. Int J Cybersecur Intell Cybercrime 2(2):5–22
Leukfeldt R, Holt T (eds) (2020) The human factor of cybercrime. Routledge, New York
Leukfeldt ER, Yar M (2016) Applying routine activity theory to cybercrime: a theoretical and empirical analysis. Deviant Behav 37(3):263–280. https://doi.org/10.1080/01639625.2015.1012409
Leung XY, Sun J, Bai B (2017) Bibliometrics of social media research: a co-citation and co-word analysis. Int J Hosp Manag 66:35–45. https://doi.org/10.1016/j.ijhm.2017.06.012
Li Q, Wei W, Xiong N, Feng D, Ye X, Jiang Y (2017) Social media research, human behavior, and sustainable society. Sustainability 9(3):384. https://doi.org/10.3390/su9030384
Lin T, Capecci DE, Ellis DM, Rocha HA, Dommaraju S, Oliveira DS, Ebner NC (2019) Susceptibility to spear-phishing emails: effects of internet user demographics and email content. ACM Trans Comput-Hum Interact 26(5):1–28. https://doi.org/10.1145/3336141
Luong TH (2021) Prevent and combat sexual assault and exploitation of children on cyberspace in Vietnam: situations, challenges, and responses. In: Elshenraki H (ed) Combating the exploitation of children in cyberspace: emerging research and opportunities. IGI Global, Hershey, pp 68–94
Chapter Google Scholar
Luong HT, Phan HD, Van Chu D, Nguyen VQ, Le KT, Hoang LT (2019) Understanding cybercrimes in Vietnam: from leading-point provisions to legislative system and law enforcement. Int J Cyber Criminol 13(2):290–308. https://doi.org/10.5281/zenodo.3700724
Lusthaus J (2020a) Cybercrime in Southeast Asia: Combating a Global Threat Locally. Retrieved from Canberra, Australia: https://s3-ap-southeast-2.amazonaws.com/ad-aspi/202005/Cybercrime%20in%20Southeast%20Asia.pdf?naTsKQp2jtSPYsWpSo4YmE1sVBNv_exJ
Lusthaus J (2020b) Modelling cybercrime development: the case of Vietnam. In: Leukfeldt R, Holt T (eds) The human factor of cybercrime. Routledge, New York, pp 240–257
Marsh I, Melville G (2008) Crime justice and the media. Crime Justice Med. https://doi.org/10.4324/9780203894781
Martí-Parreño J, Méndez-Ibáñezt E, Alonso-Arroyo A (2016) The use of gamification in education: a bibliometric and text mining analysis. J Comput Assist Learn
McLuhan M (1992) The Global Village: Transformations in World Life and Media in the 21st Century (Communication and Society). Oxford University Press, Oxford
Näsi M, Oksanen A, Keipi T, Räsänen P (2015) Cybercrime victimization among young people: a multi-nation study. J Scand Stud Criminol Crime Prev. https://doi.org/10.1080/14043858.2015.1046640
Ngo F, Jaishankar K (2017) Commemorating a decade in existence of the international journal of cyber criminology: a research agenda to advance the scholarship on cyber crime. Int J Cyber Criminol 11(1):1–9
Ngo F, Paternoster R (2011) Cybercrime victimization: an examination of individual and situational level factors. Int J Cyber Criminol 5(1):773
Nguyen VT, Luong TH (2020) The structure of cybercrime networks: transnational computer fraud in Vietnam. J Crime Justice. https://doi.org/10.1080/0735648X.2020.1818605
Oksanen A, Keipi T (2013) Young people as victims of crime on the internet: a population-based study in Finland. Vulnerable Child Youth Stud 8(4):298–309
Oliveira D, Rocha H, Yang H, Ellis D, Dommaraju S, Muradoglu M, Weir D, Soliman A, Lin T, Ebner N (2017) Dissecting spear phishing emails for older vs young adults: on the interplay of weapons of influence and life domains in predicting susceptibility to phishing. In: Conference on Human Factors in Computing Systems—Proceedings, 2017-May, 6412–6424. https://doi.org/10.1145/3025453.3025831
Orchard LJ, Fullwood C, Galbraith N, Morris N (2014) Individual differences as predictors of social networking. J Comput-Mediat Commun 19(3):388–402. https://doi.org/10.1111/jcc4.12068
Parrish JL Jr, Bailey JL, Courtney JF (2009) A personality based model for determining susceptibility to phishing attacks. University of Arkansas, Little Rock, pp 285–296
Pasadeos Y (1985) A bibliometric study of advertising citations. J Advert 14(4):52–59
Pickering C, Byrne J (2014) The benefits of publishing systematic quantitative literature reviews for PhD candidates and other early-career researchers. Higher Educ Res Devel ISSN 33(3):534–548
Reyns BW, Fisher BS, Bossler AM, Holt TJ (2019) Opportunity and Self-control: do they predict multiple forms of online victimization? Am J Crim Justice 44(1):63–82. https://doi.org/10.1007/s12103-018-9447-5
Romero L, Portillo-Salido E (2019) Trends in sigma-1 receptor research: a 25-year bibliometric analysis. Front Pharmacol. https://doi.org/10.3389/fphar.2019.00564
Saad ME, Huda Sheikh Abdullah SN, Murah MZ (2018) Cyber romance scam victimization analysis using Routine Activity Theory versus apriori algorithm. Int J Adv Comput Sci Appl 9(12):479–485. https://doi.org/10.14569/IJACSA.2018.091267
Saridakis G, Benson V, Ezingeard JN, Tennakoon H (2016) Individual information security, user behaviour and cyber victimisation: an empirical study of social networking users. Technol Forecast Soc Change 102:320–330. https://doi.org/10.1016/j.techfore.2015.08.012
Seng S, Wright M, Al-Ameen MN (2018) Understanding users’ decision of clicking on posts in facebook with implications for phishing. Workshop on Technology and Consumer Protection (ConPro 18), May, 1–6
Serafin MJ, Garcia-Vargas GR, García-Chivita MDP, Caicedo MI, Correra JC (2019) Cyberbehavior: a bibliometric analysis. Annu Rev Cyber Ther Telemed 17:17–24. https://doi.org/10.31234/osf.io/prfcw
Skinner WF, Fream AM (1997) A social learning theory analysis of computer crime among college students. J Res Crime Delinq 34(4):495–518. https://doi.org/10.1177/0022427897034004005
Tsai H, Yi S, Shillair R, Cotten SR, Winstead V, Yost E (2015) Getting grandma online: are tablets the answer for increasing digital inclusion for older adults in the US? Educ Gerontol 41(10):695–709. https://doi.org/10.1080/03601277.2015.1048165
van Eck NJ, Waltman L (2020) Manual for VOSviewer version 1.6.16
Van Wilsem J (2013) “Bought it, but never got it” assessing risk factors for online consumer fraud victimization. Eur Sociol Rev 29(2):168–178. https://doi.org/10.1093/esr/jcr053
van der Wagen W, Pieters W (2020) The hybrid victim: re-conceptualizing high-tech cyber victimization through actor-network theory. Eur J Criminol 17(4):480–497. https://doi.org/10.1177/1477370818812016
Vishwanath A (2015) Habitual Facebook use and its impact on getting deceived on social media. J Comput-Mediat Commun 20(1):83–98. https://doi.org/10.1111/jcc4.12100
Wall D (2001) Crime and the Internet: Cybercrime and cyberfears, 1st edn. Routledge, London
Wall D (2004) What are cybercrimes? Crim Justice Matters 58(1):20–21
Whitty MT, Buchanan T (2012) The online romance scam: a serious cybercrime. Cyberpsychol Behav Soc Netw 15(3):181–183. https://doi.org/10.1089/cyber.2011.0352
You GR, Sun X, Sun M, Wang JM, Chen YW (2014) Bibliometric and social network analysis of the SoS field. In: Proceedings of the 9th International Conference on System of Systems Engineering: The Socio-Technical Perspective, SoSE 2014, 13–18. https://doi.org/10.1109/SYSOSE.2014.6892456
Zyoud SH, Sweileh WM, Awang R, Al-Jabi SW (2018) Global trends in research related to social media in psychology: Mapping and bibliometric analysis. Int J Ment Health Syst 12(1):1–8. https://doi.org/10.1186/s13033-018-0182-6
Download references
Author information
Authors and affiliations.
School of Journalism and Communication, Huazhong University of Science and Technology, Wuhan, Hubei, China
Huong Thi Ngoc Ho
School of Global, Urban and Social Studies, RMIT University, Melbourne, Australia
Hai Thanh Luong
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Hai Thanh Luong .
Ethics declarations
Conflict of interest.
The authors declare that they have no competing interest.
