This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.

Manage role assignment policies in Exchange Server
- 14 contributors
If you want to customize the permissions that you assign to a group of end users, create a new custom management role assignment policy. The assignment policy you create can be customized to suit your end user's specific requirements. For more information about assignment policies in Exchange Server, see Understanding Management Role Assignment Policies .
Looking for other management tasks related to managing permissions? Check out Permissions .
What do you need to know before you begin?
Estimated time to complete each procedure: 5 minutes
To open the EAC, see Exchange admin center in Exchange Server . To open the Exchange Management Shell, see Open the Exchange Management Shell .
You need to be assigned permissions before you can perform this procedure or procedures. To see what permissions you need, see the "Assignment policies" entry in the Role management permissions topic.
For information about keyboard shortcuts that may apply to the procedures in this topic, see Keyboard shortcuts in the Exchange admin center .
Having problems? Ask for help in the Exchange forums. Visit the forums at: Exchange Server , Exchange Online , or Exchange Online Protection .
Add an assignment policy
After you've created the new assignment policy, you assign users to it. For more information, see Change the assignment policy on a mailbox .
Use the EAC to create a new assignment policy
You can only create explicit assignment policies using the Exchange admin center (EAC). If you want to create a new default assignment policy, you must use the Exchange Management Shell. For more information, see the "Use the Exchange Management Shell to create a default assignment policy" section later in this topic.
In the role assignment policy window, provide a name for the new assignment policy.
Select the check box next to the role or roles you want to add to the assignment policy. You can select multiple roles, including end-user roles you've added. If you select a role that has child roles, the child roles are automatically selected.
Click Save to save the changes to the assignment policy.
Use the Exchange Management Shell to create an explicit assignment policy
To create an explicit assignment policy that can be manually assigned to mailboxes, use the following syntax.
This example creates the explicit assignment policy Limited Mailbox Configuration and assigns the MyBaseOptions , MyAddressInformation , and MyDisplayName roles to it.
For detailed syntax and parameter information, see New-RoleAssignmentPolicy .
Use the Exchange Management Shell to create a default assignment policy
To create a default assignment policy assigned to new mailboxes, use the following syntax.
This example creates the default assignment policy Limited Mailbox Configuration and assigns the MyBaseOptions , MyAddressInformation , and MyDisplayName roles to it.
Remove an assignment policy
If you no longer need a management role assignment policy, you can remove it.
All users assigned the assignment policy must be changed to another assignment policy. For more information about how to change an assignment policy on a mailbox, see Change the assignment policy on a mailbox .
All the management role assignments between the assignment policy and the assigned management roles must be removed. For more information about how to remove a role assignment from an assignment policy, see the Remove a role from an assignment policy section later in this topic.
If you want to remove a default assignment policy, it must be the last assignment policy in the Exchange Server organization.
Use the EAC to remove an assignment policy
In the EAC, navigate to Permissions > User Roles .
Use the Exchange Management Shell to remove an assignment policy
To remove an assignment policy, use the following syntax.
This example removes the New York Temporary Users assignment policy.
For detailed syntax and parameter information, see Remove-RoleAssignmentPolicy .
View a list of assignment policies or assignment policy details
You can view management role assignment policies in a variety of ways, depending on the information you want and whether you're using the EAC or the Exchange Management Shell.
In the EAC, you can view the list of assignment policies and the roles assigned to them. In the Exchange Management Shell, you can view all the assignment policies in your organization, list the mailboxes assigned a specific policy, and more.
Use the EAC to view a list of assignment policies
In the EAC, navigate to Permissions > User Roles . All of the assignment policies in the organization are listed here.
To view the details of a specific assignment policy, select the assignment policy you want to view. The description and the roles assigned to the assignment policy are displayed in the details pane.
Use the Exchange Management Shell to view a list of assignment policies
You can view a list of all the assignment policies in your organization by not specifying any assignment policies when you run the Get-RoleAssignmentPolicy cmdlet.
This procedure makes use of pipelining and the Format-Table cmdlet. For more information about these concepts, see the following topics:
about_Pipelines
Working with Command Output
To return a list of all assignment policies in your organization, use the following command.
To return a list of specific properties for all the assignment policies in your organization, you can pipe the results to the Format-Table cmdlet and specify the properties you want in the list of results. Use the following syntax.
This example returns a list of all the assignment policies in your organization and includes the Name and IsDefault properties.
For detailed syntax and parameter information, see Get-Mailbox or Get-RoleAssignmentPolicy .
Use the Exchange Management Shell to view the details of a single assignment policy
You can view the details of a specific assignment policy by using the Get-RoleAssignmentPolicy cmdlet and piping the output to the Format-List cmdlet.
This procedure makes use of pipelining and the Format-List cmdlet. For more information about these concepts, see the following topics:
To view the details of a specific assignment policy, use the following syntax.
This example views the details about the Redmond Users - no Text Messaging assignment policy.
Use the Exchange Management Shell to find the default assignment policy
You can find the default assignment policy by piping the output of the Get-RoleAssignmentPolicy cmdlet to the Where cmdlet. With the Where cmdlet, filter the data returned to display only the assignment policy that has its IsDefault property set to $True .
This procedure makes use of pipelining and the Where cmdlet. For more information about these concepts, see the following topics:
This example returns the default assignment policy.
Use the Exchange Management Shell to view mailboxes that are assigned a specific policy
You can find all the mailboxes assigned a specific assignment policy by piping the output of the Get-Mailbox cmdlet to the Where cmdlet. With the Where cmdlet, filter the data returned to display only the mailboxes that have their RoleAssignmentPolicy property set to the assignment policy name you specify.
Use the following syntax.
This example finds all the mailboxes assigned the policy Vancouver End Users.
Change the default assignment policy
You can change the management role assignment policy assigned to new mailboxes that are created. Changing the default role assignment policy doesn't change the assignment policy assigned to existing mailboxes. To change the assignment policy assigned to existing mailboxes, see Change the assignment policy on a mailbox .
You can't use the EAC to change the default assignment policy. You need to use the Exchange Management Shell.
Use the Exchange Management Shell to change the default assignment policy
To change the default assignment policy, use the following syntax.
This example sets the Vancouver End Users assignment policy as the default assignment policy.
New mailboxes are assigned the default assignment policy even if the policy hasn't been assigned management roles. Mailboxes assigned assignment policies with no assigned management roles can't access any mailbox configuration features in Outlook on the web.
For detailed syntax and parameter information, see Set-RoleAssignmentPolicy .
Add a role to an assignment policy
Use the eac to add a role to an assignment policy.
Use the Exchange Management Shell to add a role to an assignment policy
To create a management role assignment between a role and an assignment policy, use the following syntax.
This example creates the role assignment Seattle Users - Voicemail between the MyVoicemail role and the Seattle Users assignment policy.
For detailed syntax and parameter information, see New-ManagementRoleAssignment .
Remove a role from an assignment policy
If you don't want end users to have permissions to manage certain features of their mailbox or distribution group, you can remove the management role that grants the permissions from the management role assignment policy to which the user is assigned. If other users are assigned the same assignment policy, they also lose the ability to manage that feature.
