
An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
https://www.nist.gov/itl/smallbusinesscyber/nist-cybersecurity-fundamentals-presentation

Small Business Cybersecurity Corner
Nist cybersecurity fundamentals presentation.
Download the Slides
Managing a small business is always challenging but keeping up with cybersecurity threats can be overwhelming. How do you learn about the latest threats? How do you educate your staff about best practices? NIST has prepared a training presentation (draft) that you can use to self-teach and help your team learn at the same time. Please download the slides so you can use them at your convenience.
Each slide includes speaker’s notes – so you will be able to understand and share the material and find links to resources to learn more. You can go through the materials as quickly or slowly as you need, knowing that the recommendations come from the Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST).
The material is in sections: Cybersecurity Basics; Cybersecurity Threats; Risk Management; Cybersecurity Framework; and Small Business Cybersecurity Resources. You and your team will become familiar with common threats like phishing and ransomware, understand steps you can take every day to prevent falling victim and steps to take to recover should trouble strike.
We welcome your feedback on this draft presentation and will incorporate improvements in the future.

- Last updated April 30, 2020
- In AI Origins & Evolution
10 Popular Cybersecurity Presentations On Slideshare You Should Refer To
- Published on August 12, 2019
- by Ambika Choudhury

Securing networks and protecting data from breaching has become one of the crucial motives in an organisation. Cybercrime has eventually risen with the widespread use of emerging technologies and we have been witnessing data breaches and other hacks for a few years now. In this article, we list down 10 popular presentations on cybersecurity one must read on Slideshare.
(The list is in alphabetical order)
1| Artificial Intelligence And Cybersecurity
This presentation was published in March 2019 by Olivier Busolini, a cybersecurity professional who also works with AI in cybersecurity. This presentation includes a basic introduction to AI, an overview of AI technologies, an overview of machine learning underlying technologies, basics of deep learning, introduction to red and blue AI, emerging usages of blue AI, difficulties faced during developing AI solutions and tips for cybersecurity strategy.
2| Cyber Crime And Security
This powerpoint presentation was published by Lipsita Behera, a software developer and it has gathered more than 350,000 views till now. In this PPT, you can understand the basics of cybersecurity such as how cybersecurity emerged, know about cyber threat evolution, types of cybercrime, how to take preventive measures in order to control the threats, learn various security reasons as well as methods.
3| Cybersecurity
This presentation has got more than one lakh viewers and more than 700 clipping. Here, the author introduces the basics of cybersecurity and what is the actual need of cybersecurity, what are the major security problems, different viruses and worms and its solutions, brief introduction of hackers and measures to prevent hacking, what are malware and steps to stop malware, what are trojan horses and safety measures to avoid trojans, password cracking and securing password, cybersecurity strategy in India and much more.
4| Combating cybersecurity Using Artificial Intelligence
Combating Cybersecurity using Artificial Intelligence was published in January this year by Inderjeet Singh, Director – Strategic Accounts. This presentation discusses the threats with AI and machine learning. Here, you can learn about the advanced behavioural attacks, applications of emerging technologies in cybersecurity, various malicious activities, including the future of AI and machine learning in cybersecurity.
5| Cyber Crime And Security
This powerpoint presentation was published by Aeman Khan, an automation test engineer and it has crossed over 410,000 views till now. Here, the writer discusses the basics of cybersecurity such as its introduction, history, the various categories of cybercrime, its types, how cybersecurity threatens national security, advantages of cybercrime and other safety tips to cybercrimes including cyber law in India.
6| Cybersecurity
This ppt is published by Bijay Bhandari, an engineer and project manager by profession. It has been viewed for over 210,000 times where the author discusses how to take action against cybercrime. You will know about the basics of cybersecurity and cybercrime, what constitutes cyber crimes, protection measures for cybercrime, advantages of cybersecurity and various safety measures.
7| Cyber Crime
This presentation has been viewed for over 294,000 times and it includes a basic introduction to cybercrime. You will get to know about the variants of cybercrime such as phishing, vishing, cyberstalking, cost of cybercrime in India, cyber laws, various ACTs including the preventive measures for such activities.
8| Overview Of Artificial Intelligence In cybersecurity
This presentation, an overview of artificial intelligence in cybersecurity was published in June 2019 by Olivier Busolini, a cybersecurity professional. Here, he talks about artificial imitation augmented intelligence, basic types of AI and machine learning, difficulties to develop AI solutions, challenges in machine learning, AI in cybersecurity, key flaws of cybersecurity, AI risk framework, basic introduction to defensive AI, adversarial AI as well as offensive AI and much more.
9| Security Automation And Machine Learning
The security automation and machine learning ppt is published by Siemplify, a security platform in January this year and has got more than 100 viewers. It includes a basic introduction to cybersecurity and machine learning, types of machine learning techniques, security analysis for machine learning, threats on machine learning, machine learning for prevention, detection, incident response and SOC management.
10| The Role Of Big Data, AI And ML In Cyber Intelligence
The role of big data, AI and ML in cyber intelligence ppt was published by Aladdin Dandis, an information security manager who gives a brief introduction to cyber intelligence, raw threat data and threat intelligence, understanding AI and machine learning drivers, various kinds of cybersecurity options such as phishing, anti-malware, fraud detection, cyber intelligence framework and its challenges.
Access all our open Survey & Awards Nomination forms in one place >>
Ambika Choudhury
Download our mobile app.

CORPORATE TRAINING PROGRAMS ON GENERATIVE AI
Generative ai skilling for enterprises, our customized corporate training program on generative ai provides a unique opportunity to empower, retain, and advance your talent., 3 ways to join our community, telegram group.
Discover special offers, top stories, upcoming events, and more.
Discord Server
Stay Connected with a larger ecosystem of data science and ML Professionals
Subscribe to our Daily newsletter
Get our daily awesome stories & videos in your inbox, recent stories.

Top 10 LMS Platforms for Enterprise AI Training and Development

Father of Computational Theory Wins 2023 Turing Award

TCS Records $900 Million AI and GenAI Pipeline This Quarter
Generative AI has significantly enhanced TCS’ service offerings across cloud platforms, security, and enterprise solutions.

Elon Musk’s xAI Unveils Grok-1.5 Vision, Beats OpenAI’s GPT-4V

Ola Krutrim Makes History with In-House Cloud Infrastructure, Skips AWS and Azure

Eventbrite’s Data Privacy Manager, Aditi Sharma on ‘Encrypt Data, not Empathy’

NaMo App Introduces AI Chatbot NaMo AI, Offers Quick Answers to Government Schemes
Users can inquire about initiatives like “Har Ghar Jal” and get insights.

Data Centres’ Lean Towards Nuclear-Powered Future to Combat Energy Needs

Meta Releases AI on WhatsApp, Looks Like Perplexity AI
Our mission is to bring about better-informed and more conscious decisions about technology through authoritative, influential, and trustworthy journalism., shape the future of ai.
© Analytics India Magazine Pvt Ltd & AIM Media House LLC 2024
- Terms of use
- Privacy Policy
Subscribe to Our Newsletter
The Belamy, our weekly Newsletter is a rage. Just enter your email below.
What To Include In Your Cybersecurity Board Of Directors Presentation
Executive Reporting

Most Boards today know that cybersecurity is a critical issue that simply cannot be overlooked — which means many Boards today receive regular briefings on the topic. If you’re a new CIO or CISO (or your organization has just begun this practice) it’s absolutely critical that you establish credibility when you present to your Board of Directors. If you’ve been asked to present and you’ve never briefed a Board of Directors on cybersecurity before, your questions are going to be far different than they would be if you had seven or eight presentations under your belt. So below, we’ve detailed some of the topics you should include in your cybersecurity Board of Directors presentations — for both first timers and seasoned presenters.
First-Time Cybersecurity Board Of Directors Presentation
If this is your first presentation to the Board, your goal should be to provide a very high-level overview. You’ll want to give a short background on cybersecurity, what it means, and why you (and your department) should be concerned. It’s extremely important to speak in a language that the Board can understand — which means cutting out any technical jargon . Instead, talk in terms of risk management, stock price, and bottom line.
Below are some of the topics you may want to cover in your first presentation:
- A high-level overview of different threat actors.
- How you generally approach cybersecurity: Who is in charge, how you work together, what the components are, etc.
- Risks to your cybersecurity environment (i.e., the things you’re concerned about).
- The type of data you think is most critical or sensitive.
- The types of critical operations that could be impacted by a cyber incident.
- Examples of cyber incidents that have occurred in other organizations in our sector.
- Examples of other cyber incidents that have impacted organizations more broadly that you should be aware of.
- How you think the Board members should be involved and where the Board comes into play.
- What you anticipate presenting to the Board in the future.
- The programs you have in place for cybersecurity from a strategy and technology approach.
- How you train your employees on cybersecurity.
- The cybersecurity policies you have in place today and those you’d still like to integrate.
- How you use your systems and how you know what data to collect on.
- Some of the key external threats, insider threats, and third-party risks you believe you face.
Related: Boards need more information about cybersecurity than ever before. Can you present it effectively?
Ongoing cybersecurity board of directors presentations.
Now that you’ve completed your first cybersecurity presentation to the Board of Directors, your goal should be to continuously educate the Board on critical issues. This means your focus for these presentations should shift, as the Board should be briefed on the effectiveness of the risk management tactics you’re employing. In other words, the Board should know where you are succeeding, how you are succeeding, and any areas that need strategic improvement.
Here are some topics you should focus on in your ongoing presentations to the Board:
- Technology you’ve purchased and integrated—with a focus on what it is doing for the organization.
- Technology you want to purchase and why you want to purchase it.
- “Are we ISO-27001-compliant?”
- “Do we have a vendor risk management program?”
- “Do we have any outstanding high-risk findings open from our last audit or assessment?”
- “What percentage of the NIST framework are we implementing?”
- “How quickly can we remove employee network access?”
- “How quickly can we (or our vendors) identify and respond to incidents?”
- “What percentage of our users click on spear-phishing training emails?”
- “How did we compare to our peers across certain time spans?”
- Audit & Compliance Metrics
- Operational Effectiveness Metrics
Knowing the right point to brief the Board on is critical — but there’s much more to an effective cybersecurity Board of Directors presentation. Download our ebook to learn how to take a risk-based approach to cybersecurity reporting.
A Practical Guide to Risk-Based Cybersecurity Reporting

