Risk management methodology in the supply chain: a case study applied
- S.I. : Risk Management Decisions and Value under Uncertainty
- Open access
- Published: 10 August 2021
- Volume 313 , pages 1051–1075, ( 2022 )

Cite this article
You have full access to this open access article

- M. J. Hermoso-Orzáez ORCID: orcid.org/0000-0002-6430-3233 1 &
- J. Garzón-Moreno 1
13k Accesses
9 Citations
Explore all metrics
A Correction to this article was published on 28 February 2022
This article has been updated
This work provides a general risk management procedure applied to synchronized supply chains. After conducting a literature review and taking the international standard ISO 28000 and ISO 31000 as a reference. The most important steps that enable organizations to carry out supply chain risk management are described. Steps such as defining the context, identifying and analyzing risks or avoiding them, controlling them and mitigating them are some of the main points of this work. On the other hand, we carried out a practical case in which the execution of this procedure is carried out in a real supply chain located in the city of Jaén. In this specific case study, the most important risks and those that require early treatment will be discussed. In addition, a series of suggestions and ideas will be established, by way of conclusions, that allow said organization to improve the results that we have obtained in risk management.
Similar content being viewed by others

The Model for Risk Management and Mastering Them in Supply Chain

Supply Chain Risk Management

Categorizing Supply Chain Risks: Review, Integrated Typology and Future Research
Avoid common mistakes on your manuscript.
1 Introduction
Most of the companies there are frequently alterations in their operation that cause disruptions in their daily operations (Artikis, 2016 ). These types of alterations are a consequence of potential risks that exist in the environment in which the business activity takes place (Prakash et al., 2020 ). Identifying and analyzing the risks of supply chain disruption is essential to prevent disaster scenarios (Shareef et al., 2020 ). Recent studies analyze the impact of supply risks on the company's optimal purchasing decisions (Zhang et al., 2020 ) and the importance of correctly identifying the source of supply risks (Guo et al., 2016 ).
In a globalized world, where the flow of products and / or services of many organizations have an international reach, it is essential to be able to manage the risk or at least (Xue et al., 2020 ), to have plans that mitigate (He & Yang, 2018 ) to a greater or lesser extent the potential risks to which one can Face any organization (Schauer et al., 2019 ). The configuration and coordination analyzes can be used as a foundation for further research in the context of integrating manufacturing network and supply chain theory (Rudberg & Olhager, 2003 ). On the other hand, Risk management using decision methods (AHP) (analytical hierarchy process) to face solutions with a value under uncertainty (Álvarez-lópez, 2016 ) is presented as a practical and innovative tool (Choi et al., 2017 ). There are some recently published review papers on risk management in the supply chain operations processes under uncertain environments. For example (Colicchia, 2012 ) use a rigorous literature review methodology, called systematic literature network analysis, to identify future research directions of supply chain risk management and to recognize streams of research that appear to be most promising. Heckmann et al. ( 2015 ) systematically define supply chain risk concepts, terminologies, and risk measuring and modeling methods from related fields. Fahimnia et al. ( 2015 ) use bibliometric and network analysis tools to identify key research clusters/topics, interrelationships, and generative research areas on quantitative models for managing supply chain risks. Chiu and Choi ( 2016 ) review the use of mean-risk models for analytical supply chain risk analysis. Govindan and Jepsen ( 2017 ) review the risks related to suppliers in service supply chains. Snyder et al. ( 2016 ) examine operations management literature on supply chain disruptions and provide an overview of the research within six supply chain processes (Snyder et al., 2016 ).
The result of this work is the elaboration of an applied methodology that allows companies to carry out a risk management of their supply chain in a useful and logical way (Senna et al., 2020 ) In parallel to the explanation of the procedure, we will carry out a practical case of risk management for a real supply chain located in the city of Jaén (Spain).
One of the objectives of this document is to demonstrate the importance of the risk management of a supply chain to guarantee the success of the organization (Fernando et al., 2018 ) Supply chains need great care to function properly and, risk analysis is the most powerful tool to minimize problems in the near future (da Silva et al., 2020 ).
At all times, the international standard related to the management of supply chain risks, ISO 28000, will be used as a reference and other standards that have been considered convenient, such as ISO 31000 (Leitch, 2010 ) (project risk management) or (UNE-EN- IS0 9001, 2015 ) (quality management). Both ISO 31000 (UNE-EN-31000 AENOR, 2018 ) and ISO 28000 (UNE-EN-ISO 2800 AENOR, 2008 ) reflect the need for risk management not only in the supply chain, but in all parts of an organization (Blos et al., 2016 ) Both require more reflection than many organizations do on the subject (Hermoso-Orzáez et al., 2020 ).
2 Methodology and objectives
There are studies that used the integrated approach consisting of AHP to solve multi-criteria decision-making problems (MCDM) with criteria weights (Sarkar & Biswas, 2021 ) for risk treatment. Este documento tiene como objetivo identificar, clasificar y priorizar los riesgos de la cadena de suministro que enfrentan las pequeñas y medianas empresas de fabricación de pan y derivados para desarrollar una metodología de gestión de riesgos de la cadena de suministro (Alora & Barua, 2020 ). With this study we intend a triple objective:
Risk detection, risk mitigation, and risk recovery, Reduce risk management in supply chains to a single procedure through the study and collection of numerous methods and documents related to the subject (DuHadway et al., 2019 )
Apply this procedure to a practical case in a current supply chain, measuring the results and assessing them for possible measures that can reduce the probability of occurrence of each one or reduce or mitigation its impact on the chain.
To make the reader aware of the importance of risk management in supply chains and the corresponding role they must acquire within organizations.
The methodology that is summarized in this document, we find stages that are more qualitative, such as definition of links or description of phases, and stages where it will be necessary to use numerical techniques that allow us to quantify, evaluate and prioritize the risks that are going trying during the early stages (Machado Nardi et al., 2020 ) The methodology for proper risk management consists of six steps characterized by a descriptive content in most of them and a logical chronology that helps and complements the beginning of its next phase. (Felfel et al., 2018 ) There are high impact research works that include and measure qualitative elements with methodologies designed to be qualitative, inductive and exploratory, thus involving multiple data collection methods and tools. More specifically, during the first stage of empirical analysis, these studies map and analyze preferences and perceptions of product quality at both the consumer and supply chain level.These qualitative insights may not be given adequate value initially. But it is precisely in the following stages or steps of risk monitoring and control that we are going to adjust its real impact on the supply chain (Tenorio et al., 2021 ).
2.1 Define the general process and establish the context of the supply chain to analyse
Correct risk management requires a detailed knowledge of the company, the market in which it operates and the legal, social, political and cultural environment that surrounds it.
In order for a company to initiate an analysis to make an improvement, it must know at what point it is to, from there, perform an assessment or diagnosis. These states of maturity include information, talent, workers, their objectives, values, their policy, the activities of each process, etc. Organizations must know what their position is within the chain to which they belong. Within this aspect we have two options: that the organization occupies most of the supply chain to which it belongs (the same company is responsible for most of the activities) or that the organization occupies a link within the chain supply (vertical integration is less).
Our case study will focus on "PanJaén", a family business located in the city of Jaén (Spain). This company in the services sector offers its customers a wide variety of breads, coming to work with more than 10 types of flour (some organic) for its preparation. Other of its products are savory, whether snacks or puff pastry, and cakes. In addition, during all seasons they merge the most avant-garde and innovative styles of the market to offer products of all kinds, such as mantecados or roscones de Reyes at Christmas time.
It is defined as a company experienced by a family totally related to the bakery sector and known for the quality of its artisan products. They presume to use quality raw materials, ecological ingredients and be in continuous training and qualification, integrating any technological advance for their productive development. In addition, these bakeries are in an expansion process, that is, they increasingly incorporate new products in their stores to serve the citizens of Jaén.
All the activities that “PanJaén” controls in its supply chain are in the city mentioned. Some of the general aspects of our study company are those found in Table 1 .
On the one hand, the information obtained up to this point, allows to place the entire supply chain (except the domain of the suppliers) under the same location. There will be risks that do not matter to those responsible for “PanJaén”, such as those related with customs or exchange rates.
On the other hand, knowing the main characteristics of the corporate environment of the organization, such as the objective or its policies, we will have a guide by which to make decisions about preventive measures to avoid the risks detected.
2.2 Separate the process into groups of related tasks and systematically consider the characteristics of each operation
The supply chain has different links with specific planning and execution and dependent on the rest. Therefore, we can differentiate, in general, three large blocks for all supply chains. These blocks will be supply, production and distribution. These three links are of general application, that is, depending on the supply chain we are studying the links may vary and can be all considered, depending on the interdependence they have with each other and the need to differentiate them. (Ventura et al., 2013 ).
In the “PanJaén” supply chain, we will classify four groups: suppliers, production, distribution and points of sale.
2.2.1 Suppliers
Suppliers are those companies that supply others with goods or services necessary for the proper functioning of the business. "PanJaén" has several suppliers of raw material, one of them being the main one for the elaboration of all its products. This first supplier supplies them with almost all the necessary elements, such as flour, yeast, baking powder or butter. The raw material of this supplier represents the highest percentage in the company's products.
Another provider supplies you with eggs, milk, sugar and salt.
A third supplier is the one in charge of the complements, that is to say, those components (like the decorative ones) that accompany the main product and that are normally edible. There are many products sold accompanied by edible flowers, chocolate chips or colored balls that are purchased and applied directly to the target piece.