Rights and permissions
Reprints and permissions
About this article
Ho, H.T.N., Luong, H.T. Research trends in cybercrime victimization during 2010–2020: a bibliometric analysis. SN Soc Sci 2 , 4 (2022). https://doi.org/10.1007/s43545-021-00305-4
Download citation
Received : 13 September 2021
Accepted : 15 December 2021
Published : 06 January 2022
DOI : https://doi.org/10.1007/s43545-021-00305-4
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Bibliometric analysis
- Web of science
- Co-occurrence analysis
- Find a journal
- Publish with us
- Track your research

- High contrast
- Press Centre
Search UNICEF
Cyberbullying: what is it and how to stop it, what teens want to know about cyberbullying..

- Available in:
We brought together UNICEF specialists, international cyberbullying and child protection experts, and teamed up with Facebook, Instagram, Snapchat, TikTok and X to answer some of the most common questions about online bullying and give advice on ways to deal with it.
What is cyberbullying?
Cyberbullying is bullying with the use of digital technologies. It can take place on social media, messaging platforms, gaming platforms and mobile phones. It is repeated behaviour, aimed at scaring, angering or shaming those who are targeted. Examples include:
- spreading lies about or posting embarrassing photos or videos of someone on social media
- sending hurtful, abusive or threatening messages, images or videos via messaging platforms
- impersonating someone and sending mean messages to others on their behalf or through fake accounts.
Face-to-face bullying and cyberbullying can often happen alongside each other. But cyberbullying leaves a digital footprint – a record that can prove useful and provide evidence to help stop the abuse.
If you are worried about your safety or something that has happened to you online, you can seek help by calling your national helpline . If your country does not have a helpline, please urgently speak to an adult you trust or seek professional support from trained and experienced carers.
The top questions on cyberbullying
- Am I being bullied online? How do you tell the difference between a joke and bullying?
- What are the effects of cyberbullying?
- How can cyberbullying affect my mental health?
- Who should I talk to if someone is bullying me online? Why is reporting important?
- I’m experiencing cyberbullying, but I’m afraid to talk to my parents about it. How can I approach them?
- How can I help my friends report a case of cyberbullying especially if they don’t want to do it?
- How do we stop cyberbullying without giving up access to the internet?
- How do I prevent my personal information from being used to manipulate or humiliate me on social media?
- Is there a punishment for cyberbullying?
- Technology companies don’t seem to care about online bullying and harassment. Are they being held responsible?
- Are there any online anti-bullying tools for children or young people?

1. Am I being bullied online? How do you tell the difference between a joke and bullying?
Unicef: .
All friends joke around with each other, but sometimes it’s hard to tell if someone is just having fun or trying to hurt you, especially online. Sometimes they’ll laugh it off with a “just kidding,” or “don’t take it so seriously.”
But if you feel hurt or think others are laughing at you instead of with you, then the joke has gone too far. If it continues even after you’ve asked the person to stop and you are still feeling upset about it, then this could be bullying.
And when the bullying takes place online, it can result in unwanted attention from a wide range of people including strangers. Wherever it may happen, if you are not happy about it, you should not have to stand for it.
Call it what you will – if you feel bad and it doesn’t stop, then it’s worth getting help. Stopping cyberbullying is not just about calling out bullies, it’s also about recognizing that everyone deserves respect – online and in real life.
> Back to top

2. What are the effects of cyberbullying?
When bullying happens online it can feel as if you’re being attacked everywhere, even inside your own home. It can seem like there’s no escape. The effects can last a long time and affect a person in many ways:
- Mentally – feeling upset, embarrassed, stupid, even afraid or angry
- Emotionally – feeling ashamed or losing interest in the things you love
- Physically – tired (loss of sleep), or experiencing symptoms like stomach aches and headaches
The feeling of being laughed at or harassed by others, can prevent people from speaking up or trying to deal with the problem. In extreme cases, cyberbullying can even lead to people taking their own lives.
Cyberbullying can affect us in many ways. But these can be overcome and people can regain their confidence and health.

3. How can cyberbullying affect my mental health?
When you experience cyberbullying you might start to feel ashamed, nervous, anxious and insecure about what people say or think about you. This can lead to withdrawing from friends and family, negative thoughts and self-talk, feeling guilty about things you did or did not do, or feeling that you are being judged negatively. Feeling lonely, overwhelmed, frequent headaches, nausea or stomachaches are also common.
You can lose your motivation to do the things that you usually enjoy doing and feel isolated from the people you love and trust. This can perpetuate negative feelings and thoughts which can adversely affect your mental health and well-being.
Skipping school is another common effect of cyberbullying and can affect the mental health of young people who turn to substances like alcohol and drugs or violent behaviour to deal with their psychological and physical pain. Talking to a friend, family member or school counsellor you trust can be a first step to getting help.
The effects of cyberbullying on mental health can vary depending on the medium through which it happens. For example, bullying via text messaging or through pictures or videos on social media platforms has proven to be very harmful for adolescents.
Cyberbullying opens the door to 24-hour harassment and can be very damaging. That’s why we offer in-app mental health and well-being support through our feature “ Here For You .” This Snapchat portal provides resources on mental health, grief, bullying, harassment, anxiety, eating disorders, depression, stress, and suicidal thoughts. It was developed in partnership with leading international advocacy and mental health organizations to help Snapchatters contend with some very real issues. Still, our foundational piece of guidance for any well-being issue is to talk to someone: a friend, parent, caregiver, trusted adult – anyone whom you trust to listen.
At Snap, nothing is more important than the safety and well-being of our community. Reach out and tell us how we might be able to help.
Cyberbullying has the potential of having a negative impact on people's mental health. It's why it's so important that you reach out to someone you trust – whether it's a parent, teacher, friend or caregiver – and let them know what you're going through so that they can help you.
The well-being of our community matters hugely to us, and we recognise that cyberbullying can have an adverse impact on people's mental health. As well as taking strong action against content or behaviour that seeks to shame, bully or harass members of our community, we have partnered with experts to develop our well-being guide to help people learn more about improving their well-being, and keep TikTok a safe and inclusive home for our community.

4. Who should I talk to if someone is bullying me online? Why is reporting important?
If you think you’re being bullied, the first step is to seek help from someone you trust such as your parents, a close family member or another trusted adult.
In your school you can reach out to a counsellor, the sports coach or your favourite teacher – either online or in person.
And if you are not comfortable talking to someone you know, search for a helpline in your country to talk to a professional counsellor.
If the bullying is happening on a social platform, consider blocking the bully and formally reporting their behaviour on the platform itself. Social media companies are obligated to keep their users safe.
For bullying to stop, it needs to be identified and reporting it is key.
It can be helpful to collect evidence – text messages and screen shots of social media posts – to show what’s been going on.
For bullying to stop, it needs to be identified and reporting it is key. It can also help to show the bully that their behaviour is unacceptable.
If you are in immediate danger, then you should contact the police or emergency services in your country.
Facebook/Instagram
At Meta, we take bullying and harassment situations seriously. Bullying and harassment is a unique challenge and one of the most complex issues to address because context is critical. We work hard to enforce against this content while also equipping our community with tools to protect themselves in ways that work best for them.
If you're experiencing bullying online, we encourage you to talk to a parent, teacher or someone else you can trust – you have a right to be safe and supported.
We also make it easy to report bullying directly within Facebook or Instagram. You can send our team a report from a post, comment, story or direct message (DM). Your report is anonymous; the account you reported won’t see who reported them. We have a team who reviews these reports 24/7 around the world in 70+ languages and we will remove anything that violates our policies.
Meta’s Family Center offers resources, insights and expert guidance to help parents, guardians and trusted adults support their teen’s online experiences across our technologies. Additionally, the Meta Safety Center provides bullying prevention resources that can help teens seeking support for issues related to bullying like what to do if you or a friend is being bullied or if you've been called a bully. For educators , we have expert-backed tips on how to proactively handle and work to implement bullying prevention strategies
Bullying is something no one should have to experience, either in person or online.
Snapchat’s Community Guidelines clearly and explicitly prohibit bullying, intimidation, and harassment of any kind. We don’t want it on the platform; it’s not in keeping with why Snapchat was created and designed. Learn more here .
Letting us know when you experience or witness someone breaking our rules allows us to take action, which helps to protect you and other members of our community. In addition to reporting violating content or behaviour to Snapchat, speak with a friend, parent, caregiver, or other trusted adult. Our goal is for everyone to stay safe and have fun!
Everyone has the right to feel safe and to be treated with respect and dignity. Bullying and harassment are incompatible with the inclusive environment we aim to foster on TikTok.
If you ever feel someone is bullying you or otherwise being inappropriate, reach out to someone you trust - for example, a parent, a teacher or a caregiver – who can provide support.
We deploy both technology and thousands of safety professionals to help keep bullying off TikTok. We also encourage our community members to make use of the easy in-app reporting tools to alert us if they or someone they know has experienced bullying. You can report videos, comments, accounts and direct messages so that we can take appropriate action and help keep you safe. Reports are always confidential.
You can find out more in our Bullying Prevention guide for teens, caregivers, and educators on how to identify and prevent bullying, and provide support.