Learn how to revolutionize the reporting process at every level of your organization.
Get the Weekly Cybersecurity Newsletter
Home Collections Technology Cyber security
Cyber Security Presentation Templates
Master the art of secure digital communication with slide egg's free cyber security powerpoint templates and google slides. our 100% editable designs make complex security concepts easy to understand. ideal for it professionals, educators, and students. make cyber security conversations clear and bring digital safety to the forefront with style.
- Cyber Security Awareness: It's about enlightening people, especially employees, about the lurking digital dangers and the best preventive measures.
- Computer Security: This is the individual shield for our devices, ensuring they're free from harm and theft.
- Network Security: This is akin to a digital moat around our castles, barring unwanted entities.
- Information Security: It’s the code of silence, making sure our secrets, or data, remain undisclosed.
- Risk Management: It's the strategy room, analyzing where the vulnerabilities lie and how to tackle them.
- Cyber Threat Intelligence: This is the watchtower, gathering info on potential threats to stay ahead of them.
- Strategies and Regulations: The rulebook every organization should have, outlining defense mechanisms against cyber evils.
- Eye-catching Designs: Our templates, rich in colors and nodes, ensure your presentation stands out, making every cyber security PPT memorable.
- Crystal Clear Messaging: Our infographics act like a translator, turning complex jargon into easily graspable visuals.
- Flexibility: Our cyber security templates are like clay - mold them as per your needs, be it for a seminar or a business proposal.
- User-Centric: Easy customization ensures your unique touch is added effortlessly.
- Affordable Excellence: Quality often comes with a tariff, but we break the norm with many free-to-download premium templates.
We're here to help you!
What is cyber security.
The technique of protecting networks, servers, computers, mobile devices, electronic systems, and data from hostile attacks is known as cyber security.
What are Cyber Security Presentation templates?
Cyber Security Presentation templates are the best presentation slides to visually describe the importance of the cyber security process to the people. These templates can effectively showcase the vital functions of cyber attacks in detail with their unique designs, themes, images, and backgrounds.
Where can we use these Cyber Security Presentation Slides?
You can use these Cyber Security Presentation slides for presentations and slide shows at companies, schools, colleges, and institutions. These templates can detail the complete process of cyber security in a minute.
How can I make Cyber Security Slides in a presentation?
Making a PowerPoint presentation template is frequently a straightforward process. If you are a beginner or new to the PowerPoint designing process, you must choose an easy-to-use Cyber Security template. For more PowerPoint designing ideas, visit our PowerPoint tips and tricks pages.
Who can use Cyber Security Templates?
Cyber Security professionals can use these templates to showcase the cyber attack details like security gaps, attackers, destroyed data, changes, attempts to access the systems, and so on. It is one of the ideal tools to depict the data perfectly to the viewers in an informative way.
Where can I find free Presentation Templates?
You can browse plenty of websites to download free Presentation Slides to choose from. But you might face difficulty in choosing the best template for your presentation. Also, you will face some discomfort regarding the templates' designs, colors, themes, and icons. So better to look for a loyal PowerPoint provider like Slide Egg.
Why do we need to use Cyber Security PowerPoint Slides?
The cyber security templates can quickly demonstrate the information you wish to deliver regarding cyber-attacks. Also, these templates will help save your time and designing process. These templates will have the visual themes for a perfect demonstration, so they will add an effective look to your data.
- Data Science
- Quantum Computing

- Miscellaneous

A Comprehensive Guide on RTMP Streaming
Blockchain booms, risks loom: the ai rescue mission in smart contract auditing, developing incident response plans for insider threats, weis wave: revolutionizing market analysis, top cybersecurity presentations.

Today, organizations are affected by cyberattacks like malware, phishing, man-in-the-middle attack, SQL injection attacks, and more. Due to such attacks, organizations’ systems, programs, and networks are damaged. Therefore, to avoid cyberattacks, organizations follow specific cybersecurity methods. If you are looking for an overview of cybersecurity and its practices, this article will help you with some of the best cybersecurity presentations.
Top Presentations on Cybersecurity
Listed below are some essential and primarily used cybersecurity presentations.
- Artificial Intelligence and Cybersecurity
Olivier Busolini published Artificial Intelligence and Cybersecurity presentation in March 2019, he is a cybersecurity professional working with AI in cybersecurity. This presentation provides a basic introduction to AI, an overview of AI technologies, machine learning technologies, basics of deep learning, difficulties faced during building AI solutions, and tips for cybersecurity strategy.
This presentation also includes an introduction to red and blue AI technologies and a list of organizations that are using AI to follow cybersecurity practices to secure their information. Therefore, with AI and Cybersecurity presentations, learners can get a brief idea of cybersecurity solutions.
Link to the PPT: Artificial Intelligence and Cybersecurity
2. AI and the impact on Cybersecurity
Published in October 2019, the AI and impact on Cybersecurity presentation by Graham Mann cover the explanation of what AI is and its impact on cybersecurity. The presentation includes content like the importance of AI, cloud computing, machine learning algorithms, and blockchain. It also consists of statistics on cyberattacks in 2018, cyber targets in 2019, and AI-assisted cyberattacks.
With the AI and its impact on Cybersecurity presentation, you will know the potential of AI technology and its impact on cyberattacks and cybersecurity practices. This presentation also briefs you about AI and the laws associated with it.
Link to the PPT: AI and the impact on Cybersecurity
3. How can AI help in Cybersecurity
This presentation was published by Priyanshu Ratnakar, who is the Founder, Director, and CEO of Protocol X, in March 2021. It provides a brief idea of AI in cybersecurity and is suitable for every person who wants to learn how AI can help in cybersecurity. The presentation consists of topics like the basics of AI, machine learning and deep learning, AI in real-life, the effects of AI in cybersecurity, and how hackers use AI technology to attack computer systems.
Link to the PPT: How AI can help in Cybersecurity
4. IT fundamentals of Cybersecurity
Tanishk Jharwal, a Student at Swami Keshvanand Institute of Technology Management and Gramothan (SKIT) published the IT fundamentals of Cybersecurity presentation. This presentation highlights cybersecurity in four parts:
- Introduction to cybersecurity tools and cyberattacks
- Cybersecurity roles, processes, and operating system security
- Network security and database
- Cybersecurity compliance, framework, and system administration
The presentation also includes contents such as categories of cybercrime, a list of security tools, safety tips for cybercrime, and the advantages of cybersecurity. It explains cyber crimes like hacking, phishing, spam emails, denial of service, spyware, adware, malware, and ransomware.
Link to the PPT: IT fundamentals on Cybersecurity
5. Cybersecurity 101
Wiam Younes, Carnegie Mellon University, published the cybersecurity 101 presentation. The PPT includes an introduction to cybersecurity, security threats and risks in computer systems, security measures in cybersecurity, safely managing your passwords, managing your email accounts, and securing your computer systems.
The Cybersecurity 101 presentation teaches you to protect the data you are handling and provides guidelines for protecting yourself from cyber attacks. It offers different policies and procedures for protecting your network and system.
With this cybersecurity ppt, you can identify cybercrime-related theft, including credit card fraud, financial identity theft, government identity theft, mortgage fraud, and license plate number identity theft. This ppt also guides you through different practices to protect yourself from identity theft.
Link to the PPT: Cybersecurity 101
6. Cybersecurity Introduction
The Cybersecurity Introduction is a presentation from the students of Mohawk College in Hamilton, Canada. This presentation provides you with the basics of cybersecurity, its definitions, principles, and about cyber threats. It also guides you through different sources of cyber threats, classifications of cyber threats, unstructured cyber threats, structured cyber threats, and highly structured cyber threats.
With this presentation, you can also learn about cyber attacks, their types, and the impacts of cyber threats. This presentation will also give you a brief idea about malicious code and its types. The Cybersecurity Introduction PPT highlights the vulnerabilities of your computer system in cybercrime.
Link to the PPT: Cybersecurity Introduction
7. Study of Emerging Trends and Challenges of Cybersecurity
Published in January 2022, the Study of Emerging Trends and Challenges of Cybersecurity presentation by Ritvik Kumar provides an overview of emerging trends and challenges in cybersecurity. The presentation consists of content such as the basics of cybersecurity and cybercrime, trends in changing cybersecurity, cybersecurity techniques, cyber ethics, and the roles of social media in cybersecurity.
This presentation also highlights the cybersecurity incidents reported to Cyber999 in Malaysia between January 2012 and 2013. Cyber999 is a cybersecurity center operated by Malaysia Computer Emergency Response Team (MyCERT) to report incidents related to cyberbullying or cyberattacks.
Link to the PPT: Study of Emerging Trends and Challenges of Cybersecurity
8. Cyberattacks and IT Security in 2025
The Cyberattacks and IT Security in 2025 presentation is drafted by RadarServices, the European market leader for managed security services. RadarServices interviewed designated IT security experts in Europe and Asia and shared their views in this presentation concerning the development of cyberattacks and security technologies till 2025.
The presentation provides an overview of the questions like the type of cyberattacks that will be estimated in 2025, what are the biggest challenges for IT security technologies today and which will be there in 2025, and in which areas of IT security organizations need to invest to be viable in 2025.
The presentation highlights the dangers of cyberattacks that will likely happen in 2025. It also briefs you on security technologies companies need to use to prevent cyberattacks’ dangers.
Link to the PPT: Cyberattacks and It Security in 2025
9. Cybersecurity in Society
The Cybersecurity in Society presentation by Rubal Agarwal was published in August 2018. This presentation provides an overview of cybercrime, its types, and its stages. It also provides you with the importance of cybersecurity and safety tips for cybercrime.
He also presented cyber crimes such as hacking, child pornography, phishing, denial of service attacks, cyber terrorism, virus spreading, and software piracy. It highlighted the statistics of the number of cybercrime cases in India in January 2015. The presentation also consists of the effects of cybercrime in India. The PPT also includes the top 10 security assessment tools to identify vulnerabilities in cyber security.
Link to the PPT: Cybersecurity in Society
10. Cybersecurity
The Cybersecurity presentation was published in October 2021 by Vinod Sencha. The presentation contains the importance of cybersecurity, cybersecurity domains, the CIA (Confidentiality, Integrity, and Availability) Triad, and threats and vulnerabilities in cybersecurity. It also highlights the concepts like phishing and its statics and examples, malware, viruses, bombs, Trojans, Worms, email worms, denial of service attacks, and ransomware.
Vinod Sencha focuses on the Covid-19 cyber threats in the presentation. He also briefs you about society’s types of cybercriminals, virus detection, cybersecurity and privacy, and footprinting.
Link to the PPT: Cybersecurity
Subscribe to our newsletter
Subscribe and never miss out on such trending AI-related articles.
Join our WhatsApp Channel and Discord Server to be a part of an engaging community.

RELATED ARTICLES
Enhancing efficiency: the role of data storage in ai systems, from insight to impact: the power of data expanding your business, the ultimate guide to scrape websites for data using web scraping tools, leave a reply cancel reply.
Save my name, email, and website in this browser for the next time I comment.
Most Popular

Analytics Drift strives to keep you updated with the latest technologies such as Artificial Intelligence, Data Science, Machine Learning, and Deep Learning. We are on a mission to build the largest data science community in the world by serving you with engaging content on our platform.
Contact us: [email protected]
Copyright © 2024 Analytics Drift Private Limited.
Got any suggestions?
We want to hear from you! Send us a message and help improve Slidesgo
Top searches
Trending searches

solar eclipse
25 templates

12 templates

north korea

7 templates

21 templates

48 templates
Security Presentation templates
Safety is one of the most important things in a community and there are so many people involved in different security bodies to assure that there is no danger around. if you want to speak about security in every way and form possible, we are glad to inform you that you are absolutely safe using these google slides themes & powerpoint templates.
Cyber Security Business Plan
The world is getting increasingly digital. While that’s a boost to connectivity, it comes with risks, especially to online security. Use this free template to introduce your cyber security company’s business plan and objectives!

Premium template
Unlock this template and gain unlimited access
Workplace Safety in Business
In the business world, it's essential to create a safe and secure work environment to protect employees and prevent accidents and injuries that can cause irreparable damage to workers and the company's reputation. In other words, safety first! If there are any doubts about this topic, make sure to clear...

Cybersecurity Infographics
Use these new infographics to explain all about cybersecurity, one of the main aspects that businesses should take care of in today’s world. Compare items, describe concepts, show steps in a process… Just pick one of the designs—ranging from flat and linear to isometric—and go for it!