Use the EAC to remove a role from an assignment policy
Clear the check box next to the role or roles you want to remove from the assignment policy. If you clear the check box for a role that has child roles, the check boxes for the child roles are also cleared.
Use the Exchange Management Shell to remove a role from an assignment policy
You can remove roles from assignment policies by retrieving the associated management role assignment using the Get-ManagementRoleAssignment cmdlet and then piping the role assignment returned to the Remove-ManagementRoleAssignment cmdlet.
For more information about regular and delegating role assignments, see Understanding Management Role Assignments .
This procedure uses pipelining. For more information about pipelining, see about_Pipelines .
To remove a role from an assignment policy, use the following syntax.
This example removes the MyVoicemail management role, which enables users to manage their voice mail options, from the Seattle Users assignment policy.
For detailed syntax and parameter information, see Remove-ManagementRoleAssignment .
Additional resources
Subscribe for Practical 365 updates
Please turn off your ad blocker and refresh the page to subscribe.
You may withdraw your consent at any time. Please visit our Privacy Statement for additional information
Exchange Online / Exchange Server
How to report on exchange rbac assignments.

Exchange Server and its cloud sibling are well-known for their robust administrative controls, powered by the RBAC model. Designed with great attention to detail, the RBAC model allows you to granularly control what each admin or user can do, down to the individual cmdlet or even parameter level. While this is extremely useful, because of the flexibility of the model, sometimes it can be a bit hard to keep track of just what permissions have been granted in the organization.
To address this issue, you can use PowerShell to prepare detailed reports of the roles assigned. One such example script is provided by Paul here at Practical 365, and many admins have already made a habit of running it periodically against their environments. The script, however, relies on the AD PowerShell cmdlets and as such cannot be run against Exchange Online, so in this article, we will introduce an updated/alternative approach. We will also discuss some potential improvement areas, and of course, provide you with the actual solution.
A quick refresher on Exchange RBAC
As the name suggests, Exchange’s Role-based Access Control (RBAC) permission model has management roles as its building blocks. A role represents a set of tasks or cmdlets, granted to a role assignee . The role assignee can be a user, a security group or a role group (or a role assignment policy, which we don’t cover here). The link between the role and its assignees is called a management role assignment . Role assignments, in turn, can be regular or delegating. The former is used when you grant someone access to the management tools and features. On the other hand, delegating role assignments don’t grant access to the management tools, but are used to grant someone the ability to assign a given role to others. Lastly, we have the concept of management scopes , which can be used to limit the effect of the role to a subset of the objects in your organization.
While this all might sound very confusing at first, once you understand the basic principles behind the RBAC model, you will certainly appreciate its robustness and customizability. Even more so if you come to compare it with other workloads such as SharePoint or Skype for Business. In Exchange Online, the RBAC model is a bit more limited compared to on-premises versions, but it’s still well ahead of what we get in other parts of the service, including Azure AD.
How to find out who has permissions
Just because some admin functionality exists, it doesn’t mean it’s in use. The same goes for any Exchange management roles. Role assignments effectively represent the “link” between a role and the security principals who have been granted permissions to access the cmdlets, scripts or tools available as part of the role. If no role assignment exists for a given role, then no one in the organization has access to the management tasks it enables. Generally speaking, you can omit such roles from your report. But if you want to be thorough, or are just curious, here’s how to list any (admin) roles that have no corresponding role assignments:
In the above, we are listing all roles, then for each role checking whether any role assignments exist. We are also excluding any “end user” roles, such as the ones that govern different OWA features. The resulting list will return just the “unassigned” roles if any. Again, as no one is currently assigned to said roles, they are not “in use” and you can simply ignore them. The bottom line here is that if you want to get an overview of what permissions are granted in the company at present, the Get-ManagementRoleAssignment cmdlet is your natural starting point.
We now know how to list assignments for a given role. However, this doesn’t completely answer the question of who has been granted access, as roles can be delegated to security groups, or bundled in role groups and role assignment policies. If we want to list the individual users, we have to further “expand” the corresponding object, which is effectively what Paul’s script does for Role Groups. We are trying to address a broader scenario, however, so we need to also account for assignments of type User , SecurityGroup and PartnerLinkedRoleGroup. In turn, where needed we should aim to expand group membership and list individual users.
In the on-premises world, group expansion is easily performed via the AD tools. In Office 365, however, things aren’t that straightforward, and in general, we have to use solutions such as the one described in this article . Luckily, in the case of role assignments, the good folks at Microsoft have given us an easier method, namely the -GetEffectiveUsers switch parameter. What the switch does is to recursively process each nested group and return a list of the individual user entries. Here’s an example:
The first cmdlet lists just the direct assignees to the Journaling role. Three of those entries, namely the “Compliance management” and “Organization management” role groups and the “MESGtop” security group have additional members and even some nested groups. The full list of members is returned when we rerun the cmdlet with the – GetEffectiveUsers switch, one entry per user. Which is practically all we need to generate the report.
Another approach would be to use the Get-ManagementRoleAssignment cmdlet against specific security principal entry. The cmdlet is intelligent enough to not only list direct assignments, but also any assignments corresponding to security or role groups that have the given security principal as a member, including nested groups. However, since the number of such objects in most companies is larger than the number of role assignments, this method might be slower. Just in case, here’s an example:
Preparing the output
Now that we know how to list each individual user and each role they have been assigned, all we need to do is prepare the output. One approach is to just dump all this information into a CSV file, then use Excel to filter/sort it as needed. However, as you can see from the above screenshot, some of the data presented is quite ambiguous as objects are listed by their display name. We can improve the quality of the output by finding the corresponding object and return a unique identifier. Unfortunately, this might not always be possible, but for most scenarios, we should be able to identify the correct object.
The getUPN and getGroup helper function will try to “convert” a given DisplayName to the corresponding object and return a unique identifier for it. Since there can be multiple entries matching a given display name, the functions will call the Get-ManagementRoleAssignment and use the – Role and – RoleAssignee parameters to find out which entry corresponds to the actual role assignment. If they cannot find a match or multiple matches remain even after these additional checks, the display name will be returned as is.
Apart from providing additional information about each assignee, we can also use the native PowerShell capabilities to group the output by user. This might or might not be more convenient, but as mentioned above you can also use tools such as Excel to perform any grouping, sorting and filtering operations. The output returned from the script is sampled below:
For each user, group, or role group object, the object type, and unique identifier are returned (UPN or PrimarySMTPAddress where available, GUID otherwise). Then, a list of the individual Roles assigned to the given security principal is listed, and an indicator of the type of assignment. For objects with multiple roles assigned, we can have multiple values for the assignment type. Because we are grouping results, only unique role entries will be returned, if that’s not what you expect, edit the code on line 161.
Additional parameters
The script features a few additional parameters that govern the output. The first parameter is – IncludeDelegatingAssignments , which signals the script to also return details on any non-default Delegating Role Assignments. By non-default we mean delegating role assignments outside of those assigned to the “Organization Management” role group. If you don’t agree with the logic used here, feel free to adjust the filter on line 79.