Being the target of bullying online is not easy to deal with. If you are being cyberbullied, the most important thing to do is to ensure you are safe. It’s essential to have someone to talk to about what you are going through. This may be a teacher, another trusted adult, or a parent. Talk to your parents and friends about what to do if you or a friend are being cyberbullied.
We encourage people to report accounts to us that may break our rules . You can do this on our Help Center or through the in-post reporting mechanism by clicking on the “Report a post” option.
Last updated: January 2022.

5. I’m experiencing cyberbullying, but I’m afraid to talk to my parents about it. How can I approach them?
If you are experiencing cyberbullying, speaking to a trusted adult – someone you feel safe talking to – is one of the most important first steps you can take.
Talking to parents isn’t easy for everyone. But there are things you can do to help the conversation. Choose a time to talk when you know you have their full attention. Explain how serious the problem is for you. Remember, they might not be as familiar with technology as you are, so you might need to help them to understand what’s happening.
They might not have instant answers for you, but they are likely to want to help and together you can find a solution. Two heads are always better than one! If you are still unsure about what to do, consider reaching out to other trusted people . There are often more people who care about you and are willing to help than you might think!

6. How can I help my friends report a case of cyberbullying especially if they don’t want to do it?
Anyone can become a victim of cyberbullying. If you see this happening to someone you know, try to offer support.
It is important to listen to your friend. Why don’t they want to report being cyberbullied? How are they feeling? Let them know that they don’t have to formally report anything, but it’s crucial to talk to someone who might be able to help.
Anyone can become a victim of cyberbullying.
Remember, your friend may be feeling fragile. Be kind to them. Help them think through what they might say and to whom. Offer to go with them if they decide to report. Most importantly, remind them that you’re there for them and you want to help.
If your friend still does not want to report the incident, then support them in finding a trusted adult who can help them deal with the situation. Remember that in certain situations the consequences of cyberbullying can be life threatening.
Doing nothing can leave the person feeling that everyone is against them or that nobody cares. Your words can make a difference.
We know that it can be hard to report bullying, but everyone deserves to feel safe online. If your friend is experiencing cyberbullying, encourage them to talk to a parent, a teacher or an adult they trust.
Reporting content or accounts to Facebook or Instagram is anonymous and can help us better keep our platforms safe. Bullying and harassment are highly personal by nature, so in many instances, we need a person to report this behaviour to us before we can identify or remove it. You can report something you experience yourself, but it’s also just as easy to submit a report for one of your friends. You can find more information on how to report something on our How to Report Bullying section at the Meta Safety Center.
You and your friends may be reluctant to report to a technology platform for any number of reasons, but it’s important to know that reporting on Snapchat is confidential and easy. And remember: You can report Snaps (photos and videos), Chats (messages) and accounts – about your own experiences or on behalf of someone else.
In the more public places of Snapchat, like Stories and Spotlight, simply press and hold on the piece of content and a card with “Report Tile” (as one option) will appear in red. Click that link and our reporting menu will appear. Bullying and harassment are among the first categories in the reporting list. Just follow the prompts and provide as much information as you can about the incident. We appreciate you doing your part to help us protect the Snapchat community!
If you believe another member of the TikTok community is being bullied or harassed, there are ways you can provide support. For example, you can make a confidential report on TikTok so that we take appropriate action and help keep your friend safe.
If you know the person, consider checking in with them and encourage them to read our Bullying Prevention guide so they can find out more information about how to identify bullying behaviour and take action.
If your friends are experiencing cyberbullying, encourage them to talk to a parent, a teacher or an adult they trust.
If a friend of yours does not want to report their experience, you can submit a bystander report on their behalf. This can include reports of private information , non -consensual nudity or impersonation.

7. How do we stop cyberbullying without giving up access to the Internet?
Being online has so many benefits. However, like many things in life, it comes with risks that you need to protect against.
If you experience cyberbullying, you may want to delete certain apps or stay offline for a while to give yourself time to recover. But getting off the Internet is not a long-term solution. You did nothing wrong, so why should you be disadvantaged? It may even send the bullies the wrong signal — encouraging their unacceptable behaviour.
We need to be thoughtful about what we share or say that may hurt others.
We all want cyberbullying to stop, which is one of the reasons reporting cyberbullying is so important. But creating the Internet we want goes beyond calling out bullying. We need to be thoughtful about what we share or say that may hurt others. We need to be kind to one another online and in real life. It's up to all of us!
We’re continuously developing new technologies to encourage positive interactions and take action on harmful content, and launching new tools to help people have more control over their experience. Here are some tools you can use:
- Comment warnings: When someone writes a caption or a comment that our AI detects as potentially offensive or intended to harass, we will show them an alert that asks them to pause and reflect on whether they would like to edit their language before it’s posted.
- Comment and message controls: Comments with common offensive words, phrases or emojis, and abusive messages or messages from strangers can be automatically hidden or filtered out with the ‘ Hidden words ’ setting, which is defaulted on for all people. If you want an even more personalized experience, you can create a custom list of emojis, words or phrases you don’t want to see, and comments containing these terms won’t appear under your posts and messages will be sent to a filtered inbox. All Instagram accounts have the option to switch off DMs from people they don’t follow. Messenger also gives you the option to ignore a conversation and automatically move it out of your inbox, without having to block the sender.
- Block and Mute: You can always block or mute an account that is bullying you, and that account will not be notified. When you block someone on Instagram, you’ll also have the option to block other accounts they may have or create, making it more difficult for them to interact with you.
- Restrict: With ‘Restrict,’ you can protect your account from unwanted interactions in a quieter, or more subtle way. Once Restrict is enabled, comments on your posts from a person you have restricted will only be visible to that person. You can choose to view the comment by tapping “See Comment”; approve the comment so everyone can see it; delete it; or ignore it. You won’t receive any notifications for comments from a restricted account.
- Limits: You can automatically hide comments and DM requests from people who don’t follow you, or who only recently followed you. If you’re going through an influx of unwanted comments or messages — or think you may be about to — you can turn on Limits and avoid it.
Our priority is to foster a welcoming and safe environment where people feel free to express themselves authentically. Our Community Guidelines make clear that we do not tolerate members of our community being shamed, bullied or harassed.
We use a combination of technology and moderation teams to help us identify and remove abusive content or behaviour from our platform.
We also provide our community with an extensive range of tools to help them better control their experience – whether it's control over exactly who can view and interact with your content or filtering tools to help you stay in control of comments. You can find out about them on our Safety Centre .
Since hundreds of millions of people share ideas on X every day, it’s no surprise that we don’t all agree with each other all the time. That’s one of the benefits of a public conversation in that we can all learn from respectful disagreements and discussions.
But sometimes, after you’ve listened to someone for a while, you may not want to hear them anymore. Their right to express themselves doesn’t mean you’re required to listen. If you see or receive a reply you don’t like, unfollow and end any communication with that account. If the behaviour continues, it is recommended that you block the account . If you continue receiving unwanted, targeted and continuous replies on X, consider reporting the behaviour to X here .
We are also working proactively to protect people using our service through a combination of human review and technology. Learn more about how to feel safer on X here .

8. How do I prevent my personal information from being used to manipulate or humiliate me on social media?
Think twice before posting or sharing anything on digital platforms – it may be online forever and could be used to harm you later. Don’t give out personal details such as your address, telephone number or the name of your school.
Learn about the privacy settings of your favourite social media apps. Here are some actions you can take on many of them:
- You can decide who can see your profile, send you direct messages or comment on your posts by adjusting your account privacy settings.
- You can report hurtful comments, messages, photos and videos and request they be removed.
- Besides ‘unfriending’, you can completely block people to stop them from seeing your profile or contacting you.
- You can also choose to have comments by certain people to appear only to them without completely blocking them.
- You can delete posts on your profile or hide them from specific people.
On most of your favourite social media, people aren't notified when you block, restrict or report them.

9. Is there a punishment for cyberbullying?
Most schools take bullying seriously and will take action against it. If you are being cyberbullied by other students, report it to your school.
People who are victims of any form of violence, including bullying and cyberbullying, have a right to justice and to have the offender held accountable.
Laws against bullying, particularly on cyberbullying, are relatively new and still do not exist everywhere. This is why many countries rely on other relevant laws, such as ones against harassment, to punish cyberbullies.
In countries that have specific laws on cyberbullying, online behaviour that deliberately causes serious emotional distress is seen as criminal activity. In some of these countries, victims of cyberbullying can seek protection, prohibit communication from a specified person and restrict the use of electronic devices used by that person for cyberbullying, temporarily or permanently.
However, it is important to remember that punishment is not always the most effective way to change the behaviour of bullies. Sometimes, focusing on repairing the harm and mending the relationship can be better.
On Facebook, we have a set of Community Standards , and on Instagram, we have Community Guidelines . We take action when we are aware of content that violates these policies, like in the case of bullying or harassment, and we are constantly improving our detection tools so we can find this content faster.