Digital Citizenship
Download the Digital Citizenship presentation for PowerPoint or Google Slides and start impressing your audience with a creative and original design. Slidesgo templates like this one here offer the possibility to convey a concept, idea or topic in a clear, concise and visual way, by using different graphic resources. You...

Stop Cyber Terrorism Campaign
A campaign against cyber terrorism? Yes, please! Use this slide deck to present everything you've been planning out: a cyber security software, online safety awareness and data protection solution, and detail exactly what funds you have allocated and how you’ve planned your advertising. This template’s design is very cyber-oriented and...

Workplace Radiation Safety
Download the Workplace Radiation Safety presentation for PowerPoint or Google Slides. The world of business encompasses a lot of things! From reports to customer profiles, from brainstorming sessions to sales—there's always something to do or something to analyze. This customizable design, available for Google Slides and PowerPoint, is what you...

Personal Protective Equipment (PPE) at Work
In many workplaces, personal protective equipment (PPE) is crucial to ensure the safety of employees and prevent any accidents or injuries on the job. Safety comes first! So, if a company has hired you to give a speech on PPE, including what it is, why it's essential, and how it...

Health & Safety Meeting
Safety should always come first and foremost, no matter what the topic is about. If you have a good set of recommendations and indications for your next meeting and you want everybody to pay attention to your speech, this template will make your presentation unique.

Career Technical Subject for Middle School - 6th Grade: Law, Public Safety, & Security
Give your students a bit of information about how the society they live on is structured and protected. Grab their attention with this creative template full of illustrations of judges, police officers, firemen… and maybe you wake up a passion in them! Year 6 is an optimal time for showing...

Safety Rules in Company
Do you dread workplace safety rules reviews and your bored audience who doesn’t pay attention because they’ve heard it all a hundred times before? You’ll be happy to hear that those days are over! This cute, lovingly designed Google Slides and PowerPoint template make you employees smile and pay attention...

Civil Engineering Safety
Download the Civil Engineering Safety presentation for PowerPoint or Google Slides. The world of business encompasses a lot of things! From reports to customer profiles, from brainstorming sessions to sales—there's always something to do or something to analyze. This customizable design, available for Google Slides and PowerPoint, is what you...

Health and Safety Workshop
Feeling overwhelmed about organizing a health and safety workshop? Don't worry, we've got you covered! With our creative template, you'll have all the tools you need to make your next workshop a huge success. Not only does it come fully loaded with interesting illustrations that are directly related to the...


Safety and Emergency Preparedness - Health - 8th Grade
Download the Safety and Emergency Preparedness - Health - 8th Grade presentation for PowerPoint or Google Slides. If you’re looking for a way to motivate and engage students who are undergoing significant physical, social, and emotional development, then you can’t go wrong with an educational template designed for Middle School...

Cybersecurity Agency
We use computers every day—at home, at work, almost anywhere. You need to have your data safe and secure, so if your agency offers cybersecurity services, you can promote them with this template. It catches so much attention thanks to its neon colors and its futuristic appearance. Don't forget to...

Computer Security Day
We've been using computers every day for years. Even our cell phones are like mini-computers (do we actually use them to make calls?). Even some members of the Slidesgo team are believed to be computers! No, we're just that good, but even us have to make sure our data is...

Security in Cyberspace: Protecting your Data and Privacy
Download the Security in Cyberspace: Protecting your Data and Privacy presentation for PowerPoint or Google Slides. The world of business encompasses a lot of things! From reports to customer profiles, from brainstorming sessions to sales—there's always something to do or something to analyze. This customizable design, available for Google Slides...

Traffic and Road Safety
When it comes to traffic and road safety, we all have a responsibility to do our part. That's why we're excited to present our Google Slides and PPT template that makes speaking about this topic both informative and entertaining. From eye-catching graphics to creative charts, our template is designed to...

Digital Scam Awareness Newsletter
No way! You’re telling us that you have been awarded a prize for being the 10,000th visitor of a website? And you only need to send them a picture of your card to cash it? Unbelievable. We have a better gift for you: this template about digital scamming. Use this...
- Page 1 of 9
New! Make quick presentations with AI
Slidesgo AI presentation maker puts the power of design and creativity in your hands, so you can effortlessly craft stunning slideshows in minutes.

Register for free and start editing online
- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World

How to present security to the board
You’ve been called up to “that room.” are you ready.

“We’re taking this before the Board.”
While that might be OK to hear for the CEO, but for anyone else short of the CFO, being invited to present to the Board of Directors can be a scary—even “career-defining” moment. Add to the mix, the usually-non-revenue-focused topic of “Security,” and end-of-year reviews might be even more stressful than usual.
Part of the DNA of any CEO is in how well he or she can deliver quarterly reports (good and bad) to a Board of Directors, with the usual flair of just enough excitement to keep everybody upstairs interested, all the while keeping them at a safe distance from day-to-day operations. But communicating news of a “Security” bent to the Board on a regular basis, and ahead of an event actually being reported, can be something beyond cathartic to those holding the purse strings. It could actually have a direct impact on how effective (and successful) the CSO and his/her team can be in attaining a host of credibility points in the organization, including such attributes as increased control over operational development, defining policy and increased budgets for those “special projects” no one ever seems to understand but “those security people .”
[ RELATED: Tips on how to communicate with the board ]
From a historical perspective, “Security” has usually fallen between the margins of IT and Infrastructure, with a line item mentioned on the annual budget. That was until such things as IoT attacks, DDoS and the rise of malware moved from the back pages of the trade magazines to the headlines of the national news.
With the emergence of the “Chief Security Officer” as a relatively new trend in the C-suite (and usually a hybrid role occupied by an IT leader, and often still reporting into the CFO or other C-level), many CSOs understand the virtual bloodlines that flow data throughout the infrastructure, but may still find it a challenge to translate “risk” for thoseupstairs.
When preparing that key presentation, CSOs might consider integrating the following 10 elements to help manage that all-important, ever-worrisome matter of presenting “Security” in a Board setting.:
- Remember that your priorities are not theirs
- Be the thermostat and not the thermometer
- “Headlines, Deadlines and Market-share”
- Explain what you plan to do
- Be precise and concise
- Tie your data to primary business objectives
- Be sure your information/needs are in alignment with your CEO
- Explain where you are vs where you want to be
- Justify cause and effect in basic terms (“Why should this be our direction?”)
- Know when you’ve said enough (and what not to say)
Lately, as I have traveled around the country, the topic of “presenting security to the Board” has become more prevalent in discussions with executives. Out of respect for the weight and efficacy of this subject, we’ll spend the next several posts exploring how to make the best use of this important meeting.
Part 1: Managing expectations
Preconceptions rule the day
Executives have different presumptions based on their unique work experiences, and their perceptions of how security should be addressed and managed will be fundamentally directed by their levels of exposure vs their level of accountability throughout their work histories, as well as by the advice they may or may not be getting from their peers.
The Board brings the same level of preconceptions—also based on their respective (and collective) experiences. Be sure you are managing your own expectations before you begin managing those of others, according to Lauren Still at TheGrindstone.com . “It is in your best interests to take responsibility for understanding in detail what the priorities are and what will be considered a success,” Still writes.
Where all things security are concerned, talking to a Board requires a clear path and providing simple-to-follow plans of action, based on two key factors: Assets (defining and agreeing on what they are), and access (who can get to them, how, where and why).
You say “tomato,” I say “salsa”
One of the first things that can cripple a senior presentation between practice experts (like tech-savvy CSOs) and business leaders (like principal shareholders), is when the language doesn’t align. When preparing for the trip upstairs, be sure everybody is using common terminology to describe the same things.
For example, when describing terms like “malware” and “exploits,” it might be a good idea to define how your organization looks at each, and how you classify levels of urgency around malicious activities. In a conversation, you might start by defining how your organization defines a secure enterprise, and that your risk scenarios “are actively looking at key points where the greatest compromises would impact shareholder value.”
A KISS goes a long way
The old axiom “Keep It Short and Simple” is a good one to keep in mind when presenting facts to the board. Remember that your priorities are not theirs (they’re about profitability and risk appetite, while CSOs are about protecting assets and risk tolerance). And perhaps more important, when you get that call to head up to the suites, avoid the use of the technical jargon that surrounds our industry, and keep acronyms and abbreviations to a minimum.
That said, however, shouldn’t detract CSOs from not at least giving it the old college try: If asked, for example, how you classify and prioritize your resources, explaining to the board that you are addressing industry-defined “Top 20” attack scenarios to establish your baseline, is a good way of keeping the language friendly, simple and relevant.
The thermostat or the thermometer?
Just because the suits cost a little more doesn’t mean that the Board members aren’t malleable to a little suggestive control. While the Chair is the pace-setter for board meetings, the tone of your presentation would best be served by you defining its tenor, rather than relying on others in the room to do so.
It’s often easy to fall into the trap of spreading FUD in a room of unsuspecting-but-inquiring minds, leaving your CEO to pick up the pieces and switch into “Why didn’t you tell us it was this bad” damage-control mode. However security execs being called to bear witness of the goings-on may consider something a little more palatable: “We believe the rising risks associated with the exchange of online banking accounts within the financial sector of our business is an indicator that we need to focus our efforts on better tuning of our controls, which reduce our latency to responding to real incidents.”
Planning prevents panic
For most C-levels, direct engagement with the Board is probably the highest level of time premium to have to manage, given the tremendous amount of impact they can have on the organization, and the limited amount of time anyone other than the CEO and CFO have with them. Moreover, the Board is usually comprised of people who are not directly tied to the same sector of business as those who maintain the day-to-day operations within the organization, so understanding the business of “where we’re going” is Job #1 for anyone who is presenting to them. Here are three more key elements to infuse into your planning when preparing your board-level presentation:
- Give them a road map. Tell them something that is relevant to their desire to understand what it is you’re going to do, what you’ve already done, and what you’re currently doing, all with one concern in mind: protecting their bottom line.
- Be precise and concise. The Board doesn’t want to see 25 slides on how your firewall settings are defending against the latest multi-threaded polymorphic attack. They are, however, interested in your insight into the latest attack trends as they may relate to (and impact) the organization’s assets or infrastructure.
- Don’t scare anybody. When Boards are confused they lose confidence (in a variety of things, including their decision to ask you to visit them, and their CEO who recommended it!). While that may sound harsh, according to HP CEO Meg Whitman , but more board members are becoming aware of security-related issues. “Staying out of the weeds” is still a wise decision when discussing sensitive topics.
What happens next?
In the next installment we’ll look at ways of responding to that Magic Question—that two-edged sword that every executive should be prepared to respond to and embrace (good and bad): “What do you need from the Board?”
Related content
Top it security certifications for critical infrastructure — by sector, back to school, part 2: no whaling allowed, what i learned about risk on my summer vacation, keep the change: 9 steps to adapting to it security, from our editors straight to your inbox.