The – IncludeRoleGroups parameter will force the script to return entries for “parent” role group assignments in the output. Since we are using the – GetEffectiveUsers parameter, any individual user that’s a direct member of the role group or member of any nested group within it is returned, so you might not want to see the “parent” entry as well. This is the default behavior, but if you do want to see such entries, you can specify the – IncludeRoleGroups parameter when invoking the script. No entries will be returned in the output for any nested groups, just the user objects within them! This is a limitation of using the – GetEffectiveUsers switch, but we plan to present an alternative solution in a future article.
Lastly, the – IncludeUnassignedRoleGroups switch governs whether to return entries for role groups that don’t have any role assignments. As discussed above, any cmdlets included in such role groups are effectively in “no use”, but you might want to include the role groups for completeness. This parameter can only be used when – IncludeRoleGroups is set to $true.
Here’s how the console output will look like when all these parameters are used. In the highlighted entries, you can see an object with a duplicate display name, but thanks to the additional checks performed by the script, a unique identifier is returned. You can also see users and groups with direct role assignments, including delegating ones; role groups with no assignments; “parent” groups.
The output will also be stored in the global variable $ varRoleAssignments so it can be easily reused. Don’t forget that the script will also save the “raw” output to a CSV file!
Download the script from the TechNet Gallery or GitHub , and don’t forget to send us your comments.
About the Author

Vasil Michev
Hi, Could you please test it in your environment and let me know if it works for you ? Regards
Forget this i have achieved with using parameters , but my next question is, the output of the Assignee is with ID instead of username, how can i get this with username ?

what kind of ID? A GUID? Can you do Get-Recipient -Id $Value to see what $Value (the identifier) resolves to?
Hi, this code doesn’t return any output. What could be the reason ? Thanks in advance. regards
No idea. Have you debugged it? The code is PowerShell after all, so you can step through it to discover where problems might lie.
One basic problem I see is that the script in GitHub attempts to connect to Exchange Online via basic auth. Have you tried changing the script so that it uses a simple Connect-ExchangeOnline instead of running the Check-Connectivity function?
Leave a Reply Cancel reply
Latest articles.
Migrate from EWS Application Access Policy to RBAC for Applications
On February 20, Microsoft announced their intention to remove Application Impersonation for EWS from Exchange Online. If you have existing management role assignments, this article explains how to make the transition to RBAC-based assignments.
- Exchange Online
Using Entra ID Support for Passkey Authentication with Microsoft 365
Entra ID supports passkeys as an authentication method. In fact, support is a variation of the existing FIDO2 authentication method using device-bound passkeys managed by the Microsoft Authenticator app. Passkeys are a strong phishing-proof authentication method. The question is whether the current implementation will be considered too complicated by regular users.

Practical Protection: Breaches, Exposure, and You
In this edition of Practical Protection, Paul Robichaux dives into 5 steps you can take to protect yourself, and potentially your organization, from future breaches.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Role assignment policies in Exchange Online
- 15 contributors
A role assignment policy is a collection of one or more end-user roles that enable users to manage their mailbox settings and distribution groups in Exchange Online. End-users roles are part of the role based access control (RBAC) permissions model in Exchange Online. You can assign different role assignment policies to different users to allow or prevent specific self-management features in Exchange Online. For more information, see Role assignment policies .
In Exchange Online, a default role assignment policy named Default Role Assignment Policy is specified by the mailbox plan that's assigned to users when their account is licensed. For more information about mailbox plans, see Mailbox plans in Exchange Online .
User roles and Outlook Web App policies are now available in Exchange admin center.
Role assignment policies are how end-user roles (as opposed to management roles) are assigned to users in Exchange Online. There are several ways you can use role assignment policies to assign permissions to users:
New users :
Change the end-user roles that are assigned to the default role assignment policy.
Create a custom role assignment policy and set it as the default. Note that this method only affects mailboxes that you create without specifying a role assignment policy or assigning a license (the license specifies the mailbox plan, which specifies the role assignment policy).
Specify a custom role assignment policy in the mailbox plan. For more information, see Use Exchange Online PowerShell to modify mailbox plans .
Existing users :
Assign a different license to the user. This will apply the settings of the different mailbox plan, which specifies the role assignment policy to apply.
Manually assign a custom role assignment policy to mailboxes.
The available end-user roles that you can assign to mailbox plans are described in the following table:
* This feature isn't available in all regions or organizations.

What do you need to know before you begin?
Estimated time to complete each procedure: less than 5 minutes.
The procedures in this topic require the Role Management RBAC role in Exchange Online. Typically, you get this permission via membership in the Organization Management role group (the Microsoft 365 or Office 365 Global administrator role). For more information, see Manage role groups in Exchange Online .
To open the Exchange admin center (EAC), see Exchange admin center in Exchange Online . To connect to Exchange Online PowerShell, see Connect to Exchange Online PowerShell .
Changes to permissions take effect after the user logs out and logs in again.
View roles assigned to a role assignment policy
Use the eac to view roles assigned to a role assignment policy.
In the EAC, click Roles > Admin roles . All of the role groups in your organization are listed here.
Select a role group. The details pane shows the Name , Description , and add the Permissions of the role group.
Use Exchange Online PowerShell to view roles assigned to a role assignment policy
To view the roles assigned to a role assignment policy, use the following syntax:
This example returns the roles that are assigned to the policy named Default Role Assignment Policy.
For detailed syntax and parameter information, see Get-ManagementRoleAssignment .
Note : To return a list of all available end-user roles, run the following command:
Add or remove roles from a role assignment policy
Use the eac to add or remove roles from a role assignment policy.
In the policy properties window that opens, do one of the following steps:
To add a role, select the check box next to the role.
To remove a role that's already assigned, clear the check box.
If you select a check box for a role that has child roles, the check boxes for the child roles are also selected. If you clear the check box of the parent role, the check boxes for the child roles are also cleared. You can select a child role by clearing the check box of the parent role and then selecting the individual child role.
When you're finished, click Save .
Use Exchange Online PowerShell to add roles to a role assignment policy
Adding a role to a role assignment policy creates a new role assignment with a unique name that's a combination of the names of the role and the role assignment policy.
To add roles to a role assignment policy, use the following syntax:
This example adds the role MyMailboxDelegation to the role assignment policy named Default Role Assignment Policy.
For detailed syntax and parameter information, see New-ManagementRoleAssignment .
Use Exchange Online PowerShell to remove roles from a role assignment policy
Use the procedure from the Use Exchange Online PowerShell to view roles assigned to a role assignment policy section earlier in this topic to find the name of the role assignment for the role that you want to remove (it's a combination of the names of the role and the role assignment policy).
To remove the role from the role assignment policy, use this syntax:
This example removes the MyDistributionGroups role from the role assignment policy named Default Role Assignment Policy.
For detailed syntax and parameter information, see Remove-ManagementRoleAssignment .
Create role assignment policies
Use the eac to create role assignment policies.
In the EAC, go to Roles > Admin roles and then click Add role group .
In the Add role group window, click Set up the basics section, configure the following settings and click Next :
Name : Enter a unique name for the role group.
Description : Enter an optional description for the role group.
Select the roles that you want to assign to the policy.
In the Add permissions section, select the roles and click Next . Roles define the scope of the tasks that the members assigned to this role group have permission to manage.