Bullying and harassment can happen in many places and come in many different forms from making threats and releasing personally identifiable information to sending threatening messages and making unwanted malicious contact. We do not tolerate this kind of behavior because it prevents people from feeling safe and respected on our apps.
Making sure people don’t see hateful or harassing content in direct messages can be challenging, given they’re private conversations, but we are taking steps to take tougher action when we become aware of people breaking our rules. If someone continues to send violating messages, we will disable their account. We’ll also disable new accounts created to get around our messaging restrictions and will continue to disable accounts we find that are created purely to send harmful messages.
On Snapchat, reports of cyberbullying are reviewed by Snap’s dedicated Trust & Safety teams, which operate around the clock and around the globe. Individuals found to be involved in cyberbullying may be given a warning, their accounts might be suspended or their accounts could be shut down completely.
We recommend leaving any group chat where bullying or any unwelcome behaviour is taking place and please report the behaviour and/or the account to us.
Our Community Guidelines define a set of norms and common code of conduct for TikTok and they provide guidance on what is and is not allowed to make a welcoming space for everyone. We make it clear that we do not tolerate members of our community being shamed, bullied or harassed. We take action against any such content and accounts, including removal.
We strongly enforce our rules to ensure all people can participate in the public conversation freely and safely. These rules specifically cover a number of areas including topics such as:
- Child sexual exploitation
- Abuse/harassment
- Hateful conduct
- Suicide or self-harm
- Sharing of sensitive media, including graphic violence and adult content
As part of these rules, we take a number of different enforcement actions when content is in violation. When we take enforcement actions, we may do so either on a specific piece of content (e.g., an individual post or Direct Message) or on an account.
You can find more on our enforcement actions here .

10. Technology companies don’t seem to care about online bullying and harassment. Are they being held responsible?
Technology companies are increasingly paying attention to the issue of online bullying.
Many of them are introducing ways to address it and better protect their users with new tools, guidance and ways to report online abuse.
But it is true that more is needed. Many young people experience cyberbullying every day. Some face extreme forms of online abuse. Some have taken their own lives as a result.
Technology companies have a responsibility to protect their users especially children and young people.
It is up to all of us to hold them accountable when they’re not living up to these responsibilities.

11. Are there any online anti-bullying tools for children or young people?
Each social platform offers different tools (see available ones below) that allow you to restrict who can comment on or view your posts or who can connect automatically as a friend, and to report cases of bullying. Many of them involve simple steps to block, mute or report cyberbullying. We encourage you to explore them.
Social media companies also provide educational tools and guidance for children, parents and teachers to learn about risks and ways to stay safe online.
Also, the first line of defense against cyberbullying could be you. Think about where cyberbullying happens in your community and ways you can help – by raising your voice, calling out bullies, reaching out to trusted adults or by creating awareness of the issue. Even a simple act of kindness can go a long way.
The first line of defense against cyberbullying could be you.
If you are worried about your safety or something that has happened to you online, urgently speak to an adult you trust. Many countries have a special helpline you can call for free and talk to someone anonymously. Visit United for Global Mental Health to find help in your country.
We have a number of anti-bullying tools across Facebook and Instagram:
- You can block people, including any existing and new accounts they might create.
- You can mute an account and that account will not be notified.
- You can limit unwanted interactions for a period of time by automatically hiding comments and message requests from people who don’t follow you, or who only recently followed you.
- You can use ‘ Restrict ’ to discreetly protect your account without that person being notified.
- You can moderate comments on your own posts.
- You can modify your settings so that only people you follow can send you a direct message.
- We will notify someone when they’re about to post something that might cross the line, encouraging them to reconsider.
- We automatically filter out comments and message requests that don’t go against our Community Guidelines but may be considered inappropriate or offensive. You can also create your own custom list of emojis, words or phrases that you don’t want to see.
For more tips and ideas, visit Instagram’s Safety page and Facebook’s Bullying Prevention Hub . We also offer resources, insights and expert guidance for parents and guardians on our Family Center .
We want teens and young adults to be aware of the blocking and removal functions on Snapchat. Clicking on the person’s avatar will bring up a three-dot menu in the upper right-hand corner. Opening that menu offers the option of “Manage Friendship,” which, in turn, offers the ability to Report, Block or Remove the person as a friend. Know that if you block someone, they will be told that their Snaps and Chats to you will be delivered once the relationship is restored.
It’s also a good idea to check privacy settings to ensure they continue to be set to the default setting of “Friends Only.” This way, only people you’ve added as Friends can send you Snaps and Chats.
We also recommend reviewing your Friends’ list from time to time to ensure it includes those people you still want to be friends with on Snapchat.
Alongside the work that our safety teams do to help keep bullying and harassment off our platform, we provide an extensive range of tools to help you control your TikTok experience. You can find these in full on our Safety Centre . Here are a few highlights:
- You can restrict who comments on your videos to no one, just friends or everyone (for those aged under 16, the everyone setting is not available)
- You can filter all comments or those with specific keywords that you choose. By default, spam and offensive comments are hidden from users when we detect them.
- You can delete or report multiple comments at once, and you can block accounts that post bullying or other negative comments in bulk too, up to 100 at a time.
- A comment prompt asks people to reconsider posting a comment that may be inappropriate or unkind, reminding them of our Community Guidelines and allowing them to edit their comments before sharing.
We want everybody to be safe on X. We continue to launch and improve tools for people to feel safer, be in control and manage their digital footprint. Here are some safety tools anyone on X can use:
- Select who can reply to your posts – either everyone, only people you follow or only people you mention
- Mute – removing an account's posts from your timeline without unfollowing or blocking that account
- Block – restricting specific accounts from contacting you, seeing your posts, and following you
- Report – filing a report about abusive behaviour
- Safety mode – a feature that temporarily blocks accounts for using potentially harmful language or sending repetitive and uninvited replies or mentions.
With special thanks to: Meta, Snap, TikTok and X (formerly known as Twitter). Last updated: February 2024.
To anyone who has ever been bullied online: You are not alone
TikTok stars Charli and Dixie D'Amelio open up about their personal experience of being bullied and share tips on how to make the internet a better place.
Reporting abuse and safety resources
Facebook instagram kik snapchat, tiktok tumblr wechat whatsapp youtube x, take action to stop cyberbullying.
The consequences of cyberbullying can be devastating. Youth can take action to stop it
5 ways to support your mental health online
Tips on how to look after yourself and others
Contribute to Kindly - help stop cyberbullying
Kindly - A UNICEF initiative to end cyberbullying — one message at a time
Mental health and well-being
Tips and resources to help you support your child and yourself
- Type 2 Diabetes
- Heart Disease
- Digestive Health
- Multiple Sclerosis
- COVID-19 Vaccines
- Occupational Therapy
- Healthy Aging
- Health Insurance
- Public Health
- Patient Rights
- Caregivers & Loved Ones
- End of Life Concerns
- Health News
- Thyroid Test Analyzer
- Doctor Discussion Guides
- Hemoglobin A1c Test Analyzer
- Lipid Test Analyzer
- Complete Blood Count (CBC) Analyzer
- What to Buy
- Editorial Process
- Meet Our Medical Expert Board
Cyberbullying: Everything You Need to Know
- Cyberbullying
- How to Respond
Cyberbullying is the act of intentionally and consistently mistreating or harassing someone through the use of electronic devices or other forms of electronic communication (like social media platforms).
Because cyberbullying mainly affects children and adolescents, many brush it off as a part of growing up. However, cyberbullying can have dire mental and emotional consequences if left unaddressed.
This article discusses cyberbullying, its adverse effects, and what can be done about it.
FangXiaNuo / Getty Images
Cyberbullying Statistics and State Laws
The rise of digital communication methods has paved the way for a new type of bullying to form, one that takes place outside of the schoolyard. Cyberbullying follows kids home, making it much more difficult to ignore or cope.
Statistics
As many as 15% of young people between 12 and 18 have been cyberbullied at some point. However, over 25% of children between 13 and 15 were cyberbullied in one year alone.
About 6.2% of people admitted that they’ve engaged in cyberbullying at some point in the last year. The age at which a person is most likely to cyberbully one of their peers is 13.
Those subject to online bullying are twice as likely to self-harm or attempt suicide . The percentage is much higher in young people who identify as LGBTQ, at 56%.
Cyberbullying by Sex and Sexual Orientation
Cyberbullying statistics differ among various groups, including:
- Girls and boys reported similar numbers when asked if they have been cyberbullied, at 23.7% and 21.9%, respectively.
- LGBTQ adolescents report cyberbullying at higher rates, at 31.7%. Up to 56% of young people who identify as LGBTQ have experienced cyberbullying.
- Transgender teens were the most likely to be cyberbullied, at a significantly high rate of 35.4%.
State Laws
The laws surrounding cyberbullying vary from state to state. However, all 50 states have developed and implemented specific policies or laws to protect children from being cyberbullied in and out of the classroom.
The laws were put into place so that students who are being cyberbullied at school can have access to support systems, and those who are being cyberbullied at home have a way to report the incidents.