U.S. Navy Veteran Drew Williams has a core philosophy about life and work: "Keep busy, stay engaged, and always be productive." Whether as a writer, video producer, lecturer or educator, Drew has been involved in information risk management since the mid-80s. He has developed and published Information Security standards and guidelines.
During the late 1990s, Drew contributed to re-tooling security policies for some of the largest financial institutions in the world, and worked on early adoption of GRC standards and frameworks (SOX, ITIL, ISO27799, CObIT). An original contributor to the HIPAA Security Policy (1995-1996), Drew wrote one of the early security policy guides, "HIPAA Code Blue."
As former product manager for what was the world's top Host Intrusion Detection System (AXENT/Intruder Alert), Drew also contributed to IT security initiatives (IETF / NIST), and worked with MITRE to build the Common Vulnerabilities Enumeration (CVE) framework. Drew served on the President's Council on Critical Infrastructure Security (precursor to DHS), and worked on the NIST's "Common Criteria" directives.
Drew co-authored some of the industry’s first Incident Response & Information Security Risk Assessment Services while head of the SWAT Team at AXENT/Symantec (1997-2002), and from 2006 to 2011, Drew hosted Asia's "Hacker Halted" security symposium.
As founder of Condition Zebra (2011) Drew developed information security readiness programs & mission-critical risk assessments for ministries of defense throughout Asia. He also co-developed post-graduate programs on cybersecurity at Utah Valley University and Southern Utah University, the latter where he also serves as a member of the faculty in the Graduate Program.
Drew also initiated the first "Gold" funding opportunities for the annual Black Hat Briefings in Las Vegas in 2000. A former speaker at CSI/FBI and N+i events during the 1990s-2000's, Drew is also a member of the “Founder’s Circle” at the annual RSA Security Conference, and has been a contributing source in broadcast media, including MSNBC, CNN, and NPR, and has been featured in USA Today, The Washington Post and publications throughout the US and Europe.
The opinions expressed in this blog are those of Drew Williams and do not necessarily represent those of IDG Communications, Inc., its parent, subsidiary or affiliated companies.
Most popular authors

Show me more
Attackers exploit critical zero-day flaw in palo alto networks firewalls.

CISA orders US government agencies to check email systems for signs of Russian compromise

CISA opens its malware analysis and threat hunting tool for public use

CSO Executive Sessions: Geopolitical tensions in the South China Sea - why the private sector should care

CSO Executive Sessions: 2024 International Women's Day special

CSO Executive Sessions: Former convicted hacker Hieu Minh Ngo on blindspots in data protection

LockBit feud with law enforcement feels like a TV drama

Sponsored Links
- Tomorrow’s cybersecurity success starts with next-level innovation today. Join the discussion now to sharpen your focus on risk and resilience.
This is a potential security issue, you are being redirected to https://csrc.nist.gov .
You have JavaScript disabled. This site requires JavaScript to be enabled for complete site functionality.
An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock Locked padlock icon ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
New security analysis for UOV-based signature candidates with small public key size
Description.
Among candidates for the NIST PQC additional call for digital signatures, there exist seven UOV-based multivariate schemes. Further, four UOV-based candidates, MAYO, QR-UOV, VOX, and SNOVA, achieve small public key size compared with the plain UOV. This work gives a new security analysis for these UOV variants with small public keys. Our main contributions are the following two points: First, we show that the rectangular MinRank attack originally proposed on the Rainbow scheme by Beullens is applicable to MAYO, QR-UOV, and VOX. Second, we explain the construction of SNOVA from a different point of view from the original papers, and reconsider its security analysis. Through our analysis, we show that all parameters of VOX and some parameters of SNOVA submitted in the additional call do not satisfy the claimed security levels.
Presented at
5th PQC Standardization Conference (2024) [in-person]
Event Details
Fifth PQC Standardization Conference
Related Topics
Security and Privacy: post-quantum cryptography

IT Security
Mar 30, 2019
1.12k likes | 1.33k Views
IT Security. Julie Schmitz James Mote Jason Tice . Agenda. Overview of basic IT security Human Resources Command-St. Louis Inside Financing Recommendations and Best Practices Closing and questions. IT Security Defined.
Share Presentation
- army reserve personnel center
- verifies sec
- worm reproduces
- sec specialist civilian gs-13
- harmless software upgrades

Presentation Transcript
IT Security Julie Schmitz James Mote Jason Tice
Agenda • Overview of basic IT security • Human Resources Command-St. Louis • Inside Financing • Recommendations and Best Practices • Closing and questions
IT Security Defined • “Broadly speaking, security is keeping anyone from doing things you do not want them to do to, with, or from your computers or any peripherals” -William R. Cheswick
IT Security Overview • Intruders - hackers and crackers • Insiders – fraud case at Financing • Criminals • Online Scam artists • Terrorists
IT Security Overview • Hacker • Person who enjoys exploring the details of programmable systems and how to stretch their capabilities • Hackers tend to view themselves as very knowledgeable computer programmers, sometimes to the point of arrogance • True hacker will look for weaknesses in a system and publish it Source: FBI Cyber Task Force
IT Security Overview • Cracker • One who breaks security on a target computer system • The term was coined by hackers around 1985 in defense against the journalistic misuse of the term “hacker” • Tend to never disclose their findings Source: FBI Cyber Task Force
Hackers or Crackers?
How does a Hacker Effect You? • Michael Buen and Onel de Guzman • Both are suspected of writing the “I Love You” virus • David L. Smith • Melissa virus author • Released March 26, 1999 • Caused an estimated $80 million in damages Source: FBI Cyber Task Force
IT Security at your Office • Social Engineering • Denial of service attacks (DoS) • E-mail bombs • Password cracking • Web spoofs • Trojan, worm, virus attacks • Antivirus tools Source: FBI Cyber Task Force
Social Engineering • A con game played by computer literate criminals • Works because people are the weakest link in any security system Source: FBI Cyber Task Force
Denial of Service • Prevents users from using a computer service. • A type of DoS attack involves continually sending phony authentication messages to a targeted server, keeping it constantly busy and locking out legitimate users • Ping attacks • DDoS attacks • Uses multiple computers to coordinate DoS attacks Source: FBI Cyber Task Force
Email Bombs • A type of denial of service attack • Email bombs involve sending enormous amounts of email to a particular user, in effect, shutting down the email system • Many spammers fall victim to this type of attack • No need to manually send email; downloadable programs will do it for you Source: FBI Cyber Task Force
Password Cracking • Involves repeatedly trying common passwords against an account in order to log into a computer system • Freely available “cracking” programs facilitate this process Source: FBI Cyber Task Force
Web Spoofing • “faking the origin” • The attacker creates a false or shadow copy of a reputable web site; all network traffic between the victim’s browser and the shadow page are sent through the attacker’s machine • Allows the attacker to acquire information such as passwords, credit card numbers, and account numbers Source: FBI Cyber Task Force
What Should Have Been Displayed
What was Displayed
Trojan, Worm, and Virus • A Trojan program does not propagate itself from one computer to another • A Worm reproduces ITSELF over a network • A Virus, like its human counterpart, looks for ways to infect other systems or “replicate” itself (i.e., e-mail) Source: FBI Cyber Task Force
Trojans • Trojans are malicious files masquerading as harmless software upgrades, programs, help files, screen savers, pornography, etc. • When the user opens file, the Trojan horse runs in the background and can cause damage to the computer system (hard drive damage, total access, username and password) Source: FBI Cyber Task Force
TrojanControl
Virus • A program that replicates without being asked to • Copies itself to other computers or disks • Huge threat to companies Source: FBI Cyber Task Force
Antivirus Tools • Any hardware or software designed to stop viruses, eliminate viruses, and/or recover data affected by viruses • AV tools refer to software systems deployed at the desktop or on the server to eliminate viruses, worms, trojans, and some malicious applets • Should be used as part of a security policy Source: FBI Cyber Task Force
After the Incident • Identify means to avoid another attack • Download latest patches • Repair compromised systems • Re-educate users • Run anti-virus software • Stay alert for signs the intruder is still in your system • Log traffic data Source: FBI Cyber Task Force
Security Budget
The Facts on IT Security Budgets • 62 percent of technology officers feel no pressure to increase spending this year • 40 percent of their budgets will go toward preventing existing machinery from breaking • Systems security tends to go unfixed until proven broken • A simple firewall has become the ultimate security commodity • Don’t use ROI to configure IT security budget Source: FBI Cyber Task Force
Source: Federal Bureau of Investigation / Computer Security Institute – http://www.gocsi.com - viewed 11/4/2004
I.T. SECURITY BRIEF- HUMAN RESOURCES COMMAND ST. LOUIS
Human Resources CommandSt. Louis Historical Timeline • First established in 1944 at 4300 Goodfellow • First known as the Demobilized Personnel Records Branch after WWII • In 1956, moved to its present location, 9700 Page • In 1971, Reserve Components Personnel Center at Ft. Benjamin Harrison merged with St. Louis • In 1985, Army Reserve Personnel Center (ARPERCEN) was formed. • In 2003, organization was renamed to Human Resources Command (HRC) Source: https://www.2xcitizen.usar.army.mil/2xhome.asp - viewed 11/1/2004
Human Resources Command (HRC) St. Louis Overview • Supports or conducts the Human Resources Life • Cycle for over 1.5 million customers • Workforce comprised of over 65% civilians, 30% • Active Guard-Reserve soldiers, 5% Active • Component soldiers • Of the military workforce, most officers are Majors • (O-4) & most non-commissioned officers are • Sergeants First Class (E-7s) • 65-acre facility located off Page Avenue • Total of Nine Directorates Source: https://www.2xcitizen.usar.army.mil/2xhome.asp - viewed 11/1/2004
Human Resources Command (HRC) Mission Statement • To provide the highest quality human resources life cycle management in the functional areas of structure, acquisition, distribution, development, deployment, compensation, sustainment and transition for all Army Reserve Soldiers, resulting in a trained and ready force in support of the national military strategy. • To provide human resource services to our retired reserve and veterans. Source: https://www.2xcitizen.usar.army.mil/2xhome.asp - viewed 11/1/2004
Information Assurance Office Information Assurance Manager (Rank: Major) IANCO (Rank: MSG) Assistant IAM (Rank: CPT) Civilian (GS-12) Information Tech & Sec Specialist Civilian(GS-13) Deputy IAM Civilian (GS-11) Information Tech & Sec Specialist Civilian (GS-11) Information Tech & Sec Specialist Source: Information Assurance Office, Human Resources Command, St. Louis
Information Assurance Manager Duties Major: Responsible for Overall IT Security Master Sergeant: Verifies Security Clearances; Trng; Account Requests Captain: Drafts & Submits Policy GS-13: Updates Patches & ACERT Compliance GS-12: System Security Authorization Agreement; Networthiness Certification GS-11: Investigates Computer forensics; Backup for updates & patches GS-11: Backup for Computer forensics; Trng; Account Req.; Verifies Sec. Clear. Source: Information Assurance Office, Human Resources Command, St. Louis
Information Assurance Defined • The protection of systems and information in storage, processing, or transit from unauthorized access or modification; denial of service to unauthorized users; or the provision of service to authorized users • Also includes those measures necessary to detect, document, and counter such threats • This regulation designates IA as the security discipline that encompasses COMSEC, INFOSEC, and control of compromising emanations Source: Army Regulation (AR) 25-2
Information Assurance Organization Chief Information Officer U.S. Army Reserve Command Atlanta, Georgia Information Assurance Officers- 11 Regional Support Commands Information Assurance Officer- Human Resources Command-St. Louis Source: Information Assurance Office, Human Resources Command, St. Louis
In Order to Gain System Access • All Military must have a Security Clearance • Some civilians must have Security Clearance • Other civilians must have at least a National Agency Check (NAC) • All employees must submit a request for system access Source: Information Assurance Office, Human Resources Command, St. Louis
Common End User Problems • Pornography • Running Businesses • Unauthorized use of illegal • software • Sharing of logons/passwords Source: Information Assurance Office, Human Resources Command, St. Louis
What Happens If YouGet Locked Out? • Go to your local Information Mgmt • personnel assigned to serve your • directorate Source: Information Assurance Office, Human Resources Command, St. Louis
Main Concerns of IT Security • Information Security Training • Purchasing automation equipment • without authorization • Computer left on 24/7 • Having a qualified Information • Assurance Manager that is strict • Knowledge of the system Source: Information Assurance Office, Human Resources Command, St. Louis, MO; Information Assurance Officer, 63rd Regional Readiness Command, Los Alamitos, California
Anti-Virus Activity STOPPED AT GATEWAY 45,000 IN APRIL STOPPED AT DESKTOP Source: Information Assurance Office, Human Resources Command, St. Louis
Probes and ScansAgainst Network 135,000 YTD Source: Information Assurance Office, Human Resources Command, St. Louis
Computer Security Model • Bell-LaPadula Model • Developed by the US Army in the 1970’s • Provides framework for handling data of different classifications • Known as “multilevel security system” • One of the earliest and most famous computer security models Source: Information Assurance Office, Human Resources Command, St. Louis; http://infoeng.ee.ic.ac.uk/~malikz/surprise2001/spc99e/article2 - viewed 11/6/2004
Information Unable to Obtain • IT Security Budget • Business Policy Procedures • Outsource IT providers information Source: Information Assurance Office, Human Resources Command, St. Louis
Security challenges at Financing from theCIO’s perspective
Financing Background Info • Financing is one of the largest domestic providers of inventory floor financing for several different industrial channels. • Recent focus to use IT to reduce business costs by processing transactions online. • IT operates 5 different customer facing applications handling in excess of 4 billion dollars in transactions monthly. Source: Interview and personal comments from Financing’s CIO – October 2004
Case Study Research Method • Interviewed CIO to gain their different perspectives on IT security and business. • Interview lasted approximately 2 hours and consisted of 15 questions. • Subsequent discussion based on what CIO said were issues of highest concern. Source: Interview and personal comments from Financing’s CIO – October 2004
Most Pressing Security Concerns • Eliminating bad user practices • Measures to prevent security breeches • Ability to quickly recover from security failures / breeches • Impact of compliance with SOX regulations Source: Interview and personal comments from Financing’s CIO – October 2004
Security Specifics • No specific line item budget amount. • Security costs are encompassed in other budget items, such as system development & testing, data center operations, etc. • No dedicated resources focusing solely on security. • Security related activities fall under responsibility of existing IT staff. Source: Interview and personal comments from Financing’s CIO – October 2004
Security Challenges:End User Security “Security is a 50/50 proposition. A system can be perfectly secure; however, if users don’t properly use the provided security features, then there might as well be no security at all.” -Anonymous
End User Security:Typical Financing User • Non-technology savvy office clerks and book keepers. • No on-site IT support to maintain individual system security. • Many dealers have Broadband access without firewall protection. Source: Interview and personal comments from Financing’s CIO – October 2004
End User Security:Typical Financing User • Non-technology savvy office clerks and book keepers. • No on-site IT support to maintain individual system security. • Many dealers have Broadband access without firewall protection. • What is so risky about this??? Source: Interview and personal comments from Financing’s CIO – October 2004
End User Security:Typical Financing User (2) • Known problems with Spyware and viruses. • Account reps reported seeing multiple users post their username and password in plain view in their offices. Source: Interview and personal comments from Financing’s CIO – October 2004
- More by User