In the Assign admins section, select the users to assign to this role group and click Next . They'll have permissions to manage the roles that you assigned.
In the Review role group and finish section, verify all the details, and then click Add role group .
Click Done .
Use Exchange Online PowerShell to create role assignment policies
To create a role assignment policy, use the following syntax:
This example creates a new role assignment policy named Contoso Contractors that include the specified end-user roles.
For detailed syntax and parameter information, see New-RoleAssignmentPolicy .
Modify role assignment policies
You can use the EAC or Exchange PowerShell to Add or remove roles from a role assignment policy .
You can only use Exchange Online PowerShell to specify the default role assignment policy that's applied to new mailboxes that aren't assigned a license or a role assignment policy when they're created.
Otherwise, all you can do in the EAC or Exchange Online PowerShell is modify the name and description of the role assignment policy.
Use Exchange Online PowerShell to specify the default role assignment policy
To specify the default role assignment policy, use the following syntax:
This example configures Contoso Users as the default role assignment policy.
Note : The IsDefault switch is also available on the New-RoleAssignmentPolicy cmdlets.
For detailed syntax and parameter information, see Set-RoleAssignmentPolicy .
Remove role assignment policies
You can't remove the role assignment policy that's currently specified as the default. You first need to specify another role assignment policy as the default before you can delete the policy.
You can't remove a role assignment policy that's assigned to mailboxes. Use the procedures described in the Use Exchange Online PowerShell to modify role assignment policy assignments on mailboxes section to replace the role assignment policy that's assigned to mailboxes.
Use the EAC to remove role assignment policies
In the EAC, go to Roles > Admin roles .
Select the role group and click Delete .
Click Confirm in the confirmation window.
Use Exchange Online PowerShell to remove role assignment policies
To remove a role assignment policy, use the following syntax:
This example removes the role assignment policy named Contoso Managers.
For detailed syntax and parameter information, see Remove-RoleAssignmentPolicy .
View role assignment policy assignments on mailboxes
Use the eac to view role assignment policy assignments on mailboxes.
In the mailbox properties window that opens, click Mailbox features . The role assignment policy is shown in the Role assignment policy field.
Use Exchange Online PowerShell to view role assignment policy assignments on mailboxes
To see the role assignment policy assignment on a specific mailbox, use the following syntax:
This example returns the role assignment policy for the mailbox named Pedro Pizarro.
To return all mailboxes that have a specific role assignment policy assigned, use the following syntax:
This example returns all mailboxes that have the role assignment policy named Contoso Managers assigned.
Modify role assignment policy assignments on mailboxes
A mailbox can have only one role assignment policy assigned. The role assignment policy that you assign to the mailbox will replace the existing role assignment policy that's assigned.
Use the EAC to modify role assignment policy assignments on mailboxes
In the EAC, click Recipients > Mailboxes , and do one of the following steps:
Multiple mailboxes : Select multiple mailboxes of the same type (for example, User ) by selecting a mailbox, holding down the Shift key, and select another mailbox farther down in the list or by holding down the Ctrl key as you select each mailbox. In the details pane (that's now titled Bulk Edit ): click More options > click Update . In the Role Assignment Policy section, select the role assignment policy in the window that appears > click Save .
Use Exchange Online PowerShell to modify role assignment policy assignments on mailboxes
To change the role assignment policy assignment on a specific mailbox, use this syntax:
This example applies the role assignment policy named Contoso Managers to the mailbox named Pedro Pizarro.
To change the assignment for all mailboxes that have a specific role assignment policy assigned, use the following syntax:
This example changes the role assignment policy from Default Role Assignment Policy to Contoso Staff for all mailboxes that currently have Default Role Assignment Policy assigned.
Additional resources
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
How to enforce office 365 custom "role assignment policy" applied default to all new emails to be created?
I have created a RoleAssignmentPolicy called "DisabledForwardingRoleAssignmentPolicy" via Exchange admin center --permissions-- user roles .

I would like to apply "DisabledForwardingRoleAssignmentPolicy" default to all new emails accounts to be created.
In gui of Exchange admin center, there seems to be no way to do this. So I did this by longing to office 365 in powershell.
The command successfully executed. and when I verify it via Get-RoleAssignmentPolicy it says DisabledForwardingRoleAssignmentPolicy is default .
But when I create a new email and when i go to recipients --mailboxes-- select user and mailbox features--- Role assignment policy , still the default policy is applied.

I have to change it manually to DisabledForwardingRoleAssignmentPolicy
What I'm missing here? Please shade a light.
- email-server
- microsoft-office
You need to run "Set-MailboxPlan" cmdlet to change the default role assignment policy to the customize one.
First, run "get-mailboxplan" to confirm which plan your license is used, as below:
Then, run "Set-MailboxPlan" to change the RoleAssignmentPolciy to the customize one:

- You are truly a great resource to serverfault. thanks a lot for your time testing it before posting. I was googling and no correct path was found. It worked. – user879 May 30, 2018 at 5:21
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged email exchange email-server microsoft-office mailbox ..
- The Overflow Blog
- Is GenAI the next dot-com bubble?
- What language should beginning programmers choose?
- Featured on Meta
- New Focus Styles & Updated Styling for Button Groups
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network
Hot Network Questions
- Why protest against the war in Gaza on the campus of Columbia university?
- Why do journals refuse to see substantially revised manuscripts after rejection?
- SHA-3 hash function standard references
- Are there any philosophies related to different structures of organization of information?
- To save a file to the last folder you have used in Finder
- Questioning why LVM for the OS Disks in cloud environments is not recommended
- Can I say "keep your head tipping backwards for 2 minutes" to mean to keep the head still and in a state that it is fixed at a tipping position?
- Is this job a scam or legit?
- More potent caffeine analogs (in silico study)
- Need help with a timeline using Tikz
- Do star fleet officers retain the privileges of their rank if they time travel to other Starfleet vessels?
- Why does the BRK instruction set the B flag?
- How can I restore the grout joint at the bottom of my shower walls?
- Windows Batch Script: how to recursively go through all files except certain file types and folders?
- Latin minimal pairs, distinguished only by the length of the vowel in an unstressed non-last syllable
- Who are the "we" in Colossians 1:27-28?
- Why would two different sized bikes not arrive at the same time starting from rest on the same slope?
- Does this "Ballygullion" anecdote, published as true in a law journal, originally come from a work of fiction?
- Canada visitor visa denied
- Is my simpler proof correct?
- Can you naïvely reduce the dimensionality of a QFT?
- ANOVA vs Kruskal Wallis - Small sample size
- Is Batman's utility belt ever missing something he needs?
- Data Science undergrad degree isn't what I expected to be
Microsoft 365, Teams, Intune, and other Office 365 services. | Blog by Oliver Moazzezi.
Wednesday 17 April 2013
Customizing role assignment policies for multi-tenants in exchange server 2013: gal pictures.
No comments:
Post a Comment
Stefanos Cloud
How to manage Microsoft 365 user role assignments and administrative units
- Role assignments
- Administrative Units
This article provides guidance on how to manage Microsoft 365 user role assignments and administrative units. The article is also available on my podcast and Youtube channel .
