- Jira Service Management
- Atlassian Guard
- Company News
- Continuous Delivery
- Inside Atlassian
- IT Service Management
- Work Management
- Project Management
Our State of Teams 2024 report is live! Check it out here .


We read 100 data breach notifications to make this guide (which we hope you’ll never need)

Product Marketing Manager
Nothing fills out the “worst-case scenario” column quite like a data breach. For the countless teams out there who work hard to protect their customers’ data, the idea of compromising that trust is a nightmare.
Data breaches are on a lot of minds lately with the 2017 Equifax data breach , which exposed personal data from 143 million American consumers. The company, security industry, and regulators have a huge task of working out the details on how something like this happens.
At Statuspage, we talk a lot about transparency, trust, and letting the right people know when things go wrong. Transparency around crises is a core part of our philosophy here at Atlassian and Statuspage. While we’re typically talking about these thing in relation to outages and downtime instead of data breaches, there are a lot of overlapping themes. The benchmarks of a great downtime response strategy aren’t all that different from a great data breach response strategy. We fancy ourselves experts at incident response best practices, we figured it would be interesting to take a look at data breach response best practices and see where we can notice some overlap.
A brief look at incident response vs. data breach response
For the most part, downtime is more tolerable and less troubling than a data breach. A few minutes of an unscheduled outage is usually more palatable than even a hint of a data breach. Teams will even purposefully take their service offline to prevent a breach from spreading in some cases. Because of this, most systems are built to prioritize data safety over perfect uptime . We’ve talked plenty about how downtime is inevitable and shooting for 100% uptime shouldn’t be the goal. That’s partly because 100% data protection should be the goal. Think about it. Would you rather your bank’s mobile app went down for a day or lost your transaction history for a day? It’s pretty clear that in the web service hierarchy of needs, data protection trumps uptime. And that’s OK.
Because of the heightened sensitivity to data, we see a lot more regulatory activity around data breaches. Regulators mostly leave it up to organizations on how they’ll announce downtime and service interruptions. But they have a lot to say, understandably so, about how teams should respond to data breaches.
Data breach response regulatory summary (slightly less boring than it sounds)
The Equifax breach has a lot of folks calling for updates to how regulators patrol breach response. Although there are varying opinion on whether the current rules go far enough, it’s worth taking stock of where things stand now.
Right now, there is little national oversight on how companies handle data privacy. When it comes to notifying consumers that their data has been stolen, laws vary state to state and differ in how much time and how much information companies are required to divulge. Equifax is based in Georgia, a state where there is no timeline specified for when a company must notify customers about a breach.
California’s law, enacted in 2002, was the first in the country and became the template for most other states whose lawmakers adopted similar regulations. The main paragraph of California’s law is here (note: if you’re like us and the legal-ese makes your brain hurt, fear not, we break it down in plain English in the next section).
“(a) Any agency that owns or licenses computerized data that includes personal information shall disclose any breach of the security of the system following discovery or notification of the breach in the security of the data to any resident of California (1) whose unencrypted personal information was, or is reasonably believed to have been, acquired by an unauthorized person, or, (2) whose encrypted personal information was, or is reasonably believed to have been, acquired by an unauthorized person and the encryption key or security credential was, or is reasonably believed to have been, acquired by an unauthorized person and the agency that owns or licenses the encrypted information has a reasonable belief that the encryption key or security credential could render that personal information readable or useable. The disclosure shall be made in the most expedient time possible and without unreasonable delay, consistent with the legitimate needs of law enforcement, as provided in subdivision (c), or any measures necessary to determine the scope of the breach and restore the reasonable integrity of the data system.”
Now, in English:
Who this applies to? Any person or group who owns or licenses computerized data that includes personal information.
Which has undergone what? Any breach of the security of the system.
Has to do what? Disclose the breach to any resident of California whose unencrypted personal information was, or is reasonably believed to have been, acquired by an unauthorized person. The same applies if this is encrypted information if there is a known or reasonable belief that the encryption key was also compromised. Basically, if there’s any sort of proof — or reasonable belief — that someone unauthorized was ever able to view private info, they need to notify them.
By when? The most expedient time possible and without unreasonable delay. By now you should be working with law enforcement, who may advise you on when to send the announcement.
Sounds simple enough. But how do these notifications need to be sent? And what should they say? Thankfully, the legislation includes a template which advises the following information be included:
- What happened
- What information was involved
- What’s being done
- What you can do
- Other important information
- Where to find more information
It’s important that these are the regulations for California. While other states drew inspiration from these guidelines, it’s worth noting that these change for users in different states and countries. Please do your own research and contact your own experts and lawyers if you need to put any of this into practice.
The research: 100 breach notifications
Now that we have a handle on what constitutes a breach and what a breach response looks like, let’s have a look at how organizations approach these announcements.
To get a better idea of how teams draft these response letters, we downloaded 100 of the most recent sample responses that were filed recently with the State of California. Filed breach response samples are public record and posted on the state’s Department of Justice website.
Reading these hundreds of pages of breach notification was eye-opening (and a little eye-straining). It’s surprising how much good breach response measures have in common with incident response strategies. It’s also interesting how much variety there was in both the type of organization affected (hospitals, hotels, insurance companies, law offices) and the catalyst of the breach (phishing scams, lost devices, break-ins).
In no particular order, here are a handful of our observations from this research:
- Some teams added a nice plain-English FAQ to the response. This seems helpful. It’s good to keep in mind that your customers aren’t lawyers, and they’ll be quickly skimming for answers to immediate questions.
- Many companies mention they they’ve retained the services of a forensic investigation firm. Some say the name of the firm, others are vague: “a leading cybersecurity firm” “well-respected forensics firms.” If possible, it’s nice to let people know who is working on their behalf.
- Many also note they’re working with law enforcement, but it’s not always clear if they are and/or what the status of any investigation is. Law enforcement can give guidelines on how much transparency you can deliver about what’s happening and how to give periodic updates.
- A handful of the breaches stem from a breach in third-party vendors. This underscores what we’ve always talked about regarding incidents with third-party service providers: if it affects your customers, it’s your responsibility. Your customers don’t care if it technically wasn’t your fault. It’s important to vet your vendors ahead of time. But if there is an incident, take responsibility without throwing your vendor under the but and dodging the blame.
- In some cases, one third-party outage triggered several breach notifications across other companies who used that service.
- Some teams do a nice job of specifically relaying what happened (phishing, malware, etc.). Others are pretty vague, printing statements like “individual obtained access to our system” or “sophisticated cyber-attack” It’s easy to see how this would be frustrating to a customer. How did they get access?How did you learn about the incident? What was so sophisticated about it? What are the steps you took to make sure it doesn’t happen again? To be fair, a lot of these teams are working with law enforcement, lawyers, and private investigators; all of whom might have really good reasons for keeping things on the vague side. As a customer, we would hope for more details than this eventually. In incident response, we always advocate being as specific as possible without compromising trust or finger-pointing.
- One interesting notice stemmed from an over-the-phone scam. Basically someone called the company’s IT office impostering employees. They somehow had enough info to get login credentials reset then access the system. A good reminder to keep your guard up even when you aren’t dealing with keyboards and screens.
- It’s not all sophisticated cyber-attacks. Several companies had data breaches due to physical break-ins or on-person robberies. Good reminder to keep your physical security up to par.
- One organization went above and beyond, filing a detailed, and helpful, breach response when an employee’s cell phone was stolen. Even though the phone was password protected and the company immediately wiped the data on the phone (and there was no other evidence the data had been accessed) the company did the right thing and notified its customers the proper way. We can see how easy it would be to say “it’s just a missing phone, they didn’t even have my pin, what’s the big deal?” This is a good example of taking it on the chin and putting the customer first.
Closing thoughts
Obviously this is a complicated topic, and you should talk to real experts if a data breach happens to your company. It’s important let the lawyers and law enforcement do their jobs.
If you’re interested in learning more, here are some helpful links:
- The Equifax Data Breach: What to Do
- Security Breach Notification Laws
- Comparison of US State and Federal Security Breach Notification Laws
- Cybersecurity Incident & Important Consumer Information
As people trust cloud companies to keep more and more of their info online, it’s going to be easy to take that trust for granted. Just like smart incident communication, smart data breach communication means putting yourself in the customer’s shoes. It’s about trying to make the best experience possible for the customer. Even if it’s a worst-case scenario kind of day.
Advice, stories, and expertise about work life today.

- CCI Magazine
- Writing for CCI
- Career Connection
- NEW: CCI Press – Book Publishing
- Advertise With Us
- See All Articles
- Internal Audit
- HR Compliance
- Cybersecurity
- Data Privacy
- Financial Services
- Well-Being at Work
- Leadership and Career
- Vendor News
- Submit an Event
- Download Whitepapers & Reports
- Download eBooks
- New: Living Your Best Compliance Life by Mary Shirley
- New: Ethics and Compliance for Humans by Adam Balfour
- 2021: Raise Your Game, Not Your Voice by Lentini-Walker & Tschida
- CCI Press & Compliance Bookshelf
- On-Demand Webinars: Earn CEUs
- Leadership & Career
- Getting Governance Right
- Adam Balfour
- Jim DeLoach
- Mary Shirley

Executive Responsibilities and Consequences: A Case Study of Uber’s Data Breaches
Individuals potentially face criminal charges for failing to disclose a data breach.

Organizations at risk of a data breach (that’s every organization, by the way) can learn something from Uber’s data privacy missteps. Squire Patton Boggs attorneys Colin Jennings, Ericka Johnson and Dylan Yépez offer key takeaways from the company’s high-profile data breaches.
On August 19, 2020, the former Chief Security Officer (CSO) for Uber Technologies Inc. (Uber) was charged with obstruction of justice and misprision of felony for allegedly trying to conceal from federal investigators a cyberattack that occurred in 2016, exposing the data of 57 million riders and drivers. Although an extreme case, it is a good reminder for companies and executives to take data breach disclosure obligations seriously.
The criminal complaint, filed in the U.S. District Court for the Northern District of California (“the Complaint”), appears to claim that Uber, through its former CSO, Joseph Sullivan, should have reported the 2016 data breach to federal investigators. But a business’s duty to disclose a data breach is not always clear, and there are often a myriad of laws, regulatory practices and consumer expectations when navigating a breach. Using Uber’s 2016 breach as a case study, company executives must be aware of and recognize the business and personal consequences associated with breach response, and specifically with intentionally concealing a breach.
The Obligation to Report a Data Breach is Often Not Straightforward
Across the world, countries have widely varying laws related to the protection of personal information and even greater variance on the requirements to disclose a breach of such information. Even within the United States, the definitions of “personal information” and “data breach” differ greatly from state to state, with no two state laws being identical, so businesses, particularly those operating on a national or global scale, must conduct multijurisdictional analyses to determine whether an obligation to disclose a given breach exists and, if so, the scope of the obligation. Often there are inconsistent laws and obligations, and regulatory and consumer expectations can vary greatly based on the nature, scope and context of the breach.
Many laws require disclosure of a data breach only if there is a “reasonable risk of harm” to the individual(s) whose personal information was unlawfully accessed and/or exfiltrated. This requires businesses to determine whether, based on the totality of circumstances, it is reasonably likely that a breach of personal information will harm affected individuals. On the other hand, some laws do not require any risk of harm. Further, given that the forensic review of a data breach evolves over time, it is not uncommon for the initial findings to change dramatically over the course of a breach response. What often appears to be a limited attack can become a wholesale loss of sensitive consumer or business data – and oftentimes both simultaneously.
The legal analysis is then complex, fact-specific and ever changing. Perhaps, for example, only a portion of the sensitive data was exposed (e.g., only the last four digits of a social security number or only an individual’s last name). Maybe, due to insufficient logs, forensic investigators cannot rule out the possibility that an unauthorized third party accessed the sensitive data or moved laterally into human resources data or databases containing consumer financial information. Or perhaps evidence suggests that the cybercriminals appear to be staging sensitive data for exfiltration, but have destroyed any evidence that data was actually taken. These are but a few examples of factors that can make the obligation to report far from straightforward.
As Uber’s 2016 breach response indicates, the difficulty of ascertaining a business’s breach notification obligations is not a defense to those company executives who intentionally conceal a breach. As discussed below, company executives who ultimately have to decide whether to disclose a breach should take notice of the potential consequences of making the wrong decision.
A Case Study in Intentionally Failing to Report a Breach
The Complaint alleges that, in response to Uber’s 2016 breach, former CSO Joseph Sullivan “engaged in a scheme to withhold and conceal from the [Federal Trade Commission] both the hack itself and the fact that that data breach had resulted in the hackers obtaining millions of records associated with Uber’s users and drivers.”
At the time of the breach, Sullivan was helping oversee Uber’s response to a Federal Trade Commission (FTC) investigation into Uber’s data security practices, which had been triggered, in part, by another Uber data breach that occurred in or around 2014. Sullivan was “intimately familiar with the nature and scope of the FTC’s investigation.”
About 10 days after providing sworn testimony to the FTC, however, Sullivan received an email from “[email protected],” claiming to have found a “major vulnerability in uber [ sic ],” and threatening that the hacker “was able to dump uber [ sic ] database and many other things.” Within days, Sullivan’s security team realized that an unauthorized person or persons had accessed Uber’s data and obtained, among other things, a copy of a database containing approximately 600,000 driver’s license numbers for Uber drivers.
Based on available information, this massive data breach likely triggered Uber’s duty to notify under numerous jurisdictions’ data breach laws. By contrast, the 2016 breach appeared significantly more expansive than the 2014 breach, in which a cybercriminal accessed over 100,000 individuals’ personal information on a cloud-based data warehouse.
Based on the Complaint, Sullivan allegedly took affirmative measures to conceal the data breach and the resulting exposure of data. Among other things, he allegedly:
- negotiated with the cybercriminals to pay $100,000 in exchange for the hackers to sign a nondisclosure agreement (NDA), “falsely represent[ing] that the hackers had not obtained or stored any data during their intrusion,” even though “[b]oth the hackers and Sullivan knew at the time that this representation in the NDA was false;”
- “instructed his team to keep knowledge of the 2016 breach tightly controlled;”
- “never informed the FTC of the 2016 data breach, even though he was aware that the FTC’s investigation focused on data security, data breaches and protection of [Personally Identifiable Information];” and
- “removed certain details … that would have illustrated the true scope of the [2016] breach” from a prepared summary for the new Uber CEO – changes which “resulted in both affirmative misrepresentations and misleading omissions of fact.”
Sullivan’s alleged motives to cover up the 2016 hack and data breach are the concerns that all companies must assess in connection with their breach notification responsibilities.
First , the Complaint appears to allege that one motive to conceal the breach was to prevent further reputational harm to the company. Like Uber’s customers, individuals entrust their data to companies on a daily basis, from making purchases to requesting services. Companies know, therefore, that they risk losing revenue if their customers lose confidence in the protection of their data.
Understanding this dynamic, he “became aware the attackers had accessed [the cloud] in almost the identical manner the 2014 attacker had used,” according to the Complaint. “That is, the attackers were able to access Uber’s source code on GitHub (this time by using stolen credentials), locate [a cloud] credential and use that credential to download Uber’s data.” As such, the Complaint appears to allege that both the embarrassment of falling victim to the same attack vector and the associated reputational consequences may have motivated Sullivan to conceal the breach.
Second , the Complaint appears to allege that another motive for concealing the breach was to prevent additional regulatory scrutiny. In the United States, companies like Uber are subject to many state- and industry-specific regulators (e.g., state Attorneys General, the Securities and Exchange Commission, FTC) — often simultaneously. Additionally, outside of the United States there are numerous laws and data protection or other authorities that govern data breaches.
At the time of the breach, Sullivan was actively responding to the FTC’s inquiries to assist in reaching a settlement related to the 2014 breach. For example, he approved language to the FTC representing that “‘all new database backup files’ had been encrypted since August 2014,” when in fact, they had not. Sullivan’s fears may not have been misplaced. In light of the new information regarding the 2016 breach, the FTC effectively withdrew its previous settlement terms and added requirements to the resolution with Uber.
Ultimately, it appears that such attempts to rationalize and avoid Uber’s breach notification responsibilities may have led Sullivan to engage in the actions he did.
Lesson Learned
In a public statement, the FBI advised that, “[w]hile this case is an extreme example of a prolonged attempt to subvert law enforcement, we hope companies stand up and take notice.” In effect, the consequences of failing to disclose a data breach are the most extreme in cases where a notification obligation clearly exists and the company and its officers consciously decide to circumvent that obligation during the course of an ongoing investigation. While companies have incentives to rationalize and avoid their disclosure obligations (e.g., reputational harm, regulatory oversight, expense), this incident highlights the potential consequences executives should be aware of when weighing the business decision to disclose a breach. Disclosure and direct individual notification of a data breach is now the expectation, and the decision to not disclose must be very carefully weighed – taking into account law, regulatory practice and consumer/customer expectations. One size does not fit all, and the nature, scope and circumstance of the specific breach must be carefully assessed in real time.
Ultimately, the legal analysis to determine whether an obligation exists and the business decision to disclose the same are nuanced and complex. If you experience a data breach, it is best to retain counsel who is highly experienced in the nuances of data breaches and the complexities of data breach notification laws for help determining whether and how to disclose a given breach.
How COVID-19 is Shifting Tax Reporting Regulations
Cci media group launches book publishing division targeting global audience in compliance, ethics, risk, internal audit.
Colin Jennings, Ericka Johnson and Dylan Yépez

Related Posts

News Roundup: 90% of Businesses Face Elevated Risk Levels Over Technology
Business email compromise remains key threat, while online payments industry most frequent ID theft target

News Roundup: SEC Finalizes New Cybersecurity Rules for Broker-Dealers, Others
OFAC launches public-facing sanctions database

In Crisis or In Control? Evolving Threat Actor Tactics Illustrate the Need for Clear Cybersecurity Communications Strategies
Preparing for the unexpected goes beyond IT expertise

Navigating Personal Liability: Post–Data Breach Recommendations for Officers
Executives may be on the hook if info is compromised

Privacy Policy
Founded in 2010, CCI is the web’s premier global independent news source for compliance, ethics, risk and information security.
Got a news tip? Get in touch . Want a weekly round-up in your inbox? Sign up for free. No subscription fees, no paywalls.
Browse Topics:
- Compliance Podcasts
- eBooks Published by CCI
- GRC Vendor News
- On Demand Webinars
- Resource Library
- Uncategorized
- Whitepapers
© 2024 Corporate Compliance Insights
Privacy Overview
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |

An official website of the United States government
Here’s how you know
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
Take action
- Report an antitrust violation
- File adjudicative documents
- Find banned debt collectors
- View competition guidance
- Competition Matters Blog
Slow the Roll-up: Help Shine a Light on Serial Acquisitions
View all Competition Matters Blog posts
We work to advance government policies that protect consumers and promote competition.
View Policy
Search or browse the Legal Library
Find legal resources and guidance to understand your business responsibilities and comply with the law.
Browse legal resources
- Find policy statements
- Submit a public comment

Vision and Priorities
Memo from Chair Lina M. Khan to commission staff and commissioners regarding the vision and priorities for the FTC.
Technology Blog
Global perspectives from the international competition network tech forum.
View all Technology Blog posts
Advice and Guidance
Learn more about your rights as a consumer and how to spot and avoid scams. Find the resources you need to understand how consumer protection law impacts your business.
- Report fraud
- Report identity theft
- Register for Do Not Call
- Sign up for consumer alerts
Get Business Blog updates
- Get your free credit report
- Find refund cases
- Order bulk publications
- Consumer Advice
- Shopping and Donating
- Credit, Loans, and Debt
- Jobs and Making Money
- Unwanted Calls, Emails, and Texts
- Identity Theft and Online Security
- Business Guidance
- Advertising and Marketing
- Credit and Finance
- Privacy and Security
- By Industry
- For Small Businesses
- Browse Business Guidance Resources
- Business Blog
Servicemembers: Your tool for financial readiness
Visit militaryconsumer.gov
Get consumer protection basics, plain and simple
Visit consumer.gov
Learn how the FTC protects free enterprise and consumers
Visit Competition Counts
Looking for competition guidance?
- Competition Guidance
News and Events
Latest news, ftc acts to stop student loan debt relief scheme that took millions from consumers in first case under the impersonation rule.
View News and Events
Upcoming Event
Closed commission meeting - july 1, 2024.
View more Events
Sign up for the latest news
Follow us on social media
--> --> --> --> -->

Playing it Safe: Explore the FTC's Top Video Game Cases
Learn about the FTC's notable video game cases and what our agency is doing to keep the public safe.
Latest Data Visualization
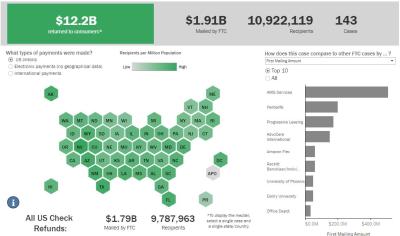
FTC Refunds to Consumers
Explore refund statistics including where refunds were sent and the dollar amounts refunded with this visualization.
About the FTC
Our mission is protecting the public from deceptive or unfair business practices and from unfair methods of competition through law enforcement, advocacy, research, and education.
Learn more about the FTC