Legal policies or programs developed to help stop cyberbullying include:
- Bullying prevention programs
- Cyberbullying education courses for teachers
- Procedures designed to investigate instances of cyberbullying
- Support systems for children who have been subject to cyberbullying
Are There Federal Laws Against Cyberbullying?
There are no federal laws or policies that protect people from cyberbullying. However, federal involvement may occur if the bullying overlaps with harassment. Federal law will get involved if the bullying concerns a person’s race, ethnicity, national origin, sex, disability, or religion.
Examples of Cyberbullying
There are several types of bullying that can occur online, and they all look different.
Harassment can include comments, text messages, or threatening emails designed to make the cyberbullied person feel scared, embarrassed, or ashamed of themselves.
Other forms of harassment include:
- Using group chats as a way to gang up on one person
- Making derogatory comments about a person based on their race, gender, sexual orientation, economic status, or other characteristics
- Posting mean or untrue things on social media sites, such as Twitter, Facebook, or Instagram, as a way to publicly hurt the person experiencing the cyberbullying
Impersonation
A person may try to pretend to be the person they are cyberbullying to attempt to embarrass, shame, or hurt them publicly. Some examples of this include:
- Hacking into someone’s online profile and changing any part of it, whether it be a photo or their "About Me" portion, to something that is either harmful or inappropriate
- Catfishing, which is when a person creates a fake persona to trick someone into a relationship with them as a joke or for their own personal gain
- Making a fake profile using the screen name of their target to post inappropriate or rude remarks on other people’s pages
Other Examples
Not all forms of cyberbullying are the same, and cyberbullies use other tactics to ensure that their target feels as bad as possible. Some tactics include:
- Taking nude or otherwise degrading photos of a person without their consent
- Sharing or posting nude pictures with a wide audience to embarrass the person they are cyberbullying
- Sharing personal information about a person on a public website that could cause them to feel unsafe
- Physically bullying someone in school and getting someone else to record it so that it can be watched and passed around later
- Circulating rumors about a person
How to Know When a Joke Turns Into Cyberbullying
People may often try to downplay cyberbullying by saying it was just a joke. However, any incident that continues to make a person feel shame, hurt, or blatantly disrespected is not a joke and should be addressed. People who engage in cyberbullying tactics know that they’ve crossed these boundaries, from being playful to being harmful.
Effects and Consequences of Cyberbullying
Research shows many negative effects of cyberbullying, some of which can lead to severe mental health issues. Cyberbullied people are twice as likely to experience suicidal thoughts, actions, or behaviors and engage in self-harm as those who are not.
Other negative health consequences of cyberbullying are:
- Stomach pain and digestive issues
- Sleep disturbances
- Difficulties with academics
- Violent behaviors
- High levels of stress
- Inability to feel safe
- Feelings of loneliness and isolation
- Feelings of powerlessness and hopelessness
If You’ve Been Cyberbullied
Being on the receiving end of cyberbullying is hard to cope with. It can feel like you have nowhere to turn and no escape. However, some things can be done to help overcome cyberbullying experiences.
Advice for Preteens and Teenagers
The best thing you can do if you’re being cyberbullied is tell an adult you trust. It may be challenging to start the conversation because you may feel ashamed or embarrassed. However, if it is not addressed, it can get worse.
Other ways you can cope with cyberbullying include:
- Walk away : Walking away online involves ignoring the bullies, stepping back from your computer or phone, and finding something you enjoy doing to distract yourself from the bullying.
- Don’t retaliate : You may want to defend yourself at the time. But engaging with the bullies can make matters worse.
- Keep evidence : Save all copies of the cyberbullying, whether it be posts, texts, or emails, and keep them if the bullying escalates and you need to report them.
- Report : Social media sites take harassment seriously, and reporting them to site administrators may block the bully from using the site.
- Block : You can block your bully from contacting you on social media platforms and through text messages.
In some cases, therapy may be a good option to help cope with the aftermath of cyberbullying.
Advice for Parents
As a parent, watching your child experience cyberbullying can be difficult. To help in the right ways, you can:
- Offer support and comfort : Listening to your child explain what's happening can be helpful. If you've experienced bullying as a child, sharing that experience may provide some perspective on how it can be overcome and that the feelings don't last forever.
- Make sure they know they are not at fault : Whatever the bully uses to target your child can make them feel like something is wrong with them. Offer praise to your child for speaking up and reassure them that it's not their fault.
- Contact the school : Schools have policies to protect children from bullying, but to help, you have to inform school officials.
- Keep records : Ask your child for all the records of the bullying and keep a copy for yourself. This evidence will be helpful to have if the bullying escalates and further action needs to be taken.
- Try to get them help : In many cases, cyberbullying can lead to mental stress and sometimes mental health disorders. Getting your child a therapist gives them a safe place to work through their experience.
In the Workplace
Although cyberbullying more often affects children and adolescents, it can also happen to adults in the workplace. If you are dealing with cyberbullying at your workplace, you can:
- Let your bully know how what they said affected you and that you expect it to stop.
- Keep copies of any harassment that goes on in the workplace.
- Report your cyberbully to your human resources (HR) department.
- Report your cyberbully to law enforcement if you are being threatened.
- Close off all personal communication pathways with your cyberbully.
- Maintain a professional attitude at work regardless of what is being said or done.
- Seek out support through friends, family, or professional help.
Effective Action Against Cyberbullying
If cyberbullying continues, actions will have to be taken to get it to stop, such as:
- Talking to a school official : Talking to someone at school may be difficult, but once you do, you may be grateful that you have some support. Schools have policies to address cyberbullying.
- Confide in parents or trusted friends : Discuss your experience with your parents or others you trust. Having support on your side will make you feel less alone.
- Report it on social media : Social media sites have strict rules on the types of interactions and content sharing allowed. Report your aggressor to the site to get them banned and eliminate their ability to contact you.
- Block the bully : Phones, computers, and social media platforms contain options to block correspondence from others. Use these blocking tools to help free yourself from cyberbullying.
Help Is Available
If you or someone you know are having suicidal thoughts, dial 988 to contact the 988 Suicide & Crisis Lifeline and connect with a trained counselor. To find mental health resources in your area, contact the Substance Abuse and Mental Health Services Administration (SAMHSA) National Helpline at 800-662-4357 for information.
Cyberbullying occurs over electronic communication methods like cell phones, computers, social media, and other online platforms. While anyone can be subject to cyberbullying, it is most likely to occur between the ages of 12 and 18.
Cyberbullying can be severe and lead to serious health issues, such as new or worsened mental health disorders, sleep issues, or thoughts of suicide or self-harm. There are laws to prevent cyberbullying, so it's essential to report it when it happens. Coping strategies include stepping away from electronics, blocking bullies, and getting.
Alhajji M, Bass S, Dai T. Cyberbullying, mental health, and violence in adolescents and associations with sex and race: data from the 2015 youth risk behavior survey . Glob Pediatr Health. 2019;6:2333794X19868887. doi:10.1177/2333794X19868887
Cyberbullying Research Center. Cyberbullying in 2021 by age, gender, sexual orientation, and race .
U.S. Department of Health and Human Services: StopBullying.gov. Facts about bullying .
John A, Glendenning AC, Marchant A, et al. Self-harm, suicidal behaviours, and cyberbullying in children and young people: systematic review . J Med Internet Res . 2018;20(4):e129. doi:10.2196/jmir.9044
Cyberbullying Research Center. Bullying, cyberbullying, and LGBTQ students .
U.S. Department of Health and Human Services: StopBullying.gov. Laws, policies, and regulations .
Wolke D, Lee K, Guy A. Cyberbullying: a storm in a teacup? . Eur Child Adolesc Psychiatry. 2017;26(8):899-908. doi:10.1007/s00787-017-0954-6
U.S. Department of Health and Human Services: StopBullying.gov. Cyberbullying tactics .
Garett R, Lord LR, Young SD. Associations between social media and cyberbullying: a review of the literature . mHealth . 2016;2:46-46. doi:10.21037/mhealth.2016.12.01
Nemours Teens Health. Cyberbullying .
Nixon CL. Current perspectives: the impact of cyberbullying on adolescent health . Adolesc Health Med Ther. 2014;5:143-58. doi:10.2147/AHMT.S36456
Nemours Kids Health. Cyberbullying (for parents) .
By Angelica Bottaro Bottaro has a Bachelor of Science in Psychology and an Advanced Diploma in Journalism. She is based in Canada.
- Original Article
- Open access
- Published: 10 February 2020
Cyber violence pattern and related factors: online survey of females in Egypt
- Fatma Mohamed Hassan ORCID: orcid.org/0000-0003-2509-6697 1 ,
- Fatma Nada Khalifa 1 ,
- Eman D. El Desouky 2 ,
- Marwa Rashad Salem 3 &
- Mona Mohamed Ali 1 , 4
Egyptian Journal of Forensic Sciences volume 10 , Article number: 6 ( 2020 ) Cite this article
11k Accesses
7 Citations
Metrics details
Background and objectives
Cyber violence against women and girls is an emerging worldwide problem with a grave impact on individuals and societies. This study aimed to assess the problem of cyber violence against women among the Egyptian population.