View this article as a how-to video on Youtube.
You need to manage existing user roles, create new custom user roles and assign users and groups to existing roles in Microsoft 365 . You need to also manage Microsoft 365 administrative units.
In this how-to article, we will show you how to manage Microsoft 365 user role assignments and administrative units.
Role assignments #
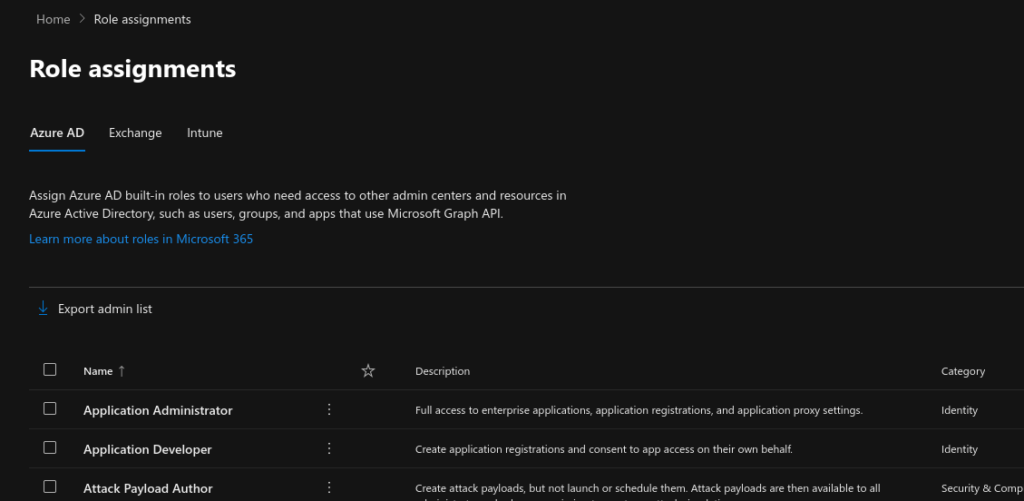
From within the Microsoft 365 Admin Center portal, you can assign Azure AD built-in roles to users who need access to other admin centers and resources in Azure Active Directory, such as users, groups, and apps which use Microsoft Graph API. The following groups of user role assignments can be made from the Admin Center portal.
- Azure AD role assignments
- Exchange Online role assignments
- Intune role assignments
In the next steps, we will show you how to assign the Global Administrator Azure AD role to a user and group. Follow the steps below to assign the Global Administrator role to a user or group.
- Navigate to https://admin.microsoft.com and authenticate as a global admin user.
- On the left pane, expand the "Roles" section and click on "Role assignments". On the main section click on the "Global Administrator" role. On the popup form on the right, you should be able to review the general properties of the role in question. On the permissions tab, the system lists details of the permissions which are assigned with the role in question.
- On the "Assigned" tab, you can assign users or groups to the role in question. Click on "Add Users" and then "Add Groups" to add a user and group respectively to the specific role.
- To run the Azure portal as a specific Azure AD user role, tick on the checkbox next to the role and click "Run As". This will show you the view of the Azure portal as if you had logged in via a user with the role in question.
- To compare permissions of user roles, tick on two or more roles and then click on "Compare Roles". In the next screen, you should see a tabular comparison of the permissions assigned to each of the compared roles. You can also click on "Export comparison" to export the comparison matrix of the selected roles.
In the next steps, we will show you how to assign the Organization Management Exchange Online role to a user and group, as well as how to create a new custom Exchange Online role. Follow the steps below.
- Navigate to the "Exchange" tab under the "Role Assignments" section.
- Click on the "Organization Management" role. On the popup form on the right, you can review the general settings of the role under the "general" tab. Under the "Permissions" tab, you can review in detail the available permissions of the role in question.
- Under the "Assigned" tab, you can assign a user or group to the role in question. Click "Add" and choose the user or group to assign to the role.
- You can also create a custom Exchange Online role by ticking the checkbox next to the role which will be used as the template for the new role. Then click on "Copy role group". This will take you to a wizard to create your new custom role. On the "Set up the basics" page, fill-in the name, description and write scope of the new role and click Next.
- Select the roles to add to the new custom role group. Roles define the scope of the tasks that the members assigned to this role group have permission to manage.
- Select the users to assign to this role group. They'll have permissions to manage the roles that you assigned in the previous step.
- Review your selections and click Finish.
In the next steps, we will show you how to assign Intune roles. Assign Intune roles to specialists who need to view or manage Intune data, devices, or services. These roles can only be assigned to users who have a license that includes Intune. Follow the steps below.
- Under the "Role assignments" section, navigate to the "Intune" tab. If you need to export existing assignments, click on the "Export assignments" button.
- Click on the Intune role you wish to edit assignments of. On the "General tab" you can review the general settings of the role in question. On the "Permissions" tab you can see in detail all permissions of the role in question.
- To assign users to the Intune role, under the "Assigned" tab click on "Add". This will take you to the "Set up the basics" wizard. Fill-in a name and description and click Next.
- Select the security groups that contain the users you want to become admins for the role. Click Next.
- Select a built-in security group like 'All users', or search for and select security groups which contain the users and devices that the Intune role can manage.
- You can optionally add tabs which limit the specific Intune policies, apps and devices that the admins can see. Click "Next".
- Review all your assignment settings and click "Finish".
Administrative Units #
Now we will move on to show you how to create and manage Microsoft 365 Administrative Units. Units let you sub-divide your organization into any unit that you want, and then assign specific administrators that can only manage that unit. For example, you can assign the Helpdesk Administrator role to a regional support specialist, so they can manage users only in that region.
Carry out the following steps:
- Under the "Roles" section, click on "Administrative Units". Click on "Add Unit" to add a new administrative unit.
- Provide a name and Description of the new administrative unit and click "Next". Administrative units let you limit admins to manage users for a specific department, region, or any segment that your organization defines. Start by giving the administrative unit a name and description that will let other admins know its purpose.
- Choose "Add up to 20 users and groups" or "Upload users" if you need to bulk upload a large number of users to be linked to the new administrative unit. If you choose "Add up to 20 users and groups", then click on "Add Users" or "Add Groups" to add the desired users to the administrative unit and click Next. The administrators assigned to this unit will manage the settings for these users and groups. Adding groups doesn't add users to the unit, it lets the assigned admins manage group settings. You can only add up to 20 members individually or you can bulk upload up to 200 users. If you need to add more, you can edit this unit to add them.
- Assign admins to scoped roles. The following roles are the only roles that support administrative units. Authentication Administrator Cloud Device Administrator Groups Administrator Helpdesk Administrator License Administrator Password Administrator SharePoint Administrator Teams Administrator Teams Device Administrator User Administrator.
Select a role and then assign admins to it. The admins that you assign to roles in this step will manage the members of this administrative unit.
- Review your selections and click "Finish". The new administrative unit has been created. You can always edit its properties by clicking on the Administrative Unit name. From that page you can edit the administrative unit's members and role assignments.
- You can also edit the name and description of an administrative unit by ticking the checkbox next to the administrative unit name and clicking on "Edit name and description".
What are your Feelings
Share this article :, how can we help.