And finally, a fourth supplier is the one that supplies the assembly, that is, the materials that the company needs to be able to transport its products, such as covers, bags or boxes for the cakes. These, unlike the previous ones, are not edible and most of them have the company logo, as well as contact information, since they have a direct relationship with the customer.
2.2.2 Production
It corresponds to the internal processes that comprise the activities and manufacturing tasks that occur within the company. In other words, a production process is a system of actions that are related to each other and whose objective is none other than to transform elements, systems or processes. For this, some input factors are needed that, throughout the process, will increase in value thanks to the transformation.
In our case study, all production processes are carried out in the same physical place established in the industrial polygon of the capital Polígino de los Olivares s/n Jaén (Spain), except for a final baking that occurs at the point of sale. According to "PanJaén", the key to its products is in slow fermentation. This process is done since the water is mixed with the flour and goes until the first minutes of baking. First, a pre-fermentation is done slowly that will favor the final fermentation in order to be precise in the furnace jump. This is the key to improving the quality of bread, since it manages to respect and take care of the benefits that each of its stages generates.
This company has tunnel ovens with independent temperature controls throughout the oven. These ovens help to easily adjust the different temperatures during the baking cycle and optimize the first bake. Once the final result is achieved, they are packaged and go to the destination physical stores, giving way to the next link in the chain. Subsequently, at the point of sale, a second baking is carried out, which lasts approximately 15 min.
2.2.3 Distribution
It is made up of the different delivery processes until reaching the customer. The first thing that comes to mind when talking about distribution is the section from when the product is ready to be delivered to the final customer until this happens, but this is not always the case. A company that belongs to an intermediate link in its supply chain is a customer and at the same time a provider of other links in the same chain, but it is not the end customer (Ocampo & Ospina, 2016 ). “PanJaén” uses a subcontracted fleet that carries out this work. Logically it is done on a daily basis due to the products with which it works. This link is, without a doubt, the one with the least dominance of the company “PanJaén” (together with the suppliers) since it does not dominate it in its entirety. Road maps, vehicle maintenance, packaging and management of entrances and exits of the means of distribution are planned and coordinated by “PanJaén” and by the transport company.
2.2.4 Points of sale
They are the places where customers directly access products, that is, physical stores. Here, the customer can observe all the products that the company offers and buy them at the same time. There are almost 20 points that "PanJaén" has in the city, so they are accessible to virtually the entire population.
Its opening hours are from 7:00 a.m. to 9:30 p.m., seven days a week. These establishments, as I have mentioned before, have ovens where the second baking of the bread is produced to achieve greater splendor for the customer.
2.3 Risk identification
No matter how much a company strives to control its processes, a crisis may arise from the weakest link. Even this link can be several levels away from the company that is directly affected (such as a supplier that provides a transport service for the distribution of food in a vehicle that does not meet the necessary quality requirements).
In general, supply chains are made up of similar agents. However, the risks for two similar chains may vary depending on various factors such as the activity to which they belong, the agents participating in it, the place where they are developed or the number of customers they satisfy. It is therefore difficult to assume that a particular risk for a supply chain has the same importance and value as that same risk in another supply chain.The biggest drawback of the risk is based on its great diversity, its multitude of origins, its variable consequences and the complex interrelation with the rest. The identification of risks involves naming the risk without explaining or quantifying it. Logically, people who work in a part of the supply chain have a greater facility to identify the risks of that part. That is why the definition and functional separation of parts of the supply chain is really important to carry out a successful risk identification.
Knowledge is an important resource in the supply chain and a critical determinant of the competitiveness of the supply chain (Jayaram & Pathak, 2013 ). This is developed both at the organizational level and at the individual level. While some authors focus on knowledge as a firm attribute, others point to the individual as the place of knowledge creation. When using the individual-level perspective of the knowledge-based vision, the company's ability to manage supply chain risk will depend on the risk mitigation competence of its supply chain managers. Therefore, we seek to better understand the factors that affect the risk mitigation competence of the manager (Ambulkar et al., 2015 ).
The risks of the supply chain can also encapsulate, for example, the risk of suppliers (delays in receiving raw material or poor quality material). Within an organization, internal risk factors, such as those related to forecast errors, failures, capacity problems and inventory problems, should also not be overlooked. Another example would be operational risks, related to the internal activity of the organization (Rogers et al., 2016 ).
Through the use of the qualitative methods “What if…?” And “Brainstorm”, the main risks that exist in the supply chain we are studying are collected (ITM Platform, 2016 ) (UNE-EN 31,010 2011). The risks identified in the “PanJaén” supply chain have been obtained from a list of their own elaboration for the first assessment of their impact using sources such as the Iowa State University College (Amling & Daugherty, 2020 ), the International Journal of Logistics and Applications Research (Rogers et al., 2016 ) and the International Journal of Production Research (Blos et al., 2016 ). The identified risks appear in Table 2 . These have been ordered according to their meaning and we have obtained a total of five risk groups: operational, direct process to the product/service, suppliers, safety and labor rights.
2.4 Risk analysis and assessment
The purpose of analyzing the risks is to obtain a list in which the risks of the chain are prioritized, which determines the relevance that should be given to each of the elements mentioned. With this prioritization, it will be much easier to visualize the importance that each risk has within the supply chain.
We will use the "Hierarchical Analytical Process, AHP". The AHP model was developed by the mathematician Saaty ( 2008 ) and consists of formalizing the intuitive understanding of complex problems by building a hierarchical model. The basis of the process is based on the fact that it allows numerical values to be given to the judgments given by people, managing to measure how each element of the hierarchy contributes to the immediately higher level from which it emerges. (Khalilzadeh & Derikvand, 2018 ; Delgado-Galván et al., 2011 ; Aznar & Guijarro, 2012 ). The process will consist of two phases: a first qualitative analysis and a second quantitative analysis. For the qualitative analysis, we will use the probability and impact matrix where the evaluator, in this case the organization, will determine for each risk these two characteristics. Probability refers, as we know, to the feasibility of something happening. The impact, on the other hand, refers to the consequences they would have on the supply chain (Ramanathan, 2001 ) (Wang et al., 2008 ).
Thus, we ask that each risk of the 14 identified be assigned a probability of occurrence between four categories (very low, low, medium or high) and an impact on the organization (mild, moderate, high or catastrophic) (Zamora Aguas et al., 2013 ). From here we will look for the relationship between the different risk groups we have. This relationship will be achieved by comparing the rating of each risk group with the rest of the rating and, depending on that comparison, we will establish the importance of one group over the other (Díaz Córdova et al., 2017 ),
Once we have each risk defined, we can assign a general probability and impact to the risk group. This allocation is given by an average of the probabilities and impacts of the risks that form that group. For example, all operational risks have an average probability, so the probability of the group of "Operational risks (1)" will have an average probability. Its impact will be high since two of the risks have this impact, while the remaining two have it moderate and catastrophic.
The next step will be to rate the risk group according to the probability and impact we have previously assigned. This rating will be determined according to Table 3 , with four possible levels (Ayuso-Muñoz et al., 2017 ).
For example, for the “Suppliers” risk group, its probability is low and its impact is high, so it will have a high rating. We will obtain a total of 5 ratings, since there are 5 types of risks we have. Once we perform this procedure for all groups, we will have as a result Table 4 , which we show below (He & Yang, 2018 ).
From here we will look for the relationship between the different risk groups we have. This relationship will be achieved by comparing the rating of each risk group with the rest of the rating and, depending on that comparison, we will establish the importance of one group over the other through Table 5 (Díaz Córdova et al., 2017 ; Khalilzadeh & Derikvand, 2018 ).
The "Linguistic variable" column refers to the importance of one risk group over another. As can be seen in Table 4 , when we are going to compare two risk groups, we will always compare the one with the highest rating with the other. In our case, we see that the risk group that has a rating above is 2, with a critical rating. The rest have a high rating, so Group 2 has a strong importance over the rest (Hermoso-Orzáez et al., 2020 ; Yusof & Salleh, 2013 ).
Once we have the relationships between the different risks, we will assign them numerical values. To do this, we will use the author Saaty comparison scales, which are shown in Table 6 (Hermoso-Orzáez et al., 2019 ; Saaty, 2008 ).
When two risks are equally important, even if they are two critical risks, the weight of one over the other will be low. The greater the weight of one risk with respect to another, the greater the importance it has over it. The intermediate values of the scales also represent that group, that is, if one risk has a strong importance over another, the value that we will assign not only can be 5, but we could also assign the values 4 or 6. These values in this Scales can be used as margins when the risks are of very similar importance, as is our case.
Looking at our results, of 5 groups of risks that we have, 4 have a high rating, that is, when we compare a risk of those four with the rest we can use the values of the scale (1, 2, 3) to prioritize in small magnitude those 4 values of equal rating. Logically, we will not be able to apply high values, such as 5 or 6 between two risk groups with the same rating, because among those risks there is not so much clear difference. Thus, we will begin by comparing the risk groups among them, assigning values of the scales corresponding to their comparison. For example, for risks 4 and 5, which have a high rating, their score will move in low values. Finally we decided that those of type 3 will have a little more importance over those of 4 because their probability of occurrence is greater, so that group 3 will have value 2 when compared with group 4.
In the end, we will add the columns to see the total in each risk. Table 7 shows the results.