Meet the Chair
Lina M. Khan was sworn in as Chair of the Federal Trade Commission on June 15, 2021.
Chair Lina M. Khan
Looking for legal documents or records? Search the Legal Library instead.
- Cases and Proceedings
- Premerger Notification Program
- Merger Review
- Anticompetitive Practices
- Competition and Consumer Protection Guidance Documents
- Warning Letters
- Consumer Sentinel Network
- Criminal Liaison Unit
- FTC Refund Programs
- Notices of Penalty Offenses
- Advocacy and Research
- Advisory Opinions
- Cooperation Agreements
- Federal Register Notices
- Public Comments
- Policy Statements
- International
- Office of Technology Blog
- Military Consumer
- Consumer.gov
- Bulk Publications
- Data and Visualizations
- Stay Connected
- Commissioners and Staff
- Bureaus and Offices
- Budget and Strategy
- Office of Inspector General
- Careers at the FTC
Data breach prevention and response: Lessons from the CafePress case
M any small businesses go to online retailing platform CafePress when they want to buy or sell customized items. However, according to a proposed FTC settlement , the company’s lax security practices allowed data thieves to take the idea of “personalization” in a disturbingly different direction. The complaint alleges that hackers exploited the company’s security failures to access personal information about millions of CafePress users – including home addresses, email addresses, passwords, security questions and answers, more than 180,000 unencrypted Social Security numbers, and partial payment card data from thousands of people. It’s particularly troubling that some of that information was later found for sale on a far more nefarious online platform – the Dark Web.
Although CafePress told customers that “100% complete security does not presently exist anywhere online or offline,” the company also touted that “our servers are secure” and that it “pledges to use the best and most accepted methods and technologies to insure your personal information is safe and secure.” On the checkout pages, it went so far as to say “Safe and Secure Shopping. Guaranteed.”
Where does the FTC say CafePress went wrong? According to the complaint, here are just some examples of the company’s questionable data practices:
- CafePress stored Social Security numbers and security Q&As in clear, readable text, and kept personal information indefinitely on its network without a business need;
- CafePress didn’t put readily-available protections in place against well-known vulnerabilities like Structured Query Language (SQL) injection attacks;
- CafePress failed to take reasonable steps to protect passwords and didn’t require users to create complex ones that would be harder to guess;
- CafePress failed to implement reasonable procedures to prevent, detect, or investigate intrusions on its network; and
- When CafePress experienced security episodes, it failed to respond reasonably.
You’ll want to read the complaint for details about multiple security incidents. But here’s the backstory about just one such episode – and the timeline is important here. According to the FTC, a person contacted CafePress in March 2019, revealing that the company had been hacked the month before and that its customer data “is currently for sale in certain circles.” The company confirmed the breach and installed a security patch, but remained mum about the matter. It required returning customers to reset their passwords, but chalked it up to an updated password policy.
In the ensuing months, the company received multiple alerts from individuals and a foreign government, including a warning that its customer data was for sale on the Dark Web. In addition, third-party monitoring services began to alert CafePress customers that their data had been hacked. It wasn’t until September 2019 – six months after CafePress was first told of the breach – that the company sent breach notifications to government agencies and affected customers.
In addition to the typical injuries that breaches impose on people, this breach took a particularly nasty turn when scammers used passwords in extortion attempts. Crooks sent emails to consumers, claiming they had obtained damaging personal information by hacking into the person’s computer and would release it unless paid in bitcoin. To add credibility to their claims, the scammers included the consumer’s recovered password in the extortion message.
The complaint alleges additional ways that small businesses and consumers were harmed by that breach and other security episodes. For example, in an earlier incident, the company learned that the accounts of certain “shopkeepers” – small businesses or individuals who sold items on CafePress – had been hacked. In a response that may define the phrase “adding insult to injury,” the company shut down those accounts and then charged each account holder a $25 closure fee. In other instances, the FTC alleges that the company withheld payable commissions from shopkeepers who accounts were closed due to a security breach.
The six-count complaint names Residual Pumpkin Entity, LLC, the former owner of CafePress, and PlanetArt, LLC, which bought CafePress in 2020. Among other things, the lawsuit alleges that the company misrepresented its data security practices, engaged in unfair security practices, and failed to take appropriate steps to secure accounts following security incidents.
The proposed settlement required the company to pay $500,000 in redress and to send notices to consumers telling them about the breach and the FTC settlement. The proposed order includes a number of other provisions that merit careful attention. For example, the order requires the company to replace any authentication methods that use security questions and answers with multi-factor authentication methods. The order also mandates that the company put in place and maintain an Information Security Program that includes (among other things) policies and procedures for data minimization and data deletion. That program must require the encryption of all Social Security numbers on the company’s networks – a particularly important protection because the company collects SSNs from small businesses for tax reporting purposes. And in addition to submitting third-party security assessments with the FTC, the company must provide redacted versions suitable for public disclosure. Once the proposed order is published in the Federal Register, the FTC will receive public comments for 30 days.
The case suggests more compliance nuggets than can be summarized here, but these may be the top three.
Don’t make it easy for data thieves to steal customer information. Hack happens, but there are numerous, cost-effective steps companies can take so their networks aren’t low-hanging fruit. The FTC offers to-the-point guidance on data security fundamentals , with special cybersecurity resources for small businesses .
Take security warnings seriously. If customers, government agencies, or others are telling you that you may have been hacked, investigate immediately.
Respond to security episodes honestly, transparently – and quickly. If your company has experienced a breach, respond with candor and speed. Move swiftly to implement a rapid response plan that honors your obligations under federal and state law. Read Data Breach Response: A Guide for Business for advice on how to secure your operations, fix vulnerabilities, and contact the people who need to know.
- Consumer Protection
- Bureau of Consumer Protection
- Data Security
- Small Business
Read Our Privacy Act Statement
It is your choice whether to submit a comment. If you do, you must create a user name, or we will not post your comment. The Federal Trade Commission Act authorizes this information collection for purposes of managing online comments. Comments and user names are part of the Federal Trade Commission’s (FTC) public records system, and user names also are part of the FTC’s computer user records system. We may routinely use these records as described in the FTC’s Privacy Act system notices . For more information on how the FTC handles information that we collect, please read our privacy policy .
Read Our Comment Policy
The purpose of this blog and its comments section is to inform readers about Federal Trade Commission activity, and share information to help them avoid, report, and recover from fraud, scams, and bad business practices. Your thoughts, ideas, and concerns are welcome, and we encourage comments. But keep in mind, this is a moderated blog. We review all comments before they are posted, and we won’t post comments that don’t comply with our commenting policy. We expect commenters to treat each other and the blog writers with respect.
- We won’t post off-topic comments, repeated identical comments, or comments that include sales pitches or promotions.
- We won’t post comments that include vulgar messages, personal attacks by name, or offensive terms that target specific people or groups.
- We won’t post threats, defamatory statements, or suggestions or encouragement of illegal activity.
- We won’t post comments that include personal information, like Social Security numbers, account numbers, home addresses, and email addresses. To file a detailed report about a scam, go to ReportFraud.ftc.gov.
We don't edit comments to remove objectionable content, so please ensure that your comment contains none of the above. The comments posted on this blog become part of the public domain. To protect your privacy and the privacy of other people, please do not include personal information. Opinions in comments that appear in this blog belong to the individuals who expressed them. They do not belong to or represent views of the Federal Trade Commission.
More from the Business Blog
First ftc impersonation rule case: why it matters to 43 million consumers – and to your business, the specs on specs: what eye doctors need to know about the ftc’s revised eyeglass rule, ftc says adobe hid key terms of “annual paid monthly” subscription plan and set up roadblocks to deter customer cancellations, succor borne every minute.
- Data Analytics and Insights
- Forensics and Collections
- Document Review
- Managed Services
- Investigations
- Securities Litigation
- Regulatory Risk Insights
- Information Governance
- Cyber Incident Response
- Antitrust and Competition Services
- Divestiture Services
- Contracts Review and Analysis
- Drafting and Negotiation
- CLM Selection and Optimization
- Contracts Process Advisory
- CLM Implementation and Integration
- Epiq Counsel
- Legal Business Advisory
- Legal Spend Management
- Knowledge Management
- Class Action Administration
- Mass Tort Solutions
- Regulatory and Voluntary Remediation
- Document Processing & Admin Support
- Shared Services: Marketing, Billing, AP/AR
- Office Services
- Print & Mail Fulfillment
- Records Management & Information Governance
- Hospitality & Concierge
- Bankruptcy Services
- Corporate Restructuring
- Trustee Services
- Epiq Bankruptcy Analytics
- Financial Services
- Pharmaceuticals
Technologies
- Epiq Case Power
- Epiq Notify
- Digital Mailroom
- Epiq Reporting & Analytics
- Smart Lockers
- Workspace Management & Hoteling
- Epiq Facilitator
- Epiq Discovery
- Epiq Processing
- Epiq Chat Connector
- AI Practice Group
- Client Portal
- Data, AI, and Analytics Platform
- Application and Services
- Infrastructure
- Amazon Web Services

Epiq Access
- Epiq Access Login
- About Epiq Access
- Meet the Experts
- The Epiq Difference
- Epiq Legal Service Management
- Corporate Social Responsibility
- Diversity, Equity, and Inclusion
- Environment, Social, and Governance
- Search Case Studies
- Blog | The Epiq Angle
- Blog | Epiq Advice
- Newsletters
- Podcasts | Cyberside Chats
- Whitepapers
Case Study: Epiq Uniquely Equipped to Administer Claims Process in Data Breach Affecting Millions
Capital One, an American Bank Holding company

United States

Client need
In July 2019, Capital One announced that it had been the victim of a criminal cyberattack on its systems. The attacker gained unauthorized access to the personal information of approximately 98 million U.S. consumers.
Client solution
With decades of experience as a class action claims administrator, Epiq was uniquely equipped to handle this case. Epiq assigned its Complex Claims Team to the project because it specializes in accurately and efficiently administering complicated data.
Notably, the sheer size of the notifications required for the breach presented unique logistical considerations. Epiq rose to the challenge by implementing an extensive notification campaign that was distributed to millions of email addresses and physical addresses, making it one of the largest datasets it has handled.
Epiq has handled some of the largest data breach settlement administrations in the U.S., and offers a scalable, global infrastructure for providing related services.

Results and Benefits
Skillful administration.
by Epiq’s Complex Claims Team yielded an efficient and accurate resolution
settlement administration
claims processed
website visits

Beyond Headlines: Case Study- The Equifax Data Breach and Lessons Learned
The Equifax data breach in 2017 stands as a stark reminder of the critical importance of robust cybersecurity measures in an era of escalating digital threats. In this case Beyond Headlines: Case Study- The Equifax Data Breach and Lessons Learned guide, we analyze the intricate details of the breach, examining the vulnerabilities that led to the compromise of the sensitive personal information of millions of individuals. By dissecting the Equifax incident, we aim to extract valuable lessons that can guide organizations in fortifying their defenses and implementing proactive strategies to safeguard against similar cyber threats in the future.

What Is Equifax?
Equifax is a consumer credit reporting agency that gathers and maintains financial and personal information on individuals. As one of the three major credit bureaus in the United States, Equifax plays a crucial role in assessing creditworthiness for lenders and financial institutions by providing a comprehensive credit report, offering a snapshot of an individual’s credit history and financial behavior.
The Background of the Equifax Breach
The background of the Equifax breach can be traced back to a series of cybersecurity vulnerabilities and failures within the company’s infrastructure. Equifax, one of the largest credit reporting agencies in the United States, suffered a massive data breach in 2017, exposing sensitive personal information of approximately 147 million consumers. This breach had far-reaching consequences, as the stolen data included names, social security numbers, birth dates, addresses, and in some cases, driver’s license numbers. The breach not only compromised the privacy of millions of individuals but also put them at risk of identity theft .
The Equifax breach highlighted the severe consequences of data breaches and the vulnerabilities that exist within credit reporting agencies. In this case, the breach was caused by a failure to patch a known vulnerability in a software application that was used to handle consumer disputes. Additionally, Equifax failed to implement adequate security controls, allowing the attackers to gain access to sensitive data. This incident served as a wake-up call for both organizations and individuals regarding the importance of protecting personal information and the potential risks associated with data breaches.
Scope and Impact of the Data Breach
Equifax’s data breach incident compromised the personally identifiable information (PII) of approximately 147 million consumers, making it one of the largest data breaches in history. The scope of the Equifax data breach was staggering. The stolen information included names, Social Security numbers, birth dates, addresses, and in some cases, driver’s license numbers. This treasure trove of sensitive data provided cyber criminals with the means to commit identity theft, fraud, and other malicious activities. The impact was felt not only by the affected individuals but also by the financial industry and the overall economy.
The consequences of this breach were severe. Individuals faced the risk of financial loss, damaged credit scores, and the arduous task of mitigating the potential damage caused by identity theft. Moreover, the breach eroded public trust in Equifax and raised concerns about the security practices of credit reporting agencies. The incident prompted regulatory scrutiny, and lawsuits, and calls for stronger data protection and breach notification laws.
Vulnerabilities in Equifax’s Security Infrastructure

One of the key vulnerabilities was Equifax’s failure to patch a known vulnerability in the Apache Struts web application framework. The vulnerability, which was disclosed months before the breach, allowed attackers to execute arbitrary code and gain remote access to Equifax’s systems. Equifax’s failure to apply this critical patch demonstrated a lack of effective vulnerability management, leaving their systems exposed to exploitation.
Additionally, Equifax’s security breaches were further exacerbated by poor data security practices. For example, the breach was facilitated by the use of weak passwords and outdated security certificates, which made it easier for attackers to infiltrate the company’s network undetected.
Poor data governance serves as a stark reminder of the importance of proactive vulnerability management and robust data security practices. Failure to do so can have severe consequences, both for the organization and the individuals whose sensitive information is at risk.
Timeline of Events Leading Up to the Equifax Data Breach
The sequence of events leading up to the Equifax data breach unveiled key insights into the weaknesses present in the company’s security infrastructure.
In March 2017, the United States Computer Emergency Readiness Team (US-CERT) alerted Equifax about a critical vulnerability in Apache Struts, a widely used web application framework. Equifax, unfortunately, failed to patch the vulnerability promptly, leaving their systems exposed to potential attacks.
Fast forward to May 2017, cybercriminals began exploiting the unpatched vulnerability and gained unauthorized access to multiple Equifax databases. For over two months, the attackers clandestinely navigated through Equifax’s network, undetected.
On July 29, 2017, Equifax discovered the breach but failed to contain it immediately. It took the company another six weeks before publicly disclosing the incident on September 7, 2017. It revealed that sensitive information of 143 million consumers, including names, Social Security numbers, birth dates, addresses, and in some cases, driver’s license numbers, was compromised.
On September 15, 2017, Equifax revised the number of affected individuals to 147 million and acknowledged that additional personal information, such as credit card details for over 200,000 people, was also exposed.
The aftermath triggered intense scrutiny from regulatory bodies, Congress, and the public. Equifax faces legal actions, investigations, and a significant decline in its stock value. The incident underscores the urgency for companies to prioritize cybersecurity and prompt disclosure in the face of data breaches.
Response and Handling of the Breach by Equifax
In response to the Equifax data breach, the company’s handling of the incident was marked by delays and a lack of effective containment measures. This mismanagement further exacerbated the impact of the breach, resulting in significant damage to Equifax’s reputation and customer trust .
Several key issues emerged during the company’s response and handling of the breach:
Slow Response Time
Equifax took six weeks to disclose the breach publicly, which allowed hackers ample time to exploit the stolen data. This delay hindered the company’s ability to mitigate the breach’s consequences effectively.
Inadequate Containment Measures
Equifax failed to implement immediate containment measures, such as isolating compromised systems and disabling unauthorized access. This oversight allowed hackers to continue accessing sensitive information, prolonging the breach’s duration.
Poor Communication
Equifax’s initial response lacked transparency and clarity, leaving affected individuals and stakeholders in the dark. The company’s communication efforts were widely criticized for being vague, generic, and lacking empathy towards those impacted.
Legal and Regulatory Implications for Equifax

One of the key regulatory agencies involved was the Securities and Exchange Commission (SEC). The SEC launched an investigation into Equifax’s cybersecurity practices and potential breaches of securities laws. This scrutiny highlighted the importance of data governance and the need for companies to have robust systems in place to protect sensitive information.
The Equifax data breach had profound legal and regulatory implications, prompting investigations and legal actions from various fronts. Following the breach, Equifax also faced scrutiny from federal and state regulatory bodies, including the Federal Trade Commission (FTC) and the Consumer Financial Protection Bureau (CFPB). These agencies examined whether Equifax had taken appropriate measures to secure consumer data and if the company had complied with data protection laws and regulations. The breach also sparked numerous class-action lawsuits from affected individuals seeking compensation for the mishandling of their personal information. Equifax ultimately agreed to settle these lawsuits, leading to one of the largest data breach settlements in history, with a fund of over $575 million established to compensate victims and enhance cybersecurity measures. The Equifax settlement team, ensured only affected individuals got compensated.
Furthermore, the Equifax incident contributed to a broader conversation around the need for enhanced data protection legislation. In its aftermath, lawmakers and regulators called for more stringent regulations to safeguard consumer data and hold companies accountable for data breaches. This momentum led to discussions about updating existing data protection laws and introducing new regulations to ensure that companies, particularly those handling sensitive consumer information, implement robust cybersecurity measures. The Equifax data breach, therefore, had a lasting impact on the legal and regulatory landscape, influencing policies aimed at fortifying cybersecurity practices and protecting individuals’ privacy in the digital age.
Lessons on the Importance of Proactive Security Measures
Equifax’s data breach serves as a stark reminder of the necessity for implementing proactive security measures. The incident highlighted the critical importance of patch management and the timely application of software patches and security updates.
The following lessons can be drawn from this breach:
Importance of Employee Training in Preventing Data Breaches
Employee training plays a crucial role in preventing data breaches by creating a culture of security awareness within an organization. It empowers employees to understand the potential consequences of their actions and make informed decisions when handling sensitive data. Through training programs, employees can learn about best practices for data protection, such as strong password management, recognizing phishing attempts, and securely handling customer information.
Lessons learned from the Equifax data breach highlight the need for continuous training efforts. Organizations should regularly update their training programs to address emerging threats and evolving technologies. Additionally, training should not be limited to IT staff alone; all employees, regardless of their role, should receive training on data security practices.
Best Practices for Secure Storage and Encryption of Data

Effective data security requires the implementation of best practices for secure storage and encryption of data. In the wake of the Equifax data breach, it has become even more crucial for organizations to adopt robust strategies to protect their confidential data.
Here are best practices for secure storage and encryption of data:
Utilize Encryption at Rest
Encrypting data at rest ensures that even if the physical storage medium is compromised, the data remains unreadable and unusable. Employing strong encryption algorithms and secure key management systems is essential to prevent unauthorized access.
Implement Strong Access Controls
Limiting access to sensitive data through role-based access controls and multifactor authentication can significantly reduce the risk of data breaches. Regularly reviewing and updating access privileges, and promptly revoking access for terminated employees, is crucial.
Regularly Backup Data
Maintaining regular backups of data is essential to mitigate the impact of data breaches. Backups should be stored securely, preferably in an offsite location, and regularly tested to ensure their integrity and availability.
By adhering to these best practices, organizations can enhance their data security posture, minimize the risk of data breaches, and protect the confidentiality and integrity of sensitive information.
The Significance of Regular Security Audits and Updates
The Equifax data breach highlighted the significant risks faced by organizations when it comes to protecting corporate data. Security audits play a crucial role in identifying vulnerabilities and weaknesses within an organization’s systems and processes. By conducting regular audits, organizations can proactively identify potential security gaps and take necessary steps to address them. These audits can assess the effectiveness of existing security measures, identify potential areas of improvement, and ensure compliance with industry standards and regulations.
Updates are equally important in maintaining data security. As cyber threats evolve rapidly, organizations must stay one step ahead by implementing the latest security patches and updates. This includes updating operating systems, software, and firmware to address any known vulnerabilities. Regular updates can help protect against emerging threats and ensure that systems are equipped with the latest security features. The absence of regular audits is what allows human error to deviate from the intended course.
Building a Culture of Cybersecurity Awareness
Creating a culture of cybersecurity awareness is imperative for organizations to mitigate the risks of data breaches and protect sensitive information.
To build a culture of cybersecurity awareness, organizations should consider the following:
Education and Training
Implement comprehensive cybersecurity training programs for employees at all levels. This should include regular updates on emerging threats, best practices for data protection, and how to identify and report suspicious activities.
Strong Leadership
Foster a culture where cybersecurity is seen as a top priority by leadership. This includes establishing clear policies and procedures, enforcing accountability, and promoting a proactive approach to cybersecurity.
Continuous Monitoring and Assessment
Regularly assess the organization’s cybersecurity posture through audits, vulnerability scans, and penetration testing. This will help identify any weaknesses or gaps in existing security measures and allow for timely remediation.
The Need for Transparency and Timely Communication

When the breach occurred in 2017, Equifax initially failed to disclose the incident promptly, delaying the provision of crucial information to affected individuals. This lack of transparency not only hindered the victims’ ability to take immediate action to protect themselves but also eroded public trust in the company’s ability to handle the situation responsibly.
Timely communication is equally critical in a data breach scenario. Delayed or inadequate communication can exacerbate the consequences of the breach, allowing hackers more time to exploit stolen information and leaving affected individuals vulnerable to further harm. Equifax’s delayed response meant that millions of consumers were left in the dark for an extended period, unaware that their data had been compromised.
Collaboration and Information Sharing Among Organizations
Effective collaboration and information sharing among stakeholders is vital in addressing the aftermath of a data breach and minimizing its impact. Organizations must recognize the importance of working together to combat cyber threats and protect sensitive information.
Here are aspects to consider when it comes to collaboration and information sharing among organizations:
Establishing Partnerships
Organizations should foster relationships with industry peers, government agencies, and cybersecurity experts to share best practices, threat intelligence, and incident response strategies. By collaborating with others, organizations can gain valuable insights and enhance their overall security posture.
Creating Information – Sharing Platforms
It is crucial to establish platforms that facilitate the sharing of threat intelligence and incident data among organizations. These platforms enable real-time information exchange, allowing organizations to stay updated on emerging threats and take proactive measures to protect their systems and data.
Building a Culture of Trust
Collaboration requires trust among organizations. To foster this trust, it is essential to promote a culture of transparency, openness, and accountability. Organizations should be willing to share information about breaches and vulnerabilities without fear of reputational damage. By doing so, they can collectively learn from each other’s experiences and strengthen their defenses against cyber threats.
The Impact of the Equifax Breach on Consumer Trust
The impact of the Equifax breach on consumer trust cannot be overstated. It has shaken the confidence of individuals in the ability of organizations to safeguard their information. Consumers now question the security measures implemented by companies, demanding more transparency and accountability. This breach has underscored the importance of data protection and the need for stringent cybersecurity measures.
Lessons learned from the Equifax breach have prompted organizations to reevaluate their security practices and invest in robust systems to protect consumer data. Companies are now recognizing the critical role of trust in maintaining customer loyalty and are taking steps to regain that trust. This breach has also prompted regulatory bodies to strengthen data protection laws, imposing stricter penalties for negligence and non-compliance.
In the aftermath of the Equifax breach, consumers are more cautious about sharing personal information and are more likely to scrutinize the security measures employed by organizations. The impact of this breach has extended beyond Equifax, affecting the broader landscape of data security. Restoring consumer trust requires organizations to prioritize data protection and adopt proactive measures to secure sensitive information.