IT Security 2004
Escalating and Evolving Requirements. Regulations and guidance are changing at an increasing rate.Federal Information Security Management Act (FISMA) --- Dec 2002NIST SP 800-64 - Security Considerations in the Information System Development Life Cycle---- October 2003 SP 800-60 Guide for Mapping
311 views • 11 slides

IT Security. CS5493(74293). IT Security. Q: Why do you need security? A: To protect assets. What are assets?. Any item that has value: People Intellectual property Physical property Data Services Reputation Assets are the things you want to protect. The SA and Assets. People
272 views • 16 slides

IT Security Fundamentals
IT Security Fundamentals. Cybersecurity primer for Individuals. About Community IT. Advancing mission through the effective use of technology. 100% Employee Owned. Presenters. Andy Weaver IT Manager Land Trust Alliance. Matthew Eshleman CTO Community IT. Agenda.
595 views • 44 slides

IT Security. Tony Brett IT Systems Manager Corpus Christi College OxCERT [email protected]. Excuses Policy E-mail Machine Security Physical Security File Security Viruses (inc. E-mail+Hoax) Public machines OS Security Network Security Student connections
495 views • 34 slides

IT Security Readings
IT Security Readings. A summary of Management's Role in Information Security in a Cyber Economy and The Myth of Secure Computing . An Important Question. Who in an organization is responsible for security?. The primary message. Who in an organization is responsible for security?
404 views • 26 slides

IT Security. Learning Path March 2013. IT Security Learning Path. IT Security Beginner. IT Security Intermediate. IT Security Expert. Vendor Specific (Microsoft). Vendor Specific (Cisco). CCNA Security (IINS ). MCSA Windows Server 2012 (Exam 70-410) )-412 ). CompTIA Cloud
254 views • 8 slides
IT Security. Presented by: Trisha Craig and Don Elsner Principal Auditors – IT Audit Duke University. Agenda. Stakeholders What is “Internal Audit” Office of Internal Audits Information Technology Audit Audit Process and IT Audits IT Controls
451 views • 15 slides

IT Security Assurance
IT Security Assurance. Management of Network and User Behavior Budi Rahardjo INDOCISC - ID-CERT [email protected] - [email protected] http://budi.insan.co.id. Holistic approach. PEOPLE. awareness, skill. PROCESS. security as part of business process. implementation. TECHNOLOGY.
259 views • 12 slides

Enterprise IT Security
Enterprise IT Security. What you need to know Presented By Vipul Shah Director, PC Solutions Limited. Objective. Raise awareness that IT Security is an important business issue, deserves the attention of the organisational leadership AND
378 views • 25 slides

IT Security MUST
IT Security MUST. Support to ”The Business” IT Security people MUST understand ”The Business” and ”The Business need” to be able to manage IT Security. IT Security Management. Final decisions about IT Security must be taken by ”The Business Expert” (”The Management”)
638 views • 53 slides

IT security Redding
Are you searching for best IT Support Company in Redding? We are leading IT services and IT Security Company. Call us now on (800) 310-2739 or visit our website for more details. https://www.apex.com
150 views • 7 slides

IT security management
Our vital security service features are designed to keep you safe, so that you can stop worrying and get back to focusing on your business goals. Call us now on (225) 706-8414 for IT Security Management services in Baton Rouge. https://www.puryear-it.com/security-management
161 views • 10 slides

It Security Partnership Program | IT Security Risk Management
The partnership program allows you to custom tailor a security suit of services to best compliment your existing team! Allow us to work with you in identifying the risk facing the organization through an annual assessment, manage and implement remediation activities and provide continuous monitoring through a periodic technical testing program. Visit us -https://itsecurityriskmanager.com/partnership-program/
127 views • 11 slides

IT security companies
We are authorized to provide IT Services. iTology OK is the largest and most extensive service networks provider company across the USA for the technology services for various IT, Telecom, and Consumer Electronics products. You have a choice to avail of our services by visiting our website.
103 views • 9 slides

IT Security | IT Audit | IT Security Audit | IT security audit Checklist | 1222 Questions
In depth and exhaustive ISO 27001 Checklist covers compliance requirements on IT Security. The checklist Contains downloadable file of 4 Excel Sheets having 1222 checklist Questions, 9 dynamic Analytical Graphs, complete list of Clauses, and list of 114 Information Security Controls, 35 control objectives, and 14 domains. To obtain the Checklist click/copy the URL link below- https://www.isocertificationtrainingcourse.org/online-store/ISO-27001-Checklist-ISO-27001-Audit-Checklist-ISO-27001-Compliance-checklist-c28241136
234 views • 15 slides

Gronau Itcloud Computing provide consulting offerings and statistics era products that make a contribution to having safer and greener organizational environments.
106 views • 8 slides

NDSU IT Security
NDSU IT Security. Theresa Semmens Chief Information Technology Security Officer Jeff Gimbel Senior Security Analyst. NDSU Physical Infrastructure. Open Network External facing network 79 subnets Open to Internet Internal facing network 79 subnets
366 views • 36 slides

Information technology security aims at guarding networks, data, computers and programs used in an organisation or by individuals from inadvertent and illicit access, damage or change. As progress continues to be made in information and technology, creating new programs, applications and data networks, IT security has become an important aspect of many organisations since the opportunities for abuse through hacking, computer viruses and other related incidences continue to pose a threat. <a href="https://superbessay.com/articles/lab-report-writing/">https://superbessay.com</a>
71 views • 3 slides

IT Computer Security
IT Computer Security. www.kait.ca. Why Security Is Important. Keeps data and equipment functioning Lack of security can expose confidential information and reduce network resources Can degrade performance of a network
231 views • 17 slides

IT Security. Threats: A threat is anything that can cause harm. Countermeasures: A countermeasure is any step you take to ward off a threat – to protect yourself, your data, or your computer from harm. Threats to Users.
255 views • 21 slides

SECURITY in IT
SECURITY in IT. ~Shikhar Agarwal. DEFINITION. Computer security is a branch of computer science that addresses enforcement of 'secure' behavior on the operation of computers.
429 views • 40 slides

Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
- Cyber Security
Business PPT
Digital Marketing
- Digital Transformation
Human Resources
Product Management
- Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories

Download Technology PowerPoint Template for Presentation and IT PPT Slides
- Sub Categories
- 5G Technology
- Agile and Scrum
- Big Data Analytics
- Cloud Computing
- Cryptocurrency
- Data Analytics
- Green Energy
- Internet Of Things
- IT Certification
- Machine Learning
- Microprocessors
- Nanotechnology
- Robotic Process Automation
- Software Testing
- Technology Project Management
- Technology Quality Assurance
- Technology Stack
- Virtualization

Introduction to Artificial Intelligence is for the mid level managers giving information about what is AI, AI levels, types of AI, where AI is used. You can also know the difference between AI vs Machine learning vs Deep learning to understand expert system in a better way for business growth.

Enthrall your audience with this ChatGPT IT Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising seventy two slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.

This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of seventy slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color,text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Cyber Security It Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the eighty one slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

Enthrall your audience with this Cloud Security IT Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising eighty nine slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Prompt Engineering For Effective Interaction With AI Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of one hundred one slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.

Enthrall your audience with this Blockchain Technology IT Powerpoint Powerpoint Presentation. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising seventy two slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Virtual And Augmented Reality IT Powerpoint Powerpoint Presentation is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the eighty one slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

Deliver an informational PPT on various topics by using this Hyperautomation IT Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with ninty three slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.

Deliver an informational PPT on various topics by using this Recommender Systems IT Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with ninty seven slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Machine Augmented Intelligence IT powerpoint presentation slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the sixty two slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

EduDecks are professionally-created comprehensive decks that provide complete coverage of the subject under discussion. These are also innovatively-designed for a powerful learning experience and maximum retention

This complete deck is oriented to make sure you do not lag in your presentations. Our creatively crafted slides come with apt research and planning. This exclusive deck with twelve slides is here to help you to strategize, plan, analyse, or segment the topic with clear understanding and apprehension. Utilize ready to use presentation slides on Digital Transformation Digital Organization Analytics Digital Technology Strategy Business with all sorts of editable templates, charts and graphs, overviews, analysis templates. It is usable for marking important decisions and covering critical issues. Display and present all possible kinds of underlying nuances, progress factors for an all inclusive presentation for the teams. This presentation deck can be used by all professionals, managers, individuals, internal external teams involved in any company organization.