The next step will be to weigh the table. It will be done by dividing each of the column values by the total calculated above. In this way we will obtain the weighting of each risk when compared to another, so we will need to average the weights in a new column.
That result will be the weighting of our risk group, which if multiplied by 100 will result in a percentage. The calculations of this step are reflected in Table 8 (Aznar & Guijarro, 2012 ; Ramanathan, 2001 ).
We note that the sum of all weights is "1", so they have been done correctly. The table that really interests us is the following (Table 9 ), with the importance that each group of risks must have when managing them.
We already have our final weights. We see that the most important risk is number 2 (Risks related to the direct process to the product / service), followed by risk group number 5 and 1 (Blos et al., 2016 ).
2.4.1 Consistency analysis of the AHP methodology
Before continuing, we will check the consistency of our results, as there are times that when it comes to rating the risks, the relationships established initially do not make sense. When the matrices are of a larger size, there are occasions that the criteria with which the risks are qualified are contrasted with each other and do not really reflect the importance of one risk over another. Thus, we have to verify that it is not our case and that the judgments carried out are consistent. (Baudry et al., 2018 ; Park et al., 2019 ).
To do this, we will calculate the consistency ratio that is given by the division of two parameters (1). This relationship will be more correct as it approaches 0. We will consider our rating reasonable as long as this ratio is less than 0.1. The two parameters that define this relationship are the consistency index and random consistency (Aznar & Guijarro, 2012 ; De Brucker et al., 2013 ).
2.4.1.1 Formula 1-consistency ratio
First, we will multiply the initial matrix by the average vtor (weights of each risk group). The result will be a vector that we will call “Total row vector”.
2.4.1.2 Formula 2-vector calculation total row
Next, we divide each term of this “Total row vector” by the average vector, resulting in a new vector that will be around the values of the size of our matrix (in this case the value 5). Ideally, the quotients should be the same number as the size of the matrix, indicating that the coherence is excellent. But as this does not happen, we will have to calculate the average of the quotients, which will correspond to \(\lambda_{\max }\) . All these calculations are reflected in Table 9 .
We calculate the consistency index, which is given by the formula ( 3 ).
2.4.1.3 Formula 3-consistency index calculation
To know what the value of the random consistency is, "RI", we move to Table 10 . The values of this variable are established depending on the size of the matrix we are studying. This consistency is the average consistency of 10,000 randomly constructed matrices and will help us move from the consistency index to the consistency ratio of a matrix.
Upon fulfilling the condition, we verify that the criteria for rating our risks are correctly performed, that is, they do not contradict each other.
We already have our final weights. We see that the most important risk is number 2 (Risks related to the direct process to the product / service), followed by risk group number 5 and 1.
The whole process must be checked for the consistency of the results, as there are times that when it comes to rating the risks, the relationships established initially do not make sense. When the matrices are of a larger size, there are occasions that the criteria with which the risks are qualified are contrasted with each other and do not really reflect the importance of one risk over another. Thus, we have to verify that it is not our case and that the judgments carried out are consistent.
This consistency relationship is given by the division of two parameters. We will consider our rating reasonable as long as this ratio is less than 0.1. The two parameters that define this relationship are the consistency index and random consistency. (Valladão et al., 2019 ).Upon fulfilling the condition, we verify that the criteria for rating our risks are correctly performed, that is, they do not contradict each other (Aznar & Guijarro, 2012 ). Once we have achieved a prioritization of risk groups, we will do the same process for each specific risk within its category. That is, we will carry out this process five times, and we will see what prioritization each risk has within its group to, finally, be able to compare the 15 risks suffered by the supply chain we are studying.
The result would be as shown in Table 11 below.
Once the prioritization of all the risks within your group has been calculated, we can make a final table where the importance of each risk group will appear on the one hand and, on the other, the importance of each risk within your group. Thus, on a percentage scale, we will see that priority occupies each of the 14 risks identified in the beginning, giving it a position of 1 to 14 possible, 1 being the most important risk of studying and 14 the least. Table 12 shows the order of importance of the risks, which have a color assigned in their box that follows the criteria of Table 13 .
2.4.2 Risk management
In risk management, good knowledge and classification of the risks obtained during the analysis process are necessary to be able to make decisions about future actions to reduce, mitigate or avoid them. Decision-making to deal with risks is often conditioned by ethical, legal, financial or strategic considerations.
It is very important to identify the risks that need treatment and those that do not. This decision of whether or not to treat risk, and how to do it, may depend on the costs and benefits of accepting the risk and/or implementing controls to mitigate, reduce or eliminate it.
In our case study, the most important risk is 2.1, which represents the risk of "Poor quality of the final product". Then we have 5.2, which represents the risk of "poor staff training," and third we have the risk of "poor customer service."
The following Fig. 1 shows a 3D bar graph that allows us to observe it visually.
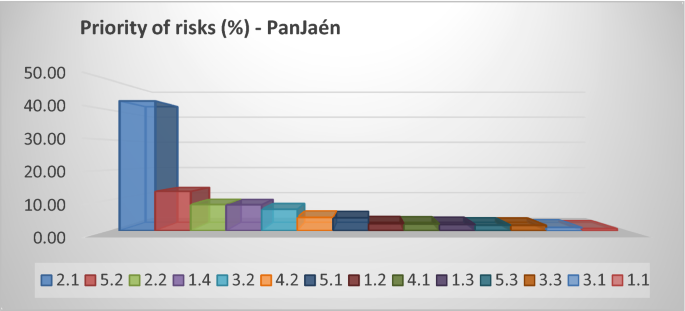
3D bar diagram of the prioritization of risks in "PanJaén". (Own elaboration)
2.5 Risk monitoring and control
As part of the risk management process, risks and controls should be monitored and reviewed on a regular basis. This monitoring must establish and maintain procedures to be able to track and evaluate the performance not only of the risks to which it is subject, but to be able to follow its own risk management system as a whole.
This evaluation of the plans, procedures and capacities should be carried out periodically through actions that the organization considers as it has been analyzed throughout the risk management process, such as performance evaluations or reports. That is why monitoring and review should take place at all stages of the process (UNE-EN 31,010 2011 ).
This monitoring and control process can be carried out by two agents: management or independent staff through audits.
The objective of this step will be to verify that:
The hypotheses established in relation to risks continue to be valid.
The assumptions on which risk assessment has been based, including external and internal contexts, continue to be valid.
The degree of compliance with the risk management policy, objectives and goals is monitored.
Risk assessment techniques have been properly applied.
The recording of data and the results of the follow-up that facilitates subsequent analysis actions.
2.6 Risk mitigation
The risks can be reduced o mitigated through supply chain redesign such as diversification or modularity in processes and design (Kleindorfer & Saad, 2005 ), strategic inventory stockpiling (Chopra & Sodhi, 2004 )), risk pooling (Sheffi, 2003 ), principles from TQM Total Quality Management (Lee & Whang, 2005 ), or reducing supply chain complexity (Manuj & Mentzer, 2008 ). Using the traditional classification of risk frequency and impact (Norrman & Jansson, 2004 ), appropriate risk levels can be determined. Identifying general risk levels for Force Majeure disruptions and designing appropriate procedural safeguards and prevention mechanisms such as earthquake-proofing or fire facilities, backup inventory or suppliers, and contingency plans can effectively reduce the impact of a disruption.
Reducing the risk of Inside Jobs and other opportunistic behavior within the supply chain is more reliant on relationships than processes put in place.
These approaches are presented in Fig. 2 and connected to the different phases of risk management (DuHadway et al., 2019 ).
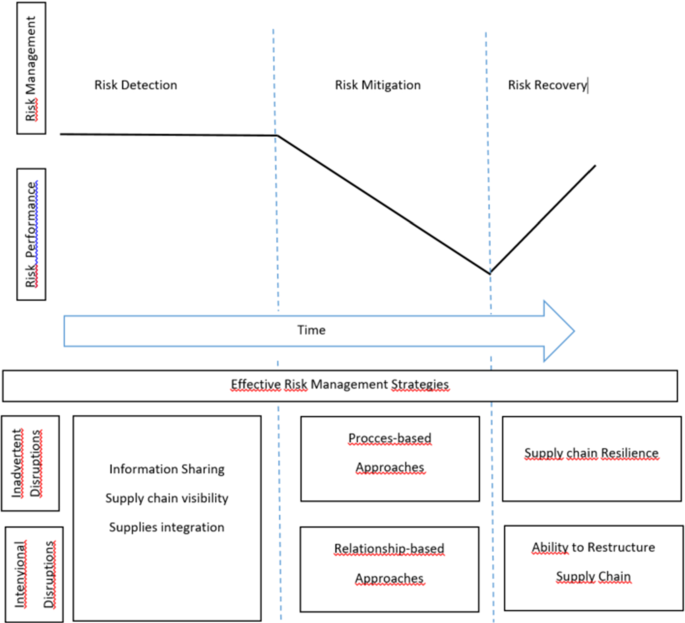
Effective risk management strategies (Own elaboration)
Reducing the risk of poor customer services, or bad quality of final products within a supply chain is manageable through setting up appropriate processes with a supply chain such as carrying safety stock and using reliable supplies (Tomlin, 2006 ), using a list of approved or preferred suppliers who have been pre-certified to some degree of reliability (Gosling et al., 2010 ), or using a risk management process to identify and manage risk levels for inadvertent disruptions which occur within the supply chain. Certain safeguards might be taken such as securing against theft (Sullivan, 2010 )(Sullivan, 2010 ), but in general, there are limited actions that a firm can take to prevent a targeted disruption. Recognizing that the entire supply chain might be exposed in the case of a disruption and strategically developing a balanced supply chain that is not extremely dependent on the contribution from a single firm can alleviate some of the risk, but there is no simple solution to eliminate targeted.
For our study case, the risk that most concerns those responsible for the supply chain is related to the final quality of the product. This may be due to several reasons:
The product has direct contact with the buyer, who is the one who finally makes sense of the supply chain. The customer expects a quality of the product they buy and this quality may not be what the customer expected, both better and worse.
The organization is not really aware of the quality of its products, that is, it does not know the real thinking of the client exactly. For this reason, when assigning a value to the probability and impact of this risk, those responsible for the chain are worried about something they cannot control, a fact that is logical because it is beyond their reach.
The good or bad quality of the final product has part of many risks that we have been analyzing before, such as raw material, poor staff knowledge or breakage through packaging. That is why quality represents, with this percentage so something, the consequences of many actions along the supply chain.
On the one hand, we know that the organization defines its products of a high quality, both in its elaboration, result and customer service. In fact, the objective of this company is “Create a quality brand image”. So, when customers go to their points of sale or buy on demand, they expect excellent quality, which is the quality that the organization claims to offer. So, could we lessen the impact of this risk in case it occurs? The answer would rather be no. If a customer is disappointed with one of their products, the impact would be catastrophic. So we will try to treat and mitigate the risk by playing with the probability of its occurrence.
There are many factors that influence the quality of "PanJaén" products. In fact, they are found along the supply chain. To analyze the causes of this risk, we will use one of the methods explained in the “Risk analysis and assessment” step, as we will analyze a risk. The method that we will use will be "Analysis of cause and effect (fish bone)", as can be seen in Fig. 3 . We will try to explain this Fig. 3 , cause and effect analysis for the risk "Poor quality of the final product". We have different causes from different points in the supply chain and a negative final effect or risk that we want to eliminate, treat or mitigate.