Steps Individuals Can Take to Protect Their Personal Information
As individuals navigate the aftermath of the Equifax breach and its impact on consumer trust, it is crucial to understand the steps they can take to protect their personal information. In a world where data breaches have become increasingly common, individuals need to be proactive in safeguarding their sensitive data.
Here are important steps individuals can take to protect their personal information:
Enroll in Credit Monitoring Services
Credit monitoring services can provide individuals with real-time alerts regarding any suspicious activity on their credit reports. This allows individuals to detect potential identity theft or fraudulent activity early on and take necessary actions to mitigate the damage.
Strengthen Password Security
One of the most common ways hackers gain access to personal information is through weak passwords. Individuals should create strong, unique passwords for each online account they use and consider using a password manager to securely store and manage their passwords.
Regularly Review Credit Reports
It is important for individuals to regularly review their credit reports from all three major credit bureaus. By monitoring their credit reports, individuals can quickly identify any unauthorized accounts or discrepancies and take appropriate actions to rectify the situation.
Frequently Asked Questions
What recommendations emerged for other companies from the equifax case study.
Other companies can learn from the Equifax case study by prioritizing regular security audits, promptly addressing software vulnerabilities, and ensuring transparent communication in the event of a data breach. Establishing robust incident response plans and investing in advanced cybersecurity measures are crucial to mitigating the risks associated with handling sensitive consumer information.
What Changes Did Equifax Make in Response to the Data Breach?
Equifax implemented various changes in response to the data breach, including enhancing its cybersecurity measures, investing in technology upgrades, and appointing new executives with a focus on security. The company also settled legal actions and established a fund for compensating affected individuals. The incident prompted a reevaluation of Equifax’s practices and a commitment to prioritizing data security.
How Did Equifax Handle the Breach, and What Criticisms Did It Face?
Equifax faced criticism for its delayed response in detecting and disclosing the breach. The company took several weeks to notify the public after discovering the intrusion, leading to concerns about the effectiveness of its cybersecurity measures and transparency in communication.
Was There Inside Trading in the Equifax Data Breach?
There were suspicions of insider trading in the Equifax data breach. Several executives, including the Chief Financial Officer, sold shares worth millions of dollars shortly after the breach was discovered but before it was publicly disclosed, leading to investigations by regulatory authorities to determine if any insider trading laws were violated.
The Equifax data breach serves as a stark reminder of the far-reaching consequences that can arise from lapses in cybersecurity. Beyond the headlines, this case study illuminates the critical importance of proactive measures to safeguard sensitive consumer information, emphasizing the need for rapid response, transparent communication, and robust data protection practices. As businesses continue to navigate the digital landscape, the lessons learned from the Equifax incident underscore the imperative to prioritize cybersecurity, foster a culture of vigilance, and enact comprehensive measures to fortify defenses against ever-evolving cyber threats.
Leave a Comment Cancel reply

Be better prepared for breaches by understanding their causes and the factors that increase or reduce costs. Explore the comprehensive findings from the Cost of a Data Breach Report 2023. Learn from the experiences of more than 550 organizations that were hit by a data breach.
This report provides valuable insights into the threats that you face, along with practical recommendations to upgrade your cybersecurity and minimize losses. Take a deep dive into the report and find out what your organization is up against and how to mitigate the risks.
The global average cost of a data breach in 2023 was USD 4.45 million, a 15% increase over 3 years.
51% of organizations are planning to increase security investments as a result of a breach, including incident response (IR) planning and testing, employee training, and threat detection and response tools.
The average savings for organizations that use security AI and automation extensively is USD 1.76 million compared to organizations that don’t.
Gain insights from IBM X-Force experts
Get the most up-to-date information on the financial implications of data breaches. Learn how to safeguard your organization’s reputation and bottom line.
Check out the recommendations based on the findings of the Cost of a Data Breach Report and learn how to better secure your organization.
Only 28% of organizations used security AI extensively, which reduces costs and speeds up containment.
Innovative technologies such as IBM Security® QRadar® SIEM use AI to rapidly investigate and prioritize high-fidelity alerts based on credibility, relevance and severity of the risk. IBM Security® Guardium® features built-in AI outlier detection that enables organizations to quickly identify abnormalities in data access.
If you need to strengthen your defenses, IBM Security® Managed Detection and Response (MDR) Services use automated and human-initiated actions to provide visibility and stop threats across networks and endpoints. With a unified, AI-powered approach, threat hunters can take decisive actions and respond to threats faster.
Explore QRadar SIEM
Explore Managed Detection and Response Services
82% of breaches involved data stored in the cloud. Organizations must look for solutions that provide visibility across hybrid environments and protect data as it moves across clouds, databases, apps and services. IBM Security Guardium helps you uncover, encrypt, monitor and protect sensitive data across more than 19 hybrid cloud environments to give you a better security posture. IBM data security services provide you with advisory, planning and execution capabilities to secure your data, whether you’re migrating to the cloud or need to secure data already in the cloud. Services include data discovery and classification, data loss prevention, data-centric threat monitoring, encryption services and more.
Explore the Guardium data security portfolio
Learn about data security services
Build security into every stage of software and hardware development. Employing a DevSecOps approach and conducting penetration and application testing are top cost-saving factors in the report. X-Force® Red is a global team of hackers hired to break into organizations and uncover risky vulnerabilities that attackers may use for personal gain. The team's offensive security services—including penetration testing, application testing, vulnerability management and adversary simulation—can help identify, prioritize and remediate security flaws covering your digital and physical ecosystem.
Discover X-Force Red offensive security services
Explore our mobile security solution
Knowing your attack surface isn’t enough. You also need an incident response (IR) plan to protect it. The IBM Security® Randori platform uses a continuous, accurate discovery process to uncover known and unknown IT assets, getting you on target quickly with correlated, factual findings based on adversarial temptation. With X-Force® IR emergency support and proactive services, teams can test your cyberattack readiness plan and minimize the impact of a breach by preparing your IR teams, processes and controls.
Get IBM Security Randori
Explore X-Force for incident response
IBM Security helps protect enterprises with an integrated portfolio of products and services, infused with security AI and automation capabilities. The portfolio enables organizations to predict threats, protect data as it moves, and respond with speed and precision while allowing for innovation.
- Data Breach Response
- Privacy Audit
- Review & LSPs
- Hospital PHI Breach Case Study
Canopy Achieves “Impossible” Data Breach Response for Hospital Network
The challenge.
A large hospital network experienced a protected health information (PHI) breach, with over 6,600 compromised PDFs — some containing up to 180,000 rows of information and over 150,000 individuals — and densely packed with PHI. Patients’ information was frequently duplicated with different PHI each time. The hospital network needed to work quickly in order to comply with the HIPAA Breach Notification Rule.
The Solution
Canopy’s algorithms recognized the information inside the PDF tables, extracting each data element and transforming them to a structured format. Then, Canopy’s advanced PHI detection algorithms identified each element of PHI. Our machine learning models deduplicated the entities into a list of unique patients and all their PHI, maintaining links to source documents.
"It was not humanly possible for our team to do this — it would have taken a couple hundred reviewers years to complete this project. We can’t even fathom the cost savings."
Project Lead
- Automated data extraction from tables in over 6,600 lengthy Crystal Reports (PDFs), some containing over 180,000 rows
- Deduplicated 4.28 billion entities to just 3 million unique patients, reducing entity list by 99%
- Enabled hospital network to comply with HIPAA Breach Notification Rule
- Saved team millions of man hours & completed "impossible" project in 15 days
By the Numbers

Crystal Reports (lengthy PDFs)

4.28 billion
entities, often frequently duplicated

for Canopy to complete the entire project

Request Case Study
See how Canopy saved one team millions of man hours with automated PDF data extraction and machine learning-powered deduplication.
Request a Demo
See how Canopy's Data Breach Response software leverages machine learning at every step, from PII detection through to generating a notification list .
Get These Results for Your Data Breach Response
Request your personalized demo to see how Canopy's AI-powered solution can transform your workflow.

Pell Center
The Pell Center for International Relations and Public Policy at Salve Regina is a multidisciplinary research center focused at the intersection of politics, policies and ideas.

The Equifax Breach is a Case Study in Why We Need a National Data Notification and Protection Law: Picks of the Week
“The Time is Now for Congress to Act of a National Data Breach Notification Law” | The Hill
“Equifax Breach Prompts Scrutiny, but New Rules May Not Follow” | The New York Times
“The single most depressing thing about the Equifax breach” | The Washington Post
It took over six weeks for credit bureau Equifax – one of the three major credit reporting firms in the U.S. – to disclose the massive data breach that potentially compromised confidential information of 143 million customers – or nearly half of the U.S. population. Aside from the reports on the company’s sloppy cybersecurity measures that made it a low-hanging fruit for hackers and its subsequent handling of what appears to one of the worst data breaches in recorded history, the fact that the company took so long to notify customers is appalling – but given the patchwork of data breach notification laws in the US and the still-too-common disregard for industry-wide cybersecurity standards, it was not all that surprising.
Breached companies often choose to delay notification of hacks, putting customers at risk while avoiding consequences. While there may be legitimate reasons to delay informing consumers about a data breach, such as an ongoing criminal investigation by law enforcement or the need to assess the full scope of the hack and extent of the damage before letting consumers know and possibly causing panic, companies often wait to go public about a data breach because they fear the damages a hack will have on their reputation, customer trust, stock value, and overall revenues.
In the case of Equifax, the company’s slowness first in patching a known vulnerability and then in effectively responding to the hack and notifying customers, combined with its high-level executives who apparently sold off almost $2 million worth of stocks days after the breach was discovered, shows a complete lack of leadership and real concern about customers’ privacy and security. Equifax has yet to disclose why it waited so long to inform customers about the breach and, in the meantime, two top executives have stepped down , the legal team and the Board are bracing for probes by the federal and state authorities and a slew of class-action lawsuits, and the CEO is preparing to testify before the U.S. Congress.
What sets Equifax’s breach apart, however, has less to do with their undue delays or with the numbers of records breached – Yahoo’s data breach last year affected as many as one billion accounts – than with the high-value of the data exposed. The data that was accessed by still-unknown hackers includes a trove of names, birth dates, Social Security numbers, addresses, driver’s license numbers, and even credit card and bank account numbers. Even individuals that never used Equifax were affected. Indeed, consumers have almost no control over whether their information is absorbed into credit bureaus like Equifax , Experian , and Trans Union , and do not have to provide consent for them to use and process their personal data. If you ever applied for a mortgage, a credit card, a cellphone plan, or to buy a car, Equifax, or a similar company likely has your information which is used to rate your credit-worthiness to banks, home sellers, auto sellers and others.
With so much personal information, criminals can easily impersonate you, take out new lines of credit in your name, file fraudulent tax returns, take out prescriptions, and craft even more sophisticated phishing emails and scams. This type of cyber risks are not isolated to Equifax, but this massive data breach revealed another inherent flaw in the U.S .: the over-reliance on Social Security numbers and the skewed credit reporting system that is in urgent need of reform. The wide use of SSNs in both government and private sectors, and the ease of using it to access highly-sensitive accounts, has made hacking systems such as credit reporting agencies even more appealing to cyber criminals.
Unfortunately, companies are not incentivized to prioritize security, resiliency, and privacy, and there is little national oversight on how companies handle data. Indeed, most companies constantly collect and store data even just because they might want to use it sometime in the future – there is no law that forces them to only collect the bare minimum of data necessary, or that limits how long a company can store data, or that requires to encrypt everything they collect, or that imposes regular security audits. When it comes to notifying consumers that their data has been stolen, laws in the U.S. vary state to state and differ in how much time and how much information companies are required to divulge, and whether to notify other parties beside the affected people (such as state attorney generals, credit bureaus or regulators). Past calls in Congress to establish a nationwide standard have repeatedly fizzled . The result is a muddled patchwork of 48 different state laws governing data breach notification, and timing is only specified in eight states and varies anywhere from 10 to 90 days. Rhode Island’s law , for instance, requires notification to be made within 45 days from the discovery of a breach. Georgia – where Equifax is based – has no timeline specified for when a company must notify customers about a breach. Alabama and South Dakota don’t even have a data breach notification law on the books. For comparison, the European Union ’s new General Data Protection Regulation, which comes into effect next year, requires that any data breach be reported within 72 hours.
Big hacks like the Equifax fiasco put into context just how much control organizations have over our personal information, how much information is regularly collected, and how valuable (and vulnerable) that information is. But as the digital world increasingly dictates where we work, play, and live our lives, we need to have control — or at the very least, basic knowledge — over what data is being collected about each one of us, where it is stored, who has access to it, and how it is being protected.
While Congress debates the merits of the various proposals to establish a national data notification and protection law , if you were a victim of this latest enormous breach (assume you were!), here are a few things you should do to protect yourself:
- Check your credit accounts immediately and regularly for any suspicious activity, and continue to monitor your credit card and bank accounts for the foreseeable future;
- Set up a fraud alert;
- Freeze your credit accounts – meaning no one can open an account (transfer money), buy a car, house or other big item – using your SSN, CC, bank account, etc.
- Set up two-factor authentication on important financial accounts to deflect hackers with stolen information;
- If you have children, enroll them into allclearid.com/ .
- ← Sunshine Menezes on “Story in the Public Square” September 23, 2017
- Pell Center Study Warns Russia Threat is Bigger than the 2016 Election →
Leave a Reply
Your email address will not be published. Required fields are marked *
Powering Data Breach Response With AI: A Case Study
Contributor.
At Seyfarth, I'm not just an attorney—I'm also an ethical hacker and digital forensic expert, and I'm proud to be one of several "attorneys who code" at Seyfarth. Here, we're passionate about technology, and we routinely seek creative ways to leverage innovations that enhance client services.
I've found that one area where emerging technology can make an enormous impact is in the data breach notification assessment space. Specifically, I've found that artificial intelligence can power the evaluation of implicated data for personal information like PII and PHI to determine notice requirements in the various implied jurisdictions. While there are many ways to accomplish that evaluation, I wanted to share my experience partnering with Text IQ, a company that builds AI for sensitive information, to power a data breach response in a blind study alongside the traditional document review and coding approach. The result was reduced risk, quicker turnaround time, and cost reduction for Seyfarth's client.
Casting an Epidemic
The specter of a data breach is an unfortunate reality for anyone that uses a computer. Corporations are obviously large targets, with potentially
thousands of employees doing things on computers. Some of those things are good, and some put the company at risk. Aside from the rapid evolution of attack sophistication and complexity, regulators are also raising the stakes in terms of liability for data breaches and security incidents
Privacy-related data incidents and data breach matters are governed by a proliferating list of statutes: GDPR, CCPA, the New York SHIELD Act, and many others from various states and companies. After they experience a security incident and confirm a data breach, corporations tend to rely on traditional methods to evaluate their exposure and act accordingly. However, these methods are breaking down in the face of burdensome regulatory reporting requirements, often within highly constrained timeframes. One of the shortest of these is GDPR's "long weekend" reporting period of only 72 hours.
As companies grow, their potential attack surfaces expand accordingly. This is evident in data breach statistics. One data breach tracker estimates that 68 records are stolen every second , thanks of a broad cast of bad actors:

In the wake of a security incident, a decent incident response will generally take some form of the following course:
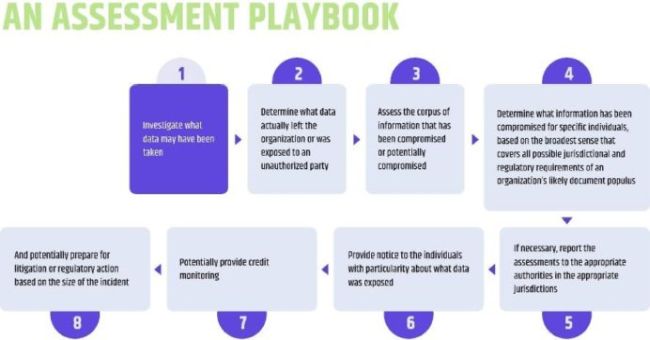
Out with the Old
Relying on traditional methods, this assessment can be a significant challenge for identifying personal information like PII and PHI.
In the status quo, search terms and search expressions may be used to find patterns and PI, and contract attorneys are hired to review the documents and log PI that has been compromised to support the various notice requirements of any jurisdiction that's implicated.
This traditional model has inherent barriers:
- Understanding the individuals whose PI has been exposed in a dataset is a challenge that calls for an entity view. But the status quo provides only a document view with embedded entities.
- There are myriad types of documents that could contain PI. How does one account for all potential government IDs, tax documents, bank documents, licenses, etc.? Even with complex and comprehensive RegEx, there's a risk of missing "models" of PI that may exist across the world. As a result, search terms and expressions suffer from inconsistent results and may miss non-obvious data. Unstructured data sources are very difficult to submit to this kind of process.
- Similar to the above, the concept of "a search" as a function, with its roots in techniques like Boolean Search and document retrieval, was never designed to navigate large-scale unstructured data, like the data that is exposed in a breach.
- Search terms yield results that are both over- and under-inclusive, requiring extensive human review. And humans are inefficient and error-prone at poring over large amounts of data. We have inconsistent decision-making across brains, and we also tend to provide typos and other ephemera that introduce incorrect data into PI assessment logs.
Taking the above obstacles into account, Seyfarth's cybersecurity attorneys have begun leveraging artificial intelligence in more of our processes, including data breach PI assessment. Our Fortune 200 clients in particular have experienced for themselves how using AI can automate rote and low value work, like document review, and augment high value work—lending human subject matter expertise to exercise judgment and give legal advice.
In our first project with Text IQ, we leveraged its AI-powered solution, Text IQ for Legal, to reduce the cost and burden of conducting privilege reviews and generating logs. Subsequently, we used another of its offerings, Text IQ for Privacy, in a Proof of Concept project to identify PI after a client suffered a data breach. To compare Text IQ with traditional document review, we conducted a blind study of human versus machine.
The results speak for themselves:

AI for Data Breach Response
Being an (ethical) hacker of things and naturally curious technologist, I wanted to know more about how it works. There are three innovations that have allowed Text IQ to achieve this kind of accuracy in PI detection.
- Social Linguistic Hypergraph TM : Text IQ combines social signals with language signals to do something better than perhaps any other AI company out there: find all traces of an individual in a dataset. Its trained machine learning models can understand meaning on a semantic level (e.g. what meaning is intended), as opposed to merely a lexical level (e.g. what terminology is used). As a result, its AI can detect concepts that capture special category information, like political opinions, genetic data, and race and ethnicity.
- Continuous Learning: Text IQ generates interactive dashboards with automatic PII and PHI linking, powering drill-down analysis and data exploration. The user can override or select highlighted PI in each document, and that feedback is automatically re-ingested into the machine in an iterative process that allows the models to self-improve over time.
- The Human Index TM : In addition to document-centric reports, Text IQ provides entity-centric reports with individuals in a column, and all their associated PI traces in rows. This is a new view that allows for a question that we couldn't ask before: what are all the traces of PII and PHI that exist in this dataset for this individual?
Relying on the status quo to understand large-scale unstructured data is risky. It's also potentially time-consuming and expensive. Today, AI can completely and reliably automate the low value work of PI identification in document review and reduce risk. It lets cybersecurity practitioners like me better serve our clients.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

United States
Mondaq uses cookies on this website. By using our website you agree to our use of cookies as set out in our Privacy Policy.