Presenting project scoping PowerPoint presentation slides. Consisting of total of 31 slides. This business scoping PPT complete deck comprises of professional templates with thoroughly researched content. Each template is well crafted and designed by our PowerPoint experts. Our designers have included all the necessary PowerPoint layouts in this deck. From icons to graphs, this PPT deck has it all. The best part is that these templates are easily customizable. Just click the download button shown below. Edit the colour, text, font size, add or delete the content as per the requirement. Download this deck now and engage your audience with this ready-made presentation.

This complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Building Digital Strategy Roadmap For Digital Transformation Complete Deck and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of thirty seven slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.

Presenting, digital revolution PowerPoint presentation slides. Providing a complete set on digital revolution, high quality and completely editable. Accessible both in standard and widescreen view. Light to transform into JPEG or PDF document. Downloadable PPT design to include data and share. Possible in high-quality resolution display. Fully cooperative with google slides. Useful for business people, researchers, analysts, marketers, etc. Add or remove text as per the business demand. Editing benefits available to customize as per your preference.

Presenting digital products features PPT slide templates PPT slide. This PPT is widely applicable by a team of managers and business analysts who foresee the business in light of change. It has impressive picture quality with high resolution. 100 percent editable slide design. There is freedom to execute the changes in color, font, text and more as per one’s personal choice. Ease of personalization with your company name and logo. It is compatible with a wide variety of format options and also harmonious with a set of software options, available both online and offline.

Presenting artificial intelligence presentation slides. This deck comprises of total of 50 slides. Each slide includes professional visuals with an appropriate content. These templates have been designed keeping the customers requirement in mind. This complete presentation covers all the design elements such as layout, diagrams, icons, and more. This deck has been crafted after an extensive research. You can easily customize each template. Edit the color, text, icon, and font size as per your requirement. Easy to download. Compatible with all screen types and monitors. Supports Google Slides. Premium Customer Support available.
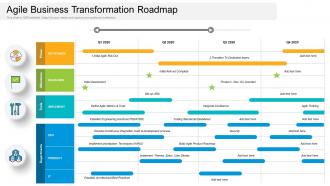
Presenting this set of slides with name Agile Business Transformation Roadmap. The topics discussed in these slides are Departments, Tools, Milestones, Phase. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Our topic specific Digital Transformation Powerpoint Presentation Slides deck contains twenty four slides to formulate the topic with a sound understanding. This PPT deck is what you can bank upon. With diverse and professional slides at your side, worry the least for a powerpack presentation. A range of editable and ready to use slides with all sorts of relevant charts and graphs, overviews, topics subtopics templates, and analysis templates makes it all the more worth. This deck displays creative and professional looking slides of all sorts. Whether you are a member of an assigned team or a designated official on the look out for impacting slides, it caters to every professional field.

Presenting our project management steps and process PowerPoint presentation slide. This PPT layout holds seventy four slides and each slide is accessible in standard as well as wide-screen formats. It is completely editable as per your requirements and preferences as well. You can use it with Microsoft Office, Google slides and many other presentation software.

If you download this PPT all you have to do is just erase the already written details and insert what is useful and required. Since these slides can be fully modified you can effortlessly change the font size, font color and font style of the information. Any kind of data, diagram, shape, and graphical illustration can be added or deleted as per the requirements of the presentation. The slideshow can be either saved in PDF or JPG format. This template is also Google Slides’ friendly. So hit the download button and impress everyone around you.

Presenting our Artificial Intelligence Machine Learning Deep Learning PPT PowerPoint Presentation Slide Templates. This is a completely adaptable PPT slide that allows you to add images, charts, icons, tables, and animation effects according to your requirements. Create and edit your text in this 100% customizable slide. You can change the orientation of any element in your presentation according to your liking. The slide is available in both 4:3 and 16:9 aspect ratios. This PPT presentation is also compatible with Google Slides.

Ready to use PowerPoint sample assist you in saving both your time and effort. Luxury to add or remove content in the design. Transmute the PPT layout with industry information i.e. banner and icon. Flexible as can be adapted in JPEG or PDF documents. Text and font can be easily reformed as the presentation need. Presentation template design shown in both standard and widescreen slide
Right to edit the PowerPoint design according to the corporate need. Attractively crafted presentation template with remarkable picture quality. Presentation slide compliant with Google slides. Precise and easy to comprehend information on PPT layout. Wide screen projection does not affect the output quality. PPT layout can be taken with different nodes and stages.

This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Project Management Playbook Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of fifty five slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
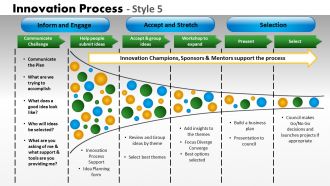
Presenting innovation process style 5 PowerPoint presentation slides. This PPT slide offers you plenty of space to put in titles and subtitles. High resolution based presentation layout, does not change the image even after resizing. This presentation is fully compatible with Google slides. Quick downloading speed and simple editing options in color text and fonts. PPT can easily be changed into JPEG and PDF applications. This diagram has been designed for entrepreneurs, corporate and business managers. Easy to use, edit and you can design attractive slides within few minutes.

This complete deck is oriented to make sure you do not lag in your presentations. Our creatively crafted slides come with apt research and planning. This exclusive deck with twenty slides is here to help you to strategize, plan, analyze, or segment the topic with clear understanding and apprehension. Utilize ready to use presentation slides on Data Analytics Powerpoint Presentation Slides with all sorts of editable templates, charts and graphs, overviews, analysis templates. The presentation is readily available in both 4:3 and 16:9 aspect ratio. Alter the colors, fonts, font size, and font types of the template as per the requirements. It can be changed into formats like PDF, JPG, and PNG. It is usable for marking important decisions and covering critical issues. This presentation deck can be used by all professionals, managers, individuals, internal-external teams involved in any company organization.

This PPT deck displays thirt two slides with in depth research. Our topic oriented Six Building Blocks Of Digital Transformation Powerpoint Presentation Slides deck is a helpful tool to plan, prepare, document and analyse the topic with a clear approach. We provide a ready to use deck with all sorts of relevant topics subtopics templates, charts and graphs, overviews, analysis templates. Outline all the important aspects without any hassle. It showcases of all kind of editable templates infographs for an inclusive and comprehensive Six Building Blocks Of Digital Transformation Powerpoint Presentation Slides. Professionals, managers, individual and team involved in any company organization from any field can use them as per requirement.

Presenting this set of slides with name - Artificial Intelligence For Digital Transformation Powerpoint Presentation Slides. This PPT deck displays eighteen slides with in-depth research. This template is compatible with Google Slides, which makes it accessible at once. Can be converted into various formats like PDF, JPG, and PNG. The slide is easily available in both 4:3 and 16:9 aspect ratio. You can change the colors, fonts, font size, and font types of the template as per the business requirements.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Zero Trust Architecture ZTA Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the eighty seven slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

Presenting Project Team PowerPoint Presentation Slides. This PowerPoint presentation includes set of 38 professionally designed slides. This complete deck 100% editable templates you can edit text font as per your convenience. Users can easily download the presentation slides in widescreen and standard format. These templates are compatible with Google Slides too. The user can use the PowerPoint presentation in PDF or JPG format.
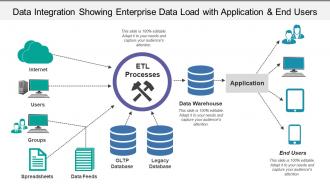
Presenting this set of slides with name - Data Integration Showing Enterprise Data Load With Application And End Users. This is a three stage process. The stages in this process are Data Integration, Data Management, Data Analysis.

Presenting this set of slides with name - Data Governance Powerpoint Presentation Slides. This PPT deck displays twenty-five slides with in-depth research. We provide a ready to use deck with all sorts of relevant topics subtopics templates, charts and graphs, overviews, analysis templates. This template is compatible with Google Slides, which makes it accessible at once. Can be converted into various formats like PDF, JPG, and PNG. The slide is easily available in both 4:3 and 16:9 aspect ratio.

Hassle free, simple and fast download. Thoroughly modifiable text as per your need. It allows you to alter the color schemes and contrast to suit the contextual requirement and personalize in respect to logo change and including your trademark. Absolutely editable orientation along with size of PPT icons. No change in the original resolution of presentation images post editing.

These graphics are 100% editable to your needs. 46 uniquely designed slides. Instantly download with just a single mouse click. Standard and widescreen compatibility for all devices. Can be opened with Google Slides also. Suitable for use by businessmen, team leaders, and firms. Premium Customer support service. The stages in this process are success, business, management, planning, project.
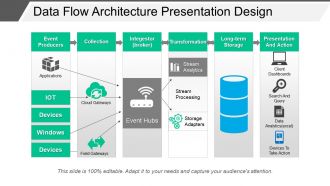
Presenting, the data flow architecture presentation PowerPoint deck. This data flow architecture PPT runs steadily and on various software. You can now steadily convert it into a JPG, PDF or even both formats for ease! Compatible with Google Slides and available in both standard 4:3 and widescreen format 16:9 after downloading. Widescreen projection without PPT graphics pixelation. Availability to insert company logo, name, and trademark for personalization has been taken care of. This is an entirely customizable PPT layout that includes font, text, color, and design. Download this design within a snap.
Fine quality, high resolution PPT icons. Bright coloured PPT graphics for a vibrant visual impact. Customisation of any icon as per need of the hour. Easy inclusion and exclusion of data possible. Hassle free conversion into varied formats. Compatible with multiple info graphic software. Beneficial for business owners, managers, investors, financers, marketers, entrepreneurs, teachers, students.
Flawless quality of components used in the designing. Presentation image can be viewed in both standard 4:3 and widescreen 16:9 display. Immediate download and simple to share with large audience. Convenience to modify the content as per the industry requirement. PowerPoint visual well-suited with Google slides. PPT design accessible with different nodes and stages. Access to add business details such as icon, image or text.
This bundle contains high-resolution powerpoint slides which are compatible with the widescreen view and Google slides. You can easily convert these into PDF or JPEG formats. Tantalizing graphs are included for comparison which can be easily personalized. Students, analysts, and marketing professionals can use these powerpoint slides for a prime experience. You can utilize these PPT's in any way after downloading.
Enthrall your audience with this Enterprise Cyber Security Awareness Employees Training Complete Deck. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising fifty four slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.

This PowerPoint Presentation contains 74 slides. PowerPoint product can be customized as per your requirements. PPT files can be appeared in both formats standard and widescreen. All slides provided in this product are compatible with Google Slides. PPT is useful for project managers to present how to deliver more value with less waste in the project context. This is a one stage process. The stages in this process are project life cycle, project scope, project objectives, project planning process, project lifecycle phases, project budgeting.

This complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Data Driven Strategy Analytics Technology Approach Corporate and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of thirteen slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.
Presenting digital transformation people process technologies powerpoint guide. This is a digital transformation people process technologies powerpoint guide. This is a three stage process. The stages in this process are digital transformation.

Presenting this set of slides with name Right Aligned Spokes Centralized Network. This is a seven stage process. The stages in this process are Right Aligned Spokes, Centralized Network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Presenting digital transformation overview ppt slide. This is a digital transformation overview ppt slide. This is a three stage process. The stages in this process are digital transformation.