Cause and effect analysis for the risk "Bad quality of the final product." (Own elaboration)
3.1 Raw material
The poor conservation that the raw material presents with respect to time, either in the places of production, due to the inventory, or at the same point of sale, makes the product quality worse.On the other hand, the complements are pieces that accompany the final product, such as nuggets or edible wrappings. These, normally, are added directly to the product to be sold, so you have to be careful with their taste since they are not treated throughout the process.Finally in this group, the components of the raw material are essential, as many of the clients look for certain properties in the bread and ours may not comply with them. Thus, we must be clear about each of the properties of each component for treatment.
3.2 Manufacturing
It can be greatly affected by ignorance of the processes. The ignorance is not only of the personnel, but that a process in general is wrong and, although the personnel carry it out correctly, the result is not the ideal one. This may occur, for example, in the stages of component blends.On the other hand, product burns are crucial, as they give an undesirable appearance and taste. Because our bread has a double baking, you have to plan well the conditions of each of them and constantly monitor them.
3.3 Point of sale
The physical conditions of the establishment, such as cleanliness or smell, cause the client's expectations to decline. In the same way, the treatment of the shopkeeper influences the clients and the way of attending or taking the products.On the other hand, the products must have a strategic distribution not only intended for consumption, but also for the mixture of odors that may arise.
3.4 Physical appearance
This is one of the most direct aspects with the client, because it includes the attractiveness of the product that can be given by its touch or its shape. On many occasions, the customer has an opinion about a cake or a loaf of bread simply by looking at it, regardless of its taste.
If we perform an ABC classification of our risks, the result is as shown in Fig. 4 . We can see that only a few risks produce very negative effects.
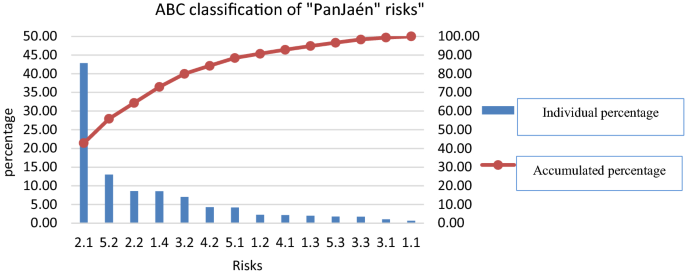
ABC classification of "PanJaén" risks. (Own elaboration)
We see that the first five risks occupy 80% of the prioritization (Group A of the classification), while the other nine add up to 20% among all. Therefore, the Plan of Measures among the five main risks could be the focus of proposing measures to reduce their probability and impact (Lo & Tang, 2019 ) See Table 14 . In this table, we identify each risk with the causes that originate it in the supply chain and the measures to be taken to avoid or mitigate it.
4 Discussion
The risk of poor quality of the final product may be given by the uncertainty of the organization about the opinions of its customers, so it would be important to take measures to inform us about the opinion of the customers about our products, as the rest of the tasks of the supply chain are under the control of the organization.
One possible measure would be for the supply chain to conform to some global standard that accredits the quality objective, such as ISO 9001(UNE-EN- IS0 9001 2015). This international standard takes into account the activities of the organization, focusing on all the elements of quality management. with which a company must have to have an effective system that allows it to manage and improve the quality of its products or services. (Khalilzadeh & Derikvand, 2018 ).
Another possible measure would be the creation of an application App movil aplications phone, for the mobile phone that rewards customer loyalty. Through this application, created by the company, consumers would have the possibility to value all products without having to do so in front of the workers. In addition, each time customers make a purchase, they can pass their identification code (on the phone screen) through a reader who is at the point of sale, transmitting the purchase data to the application. Thus, both clients and the organization would win:
The application, knowing the products that each customer purchases, can customize the suggestions and offer discounts and offers for their next purchases.
On the other hand, the organization will add more value to its chain and attract a greater number of customers. You can instantly report all your products without the need for a customer to enter the point of sale to learn about a new product.
5 Conclusion
This work allows us to conclude that the supply chain is valued by two key strategic concepts: its vulnerability and its resilience. Risk management is a fundamental tool for its control and future of the company.
Organizations will always be exposed to different types of risks that arise as an organization progresses in its activity. These risks will be characterized by their probability of occurrence and their impact on the organization. These variables can initially be assessed subjectively or qualitatively by the risk manager. Being able to seem not dependent on or outside the organization. That is, the risk exists and due to the circumstances of the moment, it will have a certain probability and impact. This is where risk management itself begins, which allows organizations to identify, analyze and quantitatively assess risks through techniques such as the use of "Hierarchical Analytical Process, AHP", presented in this study. That allows hierarchical ordering of risks, to later be able to treat and manage them appropriately, avoid them, mitigate them or eliminate them.
When an incident occurs and it is acted upon after its occurrence, the organization must be aware that early risk management allows a less demanding and faster reaction to that emergency, so risk management is an improvement process The flexibility between chain actors continues to increase.
Another of the great conclusions that we obtain from this study is the following: a supply chain can effectively challenge its vulnerabilities when all the actors that comprise it frequently share information. This will build trust, increase visibility, and decrease uncertainty in the network. Collaboration is related to visibility, as it includes the organization's willingness to share risk. Therefore, an organization regardless of its location or operating environment is part of a complex supply chain and has political, economic, competitive, logistical or infrastructure concerns. Therefore, up-to-date information flows are required regarding the products and services produced, which are highly coordinated within and outside the limits of the organization itself. All this leads us to affirm that information and its transfer are key in the processes of identification and treatment of risks.
Risk management in supply chains is increasingly important not only for the activities carried out in them but also for managers. Logically, organizations are not born with risk management in place but are created as events occur and according to the perspectives that managers acquire with their knowledge and experience.
Finally, it should be noted that the risk management process should never be an arbitrary process, but rather carefully crafted and prepared. The key tool to carry out this entire process is the creation of a department dedicated to risk management that analyzes and determines the scope of each situation and the measures to be taken, being aware that a crucial element is a strong communication. between all the members of this department and the different links in the chain. All this will give us the ability to face, avoid mitigating or eliminating the risks that affect us, whatever their nature. In this way, we will start the path towards a strong, flexible and competitive chain.
Looking at our case study, it can be seen that many of those factors that influence quality are risks that we have already identified, so the measures we take will be directed towards these risks that affect quality. In this way, we will reduce the probability and impact of these risks and we will also reduce the probability of occurrence of our main risk.
The risk of poor quality of the final product is observed as the main risk to be treated due to its impact on the supply chain of food production companies, on the final customer. It does not always have to occur in its entirety due to the combination of factors throughout the supply chain, but can be given by the uncertainty of the organization about the opinions of its customers. Therefore, it would be important to take measures to inform us about the opinion of customers about the final products placed in the hands of the consumer, since the rest of the tasks of the supply chain are under the direct control of the organization. In this process, the transmission of information along the supply chain is essential for risk management. In this sense, the use of new technologies such as Mobile Apps, which allow the customer to assess quality directly and interactively, is shown to be a powerful tool for the future for interactive risk management.
Change history
28 february 2022.
A Correction to this paper has been published: https://doi.org/10.1007/s10479-022-04583-w
Alora, A., & Barua, M. K. (2020). Development of a supply chain risk index for manufacturing supply chains. International Journal of Productivity and Performance Management . https://doi.org/10.1108/IJPPM-11-2018-0422
Article Google Scholar
Álvarez-lópez, I. R. A. A. (2016). Optimal allocation of a fixed production under price uncertainty. Annals of Operations Research . https://doi.org/10.1007/s10479-014-1702-7
Ambulkar, S., Blackhurst, J. V., & Cantor, D. E. (2015). Supply chain risk mitigation competency: An individual-level knowledge-based perspective. International Journal of Production Research, 54 (5), 1398–1411. https://doi.org/10.1080/00207543.2015.1070972
Amling, A., & Daugherty, P. J. (2020). Logistics and distribution innovation in China. IJPDLM, 50 (3), 323–332. https://doi.org/10.1108/IJPDLM-07-2018-0273
Artikis, P. T. (2016). Deriving advantage over a crisis by incorporating a new class of stochastic models for risk control operations. Annals of Operations Research, 247 (2), 823–831. https://doi.org/10.1007/s10479-015-1896-3
Ayuso-Muñoz, J. L., Yagüe-Blanco, J. L., & Capuz-Rizo, S. F. (2017). Lecture Notes in Management and Industrial Engineering Project Management and Engineering Research (Vol. 49). http://www.springer.com/series/11786
Aznar, J., & Guijarro, F. (2012). New Valuation Methods: Multicriteria Models. (Universitat Politécnica de Valencia, Ed.) ((2 a Ed.). Valencia (Spain). https://riunet.upv.es/bitstream/handle/10251/19181/TOC_6083_02_01.pdf?sequence=3
Baudry, G., Macharis, C., & Vallée, T. (2018). Range-based multi-actor multi-criteria analysis: A combined method of multi-actor multi-criteria analysis and monte carlo simulation to support participatory decision making under uncertainty. European Journal of Operational Research, 264 (1), 257–269. https://doi.org/10.1016/j.ejor.2017.06.036
Blos, M. F., Hoeflich, S. L., Dias, E. M., & Wee, H.-M. (2016). A note on supply chain risk classification: Discussion and proposal. International Journal of Production Research, 54 (5), 1568–1569. https://doi.org/10.1080/00207543.2015.1067375
Chiu, C. H., & Choi, T. M. (2016). Supply chain risk analysis with mean-variance models: A technical review. Annals of Operations Research, 240 (2), 489–507. https://doi.org/10.1007/s10479-013-1386-4
Choi, T. M., Govindan, K., Li, X., & Li, Y. (2017). Innovative supply chain optimization models with multiple uncertainty factors. Annals of Operations Research, 257 (1–2), 1–14. https://doi.org/10.1007/s10479-017-2582-4
Chopra, S., & Sodhi, M. M. S. (2004). Managing risk to avoid: Supply-chain breakdown. MIT Sloan Management Review , 46 (1).
Colicchia, F. S. (2012). Supply chain risk management: A new methodology for a systematic literature review. Supply Chain Management: An International Journal, 17 (4), 403–418.
da Silva, E. M., Ramos, M. O., Alexander, A., & Jabbour, C. J. C. (2020). A systematic review of empirical and normative decision analysis of sustainability-related supplier risk management. Journal of Cleaner Production, 244 , 118808. https://doi.org/10.1016/j.jclepro.2019.118808
De Brucker, K., MacHaris, C., & Verbeke, A. (2013). Multi-criteria analysis and the resolution of sustainable development dilemmas: A stakeholder management approach. European Journal of Operational Research, 224 (1), 122–131. https://doi.org/10.1016/j.ejor.2012.02.021
Delgado-Galván, X., Herrera, M., Izquierdo, J., & Pérez-García, R. (2011). Applications of AHP Methodology for decision making in the management of the supply network. In: Conference: XI SEREA, Seminario Iberoamericano de planificación, proyecto y operación de abastecimiento de aguaAt: Morelia, Mexico (p. 11).
Díaz Córdova, J. F., Coba Molina, E., & Navarrete López, P. (2017). Fuzzy logic and financial risk. A proposed classification of financial risk to the cooperative sector. Contaduria y Administracion, 62 (5), 1687–1703. https://doi.org/10.1016/j.cya.2017.10.001
DuHadway, S., Carnovale, S., & Hazen, B. (2019). Understanding risk management for intentional supply chain disruptions: Risk detection, risk mitigation, and risk recovery. Annals of Operations Research, 283 (1–2), 179–198. https://doi.org/10.1007/s10479-017-2452-0
Fahimnia, B., Tang, C. S., Davarzani, H., & Sarkis, J. (2015). Quantitative models for managing supply chain risks: A review. European Journal of Operational Research, 247 (1), 1–15. https://doi.org/10.1016/j.ejor.2015.04.034
Felfel, H., Ben, W., Omar, Y., & Faouzi, A. (2018). Stochastic multi-site supply chain planning in textile and apparel industry under demand and price uncertainties with risk aversion. Annals of Operations Research, 271 (2), 551–574. https://doi.org/10.1007/s10479-018-2980-2
Fernando, Y., Walters, T., Ismail, M. N., Seo, Y. W., & Kaimasu, M. (2018). Managing project success using project risk and green supply chain management: A survey of automotive industry. International Journal of Managing Projects in Business, 11 (2), 332–365. https://doi.org/10.1108/IJMPB-01-2017-0007
Gosling, J., Purvis, L., & Naim, M. M. (2010). Supply chain flexibility as a determinant of supplier selection. International Journal of Production Economics, 128 (1), 11–21. https://doi.org/10.1016/j.ijpe.2009.08.029
Govindan, K., & Jepsen; M. B. . (2017). Supplier risk assessment based on trapezoidal intuitionistic fuzzy numbers and ELECTRE TRI-C: A case illustration involving service suppliers. Journal of the Operational Research Society . https://doi.org/10.1057/jors.2015.51
Guo, S., Zhao, L., & Xu, X. (2016). Impact of supply risks on procurement decisions. Annals of Operations Research . https://doi.org/10.1007/s10479-013-1422-4
He, B., & Yang, Y. (2018). Mitigating supply risk: An approach with quantity flexibility procurement. Annals of Operations Research, 271 (2), 599–617. https://doi.org/10.1007/s10479-018-2840-0
Heckmann, I., Comes, T., & Nickel, S. (2015). A critical review on supply chain risk - Definition, measure and modeling. Omega (united Kingdom), 52 , 119–132. https://doi.org/10.1016/j.omega.2014.10.004
Hermoso-Orzáez, M. J., Orejón-Sánchez, R. D, Gago-Calderón, A. (2020). Analysis and Risk Management in Projects of Change to Led in Street Lighting According to ISO-21500 and UNE-EN-62198. In: C.-R. S. F. (eds) Ayuso Muñoz J.L., Yagüe Blanco J.L. (Ed.), Project Management and Engineering Research (1 a ed., pp. 405–424). Adolfo López-Paredes, INSISOC, University of Valladolid, Valladolid, Spain: Springer, Cham. https://doi.org/10.1007/978-3-030-54410-2_29
Hermoso-Orzáez, M. J., Cámara-Martínez, J., Rojas-Sola, J. I., & Gago-Calderon, A. (2019). Analytical and economic methodology for storage of large heavyweight equipment in industrial processes. Economic Research-Ekonomska Istrazivanja . https://doi.org/10.1080/1331677X.2019.1696692
Jayaram, J., & Pathak, S. (2013). A holistic view of knowledge integration in collaborative supply chains. International Journal of Production Research, 51 (7), 1958–1972. https://doi.org/10.1080/00207543.2012.700130