Powered by BetterDocs
Allow Users To Manage Distribution Groups Without Creating New Ones
In a previous post we discussed a scenario where users were delegated the capability to create Mail Enabled Contacts in Active Directory using a custom RBAC role. As part of the solution, we enabled the MyDistributionGroups Role. While this may meet the needs of most organisations it does introduce one issue where users who are assigned such a Role Assignment Policy can edit Distribution Groups they own but also create new ones.
This post is based on Exchange 2010. If you would prefer an Exchange 2013 specific post, please view this entry .
Update 20-1-2014 : Corrected PowerShell code to add a missing bracket in $Roles = (Get-RoleAssignmentPolicy -Identity "Default Role Assignment Policy").AssignedRoles
Update 1-6-2015: Link to an Exchange 2013 specific version of this post was added.
How can we solve the challenge of allowing users to managed Distribution Groups that they own, but also prevent them from removing or adding new ones? Well, it’s a similar story to the previous blog – we will create a custom RBAC Role!
One thing that is a little different is that the RBAC configuration for the items related to configuring your own mailbox is stored within a Role Assignment Policy . The same terminology applies but we need to be clear that end-user RBAC is contained within a Role Assignment Policy and administrator RBAC lives in Management Roles.
This scenario calls for having multiple Role Assignment Polices as each will have a different configuration. For example you may envision the following:
- Default Role Assignment Policy – can edit zero Distribution Groups
- DG-Management Role Assignment Policy – can edit Distribution Groups owned by user, cannot create new ones.
- DG-Full-Management Role Assignment Policy – can edit Distribution groups owned by user, and can create new ones.
We will create option #2 in this blog. Option1 is the initial setup with the Default Role Assignment Policy, and Option3 can be done by following the steps in the previous blog to simply enable the MyDistributionGroups Role in the relevant Role Assignment Policy.
Let’s get jiggy with it , and create a new Role Assignment Policy! **
Create New Role Assignment Policy
Let’s create a new Role Assignment Policy called DG-Management . We want to mirror the existing Default Role Assignment Policy, as a mailbox can only be assigned a single Role Assignment policy and we need to ensure that the user can perform all required activities on their mailbox. This can be customised to suit your requirements, in this example we will copy from the Default Role Assignment Policy, but this is not required.
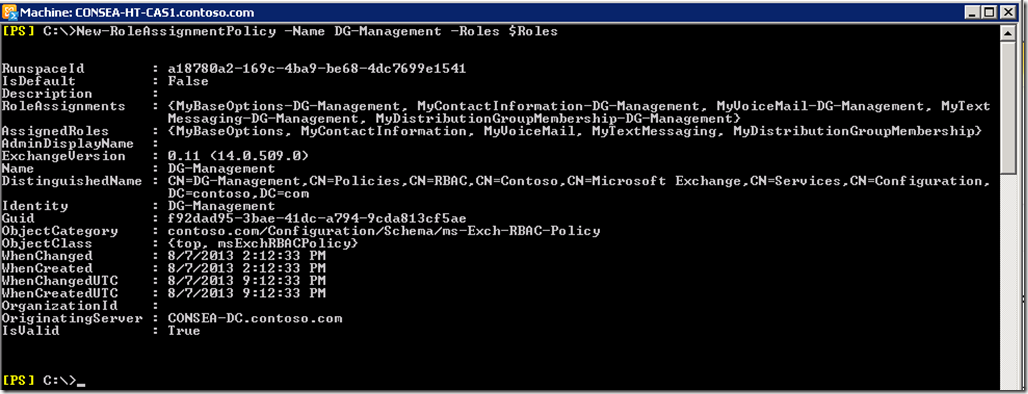
We can write down the roles assigned to the Default Role Assignment Policy and manually add them, or alternatively we can save the Default Role Assignment Policy roles to a variable. We can then provide this variable as the list of roles when the new Role Assignment Policy is created. let’s save the Roles assigned to the variable $Roles.
$Roles = (Get-RoleAssignmentPolicy -Identity "Default Role Assignment Policy").AssignedRoles
$Roles will then contain the following Roles:
MyBaseOptions MyContactInformation MyVoiceMail MyTextMessaging MyDistributionGroupMembership
When creating the new Role Assignment Policy called DG-Management , we provide the $Roles variable which contains the saved roles.
New-RoleAssignmentPolicy –Name DG-Management –Roles $Roles
Create Custom Management Role
All the Management Roles that can be assigned to a Role Assignment Policy are prefixed with “ My ” to indicate that they are for user RBAC. This is a list of the Exchange 2010 roles starting with the prefix “ My ”:
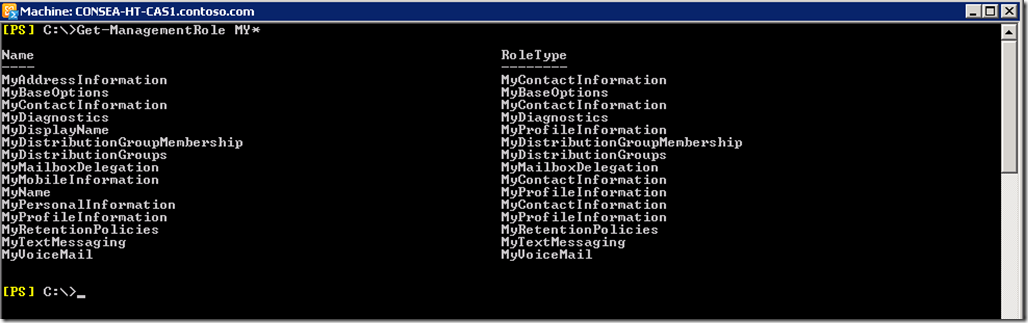
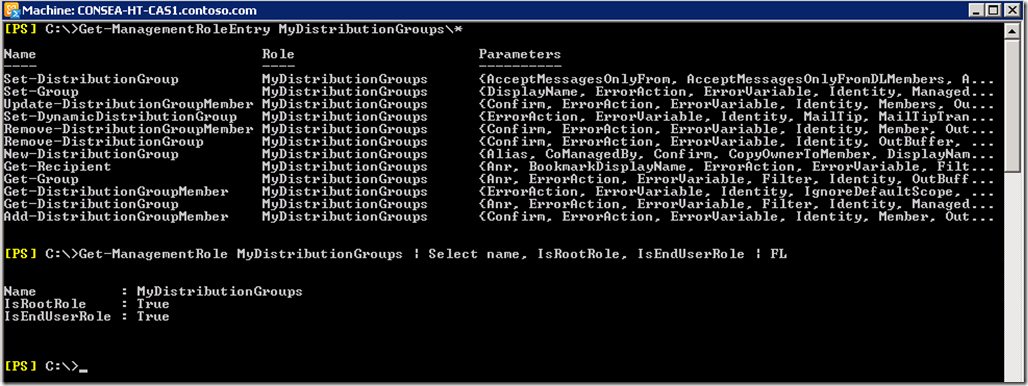
The Management Role Entries for MyDistributionGroups is shown below along with showing that this is a built-in role and is intended for end user purposes.