Data Breach Response
Swift, Complete, and Cost-Effective Data Breach Response for Global Law Firm Client After Cyber Attack

- Urgent need to isolate data sets containing Personally Identifying Information (PII) and Protected Health Information (PHI)
- Unforgiving deadlines for legally-required notification of individuals with PII/PHI potentially exposed in the attack
- Project required identifying and eliminating redundant material concerning PII/PHI of individuals and entities
- Requirement to limit costs , from initial data analysis through completion of a ‘clean’ spreadsheet without redundant material (e.g., duplicative entries for an individual because multiple datasets contained their PII/PHI)
- Extensive data mining process to identify PII and PHI using Canopy’s artificial intelligence and machine learning capabilities, its built-in, data-driven regular expression searches, and Elevate’s searches tailored to project-specific requirements
- Creation of custom coding layout that increased the efficiency of Canopy’s automation tools (e.g., its mapping feature to automatically capture dense PII and PHI in spreadsheets, charts, and tables within minutes)
- Comprehensive, optimised processes for consolidating relevant information about each individual across all sources into a single notification list entry that preserved information on the sources of any duplicative material
90% reduction in cost of review achieved via a comprehensive data mining exercise that identified and eliminated ~92% of data as irrelevant or duplicative
Savings from using india-based review teams with lower hourly rates, economical options for retaining data after project ended, rapid determination of necessary scope of the review based on detailed analysis using the comprehensive impact assessment report that elevate generated within 24 hours, dramatic reduction (i.e., weeks) in time required for necessary review using elevate’s comprehensive data mining capability to identify duplicative and irrelevant documents, met relevant deadlines , with non-stop (i.e., 24×7) work by india-based team, ensuring project concluded within allotted time.

Subscribe to our newsletter
- *First Name: *
- *Last Name: *
- *Email Address *
- Company Name
- How did you hear about us? Search Engine Social Media Recommended by Friend or Colleague Blog or Publication Industry Event Other
- Please specify
- Comments This field is for validation purposes and should be left unchanged.
How Medibank allegedly ignored the warning signs in one of Australia's worst cybersecurity breaches
Pity the IT guy.
Logging in via his work computer, he did what a lot of people do.
He saved his username and password to his personal internet browser.
Those credentials then "synced" across to his personal computer.
But as the employee of a contractor to private health insurance giant Medibank, he unwittingly opened the back door to an alleged Russian cybercriminal and one of the worst reported privacy breaches in Australian history.
More than one in three Australians suddenly found themselves at risk of having their most sensitive data leaked for public consumption.
This nightmarish scenario came true for hundreds of people in November and December 2022, with pregnancy terminations among the procedures published in detail on the so-called dark web.
Medibank chief executive David Koczkar branded the move "disgraceful" as the insurer, in line with conventional wisdom, refused to pay a ransom.
In the year following the hack, Medibank boosted its revenue and gross profit to $7.1 billion and $727.1 million respectively.
It's not the hapless IT contractor but the big corporate machine that the Australian Information Commissioner is now seeking to hold to account.
It's filed a Federal Court action, claiming the private health insurer had breached the privacy act for each of the 9.7 million individuals. Each contravention can attract a maximum fine of $2.22 million.
In court documents, the commissioner has laid out a timeline of alleged cybersecurity blunders by Medibank amounting to "serious interferences with the privacy of… approximately 9.7 million individuals".
It says on around August 7, 2022, the IT contractor's personal computer was hacked by a "threat actor" who stole his Medibank username and password.
That threat actor, according to the Australian and US governments, was a Moscow-born extortion artist of the first order, who went by online handles including "blade_runner" and "JimJones" .
The Australian government would later implicate Aleksandr Ermakov , who the US government said was linked to REvil, one of the "most notorious cybercrime gangs in the world".
REvil had allegedly pumped out ransomware on about 175,000 computers worldwide to haul in at least US$200 million ($299 million) in ransoms.
The then 32-year-old apparently hoped to squeeze out another $15 million from Medibank.
The AIC claim says the "threat actor" spent weeks obtaining his bargaining chip.
This was the mountain of Medibank client data from names to birthdays, home and email addresses, phone and passport and Medicare numbers, financial information as well as details of employment, race and ethnicity, illnesses, disabilities, injuries, and health treatments.
In Australia, this is the "most sensitive data short of classified data", Cybersecurity expert Iman Tahami told the ABC.
Alerts 'not appropriately escalated'
The hackers waited five days to test the IT contractor's admin account credentials by logging onto Medibank's Microsoft Exchange server.
About 11 days after that, they got into Medibank's "Virtual Private Network" (VPN) which controlled remote access to its corporate network.
They were only able to do so because Medibank, the $10 billion juggernaut and keeper of secrets for more than 9 million people, didn't require what's called "multi-factor authentication" for its VPN, according to the commissioner's filings.
This requirement for two or more ways of proving a user's identity was even then a bog-standard safeguard for large organisations.
Instead, the hackers only needed someone's username and password.
Still, about that time, the hackers' moves tripped a wire with the insurer's security software, which sent alerts to an IT security email.
But it seemed nobody was home.
"These alerts were not appropriately triaged or escalated by either Medibank or its service provider.... at that time," the information commissioner's claim says.
This allegedly left the coast clear for the hackers to get into various Medibank IT systems, including one containing information on how a key database elsewhere was structured.
This was the "MARS" database, which contained "personal information of Medibank's customers, including sensitive and health information".
Between August 25 and October 13, Ermakov and the REvil crew allegedly hoovered up 520 gigabytes worth of that information.
The hackers kept tripping security wires and triggering alerts but these again were "not appropriately triaged or escalated by either Medibank or [its service provider]", the commissioner alleges.
On October 11 — almost two months after the hacker first logged into the system — Medibank's Security Operations team responded to a "high severity incident" and an alert of files being modified to exploit a vulnerability.
They called in a digital forensics service called Threat Intelligence to investigate.
According to the commissioner's claim, until October 16, 2022, when a Threat Intelligence analyst noted the outflow of "suspicious volumes of data" had been taken from the network, "Medibank was not aware that customer data had been accessed by a threat actor and exfiltrated from its systems".
Ermakov and REvil had allegedly been secretly sucking out sensitive data for almost two months.
The hackers broke cover and made contact on October 19 and 22, 2022, giving Medibank a taste of the files it had.
With no ransom paid, the data began leaking out on the dark web over three weeks.
Medibank warned about 'serious deficiencies' in IT security
Given Medibank's "size, resources, the nature and volume of the personal information it held … and the risk of harm for an individual in the case of a breach", it failed to take proper steps to protect its clients' privacy, according to the commissioner's claim.
The fallout of its failure included exposing more than nine million people to "harm including potential emotional distress and the material risk of identity theft, extortion and financial crime", it says.
Medibank's core IT team included 13 full-time IT security professionals, working with a $1 million a year cyber security budget, out of a $4-5 million total budget for IT.
What's more, Medibank was "aware of serious deficiencies in its cybersecurity and information security framework", the commissioner alleges.
Between 2018 and August 2022 — the month of the hack — consultants including KPMG and PricewaterhouseCoopers repeatedly warned Medibank to lift its game around information security.
The commissioner has listed internal audits that highlighted some of Medibank's Achilles heels which allegedly exposed it to the Russian cybercriminals.
These included three tests by Threat Intelligence which identified Medibank's "insecure or weak password requirements" in March and September 2018 and November 2020.
A KPMG report in about August 2021 warned that multi-factor authentication had "not been implemented for privileged users when accessing particular systems, backend portals, or supporting servers".
An internal Medibank presentation months before the hack found that a set of controls to identify gaps in compliance with information security standards mandated by the Australian Prudential Regulation Authority had been "prepared in 2020, but never implemented".
The Federal Court action is being watched intently by law firms circling with separate compensation claims.
Elizabeth O'Shea, an internet-savvy lawyer at Maurice Blackburn acting in a group complaint seeking compensation orders from the commissioner, knew she was stating the obvious: "We welcome this development."
"We're obviously really interested in making sure that [our] representative complaint progresses," she said.
"But we say this is an important step along the way, which suggests that many of the people that we've spoken to have experienced harm as a result of this data breach, that the commissioner will agree with us that they should be entitled to compensation."
Lawyers at Baker McKenzie, which is leading a class action for affected Medibank customers, declined to comment.
Medibank has also declined to comment but in a statement to the ASX, said it intended to "defend the proceedings".
- X (formerly Twitter)
- Computer Science
- Cyber Crime
- Russian Federation

Case Study: Equifax Data Breach
By irini kanaris miyashiro.