Khalilzadeh, M., & Derikvand, H. (2018). A multi-objective supplier selection model for green supply chain network under uncertainty. Journal of Modelling in Management, 13 (3), 605–625. https://doi.org/10.1108/JM2-06-2017-0062
Kleindorfer, P. R., & Saad, G. H. (2005). Managing disruption risks in supply chains. Production and Operations Management, 14 (1), 53–68.
Lee, H. L., & Whang, S. (2005). Higher supply chain security with lower cost: Lessons from total quality management. International Journal of Production Economics, 96 (3), 289–300. https://doi.org/10.1016/j.ijpe.2003.06.003
Leitch, M. (2010). ISO 31000:2009-The new international standard on risk management. Risk Analysis, 30 (6), 887–892. https://doi.org/10.1111/j.1539-6924.2010.01397.x
Lo, A., & Tang, Z. (2019). Pareto-optimal reinsurance policies in the presence of individual risk constraints. Annals of Operations Research, 274 (1–2), 395–423. https://doi.org/10.1007/s10479-018-2820-4
Machado Nardi, V. A., Auler, D. P., & Teixeira, R. (2020). Food safety in global supply chains: A literature review. Journal of Food Science, 85 (4), 883–891. https://doi.org/10.1111/1750-3841.14999
Manuj, I., & Mentzer, J. T. (2008). Global supply chain risk management strategies. International Journal of Physical Distribution and Logistics Management, 38 (3), 192–223. https://doi.org/10.1108/09600030810866986
Norrman, A., & Jansson, U. (2004). Ericsson’s proactive supply chain risk management approach after a serious sub-supplier accident. International Journal of Physical Distribution and Logistics Management, 34 , 434–456.
Ocampo, P. C., & Ospina, R. P. (2016). Marketing and supply chain in relation to the auto parts sector in Colombia. Sinapsis, 8 , 21–41.
Google Scholar
Park, B., Nam, T., & Yeo, G. (2019). Study on location selection of integrated depot of warehouse stores utilizing AHP method. Journal of Digital Convergence, 17 (2), 135–144. https://doi.org/10.14400/JDC.2019.17.2.135
ITM Platform. (2016). Don’t let the vase break: a dozen techniques to identify risks. . Projects, Program,Portfoilo . https://www.itmplatform.com/es/blog/que-no-se-te-rompa-el-jarron-una-docena-de-tecnicas-para-identificar-riesgos/
Prakash, S., Kumar, S., Soni, G., Jain, V., & Rathore, A. P. S. (2020). Closed-loop supply chain network design and modelling under risks and demand uncertainty: An integrated robust optimization approach. Annals of Operations Research, 290 (1–2), 837–864. https://doi.org/10.1007/s10479-018-2902-3
Ramanathan, R. (2001). A note on the use of the analytic hierarchy process for environmental impact assessment. Journal of Environmental Management, 63 (1), 27–35. https://doi.org/10.1006/jema.2001.0455
Rogers, H., Srivastava, M., Pawar, K. S., & Shah, J. (2016). Supply chain risk management in India – practical insights. International Journal of Logistics Research and Applications, 19 (4), 278–299. https://doi.org/10.1080/13675567.2015.1075476
Rudberg, M., & Olhager, J. (2003). Manufacturing networks and supply chains: An operations strategy perspective. Omega, 31 (1), 29–39. https://doi.org/10.1016/S0305-0483(02)00063-4
Saaty, T. L. (2008). Decision making with the analytic hierarchy process (AHP). International Journal of Services Sciences, 1 (1), 83–98. https://doi.org/10.1504/IJSSCI.2008.017590
Sarkar, B., & Biswas, A. (2021). Pythagorean fuzzy AHP-TOPSIS integrated approach for transportation management through a new distance measure. Soft Computing . https://doi.org/10.1007/s00500-020-05433-2
Schauer, S., Polemi, N., & Mouratidis, H. (2019). Correction to MITIGATE: A dynamic supply chain cyber risk assessment methodology. Journal of Transportation Security . https://doi.org/10.1007/s12198-018-0197-x
Senna, P., Reis, A., Santos, I. L., Dias, A. C., & Coelho, O. (2020). A systematic literature review on supply chain risk management: Is healthcare management a forsaken research field? Benchmarking . https://doi.org/10.1108/BIJ-05-2020-0266
Shareef, M. A., Dwivedi, Y. K., Kumar, V., Hughes, D. L., & Raman, R. (2020). Sustainable supply chain for disaster management: structural dynamics and disruptive risks. Annals of Operations Research . https://doi.org/10.1007/s10479-020-03708-3
Sheffi, Y. (2003). Supply chain management under the threat of international terrorism. The International Journal of Logistics Management, 12 (2), 1–11.
Snyder, L. V., Atan, Z., Peng, P., Rong, Y., Schmitt, A. J., & Sinsoysal, B. (2016). OR/MS models for supply chain disruptions: a review. IIE Transactions . https://doi.org/10.1080/0740817X.2015.1067735
Sullivan, A. K. (2010). Piracy in the Horn of Africa and its effects on the global supply chain. Journal of Transportation Security, 3 (4), 231–243. https://doi.org/10.1007/s12198-010-0049-9
Tenorio, M., Pascucci, S., Verkerk, R., & Dekker, M. (2021). What does it take to go global? The role of quality alignment and complexity in designing international food supply chains. Supply Chain Management-an International Journal . https://doi.org/10.1108/SCM-05-2020-0222
Tomlin, B. (2006). On the value of mitigation and contingency strategies for managing supply chain disruption risks. Management Science, 52 (5), 639–657. https://doi.org/10.1287/mnsc.1060.0515
UNE-EN 31010. .Risk management. Risk appreciation techniques (2011). :AENOR (Spain). https://www.une.org/encuentra-tu-norma/busca-tu-norma/norma?c=N0047287
UNE-EN- IS0 9001. ISO 9001. (2015). Normas9000. Obtenido de http://www.normas9000.com/content/que-es-iso.aspx (2015). file:///C:/Users/UJA/Downloads/009001NEIS106_ES.pdf
UNE-EN-31000 AENOR. UNE-EN-ISO 31000-Risk Management (2018). Spain. https://www.aenor.com/normas-y-libros/buscador-de-normas/UNE?c=N0059900
UNE-EN-ISO 2800 AENOR. UNE-EN-ISO 2800.Specifications for security management systems for the supply chain (2008). Spain.
Valladão, D., Silva, T., & Poggi, M. (2019). Time-consistent risk-constrained dynamic portfolio optimization with transactional costs and time-dependent returns. Annals of Operations Research, 282 (1–2), 379–405. https://doi.org/10.1007/s10479-018-2991-z
Ventura, J. A., Valdebenito, V. A., & Golany, B. (2013). A dynamic inventory model with supplier selection in a serial supply chain structure. European Journal of Operational Research, 230 (2), 258–271. https://doi.org/10.1016/j.ejor.2013.03.012
Wang, Y. M., Luo, Y., & Hua, Z. (2008). On the extent analysis method for fuzzy AHP and its applications. European Journal of Operational Research, 186 (2), 735–747. https://doi.org/10.1016/j.ejor.2007.01.050
Xue, K., Li, Y., Zhen, X., & Wang, W. (2020). Managing the supply disruption risk: Option contract or order commitment contract? Annals of Operations Research, 291 (1–2), 985–1026. https://doi.org/10.1007/s10479-018-3007-8
Yusof, N. A. M., & Salleh, S. H. (2013). Analytical Hierarchy Process in Multiple Decisions Making for Higher Education in Malaysia. Procedia - Social and Behavioral Sciences, 81 , 389–394. https://doi.org/10.1016/j.sbspro.2013.06.448
Zamora Aguas, J. P., Adarme, W. A., & Arango Serna, M. D. (2013). Supply risk analysis: Applying system dynamics to the Colombian healthcare sector. Ingenieria e Investigacion, 33 (3), 76–81.
Zhang, J., Chan, F. T. S., & Xu, X. (2020). The optimal order decisions of a risk-averse newsvendor under backlogging. Annals of Operations Research . https://doi.org/10.1007/s10479-020-03636-2
Download references
Open Access funding provided thanks to the CRUE-CSIC agreement with Springer Nature.
Author information
Authors and affiliations.
Department of Graphic Engineering Design and Projects, University of Jaén, Jaén, Spain
M. J. Hermoso-Orzáez & J. Garzón-Moreno
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to M. J. Hermoso-Orzáez .
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Hermoso-Orzáez, M.J., Garzón-Moreno, J. Risk management methodology in the supply chain: a case study applied. Ann Oper Res 313 , 1051–1075 (2022). https://doi.org/10.1007/s10479-021-04220-y
Download citation
Accepted : 28 July 2021
Published : 10 August 2021
Issue Date : June 2022
DOI : https://doi.org/10.1007/s10479-021-04220-y
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Supply chain
- Multi-criterion analysis
- decision analysis
- Product quality
- Consistency
- Find a journal
- Publish with us
- Track your research
A practical approach to supply-chain risk management
In the last decade , a number of organizations have been rocked by unforeseen supply-chain vulnerabilities and disruptions, leading to recalls costing hundreds of millions of dollars in industries ranging from pharmaceuticals and consumer goods to electronics and automotive . And multiple government organizations and private businesses have struggled with cybersecurity breaches, losing critical intellectual property due to failures in the supplier ecosystem.
Stay current on your favorite topics
At the heart of these crises is a common theme—the lack of robust processes to identify and successfully manage growing supply-chain risks as the world becomes more interconnected. New threats, such as cyber-ransom attacks, are emerging alongside more traditional and longer-acknowledged supplier risks, such as supplier bankruptcy.
The challenge of supply-chain risk management has been exacerbated by globalization, where even sensitive products like defense systems use raw materials, circuit boards, and related components that may have originated in countries where the system manufacturer did not even know it had a supply chain. This increased complexity has brought with it more potential failure points and higher levels of risk.
Yet progress in addressing these risks has been slow. In our 2010 survey of 639 executives covering a range of regions and industries, 71 percent said their companies were more at risk from supply-chain disruption than previously, and 72 percent expected those risks to continue to rise. In 2018, the United States government stood up multiple agencies and task forces to better address supply-chain risk (including the Critical Infrastructure Security and Cybersecurity Agency in the Department of Homeland Security and the Protecting Critical Technology Task Force at the Department of Defense), and the private sector continues to seek a uniform and proven methodology for assessing and monitoring risks in a way that truly minimizes business disruption.
We believe public- and private-sector organizations have struggled to progress significantly on this topic for several reasons:
- Supply-base transparency is hard (or impossible) to achieve. In modern multi-tier supply chains, hundreds or thousands of suppliers may contribute to a single product. Even identifying the full set of suppliers from the raw-material sources to a final assembled system can require a significant time investment.
- The scope and scale of risks is intimidating. The probability and severity of many risks is difficult to ascertain (How likely are certain weather patterns? How often will a supplier’s employee be careless in cybersecurity practices?), and therefore difficult to address, quantify, and mitigate.
- Proprietary data restrictions impede progress. In complex products, Tier 1 or 2 suppliers may consider their supply chains to be proprietary, limiting visibility at the purchaser or integrating-manufacturer level.
Rather than admiring the problem and these difficulties, we suggest organizations begin to tackle issues in a structured way, cataloging and addressing known risks while improving the organization’s resilience for the inevitable unknown risk that becomes a problem in the future.
Would you like to learn more about our Operations Practice ?
A structured approach to supply-chain risk management.
We recommend that organizations start by thinking of their risks in terms of known and unknown risks.
Known risks can be identified and are possible to measure and manage over time. For instance, a supplier bankruptcy leading to a disruption in supply would be a known risk. Its likelihood can be estimated based on the supplier’s financial history, and its impact on your organization can be quantified through consideration of the products and markets the supplier would disrupt. Newer risks such as cybersecurity vulnerabilities in the supply chain are also now quantifiable through systems that use outside-in analysis of a company’s IT systems to quantify cybersecurity risks.
Organizations should invest time with a cross-functional team to catalog a full scope of risks they face, building a risk-management framework that determines which metrics are appropriate for measuring risks, “what good looks like” for each metric, and how to rigorously track and monitor these metrics. This team can also identify gray areas where risks are hard to understand or define (e.g., tiers of the supply chain where no visibility exists). This analysis can dimensionalize the scale and scope of unknown risks.
Unknown risks are those that are impossible or very difficult to foresee. Consider the sudden eruption of a long dormant volcano that disrupts a supplier you didn’t know was in your supply chain, or the exploitation of a cybersecurity vulnerability buried deep the firmware of a critical electronic component. Predicting scenarios like these is likely impossible for even the most risk-conscious managers.
For unknown risks, reducing their probability and increasing the speed of response when they do occur is critical to sustaining competitive advantage. Building strong layers of defense combined with a risk-aware culture can give an organization this advantage.
Managing known risks
Organizations can use a combination of structured problem solving and digital tools to effectively manage their known-risk portfolio through four steps:
Step 1: Identify and document risks
A typical approach for risk identification is to map out and assess the value chains of all major products. Each node of the supply chain—suppliers, plants, warehouses, and transport routes—is then assessed in detail (Exhibit 1). Risks are entered on a risk register and tracked rigorously on an ongoing basis. In this step, parts of the supply chain where no data exist and further investigation is required should also be recorded.
Step 2: Build a supply-chain risk-management framework
Every risk in the register should be scored based on three dimensions to build an integrated risk-management framework: impact on the organization if the risk materializes, the likelihood of the risk materializing, and the organization’s preparedness to deal with that specific risk. Tolerance thresholds are applied on the risk scores reflecting the organization’s risk appetite.
It is critical to design and use a consistent scoring methodology to assess all risks. This allows for prioritizing and aggregating threats to identify the highest-risk products and value-chain nodes with the greatest failure potential.
Step 3: Monitor risk
Once a risk-management framework is established, persistent monitoring is one of the critical success factors in identifying risks that may damage an organization. The recent emergence of digital tools has made this possible for even the most complex supply chains, by identifying and tracking the leading indicators of risk. For example, a large organization operating in a regulated industry identified 25 leading indicators of quality issues at its plants and contract manufacturers, ranging from structural drivers including geographical location and number of years in operation to operational performance metrics, such as “right first time” and deviation cycle times. These 25 indicators were carefully weighted to develop a quality risk-exposure score, and then tracked on a regular cadence.
Successful monitoring systems are customized to an organization’s needs, incorporating impact, likelihood, and preparedness perspectives. Hence, while one organization may track deviations on manufacturing lines to predict quality issues, another may follow real-time Caribbean weather reports to monitor hurricane risk at its plants in Puerto Rico. Regardless, it is critical to have an early warning system to track top risks to maximize the chances of mitigating, or at the very least limiting, the impact from their occurrence.