100% editable slides to match your taste. 50 ready-made visuals having deeply researched content. Download all slides with just a click. Standard and widescreen compatibility for all devices. Can be opened in Google Slides also. Suitable for use by server administrators, data researchers, and companies. Premium Customer support service. The professionally designed editable and multipurpose deck constituents are predictive analytics, user behavior analytics, data processing, data management, data information.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Privacy IT Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the sixty five slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

Presenting this set of slides with name - Digital Transformation Strategy Powerpoint Presentation Slides. Our topic-specific Digital Transformation Strategy Powerpoint Presentation Slides presentation deck contains twenty-three slides to formulate the topic with a sound understanding. . A range of editable and ready to use slides with all sorts of relevant charts and graphs, overviews, topics subtopics templates, and analysis templates makes it all the more worth. PPT slides are accessible in both widescreen and standard format. PowerPoint templates are compatible with Google Slides. Quick and risk-free downloading process. It can be easily converted into JPG or PDF format

Presenting Data Analytics Five Years Action Plan Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.

This PowerPoint presentation contains 74 slides. PowerPoint presentation is useful for project managers. Presentation templates are available in both widescreen & standard format. This PPT design has full editable graphics, users can modify it according to their requirements. All our content given in this deck is compatible with Google Slides. We offer premium customer support. The editable deck constituents of this deck are project management life cycle methodology , project management, value management, project accounting, project governance.

Presenting our Cyber Security for Organization Proposal PowerPoint Presentation Slides. This is a completely adaptable PPT slide that allows you to add images, charts, icons, tables, and animation effects according to your requirements. Create and edit your text in this 100% customizable slide. It is also available in widescreen. You can change the orientation of any element in your presentation according to your liking. The slide is available in both 4:3 and 16:9 aspect ratio. These PPT slides are also compatible with Google slides.
This slide focuses on five different elements of IT project management process which includes establishing project management structure, defining project, creating plan, management and control, closing, etc with identifying necessary resources. Introducing our Five Elements Of IT Project Management Process set of slides. The topics discussed in these slides are Project Definition, Project Plan, Project Close, Project Management And Control, Management Structure. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.

Introducing Agile Planning PowerPoint Presentation Slides. There are 21 high-quality slides in this complete PPT deck. All the templates are entirely editable. You can personalize font, text, patterns, background, and colors according to your wish. It is also possible to convert the PowerPoint slideshow into PDF, PNG, or JPG. You may even view it on Google Slides. Moreover, this PPT template deck is compatible with multiple screen aspect ratios and works well on standard and widescreens.

Presenting our project management methodologies PowerPoint presentation slide. This PPT layout holds forty six slides and each slide is accessible in standard as well as wide-screen formats. It is completely editable as per your requirements and preferences as well. You can use it with Microsoft Office, Google slides and many other presentation software.

This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes ITIL 4 Framework And Best Practices Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of sixty nine slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
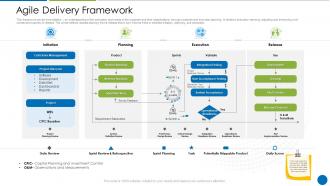
This framework moves from Initiation an understanding of the motivation and needs of the customer and their stakeholders through customer and innovator planning, to iterative execution, learning, adjusting and enhancing over consecutive sprints, to release. The whole method repeats learning from a release that in turn informs fresh or modified initiation, planning, and execution. Deliver an outstanding presentation on the topic using this Agile Delivery Framework Disciplined Agile Delivery. Dispense information and present a thorough explanation of Initiation, Planning, Execution, Release using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.

Presenting this set of slides with name - Devops Powerpoint Presentation Slides. This presentation comprises a total of twentyone slides. Each slide focuses on one of the aspects of Devops Powerpoint Presentation Slides with content extensively researched by our business research team. Our team of PPT designers used the best of professional PowerPoint templates, images, icons and layouts. Also included are impressive, editable data visualization tools like charts, graphs and tables. When you download this presentation by clicking the Download button, you get the presentation in both standard and widescreen format. All slides are fully customizable. Change the colors, font, size, add and remove things as per your need and present before your audience.
Presenting this set of slides with name - Agile Development Showing User Stories With Sprint And Launch. This is a three stage process. The stages in this process are Sprint Planning, Scrum Development, Agile Development.

This complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on How To Present Cyber Security To Senior Management Complete Deck and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of fifty five slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.
Preference to modify the content according to the business requirement. PowerPoint template accessible with different nodes and stages. Presentation graphic downloadable in standard and widescreen display view. Swift download and easy to share with large set of viewers. Adjustable PPT shape as easy to convert into JPG and PDF. Choice to add commercial details such as icon, image or insignia. Picture-perfect quality of pictures and images used in the designing. Similar designs accessible with different nodes and stages. Downloading is quick and saves you valuable time.
Pliable PPT graphic as can be customized as per your requirement. Stupendous quality PowerPoint visual with great display. Contents of slide design completely amendable to the extent. Numerous options like JPG and PDF for saving the presentation design. Easy addition or removal of unwanted elements as per your convenience. PPT illustration downloadable with different nodes and stages.

Presenting Training Deck on Building an AI-Driven Future Essential Strategies for Business Success. This deck comprises of 72 slides. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content, and present it confidently.
Images can be resized and colored. Color, style and position can be standardized, supports font size which can be read from a distance. PPT slide is compatible with Microsoft 2010 and 2013 versions. Beneficial for business people, entrepreneurs, lawyers, trade and nonprofit organizations. Background in PPT graphic is subtle and consistent to avoid presentation look flashy or vibrant.

Presenting this set of slides with name - Futuristic Modern Interactive Technology Elements. This is a four stage process. The stages in this process are Futuristic, Technology, Modern.
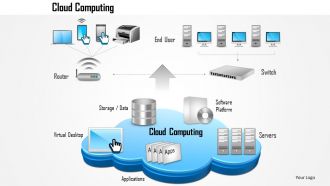
We are proud to present our 1114 entire cloud computing infrastructure with allications end users and office computers ppt slide. Define the infrastructure of cloud computing with this innovative PPT slide. This PPT slide contains the allication and end users in cloud system. Use this PPT slide and build an amazing presentation for your viewers.

Presenting robotic process automation PowerPoint presentation slide. It covers total of 23 professionally designed PPT slides. Our PowerPoint experts have included all the necessary layouts, diagrams and templates to meet the needs of the customers. This content ready deck is completely customizable. Edit the color, text and icon as per your requirement. You can also add or delete the content from the presentation as per your need. You can easily download this presentation. They are high resolution PPT templates and are perfectly compatible with Google Slides.
Presentation design quickly downloadable. Easy to save into JPEG and PDF document. PPT diagrams are harmonious with Google slides. Flexible to share in widescreen view as amazing picture quality. Easy to alter color, text, font and shape. Similar designs accessible with different nodes and stages as required. Presentable and simple to comprehend into graphic format.
Item 1 to 60 of 7365 total items
- You're currently reading page 1

Google Cloud Next 2024: Everything announced so far
Google’s Cloud Next 2024 event takes place in Las Vegas through Thursday, and that means lots of new cloud-focused news on everything from Gemini, Google’s AI-powered chatbot , to AI to devops and security. Last year’s event was the first in-person Cloud Next since 2019, and Google took to the stage to show off its ongoing dedication to AI with its Duet AI for Gmail and many other debuts , including expansion of generative AI to its security product line and other enterprise-focused updates and debuts .
Don’t have time to watch the full archive of Google’s keynote event ? That’s OK; we’ve summed up the most important parts of the event below, with additional details from the TechCrunch team on the ground at the event. And Tuesday’s updates weren’t the only things Google made available to non-attendees — Wednesday’s developer-focused stream started at 10:30 a.m. PT .
Google Vids
Leveraging AI to help customers develop creative content is something Big Tech is looking for, and Tuesday, Google introduced its version. Google Vids, a new AI-fueled video creation tool , is the latest feature added to the Google Workspace.
Here’s how it works: Google claims users can make videos alongside other Workspace tools like Docs and Sheets. The editing, writing and production is all there. You also can collaborate with colleagues in real time within Google Vids. Read more
Gemini Code Assist
After reading about Google’s new Gemini Code Assist , an enterprise-focused AI code completion and assistance tool, you may be asking yourself if that sounds familiar. And you would be correct. TechCrunch Senior Editor Frederic Lardinois writes that “Google previously offered a similar service under the now-defunct Duet AI branding.” Then Gemini came along. Code Assist is a direct competitor to GitHub’s Copilot Enterprise. Here’s why
And to put Gemini Code Assist into context, Alex Wilhelm breaks down its competition with Copilot, and its potential risks and benefits to developers, in the latest TechCrunch Minute episode.
Google Workspace
Image Credits: Google
Among the new features are voice prompts to kick off the AI-based “Help me write” feature in Gmail while on the go . Another one for Gmail includes a way to instantly turn rough email drafts into a more polished email. Over on Sheets, you can send out a customizable alert when a certain field changes. Meanwhile, a new set of templates make starting a new spreadsheet easier. For the Doc lovers, there is support for tabs now. This is good because, according to the company, you can “organize information in a single document instead of linking to multiple documents or searching through Drive.” Of course, subscribers get the goodies first. Read more
Google also seems to have plans to monetize two of its new AI features for the Google Workspace productivity suite. This will look like $10/month/user add-on packages. One will be for the new AI meetings and messaging add-on that takes notes for you, provides meeting summaries and translates content into 69 languages. The other is for the introduced AI security package, which helps admins keep Google Workspace content more secure. Read more
In February, Google announced an image generator built into Gemini, Google’s AI-powered chatbot. The company pulled it shortly after it was found to be randomly injecting gender and racial diversity into prompts about people. This resulted in some offensive inaccuracies. While we waited for an eventual re-release, Google came out with the enhanced image-generating tool, Imagen 2 . This is inside its Vertex AI developer platform and has more of a focus on enterprise. Imagen 2 is now generally available and comes with some fun new capabilities, including inpainting and outpainting. There’s also what Google’s calling “text-to-live images” where you can now create short, four-second videos from text prompts, along the lines of AI-powered clip generation tools like Runway , Pika and Irreverent Labs . Read more
Vertex AI Agent Builder
We can all use a little bit of help, right? Meet Google’s Vertex AI Agent Builder, a new tool to help companies build AI agents.
“Vertex AI Agent Builder allows people to very easily and quickly build conversational agents,” Google Cloud CEO Thomas Kurian said. “You can build and deploy production-ready, generative AI-powered conversational agents and instruct and guide them the same way that you do humans to improve the quality and correctness of answers from models.”
To do this, the company uses a process called “grounding,” where the answers are tied to something considered to be a reliable source. In this case, it’s relying on Google Search (which in reality could or could not be accurate). Read more
Gemini comes to databases
Google calls Gemini in Databases a collection of features that “simplify all aspects of the database journey.” In less jargony language, it’s a bundle of AI-powered, developer-focused tools for Google Cloud customers who are creating, monitoring and migrating app databases. Read more
Google renews its focus on data sovereignty

Image Credits: MirageC / Getty Images
Google has offered cloud sovereignties before, but now it is focused more on partnerships rather than building them out on their own. Read more
Security tools get some AI love