A convenience sampling method was used to recruit a total of 356 females. A self-completion questionnaire was distributed through one of the social media applications.
About 41.6% of the participants experienced cyber violence during the last year, and 45.3% of them reported multiple times of exposure. Social media was the most common way of exposure, and the offenders were unknown for 92.6% of the victims. The most commonly reported forms included 41.2% receiving images or symbols with sexual content, 26.4% receiving insulting e-mails or messages, 25.7% receiving offensive or humiliating posts or comments, 21.6% receiving indecent or violent images that demean women, and 20.3% receiving infected files through e-mails. The majority of the victims (76.9%) experienced psychological effects in the form of anger, worry, and fear; 13.6 % social effects; 4.1% exposed to physical harm; and 2.0% reported financial losses. Blocking the offender was the most common victims’ response.
Females in the Egyptian population are highly exposed to cyber violence, so implementation of anti-cyber violence program is essential to counteract this phenomenon.
Women across the world are subject to various forms of violence: physical, sexual, psychological, and economic regardless of their age, education, or socioeconomic classes (Habib et al. 2011 ; UN Broadband Commission for Digital Development Working Group on Broadband and Gender 2015 ). About 35% of women worldwide had exposed to either physical and/or sexual intimate partner violence or non-partner sexual violence during their lifetime as indicated by the global estimates of WHO (WHO 2017 ).
A unique form of violence against women has arisen with the increased use of the Internet, social media, and the spread of information and communication technologies (ICT) which is cyber violence (Arafa et al. 2018 ). Cyber violence is an emerging worldwide phenomenon with grave public health consequences. It is not only associated with the adverse psychological, social, and reproductive health effects but also with offline physical and sexual violence for victims (Backe et al. 2018 ; Šincek et al. 2017 ).
Cyber violence against women could have many forms including cyber harassment, cyberstalking, defamation, non-consensual pornography, e-mail spoofing, cyber hacking, and virtual rape (EIGE 2017 ; Singh 2015 ).
Data about the magnitude of cyber violence and its incidence across different populations and communities are scarce, but studies suggest that online victimization is more likely to involve women, girls, and sexual minorities (Backe et al. 2018 ). In a survey involving more than 9000 German Internet users, women were significantly more likely than men to experience online sexual harassment and cyberstalking (Staude-Müller et al. 2012 ). Also, a Pew Research Center survey in the USA including more than 4000 adults disclosed that among subjects aged 18–29, women were more vulnerable to online sexual harassment than men (21 versus 9%) (Duggan 2017 ). The European Agency for Fundamental Rights based on European Survey reported that one in 10 women had experienced a form of cyber violence since the age of 15 (European Union Agency for Fundamental Rights 2014 ).
In Egypt, the digital society includes 37.9 million users, and 35 million of them have active Facebook accounts, with a total number of male users 22 million, while the number of female users is 12 million (MICT 2018 ). However, the study of cyber violence against women has not kept up with the spread of ICT. The objective of this study was, therefore, to evaluate the problem of cyber violence against women among the Egyptian population including its prevalence, different forms, relation to sociodemographic characteristics, and impact on victims’ lives.
Sampling procedure
The study was carried out using an online survey disseminated through one of the social media most frequently used in Egypt which is the Facebook application. The researchers selected groups with a large number of female members to achieve a high response rate. Requests were sent to administrators of these groups to get permission to disseminate the survey. Then, the researchers posted the link of the survey with a statement including its purpose and encouraging the members to participate. The study spanned from 1 October 2018 to 31 December 2018.
Recruitment and participants
A convenience sampling technique was followed whereby the researchers looked on Facebook for women’s groups with a large female network. Once they located the groups, they disseminated announcements about the study to these groups, and a link to the study page was provided. For 3 months, this link was available on some groups where a total of 356 adult females (≥ 18 years old) answered the questionnaire. The majority of the participants (63.2%) aged between 26 and 35 years; most of them were married (68.8%), about half of them (48.9%) received postgraduate education, and the other half (47.5%) had received higher education; 67.4% of them was living in Greater Cairo followed by 25.8% and 6.7% in Lower Egypt and Upper Egypt, respectively; 60.7% of them had regular work, while 29.2% were not working; and 58.1% used the Internet and mobile phones for more than 3 h per day.
Data collection tool
For data collection, a pre-tested self-administrated Arabic language e-form questionnaire was designed by the research team. It included two sections:
Section I: Sociodemographic data: age, marital status, educational level, residence, occupation, and mobile phone and Internet use (h/day).
Section II: Cyber violence questions, which included 14 closed-ended question items as follows: Were you exposed to any form of cyber violence in the last year? (If your answer is no, then submit the form.) What was the way to your exposure to cyber violence? How many times were you exposed to cyber violence in the last year? Were you exposed to any of these forms of cyber violence in the last year? Do you know the offender (the person who practiced cyber violence against you)? What is the offender’s gender? What is the offender’s age? What is your relation to the offender? What was his/her motive? What was your response to the incident? What was the impact of cyber violence on you? How were you psychologically affected? How were you socially affected? What was the community response to your exposure to cyber violence?
The original language of the included items was English; they were translated to Arabic by two experts followed by back translation to English by other independent experts. The face and content validity were examined after collecting their viewpoints of public health experts. The preliminary data collection form was tested on 12 females to assess the clarity and comprehension of questions and the time needed to answer the questionnaire, and no phrases or words were omitted.
Statistical analysis
Statistical analysis was done using the Statistical Package for the Social Sciences program (SPSS, version 21.0 IBM). The data were summarized using numbers, and percentages were used for qualitative variables. Comparison between groups was performed using the chi-square test for qualitative variables. P value of less than 0.05 was considered statistically significant.
Ethical considerations
All procedures for data collection were treated with confidentiality according to Helsinki declarations of biomedical ethics. The researchers requested the informed consent of the participants after explanation of the study objectives and importance. The study page included the questionnaire, information about the purpose of the study, and informed consent. The participants were given access to the survey once provided their consent. It was clearly stated in the research announcement that the survey was examining cyber violence among women. Participants were informed that this was an anonymous survey and participation was voluntary.
Our results revealed that 41.6% of the participating females reported exposure to cyber violence during the last year and 45.3% of the victims experienced cyber violence multiple times; the most common way of exposure as reported by about three quarters of the participants (72.8%) was social media, and the offenders were unknown for the majority (92.6%) of the victims as shown in Table 1 . The known offenders were males in 10 cases, either current or ex-partners (4 cases) or the victim’s relatives, co-workers, or friends, and the recognized motives were revenge, hate, and blackmailing.
Table 2 revealed that about one half of the enrolled participants (41.2%) reported receiving images or symbols with sexual contents, 26.4% received insulting e-mails or messages, 25.7% received offensive or humiliating posts or comments, 21.6% received indecent or violent images that demean women, 20.3% received infected files through e-mails, and 14.9% were hacked.
Concerning the impact of cyber violence on exposed females, the majority (76.9%) experienced psychological effects in the form of anger, worry, fear, suicidal thoughts, and desire to revenge, while 13.6 % experienced social effects as withdrawal from online activity and being isolated (Table 3 ).
As shown in Table 4 , blocking the offender, reporting contents, and changing the contact information were the most common female responses to the cyber violence incidents (72.8, 26.5, and 25.2% respectively). While regarding the community response, 33.3% reported that their families and friends were supportive and helpful while 9.5% were asked to ignore and 5.4% were blamed.
On assessing the effects of sociodemographic characteristics on the exposure rate of cyber violence, results revealed that neither age, education, residence, occupation, nor daily Internet use had played a role in exposure to cyber violence with non-significant p value, only the marital status showed a significant effect ( p = 0.001) with married females being less likely to experience it (Table 5 ). Also, none of these variables affected the frequency of exposure (Table 6 ).
Cyber violence is a major worldwide problem that has arisen with increased use of the Internet, smartphones, and social media. This study presents an overview of cyber violence against women in Egypt.
Our results revealed that nearly half of the participating females experienced different forms of cyber violence throughout the last year with about half of them reporting multiple times of exposure. The most common forms were cyber harassment and cyberstalking represented in the following (receiving images or symbols with sexual contents, insulting e-mails or messages, receiving offensive or humiliating posts or comments, indecent or violent images that demean women, and threats of physical or sexual violence).
Our findings are lower than those of Arafa and Senosy ( 2017 ) who found that 52.9% of females participating in their study experienced cyberbullying with 69.9% reporting more than one-time exposure. They also reported that cyber harassment was the most common form. But compared to our population, their participants were university students representing specific age, and also, they conducted the study in a single governorate in Egypt.