Deliver on time or pay the fine: Speed and precision as the new supply-chain drivers
Step 4: Institute governance and regular review
The final critical step is to set up a robust governance mechanism to periodically review supply chain risks and define mitigating actions, improving the resilience and agility of the supply chain.
An effective supply-chain risk-management governance mechanism is a cross-functional risk board with participants representing every node of the value chain. It typically includes line managers who double-hat as risk owners for their function, giving them ownership of risk identification and mitigation. In most cases, the risk board receives additional support from a central risk-management function, staffed with experts to provide additional guidance on identifying and mitigating risks.
An effective board will meet periodically to review the top risks in the supply chain and define the mitigation actions. The participants will then own the execution of mitigation actions for their respective functional nodes. For example, if the board decides to qualify and onboard a new supplier for a critical component, the procurement representative on the board will own the action and ensure its execution.
Additionally, in many organizations the risk board will also make recommendations to improve the agility and resilience of the supply chain, ranging from reconfiguring the supply network, finding new ways of reducing lead times, or working with suppliers to help optimize their own operations. Increasing supply-chain agility can be a highly effective mitigation strategy for organizations to improve their preparedness for a wide range of risks.
Managing unknown risks
Unknown risks are, by their nature, difficult or impossible to predict, quantify, or incorporate into the risk-management framework discussed above for known risks. In our experience, mitigating unknown risks is best achieved through creating strong defenses combined with building a risk-aware culture.
Building strong defenses
Strong defenses, from request-for-proposal (RFP) language to worker training, all contribute to an organization identifying and stopping unknown risks before they affect operations. Exhibit 2 outlines typical layers of defense organizations employ to defend against unknown risks.
Building a risk-aware culture
A risk-aware culture helps an organization both establish and maintain strong defensive layers against unknown risks, as well as respond more quickly when an unknown risk surfaces and threatens operations.
- Acknowledgement. Management and employees need to feel empowered to pass on bad news and lessons from mistakes. This openness fosters an environment where it is okay to voice and deal with issues. Culturally, it is critical that the organization not get discouraged or point fingers when a risk event occurs, and instead works harmoniously towards a rapid resolution.
- Transparency. Leaders must clearly define and communicate an organization’s risk tolerance. Risk mitigation often has an associated incremental cost, and so it is important to align on which risks need to be mitigated and which can be borne by the organization. An organization’s culture should also allow for warning signs of both internal and external risks to be openly shared.
- Responsiveness. Employees need to be empowered to perceive and react rapidly to external change. This can be enabled by creating an ownership environment, where members feel responsible for outcome of actions and decisions.
- Respect. Employees’ risk appetites should be aligned with an organization, so that individuals or groups do not take risks or actions that benefit themselves but harm the broader organization.
The road ahead
Global supply chains are irreversible, as are the supply-chain risks that globalization has brought with it. Our experience suggests that it is critical for organizations to build robust programs for managing both known and unknown supply-chain risks. Leaders should also recognize that risk management is not merely about setting up processes and governance models, but also entails shifts in culture and mind-sets. By employing these approaches, organizations increase their chances of minimizing supply-chain disruptions and crises, while capturing the full value of their supply-chain strategies.
Tucker Bailey and Edward Barriball are partners in McKinsey’s Washington, DC office. Arnav Dey is an engagement manager in the Boston office, and Ali Sankur is a senior practice manager in Chicago.
Explore a career with us
Related articles.