Credit Reporting Agencies
The case study of the Equifax data breach exemplifies flaws inherent in management of Credit Reporting Agencies (CRAs). CRAs aggregate and sell historical credit information of individuals and companies. Credit card companies, banks, employers, and landlords sell consumers’ borrowing and repayment history to CRAs. This data is compiled into credit reports which are bought by lenders and used to assess the creditworthiness of individuals applying for loans. Those with a history of reliably paying back loans are more likely to receive credit and favorable interest rates. Credit reports might also be requested by landlords and employers to screen tenants and employees (Dollarhide).
The Players
Equifax
Equifax is a multinational credit reporting agency, founded in 1899 and headquartered in Atlanta, Georgia. One of three major US credit reporting agencies, including Experian and Transunion (known together as “the big three”), Equifax holds the information of millions of consumers and businesses worldwide (Investopedia). Equifax sells both commercial credit reports and consumer credit reports (sold to banks, insurance firms, and healthcare providers among others). Additionally, Equifax sells credit monitoring services, including credit fraud and identity theft prevention services (Equifax).
Equifax CEO Richard Smith
In 2017, Equifax’s management was led by chair and CEO Richard Smith, who took on the role in 2005 (LaMagna).
Equifax CSO Susan Mauldin
In 2017, Equifax’s security division was headed by Susan Mauldin, responsible for designing and implementing Equifax’s first patch management policy. Mauldin proposed comprehensive changes to Equifax’s cybersecurity policy, but by 2017, the majority of her reforms had not yet been implemented (PSI).
Equifax CIO David Webb
In 2017, Equifax’s global technology strategy was managed by David Webb, who was appointed chief information officer in 2010 (Equifax).
Equifax Security and IT
Equifax’s Security and IT teams are the primary divisions responsible for patch management, the process of applying updates to computer assets to address identified security vulnerabilities. Generally, security scans for vulnerabilities on Equifax networks, while IT employees implement necessary software patches (PSI).
Equifax Customers
- Companies or businesses which request the credit reports of consumers or businesses.
- Members of the public or businesses that request credit reports or pay for information about their own credit rating, such as credit monitoring services.
Members of the public assent to their information being shared with CRAs when, for example, they open up bank or credit union accounts, take out a line of credit/mortgage, or open up any kind of credit card (FTC). However, the long and convoluted language of such agreements is rarely read or fully understood, and consumers have no choice but to assent to the sharing of their information if they need a credit card. For the vast majority of people, establishing a credit history is essential to participating in society: credit checks are necessary for being hired, renting a home or taking out a mortgage to buy a home, buying a car on credit or leasing a car, and so on. Most consumers have little option but to share their information (Khalfani-Cox). Consumers who request and pay for credit monitoring services are also clients. But CRAs hold the information of millions of people irrespective of whether they or anyone else has requested a credit report for them. In fact, many members of the public are not even aware of the existence of credit agencies, what their function is, or that such agencies hold their personal information.
Federal Trade Commission (FTC)
The Federal Trade Commission is a government agency responsible for preventing unfair business practices and enforcing consumer protection laws including the Fair Credit Reporting Act (FCRA). The FCRA works to ensure the accuracy, fairness, and privacy of consumers’ credit report information by ensuring that consumers have access to a free credit report every 12 months, access to consumers’ credit information is limited, information provided in credit reports is accurate, and consumers can dispute information in their credit files, among other things (Experian).
Consumer Financial Protection Bureau (CFPB)
The Consumer Financial Protection Bureau is a government agency which oversees financial products and services offered to consumers. The CFPB works with the FTC to regulate CRAs through applicable provisions of the Dodd-Frank Wall Street Reform and Consumer Protection Act, designed to prevent unfair and deceptive acts and ensure “agencies provide meaningful and reliable credit ratings of the businesses, municipalities, and other entities they evaluate” (Hayes). The CFPB may also examine and supervise CRAs’ activities (PSI).
A cybersecurity research firm hired to investigate the Equifax breach (PSI).
Instruments
Personally Identifiable Information (PII)
Equifax’s assets include the PII of consumers whose financial data are collected. PII includes consumers’ names, addresses, dates of birth, social security numbers, and credit card numbers. Loss of PII can lead to identity theft (PSI).
The Apache Struts Vulnerability
A flaw in the popular Apache Struts Java framework, used for Java based web applications, discovered by Chinese cybersecurity researcher Nike Zheng. The software flaw allows hackers to insert malicious code in the “content-type header” of HTTP requests, which is then executed by Struts (Riley, Michael, et al).
Patch Management
Patch management refers to distributing and updating software, often to correct known software errors or vulnerabilities. In cybersecurity, Security and IT divisions maintain patch management systems to prevent hackers from exploiting software vulnerabilities to gain access to company networks (Posey).
IT Asset Inventory
The complete documentation of a company’s hardware and software, as well as the information processed on these computers. Assets are typically documented and then classified by threat level so that the appropriate protections can be installed to defend them. Equifax management proposed a plan to create a complete asset inventory by June of 2017, but at the time of the breach, it had not yet been implemented (PSI).
SSL is a security technology that allows communication between web browsers and servers to be encrypted or converted into code. SSL also allows companies to analyze and detect unusual or suspicious encrypted network traffic. SSL certificates are typically renewed annually (PSI).
In the years leading up to the breach, Equifax struggled with outdated cybersecurity policies and instruments. In April of 2015, former CSO Susan Mauldin implemented Equifax’s first patch management policy. An internal audit of the policy later that year revealed numerous security deficiencies, including over 8500 unresolved software vulnerabilities (PSI). In May of 2016, Equifax’s W-2 Express website was also hacked, resulting in the leak of 430,000 names, addresses, social security numbers, and other types of personal information (Brewster). By 2017, most of Equifax’s security deficiencies had not been remediated, allowing hackers to breach Equifax’s network and harvest the PII of 147 million consumers’ personal information (PSI).
Events began on March 7th of 2017, when Apache publicized and provided a patch for Apache Struts, an easily exploitable software vulnerability. On March 8th, The Department of Homeland Security’s US-CERT team (a division within the DHS responsible for disseminating information on cyber security threats) notified Equifax of the software flaw, and an alert was distributed to 400 employees by Equifax’s Global Threats and Vulnerability Management (GTVM) team (PSI). Apache Struts was also assigned the highest possible criticality score, a 10, by the National Institute of Standards and Technology (NIST) using the Common Vulnerability Scoring System or CVSS (PSI).
On March 10th, hackers breached Equifax’s networks by exploiting Apache Struts via Equifax’s online dispute portal. On May 13th, attackers spread from the infected portal and gained access to other parts of Equifax’s network (Fruhlinger). From May through July, hackers accessed multiple Equifax databases and extracted consumers’ personal information. Stolen data included consumers’ names, addresses, dates of birth, social security number, and credit card numbers (PSI).
After learning of the breach, Equifax GVTM teams attempted and failed to locate Apache struts on servers by conducting multiple network scans. IT and Security’s inability to locate and patch Apache Struts can be attributed to the existing flaws in their cyber security policy, outlined in a report published by the Senate Subcommittee on Investigations (PSI):
Lack of Comprehensive IT Asset Inventory
At the time of the breach, Equifax lacked a complete IT Asset Inventory, meaning they did not know the locations of the Apache struts application on their network. Instead, IT had to conduct network scans, which failed to detect the software.
Failure to follow Patch Management Policy
Equifax’s security policy mandated critical vulnerabilities be patched within 48 hours of discovery, but according to Mandiant, the lack of IT Asset Inventory made meeting this deadline impossible. Struts was ultimately patched 5 months after Equifax learned of the flaw. IT conducted multiple network scans but could not find instances of the vulnerable software. After failing to locate the application, IT and security took no further action to find Struts, and management did not check the vulnerability had been remediated.
IT and Security Management
Communication among employees on the remediation of security vulnerabilities was inconsistent. Equifax held monthly GMTV meetings to discuss new vulnerabilities, but the status of the previous months’ threats was often not discussed, even if they had not yet been remediated (PSI). Equifax did not require attendance from employees or management or keep records of who attended meetings. Additionally, the only employee who knew of Equifax’s use of Apache Struts in the online dispute portal was not included on the GTVM distribution list and did not receive news of the vulnerability. The senior manager who oversaw this lead developer and his team received the alert but failed to relay the information.
Failure to Maintain Cybersecurity Technologies
The severity and duration of the breach was exacerbated by Equifax’s failure to renew an SSL certificate needed to inspect encrypted network traffic. Hackers encrypted their activities on Equifax servers, but because the certificate had expired, incoming traffic was not decrypted, and Equifax had no knowledge of suspicious activities on the online dispute portal.
On July 29th, Equifax renewed the expired SSL certificate designed to inspect encrypted network traffic. IT immediately noticed suspicious activities on Equifax servers, leading to the discovery of the breach (Fruhlinger). On August 2nd Equifax retained law firm King and Spalding LLP, which enlisted Mandiant to investigate the breadth of the breach. Over the next several weeks, Equifax employees identified a list of affected consumers (PSI).
On September 7th of 2017, six weeks after its discovery, Equifax issued a public announcement their networks had suffered a data breach that exposed the personal information of 143 million consumers (Equifax later discovered an additional 4 million affected consumers). Initially many expected the breach would result in widespread identity theft and fraud. Ultimately, investigators came to believe the breach was executed by Chinese state-sponsored hackers as part of a government operation to collect American data (Fruhlinger).
Investigations and Findings
The Equifax breach was investigated by several Federal authorities, including the FBI, the FTC, and the CFPB. An additional insider trading investigation was conducted by the Securities and Exchange Commission (SEC) and the US Attorney’s office in Atlanta related to the sale of $2 million of Equifax stock by executives after the discovery of the breach. Equifax also faced inquiries by at least 34 State attorney generals (EPIC).
Additionally, members of Congress from the House Financial Services Committee, the Senate Banking, Housing, and Urban Affairs Committee, the Senate Commerce, Science, and Transportation Subcommittee, the House Energy and Commerce Committee, the Senate Banking Committee, and the Senate Judiciary Subcommittee on Privacy held congressional hearings covering the breach (EPIC). The breach was also investigated by the Senate’s Homeland Security Permanent Subcommittee on Investigations (PSI), a subcommittee responsible for investigating government operations, compliance with regulations and laws, and cases of crime and fraud which threaten national welfare (HSGAC).
PSI published a detailed report that concluded the breach was likely preventable and outlined Equifax’s history of lax cybersecurity practices. The consensus of investigations was Equifax was responsible for the loss of PII through negligence.
Lawsuits
Equifax faced lawsuits by both local and state governments. The city of San Francisco sued Equifax over violations of California’s unlawful, unfair, or fraudulent business practices law and the city of Chicago sued Equifax over violation of the Illinois Personal Information Privacy Act, the Illinois Consumer Fraud and Deceptive Business Practices Act, and the Chicago Consumer Fraud ordinance (EPIC). Attorney Generals Maura Healey and Curtis Hill also sued Equifax on behalf of their states of Massachusetts and Indiana (Kovacs).
Resignations
CEO Richard Smith, CSO Susan Mauldin, and CIO David Webb resigned in the aftermath of the breach (Horowitz & Wiener-Bronner). Smith retained his full pension, valued over $18 million after his resignation (LaMagna).
Arrests
In 2019, former Chief information Officer Jun Ying was found guilty of insider trading and sentenced to four months in jail. Former Equifax manager Sudhakar Reddy Bonthu was also found guilty of insider trading and sentenced to 8 months of home confinement. No other Equifax employees faced arrest related to the breach (Musil).
Equifax FTC Settlement
In July of 2019, in a settlement with the FTC, the Consumer Financial Protection Bureau, 48 states, the District of Columbia, and Puerto Rico, Equifax agreed to pay up to $700 million in fines and compensation for the 147 million affected individuals. $300 million of the settlement was distributed to individuals whose personal information had been exposed during the breach. Equifax was also required to pay up to $125 million in consumer compensation for additional out-of-pocket losses if needed. Equifax paid $175 million to states and $100 million to the CFPB in civil penalties (FTC).
The FTC alleged that Equifax violated “the FTC Act’s prohibition against unfair and deceptive practices and the Gramm-Leach-Bliley Act’s Safeguards Rule, which requires financial institutions to develop, implement, and maintain a comprehensive information security program to protect the security, confidentiality, and integrity of customer information” (FTC).To address deficiencies in Equifax’s cybersecurity, the FTC also required Equifax instate a comprehensive information security program which would include “annual assessments of internal and external security risks and assure that service providers with access to personal information stored by Equifax also implement appropriate security programs” (FTC).
Several forms of compensation were offered as part of the $300 million paid out to affected consumers (JND):
Free Credit Monitoring Services
Consumers who filed a claim within the first claims period (prior to the January 22nd, 2020 deadline) were eligible for 4 years of credit monitoring services provided by Equifax, Experian, and Transunion with up to $1,000,000 in identity theft insurance. After this 4-year period, consumers who successfully filed a claim could enroll in 6 more years of credit monitoring services provided by Equifax.
Cash Payout
Within the first claims period, consumers who had already purchased credit or identity monitoring services for at least six months prior to the breach were eligible to claim a maximum of $125 in compensation in lieu of free credit monitoring services.
Identity Theft Compensation
Consumers were eligible to receive compensation (up to 20 total hours at $25 an hour) for time spent recovering from identity theft and fraud occurring within the first claims period. Consumers could also claim up to $20,000 in out-of-pocket losses occurring within this period.
Extended Claims Period Identity Theft Compensation
While the first claims period has passed, consumers are now eligible to receive compensation for out-of-pocket losses and time spent recovering from identity theft and fraud occurring within the extended claims period of January 23, 2020 and January 22, 2024.
Identity Restoration Services
All affected consumers are eligible for Experian’s Assisted Identity Restoration Services if they experience identity theft within seven years of the breach. These services include, “access to a U.S. based call center providing services relating to identity restoration, assignment of a certified Identity Theft Restoration Specialist to assist you in addressing an identity theft event, and assistance with a step-by-step process to deal with companies, government agencies, and credit bureaus” (Equifax).
Equifax Subscription Product Reimbursement
Consumers who had an Equifax credit monitoring or identity theft protection subscription between 9/7/2016 and 9/7/2017 were eligible for reimbursement of 25% of the amount paid if they filed a claim within the first claims period.
The terms of the payout garnered criticism by both consumers and lawmakers. Equifax’s settlement with the FTC promised only $31 million in compensation for consumers who had credit monitoring services at the time of the breach, with a maximum payout of $125 per customer. As Senator Elizabeth Warren pointed out, this would only cover the $125 compensation of 248,000 individuals. Because Equifax had millions of qualified customers, the realistic payout would be far lower (Higgins). This turned out to be the case. By the December 2020 deadline, over 4.5 million consumers filed a claim, resulting in an estimated payout of only $7 each (Siegel Bernard). Consumers and lawmakers also accused the FTC of misleading consumers about the size of the cash payout because some materials seemed to suggest that every affected consumer would receive $125 (Higgins). In response, the FTC recommended that consumers elect the free credit monitoring services option instead of the cash payout (FTC).
Equifax was also accused of complicating the claiming process to reduce the number of individuals able to successfully file claims. Affected consumers received an email from the Equifax settlement team that required them to verify they had credit monitoring services in place by October 15th, 2019. Without verification, consumers’ claims would be denied. According to some consumers, the email looked illegitimate, leading many to question its authenticity. The FTC clarified the email was legitimate on their site (Warzel).
Independent Settlements with States
Massachusetts and Indiana secured $18.2 million and $19.5 million in settlements with Equifax respectively (Kovacs).
Legislation
The FTC settlement resulted in calls for legislation that would increase penalties for CRAs which lost consumer information. In 2018, Senators Elizabeth Warren and Mark Warner introduced the Data Breach Prevention and Compensation Act, which specifically responded to the Equifax breach. The Act would, “give the Federal Trade Commission more direct supervisory authority over data security at CRAs, impose mandatory penalties on CRAs to incentivize adequate protection of consumer data, and provide robust compensation to consumers for stolen data” (Warren). This would include the establishment of an Office of Cybersecurity at the FTC responsible for conducting inspections of CRA’s cybersecurity. The Act would also impose, “mandatory, strict liability penalties for breaches of consumer data beginning with a base penalty of $100 for each consumer who had one piece of personal identifying information (PII) compromised and another $50 for each additional PII compromised per consumer” (Warren). Under this Act, Equifax would have paid at least $1.5 billion to consumers.
In March of 2018, the Senate passed the Economic Growth, Regulatory Relief, and Consumer Protection Act, which allows consumers free credit freezes and the ability to place one year fraud alerts on their accounts (FTC). However, lawmakers have not made progress in passing a comprehensive reform bill responding to the Equifax breach. The Data Breach Prevention and Compensation Act was reintroduced in 2019, but since then has not further advanced in becoming law.
Ethics Analysis
Several unique aspects of Credit Reporting Agencies’ function impact their position in the economic life of American society and on their ethical responsibilities.
- CRAs have become gatekeepers for essential functions, like finding work, housing, and managing one’s money. Consumers need credit to navigate the current economic system. While we might be able to choose not to shop at Amazon, for example, electing not to establish a credit history amounts to opting out of regular economic activity. Consumers therefore lack agency in their relationship with CRAs.
- Information held by CRAs, including PII, is especially sensitive. Other businesses wouldn’t have access to this type of data. Loss of PII can result in identity theft with devastating effects, including financial instability, and lack of access to housing and employment, for consumers. Further, this loss of PII means credit information supplied to lenders is no longer reliable or valuable.
- Loss of information through data breaches not only threatens the validity of the credit reporting industry’s function but also threatens the United States’ national security and economic infrastructure. The current banking and taxation system utilizes social security numbers as PII. According to security investigators, the Equifax data breach was most likely the work of the Chinese government as part of a scheme to collect pools of consumers’ data. It’s not a stretch to imagine that a hostile international actor could use consumer data to significantly disrupt these systems.
In sum, the position CRAs hold in the US economy, the sensitivity of the information they have access to, and the serious consequences of loss of this data, heighten Equifax’s responsibility to the American public. These factors must be considered in examining the ethics of their behavior.
1. Promises and Trust: Failure to Protect Consumer Data
A company has an ethical duty to honor promises made to customers. This kind of promissory obligation is based on commitments to providing certain services and following a code of ethics and conduct. According to business ethicists like Manuel Velasquez, these promises can be understood as a kind of contractual relationship between a customer and a corporation (Velasquez). We require higher standards of performance from individuals and companies making these promises because clients put their trust in those individuals or companies based on these “contracts.”
Equifax’s failure to protect consumer data falls broadly into the category of negligence. Equifax IT and Security failed to adhere to cybersecurity policies specifically designed to prevent data breaches. Several contextual factors contribute to the ethical assessment of negligence:
- The potential consequences of negligence
For example, negligence in a trivial matter such as sorting recycling, would be weighed as far less morally repugnant than forms of negligence that could end another person’s life. Equifax’s failure to follow cybersecurity policies jeopardized the PII of millions of Americans with potentially catastrophic personal consequences as well as posing a continued threat to national security.
- Whether negligence was part of a pattern of behavior
During a senate testimony Former Equifax CEO Richard Smith blamed the breach on the actions of one security employee, who he reported was meant to apply the patch, but didn’t (Siegel Bernard & Cowley). However, the root of Equifax’s cybersecurity problem actually lies in management’s failure to create a robust patch management policy and culture of proactive and thorough cybersecurity. In a company managing thousands of employees, a reliable corporate policy should have back-up protocols to prevent the human error of one individual causing the collapse of the system. In 2015, years before the breach, Equifax’s management was made aware of systemic flaws in their patch management policy which left thousands of critical vulnerabilities unpatched (PSI). The Equifax breach was therefore the consequence of a formally acknowledged pattern of behavior.
- Whether negligence was ‘knowingly’ committed
An individual who acts carelessly, knowing she is taking a risk and understanding the possible consequences is judged more seriously than someone who acts carelessly due to forgetfulness or ignorance. Equifax management and employees were notified of the Apache Struts vulnerability by US-CERT, and NIST assigned the vulnerability the highest severity score possible, a 10. Equifax’s GTVM team circulated the notification to over 400 company employees following the alert (PSI). Equifax management knew of the risk Apache Struts posed as well as the ongoing risks associated with lax cybersecurity practices.
- Whether a company has made a promise to take certain precautions as part of a professional code
A higher standard of caution is generally required from professions or businesses that promise to abide by a code to protect their clients from harm . A physician who is careless with his patients’ health, by not checking their history of allergies before administering medications is subject to moral censure as well as the loss of license to practice. The fact this physician has sworn an oath to protect patients’ health makes carelessness even more damning. Equifax promises consumers it will protect PII and provide accurate and fair credit reports (Equifax). Thus, Equifax breached consumers trust in two ways. Firstly, Equifax clearly broke its promise to protect consumer data by failing to follow cybersecurity policy. Secondly, Equifax’s negligence created the conditions for widespread identity theft which could undermine the validity of credit information and jeopardize its promise to provide accurate and fair credit reports.
Thus, the severity of Equifax’s negligence makes this breach of trust especially difficult to accept and demonstrates Equifax’s culpability in the loss of consumer information.
2. Transparency: Failure to Report the Data Breach in a Timely Manner
Consider the maxim or statement, “Companies will lie to consumers to make more money.” Using Kantian moral reasoning, we can universalize this statement by imagining a world in which people always deceive each other for personal benefit. If we apply this maxim in this imagined world it creates a contradiction: In a world where people couldn’t make promises, how would a company deceive consumers? If companies lied consistently, trust between consumers and companies would be completely degraded. This maxim becomes irrational when made into a universal law of nature and is therefore unethical (Johnson & Cureton).
Thus, companies like Equifax have a duty of transparency. Even if customers are not directly lied to, withholding information that impacts the company’s ability to deliver on promises and may cause customers serious harm is also dishonest and unethical. Applied to CRAs, this creates a duty of timely disclosure of data breaches.
Equifax waited six weeks after its discovery of the breach to alert customers that their PII had been compromised. In most data breach cases, companies might take time to investigate the cause, identify affected consumers, and prepare a plan of remediation, but Equifax executives never explained the reasoning for their timeline (Tsukayama). During this six week period, it can be assumed management strategized on minimizing fallout and public scrutiny, choosing to prioritize the company’s reputation over the continued risk to millions of customers.
Equifax executives also sold $2 million in Equifax stock shortly after the breach was discovered. Individuals with influence in Equifax’s administration used their private knowledge of the breach for personal gain, while affected consumers had no opportunity to protect themselves from the potentially devastating effects of the loss of their personal information. Thus, executives valued the bottom line and their personal financial status over their duty to transparency.
3. Justice and Fairness: Lack of Compensatory Justice
Finally, companies have an ethical duty to follow principles of justice in compensating consumers for inflicted harm. Aristotle’s theory of corrective justice, concerned with the relationship between wrongdoer and victim, demands that “fault be cancelled by restoring the victim to the position she would have been in had the wrongful behavior not occurred” (Miller). The ultimate goal of corrective justice is to adequately reduce or reverse inflicted harm.
Equifax inflicted harm on consumers by failing to protect their PII and jeopardizing their financial security. Even if consumers didn’t experience identity theft immediately after the breach or within the extended claims period, in a digital age, loss of personal information is permanent. Consumers’ PII could still be exploited in future with little recourse.
The value of the FTC mandated cash payout did not match the severity of these injuries. The value of protecting personal information is far greater than $7 or even $125 dollars. This is demonstrated by Equifax’s own credit monitoring rates, which cost around $20 a month (Equifax). If greater numbers of consumers filed cash payout claims, the payout value would have been reduced to mere cents. Equifax’s settlement fund was not large enough to ethically compensate consumers for harm done, and thus corrective justice was not achieved. It is nearly impossible to value the price of personal information, but clearly, Equifax valued the company’s financial welfare over consumer compensation. Equifax suffered significant reputational damage as a result of the breach but has since recovered materially with few long-term consequences to their business. In 2018 and 2019, Equifax reported revenues of $3.41 and $3.5 billion respectively (Equifax).
While the free credit monitoring services offered were clearly a better deal than the cash payout, once the 10-year service period is complete, consumers will once again have to purchase credit monitoring services to regularly view their credit. The extended claims period in which consumers may be compensated for identity theft and fraud associated with the breach only lasts for an additional four years. Even though consumers’ PII are permanently lost, settlement terms do not compensate consumers in a long-term manner.
Finally, distribution of consumer compensation was poorly managed. The goal of compensatory justice is to reduce harm done to as many individuals as possible, but the FTC’s unclear representation of settlement terms and Equifax’s confusing communications with consumers made it more difficult for them to claim deserved compensation.
Policy Recommendations
The Equifax data breach should spur US regulatory agencies and the legal system to take seriously the responsibility to protect consumers from negligence and other wrongdoing by companies. The ethical failures in this case suggest the US regulatory system is inadequate as it pertains to the credit reporting industry. To prevent future breaches of this kind and properly compensate consumers for loss of PII, Congress should pass legislation that will:
- Increase regulation of CRAs cybersecurity practices
CRAs privacy practices should be regulated by an external body in the same way as other financial institutions. As senators Warren and Warner suggested, creating a division of the FTC specifically responsible for monitoring CRAs cybersecurity practices might prevent the kind of negligence in the Equifax breach by ensuring consumer data are adequately protected at all times.
- Improve breach notification laws
CRAs should be legally required to notify the public of data breaches within a few days of their discovery to reduce harm to consumers resulting from loss of PII.
- Increase consumer compensation for loss of PII
CRAs should provide consumers with increased monetary compensation based on the quantity of PII lost. As senators Warren and Warner have argued, if consumers’ personal information is properly valued, CRAs will be incentivized to protect consumer data to avoid financial losses. Further, if a breach does occur, consumers will be justly compensated for harm done.
Dollarhide, Maya. “What Is a Credit Reporting Agency?” Investopedia , Investopedia, 9 Mar. 2021, www.investopedia.com/terms/c/credit-reporting-agency.asp .
“The Top 3 Credit Bureaus.” Investopedia , Investopedia, 13 Jan. 2021, www.investopedia.com/personal-finance/top-three-credit-bureaus/ .
“Form 10-K.” Equifax , Equifax , 25 Feb. 2021, otp.tools.investis.com/clients/us/equifax/SEC/sec-show.aspx?Type=html&FilingId=14746446&CIK=0000033185& Index =10000.
LaMagna, Maria. “After Breach, Equifax CEO Leaves with $18 Million Pension, and Possibly More.” MarketWatch , MarketWatch, 27 Sept. 2017, www.marketwatch.com/story/equifax-ceo-leaves-with-18-million-pension-and-maybe-more-2017-09-26.
Portman , Rob, and Tom Carper. “How Equifax Neglected Cybersecurity and Suffered a Devastating Data Breach .” Permanent Subcommittee on Investigations United States Senate , 6 Mar. 2019.
“David C. Webb to Join Equifax as Chief Information Officer.” Equifax , Equifax , 11 Jan. 2010, investor.equifax.com/news-and-events/press-releases/2010/01-11-2010.
“Privacy Choices for Your Personal Financial Information.” Consumer Information , FTC, 13 Mar. 2018, www.consumer.ftc.gov/articles/0222-privacy-choices-your-personal-financial-information .
Khalfani-Cox, Lynnette. “Can You Avoid Equifax and the Credit Bureaus Altogether?” USA Today , Gannett Satellite Information Network, 29 Sept. 2017, www.usatoday.com/story/money/business/2017/09/27/can-you-avoid-equifax-and-credit-bureaus-altogether/706328001/ .
Resources.display. “Understanding the Fair Credit Reporting Act.” Experian , Experian, 17 Apr. 2020, www.experian.com/blogs/ask-experian/credit-education/report-basics/fair-credit-reporting-act-fcra/ .
Hayes, Adam. “Dodd-Frank Definition.” Investopedia , Investopedia, 4 Mar. 2021, www.investopedia.com/terms/d/dodd-frank-financial-regulatory-reform-bill.asp .
Riley , Michael, et al. Bloomberg.com , Bloomberg, www.bloomberg.com/news/features/2017-09-29/the-equifax-hack-has-all-the-hallmarks-of-state-sponsored-pros .
Posey, Brien. “What Is Patch Management and Why Is It Important?” SearchEnterpriseDesktop , TechTarget, 21 Jan. 2020, searchenterprisedesktop.techtarget.com/definition/patch-management .
Brewster, Thomas. “A Brief History Of Equifax Security Fails.” Forbes , Forbes Magazine, 11 Sept. 2017, www.forbes.com/sites/thomasbrewster/2017/09/08/equifax-data-breach-history/?sh=53b8d08b677c .
Fruhlinger, Josh. “Equifax Data Breach FAQ: What Happened, Who Was Affected, What Was the Impact?” CSO Online , CSO, 12 Feb. 2020, www.csoonline.com/article/3444488/equifax-data-breach-faq-what-happened-who-was-affected-what-was-the-impact.html .
“EPIC – Equifax Data Breach.” Electronic Privacy Information Center , EPIC , epic.org/privacy/data-breach/equifax/ .
“Home Security & Governmental Affairs.” About The Permanent Subcommittee on Investigations | Homeland Security & Governmental Affairs Committee , U.S. Senate Committee on Homeland Security & Governmental Affairs, www.hsgac.senate.gov/subcommittees/investigations/about .
Kovacs , Eduard. “Massachusetts, Indiana Settle With Equifax Over 2017 Data Breach.” SecurityWeek , SecurityWeek, www.securityweek.com/massachusetts-indiana-settle-equifax-over-2017-data-breach .
Horowitz , Julia, and Danielle Wiener-Bronner. “Equifax’s Chief Information Officer and Chief Security Officer Are Out.” CNN Money , Cable News Network, money.cnn.com/2017/09/15/news/equifax-top-executives-retiring/index.html?iid=EL .
Musil, Steven. “Former Equifax Exec Gets 4 Months in Prison for Insider Trading after Breach.” CNET , CNET, 30 June 2019, www.cnet.com/news/former-equifax-exec-gets-4-months-in-prison-for-insider-trading-after-breach/ .
“Equifax to Pay $575 Million as Part of Settlement with FTC, CFPB, and States Related to 2017 Data Breach.” Federal Trade Commission , Federal Trade Commission , 31 July 2019, www.ftc.gov/news-events/press-releases/2019/07/equifax-pay-575-million-part-settlement-ftc-cfpb-states-related .
“Equifax Data Breach Settlement: Am I Affected?” Home | Equifax Data Breach Settlement , JND
Higgins, Tucker. “Elizabeth Warren Calls for Investigation into FTC for ‘Misleading’ Equifax Data Breach Victims over Compensation.” CNBC , CNBC, 14 Aug. 2019, www.cnbc.com/2019/08/14/elizabeth-warren-calls-for-inquiry-into-ftc-over-equifax-settlement.html .
Siegel Bernard, Tara. “Equifax Breach Affected 147 Million, but Most Sit Out Settlement.” The New York Times , The New York Times, 23 Jan. 2020, www.nytimes.com/2020/01/22/business/equifax-breach-settlement.html .
“FTC Encourages Consumers to Opt for Free Credit Monitoring, as Part of Equifax Settlement.” Federal Trade Commission , FTC, 31 July 2019, www.ftc.gov/news-events/press-releases/2019/07/ftc-encourages-consumers-opt-free-credit-monitoring-part-equifax .
Warzel, Charlie. “Equifax Doesn’t Want You to Get Your $125. Here’s What You Can Do.” The New York Times , The New York Times, 16 Sept. 2019, www.nytimes.com/2019/09/16/opinion/equifax-settlement.html.
Newman, Lily Hay. “All the Ways Equifax Epically Bungled Its Breach Response.” Wired , Conde Nast, 24 Sept. 2017, www.wired.com/story/equifax-breach-response/ .
“Warren, Warner Unveil Legislation to Hold Credit Reporting Agencies Like Equifax Accountable for Data Breaches: U.S. Senator Elizabeth Warren of Massachusetts.” Warren, Warner Unveil Legislation to Hold Credit Reporting Agencies Like Equifax Accountable for Data Breaches | U.S. Senator Elizabeth Warren of Massachusetts , United States Senate , 10 Jan. 2018, www.warren.senate.gov/newsroom/press-releases/warren-warner-unveil-legislation-to-hold-credit-reporting-agencies-like-equifax-accountable-for-data-breaches .
“Starting Today, New Federal Law Allows Consumers to Place Free Credit Freezes And Yearlong Fraud Alerts.” Federal Trade Commission , FTC, 21 Sept. 2018, www.ftc.gov/news-events/press-releases/2018/09/starting-today-new-law-allows-consumers-place-free-credit-freezes .
Velasquez, Manuel G. Business Ethics: Concepts and Cases . Prentice-Hall, 2002.
Siegel Bernard, Tara, and Stacy Cowley. “Equifax Breach Caused by Lone Employee’s Error, Former C.E.O. Says.” The New York Times , The New York Times, 3 Oct. 2017, www.nytimes.com/2017/10/03/business/equifax-congress-data-breach.html .
“Equifax Code of Ethics and Business Conduct .” Equifax , July 2017.
Johnson, Robert, and Adam Cureton. “Kant’s Moral Philosophy.” Stanford Encyclopedia of Philosophy , Stanford University, 7 July 2016, plato.stanford.edu/entries/kant-moral/#ForUniLawNat .
Tsukayama, Hayley. “Analysis | Why It Can Take so Long for Companies to Reveal Their Data Breaches.” The Washington Post , WP Company, 8 Apr. 2019, www.washingtonpost.com/news/the-switch/wp/2017/09/08/why-it-can-take-so-long-for-companies-to-reveal-their-data-breaches/ .
Miller, David. “Justice.” Stanford Encyclopedia of Philosophy , Stanford University, 26 June 2017, plato.stanford.edu/entries/justice/#CorrVersDistJust .
“Discover Which of Our Comprehensive 3-Bureau Credit Monitoring and Identity Theft Protection Plans Is Right for You.” Equifax , Equifax , www.equifax.com/personal/products/credit/monitoring-product-comparison/ .
“Equifax Releases Fourth Quarter 2018 Results.” Equifax , Equifax , investor.equifax.com/news-and-events/press-releases/2019/02-20-2019-215733514 .
“Equifax Releases Fourth Quarter 2019 Results.” Equifax , Equifax , investor.equifax.com/news-and-events/press-releases/2020/02-12-2020-221344372 .
Image courtesy of RiverTree Advisors
- Insider Trading
- Responsibility
- Trust/trustworthiness
- Name First Last
- Your Message
- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World

Equifax data breach FAQ: What happened, who was affected, what was the impact?
In 2017, attackers exfiltrated hundreds of millions of customer records from the credit reporting agency. here's a timeline of the security lapses that allowed the breach to happen and the company's response..