Consistent with our result, several studies reported cyber harassment and cyberstalking for being the most common forms of cyber violence against women. A survey by Battered Women’s Support Services found that about one third of the participated women had experienced online harassment or cyberstalking (West 2014 ). Also, research by the African Development Bank in Kenya found that more than one third of the respondents had experienced online harassment, and another third received personal hate speech, cyberbullying, and trolling and contacted by imposters (African Development Bank Group 2016 ).
In the current study, social media platforms were the most common way of exposure to cyber violence. This is in agreement with the Pew Research Center report that found online harassment more prevalent in some online environments than others, and that most of the incidents occurred on social networking sites (Duggan et al. 2014 ).
Regarding the offenders in our study, they were unknown for 92.6% of the victims. Duggan et al. ( 2014 ) reported that the perpetrators were anonymous for half of those who had experienced online harassment. On the contrary, The Association of Progressive Communications’ (APC) research project “End violence: women’s rights and safety online” found out that half of the perpetrators were known (APC Women’s Rights Programme 2015 ).
In this study, out of the 11 known offenders, 10 were males. Alike, Pasricha ( 2016 ) found that 85% of their survey participants reported that the incidents were perpetrated by men or under accounts with a male name. Also, women’s rights organizations’ research in three of the Nordic countries (Iceland, Denmark, and Norway) described perpetrators as being typically men (Jóhannsdóttir et al. 2017 ). Concordant with APC’s research project results, our results also revealed that the known offenders were either a current or former partner or the victim’s relatives, co-workers, or friends.
This study revealed that the most common impact of cyber violence on the victims was the psychological, followed by the social, then the physical and economic impacts. It also pointed to many psychological effects including the most common: anger, worry, and fear, and the gravest—suicidal thoughts. Similarly, West ( 2014 ) found that 65% of their survey respondents reported being psychologically affected. Moreover, Lenhart et al. ( 2016 ) found that women were more likely than men to be angry, worried, and scared.
Regarding the female response to the cyber violence incidents in this study, they commonly responded by blocking the offender, reporting contents to platforms, and changing their contact information. Likewise, previous studies showed that the same finding (African Development Bank Group 2016 ; Duggan et al. 2014 ; Pasricha 2016 ). Surprisingly, none of the victims in our study reported the incidents to the police. Lewis et al. ( 2017 ) mentioned that victims might think these incidents are personal issues and their reputation might be damaged by reporting and making it public. Also, unawareness of the laws that condemn cyber violence may play a role.
In this study, about one third of the victims did not tell anyone about their exposure to cyber violence. The conservative nature of our community and the fear of shame, disgrace, or blame that may arise after disclosing their experience even to families or friends may be the cause.
About the impact of the studied sociodemographic factors on the rate and frequency of exposure to cyber violence, we found that the only significant finding with cyber violence exposure was the marital status; married females were significantly less exposed. We expect that married females are less likely to engage in social networking and that they are more careful in their social activities which make them less likely to cyber violence exposure. Moreover, offenders might think married women have more support so avoid attacking them.
Previous research showed inconsistent results in this issue. Arafa et al. ( 2018 ) and Arafa and Senosy ( 2017 ) found that the duration of daily Internet use significantly associated with exposure and frequency of exposure to cyber violence. Also, Winkelman et al. ( 2015 ) found that age significantly associated with exposure and they reported that women who had been threatened via text or instant messaging were significantly older compared to those who were not victimized in this area.
Limitations
This study had some limitations. The study population may not be representative of the female population in Egypt as the study targeted only women with an online presence on Facebook. Besides, the study included only victims, not offenders or witnesses of cyber violence. Also, participation in the study relied on self-report data, and therefore, response bias on cyber violence would over-represent those who had been victimized and those severely affected. However, this study could contribute to the limited research published on this topic and be a base for more comprehensive studies that explore cyber violence against women.
Conclusion and recommendation
In conclusion, a high rate of cyber violence against women had been detected among the Egyptian population in the past year. Consequently, it is urgent that the government enact strong laws that criminalize cyber violence in its various forms. It is also essential to arrange awareness programs for women how to maintain their online personal safety, protect their identity, and how to deal with cyber violence incidents. In addition, media awareness campaigns should be raised to change the attitude of society towards women exposed to cyber violence. Finally, further research should be conducted to get adequate women’s representations of this problem and detect awareness-raising needs.
Availability of data and materials
The datasets supporting the conclusions of this article are included within the article.
Abbreviations
Association of Progressive Communications
Information and Communication Technologies
Statistical Package for the Social Sciences program
World Health Organization
African Development Bank Group (2016) Minding the gaps: identifying strategies to address gender-based cyber violence in Kenya. https://www.afdb.org/fileadmin/uploads/afdb/Documents/Generic-Documents/Policy_Brief_on_Gender_Based_Cyber_Violence_in_Kenya.pdf . Accessed 12 Dec 2018.
APC Women’s Rights Programme (2015) Briefing paper on VAW. https://www.apc.org/sites/default/files/HRC%2029%20VAW%20a%20briefing%20paper_FINAL_June%202015.pdf . Accessed 3 Mar 2019.
Arafa AE, Elbahrawe RS, Saber NM, Ahmed SA, Abbas AM (2018) Cyber sexual harassment: a cross-sectional survey over female university students in Upper Egypt. Int J Community Med Public Health 5(1):61–65. https://doi.org/10.18203/2394-6040.ijcmph20175763
Article Google Scholar
Arafa AE, Senosy SA (2017) Pattern and correlates of cyberbullying victimization among Egyptian university students in Beni-Suef, Egypt. J Egypt Public Health Assoc 92(2):107–115. https://doi.org/10.21608/epx.2018.8948
Article PubMed Google Scholar
Backe EL, Lilleston P, McCleary-Sills J (2018) Networked individuals, gendered violence: a literature review of cyber violence. Violence Gender 5(3):135–145. https://doi.org/10.1089/vio.2017.0056
Duggan M (2017) Online harassment. Pew Research Center https://www.pewinternet.org/2017/07/11/online-harassment-2017 . Accessed 28 Feb 2019.
Duggan M, Rainie L, Smith A, Funk C, Lenhart A, Madden M (2014) Online harassment. Pew Research Center http://www.pewinternet.org/2014/10/22/part-1-experiencing-online-harassment/ . Accessed 3 Mar 2019.
European Institute for Gender Equality (2017) Cyber violence against women and girls. https://doi.org/10.2839/876816
Book Google Scholar
European Union Agency for Fundamental Rights (2014) Violence against women: an EU-wide survey—main results. https://fra.europa.eu/sites/default/files/fra_uploads/fra-2014-vaw-survey-main-results-apr14_en.pdf . Accessed 10 Mar 2019.
Habib SR, Abdel Azim EK, Fawzy IA, Kamal NN, El Sherbini AM (2011) Prevalence and effects of violence against women in a rural community in Minia Governorate, Egypt. J Forensic Sci 56(6):1521–1527. https://doi.org/10.1111/j.1556-4029.2011.01886.x
Jóhannsdóttir A, Aarbakke MH, Nielsen RT (2017) Online violence against women in the nordic countries. http://www.kun.no/uploads/7/2/2/3/72237499/2017_onlineviolence_web.pdf . Accessed 12 Mar 2019.
Lenhart A, Ybarra M, Zickuhr K, Price-Fenney M (2016) Online harassment, digital abuse, and cyberstalking in America. Data & Society https://www.datasociety.net/pubs/oh/Online_Harassment_2016.pdf . Accessed 20 Jan 2019
Lewis R, Rowe M, Wiper C (2017) Online abuse of feminists as an emerging form of violence against women and girls. Br J Criminol 57(6):1462–1481. https://doi.org/10.1093/bjc/azw073
Pasricha J (2016) Violence online in India: cybercrimes against women & minorities on social media. https://feminisminindia.com/wp-content/uploads/2016/05/FII_cyberbullying_report_website.pdf . Accessed 20 Feb 2019.
Šincek D, Duvnjak I, Milić M (2017) Psychological outcomes of cyber-violence on victims, perpetrators and perpetrators/victims. Hrvatska revija za rehabilitacijska istraživanja 53(2):98–110. https://doi.org/10.31299/hrri.53.2.8
Singh J (2015) Violence against women in cyber world: a special reference to India. Int J Adv Res Manag Soc Sci 4(1):60–76
CAS Google Scholar
Staude-Müller F, Hansen B, Voss M (2012) How stressful is online victimization? Effects of victim’s personality and properties of the incident. Eur J Dev Psychol 9(2):260–274. https://doi.org/10.1080/17405629.2011.643170
The Ministry of Communications and Information Technology (MCIT) (2018) ICT indicators in brief, November 2018 monthly issue. http://www.egyptictindicators.gov.eg/en/Publications/PublicationsDoc/ICT%20Indicators%20in%20brif%20November%202018%20English.pdf . Accessed 30 Dec 2018.