In order to stop users with this Management Role creating and deleting Distribution Groups, we need to remove the “New-DistributionGroup” and “Remove-DistributionGroup” cmdlets. As before, the built-in RBAC roles are read only so we need to make a writable copy.
New-ManagementRole -Name "Edit-Existing-DG-Only" -Parent MyDistributionGroups
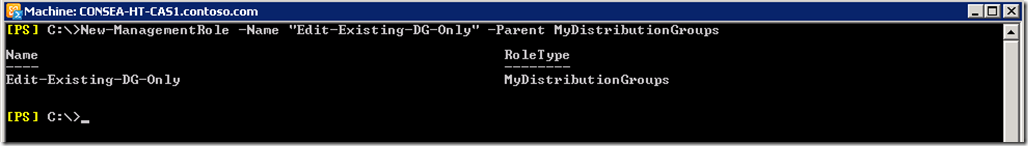
Then removing the new and remove distribution group cmdlets:
Remove-ManagementRoleEntry Edit-Existing-DG-OnlyNew-Distributiongroup
Remove-ManagementRoleEntry Edit-Existing-DG-OnlyRemove-Distributiongroup
Checking to see the current Management Role Entries, note the New and Remove cmdlets are gone:
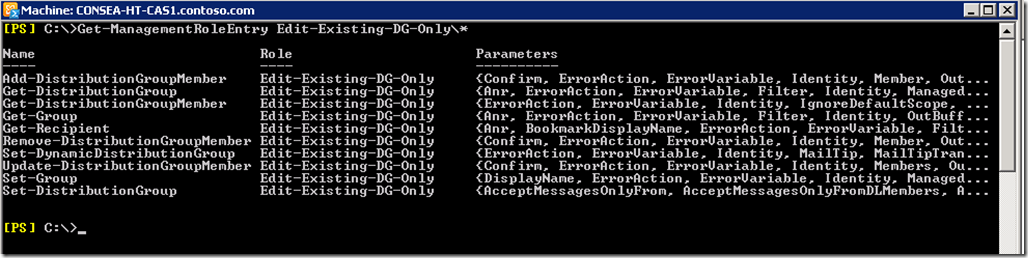
Once happy, will assign this custom Role to our new Role Assignment Policy.
New-ManagementRoleAssignment -Policy "DG-Management" -Role Edit-Existing-DG-Only
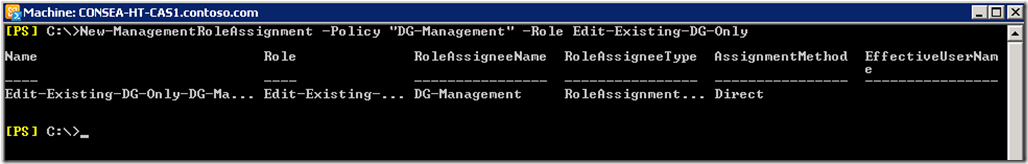
Note that we can do most RBAC work in ECP after Exchange 2010 SP1, though I still prefer PowerShell as that was what I had to learn initially. Old dog, new tricks etc…..
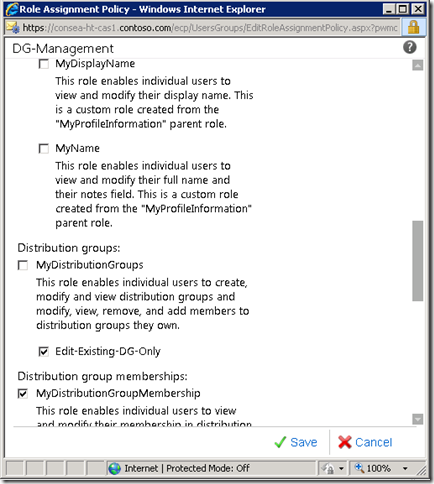
Testing & Validation
In order to test the work we have done, the Role Assignment Policy must be assigned to a mailbox. As mentioned above a mailbox can only have a singe Role Assignment Policy at any given time. You can have multiple Role Assignment Policies, and assign one to a given mailbox. You do not have to explicitly assign a Role Assignment Policy, and this is the default behaviour for a mailbox. If you do not explicitly state which one should be used when creating or moving a mailbox to Exchange 2010, Exchange will use the one marked as default. Note it is not necessarily the one called “Default Role Assignment Policy”; that one is created by default, is the only one by default and is initially marked as default. This can be changed to suit your needs. Let’s say you create a Role Assignment Policy that you want 95% of the users to have as it’s your base standard then you can mark it as the default.
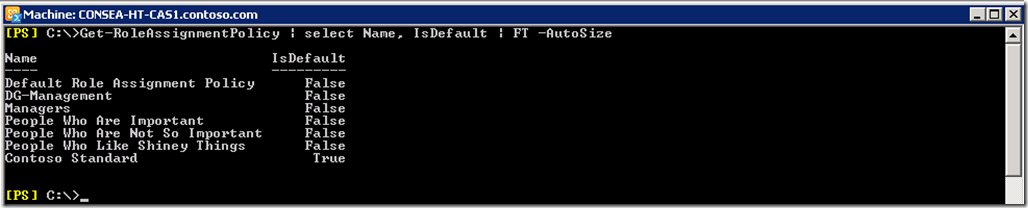
Set-RoleAssignmentPolicy -Identity "Contoso Standard" -IsDefault:$true
Viewing all of the Role Assignment Policies shows Contoso Standard is the default. Mailboxes created will now leverage the Contoso Standard Role Assignment Policy unless explicitly stated otherwise. Mailboxes created prior to this point will continue to use their existing Role Assignment Policy and will not automagically change to this new default policy.
Let’s set our test mailbox (user-20) to explicitly use the DG-Management Role Assignment Policy
Set-Mailbox -Identity user-20 -RoleAssignmentPolicy DG-Management
When user-20 then opens up ECP, they have the following capabilities, note that there is no New or Delete button under “Public Groups That I Own”.
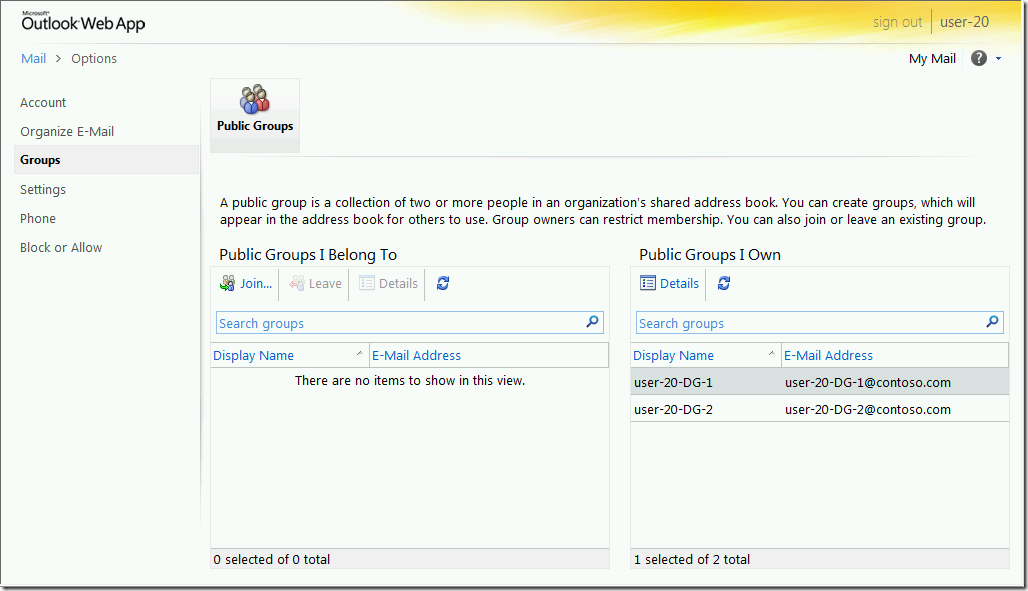
For a Distribution Group to show up, it must have the ManagedBy attribute set. In this test org there are several DGs, but only the ones that user-20 has ManagedBy appear.