In March 2017, personally identifying data of hundreds of millions of people was stolen from Equifax, one of the credit reporting agencies that assess the financial health of nearly everyone in the United States.
As we’ll see, the breach spawned a number of scandals and controversies: Equifax was criticized for everything ranging from their lax security posture to their bumbling response to the breach, and top executives were accused of corruption in the aftermath. And the question of who was behind the breach has serious implications for the global political landscape.
How did the Equifax breach happen?
Like plane crashes, major infosec disasters are typically the result of multiple failures. The Equifax breach investigation highlighted a number of security lapses that allowed attackers to enter supposedly secure systems and exfiltrate terabytes of data.
Most of the discussion in this section and the subsequent one comes from two documents: A detailed report from the U.S. General Accounting Office , and an in-depth analysis from Bloomberg Businessweek based on sources inside the investigation. A top-level picture of how the Equifax data breach happened looks like this:
- The company was initially hacked via a consumer complaint web portal, with the attackers using a widely known vulnerability that should have been patched but, due to failures in Equifax’s internal processes, wasn’t.
- The attackers were able to move from the web portal to other servers because the systems weren’t adequately segmented from one another, and they were able to find usernames and passwords stored in plain text that then allowed them to access still further systems.
- The attackers pulled data out of the network in encrypted form undetected for months because Equifax had crucially failed to renew an encryption certificate on one of their internal security tools.
- Equifax did not publicize the breach until more than a month after they discovered it had happened; stock sales by top executives around this time gave rise to accusations of insider trading.
To understand how exactly all these crises intersected, let’s take a look at how the events unfolded.
When did the Equifax breach happen?
The crisis began in March of 2017. In that month, a vulnerability, dubbed CVE-2017-5638 , was discovered in Apache Struts, an open source development framework for creating enterprise Java applications that Equifax, along with thousands of other websites, uses. If attackers sent HTTP requests with malicious code tucked into the content-type header, Struts could be tricked into executing that code, and potentially opening up the system Struts was running on to further intrusion. On March 7, the Apache Software Foundation released a patch for the vulnerabilities; on March 9, Equifax administrators were told to apply the patch to any affected systems, but the employee who should have done so didn’t. Equifax’s IT department ran a series of scans that were supposed to identify unpatched systems on March 15; there were in fact multiple vulnerable systems, including the aforementioned web portal, but the scans seemed to have not worked, and none of the vulnerable systems were flagged or patched.
While it isn’t clear why the patching process broke down at this point, it’s worth noting what was happening at Equifax that same month, according to Bloomberg Businessweek: Unnerved by a series of incidents in which criminals had used Social Security numbers stolen from elsewhere to log into Equifax sites, the credit agency had hired the security consulting firm Mandiant to assess their systems. Mandiant warned Equifax about multiple unpatched and misconfigured systems, and the relationship devolved into in acrimony within a few weeks.
Forensics analyzed after the fact revealed that the initial Equifax data breach date was March 10, 2017: that was when the web portal was first breached via the Struts vulnerability. However, the attackers don’t seem to have done much of anything immediately. It wasn’t until May 13, 2017 — in what Equifax referred to in the GAO report as a “separate incident” — that attackers began moving from the compromised server into other parts of the network and exfiltrating data in earnest. (We’ll revisit this time gap later, as it’s important to the question of who the attackers were.)
From May through July of 2017, the attackers were able to gain access to multiple Equifax databases containing information on hundreds of millions of people; as noted, a number of poor data governance practices made their romp through Equifax’s systems possible. But how were they able to remove all that data without being noticed? We’ve now arrived at another egregious Equifax screwup. Like many cyberthieves, Equifax’s attackers encrypted the data they were moving in order to make it harder for admins to spot; like many large enterprises, Equifax had tools that decrypted, analyzed, and then re-encrypted internal network traffic, specifically to sniff out data exfiltration events like this. But in order to re-encrypt that traffic, these tools need a public-key certificate , which is purchased from third parties and must be annually renewed. Equifax had failed to renew one of their certificates nearly 10 months previously — which meant that encrypted traffic wasn’t being inspected .
The expired certificate wasn’t discovered and renewed until July 29, 2019, at which point Equifax administrators almost immediately began noticing all that previously obfuscated suspicious activity; this was when Equifax first knew about the breach.
It took another full month of internal investigation before Equifax publicized the breach, on September 8, 2017. Many top Equifax executives sold company stock in early August, raising suspicions that they had gotten ahead of the inevitable decline in stock price that would ensue when all the information came out. They were cleared, though one lower-level exec was charged with insider trading .
What data was compromised and how many people were affected?
Equifax specifically traffics in personal data, and so the information that was compromised and spirited away by the attackers was quite in-depth and covered a huge number of people. It potentially affected 143 million people — more than 40 percent of the population of the United States — whose names, addresses, dates of birth, Social Security numbers, and drivers’ licenses numbers were exposed. A small subset of the records — on the order of about 200,000 — also included credit card numbers ; this group probably consisted of people who had paid Equifax directly in order to order to see their own credit report.
This last factor is somewhat ironic, as the people concerned enough about their credit score to pay Equifax to look at it also had the most personal data stolen, which could lead to fraud that would then damage their credit score. But a funny thing happened as the nation braced itself for the wave of identity theft and fraud that seemed inevitable after this breach: it never happened. And that has everything to do with the identity of the attackers.
Who was responsible for the Equifax data breach?
As soon as the Equifax breach was announced, infosec experts began keeping tabs on dark web sites, waiting for huge dumps of data that might be connected to it. They waited, and waited, but the data never appeared. This gave rise to what’s become a widely accepted theory: that Equifax was breached by Chinese state-sponsored hackers whose purpose was espionage, not theft.
The Bloomberg Businessweek analysis follows these lines and points to a number of additional clues beyond the fact that the stolen data never seems to have leaked. For instance, recall that the initial breach on March 10 was followed by more than two months of inactivity before attackers began abruptly moving onto high-value targets within Equifax’s network. Investigators believe that the first incursion was achieved by relatively inexperienced hackers who were using a readily available hacking kit that had been updated to take advantage of the Struts vulnerability, which was only a few days old at that point and easy to exploit. They may have found the unpatched Equifax server using a scanning tool and not realized how potentially valuable the company they had breached was. Eventually, unable to get much further beyond their initial success, they sold their foothold to more skilled attackers, who used a variety of techniques associated with Chinese state-backed hackers to get access to the confidential data.
And why would the Chinese government be interested in Equifax’s data records? Investigators tie the attack into two other big breaches that similarly didn’t result in a dump of personally identifying data on the dark web: the 2015 hack of the U.S. Office of Personnel Management , and the 2018 hack of Marriott’s Starwood hotel brands . All are assumed to be part of an operation to build a huge “data lake” on millions of Americans, with the intention of using big data techniques to learn about U.S. government officials and intelligence operatives. In particular, evidence of American officials or spies who are in financial trouble could help Chinese intelligence identify potential targets of bribery or blackmail attempts.
In February of 2020, the United States Department of Justice formally charged four members of the Chinese military with the attack . This was an extremely rare move — the U.S. rarely files criminal charges against foreign intelligence officers in order to avoid retaliation against American operatives — that underscored how seriously the U.S. government took the attack.
How did Equifax handle the breach?
At any rate, once the breach was publicized, Equifax’s immediate response did not win many plaudits. Among their stumbles was setting up a separate dedicated domain, equifaxsecurity2017.com, to host the site with information and resources for those potentially affected. These sorts of lookalike domains are often used by phishing scams, so asking customers to trust this one was a monumental failure in infosec procedure. Worse, on multiple occasions official Equifax social media accounts erroneously directed people to securityequifax2017.com instead; fortunately, the person who had snapped up that URL used it for good, directing the 200,000 (!) visitors it received to the correct site .
Meanwhile, the real equifaxsecurity2017.com breach site was judged insecure by numerous observers, and may have just been telling everyone that they were affected by the breach whether they really were or not . Language on the site (later retracted by Equifax) implied that just by checking to see if you were affected meant that you were giving up your right to sue over it . And in the end, if you were affected, you were directed to enroll in an Equifax ID protection service — for free, but how much do you trust the company at this point?
What happened to Equifax after the data breach?
What, ultimately, was the Equifax breach’s impact? Well, the upper ranks of Equifax’s C-suite rapidly turned over . Legislation sponsored by Elizabeth Warren and others that would’ve imposed fines on credit-reporting agencies that get hacked went nowhere in the Senate.
That doesn’t mean the Equifax breach cost the company nothing, though. Two years after the breach, the company said it had spent $1.4 billion on cleanup costs , including “incremental costs to transform our technology infrastructure and improve application, network, [and] data security.” In June 2019, Moody’s downgraded the company’s financial rating in part because of the massive amounts it would need to spend on infosec in the years to come. In July 2019 the company reached a record-breaking settlement with the FTC, which wrapped up an ongoing class action lawsuit and will require Equifax to spend at least $1.38 billion to resolve consumer claims.
Was I affected by the Equifax breach?
This was a lot of anguish just to find out if you were one of the unlucky 40 percent of Americans whose data was stolen in the hack. Things have settled down in the subsequent years, and now there’s a new site where you can check to see if you’re affected, with yet another somewhat confusing name: eligibility.equifaxbreachsettlement.com/en/Eligibility .
That settlement eligibility website actually isn’t hosted by Equifax at all; instead, it’s from the FTC.
How does the Equifax settlement work?
The Equifax settlement dangles the prospect that you might get a check for your troubles, but there are some catches. The settlement mandates that Equifax compensate anyone affected by the breach with credit monitoring services; Equifax wants you to sign up for their own service, of course, and while they will also give you a $125 check to go buy those services from somewhere else, you have to show that you do have alternate coverage to get the money (though you could sign up for a free service).
More cash is available if you’ve actually lost money from identity theft or spent significant amounts of time dealing with the fallout, but here, too, documentation is required. And that $125 is just a maximum; it almost certainly will go down if too many people request checks .
What are the lessons learned from the Equifax breach?
If we wanted to make a case study of the Equifax breach, what lessons would we pull from it? These seem to be the big ones:
- Get the basics right. No network is invulnerable. But Equifax was breached because it failed to patch a basic vulnerability, despite having procedures in place to make sure such patches were applied promptly. And huge amounts of data was exfiltrated unnoticed because someone neglected to renew a security certificate. Equifax had spent millions on security gear , but it was poorly implemented and managed.
- Silos are defensible. Once the attackers were inside the perimeter, they were able to move from machine to machine and database to database . If they had been restricted to a single machine, the damage would’ve been much less.
- Data governance is key — especially if data is your business. Equifax’s databases could’ve been stingier in giving up their contents . For instance, users should only be given access to database content on a “need to know basis”; giving general access to any “trusted” users means that an attacker can seize control of those user accounts and run wild. And systems need to keep an eye out for weird behavior; the attackers executed up to 9,000 database queries very rapidly, which should’ve been a red flag.
Related content
Reduce security risk with 3 edge-securing steps, teamviewer targeted by apt29 hackers, containment measures in place, top 12 cloud security certifications, the cso guide to top security conferences, from our editors straight to your inbox.

Josh Fruhlinger is a writer and editor who lives in Los Angeles.
More from this author
What is swatting criminal harassment falsely involving armed police, ccsp certification: exam, cost, requirements, training, salary, certified ethical hacker (ceh): certification cost, training, and value, whitelisting explained: how it works and where it fits in a security program, download our password managers enterprise buyer’s guide, cism certification: requirements, training, exam, and cost, two-factor authentication (2fa) explained: how it works and how to enable it, what is spear phishing examples, tactics, and techniques, most popular authors.

Show me more
Cyberattackers are using more new malware, attacking critical infrastructure.

Download our endpoint detection and response (EDR) buyer’s guide

Infinidat Revolutionizes Enterprise Cyber Storage Protection to Reduce Ransomware and Malware Threat Windows

CSO Executive Sessions India with Hilal Lone, CISO, Razorpay

CSO Executive Sessions: The new realities of the CISO role - whistleblowing and legal liabilities

CSO Executive Sessions India with Pradipta Kumar Patro, Global CISO and Head IT Platform, KEC International

CSO Executive Session India with Hilal Lone, CISO, Razorpay

Sponsored Links
- Tomorrow’s cybersecurity success starts with next-level innovation today. Join the discussion now to sharpen your focus on risk and resilience.
- Visibility, monitoring, analytics. See Cisco SD-WAN in a live demo.
Cyber Case Study: Marriott Data Breach
by Kelli Young | Oct 11, 2021 | Case Study , Cyber Liability Insurance