Image Credits: Getty Images
Google jumps on board the productizing generative AI-powered security tool train with a number of new products and features aimed at large companies. Those include Threat Intelligence, which can analyze large portions of potentially malicious code. It also lets users perform natural language searches for ongoing threats or indicators of compromise. Another is Chronicle, Google’s cybersecurity telemetry offering for cloud customers to assist with cybersecurity investigations. The third is the enterprise cybersecurity and risk management suite Security Command Center. Read more
Nvidia’s Blackwell platform
One of the anticipated announcements is Nvidia’s next-generation Blackwell platform coming to Google Cloud in early 2025. Yes, that seems so far away. However, here is what to look forward to: support for the high-performance Nvidia HGX B200 for AI and HPC workloads and GB200 NBL72 for large language model (LLM) training. Oh, and we can reveal that the GB200 servers will be liquid-cooled. Read more
Chrome Enterprise Premium
Meanwhile, Google is expanding its Chrome Enterprise product suite with the launch of Chrome Enterprise Premium . What’s new here is that it mainly pertains mostly to security capabilities of the existing service, based on the insight that browsers are now the endpoints where most of the high-value work inside a company is done. Read more
Gemini 1.5 Pro
Everyone can use a “half” every now and again, and Google obliges with Gemini 1.5 Pro. This, Kyle Wiggers writes, is “Google’s most capable generative AI model,” and is now available in public preview on Vertex AI, Google’s enterprise-focused AI development platform. Here’s what you get for that half: T he amount of context that it can process, which is from 128,000 tokens up to 1 million tokens, where “tokens” refers to subdivided bits of raw data (like the syllables “fan,” “tas” and “tic” in the word “fantastic”). Read more
Open source tools

At Google Cloud Next 2024, the company debuted a number of open source tools primarily aimed at supporting generative AI projects and infrastructure. One is Max Diffusion, which is a collection of reference implementations of various diffusion models that run on XLA, or Accelerated Linear Algebra, devices. Then there is JetStream, a new engine to run generative AI models. The third is MaxTest, a collection of text-generating AI models targeting TPUs and Nvidia GPUs in the cloud. Read more
We don’t know a lot about this one, however, here is what we do know : Google Cloud joins AWS and Azure in announcing its first custom-built Arm processor, dubbed Axion. Frederic Lardinois writes that “based on Arm’s Neoverse 2 designs, Google says its Axion instances offer 30% better performance than other Arm-based instances from competitors like AWS and Microsoft and up to 50% better performance and 60% better energy efficiency than comparable X86-based instances.” Read more
The entire Google Cloud Next keynote
If all of that isn’t enough of an AI and cloud update deluge, you can watch the entire event keynote via the embed below.
Google Cloud Next’s developer keynote
On Wednesday, Google held a separate keynote for developers . They offered a deeper dive into the ins and outs of a number of tools outlined during the Tuesday keynote, including Gemini Cloud Assist, using AI for product recommendations and chat agents, ending with a showcase from Hugging Face. You can check out the full keynote below.

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
- Get Involved
Know2Protect

Know2Protect is a forthcoming Department of Homeland Security (DHS) national public awareness campaign to educate and empower children, teens, parents, trusted adults, and policymakers to prevent and combat online child sexual exploitation and abuse (CSEA); explain how to report online enticement and victimization; and offer response and support resources for victims and survivors of online child sexual exploitation. The campaign will launch Spring 2024.
Know2Protect's Purpose
Online CSEA is a horrific crime that targets some of the most vulnerable people in our communities – our children and teens. It includes a broad range of criminal acts that involve the victimization of a minor for sexual gratification or some other personal or financial gain.
DHS’ Homeland Security Investigations (HSI) is a global leader in combating online CSEA. Despite the collaborative work with key partners, online CSEA is growing at an alarming rate and HSI cannot investigate and arrest its way out of this crisis.
In the last decade, this crime has increased exponentially and is now a global epidemic. The lack of understanding of online CSEA and increased technology use among children and teens has created space for these crimes to flourish. For too long, our communities have been left on their own when it comes to understanding the online dangers that exist and how to prevent them.
Know2Protect will shine a spotlight on this horrific crime. It will rely on the expertise and authority of HSI special agents tasked with finding online predators and bringing them to justice. It will spread awareness about these global threats, share preventative strategies to stop future victimization, empower the public to report suspected abuse, and support survivors of online CSEA.
Project iGuardian TM

Project iGuardian TM is the official in-person educational arm of the forthcoming Know2Protect campaign to teach the public about the ongoing threats children and teens face from online predators. These presentations rely on HSI subject matter expertise, their unique law enforcement perspective and authorities that have led to successful investigations and prosecutions. Project iGuardian is designed to inform children, teens, parents, and trusted adults on the threat of online child sexual exploitation and abuse (CSEA), how to implement preventative strategies, and report suspected abuse to law enforcement.

Meet the iGuardians TM
A savvy duo of HSI special agents and their trusty canine sidekick join forces with a student and teacher to form our team of iGuardians TM . They spread Know2Protect’s call to action: educate the public on the dangers of online CSEA, help prevent future crimes, and empower the public to report suspected abuse.
Schedule an iGuardian TM Presentation
The Project iGuardian™ team is available to inform your community of ways to protect children and teens from online predators. Our presentations are delivered by HSI special agents and other subject matter experts. These audience-specific presentations are given to schools, community groups, corporations, and nonprofit organizations that are looking to learn more and join the fight against online CSEA.
To request a presentation, email us at [email protected] .
- Homeland Security Investigations (HSI)
- Immigration and Customs Enforcement (ICE)

IMAGES
VIDEO
COMMENTS
Managing a small business is always challenging but keeping up with cybersecurity threats can be overwhelming. How do you learn about the latest threats? How do you educate your staff about best practices? NIST has prepared a training presentation (draft) that you can use to self-teach and help your team learn at the same time.
The USP of this presentation template is the slide on cyber security awareness trends in 2023, an almost real-time repository of information. Statistics on the lack of cybersecurity awareness create an urgency about the issue that it deserves. Download this slide now and master your defences against the unseen warrior.
Download your presentation as a PowerPoint template or use it online as a Google Slides theme. 100% free, no registration or download limits. Use these IT security templates to create secure and informative presentations that protect your data. No Download Limits Free for Any Use No Signups.
\爀ꀀ屲The Cybersecurity and Infrastructure Security Agency \⠀䌀䤀匀䄀尩 leads Cybersecurity Awareness Month alongside private sector對 partner, the National Cyber Security Alliance \⠀一䌀匀䄀尩. They work closely with partners at all levels to help enhance our Natio\൮'s cybersecurity posture through engagement with their ...
Slides 3 through 6 should discuss how external events will affect security, an assessment of the existing risk position (this can change depending on acquisitions and other events) and the entire security strategy. Slide 7: The call to action. Finally, wrap up the presentation with a closing slide to reiterate your main points and any action items.
It has an image of a big key is the main focus of this background. 6. Cybercrime Prevention - Free Cyber Security PPT Template. If you want to create a cyber security PowerPoint strategy, this is a great option. It includes an image of a shield or security logo is part of this background.
Slides 3 through 6 should discuss how external events will affect security, an assessment of the existing risk position (this can change depending on acquisitions and other events) and the entire security strategy. Slide 7: The call to action. Finally, wrap up the presentation with a closing slide to reiterate the main points and any action items.
The security automation and machine learning ppt is published by Siemplify, a security platform in January this year and has got more than 100 viewers. It includes a basic introduction to cybersecurity and machine learning, types of machine learning techniques, security analysis for machine learning, threats on machine learning, machine ...
Then revisit the security presentations for new staff and as refresher training for all staff at least every 2 years. 10. Get feedback and act on it. It's important to get feedback on the security awareness presentation - via questionnaires completed by the attendees, for example - to identify any changes that might be useful when carrying ...
Experience Gartner Conferences. Join your peers for the unveiling of the latest insights at Gartner conferences. Use this presentation template to educate business stakeholders on how they can work with Information Security and the value security adds to business outcomes.
This Cyber Security Roadmap template for Google Slides and PowerPoint provides a roadmap to ensure the safety of your digital assets. Constructed with a cool, modern blue aesthetic, it instills both confidence and serenity. It showcases a range of factors from threat identification to mitigation measures. This visual timeline indicates the ...
Below are some of the topics you may want to cover in your first presentation: A high-level overview of different threat actors. Risks to your cybersecurity environment (i.e., the things you're concerned about). The type of data you think is most critical or sensitive.
In addition, computer security PPT contains the critical elements of information security, network risk identification and assessment, steps to mitigate those risks, benefits of information security, and automations role in information security. Further, this data security presentation comes with a checklist to implement information security in ...
Cyber Security Presentation Templates. Master the art of secure digital communication with Slide Egg's free cyber security PowerPoint templates and Google Slides. Our 100% editable designs make complex security concepts easy to understand. Ideal for IT professionals, educators, and students. Make cyber security conversations clear and bring ...
IT Security Presentation. Jan 28, 2010 •. 4 likes • 11,210 views. E. elihuwalker. 1 of 7. Download Now. Download to read offline. IT Security Presentation - Download as a PDF or view online for free.
Use IT security PowerPoint Presentation Slides to educate your audience about the cyber security. Incorporate professionally designed content-ready IT security PPT templates to showcase the techniques of protecting computers, networks, programs, and data from attacks that are aimed for exploitation. Demonstrate the preventive measures to ...
2. AI and the impact on Cybersecurity. Published in October 2019, the AI and impact on Cybersecurity presentation by Graham Mann cover the explanation of what AI is and its impact on cybersecurity. The presentation includes content like the importance of AI, cloud computing, machine learning algorithms, and blockchain.
Security Presentation templates Safety is one of the most important things in a community and there are so many people involved in different security bodies to assure that there is no danger around. If you want to speak about security in every way and form possible, we are glad to inform you that you are absolutely safe using these Google ...
Use IT security PowerPoint Presentation Slides to educate your audience about the cyber security. Incorporate professionally designed content-ready IT security PPT templates to showcase the techniques of protecting computers, networks, programs, and data from attacks that are aimed for exploitation. Demonstrate the preventive measures to ...
When preparing that key presentation, CSOs might consider integrating the following 10 elements to help manage that all-important, ever-worrisome matter of presenting "Security" in a Board ...
I give introduction to security presentations to non-profits from time to time and they're usually about an hour. I cover the importance of security, data/asset security, social engineering, and password security. In 10 minutes I'd probably talk about good password security like u/grabherbythecovfefe suggested...
Among candidates for the NIST PQC additional call for digital signatures, there exist seven UOV-based multivariate schemes. Further, four UOV-based candidates, MAYO, QR-UOV, VOX, and SNOVA, achieve small public key size compared with the plain UOV. This work gives a new security analysis for these UOV variants with small public keys. Our main contributions are the following two points: First ...
IT Security. An Image/Link below is provided (as is) to download presentation Download Policy: Content on the Website is provided to you AS IS for your information and personal use and may not be sold / licensed / shared on other websites without getting consent from its author. Download presentation by click this link.
Encompassed with stylized slides presenting various concepts, this Cyber Security It Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the eighty one slides are editable and modifiable, so feel free to adjust them to your business setting. ...
Google jumps on board the productizing generative AI-powered security tool train with a number of new products and features aimed at large companies. Those include Threat Intelligence, which can ...
Know2Protect is a forthcoming Department of Homeland Security (DHS) national public awareness campaign to educate and empower children, teens, parents, trusted adults, and policymakers to prevent and combat online child sexual exploitation and abuse (CSEA); explain how to report online enticement and victimization; and offer response and support resources for victims and survivors of online ...