The route to no-touch planning: Taking the human error out of supply chain planning

The automation imperative
Right product, right time, right location: Quantifying the semiconductor supply chain
Risk Management of Port Operations: a Systematic Literature Review and Future Directions
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents

Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Exploring acceptable risk in engineering and operations research and management science by bibliometric analysis
Affiliations.
- 1 School of Safety Science and Engineering, Xi'an University of Science and Technology, Xi'an, China.
- 2 Xi'an Key Laboratory of Urban Public Safety and Fire Rescue, Xi'an, China.
- PMID: 36307897
- DOI: 10.1111/risa.14049
As the decision-making basis for "safety" in risk management and risk assessment activities, acceptable risk has always been an important topic of risk-related research. Based on the records in the Science Citation Index Expanded database and Social Sciences Citation Index database via the Web of Science Core Collection, 1124 articles or reviews related to acceptable risk in engineering and operations research and management science were retrieved. These documents, published between 1961 and 2021, covered 3056 authors, 75 countries/territories, 1296 institutions, and 323 journals. In this study, bibliometric data such as annual growth trends were analyzed by using descriptive statistics. Through the co-occurrence maps created by CiteSpace and Gephi, the most productive and influential countries/territories, institutions, and authors as well as their cooperation networks were identified. Further analysis was conducted to determine the core publications and publication sources in this field through co-citation analysis. Insights into focus areas and research topics over time were obtained through keyword co-occurrence analysis. This study provides a macroscopic overview of acceptable risk research and may help researchers better understand this research field and predict its dynamic directions.
Keywords: CiteSpace; Gephi; acceptable risk; bibliometric analysis; quantitative risk assessment; safety.
© 2022 Society for Risk Analysis.
- Global directory Global directory
- Product logins Product logins
- Contact us Contact us
Our Privacy Statement & Cookie Policy
All Thomson Reuters websites use cookies to improve your online experience. They were placed on your computer when you launched this website. You can change your cookie settings through your browser.
- Privacy Statement
- Cookie Policy

Join our community
Sign up for industry-leading insights, updates, and all things AI @ Thomson Reuters.

The growing importance of adverse media searches
False positives and false negatives: How best to leverage adverse media searches in the battle against financial crime.

Charting a path forward with AI adoption in compliance: Reducing uncertainty and embracing change
Industry experts discuss the best examples of AI being used for compliance, the key risks, what this means for compliance analysts, and how leaders can make themselves and regulators comfortable with putting AI to use.

Mitigate risk, detect fraudulent activity, and streamline investigations
In today’s digital world, risk and fraud detection is even more important than ever before
Related posts

How technology solves 5 key challenges hampering law enforcement investigations

How businesses can responsibly use AI and address ethical and security challenges

Fraud investigation: An overview
More answers.

Five of the most important benefits of a global legal department

When to send work to outside counsel (and when to keep it)

Researching market-standard language through SEC documents
Five Compliance Best Practices for … Conducting a Risk Assessment

As an accompaniment to our biweekly series on “What Every Multinational Should Know About” various international trade, enforcement, and compliance topics, we are introducing a second series of quick-hit pieces on compliance best practices. Give us two minutes, and we will give you five suggested compliance best practices that will benefit your international regulatory compliance program.
Conducting an international risk assessment is crucial for identifying and mitigating potential risks associated with conducting business operations in foreign countries and complying with the expansive application of U.S. law. Because compliance is essentially an exercise in identifying, mitigating, and managing risk, the starting point for any international compliance program is to conduct a risk assessment. If your company has not done one within the last two years, then your organization probably should be putting one in motion.
Here are five compliance checks that are important to consider when conducting a risk assessment:
- Understand Business Operations: A good starting point is to gain a thorough understanding of the organization’s business operations, including products, services, markets, supply chains, distribution channels, and key stakeholders. You should pay special attention to new risk areas, including newly acquired companies and divisions, expansions into new countries, and new distribution patterns. Identifying the business profile of the organization, and how it raises systemic risks, is the starting point of developing the risk profile of the company.
- Conduct Country- and Industry-Specific Risk Factors: Analyze the political, economic, legal, and regulatory landscape of each country where the organization operates or plans to operate. Consider factors such as political stability, corruption levels, regulatory environment, and cultural differences. You should also understand which countries also raise indirect risks, such as for the transshipment of goods to sanctioned countries. You also should evaluate industry-specific risks and trends that may impact your company’s risk profile, such as the history of recent enforcement actions.
- Gather Risk-Related Data and Information: You should gather relevant data and information from internal and external sources to inform the risk-assessment process. Relevant examples include internal documentation, industry publications, reports of recent enforcement actions, and areas where government regulators are stressing compliance, such as the recent focus on supply chain factors. Use risk-assessment tools and methodologies to systematically evaluate and prioritize risks, such as risk matrices, risk heat maps, scenario analysis, and probability-impact assessments. (The Foley anticorruption, economic sanctions, and forced labor heat maps are found here .)
- Engage Stakeholders: Engage key stakeholders throughout the risk-assessment process to gather insights, perspectives, and feedback. Consult with local employees and business partners to gain feedback on compliance issues that are likely to arise while also seeking their aid in disseminating the eventual compliance dictates, internal controls, and other compliance measures that your organization ends up implementing or updating.
- Document Findings and Develop Risk-Mitigation Strategies: Document the findings of the risk assessment, including identified risks, their potential impact and likelihood, and recommended mitigation strategies. Ensure that documentation is clear, concise, and actionable. Use the documented findings to develop risk-mitigation strategies and action plans to address identified risks effectively while prioritizing mitigation efforts based on risk severity, urgency, and feasibility of implementation.
Most importantly, you should recognize that assessing and addressing risk is an ongoing process. You should ensure your organization has established processes for the ongoing monitoring and review of risks to track changes in the risk landscape and evaluate the effectiveness of mitigation measures. Further, at least once every two years, most multinational organizations should be updating their risk assessment periodically to reflect evolving risks and business conditions as well as changing regulations and regulator enforcement priorities.
If you have questions or concerns concerning this article, please feel free to reach out to any of the authors or your Foley & Lardner attorney. Would you like more practical compliance tips like these? Click Here to Register for our email list to receive future biweekly emails and practical international regulatory compliance tips.

Gregory Husisian
Related insights, what every multinational company should know about … antiboycott regulations, a review of recent whistleblower developments, doj and ftc raise concerns about overlapping ownership in public utility companies.
Company Filings | More Search Options
Company Filings More Search Options -->

- Commissioners
- Reports and Publications
- Securities Laws
- Commission Votes
- Corporation Finance
- Enforcement
- Investment Management
- Economic and Risk Analysis
- Trading and Markets
- Office of Administrative Law Judges
- Examinations
- Litigation Releases
- Administrative Proceedings
- Opinions and Adjudicatory Orders
- Accounting and Auditing
- Trading Suspensions
- How Investigations Work
- Receiverships
- Information for Harmed Investors
- Rulemaking Activity
- Proposed Rules
- Final Rules
- Interim Final Temporary Rules
- Other Orders and Notices
- Self-Regulatory Organizations
- Staff Interpretations
- Investor Education
- Small Business Capital Raising
- EDGAR – Search & Access
- EDGAR – Information for Filers
- Company Filing Search
- How to Search EDGAR
- About EDGAR
- Press Releases
- Speeches and Statements
- Securities Topics
- Upcoming Events
- Media Gallery
- Divisions & Offices
- Public Statements
- Divisions and Offices
DERA Careers
- Economist Bios
- Economic Analysis in Rulemaking
- Staff Papers and Analyses
- Academic Publications
- Structured Disclosure
- DERA Events
- Academic Seminars
May 3, 2024
Why should I work for DERA?
Explore the various type of work DERA does:
Financial economist, research associate, statistician, operations research analyst.
Operations Research Analysts (or Data Scientists) in DERA are federal employees who typically have a bachelor’s or higher degree in operations research, mathematics, or similar quantitative field, and perform quantitatively intensive analyses using a wide range of advanced techniques such as data mining, text analytics, natural language processing, topic modeling, machine learning, as well as classical statistical methods. Using these techniques, Operations Research Analysts generate risk metrics and develop processes designed to identify potential market misconduct, federal securities law statutory or rule violations, and other issues that could adversely affect the well-functioning of financial market activity and investors. DERA Operations Research Analysts commonly use tools like JAVA, Python, SAS, and R to implement cutting-edge analytical methods, and to design, develop, maintain, and modify quantitative models, metrics and reports that support market risk assessment and monitoring activities.
Financial Analyst
It specialist, honors internship, which position(s) do i qualify for, [+] use this matrix to find out more about applying, how do i apply.
- Washington State University
- Announcements & Notices
- Awards & Achievements
- Business Operations
- Campus Announcements
- Community & Culture
- Professional Resources & Training
- Student News
- WSU College of Medicine
ChatGPT Fails at Heart Risk Assessment