In the final months of 2018, Marriott International—a hospitality company that oversees one of the biggest hotel chains in the world—discovered that cybercriminals had compromised its guest reservation system. This Marriott data breach exposed the personal information of hundreds of millions of customers from various countries who had made bookings with the company’s Starwood properties over the past several years. As a result of the incident, Marriott faced significant recovery expenses, legal ramifications and reputational damages.
This breach—which ultimately stemmed from existing security vulnerabilities that carried over during Marriott’s 2016 acquisition of Starwood—has since become known as one of the largest cyber incidents the world has ever seen, showcasing the importance of prioritizing cybersecurity during merger and acquisition (M&A) events. In hindsight, there are various cybersecurity lessons that organizations can learn by reviewing the details of this incident, its impact and the mistakes Marriott made along the way. Here’s what your organization needs to know.
The Details of the Marriott Data Breach
In 2014—two years before Marriott even acquired Starwood—the latter company’s guest reservation system was infiltrated by cybercriminals via remote access trojan (RAT). Put simply, a RAT is a harmful computer program that grants the perpetrator unauthorized administrative control of their victim’s technology. A multitude of digital vulnerabilities at Starwood’s properties could have contributed to the success of the cyber-criminals’ RAT. Namely, these properties were using outdated versions of Windows Server across their computer systems and had left their remote desk protocol (RDP) ports open to the internet. Despite this intrusion within the guest reservation system, Starwood was unable to detect the cybercriminals’ activity—allowing them to remain unnoticed.
Moving forward to September 2016, Marriott officially acquired Starwood. During the acquisition process, Marriott failed to complete a detailed cybersecurity audit of Starwood’s networks and technology. As such, Marriott was also unable to identify the cybercriminals’ activity within Starwood’s guest reservation system—permitting them to stay undetected throughout the acquisition. Additionally, Marriott didn’t discover that Starwood had been further targeted by separate attackers in an unrelated incident during 2015, leaving its workplace devices infected with malware.
Rather than adopt uniform networks and technology following the acquisition, Marriott allowed Starwood properties to move forward with their current operations—thus utilizing a compromised guest reservation system and malware-ridden devices. Marriott also began migrating information from several databases housed within Starwood’s guest reservation system. This information included a variety of customers’ personal details—such as names, addresses, phone numbers, email addresses, passport numbers and credit card numbers.
While the information in these databases was encrypted, the cybercriminals were eventually able to locate their associated decryption keys and subsequently unlock the information. From there, the cybercriminals began exfiltrating the information. After transporting this information, the cybercriminals then re-encrypted it in an effort to remain undetected within the system.
In September 2018—a full two years after the acquisition—Marriott finally identified the breach due to a system security alert. Upon this discovery, Marriott reported the incident to law enforcement officials and consulted forensic specialists to launch an investigation. On Nov. 30, 2018, Marriott revealed the details of the breach to the public in an official statement. At this time, Marriott confirmed that the personal information of nearly 500 million customers around the world—including the United States, Canada and the United Kingdom—had been compromised.
The Impact of the Marriott Data Breach
In addition to exposed data, Marriott faced several consequences following the large-scale breach. This includes the following:
Recovery costs Marriott incurred nearly $30 million in overall recovery expenses as a result of the breach. This total includes costs related to investigating the cause of the breach, notifying impacted customers of the breach, providing these customers with year-long access to security monitoring software, developing an international call center related to the breach and implementing updated cybersecurity measures to prevent future incidents.
Reputational damages Apart from recovery costs, Marriott also received widespread criticism for its cybersecurity shortcomings after the incident. In particular, the media and IT experts scrutinized Marriott’s failures to perform its due diligence on Starwood’s existing security vulnerabilities prior to the M&A process and detect the cybercriminals’ activity after the acquisition was finalized—essentially allowing the cybercriminals to access and exfiltrate customers’ personal information for nearly four years. Consequently, Marriott’s stocks dropped by 5% almost immediately after it announced the details of the breach. What’s more, the company is estimated to have suffered over $1 billion in lost revenue due to diminished customer loyalty following the incident.
Legal ramifications Lastly, Marriott encountered costly legal ramifications from various avenues because of the breach. Since the incident affected individuals from the United Kingdom, the Information Commissioner’s Office fined Marriott over $120 million for violating British customers’ privacy rights under the General Data Protection Regulation. In North America, Marriott was met with multiple class-action lawsuits after announcing the breach—one of which requested $12.5 billion in damages, or $25 for every impacted customer.
Lessons Learned
There are several cybersecurity takeaways from the Marriott data breach. Specifically, the incident emphasized these important lessons:
RDP ports require proper safeguards. Exposed RDP ports were another potential culprit of this costly incident. Although RDP ports are useful workplace tools that permit employees to connect remotely to other servers or devices, leaving these ports open can allow cybercriminals to leverage them as a vector for deploying malicious software or other harmful programs (including RATs). That being said, RDP ports should never be unnecessarily left open to the internet. Virtual private networks (VPNs) and multi-factor authentication protocols can also be utilized to help keep RDP ports from being exploited by cybercriminals.
Cybersecurity must be considered during M&A events. Marriott neglecting to prioritize cybersecurity amid its acquisition of Starwood proved detrimental in this breach. Primarily, Marriott should have diligently assessed Starwood’s IT vulnerabilities throughout the M&A process. Further, Marriott should have ensured an effective cybersecurity infrastructure between the combined companies once the acquisition took place. Especially as cyber incidents continue to surge in both cost and frequency, cybersecurity should be top of mind during any M&A activity. In particular, each company involved in the M&A process should be carefully evaluated for potential cybersecurity gaps. A proper plan for rectifying or—at the very least—mitigating these exposures should be developed prior to the finalization of the M&A event. In many cases, it can also be advantageous for merged companies to adopt shared digital processes and security policies in order to maintain uniform defense strategies against cybercriminals.
Effective security and threat detection software is critical. A wide range of security and threat detection software likely could have helped both Starwood and Marriott identify and mitigate this breach in a much faster manner—thus reducing the resulting damages. Although this software may seem like an expensive investment, it’s well worth it to minimize the impacts of potentially devastating cyber incidents. Necessary software to consider includes network monitoring systems, antivirus programs, endpoint detection products and patch management tools. Also, it’s valuable to conduct routine penetration testing to determine whether this software possesses any security gaps or ongoing vulnerabilities. If such testing reveals any problems, these issues should be addressed immediately.
Proper coverage can provide much-needed protection. Finally, this breach made it clear that no organization—not even an international hospitality company—is immune to cyber-related losses. That’s why it’s crucial to ensure adequate protection against potential cyber incidents by securing proper coverage. Make sure your organization works with a trusted insurance advisor when navigating these coverage decisions.
We are here to help.
If you’d like additional information and resources, we’re here to help you analyze your needs and make the right coverage decisions to protect your operations from unnecessary risk. You can download a free copy of our eBook , or if you’re ready make Cyber Liability Insurance a part of your insurance portfolio, Request a Proposal or download and get started on our Cyber & Data Breach Insurance Application and we’ll get to work for you.
What is a data breach and what do we have to do in case of a data breach?
A data breach occurs when the data for which your company/organisation is responsible suffers a security incident resulting in a breach of confidentiality, availability or integrity. If that occurs, and it is likely that the breach poses a risk to an individual’s rights and freedoms, your company/organisation has to notify the supervisory authority without undue delay, and at the latest within 72 hours after having become aware of the breach . If your company/organisation is a data processor it must notify every data breach to the data controller.
If the data breach poses a high risk to those individuals affected then they should all also be informed, unless there are effective technical and organisational protection measures that have been put in place, or other measures that ensure that the risk is no longer likely to materialise.
As an organisation it is vital to implement appropriate technical and organisational measures to avoid possible data breaches.
Organisation must notify the DPA and individuals The data of a textile company’s employees has been disclosed. The data included the personal addresses, family composition, monthly salary and medical claims of each employee. In that case, the textile company must inform the supervisory authority of the breach. Since the personal data includes sensitive data, such as health data, the company has to notify the employees as well.
A hospital employee decides to copy patients’ details onto a CD and publishes them online. The hospital finds out a few days later. As soon as the hospital finds out, it has 72 hours to inform the supervisory authority and, since the personal details contain sensitive information such as whether a patient has cancer, is pregnant, etc., it has to inform the patients as well. In that case, there would be doubts about whether the hospital has implemented appropriate technical and organisational protection measures. If it had indeed implemented appropriate protection measures (for example encrypting the data), a material risk would be unlikely and it could be exempt from notifying the patients.
Company must notify clients and they may then have to notify the DPA and individuals A cloud service loses several hard drives containing personal data belonging to several of its clients. It has to notify those clients as soon as it becomes aware of the breach. Its clients must notify the DPA and the individuals depending on the data that was processed by the data processor.
- EDPB Guidelines on Personal data breach notification under Regulation 2016/679
- Article 4(12) and Articles 33 and 34 and Recitals (85) to (88) of the GDPR
Share this page
The ICO exists to empower you through information.
Personal data breach examples
Share this page.
- Share via Reddit
- Share via LinkedIn
- Share via email
To help you assess the severity of a breach we have selected examples taken from various breaches reported to the ICO. These also include helpful advice about next steps to take or things to think about.
Case study 1: Failure to redact personal data
Reporting decision: notifying the ico and data subjects.
What happened?
A data controller sent paperwork to a child’s birth parents without redacting the adoptive parents’ names and address. After discovering the breach, the data controller did not inform the adoptive parents.
Why was this a problem?
The breach presented a high risk to the adoptive parents’ safety. The birth parents visited the adoptive parents’ address and had to be removed by the police, and the adoptive parents and their children had to relocate.
What should have happened?
The controller should have notified the adoptive parents as soon as the breach was discovered. This would have allowed the adoptive parents to take steps to minimise the risk, for example by moving into alternative accommodation or putting additional safeguarding measures in place.
The incident also needed to be reported to the ICO, as there was likely to be a risk to individuals.
The controller should also investigate why the incident occurred and take steps to prevent a similar incident occurring in the future.
Case study 2: Emailing a file in error
Reporting decision: documenting the breach on internal breach log only.
A debt insolvency agent emailed a vulnerable new client’s file in error to a colleague in a different department. The colleague who received the file immediately deleted the email and informed the sender of the error.
The file contained a list of the client’s outstanding debts, their contact details, basic financial history, information about their mental health and reasons for seeking support with their financial situation. The client was vulnerable due to their mental state.
What did the data controller do?
The sender and recipient work for the same organisation in similar roles, but in different departments. Both work to the same data security measures and have completed training on working with vulnerable people.
The recipient correctly deleted the email and informed the sender. As a result, it is very unlikely that there would be any risk of harm or detriment to the data subject, despite special category personal data being involved. Therefore, there is no legal obligation to report the breach to the ICO or inform the affected data subject.
The organisation documented the breach internally and provided guidance to staff about checking contact details when sending emails, to minimise the risk to their data subjects. If the email had been sent to a member of the public, the risk to the data subject would have been higher.
Case study 3: Working on an unencrypted laptop
Reporting decision: initially not reportable, but then reportable to both the ico and data subjects.
An employee lost his briefcase, containing work on an unencrypted laptop and unredacted paper files relating to a sensitive court case – including information on criminal convictions and health information.
Initially, the employee told his manager that he believed the laptop was encrypted and the paper files were redacted. The manager reported the incident to the IT department, who remotely wiped the laptop.
At that point, the data controller did not report the breach to the ICO as they believed there was little or no risk to data subjects, though they did record the incident on their breach log.
After being informed by the IT department that the laptop was unencrypted, and after the employee discovered the paper files had not been redacted, the controller reported the breach to the ICO and informed the data subjects.
The paper files were unredacted and not secured, so somebody could have accessed sensitive data. As the laptop was unencrypted, there was no way for the controller to know whether the data had been accessed. Therefore, they could not be certain that a risk to the data subjects would not occur.
They updated the internal breach log to reflect the new information and documented the developing situation, including the way the breach changed from being not reportable to reportable. On discovering the possibility of a risk to data subjects, the controller correctly reported the breach to the ICO and informed the data subjects.
The controller was then able to use their internal breach log to explain the delay in reporting the breach to the ICO, outside the required 72 hours.
Case study 4: Sending medication to the wrong patient
A courier, delivering medication for a Scottish pharmacy, delivered one set of medication to the wrong patient (Patient A).
Patient A called the pharmacy to complain. The pharmacist then realised the prescription was for a different patient with a similar name (Patient B). After contacting the courier, the unopened medication was collected and delivered to Patient B.
Patient A and Patient B both complained to the pharmacist. Patient B felt their medical information and address had been shared inappropriately with Patient A.
The pharmacist decided that any risk to Patient B was unlikely, due to the actions of Patient A, the pharmacy and the courier. However, they decided to report the breach to the ICO in case Patient B subsequently complained to the ICO about how their personal data had been handled.
Did the data controller need to report the breach?
As the pharmacy had concluded it was unlikely there was a risk to Patient B, the breach did not need to be reported to the ICO.
There would be no further action for the pharmacy to take, assuming they had documented the details of the breach, their decision not to report and any safeguards put in place to prevent a recurrence. The threshold for informing data subjects is higher than for informing the ICO. Therefore, the pharmacy didn’t need to tell data subjects about the breach either. Informing individuals about minor breaches that are unlikely to cause risk or harm can cause unnecessary worry to data subjects and can also result in data subjects becoming fatigued if informed of numerous breaches.
The pharmacist should have had confidence in their decision making and taken responsibility for it. If, having received a complaint from the data subject, the ICO wanted to know why the pharmacy had not reported the breach, they would be able to refer to the rationale recorded on the internal breach log.
Note that if the pharmacy had been in England, it would have reported the incident via the Data Security and Protection Incident Reporting tool, regardless of the threshold for reporting to the ICO.
Case study 5: A phishing attack
A law firm employee failed to recognise a phishing attack. They received an email, clicked a link to download a document, then inadvertently entered login credentials into what they believed was a legitimate website.
A while later, the employee contacted the company’s IT department as they noticed they were no longer receiving emails.
The data controller discovered the employee’s email account had been compromised when they entered their login details. A forwarding rule had also been set up, diverting the employee’s emails to a third party.
Additionally, the third party had responded to several emails using a spoofed email account, advising the recipients of a change in bank details. This resulted in two clients making significant payments to the third party.
The controller also discovered that the compromised email account contained scanned copies of client ID documents.
The controller reported the breach to the ICO and notified affected clients about the breach.
The controller identified a high risk to affected clients’ rights and freedoms, partly due to the financial detriment that two clients experienced after making payments to the third party. It is also likely that other clients will have received emails asking for payments.
Also, the controller identified that there was a high risk of identity theft or fraud, due to scanned copies of ID documents being held on the compromised account.

- HIPAA Resources
- Website Accessibility
Resource Library
Case study comparison: hipaa data breaches and phi on stolen laptops.
According to HHS data, more than a third of all data breaches reported through 2017 involved a laptop, desktop, or mobile device. 1 Compare Cases One and Two, and consider how better security practices protected the covered entity in Case Two.
HIPAA Breach Analysis Flowchart
The following flowchart outlines how a privacy or security incident is analyzed to determine whether a HIPAA breach has occurred. It forms the basis of the analyses in the cases presented here.
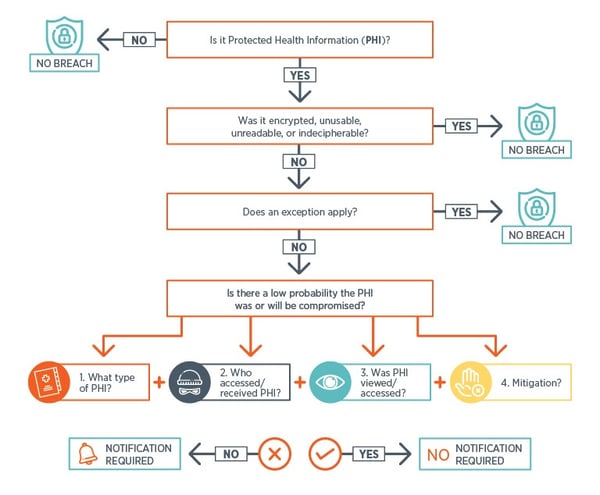
At a busy family practice office, a medical assistant was tasked with reviewing 100 random patient records for quality purposes. Because she was about to miss her deadline for the project, she downloaded the records onto her laptop so she could work on the project over the weekend. She put her laptop in her car trunk and met friends for dinner on the way home. While she was having dinner, her laptop was stolen. The data on the laptop were not encrypted and there was no password protection.
HIPAA Breach Analysis
Q. Was PHI involved?
A. Yes. Full medical records were being stored on the laptop.
Q. Was the information on the compromised device encrypted, unusable, unreadable, or indecipherable?
Q. Does one of the three HIPAA disclosure exceptions apply?
A. No. Theft of a computer/storage device is not considered an exception.
Q. Is there a low probability that PHI has been compromised? (Risk Assessment)
- Type of PHI : The information was very sensitive and included numerous patient identifiers. There was a high possibility the PHI could be used by an unauthorized recipient in a manner adverse to the patients, or could be used to further the unauthorized recipient’s own interests.
- Who took it/received it : Unknown
- Ease of access : Whether the medical information was viewed was unknown, but because there was no password protection on the computer, the chance that the PHI could be viewed was high.
- Mitigation : There was no way to assure the PHI would not be used.
A. The attorney who reviewed this case found that based on the risk assessment the clinic could not demonstrate a low probability that the PHI was compromised; therefore, a breach occurred. The practice was required to comply with the HIPAA breach notification requirements.
At a community clinic, a nurse practitioner (NP) carried a laptop computer with her, using it to enter patient information into the electronic health record (EHR) as she examined patients. Between patients, she left her laptop at the nurses’ station while she went to get a cup of coffee in the break room. When she returned, the laptop was gone. The laptop required a password to log in. Although the NP accessed patient records from the laptop, no PHI was stored on the device’s hard drive. In order to access the patient records, she had to sign on to the EHR system with a unique username and password. She immediately reported to the office administrator that the laptop had been stolen. The administrator immediately disabled the NP’s user account. Although the laptop was never recovered, the administrator monitored the EHR system to determine whether anyone had attempted to sign on with the NP’s credentials, and no one had.
A. Yes. PHI could be accessed from the device, but there was no PHI stored on the device.
A. No. Theft of a computer/storage device is not an exception.
- Type of PHI: The information was very sensitive and included numerous patient identifiers. There was a high possibility the PHI could be used by an unauthorized recipient in a manner adverse to the patients or could be used to further the unauthorized recipient’s own interests.
- Who took it/received it: Unknown
- Ease of access: Because the computer was password protected, did not store any PHI, and required additional password sign-in to access the EHR, the chance that PHI could be accessed was low.
- Mitigation: The office administrator moved quickly to disable the NP’s user account, which would most likely prohibit the thief from being able to access the community clinic patient records.
A. In this case, the attorney who reviewed the case found that based on the risk assessment the clinic could determine there was a low probability the PHI had been compromised. Therefore, it was determined that notification was not required under the HIPAA breach notification rules.
Stolen Smartphones Present a HIPAA Compliance Risk
According to the 2018 Verizon Data Breach Investigations Report (DBIR) , physical theft and loss of devices accounts for more than 10% of all data breaches in healthcare. Chances are, a certain number of clinicians and staff who use their smartphones to send and receive PHI will have their phones stolen.
For general information on securing smartphones, the Federal Communications Commission offers their FCC Smartphone Security Checker with tips for various brands of phones. Clinicians and staff who are contemplating using their cellphones to transmit PHI should also consult with IT professionals to determine whether the devices can be appropriately secured for HIPAA compliance.
Medical Liability Risk Management Recomendations — Laptop Theft Protection
The Federal Trade Commission suggests that individuals think of their computers as cash on the table or an open wallet sitting on the back seat of a car. 2 Consider the following strategies to safeguard laptops: 2,3
- If a laptop must be left unattended, lock it to something heavy with a laptop security cable.
- Make computers personally identifiable with permanent markings or engravings.
- Install a computer alarm that activates when the computer is moved out of a particular range.
- Install a program that tracks the location of a stolen computer.
- When going through airport security, keep your laptop and phone with you until the last minute, then visually track them and retrieve them immediately.
- When staying in a hotel, lock your laptop in the safe, lock it to something heavy or take it with you.
- Do not leave your laptop in a car.
- Do not use a laptop bag; consider using a bag that hides the fact that there is a laptop in it.
- Encrypt your computer’s hard drive.
- Keep your laptop password protected and do not store passwords with, in or on it.
- If you have to put your laptop on the floor, place it between your legs so you remember it.
- Institute “clean desk” policies for employees, requiring secure physical locations for devices both during and outside of standard work hours.
More Information About Preventing HIPAA Data Breaches
- Overview: Preventing HIPAA Data Breaches: Case Studies and Best Practices
- Best Practices: Mobile Device Policies for Preventing HIPAA Data Breaches
- Best Practices: Best Practices for Preventing HIPAA Data Breaches by Criminal Hackers
- Closed Claim Case Study: Misdelivered Email Results in a HIPAA Data Breach
- Closed Claim Case Study: Employee Voyeurism Leads to a HIPAA Data Breach
- Closed Claim Case Study: Unsecured PHI on a Lost Flash Drive Results in a HIPAA Data Breach
Additional Resources for Policyholders
Guidance and additional information on the HIPAA Security Rule and on medical records security, access and release are available to all NORCAL policyholders by contacting a NORCAL Risk Management Specialist at 855.882.3412.
Information and Network Security Coverage
Call NORCAL Customer Service at 844.4NORCAL or visit our Information and Network Security coverage page for more information about this coverage available at no additional cost as part of the Health Care Professional (HCP) policy.

1. U.S. Department of Health and Human Services Office for Civil Rights (OCR). “ Breach Portal: Notice to the Secretary of HHS Breach of Unsecured Protected Health Information .” (accessed 5/14/2018)
2. Federal Trade Commission. “ Laptop Security .” (accessed 5/14/2018)
3. Oglesby P. “ Laptop Anti-Theft: Travel Identity Theft Computer Theft Prevention .” Updated on September 19, 2016. (accessed 5/14/2018)
Additional Linked Sources
Health Info & the Law Project. “ States .” (accessed 5/14/2018)
Verizon Enterprise. “ 2018 Data Breach Investigations Report .” (accessed 5/14/2018)
Federal Communications Commission (FCC). “ FCC Smartphone Security Checker .” (accessed 5/14/2018)
Filed under: Digital Health , Privacy & HIPAA , Cybersecurity , Case Study , Practice Manager , Information Security
Topics
specialties , recently added.
Interested in NORCAL Group?
Contact Your Agent/Broker or call 844.4NORCAL today

© 2001 - 2023 ProAssurance All rights reserved
- 844-466-7225
- Privacy Policy
- Terms of Use
Ticketmaster sends notifications about recent massive data breach
Lawrence abrams.
- June 28, 2024