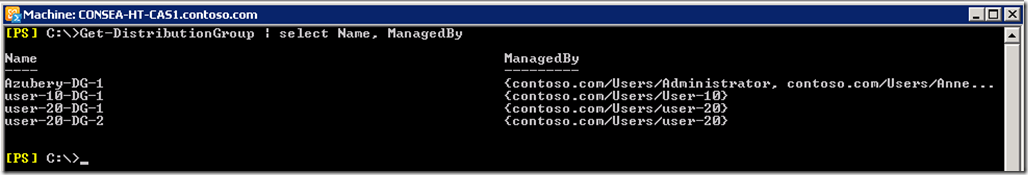
We can see that the basic steps to tune and customise RBAC are very similar to the previous blog on delegating Mail Enabled Contact creation . There are some differences as we are creating a custom Management Role to be used as part of a Role Assignment Policy though all the concepts still apply.
** – Forget the music and stuff Will Smith, where is Independence Day 2 anyway ?!?!?
Rhoderick Milne [MSFT]
One comment.
I had to update the syntax for Remove-ManagementRoleEntry to "Remove-ManagementRoleEntry Edit-Existing-DG-Only\New-Distributiongroup"
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Skip to primary navigation
- Skip to main content
- Skip to primary sidebar
- Skip to secondary sidebar

OpenTechTips
Short Guides for IT Enthusiasts
How to Clone a Role Assignment Policy in Microsoft Exchange
November 21, 2020 - by Zsolt Agoston - last edited on January 30, 2021
This script is for cloning a Role Assignment Policy in Exchange.
For example, if you want to allow certain users to add/remove members to the distribution groups they own, you need to enable the "MyDistributionGroups" option in the role assignment policy that is assigned to the user mailboxes, but you probably don't want to alter the default one.
This case it's simple to clone the default policy, make changes to that cloned version and assign it to only those mailboxes that needs it.
Now you can edit the new policy and assign it as needed with the Set-Mailbox -RoleAssignmentPolicy cmdlet.
Reader Interactions
Comments cancel reply.
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
To provide the best experiences, we and our partners use technologies like cookies to store and/or access device information. Consenting to these technologies will allow us and our partners to process personal data such as browsing behavior or unique IDs on this site and show (non-) personalized ads. Not consenting or withdrawing consent, may adversely affect certain features and functions.
Click below to consent to the above or make granular choices. Your choices will be applied to this site only. You can change your settings at any time, including withdrawing your consent, by using the toggles on the Cookie Policy, or by clicking on the manage consent button at the bottom of the screen.

IMAGES
VIDEO
COMMENTS
For detailed syntax and parameter information, see Set-RoleAssignmentPolicy.. Add a role to an assignment policy Use the EAC to add a role to an assignment policy. In the EAC, navigate to Permissions > User Roles.. Select the assignment policy you want to add one or more roles to, and then click Edit.. Select the check box next to the role or roles you want to add to the assignment policy.
As the name suggests, Exchange's Role-based Access Control (RBAC) permission model has management roles as its building blocks. A role represents a set of tasks or cmdlets, granted to a role assignee. The role assignee can be a user, a security group or a role group (or a role assignment policy, which we don't cover here).
Admins can learn about role assignment policies, and how to view, create, modify, remove, and assign them in Exchange Online. Skip to main content. This browser is no longer supported. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. ... Role assignment policies in Exchange Online ...
The "Default Role Assignment Policy" is assigned to every mailbox and " grants end users the permission to set their options in Outlook on the web and perform other self-administration tasks ". You'll find the policy in the Exchange Admin Center under "Permissions" and "User Roles".
You need to run "Set-MailboxPlan" cmdlet to change the default role assignment policy to the customize one. First, run "get-mailboxplan" to confirm which plan your license is used, as below: Get-MailboxPlan |fl identity,RoleAssignmentPolicy Then, run "Set-MailboxPlan" to change the RoleAssignmentPolciy to the customize one:
Creating a new user role assignment policy. If your organization does decide to limit the self-management permissions of your users in Exchange Online, you have a couple of options. You can either modify the default role assignment policy, or you can create a new role assignment policy. Modifying the default role assignment policy is very easy.
Customizing Role Assignment Policies for multi-tenants in Exchange Server 2013: Gal Pictures When dealing with multi-tenants in Exchange Server 2013 (RTM and CU1) with a Hosting Control Panel that can only feed data into Exchange, rather than taking data back out of it to back-fill the Portal we have to lock down certain elements to only allow ...
Follow the steps below to assign the Global Administrator role to a user or group. Navigate to https://admin.microsoft.com and authenticate as a global admin user. On the left pane, expand the "Roles" section and click on "Role assignments". On the main section click on the "Global Administrator" role.
Step 2: Navigate to the Exchange admin center. Step 3: Go to Permissions > User roles, select the role assignment policy, and then click Edit. Step 4: Select the check box next to the role. Step 5: Click Save
1.What role assignment policy is assigned to all our mailboxes in Office 365. "Default Role Assignment Policy" is assigned to existing and new mailboxes that aren't explicitly assigned a specific role assignment policy when they're created. The policy contains 13 roles for "commonly used permissions" as defined by Microsoft.
In a previous post we discussed a scenario where users were delegated the capability to create Mail Enabled Contacts in Active Directory using a custom RBAC role. As part of the solution, we enabled the MyDistributionGroups Role. While this may meet the needs of most organisations it does introduce one issue where users who are assigned such a Role Assignment Policy can edit Distribution ...
This script is for cloning a Role Assignment Policy in Exchange. For example, if you want to allow certain users to add/remove members to the distribution groups they own, you need to enable the "MyDistributionGroups" option in the role assignment policy that is assigned to the user mailboxes, but you probably don't want to alter the default ...
You can fix it by creating an Admin/Management role assignment (edit: on-prem) granting the same access to the MyDistributionGroups role and then adding all of the affected users in to the ManagementRoleAssignment group. It's a bit clunky for the users (they see all groups in the ECP but can only make changes to their own) but it's the best ...
Hi, wonder if anyone can help. I have a user with 3 'default role assignment policies' set in Office365 under the Exchange admin section (permissions > user roles). There should only be one such policy. This is causing a problem when I setup new users with a mailbox - I see the message below and their mailbox setup never completes. I can't work out how to remove the 2 other policies (we ...