Originally published by WSU Insider
SPOKANE, Wash. – Despite ChatGPT’s reported ability to pass medical exams, new research indicates it would be unwise to rely on it for some health assessments, such as whether a patient with chest pain needs to be hospitalized.
In a study involving thousands of simulated cases of patients with chest pain, ChatGPT provided inconsistent conclusions, returning different heart risk assessment levels for the exact same patient data. The generative AI system also failed to match the traditional methods physicians use to judge a patient’s cardiac risk. The findings were published in the journal PLOS ONE .
“ChatGPT was not acting in a consistent manner,” said lead author Dr. Thomas Heston, a researcher with Washington State University’s Elson S. Floyd College of Medicine. “Given the exact same data, ChatGPT would give a score of low risk, then next time an intermediate risk, and occasionally, it would go as far as giving a high risk.”
The authors believe the problem is likely due to the level of randomness built into the current version of the software, ChatGPT4, which helps it vary its responses to simulate natural language. This same randomness, however, does not work well for healthcare uses that require a single, consistent answer, Heston said.
“We found there was a lot of variation, and that variation in approach can be dangerous,” he said. “It can be a useful tool, but I think the technology is going a lot faster than our understanding of it, so it’s critically important that we do a lot of research, especially in these high-stakes clinical situations.”
Chest pains are common complaints in emergency rooms, requiring doctors to rapidly assess the urgency of a patient’s condition. Some very serious cases are easy to identify by their symptoms, but lower risk ones can be trickier, Heston said, especially when determining whether someone should be hospitalized for observation or sent home and receive outpatient care.
Currently medical professionals often use one of two measures that go by the acronyms TIMI and HEART to assess heart risk. Heston likened these scales to calculators with each using a handful of variables including symptoms, health history and age. In contrast, an AI neural network like ChatGPT can assess billions of variables quickly, meaning it could potentially analyze a complex situation faster and more thoroughly.
For this study, Heston and colleague Dr. Lawrence Lewis of Washington University in St. Louis first generated three datasets of 10,000 randomized, simulated cases each. One dataset had the seven variables of the TIMI scale, the second set included the five HEART scale variables and a third had 44 randomized health variables. On the first two datasets, ChatGPT gave a different risk assessment 45% to 48% of the time on individual cases than a fixed TIMI or HEART score. For the last data set, the researchers ran the cases four times and found ChatGPT often did not agree with itself, returning different assessment levels for the same cases 44% of the time.
Despite the negative findings of this study, Heston sees great potential for generative AI in health care – with further development. For instance, assuming privacy standards could be met, entire medical records could be loaded into the program, and an in an emergency setting, a doctor could ask ChatGPT to give the most pertinent facts about a patient quickly. Also, for difficult, complex cases, doctors could ask the program to generate several possible diagnoses. “ChatGPT could be excellent at creating a differential diagnosis and that’s probably one of its greatest strengths,” said Heston. “If you don’t quite know what’s going on with a patient, you could ask it to give the top five diagnoses and the reasoning behind each one. So it could be good at helping you think through a problem, but it’s not good at giving the answer.”
Media Contacts
- Thomas Heston, WSU Elson S. Floyd College of Medicine, 509-473-3456 , [email protected]
- Sara Zaske, WSU News & Media Relations, 509-335-4846 , [email protected]
Norway's wealth fund backs bid for PepsiCo biodiversity risk assessment
- Medium Text

- Company PepsiCo Inc Follow
Sign up here.
Reporting by Helen Reid Editing by Ros Russell
Our Standards: The Thomson Reuters Trust Principles. New Tab , opens new tab

Thomson Reuters
London-based reporter covering the European retail sector through a global lens. Focusing on companies including Adidas, H&M, Ikea, and Inditex and analysing corporate strategy, consumer trends, and regulatory changes, Helen also covers major supermarket groups like Ahold Delhaize, Carrefour, and Casino. She has a special interest in sustainability and how investors push for change in companies. Previously based in Johannesburg where she covered the mining industry.

Britain's oil and gas regulator on Friday awarded 31 new hydrocarbon exploration licences as part of efforts to extend production in the ageing basin.

Sustainability Chevron
Rains in southern brazil kill at least 39, some 70 still missing.
Heavy rains battering Brazil's southernmost state of Rio Grande do Sul have killed 39 people, local authorities said on Friday, and the death toll is expected to rise as dozens still have not been accounted for.


COMMENTS
Risk assessment and management was established as a scientific field some 30-40 years ago. Principles and methods were developed for how to conceptualise, assess and manage risk. These principles and methods still represent to a large extent the foundation of this field today, but many advances have been made, linked to both the theoretical ...
Annals of Operations Research - The year 2020 can be earmarked as the year of global supply chain disruption owing to the outbreak of the coronavirus (COVID-19). ... Risk assessment and operational approaches to manage risk in global supply chains. Transportation Journal, 52(3), 391-411. Google Scholar Kwak, D. W., Rodrigues, V. S., Mason, R ...
Risks exist in all aspects of our business world. Many risks exhibit properties of interconnection and complexity besides uncertainty and dynamics, and therefore may be difficult to quantify (Arena et al. 2010, 2011; Wu and Olson 2010; Wu et al. 2014).Operations research provides many tools, such as game theory and optimization, for dealing with risks in today's uncertain world (Wu et al ...
A risk assessment determines the likelihood, consequences and tolerances of possible incidents. "Risk assessment is an inherent part of a broader risk management strategy to introduce control measures to eliminate or reduce any potential risk- related consequences." 1 The main purpose of risk assessment is to avoid negative consequences related to risk or to evaluate possible opportunities.
Review. abstract. Risk assessment and management was established as a scientific field some 30-40 years ago. Principles. and methods were developed for how to conceptualise, assess and manage ...
The role of data analytics within operational risk management: A systematic review from the financial services and energy sectors ... research succumbs to the variability of experts' experiences and inherent human biases in risk assessment. For example, experts may not have experienced many operational loss events, nor the range of business ...
This work provides a general risk management procedure applied to synchronized supply chains. After conducting a literature review and taking the international standard ISO 28000 and ISO 31000 as a reference. The most important steps that enable organizations to carry out supply chain risk management are described. Steps such as defining the context, identifying and analyzing risks or avoiding ...
We discuss the need for data monitoring and the integration of various analytical tools into decision making processes by classifying the literature on application fields, analytics techniques, and the strategies used for implementation. We summarize our findings and propose a process to implement data-driven ORM with future research directions.
Abstract As the decision-making basis for "safety" in risk management and risk assessment activities, acceptable risk has always been an important topic of risk-related research. ... 1124 articles or reviews related to acceptable risk in engineering and operations research and management science were retrieved. These documents, published ...
Step 1: Identify and document risks. A typical approach for risk identification is to map out and assess the value chains of all major products. Each node of the supply chain—suppliers, plants, warehouses, and transport routes—is then assessed in detail (Exhibit 1). Risks are entered on a risk register and tracked rigorously on an ongoing ...
The interdependence of container shipping operations (CSOs) creates a hotbed of multiple operational risks. Risk analysis and assessment (RAA) is, therefore, a growing research focus on container shipping policy and management. Currently, it is challenging to grasp a state-of-the-art understanding of the field due to the fragmentation of the ...
Conclusions. The prepared systematic literature review was aimed at providing a general overview of related research to risk in mining sector. After a search process that yielded 736 results, 94 papers were selected. These papers were strictly related to the area of analysis, assessment and risk management in mining.
The operations in the process industry are challenged by a series of adverse factors, e.g., harsh environment, corrosion, fatigue, and natural hazards. The process industry is implementing risk assessment to identify and manage potential failure modes that can interrupt operation processes.
In this research, literature from three aspects including risk assessment of port operations and service, safety management of dangerous goods, and port supply chain risk management was collected and investigated, in order to put forward the future research direction related to the risk management of port operations. The research results show ...
European Journal of Operational Research, 253 (1), 1-13. 2. Calow, P. P. (Ed.). ... Risk assessment and management was established as a scientific field some 30-40 years ago. Principles and ...
In order to adopt a risk-based approach to managing health emergencies and mitigating risk, countries first need to identify hazards and assess their level of risk within the country. The results from a risk assessment allows proper planning and prioritization of efforts to better prevent, mitigate, detect early,
Second, this paper contributes to the field of risk management research in healthcare. Third, the tools and techniques for risk assessment and management that are applicable to staff areas of healthcare organizations are mentioned. ... Kumar S,J, Himes K,P, Kritzer C. Risk assessment and operational approaches to managing risk in global supply ...
A risk assessment is a systematic process performed by a competent person which involves identifying, analyzing, and controlling hazards and risks present in a situation or a place. This decision-making tool aims to determine which measures should be put in place in order to eliminate or control those risks, as well as specify which of them ...
As the decision-making basis for "safety" in risk management and risk assessment activities, acceptable risk has always been an important topic of risk-related research. ... 1124 articles or reviews related to acceptable risk in engineering and operations research and management science were retrieved. These documents, published between 1961 ...
In many engineering organizations, risk assessment inevitably focuses on engineering/technical risks with the possibility of financial risks being considered if, ... Journal of the Operational Research Society Volume 58, 2007 - Issue 1. Submit an article Journal homepage. 500 Views ...
Conducting a Risk Assessment. 1. Conducting a Risk Assessment. A risk assessment can be a valuable tool to help your unit identify, evaluate and prioritize its risks in order to improve decision-making and resource allocation. Harvard's Institutional Risk Management (IRM) program recommends the following process for c onducting risk assessments.
1. Background. There has been a shift around the approach to risk management of human subjects' research over the past decade. Previously, the most common approach included frequent on-site visits to conduct extensive source data monitoring, which potentially led to a review of all data elements (commonly referred to as 100% source data verification and review).
Risk analysis prioritizes risks based on their likelihood and their potential for harm. Through a thorough assessment of these risks and an impact analysis of each, the organization can put in place measures to manage them. Risk analysis is an essential piece to an effective risk assessment process for the overall framework of risk management ...
Here are five compliance checks that are important to consider when conducting a risk assessment: Understand Business Operations: A good starting point is to gain a thorough understanding of the organization's business operations, including products, services, markets, supply chains, distribution channels, and key stakeholders.
Operations Research Analysts (or Data Scientists) in DERA are federal employees who typically have a bachelor's or higher degree in operations research, mathematics, or similar quantitative field, and perform quantitatively intensive analyses using a wide range of advanced techniques such as data mining, text analytics, natural language processing, topic modeling, machine learning, as well ...
International Transactions in Operational Research. Early View. Original Article. Improved RBM-based feature extraction for credit risk assessment with high dimensionality. Jianxin Zhu, Jianxin Zhu [email protected] School of Economics and Management, Harbin Engineering University, Harbin, 150001 People's Republic of China ...
Over the last two decades, the UAE's construction sector has grown significantly with the development of tall buildings, but the region faces seismic risks. Similar concerns in China led to earthquake simulation research on a city scale. The objectives include developing programming for parallel computing and creating simplified models for estimating losses. The challenges include ...
On the first two datasets, ChatGPT gave a different risk assessment 45% to 48% of the time on individual cases than a fixed TIMI or HEART score. For the last data set, the researchers ran the cases four times and found ChatGPT often did not agree with itself, returning different assessment levels for the same cases 44% of the time.
Risk assessment for the supply chain of fast fashion apparel industry: A system dynamics framework. International Journal of Production Research. 2016; 54 (1):28-48. [Google Scholar] Meng Q, Liu X, Song Y, Wang W. An extended generalized TODIM method for risk assessment of supply chain in social commerce under interval type-2 fuzzy environment.
Norway's sovereign wealth fund plans to back a shareholder proposal demanding PepsiCo conduct a biodiversity risk assessment to gauge how vulnerable the soft drink and snacks giant's operations ...