Ticketmaster has started to notify customers who were impacted by a data breach after hackers stole the company's Snowflake database, containing the data of millions of people.
"Ticketmaster recently discovered that an unauthorized third party obtained information from a cloud database hosted by a third-party data services provider," reads a data breach notification shared with the Office of the Maine Attorney General.
"Based on our investigation, we determined that the unauthorized activity occurred between April 2, 2024, and May 18, 2024. On May 23, 2024, we determined that some of your personal information may have been affected by the incident. We have not seen any additional unauthorized activity in the cloud database since we began our investigation."
Ticketmaster says that the breach exposed customers' names, basic contact information, and "<extra>" information, which is different depending on the user.
The company recommends customers "remain vigilant" against identity theft and fraud and has offered one year of free identity monitoring to track their credit history.
While Ticketmaster lazily said the breach only impacted more than 1000 people (">1000"), it actually impacted millions of customers worldwide and exposed what many would consider much more sensitive information.
Ticketmaster's Snowflake data theft attack
Last month, a threat actor known as ShinyHunters began selling stolen data from Live Nation/Ticketmaster, claiming it contained the personal information and credit card information of 560 million users.
The threat actors used compromised Ticketmaster credentials that did not have multi-factor authentication enabled to steal the data from their Snowflake account.
Snowflake is a cloud-based data warehousing company used by the enterprise to store databases, process data, and perform analytics.
ShinyHunters began selling the data on May 28 on a well-known hacking forum for $500,000. The threat actor claimed that the data was 1.3TB and contained information for 560 million customers, ticket sales, event information, customer fraud, and partial credit card information.
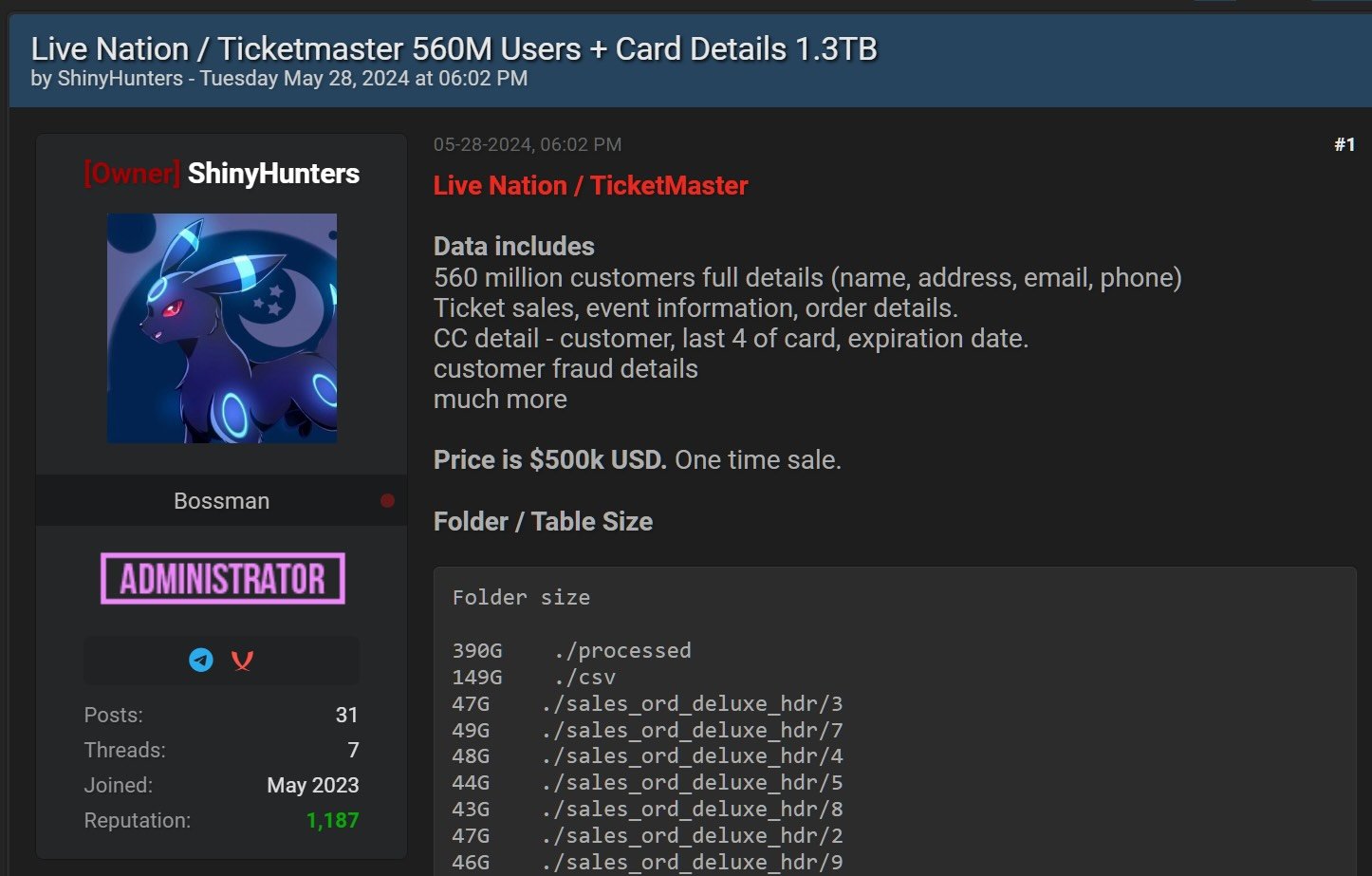
Samples of the data seen by BleepingComputer contained more than just "basic contact information," including full names, email addresses, phone numbers, addresses, hashed credit card details, and payment amounts.
After remaining silent for days, Ticketmaster eventually confirmed the breach on May 31, in a Friday evening SEC filing, stating that they did not believe the breach would have a material impact on their company.
Ticketmaster's breach is one of many recent data theft attacks linked to the Snowflake database platform.
A joint investigation by SnowFlake, Mandiant, and CrowdStrike revealed that a threat actor, tracked as UNC5537, used compromised customer credentials to target at least 165 organizations that had not configured multi-factor authentication protection on their accounts.
To breach Snowflake accounts, the threat actor used credentials stolen by information-stealing malware infections dating back to 2020.
Recent breaches linked to these attacks include Neiman Marcus , Santander , Ticketmaster , QuoteWizard/LendingTree , Advance Auto Parts , Los Angeles Unified , and Pure Storage .
Related Articles:
Ticketmaster confirms massive breach after stolen data for sale online
Advance Auto Parts confirms data breach exposed employee information
Neiman Marcus confirms data breach after Snowflake account hack
Cylance confirms data breach linked to 'third-party' platform
Pure Storage confirms data breach after Snowflake account hack
- Data Breach
- Live Nation
- ShinyHunters
- Ticketmaster
- Previous Article
- Next Article

itjohan - 2 hours ago
if I had $500000, what could I do with such a big list?
Post a Comment Community Rules
You need to login in order to post a comment.
Not a member yet? Register Now
You may also like:

Dev rejects CVE severity, makes his GitHub repo read-only

Meet Brain Cipher — The new ransomware behind Indonesia's data center attack
Help us understand the problem. What is going on with this comment?
- Abusive or Harmful
- Inappropriate content
- Strong language
Read our posting guidelinese to learn what content is prohibited.
We've detected unusual activity from your computer network
To continue, please click the box below to let us know you're not a robot.
Why did this happen?
Please make sure your browser supports JavaScript and cookies and that you are not blocking them from loading. For more information you can review our Terms of Service and Cookie Policy .
For inquiries related to this message please contact our support team and provide the reference ID below.
Cyber claims case study: Reputational repercussions
Online retailer grapples with data breach aftermath
Cyber Case study 10 min 10 Sep, 2018
- Copy page URL

Businesses are increasingly dependent on their computer systems to perform critical elements of their operations, so it comes as no surprise that financial losses due to system outages are becoming both more frequent and severe. This has made business interruption cover an increasingly important part of any cyber policy. However, brokers and their clients shouldn’t focus solely on system outages when it comes to business interruption.
Often referred to as reputational harm, business interruption as a result of a data breach is starting to impact many organisations and can be equally as disruptive as a system outage. In such cases, even though an insured may not have suffered any meaningful system downtime, they can suffer serious reputational harm in the eyes of their customers and suppliers, resulting in a subsequent drop-off in income. For instance, in 2013, the US retail giant Target was the victim of a data breach that resulted in 40 million customer credit card details being stolen.
After news of this spread, Target saw its sales fall by some 46% year-on-year in the fourth quarter of 2013. But it’s not just well-publicised data breaches like Target’s that can result in reputational harm and financial loss. Even small companies that experience a data breach outside the public domain can be impacted by reduced customer loyalty when they inform affected customers. One of our policyholders to suffer such a loss was a small online retailer in the US, selling medical treatments and accessories.
Notification becomes necessary
In February 2017, our policyholder suffered a number of attacks on their website. The company first became aware of the issue when they received an email from the hackers that claimed that they had obtained thousands of customers’ credit card details and demanded that a ransom be paid in order to prevent the data from being released into the public domain. It was at this point that the policyholder reported the situation to CFC’s in-house cyber incident response team.
Our team engaged one of our IT forensic partners who quickly rectified the problem by addressing and removing the vulnerabilities and malicious code that had allowed the hackers to gain access to the insured’s systems. However, in the process of carrying out their investigations into the policyholder’s computer systems, the forensic consultants discovered that a database containing the credit card details of over 90,000 customers had been accessed by the hackers and exfiltrated from the system.

The forensic consultants discovered that a database containing the credit card details of over 90,000 customers had been accessed
CFC engaged our specialist privacy legal team who determined that the insured was required to notify all of the affected individuals, as each of the impacted customers lived in states with relevant breach notification laws in place. The organisation also opted to provide identity theft restoration services to these clients.
By this point, the costs of IT forensics and the provision of legal advice and breach notification services came in at just over £230,000. Under many cyber policies, with these issues taken care of, the insurer would typically consider the matter resolved and close the claim file accordingly.
An expensive side effect
But this wasn’t the end of the matter for the insured.
In the months following the notification, the business began to notice a drop-off in existing customers re-ordering products they had previously purchased, which was leading to a reduction in revenue and a resultant loss of profits. In order to establish the size of the loss and the extent to which it could be attributed to the notification of the data breach, CFC worked with one of our forensic accounting partners to assess the case.
As a first step, the insured put together a loss calculation based on the number of actual re-orders against their budget. It was initially established that from January 2016 to the end of March 2017 (prior to the notification), the business had on average been achieving a re-order rate of 96.4%. However, in April 2017 (after the notification) the figure dipped to 85.8% and by June it had dropped to as low as 79.7%. Thereafter the re-order rate picked up again but never returned to the established average of 96.4% during the 12-month indemnity period. After comparing the number of re-orders expected at a re-order rate of 96.4% to the actual number of re-orders over 12 months, it was determined that some 5,220 orders had been lost.
In order to corroborate the insured’s estimate, the forensic accountants used an alternative approach, looking at the loss on a customer-by-customer basis. Initially, it was calculated that the insured had acquired 116,738 new customers prior to the notification but only 51,029 customers had continued to place re-orders after the notification letters were sent out, leaving some 65,709 potentially lost customers.

In order to deduce which customers were lost due to the data breach notification, the forensic accountants conducted an analysis of customer buying habits. They established that repeat customers tended to re-order every three months. If a customer did not engage in this repeat order cycle, the accountants deduced that they had been lost as part of regular customer churn. Once these customers were removed from the calculation, they were able to identify that 1,299 repeat customers appeared to have been lost in the aftermath of the data breach. As these customers were expected to re-order roughly every three months, this meant that over a 12-month period, 5,196 orders had been lost due to the data breach. Given the confluence between the insured’s figure of 5,220 lost orders and the accountancy’s figure of 5,196, the higher figure was decided upon as the overall loss figure.
With the insured losing 5,220 orders at a rate of profit per order of £91.12, this meant that over the course of a year, the business interruption costs associated with reputational harm came to some £475,646. Fortunately for the insured, however, the cyber policy that they had with CFC covered the costs of reputational harm following a cyber event over a 12-month indemnity period.
Reputational harm cover is key
Incidents like this highlight a few key issues. First, it illustrates the importance of having business interruption coverage in place that extends to cover reputational harm. Many cyber policies will only cover business interruption as a result of system outage. In this instance, the insured had no meaningful system outage, yet ended up with a sizeable business interruption loss due to a reduction in customer loyalty caused by a data breach.
Secondly, it demonstrates the value of having longer indemnity periods. Traditional business interruption policies connected to property damage will typically offer 12-month indemnity periods as an absolute minimum, with 18, 24 and even 36 month periods being fairly common. However, many cyber policies only offer 3-month indemnity periods as standard. In this case, had the policyholder only had a 3-month indemnity period, they would only have been eligible to claim for three months’ worth of lost profits at a cost of £188,072, leaving the insured with a shortfall of £287,574 over the course of the year.
When purchasing a cyber policy, brokers and their clients should consider not only system outages but the whole range of business interruption exposures that they may face as a result of a cyber incident.
You might also like
Last year, we responded to over 1,000 cyber claims comprised of theft of funds, data breaches, ransomware & extortion, malware and more.
Cyber Article 2 min Apr 05, 2019

Additional extra expense, known as "additional increased cost of working" in some territories, is one of the valuable new features we've added to o...
Cyber Article 5 min Jan 25, 2019

This digital agency found itself facing a significant payout to a client over the late delivery of an ecommerce platform. Fortunately, the agency’s...
Technology Case study 3 min Jun 21, 2024
Get in touch
Trade with us, let's get you signed up, you've successfully signed up.
Which newsletter would you like to receive?
We won’t share your data with anyone else or bombard you with emails, we simply want to keep you in the loop of upcoming events and news. View Privacy Policy
Upload your files here (max 5MB each)
Watch CBS News
CDK Global calls cyberattack that crippled its software platform a "ransom event"
By Megan Cerullo
Edited By Anne Marie Lee
Updated on: June 25, 2024 / 9:06 AM EDT / CBS News
CDK Global is now calling the cyberattack that took down its software platform for its auto dealership clients "a ransom event."
In a note to clients Saturday, CDK for the first time acknowledged that the hackers that made its dealer management system, or DMS, unavailable to clients for days , are demanding a ransom to restore its systems.
"Thank you for your patience as we recover from the cyber ransom event that occurred on June 19th," CDK said in a memo to clients on Saturday, according to a copy of the email obtained by CBS MoneyWatch .
CDK added in the note that it has started restoring its systems and expects the process of bringing major applications back online "to take several days and not weeks."
Beware of phishing
In its memo, the company also warned car dealerships to be alert to phishing scams, or entities posing as CDK but who are in fact bad actors trying to obtain proprietary information like customers' passwords.
A CDK spokesperson told CBS MoneyWatch that it is providing customers "with alternate ways to conduct business" while its systems remain inoperative.
The cybercriminals behind the CDK attack are linked to a group called BlackSuit, Bloomberg reported on Monday, citing Allan Liska of computer security firm Recorded Future. In a June 21 story , the media outlet also said the hackers were demanding tens of millions of dollars and that CDK planned to pay the ransom.
Liska didn't immediately respond to a request for comment. CDK itself hasn't pointed to any group behind the attack on its system that has disrupted car dealerships across the U.S. since last week. Companies targeted in ransomware schemes are often reluctant to disclose information in the midst of negotiations with hackers on a payment.
"When you see an attack of this kind, it almost always ends up being a ransomware attack," Cliff Steinhauer, director of information security and engagement at the National Cybersecurity Alliance, told the Associated Press. "We see it time and time again unfortunately, [particularly in] the last couple of years. No industry and no organization or software company is immune."
"Doing everything manually"
The hack has left some car dealers unable to do business altogether, while others report using pen and paper, and even "sticky notes" to record transactions.
Tom Maoli, owner of Celebrity Motor Car Company, which operates five luxury car dealerships across New York and New Jersey, on Monday told CBS MoneyWatch his employees "are doing everything manually."
"We are trying to keep our customers happy and the biggest issue is the banking side of things, which is completely backed up. We can't fund deals," he said.
Asbury Automotive Group, a Fortune 500 company operating more than 150 new car dealerships across the U.S., in a statement on Monday said the attack has "adversely impacted" its operations and has hindered its ability to do business. Its Koons Automotive dealerships in Maryland and Virginia, however, which don't rely on CDK's software, have been able to operate without interruption, the company said.
Ransomware attacks are on the rise. In 2023, more than 2,200 entities, including U.S. hospitals, schools and governments were directly impacted by ransomware, according to Emisoft , an anti-malware software company. Additionally, thousands of private sector companies were targeted. Some experts believe that the only way to stop such attacks is to ban the payment of ransoms, which Emisoft said would lead bad actors to "quickly pivot and move from high impact encryption-based attacks to other less disruptive forms of cybercrime."
Earlier this year, the U.S. Department of State offered $10 million in exchange for the identities of leaders of the Hive ransomware gang, which since 2021 has been responsible for attacks on more than 1,500 institutions in over 80 countries, resulting in the theft of more than $100 million.
- Cybersecurity and Infrastructure Security Agency
- Cyberattack
Megan Cerullo is a New York-based reporter for CBS MoneyWatch covering small business, workplace, health care, consumer spending and personal finance topics. She regularly appears on CBS News 24/7 to discuss her reporting.
More from CBS News

Boeing, Airbus announce plans to buy parts of subcontractor Spirit AeroSystems

Nelly Korda withdraws from London tournament after being bitten by a dog

Should you refinance your home equity loan this summer? Here's when it may make sense

Suspected female suicide bombers kill at least 18 in Nigeria, officials say

IMAGES
COMMENTS
A brief look at incident response vs. data breach response. For the most part, downtime is more tolerable and less troubling than a data breach. A few minutes of an unscheduled outage is usually more palatable than even a hint of a data breach. Teams will even purposefully take their service offline to prevent a breach from spreading in some cases.
Using Uber's 2016 breach as a case study, company executives must be aware of and recognize the business and personal consequences associated with breach response, and specifically with intentionally concealing a breach. ... Disclosure and direct individual notification of a data breach is now the expectation, and the decision to not disclose ...
1. This case study containing a detailed analysis to identify and understand the technical modus operandi of the attack, as well as what conditions allowed a breach and the related regulations; 2. Technical assessment of the main regulations related to the case study; 3.
In addition to federal HIPAA regulations, covered entities may also have to comply with state data breach laws. State laws vary on what triggers a breach notification obligation and the nature of breach notification obligations. The linked case studies focus on federal data breach notification laws.
Data breach prevention and response: Lessons from the CafePress case. By. Lesley Fair. March 15, 2022. Many small businesses go to online retailing platform CafePress when they want to buy or sell customized items. However, according to a proposed FTC settlement, the company's lax security practices allowed data thieves to take the idea of ...
Case Study: Epiq Uniquely ... Notably, the sheer size of the notifications required for the breach presented unique logistical considerations. Epiq rose to the challenge by implementing an extensive notification campaign that was distributed to millions of email addresses and physical addresses, making it one of the largest datasets it has ...
Executive Summary. In this case study, we examine the 2013 breach of American retailer Target, which led to the theft of personally identifiable information (PII) and credit card information belonging to over 70 million customers from Target's databases. This case study will first consider Target's vulnerabilities to an external attack in ...
The Equifax data breach in 2017 stands as a stark reminder of the critical importance of robust cybersecurity measures in an era of escalating digital threats. In this case Beyond Headlines: Case Study- The Equifax Data Breach and Lessons Learned guide, we analyze the intricate details of the breach, examining the vulnerabilities that led to the compromise of the sensitive personal information ...
The global average cost of a data breach in 2023 was USD 4.45 million, a 15% increase over 3 years. 51%. 51% of organizations are planning to increase security investments as a result of a breach, including incident response (IR) planning and testing, employee training, and threat detection and response tools. USD 1.76 million.
The Challenge. A large hospital network experienced a protected health information (PHI) breach, with over 6,600 compromised PDFs — some containing up to 180,000 rows of information and over 150,000 individuals — and densely packed with PHI. Patients' information was frequently duplicated with different PHI each time.
Data Breach Response. Steps that an organization should take in responding to a breach of personal information, including verification, containment, investigation and analysis, notification, and ...
"The Time is Now for Congress to Act of a National Data Breach Notification Law" | The Hill "Equifax Breach Prompts Scrutiny, but New Rules May Not Follow" | The New York Times "The single most depressing thing about the Equifax breach" | The Washington Post It took over six weeks for credit bureau Equifax - one of the three major credit reporting firms in the U.S. - to ...
As companies grow, their potential attack surfaces expand accordingly. This is evident in data breach statistics. One data breach tracker estimates that 68 records are stolen every second, thanks of a broad cast of bad actors: In the wake of a security incident, a decent incident response will generally take some form of the following course:
Case Study Data Breach Response. Swift, Complete, and Cost-Effective Data Breach Response for Global Law Firm Client After Cyber Attack ... optimised processes for consolidating relevant information about each individual across all sources into a single notification list entry that preserved information on the sources of any duplicative ...
Given Medibank's "size, resources, the nature and volume of the personal information it held … and the risk of harm for an individual in the case of a breach", it failed to take proper steps to ...
The case study of the Equifax data breach exemplifies flaws inherent in management of Credit Reporting Agencies (CRAs). CRAs aggregate and sell historical credit information of individuals and companies. Credit card companies, banks, employers, and landlords sell consumers' borrowing and repayment history to CRAs.
143 million: Number of consumers whose data was potentially affected by the breach. $125: The most you can expect to get in compensation if your data was exfiltrated from Equifax's systems. $1.4 ...
In September 2018—a full two years after the acquisition—Marriott finally identified the breach due to a system security alert. Upon this discovery, Marriott reported the incident to law enforcement officials and consulted forensic specialists to launch an investigation. On Nov. 30, 2018, Marriott revealed the details of the breach to the ...
Change, not providers, responsible for breach notifications: HHS Why Change Healthcare's restoration process has taken so long Change Healthcare breach could cost UnitedHealth $1.6B this year
Data breaches represent a permanent threat to all types of organizations. Although the types of breaches are different, the impacts are always the same. This paper focuses on analyzing over 9000 data breaches made public since 2005 that led to the loss of 11,5 billion individual records which have a significant financial and technical impact.
Abstract As the number of data breaches in the United States grows each year, cybersecurity has become an increasingly important policy area. The primary mechanism for regulating and deterring data...
A data breach occurs when the data for which your company/organisation is responsible suffers a security incident resulting in a breach of confidentiality, availability or integrity. If that occurs, and it is likely that the breach poses a risk to an individual's rights and freedoms, your company/organisation has to notify the supervisory ...
Case study 1: Failure to redact personal data Reporting decision: Notifying the ICO and data subjects. ... After discovering the breach, the data controller did not inform the adoptive parents. Why was this a problem? The breach presented a high risk to the adoptive parents' safety. The birth parents visited the adoptive parents' address ...
These case studies focus on federal data breach notification laws. The Health Information & the Law website has an interactive map that provides links to state health data security and breach notification laws. Case One. At a busy family practice office, a medical assistant was tasked with reviewing 100 random patient records for quality ...
A data breach is the unauthorized or unintentional exposure, disclo-sure, or loss of sensitive personal information. These incidents deprive people of their right to confi-dentiality, privacy and integrity of their personal information. Most data breaches are currently a result of external actors such as hackers.
The UnitedHealth Group unit tells healthcare providers that medical diagnoses, insurance information, payment details and passport numbers could have been exposed in February breach.
Ticketmaster has started to notify customers who were impacted by a data breach after hackers stole the company's Snowflake database, containing the data of millions of people. "Ticketmaster ...
Roughly 15,000 car dealerships across the US and Canada have gone days without software systems crucial to running their business, following multiple cyberattacks on CDK Global. The company is one ...
An online retailer grapples with data breach aftermath in this cyber insurance claims case study. ... In order to deduce which customers were lost due to the data breach notification, the forensic accountants conducted an analysis of customer buying habits. They established that repeat customers tended to re-order every three months.
CDK Global is now calling the cyberattack that took down its software platform for its auto dealership clients "a ransom event." In a note to clients Saturday, CDK for the first time acknowledged ...