UN Broadband Commission for Digital Development Working Group on Broadband and Gender (2015) Cyber violence against women and girls: a worldwide wake-up call. United Nations http://www.unwomen.org/~/media/headquarters/attachments/sections/library/publications/2015/cyber_violence_gender%20report.pdf?v=1&d=20150924T154259 . Accessed 15 Jan 2019.
West J (2014) Cyber-violence against women. Battered Women’s Support Services https://www.bwss.org/cyber-violence-against-women/ . Accessed 30 Jan 2019.
Winkelman SB, Early JO, Walker AD, Chu L, Yick-Flanagan A (2015) Exploring cyber harassment among women who use social media. Univ J Public Health 3(5):194–201. https://doi.org/10.13189/ujph.2015.030504
World Health Organization (2017) Violence against women. https://www.who.int/news-room/fact-sheets/detail/violence-against-women . Accessed 30 Jan 2019.
Download references
Acknowledgements
Author information, authors and affiliations.
Department of Forensic Medicine and Clinical Toxicology, Faculty of Medicine, Cairo University, Kasr Alainy Street, Cairo, 11562, Egypt
Fatma Mohamed Hassan, Fatma Nada Khalifa & Mona Mohamed Ali
Department of Epidemiology and Biostatistics, Faculty of Medicine, National Cancer Institute, Cairo University, Kasr Alainy Street, Cairo, 11562, Egypt
Eman D. El Desouky
Department of Public Health and Community Medicine, Faculty of Medicine, Cairo University, Kasr Alainy Street, Cairo, 11562, Egypt
Marwa Rashad Salem
Forensic Medicine and Clinical Toxicology, Faculty of Medicine, Taif University, Ta’if, Saudi Arabia
Mona Mohamed Ali
You can also search for this author in PubMed Google Scholar
Contributions
FMH: designing the study and writing of the manuscript. FNK: collecting the data. EDED and MRS: analyzing the data and finalizing the methodology and tools used. MMA: final and critical revision of the manuscript. All the authors made significant contributions in finalizing the manuscript. The final manuscript has been read and approved by all the authors.
Corresponding author
Correspondence to Fatma Mohamed Hassan .
Ethics declarations
Ethics approval and consent to participate.
The study was approved by the Ethical Committee of Faculty of Medicine, Cairo University. All procedures for data collection were treated with confidentiality according to Helsinki declarations of biomedical ethics. The researchers requested the informed consent of the participants after explanation of the study objectives and importance. Participants were informed that this was an anonymous survey and participation was voluntary.
Consent for publication
Not applicable.
Competing interests
The authors declare that they have no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License ( http://creativecommons.org/licenses/by/4.0/ ), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
Reprints and permissions
About this article
Cite this article.
Hassan, F.M., Khalifa, F.N., El Desouky, E.D. et al. Cyber violence pattern and related factors: online survey of females in Egypt. Egypt J Forensic Sci 10 , 6 (2020). https://doi.org/10.1186/s41935-020-0180-0
Download citation
Received : 12 November 2019
Accepted : 28 January 2020
Published : 10 February 2020
DOI : https://doi.org/10.1186/s41935-020-0180-0
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cyber violence
- Cyber harassment
- Social media

IMAGES
VIDEO
COMMENTS
A few psychological studies have begun examining the characteristics of individuals who engage in cyber aggression and violence, which include both traditional criminal risk factors (i.e., externalizing traits) and potentially new risk factors (i.e., internalizing traits). 3.1. Low self-control or impulsivity.
This paper reviews the existing literature on the relationship between social media and violence, including prevalence rates, typologies, and the overlap between cyber and in-person violence. This review explores the individual-level correlates and risk factors associated with cyber violence, the group processes involved in cyber violence, and the macro-level context of online aggression. The ...
Cyberviolence is a form of violence that involves using the Internet as a means of abusing, attacking, insulting, and defaming the victim while also endangering their privacy, personal safety, and ...
Introduction to Cyber Violence. In this particular essay, we will look to discuss policy, by starting, with the definition of cyber violence, the legal framework governing the problem, providing official statistics on the extent of the problem, what are the empirical research findings, and finally offer recommendations on how best to tackle the issue.
Cyber-stalking, revenge porn, hate speech and cyberbullying are just some forms of online violence (cyber-violence). This issue reflects on the problematic issue of cyberviolence from different perspectives including the social, psychological, and educational.
Unfortunately, it can also lead to cyberviolence - harms such as bullying, harassment, loss of privacy and direct violence - especially against women and girls who are just crossing the digital divide. These risks need to be eliminated so that women and girls have equal access to and use of digital tools and can equally benefit from growth in ...
Introduction. Cyber violence refers to any behavior on the Internet advocating violence or using language calculated to inflame the passions to achieve mass emotional catharsis (Hou and Li, 2017), which can be considered an extension of social violence to the Internet (Li et al., 2017).In the past 2 years, with the rapid growth of Internet users, cyber violence incidents on social media have ...
Highlights. One of the first comprehensive literature reviews on social media and violence. Interdisciplinary look at prevalence rates and typologies of cyber violence. Explores individual risk factors, group processes, and context of cyber violence. Provides a framework for reconciling conflicting levels of explanation.
Words: 840 Pages: 3. Recently, social media has become a platform for cyber violence. This issue primarily concerns public health and is associated with adverse mental or physical outcomes. As a result, cyberbullying is one of the top contemporary problems that needs to be approached from different angles to be resolved entirely.
A Mapping Study on Cyberviolence was carried out by the T-CY Working Group on cyberbullying and other forms of online violence, especially against women and children. The Group aimed to study the topic in the form of a mapping exercise, including comparative approaches to legislation as well as documentation of good practices.
This paper reviews the existing literature on the relationship between social media and violence, including prevalence rates, typologies, and the overlap between cyber and in-person violence. This review explores the individual-level correlates and risk factors associated with cyber violence, the group processes involved in cyber violence, and the macro-level context of online aggression. The ...
Background. "Cyberviolence is the use of computer systems to cause, facilitate, or threaten violence against individuals that results in, or is likely to result in, physical, sexual, psychological or economic harm or suffering and may include the exploitation of the individual's circumstances, characteristics or vulnerabilities." (T-CY ...
Cybercrime, or the use of computer technology or online networks to commit crimes, ranges from fraud and identity theft to threats and intimidation. Cybercrime and its many manifestations has clearly increased over the past 20 years. For example, cybercrime costs increased from approximately $3 trillion in 2015 to more than $6 trillion in 2021 ...
The essay "Causes and Effects of Cyber Bullying" presents a clear explanation of the topic, but there are some shortcomings that need to be addressed to improve the quality of the essay. One of the issues is the repetition of certain words, such as "cyberbullying" and "online harassment." To avoid this repetition, the writer should use synonyms ...
The deadly insurrection at the U.S. Capitol in January exposed the power of social media to influence real-world behavior and incite violence. But many adolescents, who spend more time on social media than all other age groups, have known this for years. "On social media, when you argue, something so small can turn into something so big so fast," said Justin, a 17-year-old living in ...
Introduction to Cyber Violence In this particular essay, we will look to discuss policy, by starting, with the definition of cyber violence, the legal framework governing the problem, providing official statistics on the extent of the problem, what are the empirical research findings, and finally offer recommendations on how best to tackle the issue.
Nagle J (2018) Twitter, cyber-violence, and the need for a critical social media literacy in teacher education: A review of the literature. Teach Teach Educ 76:86-94 Article Google Scholar
Introduction. Cyber violence was defined as "an aggressive, intentional act carried out by a group or individual, using electronic forms of contact, repeatedly and over time against a victim who cannot easily defend him or herself." (Smith, Maddavi, Carvalho, Fisher, Russell, and Tippett, 2008: 376). The prevalence and impacts of cyber ...
Research on cybercrime victimization is relatively diversified; however, no bibliometric study has been found to introduce the panorama of this subject. The current study aims to address this research gap by performing a bibliometric analysis of 387 Social Science Citation Index articles relevant to cybercrime victimization from Web of Science database during the period of 2010-2020. The ...
People who are victims of any form of violence, including bullying and cyberbullying, have a right to justice and to have the offender held accountable. Laws against bullying, particularly on cyberbullying, are relatively new and still do not exist everywhere. This is why many countries rely on other relevant laws, such as ones against ...
Research shows many negative effects of cyberbullying, some of which can lead to severe mental health issues. Cyberbullied people are twice as likely to experience suicidal thoughts, actions, or behaviors and engage in self-harm as those who are not. Other negative health consequences of cyberbullying are: Depression. Anxiety.
Cyberbullying occurs when someone uses technology to demean, inflict harm, or cause pain to another person. It is "willful and repeated harm inflicted through the use of computers, cell phones, and other electronic devices.". Perpetrators bully victims in any online setting, including social media, video or computer games, discussion boards ...
Cyber violence against women and girls is an emerging worldwide problem with a grave impact on individuals and societies. This study aimed to assess the problem of cyber violence against women among the Egyptian population. A convenience sampling method was used to recruit a total of 356 females. A self-completion questionnaire was distributed through one of the social media applications.